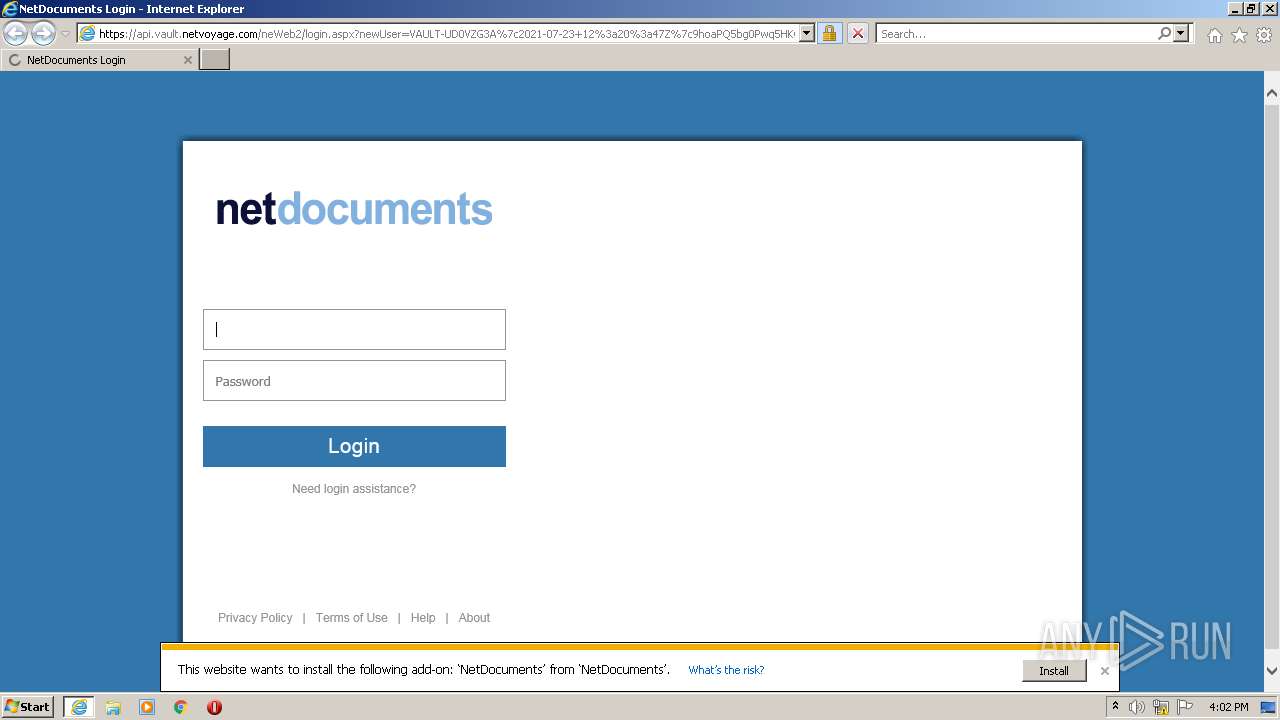
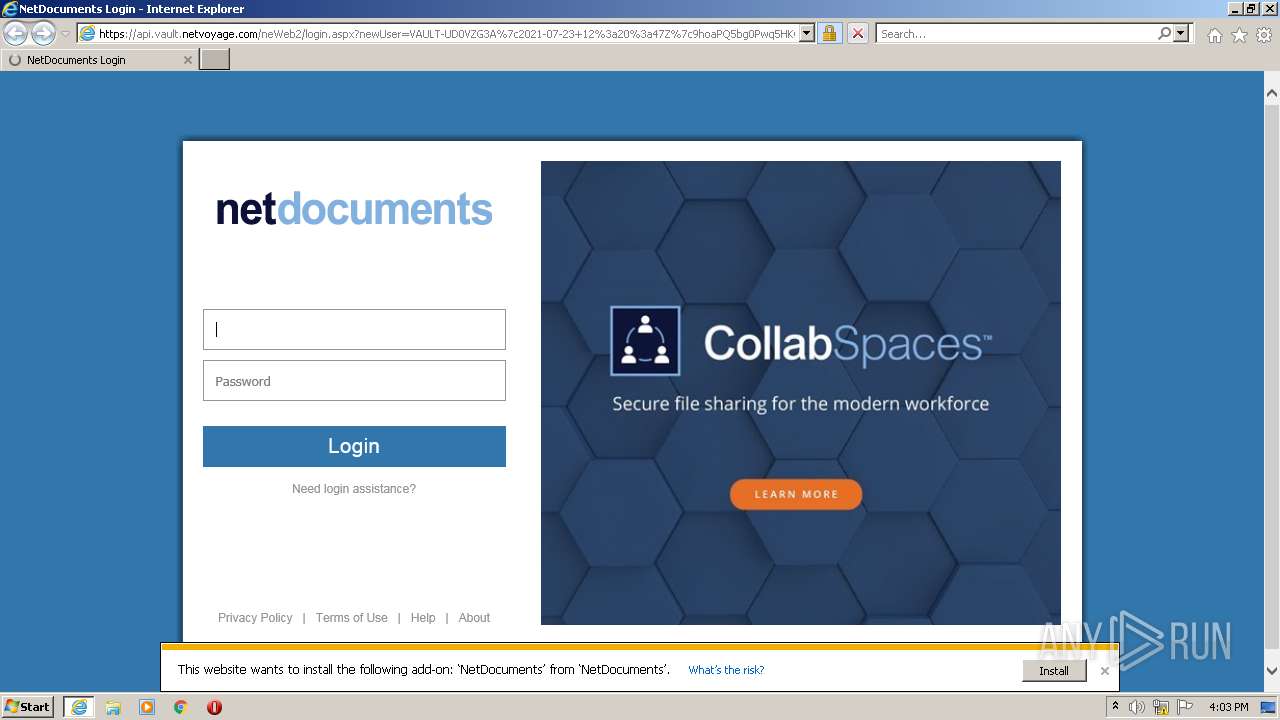
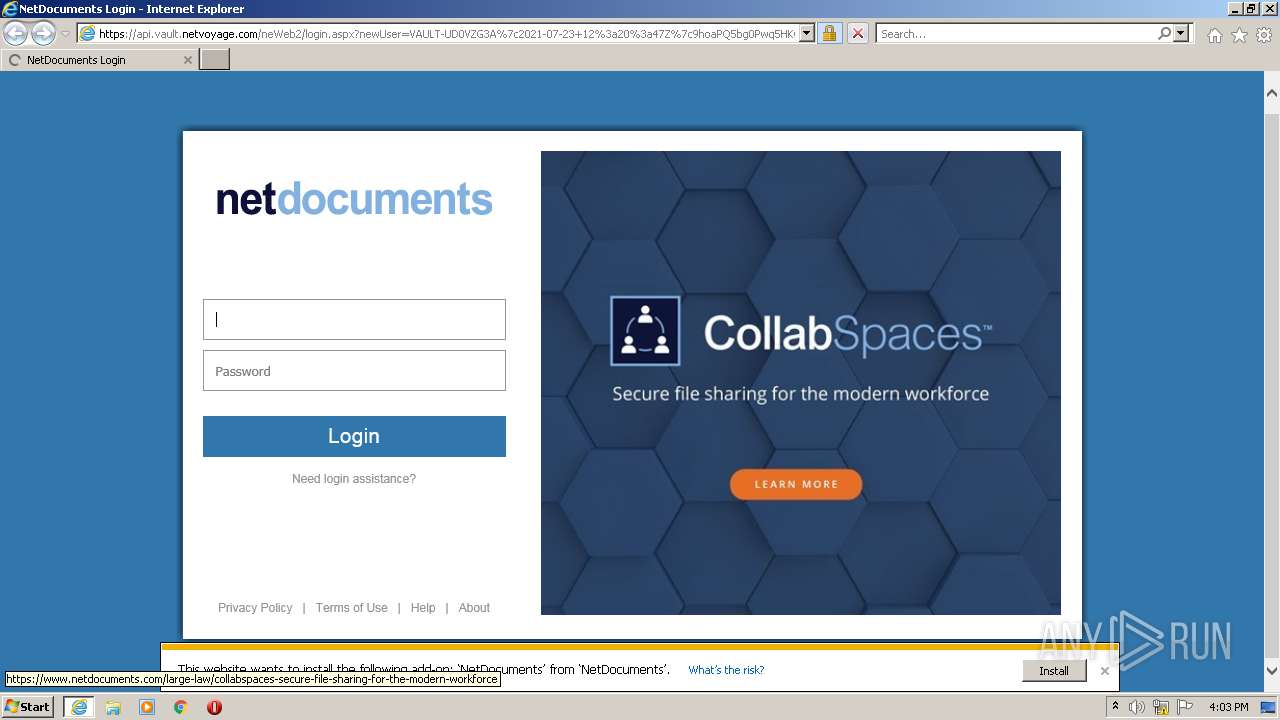
| URL: | https://api.vault.netvoyage.com/neWeb2/login.aspx?newUser=VAULT-UD0VZG3A%7c2021-07-23+12%3a20%3a47Z%7c9hoaPQ5bg0Pwq5HKG708Q4RhxD4%3d |
| Full analysis: | https://app.any.run/tasks/474e6db5-68b4-4df4-b633-f9cec734ce20 |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2021, 15:02:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0B2F0E9B2BACE0B1EBB26858993ECA7E |
| SHA1: | 0433DDF05B0C45C16BD2C614B61F12FE45BFC2D4 |
| SHA256: | FBDC09008D01C0555A57DACF2028E6A5CE13DA676F0D69B636F1A7193CA229E3 |
| SSDEEP: | 3:N8DLtJtL0TKX3LVKPnaKBy/1cANSIZ5fIWNKE+QHBSUyGn:2XhL0J5g/qAN7Z50FQhRyGn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 420)
INFO
Checks supported languages
- iexplore.exe (PID: 2540)
- iexplore.exe (PID: 420)
Reads the computer name
- iexplore.exe (PID: 2540)
- iexplore.exe (PID: 420)
Reads settings of System Certificates
- iexplore.exe (PID: 2540)
- iexplore.exe (PID: 420)
Changes internet zones settings
- iexplore.exe (PID: 2540)
Application launched itself
- iexplore.exe (PID: 2540)
Reads internet explorer settings
- iexplore.exe (PID: 420)
Checks Windows Trust Settings
- iexplore.exe (PID: 420)
- iexplore.exe (PID: 2540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2540 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2540 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://api.vault.netvoyage.com/neWeb2/login.aspx?newUser=VAULT-UD0VZG3A%7c2021-07-23+12%3a20%3a47Z%7c9hoaPQ5bg0Pwq5HKG708Q4RhxD4%3d" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 080
Read events
16 949
Write events
131
Delete events
0
Modification events
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30900179 | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30900179 | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
25
Text files
40
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2540 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2540 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\login[1].htm | html | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_9487BC0D4381A7CDEB9A8CC43F66D27C | binary | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_9487BC0D4381A7CDEB9A8CC43F66D27C | der | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\644B8874112055B5E195ECB0E8F243A4 | der | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ndCommon[1].js | text | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ndCommon[1].css | text | |
MD5:— | SHA256:— | |||
| 420 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\644B8874112055B5E195ECB0E8F243A4 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
86
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2540 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
420 | iexplore.exe | GET | 200 | 23.55.163.73:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
420 | iexplore.exe | GET | 200 | 13.32.23.104:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
420 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
420 | iexplore.exe | GET | 200 | 143.204.101.74:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2540 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
420 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
420 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEE%2BCYJEt56dwAwAAAADMWJE%3D | US | der | 471 b | whitelisted |
420 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAo1CNVcKSsBffitZcAP9%2BQ%3D | US | der | 471 b | whitelisted |
420 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
420 | iexplore.exe | 23.36.235.31:443 | api.vault.netvoyage.com | Akamai Technologies, Inc. | NL | unknown |
2540 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2540 | iexplore.exe | 67.27.157.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2540 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
420 | iexplore.exe | 67.27.157.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
420 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2540 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2540 | iexplore.exe | 67.26.139.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
420 | iexplore.exe | 52.49.198.28:443 | www.netdocuments.com | Amazon.com, Inc. | IE | malicious |
420 | iexplore.exe | 23.55.163.73:80 | crl.identrust.com | Akamai International B.V. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.vault.netvoyage.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.netdocuments.com |
| malicious |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |