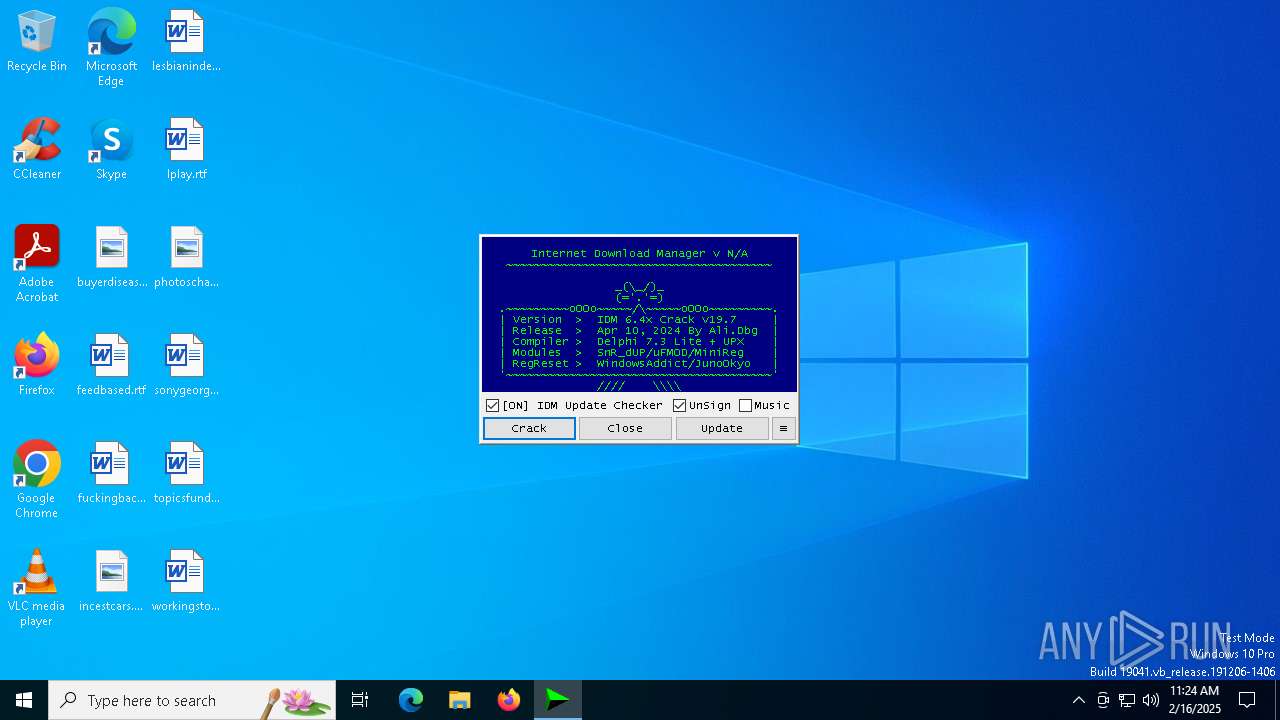
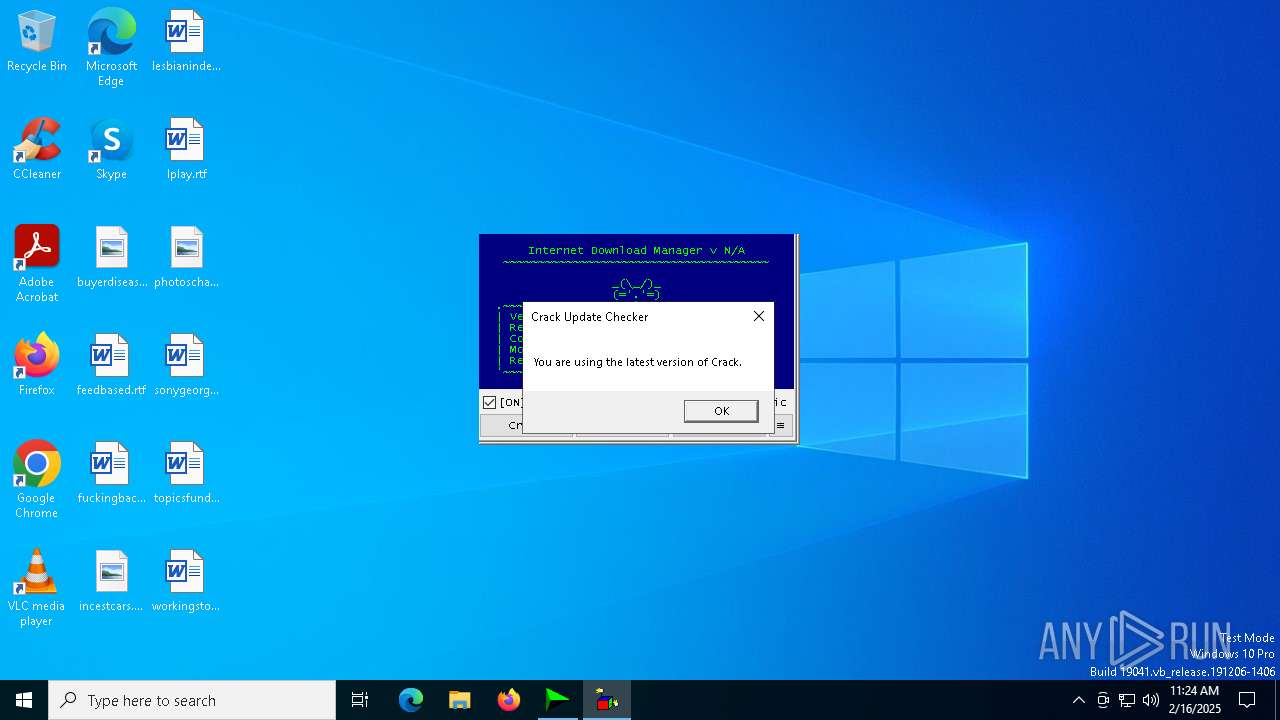
| File name: | IDM_6.4x_Crack_v19.7.exe |
| Full analysis: | https://app.any.run/tasks/8e2f4b56-b287-47e4-aca0-ff4bdd1d9a80 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 11:24:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 27016937B5781C4F84B6B3432170F4D0 |
| SHA1: | BC812A8C4D44A3503FFD6A46E4FDAB925C622344 |
| SHA256: | FC1A02B509B8F351AC45BD45EFD4E7296B365545A48FFD6A14E8E07BC7189155 |
| SSDEEP: | 1536:kaaR+ChjLjFnDrpfBzftBr20ezIL6bFwNA5fufSiaAx:khRdHjNDrpfdfjr20xUH9uKdAx |
MALICIOUS
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 6768)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6768)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6768)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6768)
Deletes a file (SCRIPT)
- wscript.exe (PID: 6768)
SUSPICIOUS
The process executes VB scripts
- IDM_6.4x_Crack_v19.7.exe (PID: 6200)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6768)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6768)
INFO
Reads the computer name
- IDM_6.4x_Crack_v19.7.exe (PID: 6200)
Checks supported languages
- IDM_6.4x_Crack_v19.7.exe (PID: 6200)
Create files in a temporary directory
- IDM_6.4x_Crack_v19.7.exe (PID: 6200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 57344 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 184320 |
| EntryPoint: | 0x3b700 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
129
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.7.exe" | C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6200 | "C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.7.exe" | C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.7.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6768 | wscript.exe "C:\Users\admin\AppData\Local\Temp\\UPDT.vbs" /browser:"C:\Program Files\Google\Chrome\Application\chrome.exe" /crkver:"19.7" | C:\Windows\SysWOW64\wscript.exe | IDM_6.4x_Crack_v19.7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
540
Read events
528
Write events
12
Delete events
0
Modification events
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wow6432Node\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 0 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableCMD |
Value: 0 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 0 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 0 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | DisallowRun |
Value: 0 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\PowerShell |
| Operation: | write | Name: | EnableScripts |
Value: 1 | |||
| (PID) Process: | (6200) IDM_6.4x_Crack_v19.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\PowerShell\1\ShellIds\ScriptedDiagnostics |
| Operation: | write | Name: | ExecutionPolicy |
Value: Bypass | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6200 | IDM_6.4x_Crack_v19.7.exe | C:\Users\admin\AppData\Local\Temp\UPDT.vbs | text | |
MD5:7B18A872D4BE22EECF2F95CE5E63CE15 | SHA256:E64D9B855B8F02B15626C7E932C0451C07AF8E8EBB53BB17626C66E117F50CBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6076 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6076 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6448 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6908 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6908 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4872 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6076 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6076 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.58:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
idm.0dy.ir |
| unknown |
arc.msn.com |
| whitelisted |