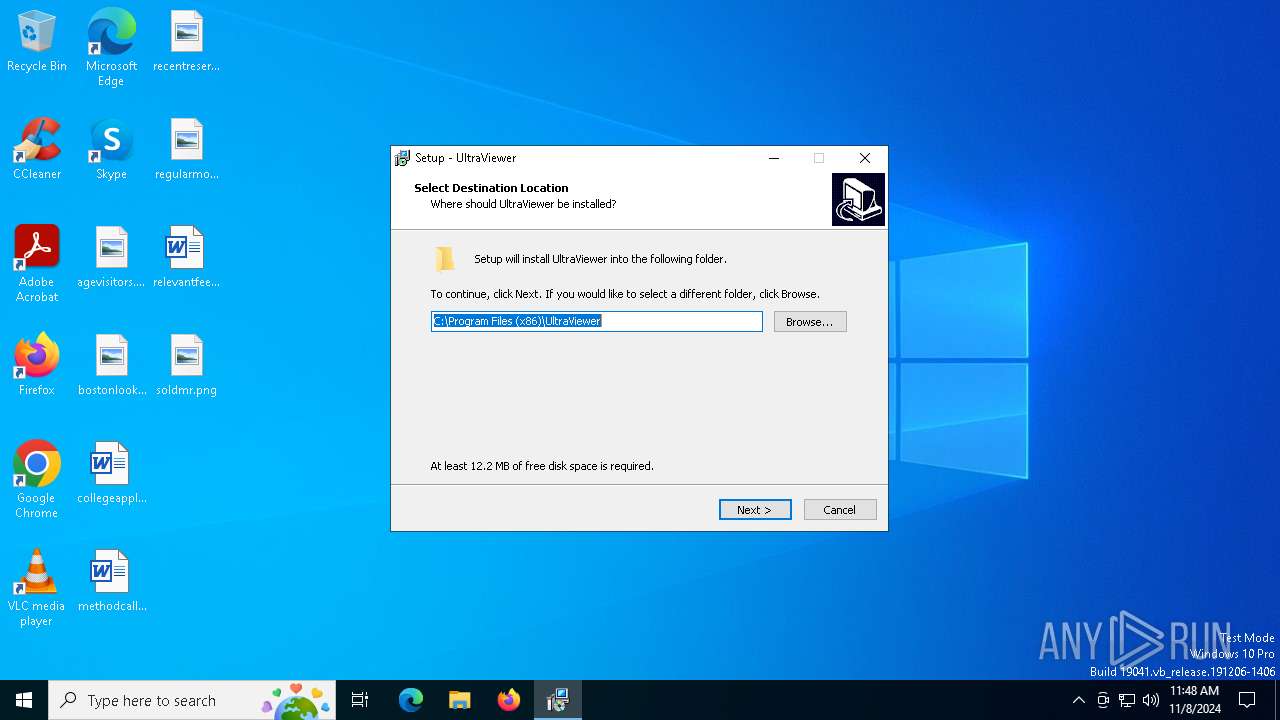
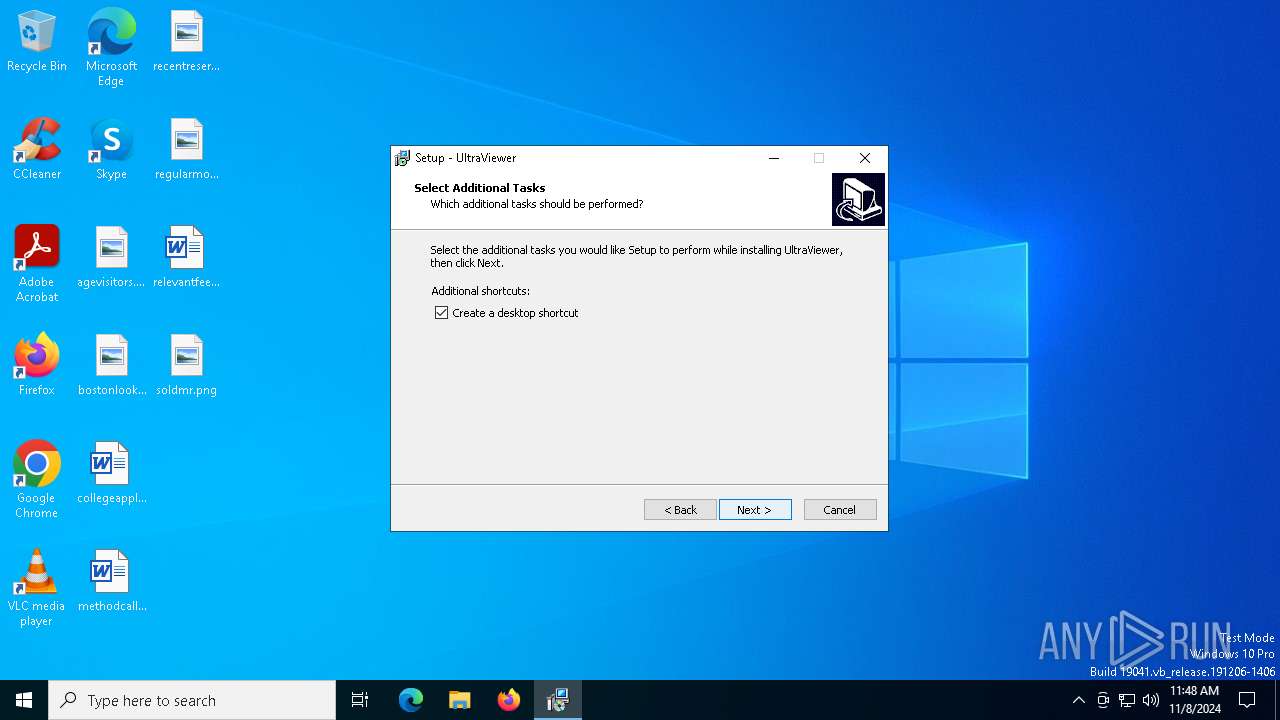
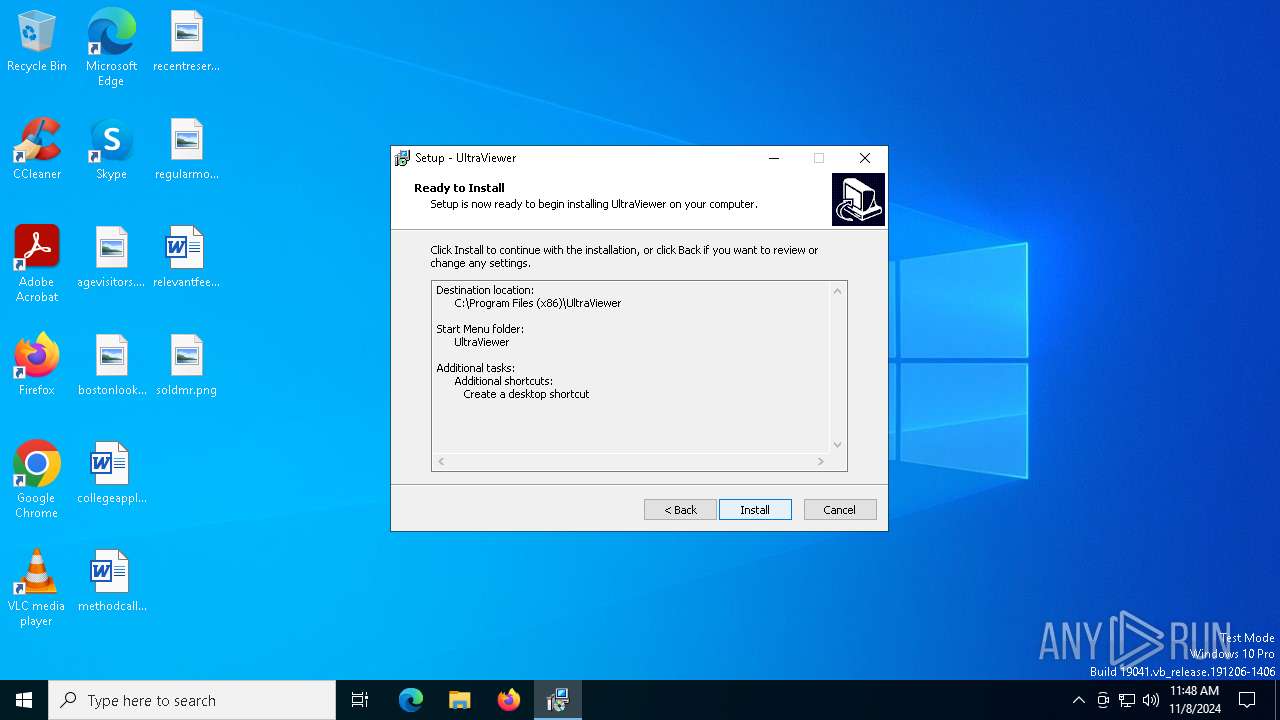
| File name: | UltraViewer_setup_6.6.108_en.exe |
| Full analysis: | https://app.any.run/tasks/a25e2d81-63f8-47fd-92c3-f4b002c91bd3 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2024, 11:48:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | CD546A1249E93CE0BC7DF42FD06B3C68 |
| SHA1: | 9ADB885F54107908413787D29DC8A3C04B2D19F5 |
| SHA256: | FBCCA6EE7A05063C2E7816F771B0CE370BC498620E2A8209CE2C0A50EE177313 |
| SSDEEP: | 98304:8g+AtDi7PImpRp7TCCI/Skb5FQTXN2MY0bqOsTiWgrKeCtobg2xrHJl/iFcGapa5:E7HSqE |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 528)
- net.exe (PID: 6664)
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
SUSPICIOUS
Executable content was dropped or overwritten
- UltraViewer_setup_6.6.108_en.exe (PID: 6568)
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
- UltraViewer_setup_6.6.108_en.exe (PID: 5084)
Reads security settings of Internet Explorer
- UltraViewer_setup_6.6.108_en.tmp (PID: 5748)
Process drops legitimate windows executable
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
Executes as Windows Service
- UltraViewer_Service.exe (PID: 7088)
Uses TASKKILL.EXE to kill process
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
INFO
Create files in a temporary directory
- UltraViewer_setup_6.6.108_en.exe (PID: 6568)
Checks supported languages
- UltraViewer_setup_6.6.108_en.exe (PID: 6568)
- UltraViewer_setup_6.6.108_en.tmp (PID: 5748)
Reads the computer name
- UltraViewer_setup_6.6.108_en.tmp (PID: 5748)
Process checks computer location settings
- UltraViewer_setup_6.6.108_en.tmp (PID: 5748)
UPX packer has been detected
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
Confuser has been detected (YARA)
- UltraViewer_setup_6.6.108_en.tmp (PID: 1576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:06 14:39:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 53760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117dc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | DucFabulous |
| FileDescription: | UltraViewer Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | UltraViewer |
| ProductVersion: | 6.6.108 |
Total processes
563
Monitored processes
429
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "net" stop UltraViewService | C:\Windows\SysWOW64\net.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 528 | "taskkill.exe" /f /im "UltraViewer_Desktop.exe" | C:\Windows\SysWOW64\taskkill.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "taskkill.exe" /f /im "UltraViewer_Desktop.exe" | C:\Windows\SysWOW64\taskkill.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "taskkill.exe" /f /im "UltraViewer_Desktop.exe" | C:\Windows\SysWOW64\taskkill.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | "taskkill.exe" /f /im "UltraViewer_Desktop.exe" | C:\Windows\SysWOW64\taskkill.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | "taskkill.exe" /f /im "UltraViewer_Desktop.exe" | C:\Windows\SysWOW64\taskkill.exe | — | UltraViewer_setup_6.6.108_en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 045
Read events
22 590
Write events
1 455
Delete events
0
Modification events
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32 |
| Operation: | write | Name: | Class |
Value: RemoteControl.ComRegistrationException | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32 |
| Operation: | write | Name: | Assembly |
Value: RemoteControl, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32 |
| Operation: | write | Name: | RuntimeVersion |
Value: v4.0.30319 | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | Class |
Value: RemoteControl.ComRegistrationException | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | Assembly |
Value: RemoteControl, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1CA5DE22-F295-3F03-8D69-018007836F60}\InprocServer32\1.0.0.0 |
| Operation: | write | Name: | RuntimeVersion |
Value: v4.0.30319 | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Component Categories\{62C8FE65-4EBB-45E7-B440-6E39B2CDBF29} |
| Operation: | write | Name: | 0 |
Value: .NET Category | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{315D07B8-9F8F-3885-AB17-1C3D460CEE4E}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6736) RegAsm.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{315D07B8-9F8F-3885-AB17-1C3D460CEE4E}\InprocServer32 |
| Operation: | write | Name: | Class |
Value: RemoteControl.ExtendTreeView | |||
Executable files
39
Suspicious files
20
Text files
168
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\is-BLL8Q.tmp | binary | |
MD5:7112E8CE3E408DCE8CCB4E7D4CE48FFE | SHA256:9AA45789D9FF9D329A623A685D57B67E33C777019DE9CE1F273F21860E4BFE6B | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Users\admin\AppData\Local\Temp\is-013KM.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Users\admin\AppData\Local\Temp\is-013KM.tmp\UVUninstallHelper.exe.config | text | |
MD5:679ACA3E8125584E8704B2DFDFA20A0B | SHA256:470CE4147BFF777EBEFC7CCC9E2D1BC5DF203B727134FC90B0134BF3CDC7ADD4 | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\CloseRDP.bat | text | |
MD5:AB6894E112614829CDDB91290EB8A045 | SHA256:C46517EE870DAD84C8D778AC1F39CC96394BAF4DB59535F4D64C5B070C7F751E | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Users\admin\AppData\Local\Temp\is-013KM.tmp\UVUninstallHelper.exe | executable | |
MD5:ECECB301656F5F8C6A46A8ABF8D928FE | SHA256:801BBE7A174CA09BB029AEDF54C3073D96C033FA01DCD68F4240983D2AD7CB6B | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Users\admin\AppData\Local\Temp\is-013KM.tmp\isxdl.dll | executable | |
MD5:48AD1A1C893CE7BF456277A0A085ED01 | SHA256:B0CC4697B2FD1B4163FDDCA2050FC62A9E7D221864F1BD11E739144C90B685B3 | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\8bit.dat | binary | |
MD5:7112E8CE3E408DCE8CCB4E7D4CE48FFE | SHA256:9AA45789D9FF9D329A623A685D57B67E33C777019DE9CE1F273F21860E4BFE6B | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\HtmlAgilityPack.dll | executable | |
MD5:00DC215CEE6BE49802295AD6802DA661 | SHA256:78750E7BD53ED088D8365FC2E69B74883A813B0EA0D461873AD61FD8059DBD31 | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\is-UE6IA.tmp | text | |
MD5:AB6894E112614829CDDB91290EB8A045 | SHA256:C46517EE870DAD84C8D778AC1F39CC96394BAF4DB59535F4D64C5B070C7F751E | |||
| 1576 | UltraViewer_setup_6.6.108_en.tmp | C:\Program Files (x86)\UltraViewer\is-88KSS.tmp | text | |
MD5:5E28EF7C6FB2D23E9DF42B3355BDCEB7 | SHA256:F899D1C4F1B55BDFA9F4237CFC593BF8AEDE52AF4D5EB3CC2AAEF8B77CF5C519 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
45
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB2iSDBvmyYY0ILgln0z02o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQ5suEceKjAJbxseAmHFkQ9FrhTWQQUDuE6qFM6MdWKvsG7rWcaA4WtNA4CEQD%2FsTvXwnyKgewdOVs7Xv3z | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |