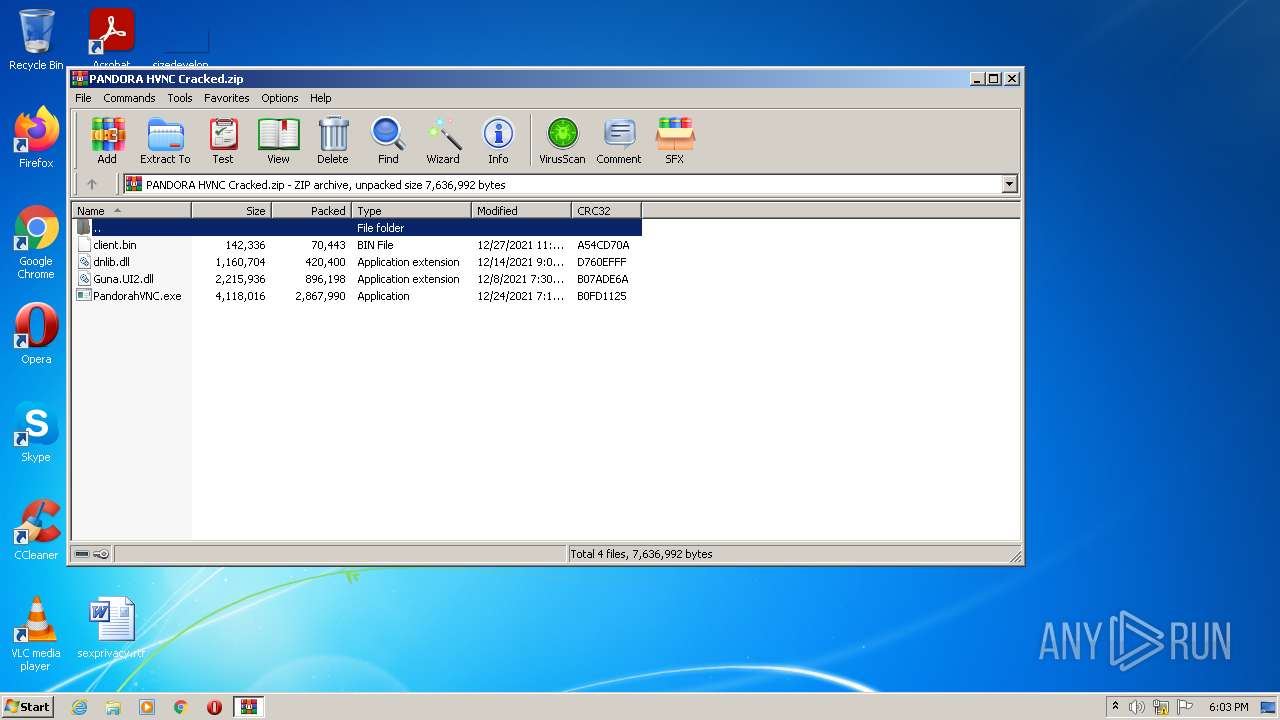
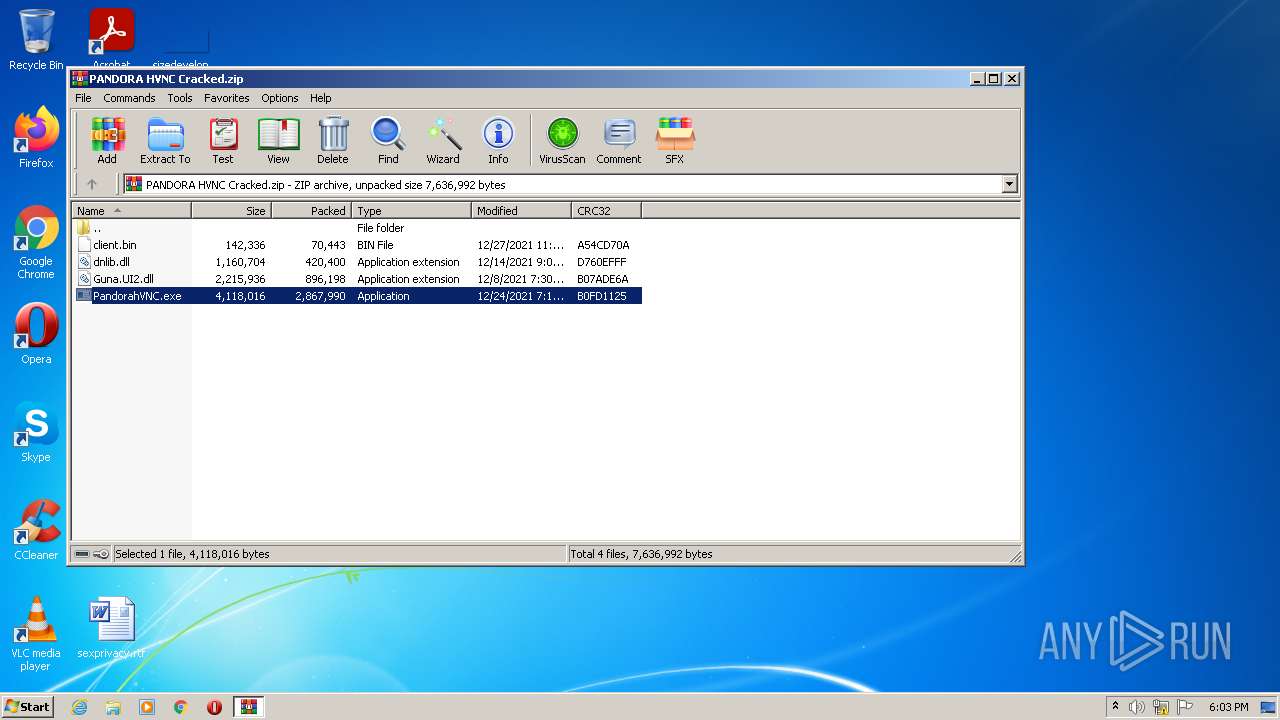
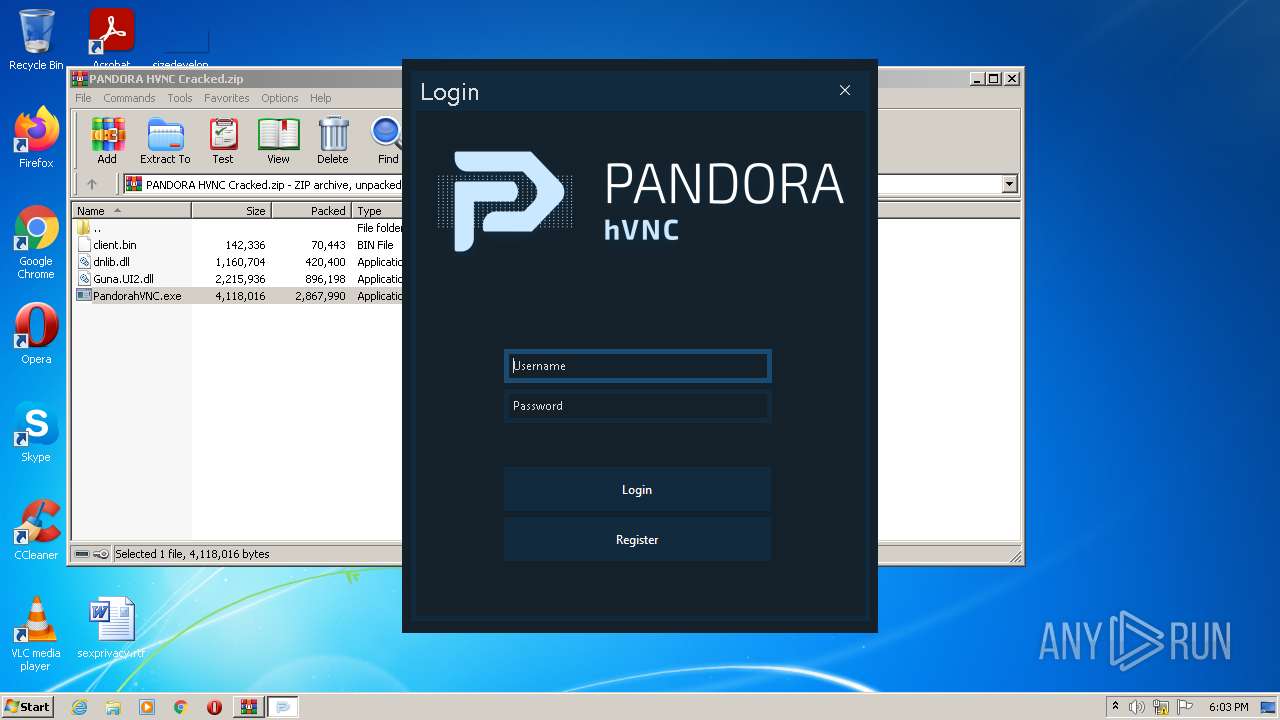
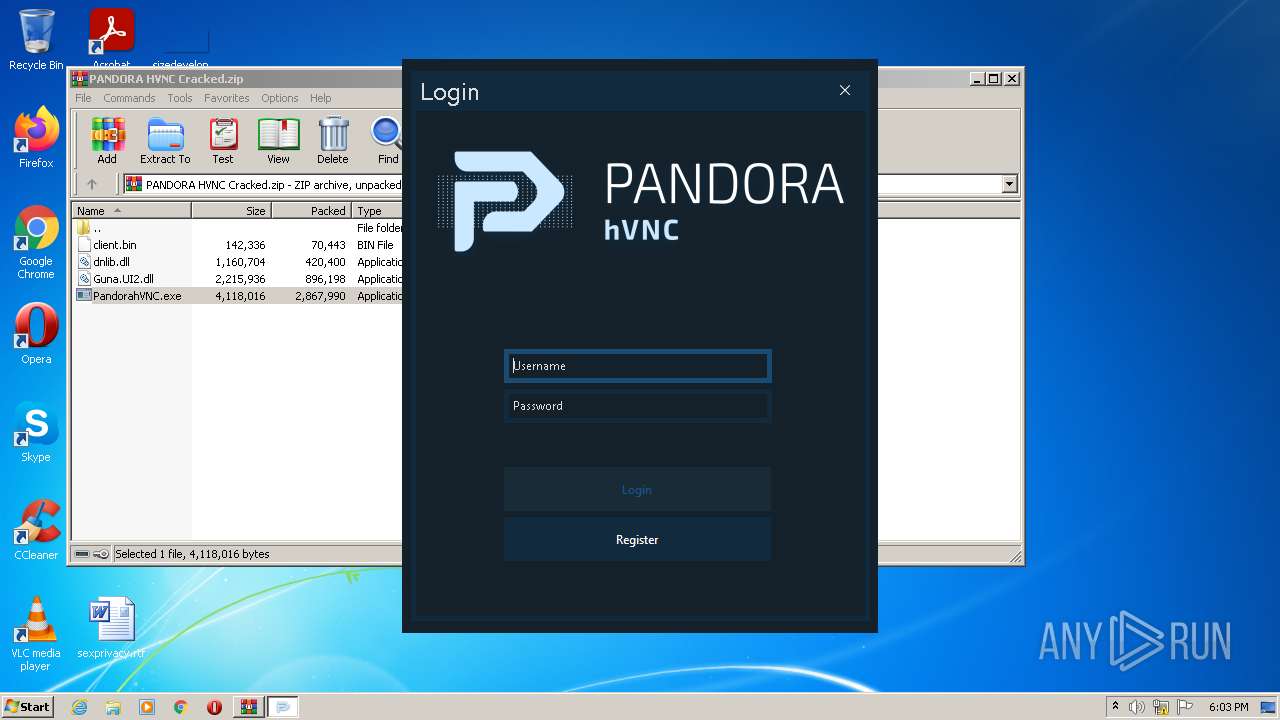
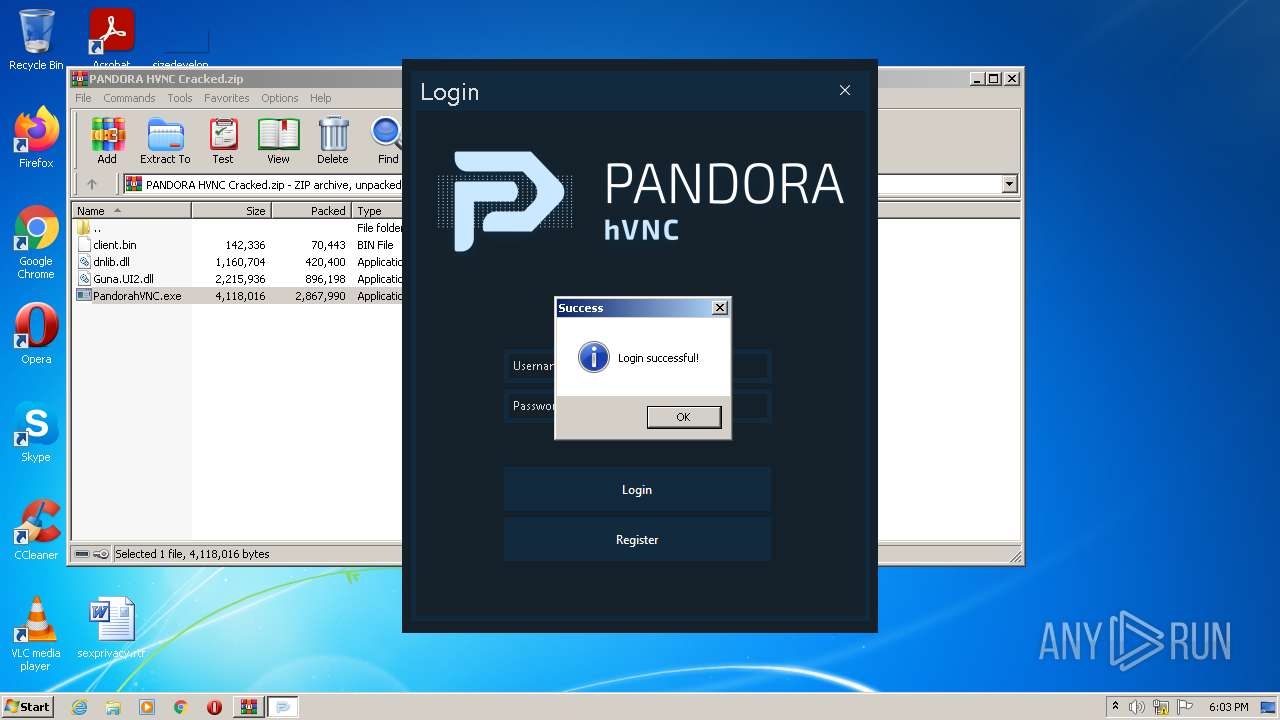
| File name: | PANDORA HVNC Cracked.zip |
| Full analysis: | https://app.any.run/tasks/3538514a-3275-4c84-a3f9-17f89510bb31 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2022, 18:03:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 777AAF5C482A7684F1ED0687DD61D8D0 |
| SHA1: | 1F32A4D672195828D35BCA92802100BF5BC1B049 |
| SHA256: | FC32BB70AA44B81D2DA4C32A8EE7A47A66C6DFFFA495B1F77E9349CEB737B0AE |
| SSDEEP: | 98304:GiJ6eDGzffAEWVVNMUWfWw96NmNqEg80e:GiJL6bfSVDJzw9+n980e |
MALICIOUS
Drops executable file immediately after starts
- PandorahVNC.exe (PID: 3416)
Loads dropped or rewritten executable
- PandorahVNC.exe (PID: 3416)
Application was dropped or rewritten from another process
- PandorahVNC.exe (PID: 3416)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3644)
Reads the computer name
- WinRAR.exe (PID: 3644)
- PandorahVNC.exe (PID: 3416)
Checks supported languages
- PandorahVNC.exe (PID: 3416)
- WinRAR.exe (PID: 3644)
Executable content was dropped or overwritten
- PandorahVNC.exe (PID: 3416)
- WinRAR.exe (PID: 3644)
Drops a file that was compiled in debug mode
- PandorahVNC.exe (PID: 3416)
- WinRAR.exe (PID: 3644)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | PandorahVNC.exe |
|---|---|
| ZipUncompressedSize: | 4118016 |
| ZipCompressedSize: | 2867990 |
| ZipCRC: | 0xb0fd1125 |
| ZipModifyDate: | 2021:12:24 19:11:03 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3416 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\PandorahVNC.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\PandorahVNC.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Pandora hVNC Exit code: 0 Version: 1.0.1 Modules
| |||||||||||||||
| 3644 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PANDORA HVNC Cracked.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 079
Read events
1 060
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PANDORA HVNC Cracked.zip | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\dnlib.dll | executable | |
MD5:E517EAEABD955F1E0F83ED04A0E6DD86 | SHA256:D04369E2FAFABB36FDC31FC63B9A4BFD2BBA577A203EE8180F9B084D9B344676 | |||
| 3644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\Guna.UI2.dll | executable | |
MD5:D65FD6DBBD3C9AC74139AEAEDC4A5816 | SHA256:84199A22C8669A39800272C3DA0D969EC4E8D77D67B9D324CA049953A5042C71 | |||
| 3416 | PandorahVNC.exe | C:\Users\admin\AppData\Local\Temp\1a5fdae6-8f46-4b8b-a738-d6572f690d43\AgileDotNetRT.dll | executable | |
MD5:14FF402962AD21B78AE0B4C43CD1F194 | SHA256:FB9646CB956945BDC503E69645F6B5316D3826B780D3C36738D6B944E884D15B | |||
| 3644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\PandorahVNC.exe | executable | |
MD5:39EF11E7673738D7DAB6B7396044D003 | SHA256:ECED18F42CC7A54E40444F42B4EE3A200022837B66235E5239CEBE0AB96A2740 | |||
| 3644 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3644.45626\client.bin | executable | |
MD5:60B39085C266F364C6B1269AB8FE79F5 | SHA256:AD45703EBDFD43596469416BC9E24374D77A6F361057A31B6CC659789522DA75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report