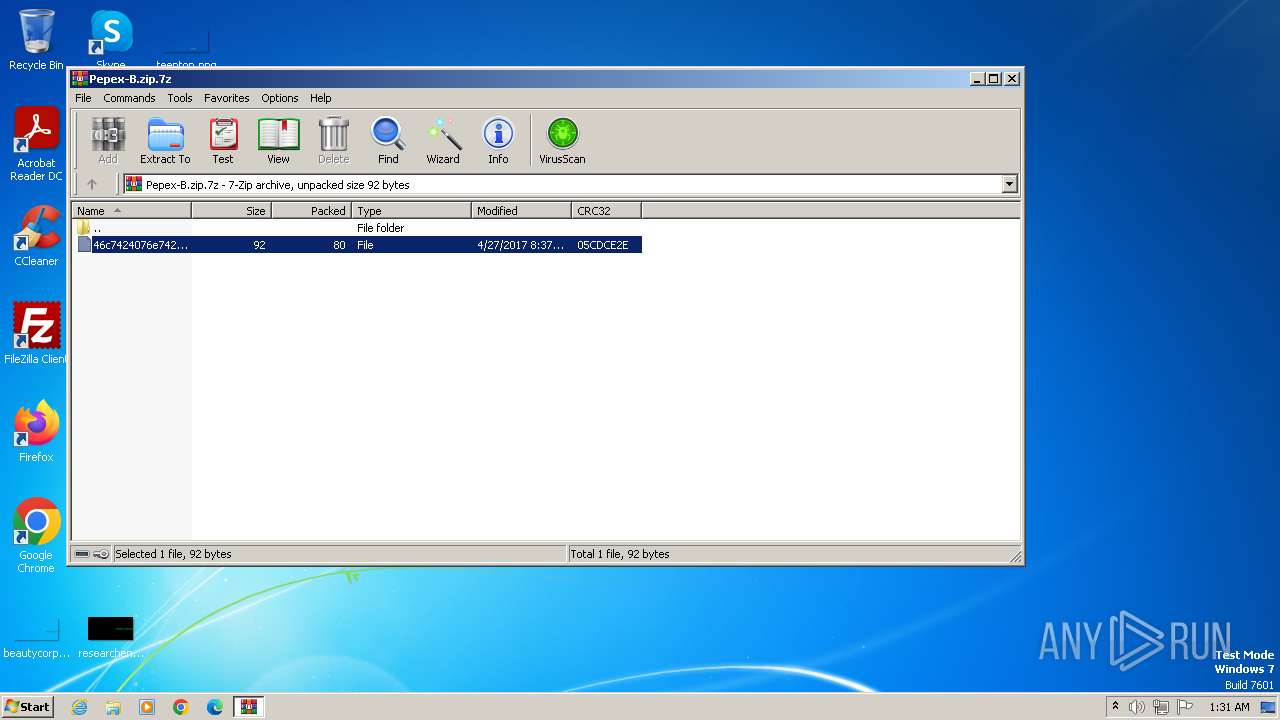
| File name: | Pepex-B.zip |
| Full analysis: | https://app.any.run/tasks/88d78e35-441d-4840-827c-c18d3c1da4c5 |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2023, 00:30:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 76C91CA2129FEE6D7E754FFF2A8E372E |
| SHA1: | FF18B163990A69A8F10B799A85EA0091B037936E |
| SHA256: | FBD46C0BA42CC0BB4EE6E5F359C0F5C2C4499E09FBB7855904C9FDBECC64E738 |
| SSDEEP: | 6:ublaazVUfF+Y8EgQNz9pdhXbDpyS6luvVFFnVtxC1:Y5zGUIf/dxD4narC1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2980)
Reads the Internet Settings
- rundll32.exe (PID: 2196)
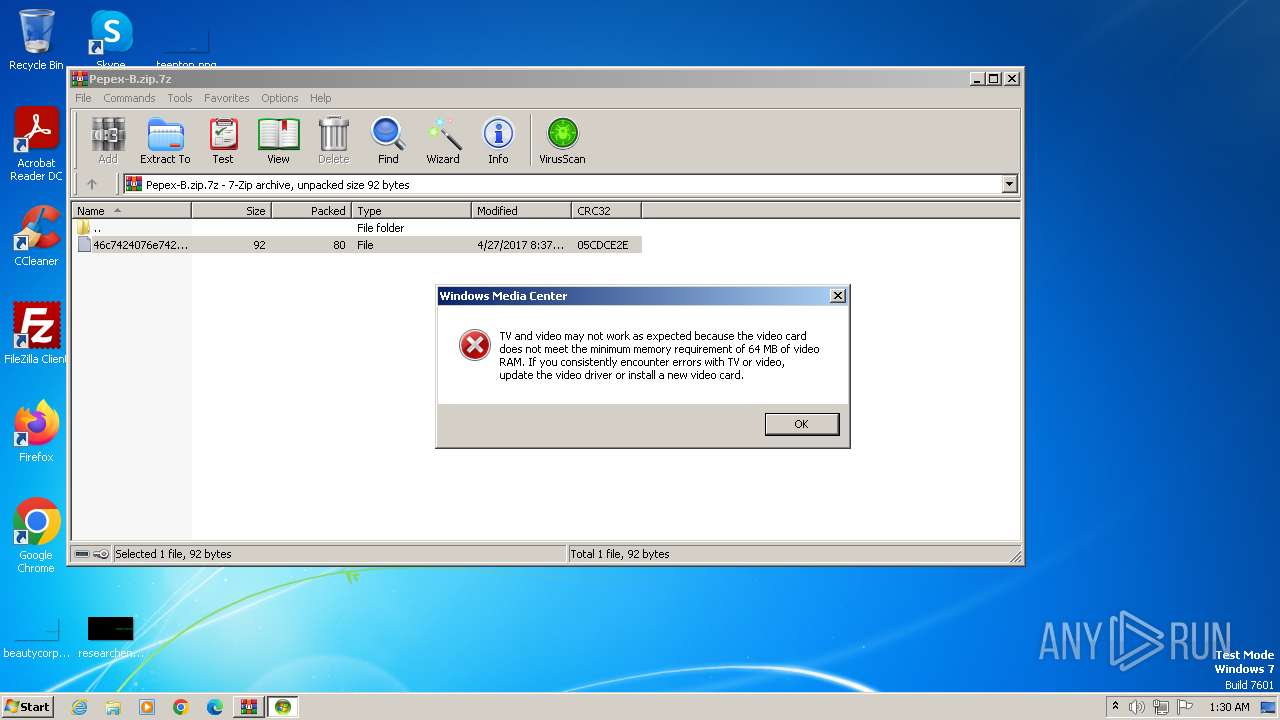
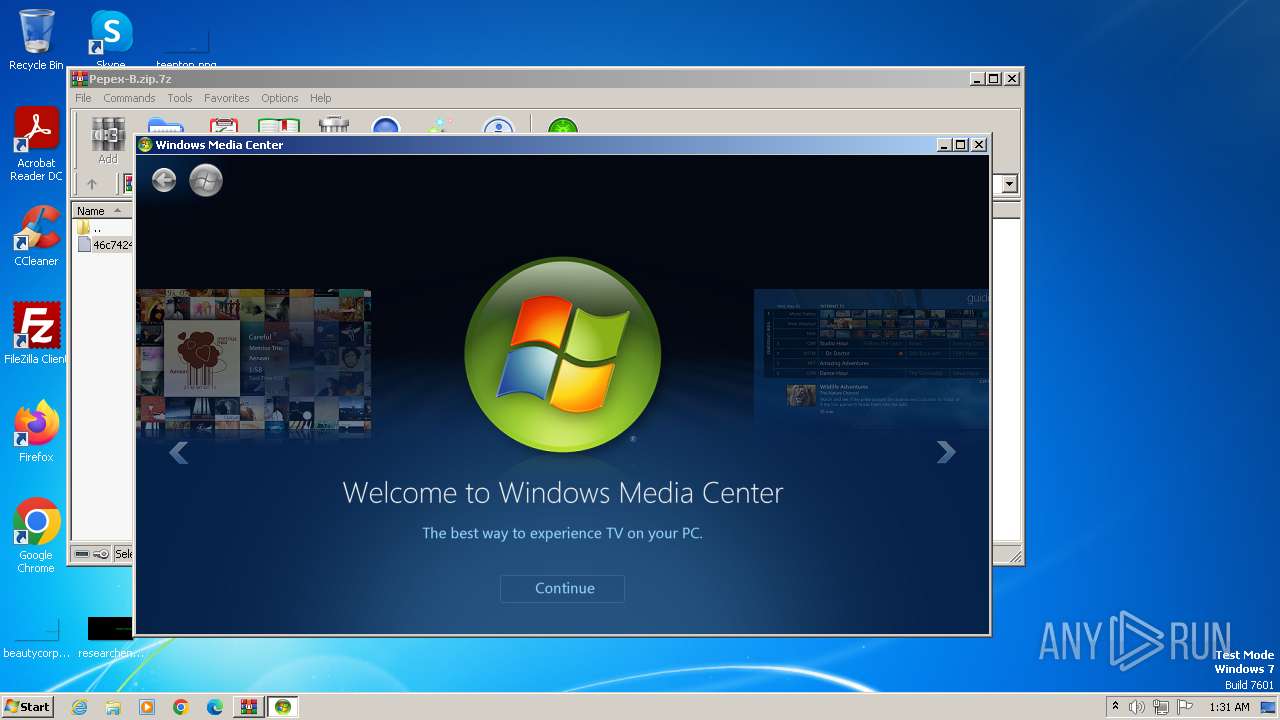
Executes as Windows Service
- ehsched.exe (PID: 1560)
INFO
Reads the computer name
- ehshell.exe (PID: 2564)
- ehsched.exe (PID: 1560)
- ehtray.exe (PID: 3536)
- ehrec.exe (PID: 2968)
Reads the machine GUID from the registry
- ehshell.exe (PID: 2564)
- ehsched.exe (PID: 1560)
- ehtray.exe (PID: 3536)
- ehrec.exe (PID: 2968)
Checks supported languages
- ehshell.exe (PID: 2564)
- ehsched.exe (PID: 1560)
- ehtray.exe (PID: 3536)
- ehrec.exe (PID: 2968)
Process checks computer location settings
- ehshell.exe (PID: 2564)
Creates files or folders in the user directory
- ehshell.exe (PID: 2564)
Creates files in the program directory
- ehshell.exe (PID: 2564)
- ehrec.exe (PID: 2968)
- ehsched.exe (PID: 1560)
Manual execution by a user
- ehtray.exe (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
41
Monitored processes
6
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | C:\Windows\ehome\ehsched.exe | C:\Windows\ehome\ehsched.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Scheduler Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2196 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb2980.2710\46c7424076e7421298191c1e439c7ed8 | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | "C:\Windows\eHome\ehshell.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2980.2710\46c7424076e7421298191c1e439c7ed8" | C:\Windows\ehome\ehshell.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2968 | C:\Windows\ehome\ehRec.exe -Embedding | C:\Windows\ehome\ehrec.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Media Center Host Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Pepex-B.zip.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3536 | "C:\Windows\eHome\EhTray.exe" /nav:-2 | C:\Windows\ehome\ehtray.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 262
Read events
6 121
Write events
141
Delete events
0
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | ehrec.exe | C:\programdata\microsoft\ehome\mcepg2-0.db | binary | |
MD5:FD186493475A7BF9F67C417F32BC0589 | SHA256:BED7F7D312B3CE7ED509680B4D1A554D2FBBDAFF6D0151AC0462795F0E560770 | |||
| 2564 | ehshell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\8f96978fc46d9f00d8780351026924d7_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:DB733E033C397FEC5917611957620271 | SHA256:1F3FFADD3B80C7F95BE06E245410768E8302A24E573868DA3C6FD91230025BDC | |||
| 3536 | ehtray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\YWKL459F55I0T1X7UNID.temp | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2980.2710\46c7424076e7421298191c1e439c7ed8 | binary | |
MD5:46C7424076E7421298191C1E439C7ED8 | SHA256:C0EE36B8EE8FA41C1C9091C510B30A2A3CE2AE1C753AF7616F89589AD115A325 | |||
| 2968 | ehrec.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-20\8f96978fc46d9f00d8780351026924d7_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:DB733E033C397FEC5917611957620271 | SHA256:1F3FFADD3B80C7F95BE06E245410768E8302A24E573868DA3C6FD91230025BDC | |||
| 2564 | ehshell.exe | C:\ProgramData\Microsoft\eHome\Logs\FirstRun.log | xml | |
MD5:37E130BFFD244CE7DB392E18FD0D7D44 | SHA256:73B4DE534458370ADF82DE388952AAB737F6AE641A279EF4BF9216099B0C14D4 | |||
| 3536 | ehtray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b91050d8b077a4e8.customDestinations-ms~RF1f4465.TMP | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 3536 | ehtray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b91050d8b077a4e8.customDestinations-ms | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
| 3536 | ehtray.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\MY165NKII4HVGV5AR0GG.temp | binary | |
MD5:B9BD716DE6739E51C620F2086F9C31E4 | SHA256:7116FF028244A01F3D17F1D3BC2E1506BC9999C2E40E388458F0CCCC4E117312 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
ehshell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|