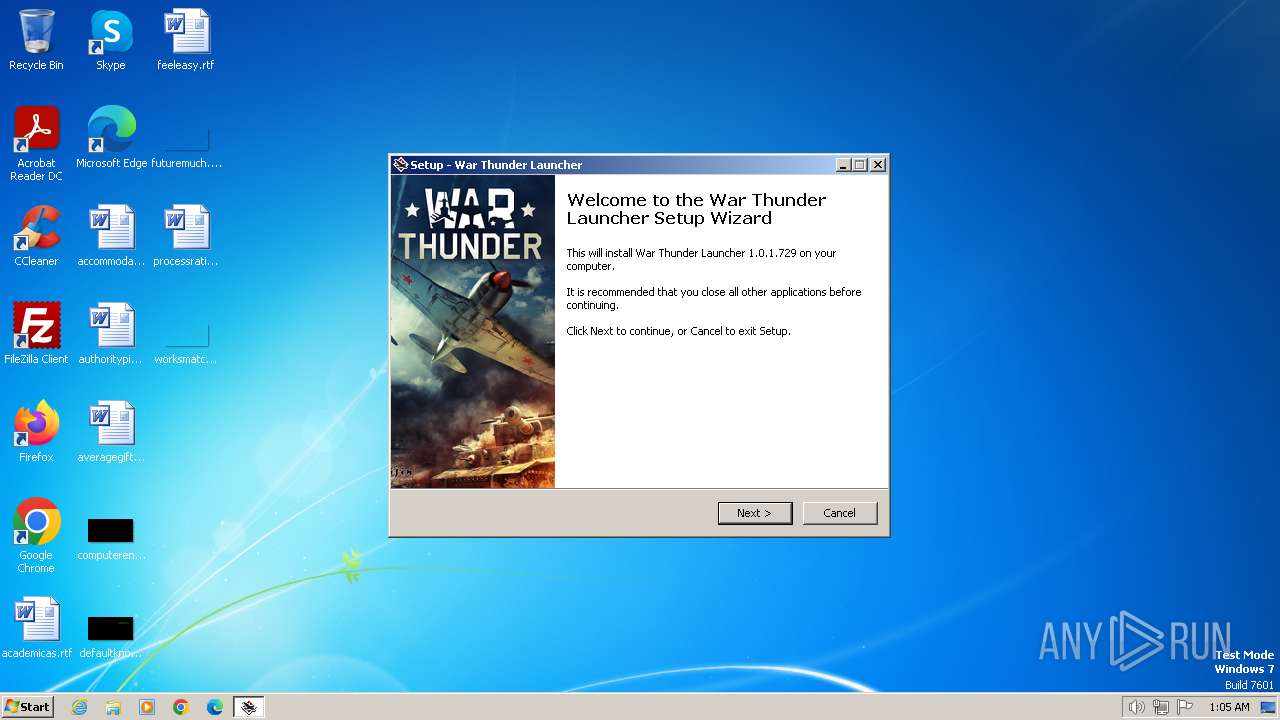
| File name: | wt_launcher_1.0.1.729.exe |
| Full analysis: | https://app.any.run/tasks/fce28093-620a-484b-90b5-7054dcf84faa |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2024, 00:05:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5AC7EFFDD6A264993E20360A2EB35005 |
| SHA1: | A372FD1EA28490E6837FD2A4FE238A044BCEA6A1 |
| SHA256: | FC51D6DE9C769F2A68720D6442A6E683A504E7DD44A3342EE61E8593E2342D42 |
| SSDEEP: | 98304:noeSD406+4pPu2N0bYVnNCGplWLAGsaFtoafSYZs8COUaeB16fxS5GiCKOjCF1E+:PO0wty/yoaJrXAiik/J6 |
MALICIOUS
Drops the executable file immediately after the start
- wt_launcher_1.0.1.729.exe (PID: 4008)
- wt_launcher_1.0.1.729.exe (PID: 3488)
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- launcher.exe (PID: 3216)
- run.exe (PID: 3736)
- launcher.exe (PID: 3988)
Changes the autorun value in the registry
- launcher.exe (PID: 3216)
- launcher.exe (PID: 1624)
SUSPICIOUS
Executable content was dropped or overwritten
- wt_launcher_1.0.1.729.exe (PID: 4008)
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- wt_launcher_1.0.1.729.exe (PID: 3488)
- launcher.exe (PID: 3216)
- run.exe (PID: 3736)
- launcher.exe (PID: 3988)
Process drops legitimate windows executable
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Uses NETSH.EXE to add a firewall rule or allowed programs
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Reads the Windows owner or organization settings
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Uses ICACLS.EXE to modify access control lists
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Reads the Internet Settings
- launcher.exe (PID: 3216)
- launcher.exe (PID: 1624)
- launcher.exe (PID: 3988)
Checks Windows Trust Settings
- launcher.exe (PID: 3216)
- launcher.exe (PID: 3988)
Uses TASKKILL.EXE to kill process
- launcher.exe (PID: 3216)
- launcher.exe (PID: 1624)
Reads security settings of Internet Explorer
- launcher.exe (PID: 3216)
- launcher.exe (PID: 1624)
- launcher.exe (PID: 3988)
Non-standard symbols in registry
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Application launched itself
- launcher.exe (PID: 3216)
Starts CMD.EXE for commands execution
- launcher.exe (PID: 1624)
- launcher.exe (PID: 3216)
Creates file in the systems drive root
- launcher.exe (PID: 3988)
- gaijin_downloader.exe (PID: 1604)
Reads settings of System Certificates
- launcher.exe (PID: 3988)
- launcher.exe (PID: 3216)
Connects to unusual port
- launcher.exe (PID: 3988)
INFO
Create files in a temporary directory
- wt_launcher_1.0.1.729.exe (PID: 4008)
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- wt_launcher_1.0.1.729.exe (PID: 3488)
Checks supported languages
- wt_launcher_1.0.1.729.exe (PID: 4008)
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- wt_launcher_1.0.1.729.tmp (PID: 1836)
- wt_launcher_1.0.1.729.exe (PID: 3488)
- launcher.exe (PID: 3216)
- run.exe (PID: 3736)
- gjagent.exe (PID: 2244)
- gjagent.exe (PID: 2888)
- gjagent.exe (PID: 2576)
- gjagent.exe (PID: 3540)
- launcher.exe (PID: 1624)
- gjagent.exe (PID: 3444)
- run.exe (PID: 3224)
- launcher.exe (PID: 3988)
- gaijin_downloader.exe (PID: 1604)
- gjagent.exe (PID: 1072)
Reads the computer name
- wt_launcher_1.0.1.729.tmp (PID: 1836)
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- run.exe (PID: 3736)
- gjagent.exe (PID: 2888)
- gjagent.exe (PID: 3540)
- gjagent.exe (PID: 2244)
- gjagent.exe (PID: 2576)
- launcher.exe (PID: 1624)
- run.exe (PID: 3224)
- gjagent.exe (PID: 3444)
- launcher.exe (PID: 3988)
- gaijin_downloader.exe (PID: 1604)
- launcher.exe (PID: 3216)
Creates files or folders in the user directory
- wt_launcher_1.0.1.729.tmp (PID: 3180)
- launcher.exe (PID: 3216)
- gjagent.exe (PID: 2888)
- gjagent.exe (PID: 2244)
- gjagent.exe (PID: 3540)
- gjagent.exe (PID: 2576)
- gjagent.exe (PID: 3444)
- launcher.exe (PID: 3988)
- gjagent.exe (PID: 1072)
Creates a software uninstall entry
- wt_launcher_1.0.1.729.tmp (PID: 3180)
Creates files in the program directory
- launcher.exe (PID: 3216)
- launcher.exe (PID: 1624)
Reads the machine GUID from the registry
- run.exe (PID: 3736)
- gjagent.exe (PID: 2244)
- gjagent.exe (PID: 2888)
- gjagent.exe (PID: 2576)
- gjagent.exe (PID: 3540)
- launcher.exe (PID: 1624)
- run.exe (PID: 3224)
- gjagent.exe (PID: 3444)
- launcher.exe (PID: 3988)
- gaijin_downloader.exe (PID: 1604)
- gjagent.exe (PID: 1072)
- launcher.exe (PID: 3216)
Reads the software policy settings
- launcher.exe (PID: 3216)
- launcher.exe (PID: 3988)
Process checks computer location settings
- launcher.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:01:30 14:21:56+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 65024 |
| InitializedDataSize: | 197120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x113bc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Gaijin Entertainment |
| FileDescription: | War Thunder Launcher Setup |
| FileVersion: | |
| LegalCopyright: | Copyright © 2011-2016 Gaijin Entertainment |
| ProductName: | War Thunder Launcher |
| ProductVersion: |
Total processes
134
Monitored processes
55
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\System32\taskkill.exe" /IM bpreport.exe | C:\Windows\System32\taskkill.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | "C:\Windows\System32\taskkill.exe" /F /IM aces.exe | C:\Windows\System32\taskkill.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Windows\system32\netsh" firewall add portopening protocol = TCP port = 33333 name = "War Thunder" | C:\Windows\System32\netsh.exe | — | wt_launcher_1.0.1.729.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\taskkill.exe" /IM aces.exe | C:\Windows\System32\taskkill.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Windows\system32\netsh.exe" firewall add allowedprogram "C:\WarThunder\win64\AFR-FriendlyD3D.exe" "War Thunder Game Client for CrossFire\SLI" ENABLE ALL | C:\Windows\System32\netsh.exe | — | wt_launcher_1.0.1.729.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | "C:\Windows\system32\netsh" firewall add portopening protocol = TCP port = 80 name = "War Thunder" | C:\Windows\System32\netsh.exe | — | wt_launcher_1.0.1.729.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 984 | "C:\Windows\system32\netsh.exe" firewall add allowedprogram "C:\WarThunder\win64\ForceSingleGPU.exe" "War Thunder Game Client for disabled CrossFire\SLI" ENABLE ALL | C:\Windows\System32\netsh.exe | — | wt_launcher_1.0.1.729.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Gaijin\Program Files (x86)\NetAgent\gjagent.exe" | C:\Users\admin\AppData\Local\Gaijin\Program Files (x86)\NetAgent\gjagent.exe | — | launcher.exe | |||||||||||
User: admin Company: Gaijin Integrity Level: MEDIUM Description: Gaijin.Net Updater Exit code: 1 Version: 1.0.51 Modules
| |||||||||||||||
| 1124 | "C:\Windows\System32\taskkill.exe" /F /IM aces64.exe | C:\Windows\System32\taskkill.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Windows\System32\cmd.exe" /c md content | C:\Windows\System32\cmd.exe | — | launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
39 375
Read events
38 152
Write events
1 212
Delete events
11
Modification events
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 6C0C0000566C3347368DDA01 | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: C3B54743DA19B3F89460254838E70BF5AA9400878EA464EE00112CC2D5CE025B | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\WarThunder\launcher.exe | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 9C743356A478EF0AFBB85385729C7576FDD8770E3911DB0AE4631CDB608D9AC0 | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Gaijin\WarThunder |
| Operation: | write | Name: | StartupWithWindows |
Value: Yes | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Gaijin\WarThunder |
| Operation: | write | Name: | Version |
Value: 1.0.0.0 | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Gaijin\WarThunder |
| Operation: | write | Name: | InstallDir |
Value: C:\WarThunder | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Gaijin\WarThunder |
| Operation: | write | Name: | InstallPath |
Value: C:\WarThunder | |||
| (PID) Process: | (3180) wt_launcher_1.0.1.729.tmp | Key: | HKEY_CURRENT_USER\Software\Gaijin\WarThunder |
| Operation: | write | Name: | Dir |
Value: C:\WarThunder | |||
Executable files
36
Suspicious files
93
Text files
29
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4008 | wt_launcher_1.0.1.729.exe | C:\Users\admin\AppData\Local\Temp\is-HV3DH.tmp\wt_launcher_1.0.1.729.tmp | executable | |
MD5:— | SHA256:— | |||
| 3488 | wt_launcher_1.0.1.729.exe | C:\Users\admin\AppData\Local\Temp\is-1SJB8.tmp\wt_launcher_1.0.1.729.tmp | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\Users\admin\AppData\Local\Temp\is-7R3N0.tmp\_isetup\_shfoldr.dll | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\is-EU5Q8.tmp | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\is-0N9FO.tmp | image | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\icon.ico | image | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\is-JJ1LE.tmp | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\launcher.exe | executable | |
MD5:— | SHA256:— | |||
| 3180 | wt_launcher_1.0.1.729.tmp | C:\WarThunder\is-NMVL3.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
1 768
DNS requests
21
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3736 | run.exe | POST | 200 | 52.214.193.195:80 | http://yupmaster.gaijinent.com/launcher/version.php | unknown | — | — | unknown |
3736 | run.exe | POST | 302 | 52.214.193.195:80 | http://yupmaster.gaijinent.com/launcher/update.php | unknown | — | — | unknown |
3216 | launcher.exe | GET | 301 | 104.20.82.98:80 | http://warthunder.com/news3-en.html | unknown | — | — | unknown |
1624 | launcher.exe | GET | 301 | 104.20.82.98:80 | http://warthunder.com/news3-en.html | unknown | — | — | unknown |
3216 | launcher.exe | POST | 200 | 52.214.193.195:80 | http://yupmaster.gaijinent.com/yuitem/get_yup.php | unknown | — | — | unknown |
1624 | launcher.exe | POST | 200 | 52.214.193.195:80 | http://yupmaster.gaijinent.com/yuitem/get_yup.php | unknown | — | — | unknown |
3988 | launcher.exe | GET | 206 | 185.40.154.13:80 | http://04-warthunder-cdnnow.cdn.gaijin.net/warthunder/2.35.1.47/750d7830aa75593c38c8bb1b584e30ac170da235/compiledShaders/game.compatibilitySpirV.ps50.shdump.bin | unknown | — | — | unknown |
1624 | launcher.exe | POST | 200 | 52.214.193.195:80 | http://yupmaster.gaijinent.com/launcher/cdn_conf.php | unknown | — | — | unknown |
3988 | launcher.exe | GET | — | 185.40.154.13:80 | http://04-warthunder-cdnnow.cdn.gaijin.net/warthunder/2.35.1.47/750d7830aa75593c38c8bb1b584e30ac170da235/aces.vromfs.bin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20101 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20100 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20105 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20103 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20102 | — | — | — | unknown |
3216 | launcher.exe | 173.193.77.103:20104 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client-stats.warthunder.com |
| unknown |
yupmaster.gaijinent.com |
| unknown |
aws-yup-distr-02.gaijinent.com |
| unknown |
seeder.gaijin.lan |
| unknown |
warthunder.com |
| whitelisted |
aws-yup-distr-01.gaijinent.com |
| unknown |
aws-yup-distr-03.gaijinent.com |
| unknown |
router.bittorrent.com |
| shared |
client-stats.gaijin.net |
| unknown |
dht.libtorrent.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3988 | launcher.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
3988 | launcher.exe | Misc Attack | ET CINS Active Threat Intelligence Poor Reputation IP group 8 |
3988 | launcher.exe | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent peer sync |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT announce_peers request |
12 ETPRO signatures available at the full report
Process | Message |
|---|---|
launcher.exe | BUILD TIMESTAMP: Dec 12 2016 13:58:41
|
launcher.exe | TIMER freq: ticks/usec=3 ticks/msec=3579
|
launcher.exe | statsd::connect: statsd server: client-stats.warthunder.com:20010 |
launcher.exe | Thread "Watchdog thread" started (auto delete is 1) |
launcher.exe | Creating thread "Watchdog thread"... |
launcher.exe | No config.blk found
|
launcher.exe | |
launcher.exe | Current language is English
|
launcher.exe | Unable to load BLK from files "C:\WarThunder\config.blk", "C:\WarThunder\config.blk.blk", "C:\WarThunder\config.blk.bin", "C:\WarThunder\config.blk.blk.bin"
|
launcher.exe | |