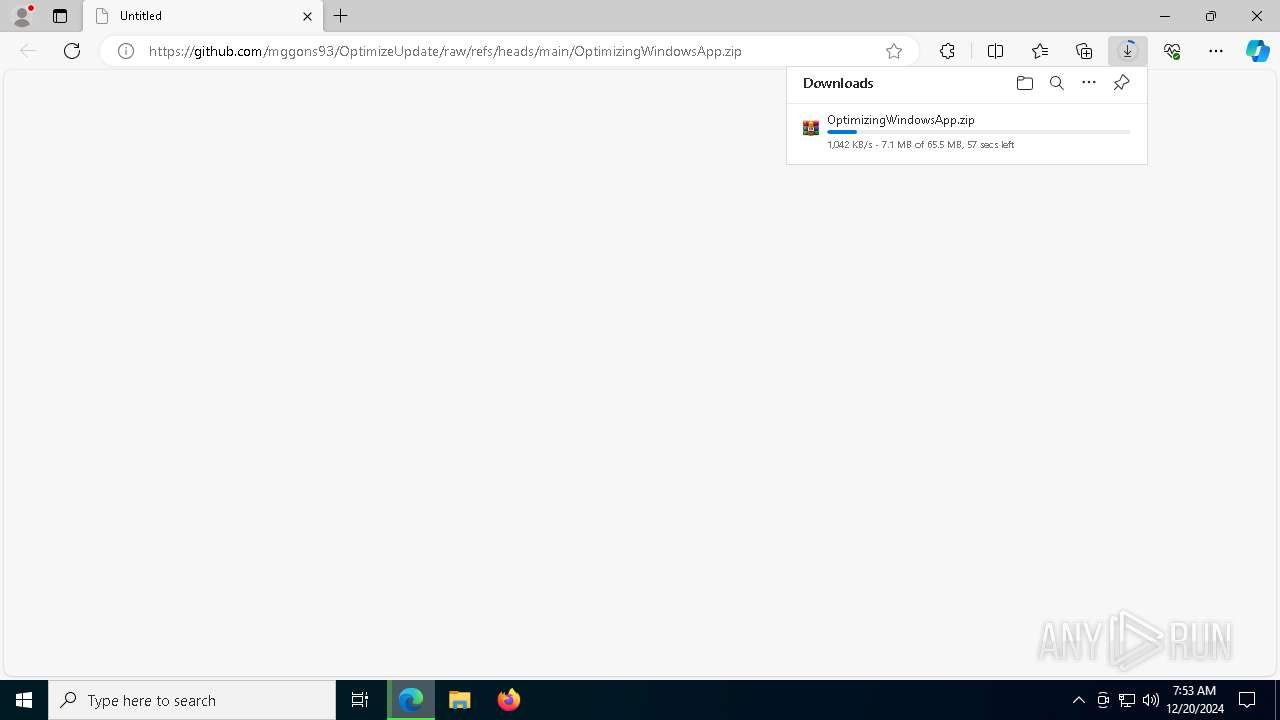
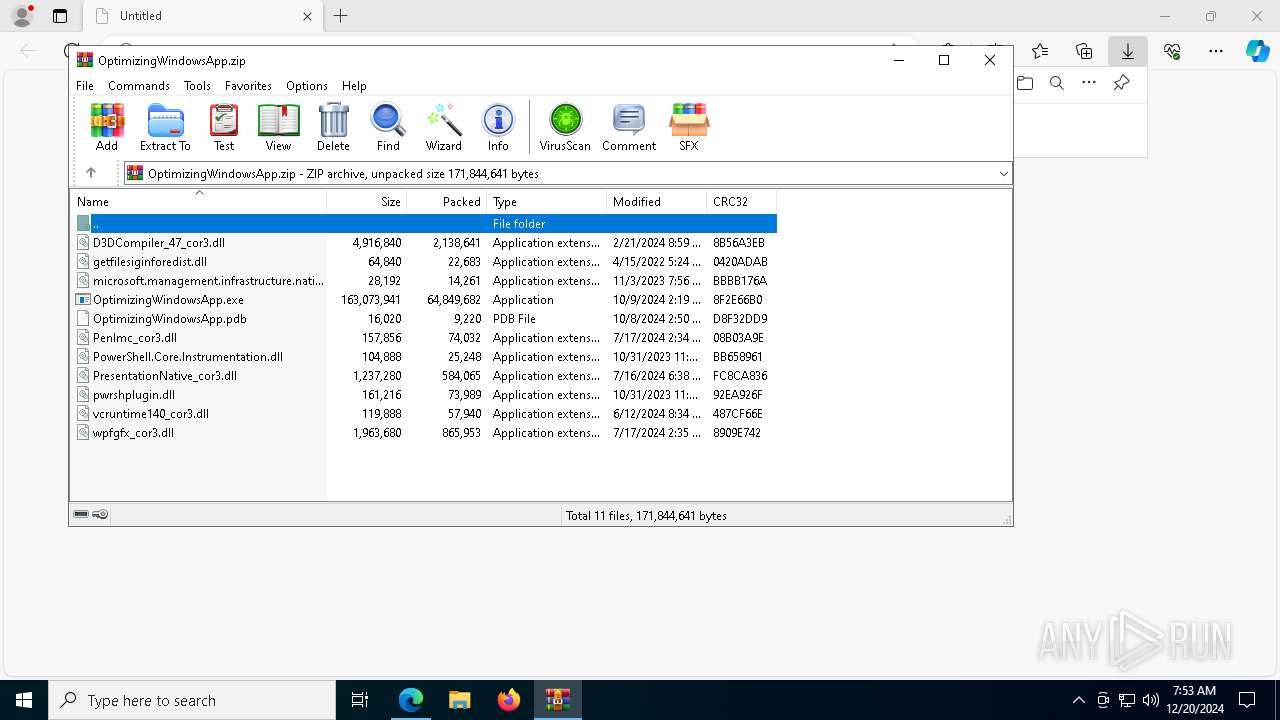
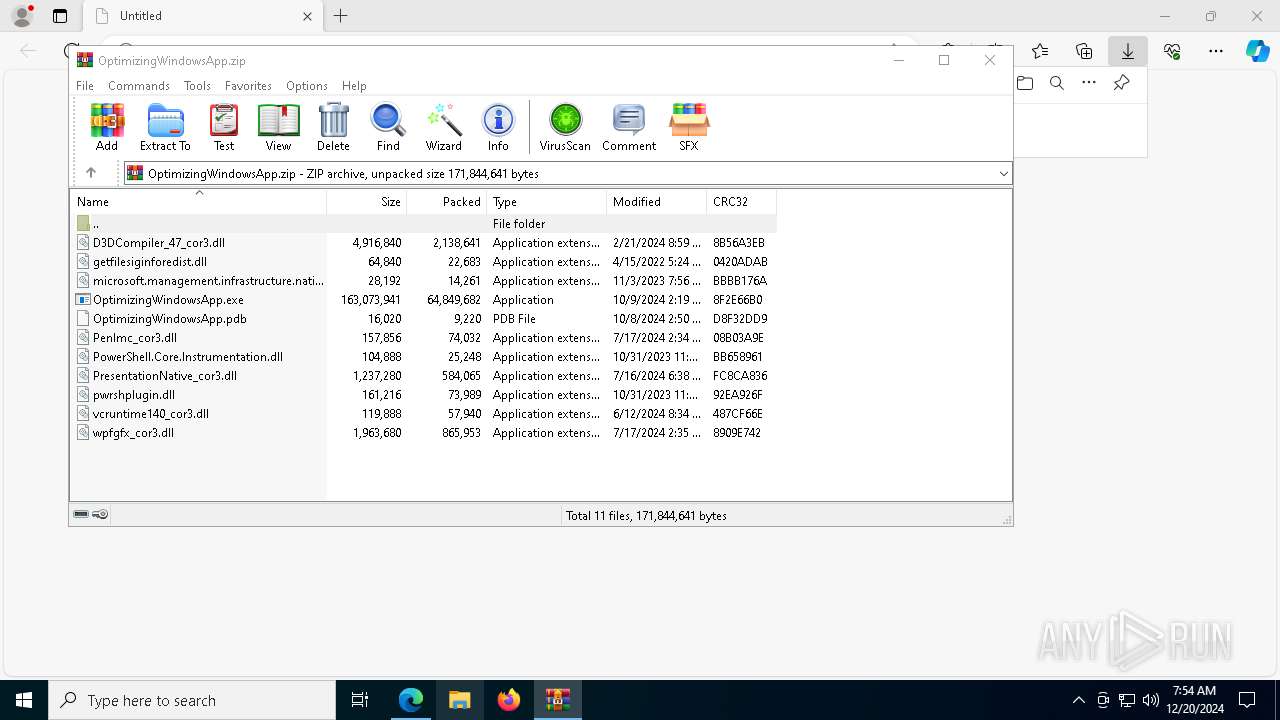
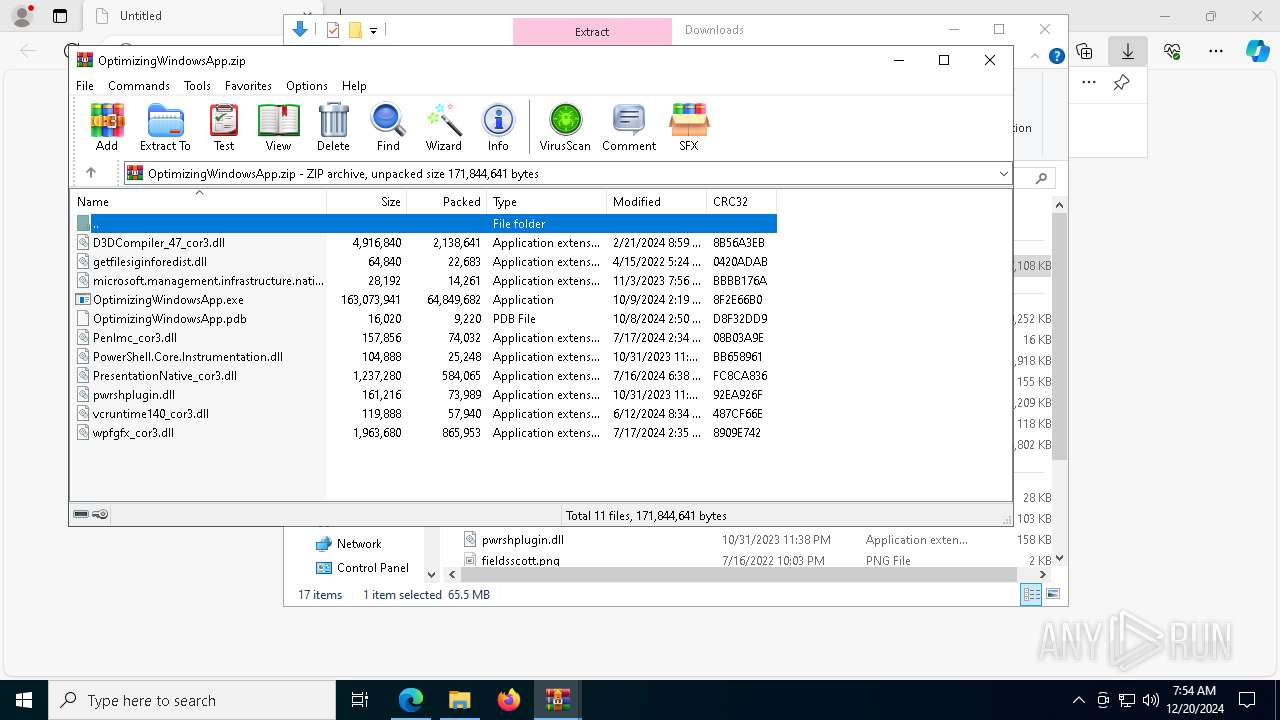
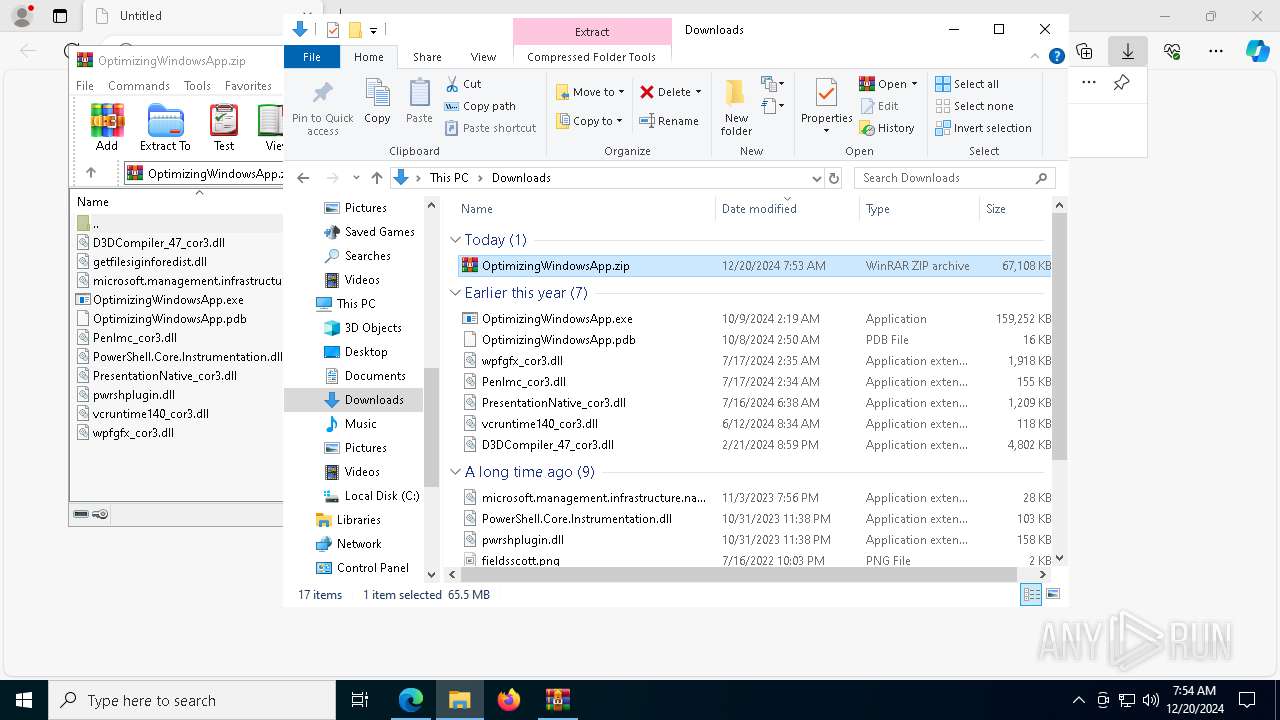
| URL: | https://github.com/mggons93/OptimizeUpdate/raw/refs/heads/main/OptimizingWindowsApp.zip |
| Full analysis: | https://app.any.run/tasks/90724128-0745-49ce-a94a-2029c82f07ea |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | December 20, 2024, 07:53:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 450C654E6B012F932E5D8C66FE8BE1C7 |
| SHA1: | 9667D29C9E7156ADF12AA97460DB6A5000A15A74 |
| SHA256: | FC1E077BFB44B0C82AD1264C045E1B33D96C5AB735DF43BAD4F797A5430E6889 |
| SSDEEP: | 3:N8tEd4eWKF/DF3LNKeMZKKL8qVYV:2uuJg3LNKsQ8B |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7904)
- powershell.exe (PID: 4396)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 4708)
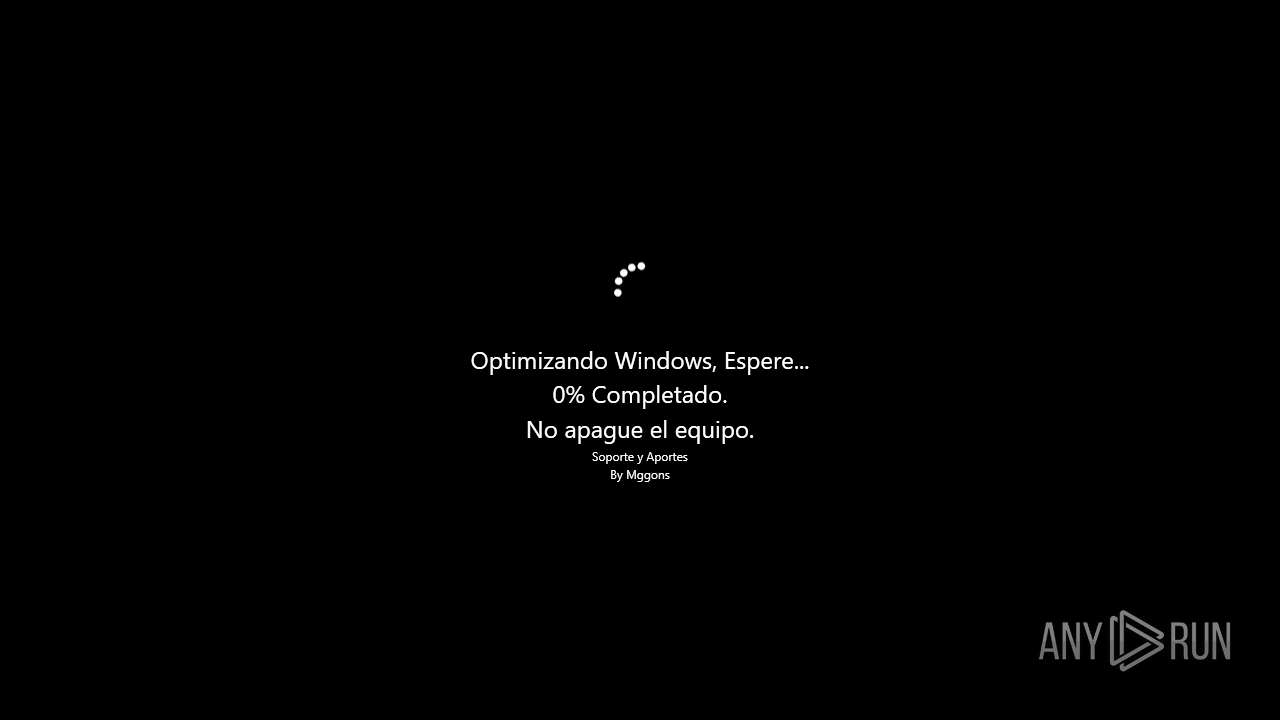
- OptimizingWindowsApp.exe (PID: 5488)
- runonce.exe (PID: 4288)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 7904)
Changes Windows Error Reporting flag
- powershell.exe (PID: 7904)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2420)
- WinRAR.exe (PID: 4052)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4052)
- StartMenuExperienceHost.exe (PID: 3876)
The process bypasses the loading of PowerShell profile settings
- OptimizingWindowsApp.exe (PID: 5488)
- powershell.exe (PID: 4708)
The process executes Powershell scripts
- OptimizingWindowsApp.exe (PID: 5488)
- powershell.exe (PID: 4708)
Application launched itself
- powershell.exe (PID: 4708)
Starts POWERSHELL.EXE for commands execution
- OptimizingWindowsApp.exe (PID: 5488)
- powershell.exe (PID: 4708)
- runonce.exe (PID: 4288)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7904)
The process creates files with name similar to system file names
- Dism.exe (PID: 5576)
- Dism.exe (PID: 3420)
Executable content was dropped or overwritten
- Dism.exe (PID: 5576)
- Dism.exe (PID: 3420)
- powershell.exe (PID: 7904)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 7196)
- DismHost.exe (PID: 6152)
- DismHost.exe (PID: 5044)
Uses powercfg.exe to modify the power settings
- powershell.exe (PID: 7904)
Executes as Windows Service
- VSSVC.exe (PID: 1400)
Connects to unusual port
- powershell.exe (PID: 7904)
Potential Corporate Privacy Violation
- powershell.exe (PID: 7904)
Process requests binary or script from the Internet
- powershell.exe (PID: 7904)
Creates file in the systems drive root
- powershell.exe (PID: 7904)
- OEM.exe (PID: 5536)
Changes the desktop background image
- powershell.exe (PID: 7904)
Uses ICACLS.EXE to modify access control lists
- powershell.exe (PID: 7904)
Takes ownership (TAKEOWN.EXE)
- powershell.exe (PID: 7904)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7904)
The system shut down or reboot
- powershell.exe (PID: 7904)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3680)
Possibly malicious use of IEX has been detected
- runonce.exe (PID: 4288)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 7904)
INFO
Checks supported languages
- identity_helper.exe (PID: 7976)
- OptimizingWindowsApp.exe (PID: 5488)
- DismHost.exe (PID: 7196)
- OEM.exe (PID: 5536)
- SearchApp.exe (PID: 4008)
- TextInputHost.exe (PID: 7636)
- DismHost.exe (PID: 5044)
- StartMenuExperienceHost.exe (PID: 3876)
The process uses the downloaded file
- msedge.exe (PID: 6408)
- msedge.exe (PID: 5788)
- WinRAR.exe (PID: 2420)
- powershell.exe (PID: 7904)
Application launched itself
- msedge.exe (PID: 6408)
Reads Environment values
- identity_helper.exe (PID: 7976)
- DismHost.exe (PID: 7196)
- DismHost.exe (PID: 6152)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2420)
- WinRAR.exe (PID: 4052)
- msedge.exe (PID: 4116)
Reads the computer name
- identity_helper.exe (PID: 7976)
- OptimizingWindowsApp.exe (PID: 5488)
- DismHost.exe (PID: 7196)
- TextInputHost.exe (PID: 7636)
- DismHost.exe (PID: 5044)
- PLUGScheduler.exe (PID: 3680)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6408)
The sample compiled with english language support
- WinRAR.exe (PID: 2420)
- Dism.exe (PID: 5576)
- WinRAR.exe (PID: 4052)
- Dism.exe (PID: 3420)
- msedge.exe (PID: 4116)
- cleanmgr.exe (PID: 1864)
Manual execution by a user
- OptimizingWindowsApp.exe (PID: 5488)
- WinRAR.exe (PID: 4052)
- WinRAR.exe (PID: 8136)
- runonce.exe (PID: 4288)
- powershell.exe (PID: 5776)
Creates files in the program directory
- OptimizingWindowsApp.exe (PID: 5488)
Create files in a temporary directory
- OptimizingWindowsApp.exe (PID: 5488)
- Dism.exe (PID: 5576)
- Dism.exe (PID: 3420)
- cleanmgr.exe (PID: 1864)
Sends debugging messages
- Dism.exe (PID: 5576)
- DismHost.exe (PID: 7196)
- Dism.exe (PID: 3420)
- DismHost.exe (PID: 6152)
- StartMenuExperienceHost.exe (PID: 3876)
- cleanmgr.exe (PID: 1864)
- DismHost.exe (PID: 5044)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7904)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7904)
Manages system restore points
- SrTasks.exe (PID: 3836)
Checks proxy server information
- powershell.exe (PID: 7904)
- SearchApp.exe (PID: 4008)
- cleanmgr.exe (PID: 1864)
Process checks computer location settings
- SearchApp.exe (PID: 4008)
Reads the software policy settings
- SearchApp.exe (PID: 4008)
- cleanmgr.exe (PID: 1864)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4008)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
356
Monitored processes
94
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5840 --field-trial-handle=2600,i,7413016522343359750,16377035829214892009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 420 | "C:\WINDOWS\system32\cmd.exe" /c Cleanmgr /sagerun:65535 | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6444 --field-trial-handle=2600,i,7413016522343359750,16377035829214892009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1400 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7268 --field-trial-handle=2600,i,7413016522343359750,16377035829214892009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1864 | Cleanmgr /sagerun:65535 | C:\Windows\System32\cleanmgr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Disk Space Cleanup Manager for Windows Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6508 --field-trial-handle=2600,i,7413016522343359750,16377035829214892009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7212 --field-trial-handle=2600,i,7413016522343359750,16377035829214892009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2292 | "C:\WINDOWS\system32\powercfg.exe" -duplicatescheme e9a42b02-d5df-448d-aa00-03f14749eb61 | C:\Windows\System32\powercfg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
93 435
Read events
92 888
Write events
500
Delete events
47
Modification events
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5FB3393945882F00 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 7DFA2E3945882F00 | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {BE0C19E0-9D80-410C-80A3-9373F2C10825} | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DF9CF4B9-F016-47F9-B58F-479A85E779D8} | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (6408) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
196
Suspicious files
1 002
Text files
304
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1357d7.TMP | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1357e7.TMP | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1357e7.TMP | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1357f7.TMP | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1357f7.TMP | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
124
DNS requests
107
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
68 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2324 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1735157354&P2=404&P3=2&P4=mL7LOM1QBv6ZL%2fXwM18w0nDT7HtN6FDnD79maRV3YEXIHJbrqm9qJd2x9iR7hq6nx5kU7iScYZp%2f3OO4Scbnnw%3d%3d | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6584 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2324 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1735157354&P2=404&P3=2&P4=mL7LOM1QBv6ZL%2fXwM18w0nDT7HtN6FDnD79maRV3YEXIHJbrqm9qJd2x9iR7hq6nx5kU7iScYZp%2f3OO4Scbnnw%3d%3d | unknown | — | — | whitelisted |
2324 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1735157354&P2=404&P3=2&P4=mL7LOM1QBv6ZL%2fXwM18w0nDT7HtN6FDnD79maRV3YEXIHJbrqm9qJd2x9iR7hq6nx5kU7iScYZp%2f3OO4Scbnnw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4804 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
68 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
68 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6936 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6936 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6936 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7904 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
7904 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
7904 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7904 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
7904 | powershell.exe | Misc activity | ET INFO Request for EXE via Powershell |
7904 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7904 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
Dism.exe | PID=5576 TID=4968 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5576 TID=4968 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5576 TID=4968 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5576 TID=4968 Loading Provider from location C:\WINDOWS\system32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5576 TID=4968 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5576 TID=4968 Connecting to the provider located at C:\WINDOWS\system32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=7196 TID=7228 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=7196 TID=7228 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=7196 TID=7228 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=5576 TID=4968 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |