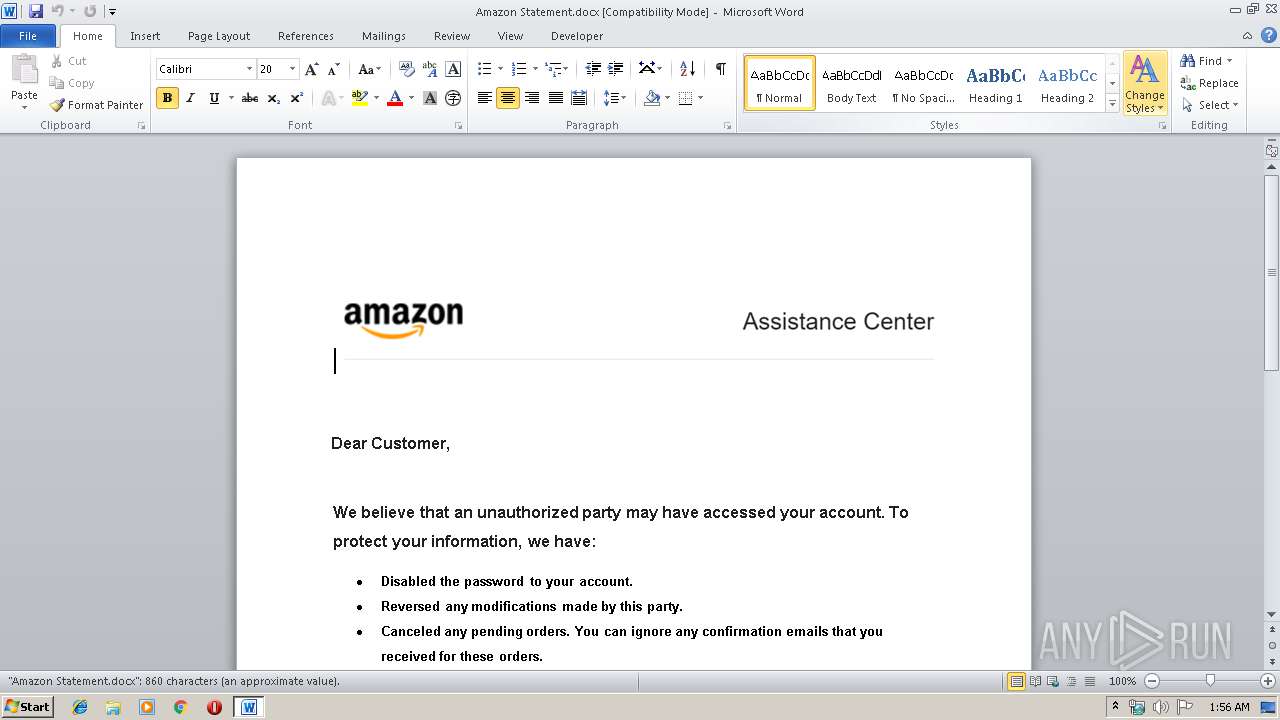
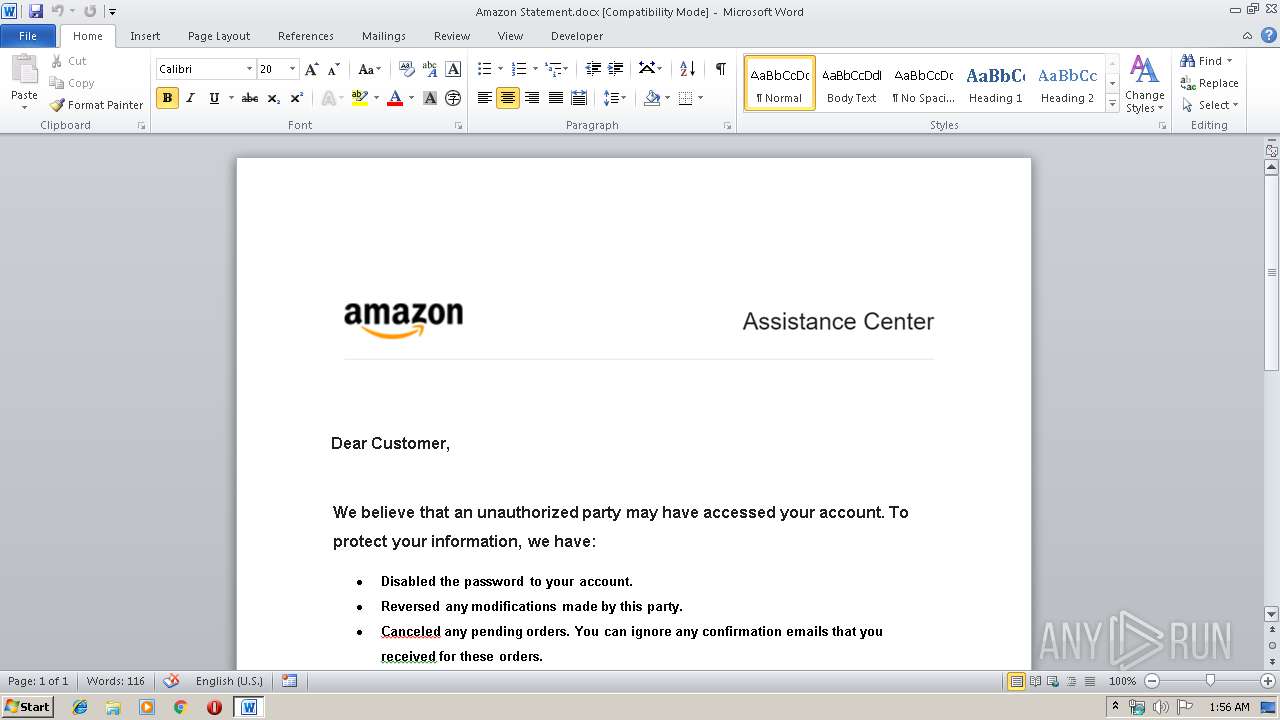
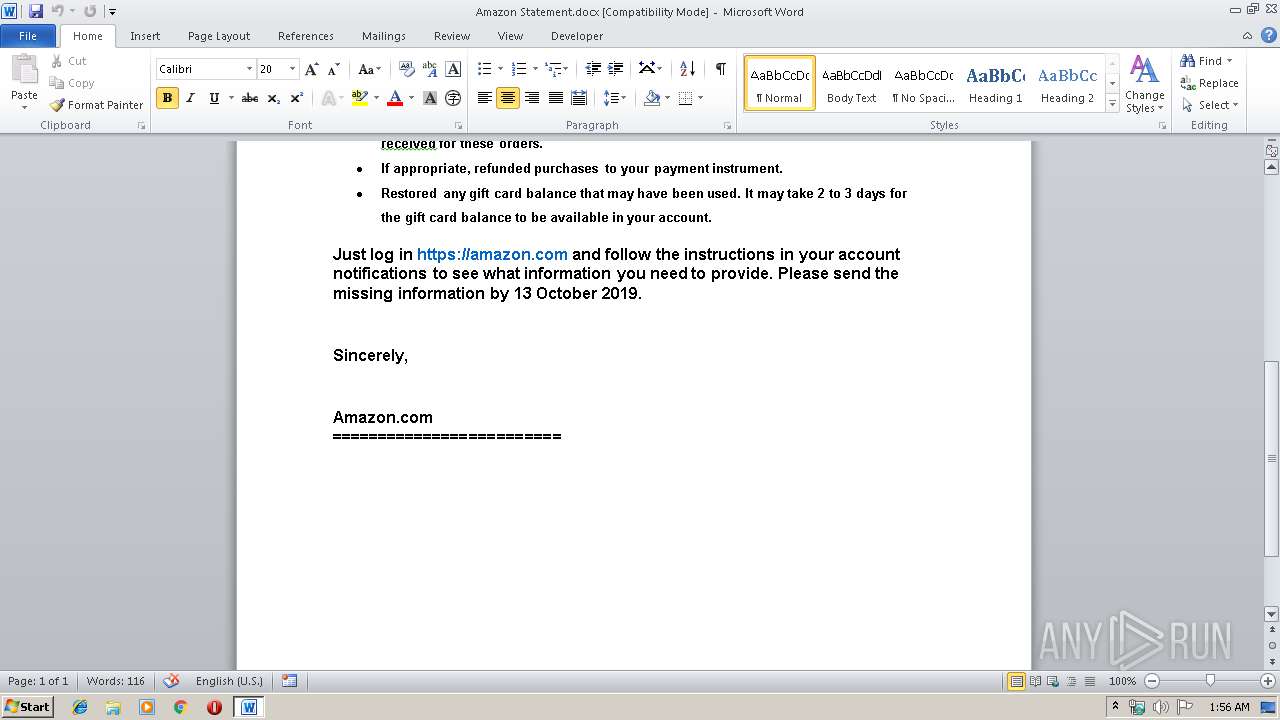
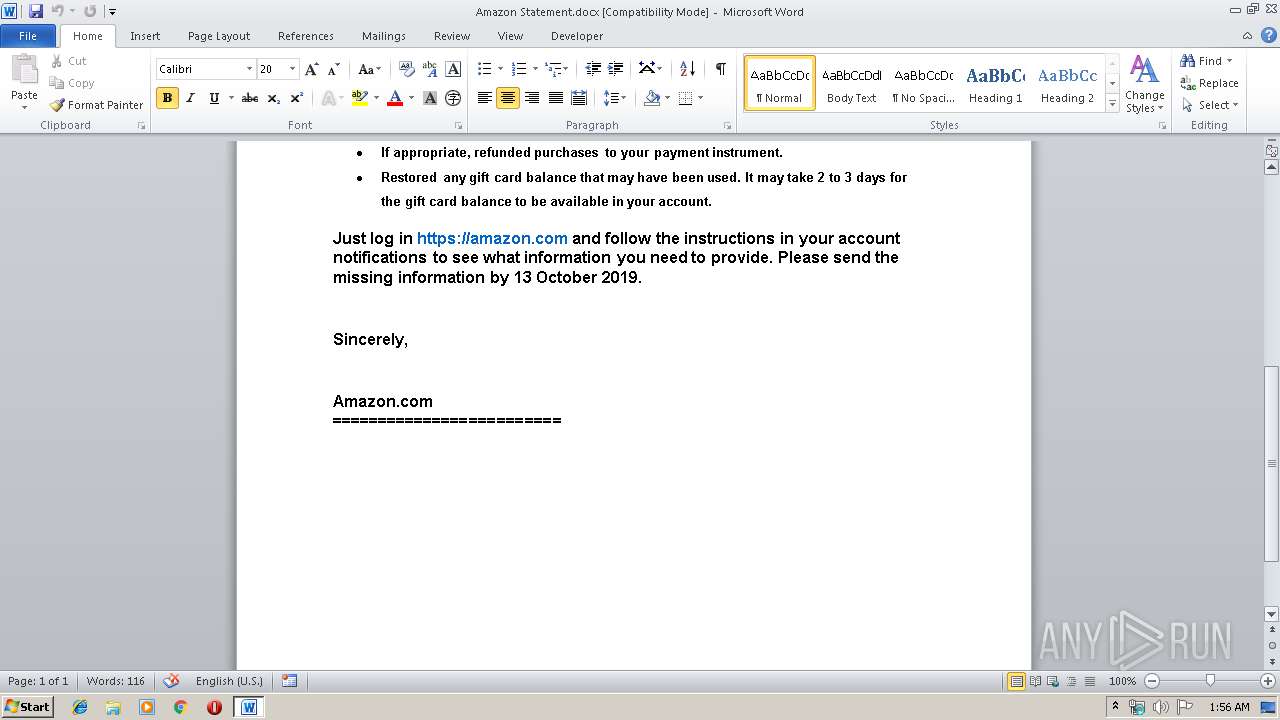
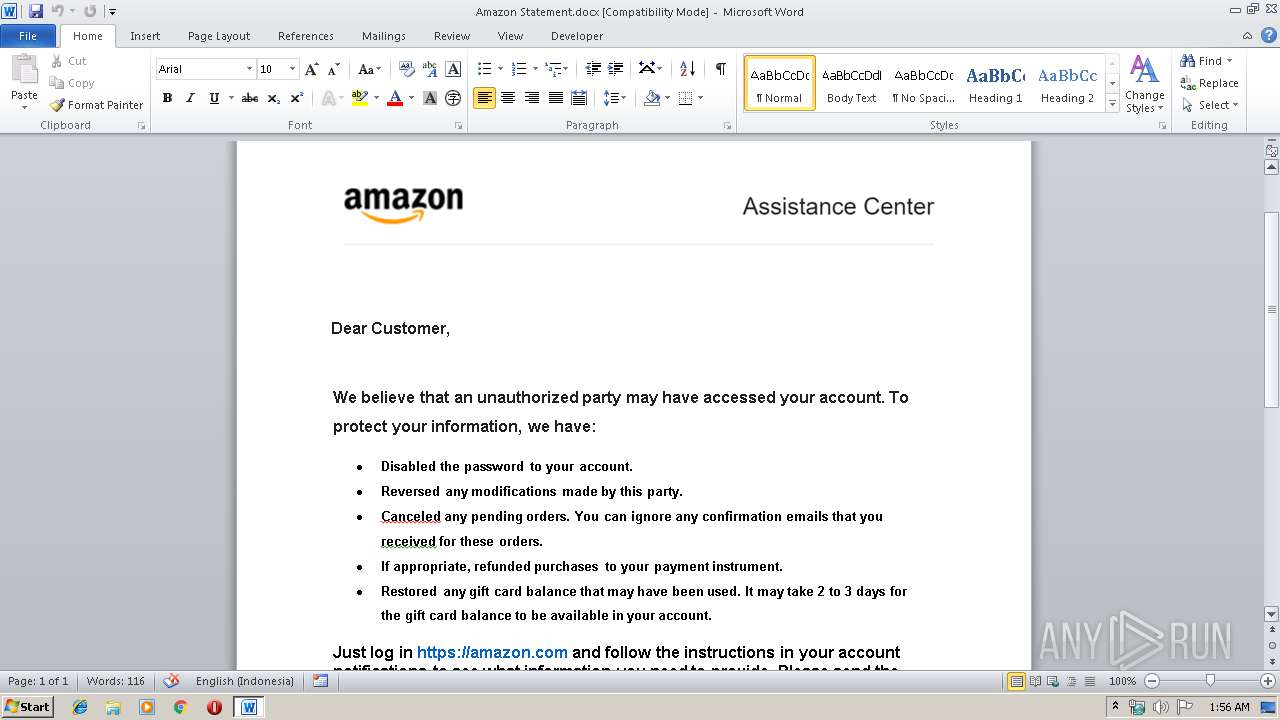
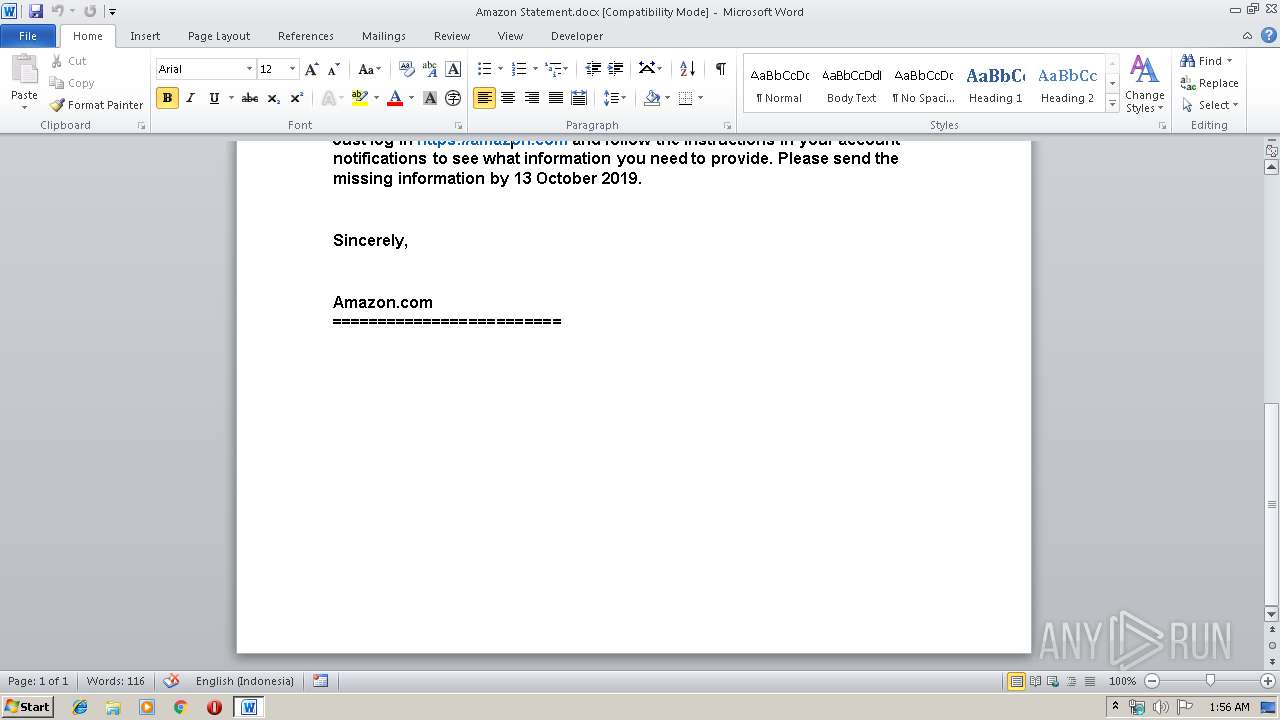
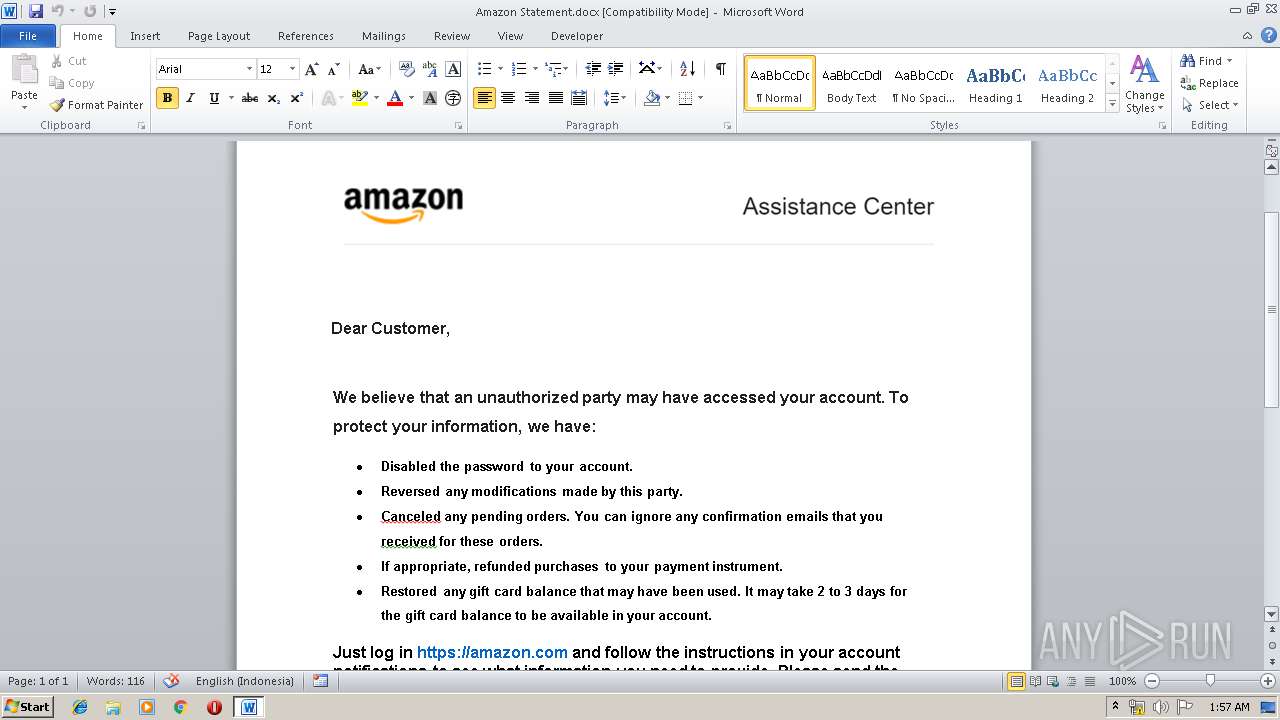
| File name: | Amazon Statement.docx |
| Full analysis: | https://app.any.run/tasks/53c854c0-934a-41b7-ac28-ba9f22611916 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2019, 00:55:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 36D9775EDCD5A5584EA2A331CF8D06EC |
| SHA1: | 3650D632D13A69747FC5D7483C9B444C29CD6609 |
| SHA256: | FBEA3549E1A0B3A0977E5DBED5C3AB8CD7D2190EF4702D3145CCF3D0F0FEEB61 |
| SSDEEP: | 1536:ynRMoLwcU9aCzhR5LjD9Gq4ULwF2Jg6a/7b:iJLCB7DTEF8pa/7b |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 992)
Creates files in the user directory
- WINWORD.EXE (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x2c4825bf |
| ZipCompressedSize: | 444 |
| ZipUncompressedSize: | 1869 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | vincent ah ah ah |
|---|
XML
| LastModifiedBy: | Azure |
|---|---|
| RevisionNumber: | 138 |
| LastPrinted: | 2019:01:27 08:09:00Z |
| CreateDate: | 2019:09:27 07:14:00Z |
| ModifyDate: | 2019:10:13 23:23:00Z |
| Template: | Account-Verify.dot |
| TotalEditTime: | 1.0 hours |
| Pages: | 1 |
| Words: | 155 |
| Characters: | 888 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 7 |
| Paragraphs: | 2 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1041 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
Total processes
35
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 992 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Amazon Statement.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 598
Read events
918
Write events
550
Delete events
130
Modification events
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 1pc |
Value: 31706300E0030000010000000000000000000000 | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (992) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA831.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msoAF27.tmp | — | |
MD5:— | SHA256:— | |||
| 992 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 992 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$azon Statement.docx | pgc | |
MD5:— | SHA256:— | |||
| 992 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN3809.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report