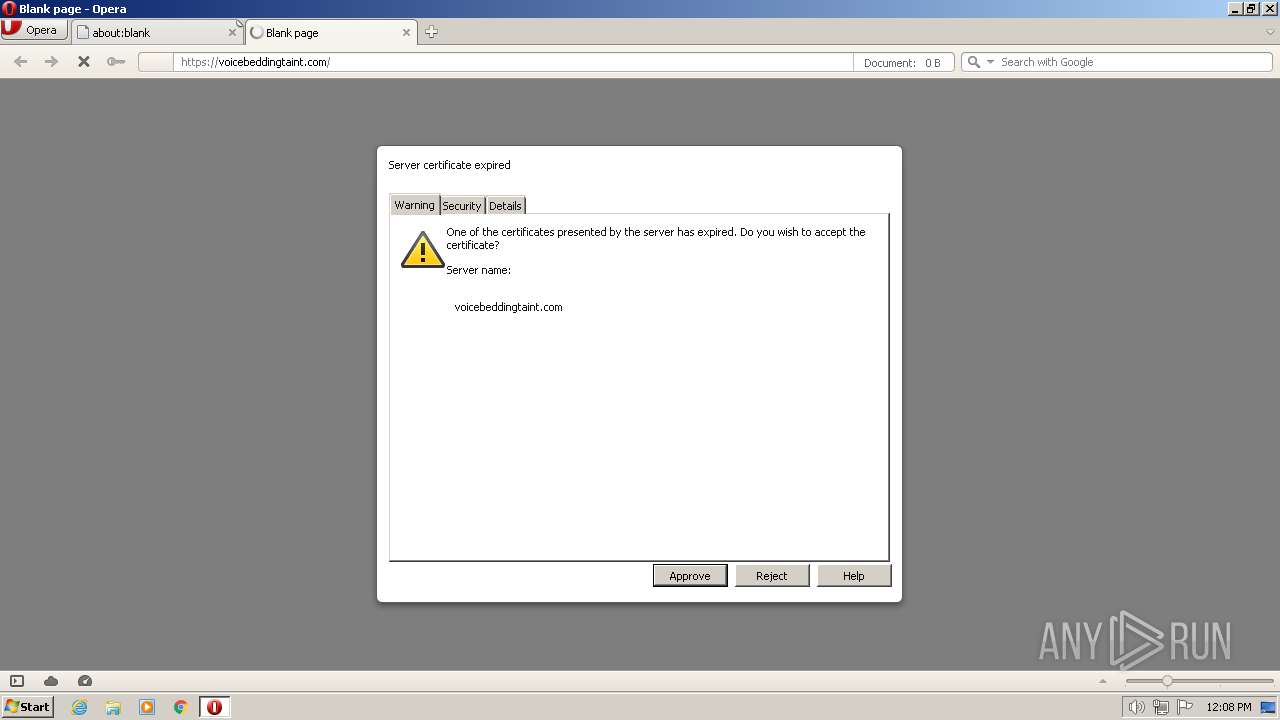
| URL: | https://voicebeddingtaint.com |
| Full analysis: | https://app.any.run/tasks/dadb31f8-3aac-4715-8f00-42744c90ac8d |
| Verdict: | Malicious activity |
| Analysis date: | March 02, 2023, 12:07:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MD5: | 3FF5D87CFFFAB7C31147E6A76EB05B8D |
| SHA1: | F3CEA5FFBDA107FDB98C632B595448AD81A91D1F |
| SHA256: | FBEEC2D17DF3F95AA1B814D141AF1670DDF547F20392D7B30D00E4ADA95B6CCC |
| SSDEEP: | 3:N8FHA8L2I:2i8L2I |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3432 | "C:\Program Files\Opera\opera.exe" "https://voicebeddingtaint.com" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
2 190
Read events
2 072
Write events
118
Delete events
0
Modification events
| (PID) Process: | (3432) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "https://voicebeddingtaint.com" | |||
| (PID) Process: | (3432) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
16
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr1A28.tmp | text | |
MD5:— | SHA256:— | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr1A97.tmp | xml | |
MD5:— | SHA256:— | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\autosave.win | text | |
MD5:0100E3D2A29941CEEF4E37312A7FA332 | SHA256:0C42C7737A5ABA75C8E2EA967E2A994542B2C641D0A370EDC41BC4D70A7CAC70 | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\autosave.win.bak | text | |
MD5:46A734B275C8C258D9D6F508E73B36AD | SHA256:B80192EDC377DD212C9E488E1983FBCD68CF83330576EFD7579B7AB30FA3672B | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\8A17Q5R2N6KXNJCEFQNR.temp | binary | |
MD5:FDBCDB294DED05EA01DCAA246B98C2C5 | SHA256:EAEC5A291DBC8E8760BAB0C1BB27CB801F671166CE85310FD173F54111357C4B | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr1A18.tmp | text | |
MD5:0100E3D2A29941CEEF4E37312A7FA332 | SHA256:0C42C7737A5ABA75C8E2EA967E2A994542B2C641D0A370EDC41BC4D70A7CAC70 | |||
| 3432 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF10c2572.TMP | binary | |
MD5:DBC8C3C79F0DFF4745A5E25E13611AEF | SHA256:70C54F2C53CF246603B8DE4755D95C5AA51BF4B232340BEA5879724A1F84F675 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
20
DNS requests
10
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3432 | opera.exe | GET | 200 | 2.16.186.27:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgODT7uuLu9XOyEYZea2UiaUoQ%3D%3D | unknown | der | 503 b | shared |
3432 | opera.exe | GET | 200 | 23.37.41.57:80 | http://x1.c.lencr.org/ | NL | der | 740 b | whitelisted |
3432 | opera.exe | GET | 200 | 104.18.39.201:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3432 | opera.exe | 192.243.59.12:443 | voicebeddingtaint.com | DataWeb Global Group B.V. | US | malicious |
3432 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3432 | opera.exe | 23.37.41.57:80 | x1.c.lencr.org | AKAMAI-AS | DE | suspicious |
3432 | opera.exe | 142.250.184.238:443 | google.com | GOOGLE | US | whitelisted |
3432 | opera.exe | 104.18.39.201:80 | crl.identrust.com | CLOUDFLARENET | — | unknown |
— | — | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3432 | opera.exe | 2.16.186.27:80 | r3.o.lencr.org | Akamai International B.V. | DE | whitelisted |
3432 | opera.exe | 107.167.110.216:443 | sitecheck2.opera.com | OPERASOFTWARE | US | malicious |
3432 | opera.exe | 192.243.59.20:443 | voicebeddingtaint.com | DataWeb Global Group B.V. | US | malicious |
3432 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
voicebeddingtaint.com |
| suspicious |
certs.opera.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
crl.identrust.com |
| whitelisted |
r3.o.lencr.org |
| shared |
google.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3432 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |