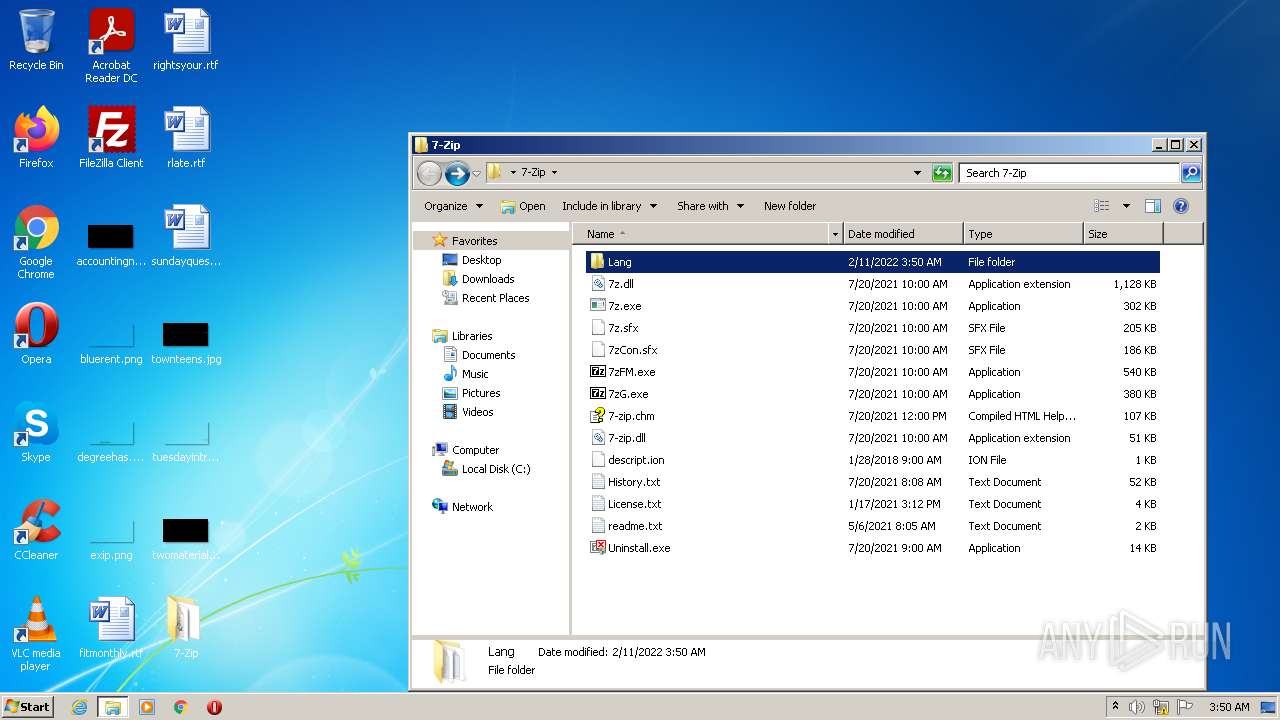
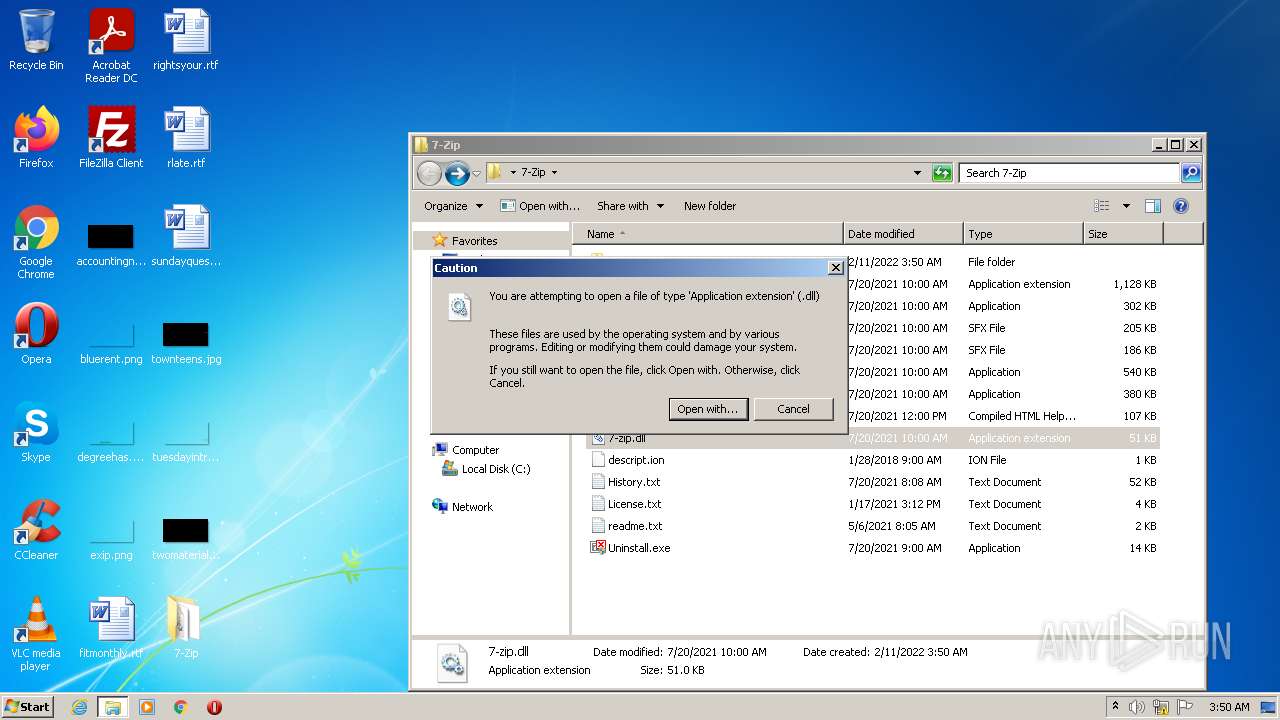
| File name: | Vulkan-5.0-X-mas-edition_70726.exe |
| Full analysis: | https://app.any.run/tasks/c9dc323b-28e2-4f08-bbad-9eda46f3bf0a |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2022, 03:49:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F31477735EA3A00A5EC85D2BB99D5BCD |
| SHA1: | 111E19CCCDC0B9FB097AD734B7663CB2DF7C1FC9 |
| SHA256: | FC641328409E6F96D3CEB0E3C0E23F6AEBEB7CE8BB7984E679D72291B4DB056A |
| SSDEEP: | 49152:CgwRjdTyuTVDUK8obXKMrk9hfQpc16O3N1+qnvgLkO7Z+8Ufc4:CgwRjdukDUK8ob60ehf51x9w28hUfJ |
MALICIOUS
Application was dropped or rewritten from another process
- LIKEDADApp.exe (PID: 1232)
- LIKEDADApp.exe (PID: 548)
- LIKEfApp.exe (PID: 1972)
- 7z.exe (PID: 2248)
- 7z.exe (PID: 1344)
- 7z.exe (PID: 148)
- 7z.exe (PID: 3652)
- 7z.exe (PID: 3996)
- 7z.exe (PID: 524)
- 7z.exe (PID: 3176)
Loads dropped or rewritten executable
- LIKEDADApp.exe (PID: 548)
- SearchProtocolHost.exe (PID: 3712)
- Explorer.EXE (PID: 964)
SUSPICIOUS
Checks supported languages
- LIKEDADApp.exe (PID: 1232)
- Vulkan-5.0-X-mas-edition_70726.exe (PID: 3740)
- LIKEDADApp.exe (PID: 548)
- LIKEfApp.exe (PID: 1972)
- cmd.exe (PID: 2648)
- cmd.exe (PID: 3956)
- 7z.exe (PID: 1344)
- 7z.exe (PID: 2248)
- 7z.exe (PID: 148)
- 7z.exe (PID: 3176)
- 7z.exe (PID: 3652)
- 7z.exe (PID: 3996)
- 7z.exe (PID: 524)
Executable content was dropped or overwritten
- Vulkan-5.0-X-mas-edition_70726.exe (PID: 3740)
- LIKEDADApp.exe (PID: 548)
- LIKEfApp.exe (PID: 1972)
Reads the computer name
- Vulkan-5.0-X-mas-edition_70726.exe (PID: 3740)
- LIKEDADApp.exe (PID: 1232)
- LIKEDADApp.exe (PID: 548)
- LIKEfApp.exe (PID: 1972)
Application launched itself
- LIKEDADApp.exe (PID: 1232)
- cmd.exe (PID: 2648)
Creates a directory in Program Files
- LIKEDADApp.exe (PID: 548)
Creates files in the program directory
- LIKEDADApp.exe (PID: 548)
- LIKEfApp.exe (PID: 1972)
Starts CMD.EXE for commands execution
- LIKEDADApp.exe (PID: 548)
- cmd.exe (PID: 2648)
Creates/Modifies COM task schedule object
- LIKEfApp.exe (PID: 1972)
Creates files in the user directory
- Explorer.EXE (PID: 964)
Creates a software uninstall entry
- LIKEfApp.exe (PID: 1972)
Uses RUNDLL32.EXE to load library
- Explorer.EXE (PID: 964)
INFO
Checks supported languages
- timeout.exe (PID: 2816)
- NOTEPAD.EXE (PID: 3104)
- rundll32.exe (PID: 1512)
- hh.exe (PID: 3548)
Manual execution by user
- NOTEPAD.EXE (PID: 3104)
- 7z.exe (PID: 2248)
- 7z.exe (PID: 1344)
- 7z.exe (PID: 524)
- 7z.exe (PID: 3176)
- 7z.exe (PID: 148)
- 7z.exe (PID: 3652)
- 7z.exe (PID: 3996)
- rundll32.exe (PID: 1512)
Reads the computer name
- rundll32.exe (PID: 1512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| ProductVersion: | 1.55.0.4 |
|---|---|
| ProductName: | LIKE DAD App |
| OriginalFileName: | LIKEDADApp.exe |
| LegalCopyright: | LIKE DAD (c). All rights reserved |
| InternalName: | LIKEDADApp.exe |
| FileVersion: | 1.55.0.4 |
| FileDescription: | LIKE DAD App |
| CompanyName: | LIKE DAD |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.55.0.4 |
| FileVersionNumber: | 1.55.0.4 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x1942f |
| UninitializedDataSize: | - |
| InitializedDataSize: | 89088 |
| CodeSize: | 101888 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| TimeStamp: | 2012:12:31 01:38:51+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 31-Dec-2012 00:38:51 |
| Detected languages: |
|
| CompanyName: | LIKE DAD |
| FileDescription: | LIKE DAD App |
| FileVersion: | 1.55.0.4 |
| InternalName: | LIKEDADApp.exe |
| LegalCopyright: | LIKE DAD (c). All rights reserved |
| OriginalFilename: | LIKEDADApp.exe |
| ProductName: | LIKE DAD App |
| ProductVersion: | 1.55.0.4 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0060 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000060 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 31-Dec-2012 00:38:51 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00018DDE | 0x00018E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.67402 |
.rdata | 0x0001A000 | 0x00003BCA | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.71339 |
.data | 0x0001E000 | 0x00004DEC | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.45098 |
.rsrc | 0x00023000 | 0x00011514 | 0x00011600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.74701 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.01659 | 1656 | Latin 1 / Western European | English - United States | RT_MANIFEST |
5 | 1.43775 | 52 | UNKNOWN | English - United States | RT_STRING |
500 | 3.09294 | 184 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
65
Monitored processes
19
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Users\admin\Desktop\7-Zip\7z.exe" | C:\Users\admin\Desktop\7-Zip\7z.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 21.03 beta Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\7-Zip\7z.exe" | C:\Users\admin\Desktop\7-Zip\7z.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 21.03 beta Modules
| |||||||||||||||
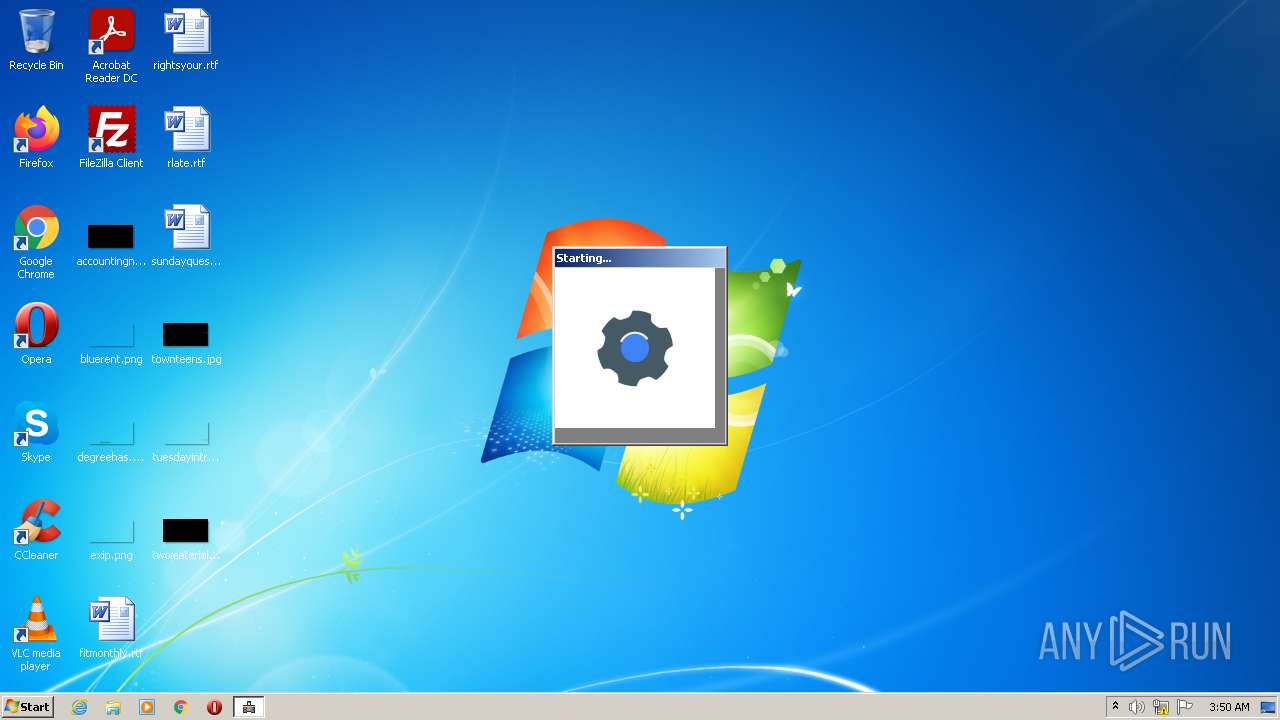
| 548 | "C:\Users\admin\AppData\Local\LIKEDAD\LIKEDADApp.exe" "C:\Users\admin\AppData\Local\Temp\Vulkan-5.0-X-mas-edition_70726.exe" uFKFzIV41XSN1aEcu2vpGefO+1qS/0pNoMrCjB9av0DvOKoJjbOMkfkk2ef1jmjoXyzlLwvIIgCrwicWXZMiDkk9NelBhSsvfhmNftdF8OU= /uuv | C:\Users\admin\AppData\Local\LIKEDAD\LIKEDADApp.exe | LIKEDADApp.exe | ||||||||||||
User: admin Company: LIKE DAD Integrity Level: HIGH Description: LIKE DAD App Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 964 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Local\LIKEDAD\LIKEDADApp.exe" "C:\Users\admin\AppData\Local\Temp\Vulkan-5.0-X-mas-edition_70726.exe" | C:\Users\admin\AppData\Local\LIKEDAD\LIKEDADApp.exe | — | Vulkan-5.0-X-mas-edition_70726.exe | |||||||||||
User: admin Company: LIKE DAD Integrity Level: MEDIUM Description: LIKE DAD App Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\Desktop\7-Zip\7z.exe" | C:\Users\admin\Desktop\7-Zip\7z.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 21.03 beta Modules
| |||||||||||||||
| 1512 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\7-Zip\7-zip.dll | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
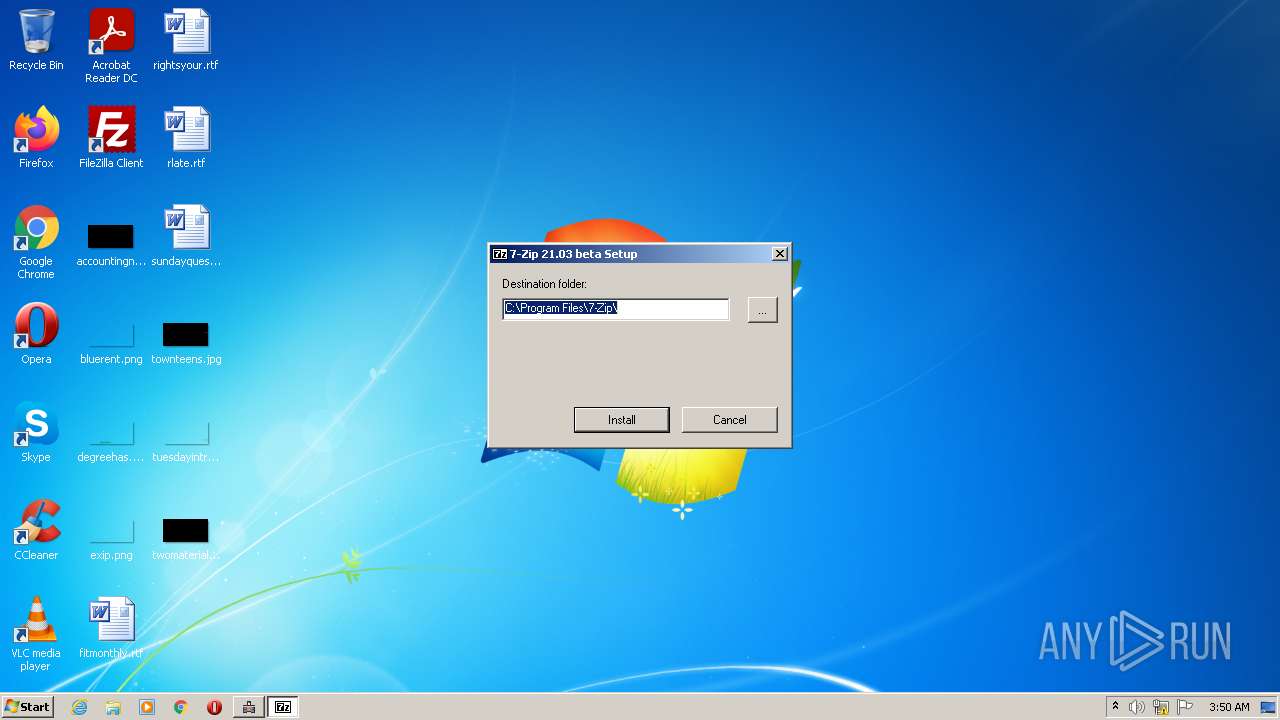
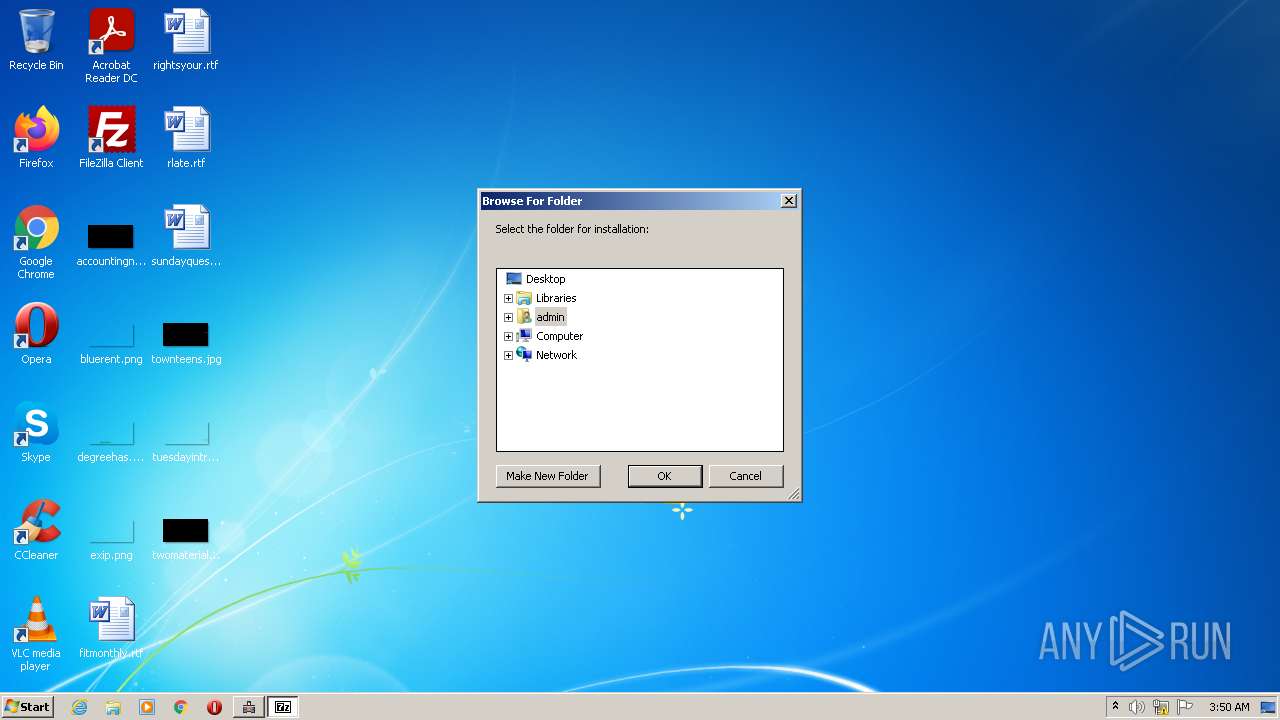
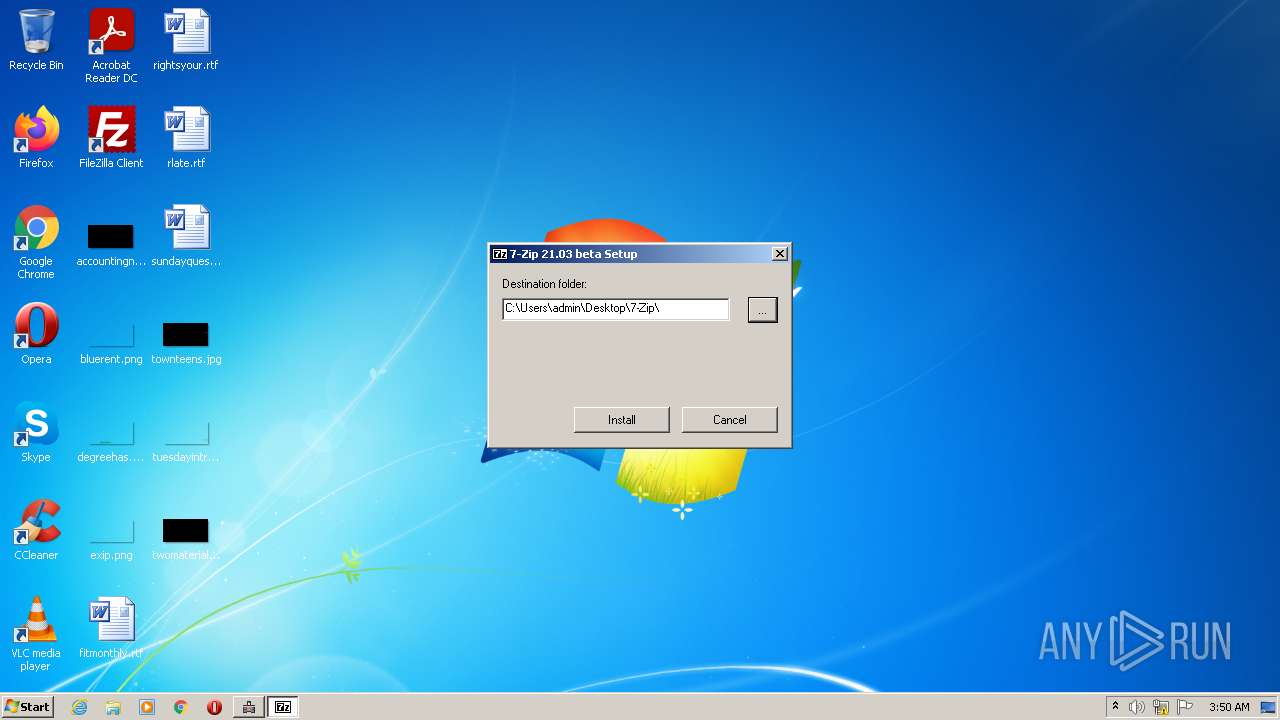
| 1972 | "C:\Program Files\LIKEDADekoApp\LIKEfApp.exe" | C:\Program Files\LIKEDADekoApp\LIKEfApp.exe | LIKEDADApp.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 21.03 beta Modules
| |||||||||||||||
| 2248 | "C:\Users\admin\Desktop\7-Zip\7z.exe" | C:\Users\admin\Desktop\7-Zip\7z.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 21.03 beta Modules
| |||||||||||||||
| 2648 | "C:\Windows\system32\cmd.exe" /d /c timeout 10 & cmd /d /c rd /s /q "C:\Users\admin\AppData\Local\LIKEDAD" | C:\Windows\system32\cmd.exe | — | LIKEDADApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 32 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
8 235
Read events
7 935
Write events
297
Delete events
3
Modification events
| (PID) Process: | (964) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\NccQngn\Ybpny\Grzc\Ihyxna-5.0-K-znf-rqvgvba_70726.rkr |
Value: 00000000000000000000000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (964) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000470100007B020000FF5A17013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01 | |||
| (PID) Process: | (3740) Vulkan-5.0-X-mas-edition_70726.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3740) Vulkan-5.0-X-mas-edition_70726.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3740) Vulkan-5.0-X-mas-edition_70726.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3740) Vulkan-5.0-X-mas-edition_70726.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (964) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\NccQngn\Ybpny\YVXRQNQ\YVXRQNQNcc.rkr |
Value: 00000000000000000100000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (964) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000470100007C020000FF5A17013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E45102000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01000000007200000032AC5D004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000045003700430036004500410037004400320037007D005C0063006D0064002E0065007800650000000000D45D38760000000005000000D80B3902000000000000000000000000000000000000000000000000CB0501AD000000000000000000000000000000000000000000000000000000000000000030E69D01A8323876B8E59D01C0E59D0154E59D0100000000000000000000000000000000480B39020000000005000000D80B390200000000340C390268E59D01B0E59D010000000000000000E8B93902050000002000000000000000000000000400400000001A0098E59D0100000000000000000000000000000000040000009EE69D0110E69D015DA5B3779EE69D01D26EB37779A5B377114526769EE69D0188E89D0104000000C6E69D0138E69D015DA5B377C6E69D01D26EB37779A5B37739452676C6E69D01B0E89D0100010000E8FE1C0012E69D01C6E69D0168E69D015DA5310033003300350033003800310011000000104F1D00084F1D001AE79D018CE69D015DA5B37774E60000B777588D24E69D015E90D47674E69D0128E69D010394D47600000000D422E60250E69D01A993D476D422E602FCE69D01481EE602BD93D47600000000481EE602FCE69D0158E69D01 | |||
| (PID) Process: | (1232) LIKEDADApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1232) LIKEDADApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
11
Suspicious files
0
Text files
97
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3740 | Vulkan-5.0-X-mas-edition_70726.exe | C:\Users\admin\AppData\Local\LIKEDAD\LIKEDADApp.exe | executable | |
MD5:— | SHA256:— | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\7-zip.chm | chm | |
MD5:2968879E0E6AC82FE3EB5E5A09E9BE34 | SHA256:CCCCFD236FAD1FC054829A549AFE1A9C7E0E04D4C0AC7DF38E52DD8546E99ACF | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\Lang\an.txt | text | |
MD5:BF8564B2DAD5D2506887F87AEE169A0A | SHA256:0E8DD119DFA6C6C1B3ACA993715092CDF1560947871092876D309DBC1940A14A | |||
| 548 | LIKEDADApp.exe | C:\Program Files\LIKEDADekoApp\LIKEfApp.exe | executable | |
MD5:7358BF3886A22150B2661340B94D5497 | SHA256:447916156F9F8A4D0BF9371745250EC4A59C6172993E428141BD2F28D68A0FB9 | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\History.txt | text | |
MD5:9EBDE31BD2CD85CD81DCD76977318B8A | SHA256:C588599CAA710A918E330D41A41A5BA876BE7BB5CBCE1A43D7793586410CD6A2 | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\Lang\cs.txt | text | |
MD5:641B90F9AEDFC68486D0D20B40F7ECA6 | SHA256:87A4B9369FD51D76C9032C0E65C3C6221659E086798829072785BE589E55B839 | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\Lang\ba.txt | text | |
MD5:D83B65AC086DA0C94D6EB57BEE669C2B | SHA256:2901B54F7621C95429658CB4EDB28ABD0CB5B6E257C7D9A364FC468A8B86BAAE | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\Lang\ca.txt | text | |
MD5:1657720023A267B5B625DE17BF292299 | SHA256:ED8748DA8FA99DB775FF621D3E801E2830E6C04DA42C0B701095580191A700A6 | |||
| 1972 | LIKEfApp.exe | C:\Users\admin\Desktop\7-Zip\Lang\be.txt | text | |
MD5:3C21135144AC7452E7DB66F0214F9D68 | SHA256:D095879B8BBC67A1C9875C5E9896942BACF730BD76155C06105544408068C59E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
548 | LIKEDADApp.exe | 104.26.4.240:443 | webmanagefile.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
webmanagefile.com |
| unknown |