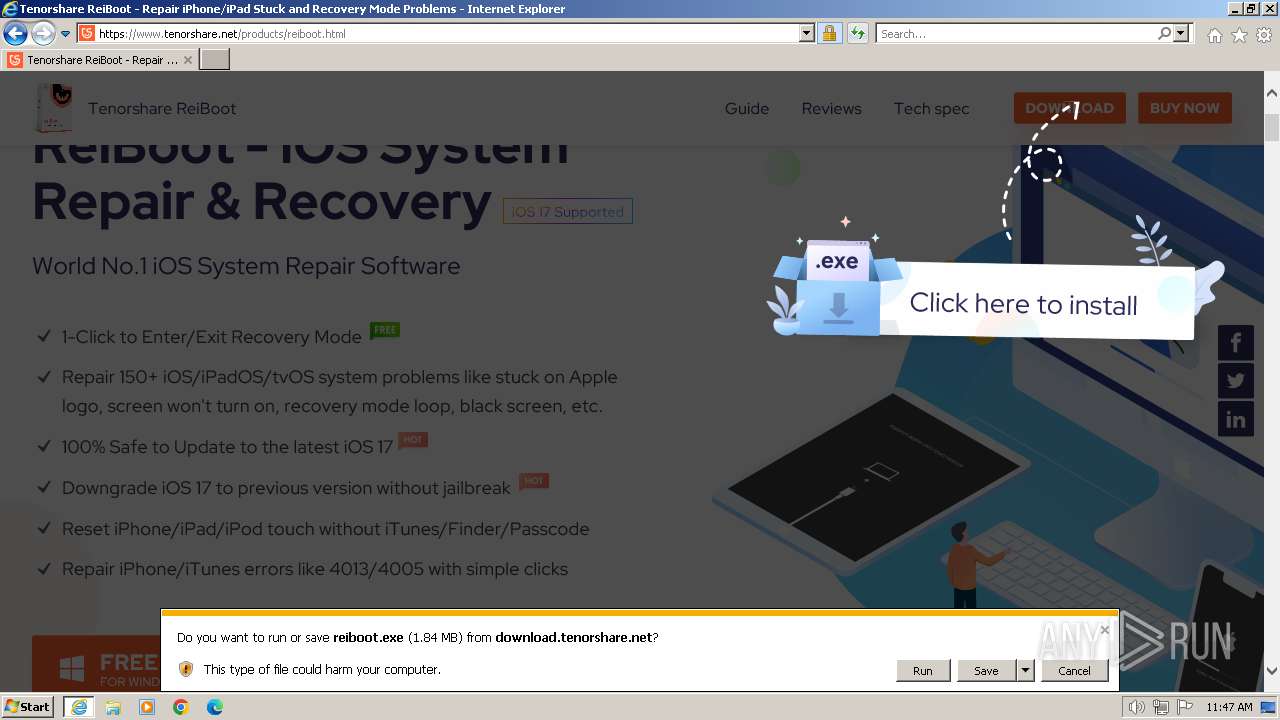
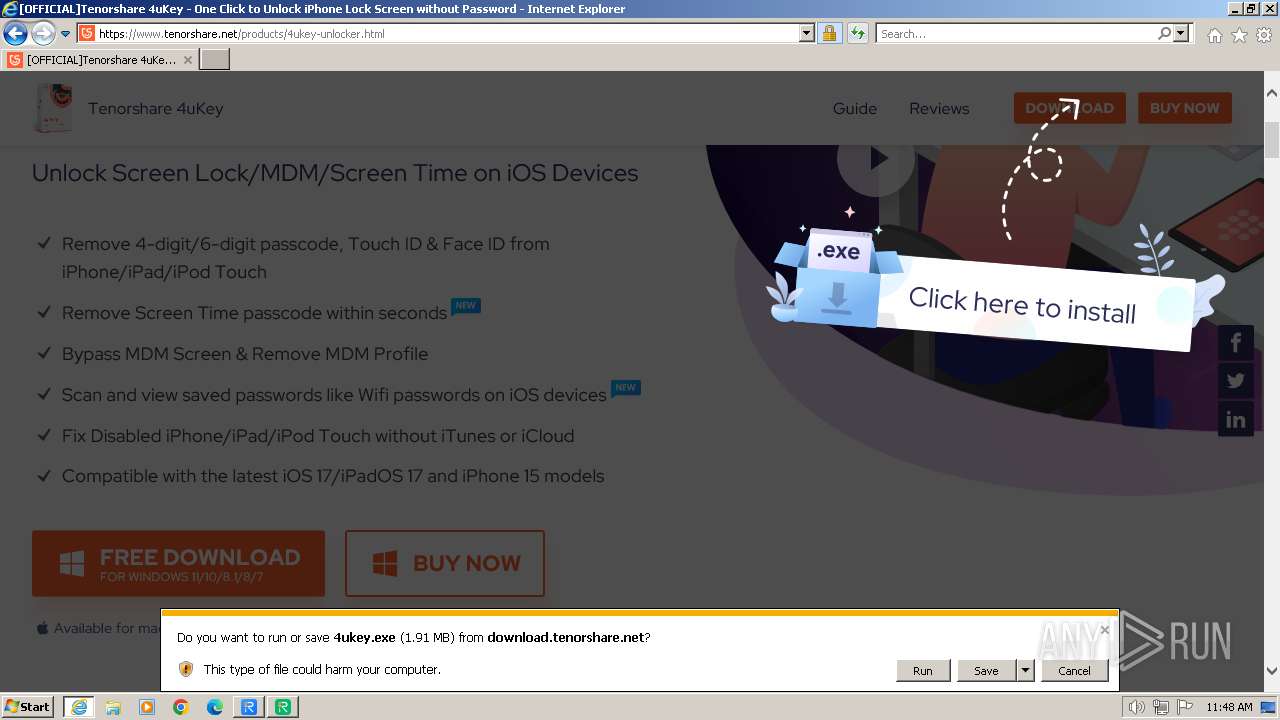
| URL: | https://www.tenorshare.net/ |
| Full analysis: | https://app.any.run/tasks/cd7de954-ae73-47d8-9ab0-b3ff87a7917a |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 11:47:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2B7FBC0F4DAF2D7F9B7AAB93086784FF |
| SHA1: | 65F4A78EF77C045AD8FFA0F2BAC4C386F3F9F31A |
| SHA256: | FC62A9F4F54CF717862C8B3B1C07CEF7797F39CF0C2341AEFD5299AF1E126F72 |
| SSDEEP: | 3:N8DSLbXILLzn:2OLELX |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 2204)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 3196)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
SUSPICIOUS
Reads the Internet Settings
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- NetFrameCheck.exe (PID: 2376)
- ReiBoot.exe (PID: 3220)
- Start.exe (PID: 876)
- ReibootForAndroid.exe (PID: 2112)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- Tenorshare 4uKey.exe (PID: 4056)
- Start.exe (PID: 3492)
- WMIC.exe (PID: 3008)
- WMIC.exe (PID: 2808)
- WMIC.exe (PID: 3272)
- WMIC.exe (PID: 2436)
- WMIC.exe (PID: 268)
- WMIC.exe (PID: 3740)
- WMIC.exe (PID: 3120)
- WMIC.exe (PID: 3056)
- WMIC.exe (PID: 3680)
- WMIC.exe (PID: 844)
- WMIC.exe (PID: 2112)
- WMIC.exe (PID: 3304)
- WMIC.exe (PID: 3136)
- WMIC.exe (PID: 3120)
Reads security settings of Internet Explorer
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- Tenorshare 4uKey.exe (PID: 4056)
Reads settings of System Certificates
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- rundll32.exe (PID: 188)
- rundll32.exe (PID: 3488)
- Tenorshare 4uKey.exe (PID: 4056)
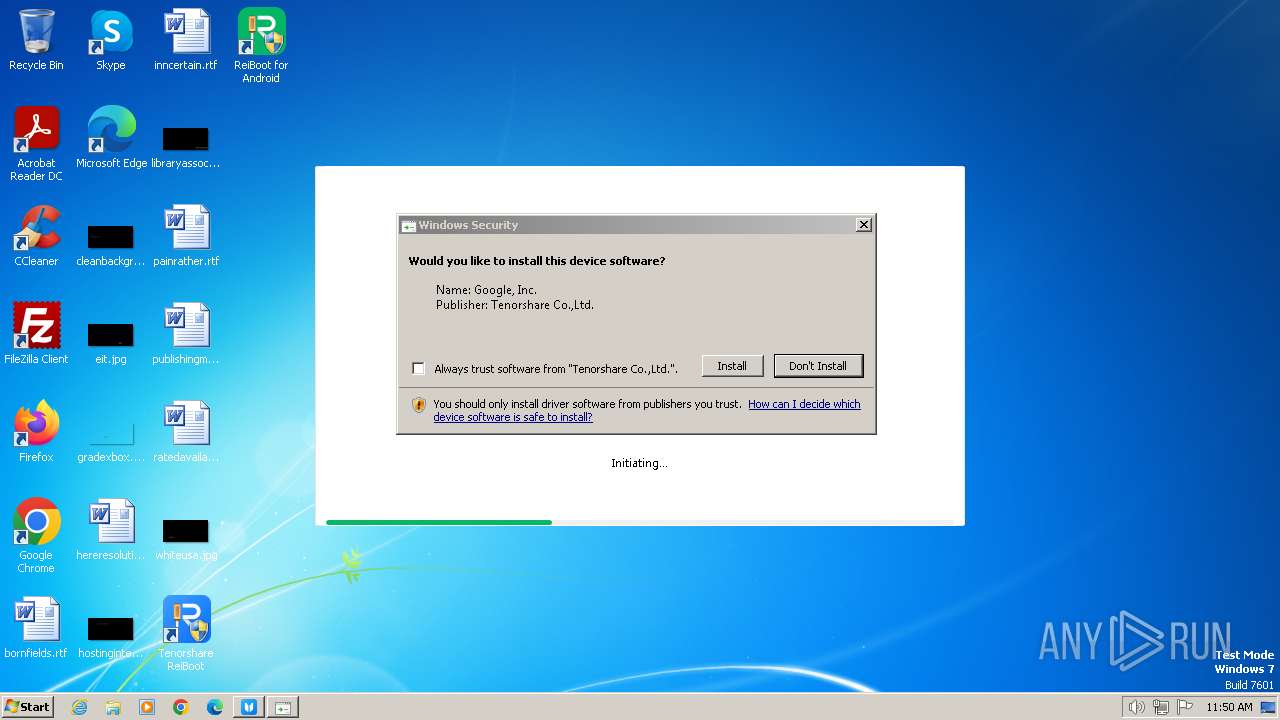
Checks Windows Trust Settings
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- reiboot.exe (PID: 1388)
- ReiBoot.exe (PID: 3220)
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 2204)
- ReibootForAndroid.exe (PID: 2112)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
- drvinst.exe (PID: 3196)
- Tenorshare 4uKey.exe (PID: 4056)
Reads the Windows owner or organization settings
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
Drops a system driver (possible attempt to evade defenses)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- PnPutil.exe (PID: 3316)
- drvinst.exe (PID: 2976)
- PnPutil.exe (PID: 3288)
- drvinst.exe (PID: 1548)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- drvinst.exe (PID: 1316)
- DPInst32.exe (PID: 316)
- drvinst.exe (PID: 1408)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
Uses NETSH.EXE to add a firewall rule or allowed programs
- reibootforios_net_9.3.1.tmp (PID: 3536)
Creates a software uninstall entry
- reiboot.exe (PID: 1388)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- 4ukey.exe (PID: 3332)
- Tenorshare 4uKey.exe (PID: 4056)
Searches for installed software
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- Tenorshare 4uKey.exe (PID: 4056)
Creates files in the driver directory
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 2204)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 3196)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
Starts CMD.EXE for commands execution
- ReibootForAndroid.exe (PID: 2112)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- Tenorshare 4uKey.exe (PID: 4056)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 332)
- cmd.exe (PID: 3972)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 1020)
- cmd.exe (PID: 3876)
Starts SC.EXE for service management
- cmd.exe (PID: 3516)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 1000)
- cmd.exe (PID: 3668)
- cmd.exe (PID: 2056)
- cmd.exe (PID: 3636)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 332)
- cmd.exe (PID: 3824)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- Tenorshare 4uKey.exe (PID: 4056)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 116)
Create files in a temporary directory
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- reibootforios_net_9.3.1.exe (PID: 3540)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- PnPutil.exe (PID: 3316)
- PnPutil.exe (PID: 3288)
- reibootforandroid_net_2.1.19.exe (PID: 2304)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- ReibootForAndroid.exe (PID: 2112)
- DPInst32.exe (PID: 316)
- 4ukeyforios_net_3.4.0.exe (PID: 2572)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- adb.exe (PID: 2340)
- Tenorshare 4uKey.exe (PID: 4056)
Checks proxy server information
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- Tenorshare 4uKey.exe (PID: 4056)
Reads the machine GUID from the registry
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- ReiBoot.exe (PID: 3220)
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 1548)
- ReibootForAndroid.exe (PID: 2112)
- DPInst32.exe (PID: 316)
- drvinst.exe (PID: 2204)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 3196)
- drvinst.exe (PID: 1408)
- drvinst.exe (PID: 1316)
- adb.exe (PID: 2444)
- adb.exe (PID: 2340)
- Tenorshare 4uKey.exe (PID: 4056)
Checks supported languages
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reibootforios_net_9.3.1.exe (PID: 3540)
- NetFrameCheck.exe (PID: 2376)
- ReiBoot.exe (PID: 3220)
- Monitor.exe (PID: 3240)
- CheckErrorx86.exe (PID: 3416)
- AppleMobileDeviceProcess.exe (PID: 3420)
- infInstallx86.exe (PID: 1728)
- mDNSResponder.exe (PID: 2912)
- infInstallx86.exe (PID: 2348)
- infInstallx86.exe (PID: 3504)
- drvinst.exe (PID: 2976)
- infInstallx86.exe (PID: 3008)
- drvinst.exe (PID: 1548)
- reibootforandroid_net_2.1.19.exe (PID: 2304)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- Start.exe (PID: 876)
- ReibootForAndroid.exe (PID: 2112)
- fastboot.exe (PID: 324)
- InstallAndDriver.exe (PID: 2628)
- repair.exe (PID: 3748)
- fastboot.exe (PID: 296)
- DPInst32.exe (PID: 316)
- drvinst.exe (PID: 2204)
- fastboot.exe (PID: 2528)
- fastboot.exe (PID: 3604)
- fastboot.exe (PID: 2068)
- fastboot.exe (PID: 664)
- fastboot.exe (PID: 2568)
- fastboot.exe (PID: 3208)
- fastboot.exe (PID: 668)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- fastboot.exe (PID: 2096)
- drvinst.exe (PID: 1548)
- fastboot.exe (PID: 4076)
- fastboot.exe (PID: 2660)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 3688)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 1792)
- drvinst.exe (PID: 3196)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 2972)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
- fastboot.exe (PID: 3868)
- fastboot.exe (PID: 3100)
- fastboot.exe (PID: 2024)
- adb.exe (PID: 3020)
- adb.exe (PID: 3400)
- adb.exe (PID: 1584)
- adb.exe (PID: 2444)
- fastboot.exe (PID: 3948)
- adb.exe (PID: 2032)
- fastboot.exe (PID: 1172)
- adb.exe (PID: 1236)
- adb.exe (PID: 2656)
- fastboot.exe (PID: 3696)
- 4ukeyforios_net_3.4.0.exe (PID: 2572)
- adb.exe (PID: 2868)
- adb.exe (PID: 2340)
- fastboot.exe (PID: 3972)
- fastboot.exe (PID: 560)
- fastboot.exe (PID: 3908)
- fastboot.exe (PID: 1264)
- fastboot.exe (PID: 4076)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 1832)
- fastboot.exe (PID: 2360)
- fastboot.exe (PID: 2484)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 492)
- fastboot.exe (PID: 664)
- fastboot.exe (PID: 3956)
- fastboot.exe (PID: 2812)
- fastboot.exe (PID: 3512)
- fastboot.exe (PID: 3324)
- fastboot.exe (PID: 3716)
- fastboot.exe (PID: 2952)
- fastboot.exe (PID: 3636)
- fastboot.exe (PID: 1388)
- fastboot.exe (PID: 4068)
- fastboot.exe (PID: 4072)
- fastboot.exe (PID: 2824)
- fastboot.exe (PID: 2000)
- fastboot.exe (PID: 3076)
- fastboot.exe (PID: 992)
- fastboot.exe (PID: 3472)
- fastboot.exe (PID: 3932)
- fastboot.exe (PID: 3108)
- fastboot.exe (PID: 2868)
- fastboot.exe (PID: 2292)
- fastboot.exe (PID: 3960)
- fastboot.exe (PID: 3284)
- fastboot.exe (PID: 3516)
- Tenorshare 4uKey.exe (PID: 4056)
- Start.exe (PID: 3492)
- Monitor.exe (PID: 2472)
- infInstallx86.exe (PID: 2932)
- CheckErrorx86.exe (PID: 3348)
- infInstallx86.exe (PID: 1768)
- infInstallx86.exe (PID: 3492)
- infInstallx86.exe (PID: 2928)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2032)
- iexplore.exe (PID: 116)
- reibootforios_net_9.3.1.exe (PID: 3540)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- PnPutil.exe (PID: 3316)
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 1548)
- PnPutil.exe (PID: 3288)
- reibootforandroid_net_2.1.19.exe (PID: 2304)
- ReibootForAndroid.exe (PID: 2112)
- drvinst.exe (PID: 2204)
- DPInst32.exe (PID: 316)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- 4ukeyforios_net_3.4.0.exe (PID: 2572)
- drvinst.exe (PID: 1548)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- drvinst.exe (PID: 3196)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
Reads the computer name
- reiboot.exe (PID: 1388)
- 4ukey.exe (PID: 3332)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reiboot-for-android.exe (PID: 952)
- NetFrameCheck.exe (PID: 2376)
- ReiBoot.exe (PID: 3220)
- Monitor.exe (PID: 3240)
- CheckErrorx86.exe (PID: 3416)
- AppleMobileDeviceProcess.exe (PID: 3420)
- infInstallx86.exe (PID: 1728)
- mDNSResponder.exe (PID: 2912)
- infInstallx86.exe (PID: 2348)
- drvinst.exe (PID: 2976)
- drvinst.exe (PID: 1548)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- Start.exe (PID: 876)
- ReibootForAndroid.exe (PID: 2112)
- fastboot.exe (PID: 296)
- fastboot.exe (PID: 324)
- DPInst32.exe (PID: 316)
- drvinst.exe (PID: 2204)
- fastboot.exe (PID: 2528)
- fastboot.exe (PID: 668)
- fastboot.exe (PID: 2068)
- fastboot.exe (PID: 664)
- fastboot.exe (PID: 3208)
- fastboot.exe (PID: 2568)
- fastboot.exe (PID: 3604)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- fastboot.exe (PID: 2096)
- drvinst.exe (PID: 1548)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 3688)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 2660)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 2972)
- fastboot.exe (PID: 1792)
- drvinst.exe (PID: 3196)
- drvinst.exe (PID: 1316)
- drvinst.exe (PID: 1408)
- fastboot.exe (PID: 3868)
- fastboot.exe (PID: 3100)
- fastboot.exe (PID: 2024)
- fastboot.exe (PID: 1172)
- fastboot.exe (PID: 3696)
- adb.exe (PID: 2444)
- adb.exe (PID: 2340)
- fastboot.exe (PID: 3948)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 3972)
- fastboot.exe (PID: 1832)
- fastboot.exe (PID: 560)
- fastboot.exe (PID: 1264)
- fastboot.exe (PID: 3908)
- fastboot.exe (PID: 4076)
- fastboot.exe (PID: 492)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 2484)
- fastboot.exe (PID: 3956)
- fastboot.exe (PID: 2812)
- fastboot.exe (PID: 2360)
- fastboot.exe (PID: 3512)
- fastboot.exe (PID: 3716)
- fastboot.exe (PID: 3324)
- fastboot.exe (PID: 4068)
- fastboot.exe (PID: 664)
- fastboot.exe (PID: 3636)
- fastboot.exe (PID: 1388)
- fastboot.exe (PID: 4072)
- fastboot.exe (PID: 2000)
- fastboot.exe (PID: 2824)
- fastboot.exe (PID: 3076)
- fastboot.exe (PID: 2952)
- fastboot.exe (PID: 992)
- fastboot.exe (PID: 3472)
- fastboot.exe (PID: 3516)
- fastboot.exe (PID: 3108)
- fastboot.exe (PID: 2292)
- fastboot.exe (PID: 3932)
- fastboot.exe (PID: 3960)
- fastboot.exe (PID: 3284)
- fastboot.exe (PID: 2868)
- Tenorshare 4uKey.exe (PID: 4056)
- Start.exe (PID: 3492)
- Monitor.exe (PID: 2472)
- CheckErrorx86.exe (PID: 3348)
- infInstallx86.exe (PID: 2932)
- infInstallx86.exe (PID: 2928)
- fastboot.exe (PID: 4076)
Checks for external IP
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
Reads Environment values
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- 4ukey.exe (PID: 3332)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- Tenorshare 4uKey.exe (PID: 4056)
Creates files or folders in the user directory
- reiboot.exe (PID: 1388)
- reiboot-for-android.exe (PID: 952)
- ReiBoot.exe (PID: 3220)
- ReibootForAndroid.exe (PID: 2112)
- Tenorshare 4uKey.exe (PID: 4056)
Application launched itself
- iexplore.exe (PID: 116)
- msedge.exe (PID: 3552)
- msedge.exe (PID: 2768)
- msedge.exe (PID: 3308)
- msedge.exe (PID: 1140)
- adb.exe (PID: 3400)
- adb.exe (PID: 1584)
- msedge.exe (PID: 1404)
- msedge.exe (PID: 1624)
Connects to the CnC server
- reiboot.exe (PID: 1388)
Creates files in the program directory
- reiboot.exe (PID: 1388)
- 4ukey.exe (PID: 3332)
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reiboot-for-android.exe (PID: 952)
- NetFrameCheck.exe (PID: 2376)
- ReiBoot.exe (PID: 3220)
- AppleMobileDeviceProcess.exe (PID: 3420)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- Start.exe (PID: 876)
- ReibootForAndroid.exe (PID: 2112)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- Start.exe (PID: 3492)
- Tenorshare 4uKey.exe (PID: 4056)
The process drops C-runtime libraries
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
Drops 7-zip archiver for unpacking
- reibootforios_net_9.3.1.tmp (PID: 3536)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- ReibootForAndroid.exe (PID: 2112)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
Manual execution by a user
- msedge.exe (PID: 2768)
- msedge.exe (PID: 1140)
- msedge.exe (PID: 1624)
Process drops legitimate windows executable
- reibootforios_net_9.3.1.tmp (PID: 3536)
- PnPutil.exe (PID: 3288)
- drvinst.exe (PID: 1548)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
- DPInst32.exe (PID: 316)
- drvinst.exe (PID: 2204)
- 4ukeyforios_net_3.4.0.tmp (PID: 1560)
- drvinst.exe (PID: 1548)
- drvinst.exe (PID: 3196)
Process drops legitimate windows executable (CertUtil.exe)
- reibootforandroid_net_2.1.19.tmp (PID: 2516)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 188)
- rundll32.exe (PID: 3488)
Executes as Windows Service
- VSSVC.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
468
Monitored processes
291
Malicious processes
23
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.tenorshare.net/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 124 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 148 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1312 --field-trial-handle=1400,i,4204309666122881323,5744907838104427696,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 188 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{75dadf7e-15d2-4fbb-8302-fc7babd6686c} Global\{14c4e430-a6c5-339a-efe8-fe548da2c768} C:\Windows\System32\DriverStore\Temp\{2ee92f9c-d34f-129e-9a55-ef35222d896f}\android_general.inf C:\Windows\System32\DriverStore\Temp\{2ee92f9c-d34f-129e-9a55-ef35222d896f}\android_general.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | wmic BaseBoard get SerialNumber | C:\Windows\System32\wbem\WMIC.exe | — | Tenorshare 4uKey.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | sc start winmgmt | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1056 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Tenorshare\ReiBoot for Android\DPInst32.exe" /F /D /SW /PATH "C:\Program Files\Tenorshare\ReiBoot for Android\mobiledrv" | C:\Program Files\Tenorshare\ReiBoot for Android\DPInst32.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 1280 Version: 2.1 Modules
| |||||||||||||||
| 324 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 324 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
113 817
Read events
112 711
Write events
1 086
Delete events
20
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1 657
Suspicious files
541
Text files
677
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:F6F8B4B0F1271AD09BE8ECD9728BFEF6 | SHA256:32E7864AD091668FFD0DB8CC47535C98DFF77F6BBD24C1F8D2BA676B7E2461E4 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\HSW3ANKI.txt | text | |
MD5:E19E5274700202DACD8ABBAE0F69F544 | SHA256:8A92DD725F979636D93EB2E43E40DB3D4D1B00E3E4BE50147E7301424ADC415A | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\windows-boot-genius-3[1].svg | image | |
MD5:C1B02300A6EB5BC7EC2E9184861CE9E1 | SHA256:4B87C70C160664D62EDF4FCB2226D9171BD39F082A580B81B1150C7986B5E917 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\app[1].css | text | |
MD5:4FA3EEFB912C860C37243E7C474EE49A | SHA256:FA4A647E3257CA77F7E266A7EF0E242D395FEEE6763C89D77A474AAE1FAB675E | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:95F1E1AC9DA7950C15EAC7B35E0C26E6 | SHA256:C3608FC592FFCFAADA330C48024F614D8704A31FD31801F9E43CBFA438FB6DC9 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\icon-repaik-2[1].svg | image | |
MD5:FBB35201F3BDD1CA8364A8EEAAA5738C | SHA256:16A02C9F6A578C825F6F375848325E8C81A7B718C1C05778F6511D46A8133E99 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\rn-ui-tenorshare2-1.0.0.min[2].css | text | |
MD5:54536E3EB94EA6125773ED31AB7A8A99 | SHA256:72369DCF97771D0A76A1C8E34187729FD2AD2E8ED98C26A009D748F17911236B | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\app[1].js | text | |
MD5:E18AFEBF30EDDEB8600240636BCB05BD | SHA256:BE7181738A9AF60EC9582FE1DAD91E287445DF77456E21DACCF7249D091BC75F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
163
TCP/UDP connections
622
DNS requests
231
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2032 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCED%2FWajMRo4tVEJ1N5h9TM0M%3D | unknown | binary | 471 b | unknown |
116 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d8f761b8c0f86c21 | unknown | — | — | unknown |
116 | iexplore.exe | GET | 304 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a6e676fbb64f2cc | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2032 | iexplore.exe | 104.18.10.138:443 | www.tenorshare.net | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2032 | iexplore.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2032 | iexplore.exe | 151.101.65.26:443 | polyfill.io | FASTLY | US | unknown |
2032 | iexplore.exe | 104.18.16.57:443 | assets.afirstsoft.com | CLOUDFLARENET | — | shared |
2032 | iexplore.exe | 104.18.25.249:443 | www.tenorshare.com | CLOUDFLARENET | — | unknown |
2032 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tenorshare.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
polyfill.io |
| whitelisted |
assets.afirstsoft.com |
| unknown |
www.tenorshare.com |
| whitelisted |
images.tenorshare.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.starfieldtech.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1388 | reiboot.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
1388 | reiboot.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1388 | reiboot.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
1388 | reiboot.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1388 | reiboot.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Tensorshare Google Analytics Checkin |
952 | reiboot-for-android.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
952 | reiboot-for-android.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3332 | 4ukey.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3332 | 4ukey.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3220 | ReiBoot.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
9 ETPRO signatures available at the full report
Process | Message |
|---|---|
ReiBoot.exe | log4net:ERROR Appender named [ConsoleAppender] not found.
|
ReiBoot.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ConsoleAppender] could be found.
|
AppleMobileDeviceProcess.exe | ASL checking for logging parameters in environment variable "asl.log"
|
AppleMobileDeviceProcess.exe | ASL checking for logging parameters in environment variable "AppleMobileDeviceProcess.exe.log"
|
ReiBoot.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Tenorshare\Tenorshare ReiBoot\x86\SQLite.Interop.dll"...
|
ReiBoot.exe | Couldn't load our private device map. Device identification will be limited. |
ReiBoot.exe | DeviceMap argument is empty. Skipping appending of deprecated devices. |
ReiBoot.exe | |
ReiBoot.exe | |
ReiBoot.exe | ASL checking for logging parameters in environment variable "ReiBoot.exe.log"
|