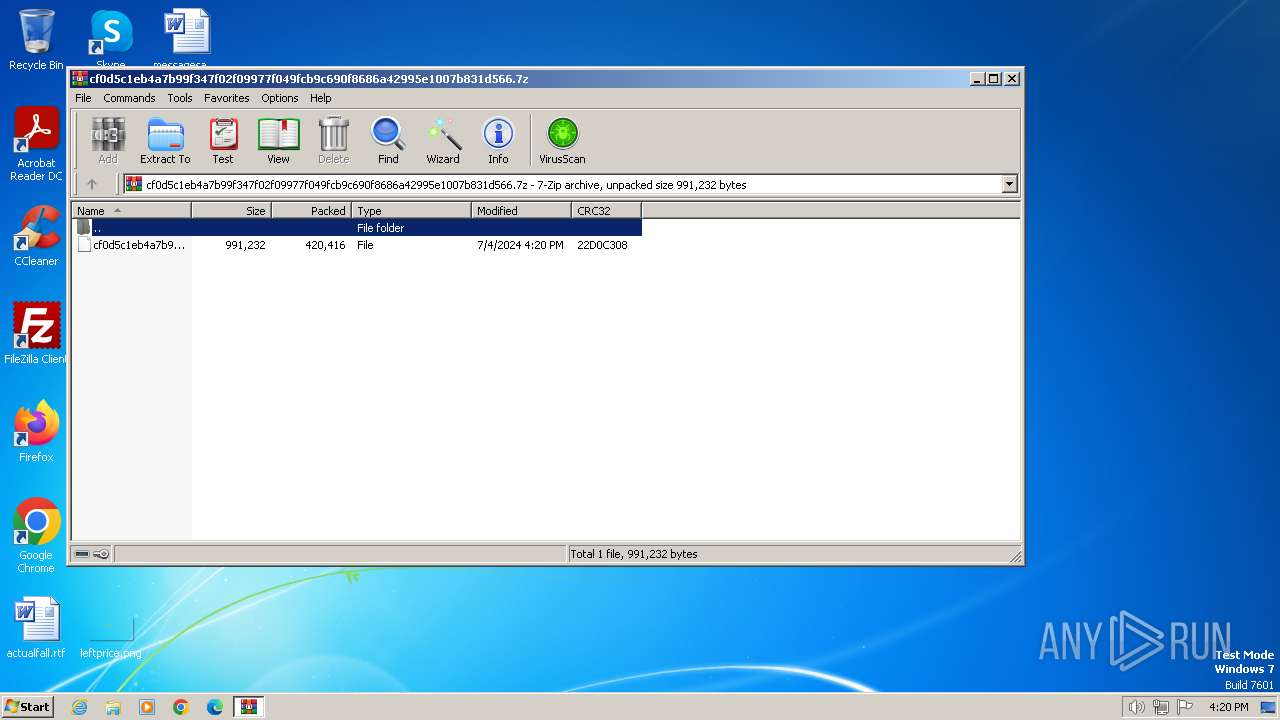
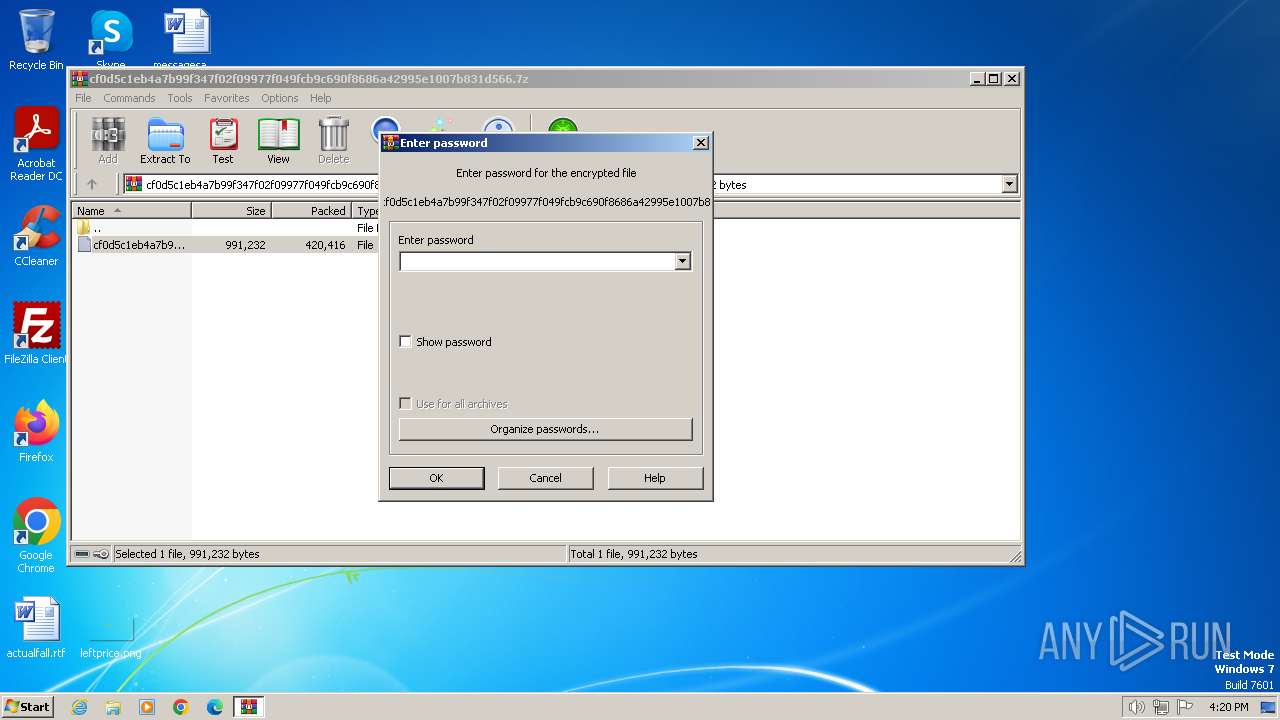
| File name: | cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.7z |
| Full analysis: | https://app.any.run/tasks/3739197c-0c3c-42fc-88c5-bd046d3993e7 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 15:20:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 418767DF792C8DF04D2A693B37C77C94 |
| SHA1: | A034F987F8042FF01FAF92AAE38842EC5200E121 |
| SHA256: | FC6FC38D83635663EF57ACB9CBDC7F3E4DBEE67858988B69E33D71F6A79CD291 |
| SSDEEP: | 12288:D/7YYGQ9a1wjNSIs1om98S9MeFxf07NICLcW9gu+HzllIrdw7AXmN3o1TMZ:b7YYGQ9ayjNDsOm9r9MeFxf07N1cW9gz |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3416)
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
Changes the autorun value in the registry
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
Connects to the CnC server
- Synaptics.exe (PID: 1980)
SUSPICIOUS
Reads security settings of Internet Explorer
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- Synaptics.exe (PID: 1980)
Executable content was dropped or overwritten
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
Reads the date of Windows installation
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
Reads the Internet Settings
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- Synaptics.exe (PID: 1980)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 1980)
Checks Windows Trust Settings
- Synaptics.exe (PID: 1980)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 1980)
Reads settings of System Certificates
- Synaptics.exe (PID: 1980)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 1980)
INFO
Reads the computer name
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- Synaptics.exe (PID: 1980)
Checks supported languages
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- ._cache_cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 2752)
- Synaptics.exe (PID: 1980)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3416)
Creates files in the program directory
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- Synaptics.exe (PID: 1980)
Manual execution by a user
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- chrome.exe (PID: 3132)
Reads the machine GUID from the registry
- cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe (PID: 3212)
- Synaptics.exe (PID: 1980)
Checks proxy server information
- Synaptics.exe (PID: 1980)
Application launched itself
- chrome.exe (PID: 3132)
Create files in a temporary directory
- Synaptics.exe (PID: 1980)
Creates files or folders in the user directory
- Synaptics.exe (PID: 1980)
Reads the software policy settings
- Synaptics.exe (PID: 1980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
MPEG
| MPEGAudioVersion: | 2 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 48 kbps |
| SampleRate: | 24000 |
| ChannelMode: | Joint Stereo |
| MSStereo: | Off |
| IntensityStereo: | Off |
| CopyrightFlag: | - |
| OriginalMedia: | |
| Emphasis: | CCIT J.17 |
Composite
| Duration: | 0:01:10 (approx) |
|---|
Total processes
68
Monitored processes
25
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6aaa8b38,0x6aaa8b48,0x6aaa8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3832 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3812 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1108 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3112 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1980 | "C:\ProgramData\Synaptics\Synaptics.exe" InjUpdate | C:\ProgramData\Synaptics\Synaptics.exe | cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2116 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1380 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1284 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2800 --field-trial-handle=1128,i,2494035922413245836,610974833084478508,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
22 377
Read events
22 090
Write events
278
Delete events
9
Modification events
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.7z | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
169
Text files
35
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF580ff.TMP | — | |
MD5:— | SHA256:— | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3416.26229\cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566 | executable | |
MD5:84BC432D6136C6593F18D7D73F2CCB3B | SHA256:CF0D5C1EB4A7B99F347F02F09977F049FCB9C690F8686A42995E1007B831D566 | |||
| 3212 | cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe | C:\ProgramData\Synaptics\RCX1AB3.tmp | executable | |
MD5:53A60CB0E461FD7B1E5AD57E428A2B2B | SHA256:D37592E317BD6283512624CB206440F67B6FBF4937F175AD8BAD0338C7D7FAE6 | |||
| 3212 | cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:84BC432D6136C6593F18D7D73F2CCB3B | SHA256:CF0D5C1EB4A7B99F347F02F09977F049FCB9C690F8686A42995E1007B831D566 | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:456D3EF989973A7C218E338A6CFFAD25 | SHA256:75631D994431F254B94255C50038A3657BFC45D76FCE9D794D514E57CA678872 | |||
| 3212 | cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe | C:\Users\admin\Desktop\._cache_cf0d5c1eb4a7b99f347f02f09977f049fcb9c690f8686a42995e1007b831d566.exe | executable | |
MD5:ECE1444158A600A00E018EFE4CAC5DBE | SHA256:11A506B6D25226A4F1308258037842D24AE6B1B5C885905DA448E82511091B4F | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF5840c.TMP | — | |
MD5:— | SHA256:— | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF580ff.TMP | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
67
DNS requests
73
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
1980 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | unknown |
2512 | chrome.exe | GET | — | 216.239.32.21:80 | http://virustotal.com/ | unknown | — | — | unknown |
844 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
1980 | Synaptics.exe | GET | 200 | 142.250.185.99:80 | http://crl.pki.goog/gsr1/gsr1.crl | unknown | — | — | unknown |
844 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
844 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1980 | Synaptics.exe | 69.42.215.252:80 | freedns.afraid.org | AWKNET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
xred.mooo.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3 ETPRO signatures available at the full report