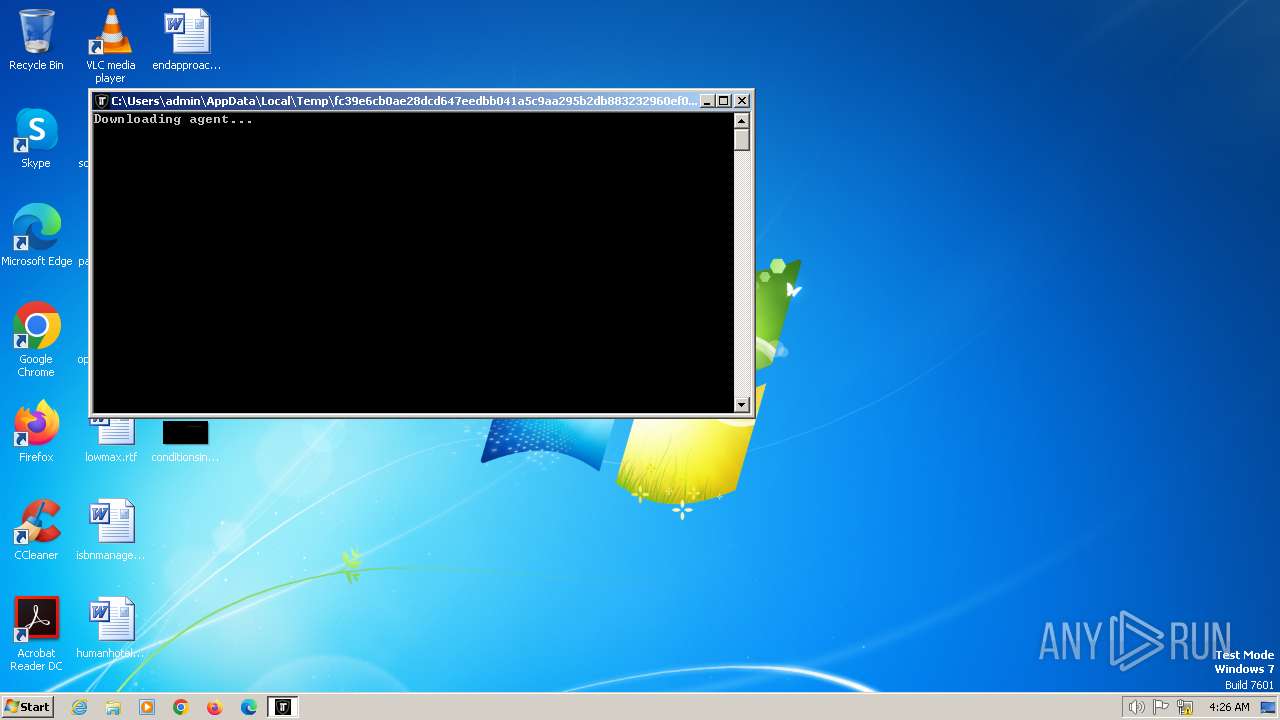
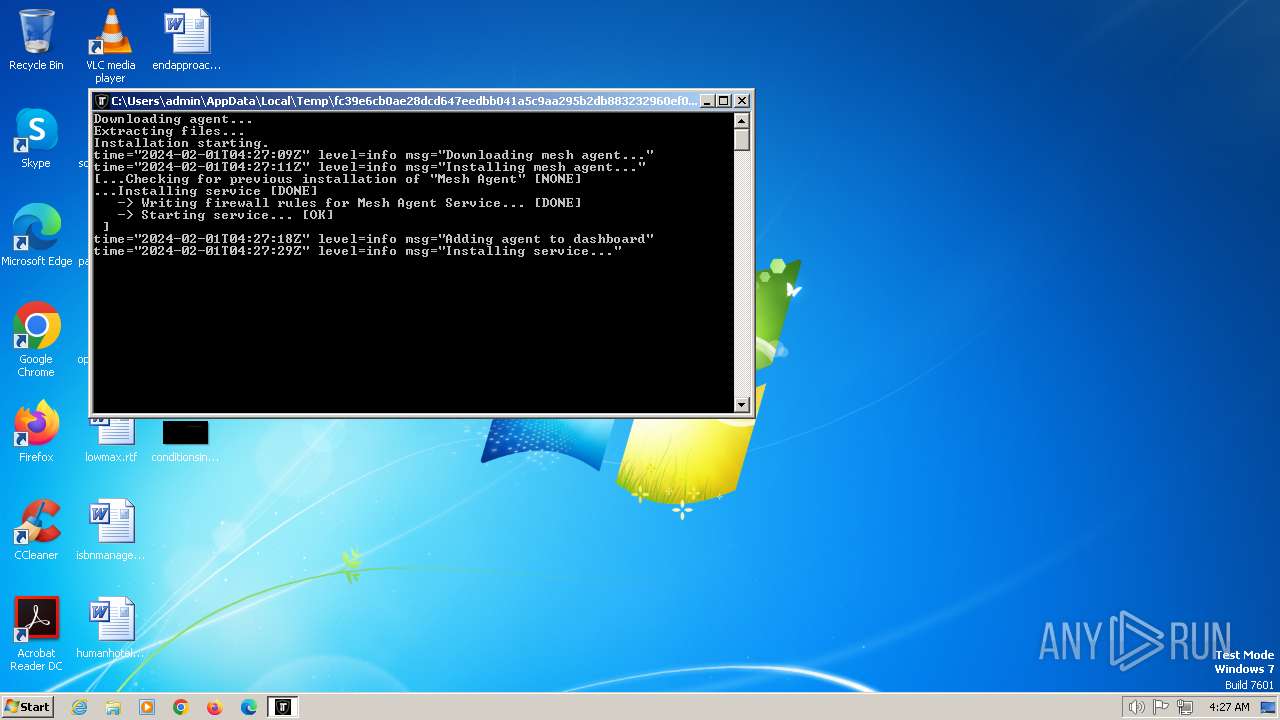
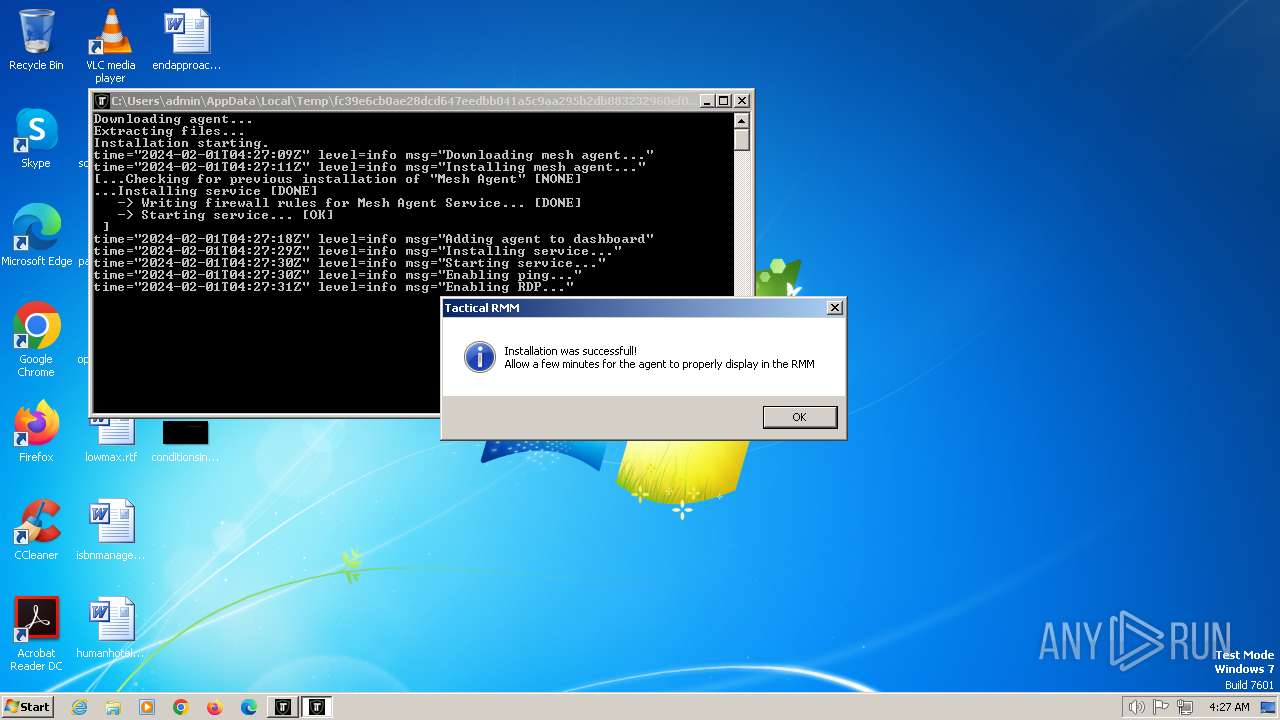
| File name: | fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe |
| Full analysis: | https://app.any.run/tasks/20ced0de-2a62-4991-b2be-3c5b527e198b |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2024, 04:26:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | B8B966DB021D7B8AAEE6965B3DBA4A28 |
| SHA1: | 189ED55B5E1BEF3F1F2FDE5C092F70DC6779A3F6 |
| SHA256: | FC39E6CB0AE28DCD647EEDBB041A5C9AA295B2DB883232960EF0A48D86E93856 |
| SSDEEP: | 98304:qUFz9qgAoj3+uaOhkwMteU4ZSCPy1RYQau6qLm:WE |
MALICIOUS
Drops the executable file immediately after the start
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalagent-v2.6.1-windows-amd64.exe (PID: 2812)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 3000)
- meshagent.exe (PID: 1932)
- powershell.exe (PID: 2692)
- csc.exe (PID: 2952)
- tacticalrmm.exe (PID: 1088)
Starts NET.EXE for service management
- cmd.exe (PID: 2260)
- net.exe (PID: 2156)
- net.exe (PID: 1004)
- net.exe (PID: 2416)
- net.exe (PID: 884)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2192)
- cmd.exe (PID: 2172)
Creates a writable file in the system directory
- powershell.exe (PID: 2664)
- MeshAgent.exe (PID: 756)
- powershell.exe (PID: 2692)
Bypass execution policy to execute commands
- powershell.exe (PID: 2692)
Changes powershell execution policy (Bypass)
- tacticalrmm.exe (PID: 1088)
SUSPICIOUS
Reads settings of System Certificates
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalrmm.exe (PID: 3000)
Executable content was dropped or overwritten
- tacticalagent-v2.6.1-windows-amd64.exe (PID: 2812)
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 3000)
- meshagent.exe (PID: 1932)
- tacticalrmm.exe (PID: 1088)
- powershell.exe (PID: 2692)
- csc.exe (PID: 2952)
Starts CMD.EXE for commands execution
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 3000)
Reads the Windows owner or organization settings
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2260)
- cmd.exe (PID: 2172)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2480)
Adds/modifies Windows certificates
- tacticalrmm.exe (PID: 3000)
Creates or modifies Windows services
- meshagent.exe (PID: 1932)
- tacticalrmm.exe (PID: 3000)
- tacticalrmm.exe (PID: 1088)
- tacticalrmm.exe (PID: 1400)
Reads the Internet Settings
- tacticalrmm.exe (PID: 3000)
Starts POWERSHELL.EXE for commands execution
- MeshAgent.exe (PID: 756)
- tacticalrmm.exe (PID: 1088)
Uses WMIC.EXE to obtain system information
- MeshAgent.exe (PID: 756)
Uses WMIC.EXE to obtain operating system information
- MeshAgent.exe (PID: 756)
Uses WMIC.EXE to obtain computer system information
- MeshAgent.exe (PID: 756)
The process hides Powershell's copyright startup banner
- MeshAgent.exe (PID: 756)
The process bypasses the loading of PowerShell profile settings
- MeshAgent.exe (PID: 756)
- tacticalrmm.exe (PID: 1088)
Searches for installed software
- tacticalrmm.exe (PID: 3000)
- tacticalrmm.exe (PID: 1088)
Executes as Windows Service
- tacticalrmm.exe (PID: 1088)
- MeshAgent.exe (PID: 756)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2256)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2124)
Process drops legitimate windows executable
- tacticalrmm.exe (PID: 1088)
The process hide an interactive prompt from the user
- tacticalrmm.exe (PID: 1088)
The Powershell connects to the Internet
- powershell.exe (PID: 2692)
The process executes Powershell scripts
- tacticalrmm.exe (PID: 1088)
Application launched itself
- tacticalrmm.exe (PID: 1088)
Unusual connection from system programs
- powershell.exe (PID: 2692)
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 2692)
The process drops C-runtime libraries
- tacticalrmm.exe (PID: 1088)
INFO
Checks supported languages
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalagent-v2.6.1-windows-amd64.exe (PID: 2812)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 2268)
- tacticalrmm.exe (PID: 3000)
- meshagent.exe (PID: 1932)
- MeshAgent.exe (PID: 2416)
- tacticalrmm.exe (PID: 1088)
- MeshAgent.exe (PID: 756)
- MeshAgent.exe (PID: 2332)
- tacticalrmm.exe (PID: 1400)
- csc.exe (PID: 2952)
- cvtres.exe (PID: 892)
- choco.exe (PID: 2540)
Reads the computer name
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 2268)
- meshagent.exe (PID: 1932)
- tacticalrmm.exe (PID: 3000)
- MeshAgent.exe (PID: 756)
- MeshAgent.exe (PID: 2416)
- tacticalrmm.exe (PID: 1088)
- MeshAgent.exe (PID: 2332)
- tacticalrmm.exe (PID: 1400)
- choco.exe (PID: 2540)
Reads the machine GUID from the registry
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalrmm.exe (PID: 2268)
- meshagent.exe (PID: 1932)
- tacticalrmm.exe (PID: 3000)
- MeshAgent.exe (PID: 756)
- tacticalrmm.exe (PID: 1088)
- tacticalrmm.exe (PID: 1400)
- csc.exe (PID: 2952)
- cvtres.exe (PID: 892)
- choco.exe (PID: 2540)
Creates files in the program directory
- fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe (PID: 896)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 2268)
- tacticalrmm.exe (PID: 3000)
- meshagent.exe (PID: 1932)
- MeshAgent.exe (PID: 756)
- tacticalrmm.exe (PID: 1088)
- powershell.exe (PID: 2692)
- choco.exe (PID: 2540)
Create files in a temporary directory
- tacticalagent-v2.6.1-windows-amd64.exe (PID: 2812)
- tacticalagent-v2.6.1-windows-amd64.tmp (PID: 2692)
- tacticalrmm.exe (PID: 3000)
Reads product name
- tacticalrmm.exe (PID: 2268)
- tacticalrmm.exe (PID: 3000)
- tacticalrmm.exe (PID: 1088)
- tacticalrmm.exe (PID: 1400)
Reads Environment values
- tacticalrmm.exe (PID: 2268)
- tacticalrmm.exe (PID: 3000)
- tacticalrmm.exe (PID: 1088)
- tacticalrmm.exe (PID: 1400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2520576 |
| InitializedDataSize: | 246784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x66fe0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.0.4.0 |
| ProductVersionNumber: | 2.0.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | AmidaWare LLC |
| FileDescription: | Tactical RMM Installer |
| FileVersion: | v2.0.4.0 |
| InternalName: | rmm.exe |
| LegalCopyright: | Copyright (c) 2022 AmidaWare LLC |
| OriginalFileName: | installer.go |
| ProductName: | Tactical RMM Installer |
| ProductVersion: | v2.0.4.0 |
Total processes
105
Monitored processes
50
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | ping 127.0.0.1 -n 2 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | "C:\Program Files\Mesh Agent\MeshAgent.exe" --installedByUser="S-1-5-21-3896776584-4254864009-862391680-1000" | C:\Program Files\Mesh Agent\MeshAgent.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: MeshCentral Background Service Agent Exit code: 0 Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 856 | wmic SystemEnclosure get ChassisTypes | C:\Windows\System32\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 884 | net start tacticalrmm | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | wmic ComputerSystem get PCSystemType /FORMAT:"C:\Windows\system32\wbem\en-US\csv" | C:\Windows\System32\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Windows\TEMP\RES8972.tmp" "c:\Windows\Temp\t3zlfl45\CSCC2B8AB70BF1642DF8FD54E931FFDDB7B.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 896 | "C:\Users\admin\AppData\Local\Temp\fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe" | C:\Users\admin\AppData\Local\Temp\fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe | explorer.exe | ||||||||||||
User: admin Company: AmidaWare LLC Integrity Level: HIGH Description: Tactical RMM Installer Exit code: 0 Version: v2.0.4.0 Modules
| |||||||||||||||
| 1004 | net stop tacticalagent | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1088 | "C:\Program Files\TacticalAgent\tacticalrmm.exe" -m svc | C:\Program Files\TacticalAgent\tacticalrmm.exe | services.exe | ||||||||||||
User: SYSTEM Company: AmidaWare Inc Integrity Level: SYSTEM Description: Tactical RMM Agent Exit code: 0 Version: v2.6.1.0 Modules
| |||||||||||||||
| 1104 | "cmd.exe" /c sc delete tacticalrpc | C:\Windows\SysWOW64\cmd.exe | — | tacticalagent-v2.6.1-windows-amd64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
22 402
Read events
20 510
Write events
1 892
Delete events
0
Modification events
| (PID) Process: | (896) fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2268) tacticalrmm.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\partmgr |
| Operation: | write | Name: | EnableCounterForIoctl |
Value: 1 | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA6030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E81D000000010000001000000073B6876195F5D18E048510422AEF04E314000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E090000000100000016000000301406082B0601050507030206082B060105050703010B000000010000001A0000004900530052004700200052006F006F007400200058003100000062000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000000CD2F9E0DA1773E9ED864DA5E370E74E0F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6362000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F0074002000580031000000090000000100000016000000301406082B0601050507030206082B0601050507030114000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E3030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E81900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA620000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\DAC9024F54D8F6DF94935FB1732638CA6AD77C13 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000006CF252FEC3E8F20996DE5D4DD9AEF424030000000100000014000000DAC9024F54D8F6DF94935FB1732638CA6AD77C1368000000010000000800000000409120D035D9017E000000010000000800000000C001B39667D6017F000000010000000E000000300C060A2B0601040182370A03041D00000001000000100000004558D512EECB27464920897DE7B66053140000000100000014000000C4A7B1A47B2C71FADBE14B9075FFC415608589100B000000010000001E000000440053005400200052006F006F00740020004300410020005800330000006200000001000000200000000687260331A72403D909F105E69BCF0D32E1BD2493FFC6D9206D11BCD6770739090000000100000042000000304006082B06010505070302060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030106082B060105050703080F00000001000000140000005BCAA1C2780F0BCB5A90770451D96F38963F012D20000000010000004E0300003082034A30820232A003020102021044AFB080D6A327BA893039862EF8406B300D06092A864886F70D0101050500303F31243022060355040A131B4469676974616C205369676E617475726520547275737420436F2E311730150603550403130E44535420526F6F74204341205833301E170D3030303933303231313231395A170D3231303933303134303131355A303F31243022060355040A131B4469676974616C205369676E617475726520547275737420436F2E311730150603550403130E44535420526F6F7420434120583330820122300D06092A864886F70D01010105000382010F003082010A0282010100DFAFE99750088357B4CC6265F69082ECC7D32C6B30CA5BECD9C37DC740C118148BE0E83376492AE33F214993AC4E0EAF3E48CB65EEFCD3210F65D22AD9328F8CE5F777B0127BB595C089A3A9BAED732E7A0C063283A27E8A1430CD11A0E12A38B9790A31FD50BD8065DFB7516383C8E28861EA4B6181EC526BB9A2E24B1A289F48A39E0CDA098E3E172E1EDD20DF5BC62A8AAB2EBD70ADC50B1A25907472C57B6AAB34D63089FFE568137B540BC8D6AEEC5A9C921E3D64B38CC6DFBFC94170EC1672D526EC38553943D0FCFD185C40F197EBD59A9B8D1DBADA25B9C6D8DFC115023AABDA6EF13E2EF55C089C3CD68369E4109B192AB62957E3E53D9B9FF0025D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E04160414C4A7B1A47B2C71FADBE14B9075FFC41560858910300D06092A864886F70D01010505000382010100A31A2C9B17005CA91EEE2866373ABF83C73F4BC309A095205DE3D95944D23E0D3EBD8A4BA0741FCE10829C741A1D7E981ADDCB134BB32044E491E9CCFC7DA5DB6AE5FEE6FDE04EDDB7003AB57049AFF2E5EB02F1D1028B19CB943A5E48C4181E58195F1E025AF00CF1B1ADA9DC59868B6EE991F586CAFAB96633AA595BCEE2A7167347CB2BCC99B03748CFE3564BF5CF0F0C723287C6F044BB53726D43F526489A5267B758ABFE67767178DB0DA256141339243185A2A8025A3047E1DD5007BC02099000EB6463609B16BC88C912E6D27D918BF93D328D65B4E97CB15776EAC5B62839BF15651CC8F677966A0A8D770BD8910B048E07DB29B60AEE9D82353510 | |||
| (PID) Process: | (3000) tacticalrmm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\SystemCertificates\AuthRoot\Certificates\DAC9024F54D8F6DF94935FB1732638CA6AD77C13 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000410352DC0FF7501B16F0028EBA6F45C50F00000001000000140000005BCAA1C2780F0BCB5A90770451D96F38963F012D090000000100000042000000304006082B06010505070302060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030106082B060105050703086200000001000000200000000687260331A72403D909F105E69BCF0D32E1BD2493FFC6D9206D11BCD67707390B000000010000001E000000440053005400200052006F006F0074002000430041002000580033000000140000000100000014000000C4A7B1A47B2C71FADBE14B9075FFC415608589101D00000001000000100000004558D512EECB27464920897DE7B660537F000000010000000E000000300C060A2B0601040182370A03047E000000010000000800000000C001B39667D60168000000010000000800000000409120D035D901030000000100000014000000DAC9024F54D8F6DF94935FB1732638CA6AD77C131900000001000000100000006CF252FEC3E8F20996DE5D4DD9AEF42420000000010000004E0300003082034A30820232A003020102021044AFB080D6A327BA893039862EF8406B300D06092A864886F70D0101050500303F31243022060355040A131B4469676974616C205369676E617475726520547275737420436F2E311730150603550403130E44535420526F6F74204341205833301E170D3030303933303231313231395A170D3231303933303134303131355A303F31243022060355040A131B4469676974616C205369676E617475726520547275737420436F2E311730150603550403130E44535420526F6F7420434120583330820122300D06092A864886F70D01010105000382010F003082010A0282010100DFAFE99750088357B4CC6265F69082ECC7D32C6B30CA5BECD9C37DC740C118148BE0E83376492AE33F214993AC4E0EAF3E48CB65EEFCD3210F65D22AD9328F8CE5F777B0127BB595C089A3A9BAED732E7A0C063283A27E8A1430CD11A0E12A38B9790A31FD50BD8065DFB7516383C8E28861EA4B6181EC526BB9A2E24B1A289F48A39E0CDA098E3E172E1EDD20DF5BC62A8AAB2EBD70ADC50B1A25907472C57B6AAB34D63089FFE568137B540BC8D6AEEC5A9C921E3D64B38CC6DFBFC94170EC1672D526EC38553943D0FCFD185C40F197EBD59A9B8D1DBADA25B9C6D8DFC115023AABDA6EF13E2EF55C089C3CD68369E4109B192AB62957E3E53D9B9FF0025D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E04160414C4A7B1A47B2C71FADBE14B9075FFC41560858910300D06092A864886F70D01010505000382010100A31A2C9B17005CA91EEE2866373ABF83C73F4BC309A095205DE3D95944D23E0D3EBD8A4BA0741FCE10829C741A1D7E981ADDCB134BB32044E491E9CCFC7DA5DB6AE5FEE6FDE04EDDB7003AB57049AFF2E5EB02F1D1028B19CB943A5E48C4181E58195F1E025AF00CF1B1ADA9DC59868B6EE991F586CAFAB96633AA595BCEE2A7167347CB2BCC99B03748CFE3564BF5CF0F0C723287C6F044BB53726D43F526489A5267B758ABFE67767178DB0DA256141339243185A2A8025A3047E1DD5007BC02099000EB6463609B16BC88C912E6D27D918BF93D328D65B4E97CB15776EAC5B62839BF15651CC8F677966A0A8D770BD8910B048E07DB29B60AEE9D82353510 | |||
| (PID) Process: | (1932) meshagent.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Mesh Agent |
| Operation: | write | Name: | ImagePath |
Value: "C:\Program Files\Mesh Agent\MeshAgent.exe" | |||
| (PID) Process: | (756) MeshAgent.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
172
Suspicious files
51
Text files
1 455
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2812 | tacticalagent-v2.6.1-windows-amd64.exe | C:\Users\admin\AppData\Local\Temp\is-TF22D.tmp\tacticalagent-v2.6.1-windows-amd64.tmp | executable | |
MD5:1A72B8895835B7B6395EBB8745DBDAF3 | SHA256:9E01307B6D0884E0384CCC1476BB26B71726D550CCC7C6BD342059C4974879DD | |||
| 2692 | tacticalagent-v2.6.1-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-ODM2P.tmp | executable | |
MD5:F93CAC9DE0548EA909FAF3EB1807122D | SHA256:6AF022E259A16E958501D614F47814FE3CF8598989DF683718F4D7DD3AF6555B | |||
| 896 | fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe | C:\ProgramData\TacticalRMM\tacticalagent-v2.6.1-windows-amd64.exe | executable | |
MD5:1B03A5C84F80E3CECD83AB99118E1576 | SHA256:1C85338D737773209FE6485EF61102B3012F0B81D1CAB1D7CCB29681FCE8428D | |||
| 2692 | tacticalagent-v2.6.1-windows-amd64.tmp | C:\Users\admin\AppData\Local\Temp\is-IVM2I.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2692 | tacticalagent-v2.6.1-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.exe | executable | |
MD5:F93CAC9DE0548EA909FAF3EB1807122D | SHA256:6AF022E259A16E958501D614F47814FE3CF8598989DF683718F4D7DD3AF6555B | |||
| 756 | MeshAgent.exe | C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\0A786543C1F7E3449D4FD93449414BA5CAB3D00B | binary | |
MD5:33E852A71749AB890E1B9430441D89C0 | SHA256:FD6B85314DD8313171DFECE720768D3DA00F23F72F9D8DEE6087D03CF3F6A828 | |||
| 3000 | tacticalrmm.exe | C:\Program Files\TacticalAgent\meshagent.exe | executable | |
MD5:8694A74276EA28EED69EB7D70FAEB653 | SHA256:FCE3F1CE8ADD63C9984C0819D52B9753AD60E9BF13F78177DA6CA8FFFADD414D | |||
| 756 | MeshAgent.exe | C:\Windows\system32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\40AAFFAF6F04D0C97A402F4A24C7517B4ECAD2A4 | binary | |
MD5:B1866D3322CDD0E13ED91F728252FD70 | SHA256:57CE3B50EC19B1C26B6CCE7BD65C60B3D2B176D1D039397940E5BB06CD5932BA | |||
| 3000 | tacticalrmm.exe | C:\Users\admin\AppData\Local\Temp\TarD72A.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1932 | meshagent.exe | C:\Program Files\Mesh Agent\MeshAgent.exe | executable | |
MD5:8694A74276EA28EED69EB7D70FAEB653 | SHA256:FCE3F1CE8ADD63C9984C0819D52B9753AD60E9BF13F78177DA6CA8FFFADD414D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
32
DNS requests
10
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3000 | tacticalrmm.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5fe0405e3712e774 | unknown | compressed | 65.2 Kb | unknown |
2692 | powershell.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?659314f0cf787bda | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
896 | fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
896 | fc39e6cb0ae28dcd647eedbb041a5c9aa295b2db883232960ef0a48d86e93856.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
3000 | tacticalrmm.exe | 34.38.164.94:443 | api.bithumb.ceo | GOOGLE-CLOUD-PLATFORM | US | unknown |
3000 | tacticalrmm.exe | 23.32.238.219:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
756 | MeshAgent.exe | 34.38.164.94:443 | api.bithumb.ceo | GOOGLE-CLOUD-PLATFORM | US | unknown |
3000 | tacticalrmm.exe | 188.114.97.3:443 | icanhazip.tacticalrmm.io | CLOUDFLARENET | NL | unknown |
1088 | tacticalrmm.exe | 34.38.164.94:443 | api.bithumb.ceo | GOOGLE-CLOUD-PLATFORM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
objects.githubusercontent.com |
| shared |
api.bithumb.ceo |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
mesh.bithumb.ceo |
| unknown |
icanhazip.tacticalrmm.io |
| unknown |
chocolatey.org |
| whitelisted |
community.chocolatey.org |
| malicious |
packages.chocolatey.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | tacticalrmm.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2692 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |