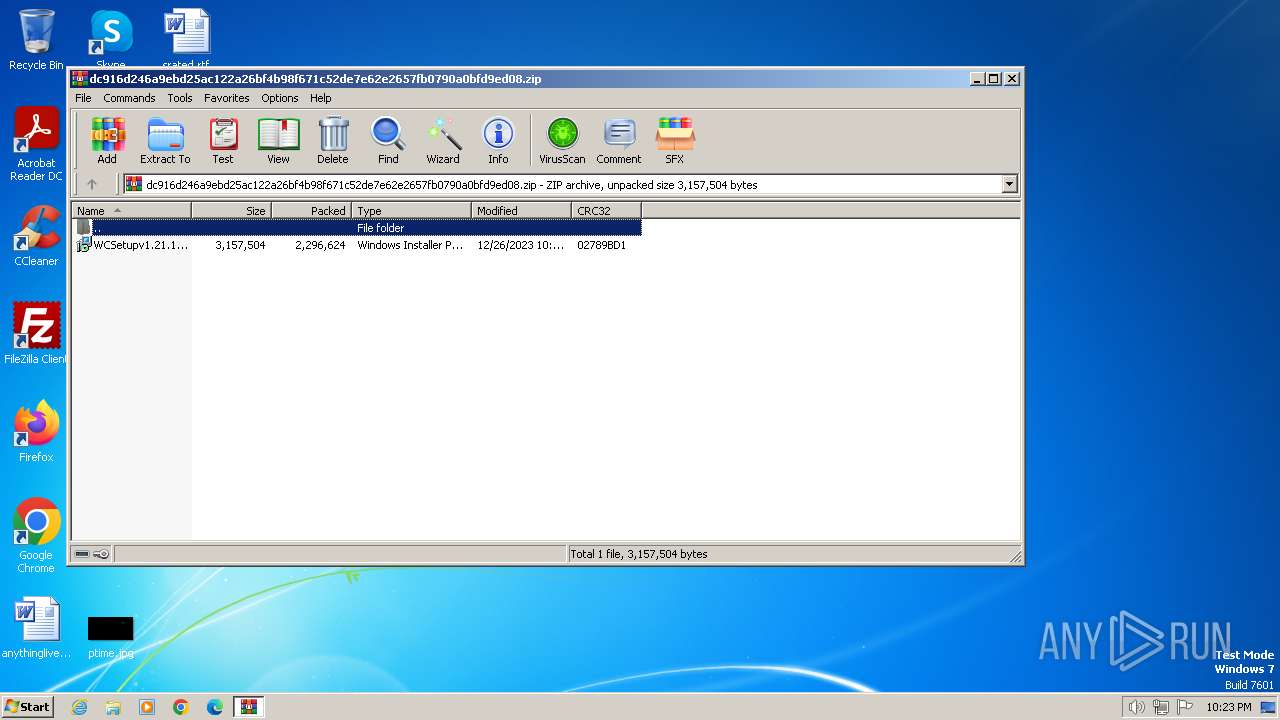
| File name: | dc916d246a9ebd25ac122a26bf4b98f671c52de7e62e2657fb0790a0bfd9ed08.zip |
| Full analysis: | https://app.any.run/tasks/689af998-e081-4e28-91b8-4d0ef5b4b12e |
| Verdict: | Malicious activity |
| Analysis date: | December 26, 2023, 22:23:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D6621B0F43C2342DC5FA58B0D3623831 |
| SHA1: | A30A99EBA01C51F9662633D170B4EDC87A73BCF3 |
| SHA256: | FC25F6403E477A78CE3B1B8BC019BD1DFD32680231B69892B8CA376A2E7E5F4A |
| SSDEEP: | 98304:rMxRQ2M2YE0ZAyl+TeVp8u6pHadvoDFHHlOaiekRSQsHYVtYa7hgB6CgfGlJDGuw:8O+67d |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 2424)
- powershell.exe (PID: 1600)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 1000)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 2656)
- powershell.exe (PID: 3200)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 2096)
- MSI7093.tmp (PID: 3012)
SUSPICIOUS
Checks Windows Trust Settings
- msiexec.exe (PID: 2020)
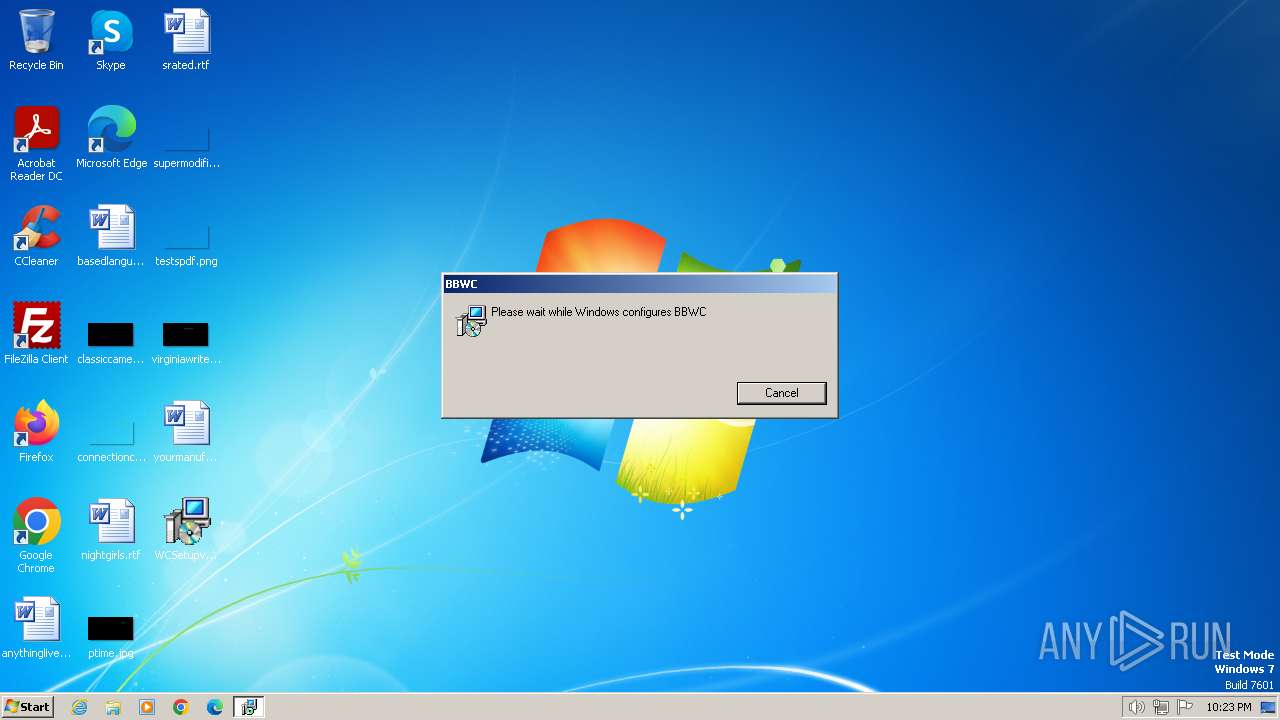
The process hide an interactive prompt from the user
- msiexec.exe (PID: 2096)
- MSI7093.tmp (PID: 3012)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 2096)
- MSI7093.tmp (PID: 3012)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 2096)
The process executes Powershell scripts
- msiexec.exe (PID: 2096)
Reads the Internet Settings
- powershell.exe (PID: 2424)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 1000)
- MSI7093.tmp (PID: 3012)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2656)
Probably obfuscated PowerShell command line is found
- MSI7093.tmp (PID: 3012)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3056)
- powershell.exe (PID: 3200)
Unusual connection from system programs
- powershell.exe (PID: 2656)
- powershell.exe (PID: 1000)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 2368)
The Powershell connects to the Internet
- powershell.exe (PID: 2656)
INFO
Manual execution by a user
- msiexec.exe (PID: 2076)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2076)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 1600)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 1000)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 3200)
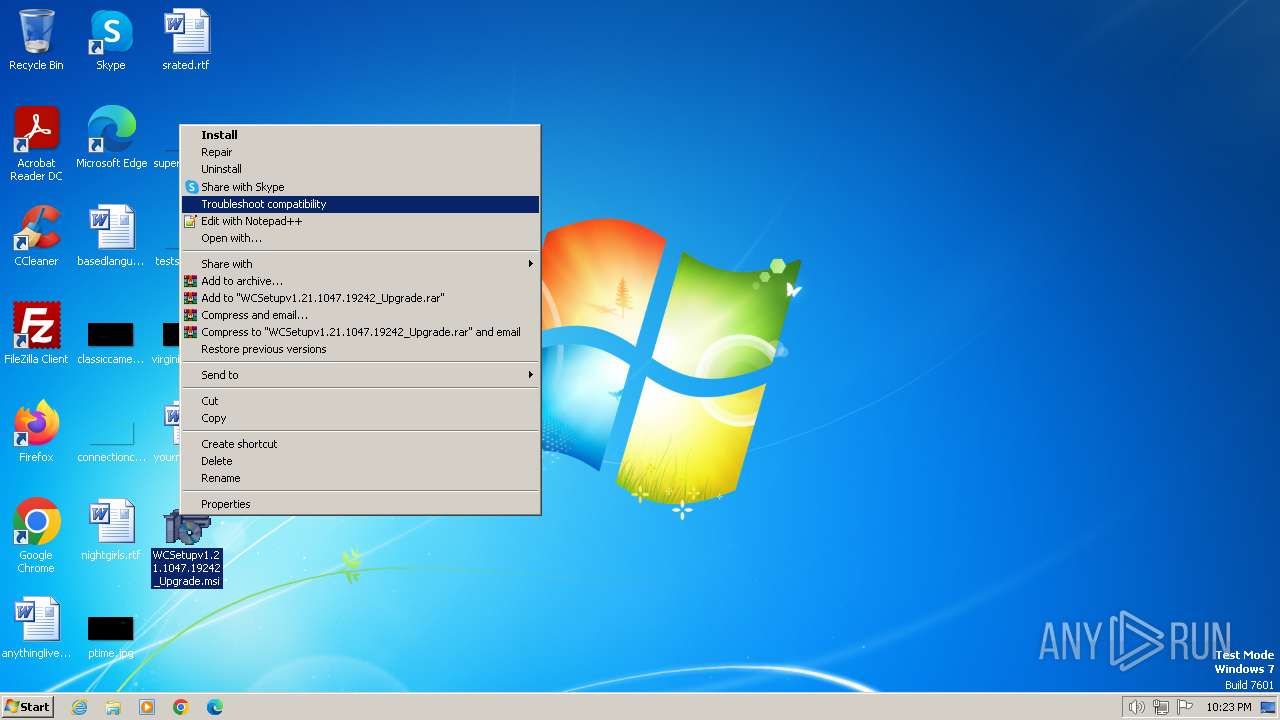
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
- msiexec.exe (PID: 2020)
- 7za.exe (PID: 2728)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2020)
- msiexec.exe (PID: 2096)
Application launched itself
- msiexec.exe (PID: 2020)
Executes as Windows Service
- VSSVC.exe (PID: 784)
Checks supported languages
- msiexec.exe (PID: 2096)
- 7za.exe (PID: 2728)
- MSI7093.tmp (PID: 3012)
- msiexec.exe (PID: 2020)
Reads the computer name
- msiexec.exe (PID: 2096)
- 7za.exe (PID: 2728)
- MSI7093.tmp (PID: 3012)
- msiexec.exe (PID: 2020)
Create files in a temporary directory
- msiexec.exe (PID: 2096)
- powershell.exe (PID: 2424)
- msiexec.exe (PID: 2020)
- powershell.exe (PID: 1600)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 1000)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 3056)
- powershell.exe (PID: 3200)
Reads Environment values
- msiexec.exe (PID: 2096)
- MSI7093.tmp (PID: 3012)
Creates files or folders in the user directory
- msiexec.exe (PID: 2020)
- 7za.exe (PID: 2728)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 2020)
Starts application with an unusual extension
- msiexec.exe (PID: 2020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:26 22:22:56 |
| ZipCRC: | 0x02789bd1 |
| ZipCompressedSize: | 2296624 |
| ZipUncompressedSize: | 3157504 |
| ZipFileName: | WCSetupv1.21.1047.19242_Upgrade.msi |
Total processes
58
Monitored processes
15
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss67DC.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1600 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss5DF0.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2020 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\dc916d246a9ebd25ac122a26bf4b98f671c52de7e62e2657fb0790a0bfd9ed08.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2076 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\WCSetupv1.21.1047.19242_Upgrade.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | C:\Windows\system32\MsiExec.exe -Embedding 43E95603D7A4B21C03CE5796E1FC2E33 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2368 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss6BD7.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2424 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss5820.tmp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2656 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noninteractive -ExecutionPolicy bypass -c "$w="$env:APPDATA"+'/BBWC/';[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'Newtonsoft.Json.dll'));[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'System.Data.SQLite.dll'));[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'ICSharpCode.SharpZipLib.dll'));[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'LZ4.dll'));$f=$w+'WC.txt';$h=Get-Content -Path $f -Raw;$h=Get-Content -Path $f -Raw;[byte[]]$bytes=($h -split '(.{2})' -ne '' -replace '^','0X');[Reflection.Assembly]::Load($bytes);[WebCompanion.StartUp]::Start()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | MSI7093.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
16 272
Read events
16 172
Write events
89
Delete events
11
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
21
Suspicious files
27
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2020 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi580E.tmp.txt | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss580F.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss5820.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi5D14.tmp.txt | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss5D15.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 2096 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss5DF0.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 2020 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:78CFF8199E57B2EDE23A515C9C044B8D | SHA256:56E0D2AB816B9E6EC42C70A5A23BE0718EAF381FE0B99DC7F830E36CC83E0681 | |||
| 2020 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{26122e17-1de7-46d6-b0b8-2ed306502c2e}_OnDiskSnapshotProp | binary | |
MD5:78CFF8199E57B2EDE23A515C9C044B8D | SHA256:56E0D2AB816B9E6EC42C70A5A23BE0718EAF381FE0B99DC7F830E36CC83E0681 | |||
| 2020 | msiexec.exe | C:\Windows\Installer\MSI57B1.tmp | executable | |
MD5:07EBB743BBD7230E04C23BCBAA03FC44 | SHA256:194B29C26D925FDC1F1AA1802714118D0CA30E413C7FEA5C19A928EBA7CC43B0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
10
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2424 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2660 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
1000 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2368 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2656 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2656 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2656 | powershell.exe | GET | 404 | 18.239.18.3:80 | http://2r5kg4.com/ext/fhgid?fid= | unknown | html | 1.76 Kb | unknown |
2656 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
2656 | powershell.exe | POST | 200 | 18.239.15.157:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | binary | 19 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2424 | powershell.exe | 18.239.15.157:80 | d2vtta4ibs40qt.cloudfront.net | — | US | unknown |
2660 | powershell.exe | 18.239.15.157:80 | d2vtta4ibs40qt.cloudfront.net | — | US | unknown |
1000 | powershell.exe | 18.239.15.157:80 | d2vtta4ibs40qt.cloudfront.net | — | US | unknown |
2368 | powershell.exe | 18.239.15.157:80 | d2vtta4ibs40qt.cloudfront.net | — | US | unknown |
2656 | powershell.exe | 18.239.15.157:80 | d2vtta4ibs40qt.cloudfront.net | — | US | unknown |
2656 | powershell.exe | 18.239.18.3:80 | 2r5kg4.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d2vtta4ibs40qt.cloudfront.net |
| unknown |
2r5kg4.com |
| unknown |