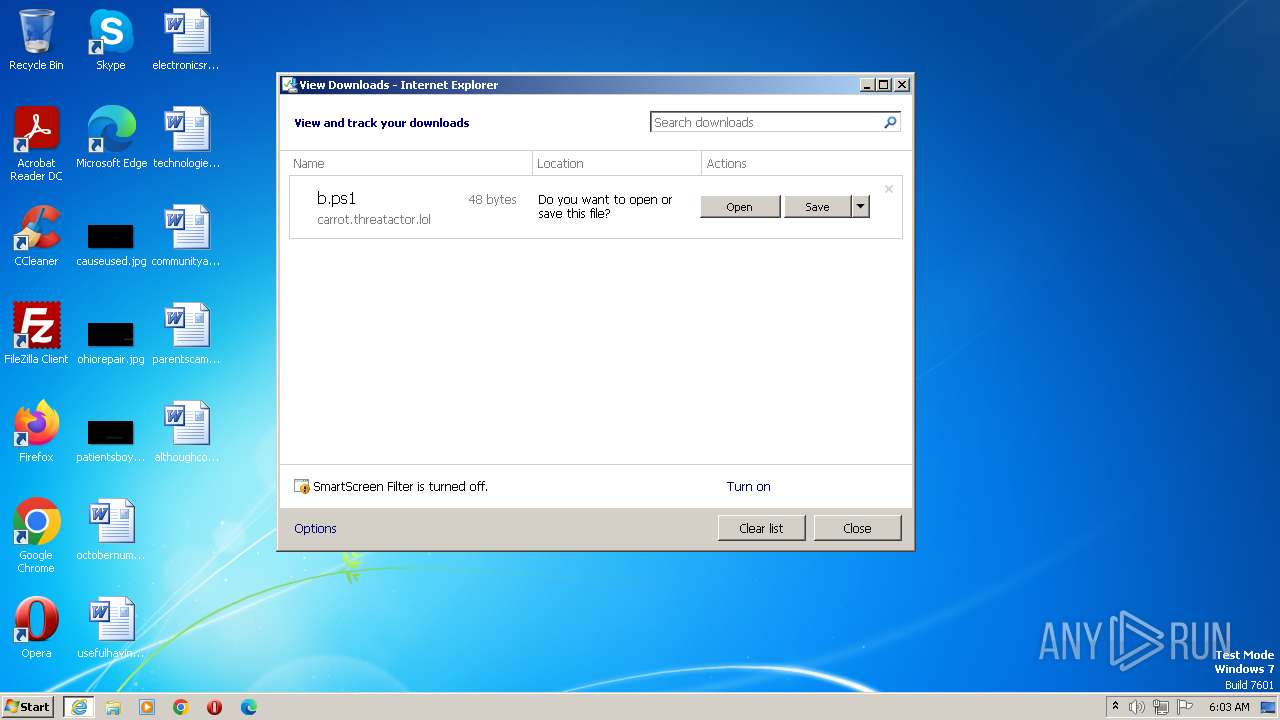
| URL: | http://carrot.threatactor.lol/b.ps1 |
| Full analysis: | https://app.any.run/tasks/0c7258bf-8f4b-4cf7-bc50-aa25a809f525 |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2023, 05:02:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7FF154709DFE9D9166729CD7B38E97C2 |
| SHA1: | 7469F2117FF7697986D97D1C6B00693A872E27FA |
| SHA256: | FBB27319F7839CD4652EB17A1D8CD1EC263F3AA4789F365D4FEEB58606C0F9C2 |
| SSDEEP: | 3:N1KdEHsRvRK7LVT:CGQvsd |
MALICIOUS
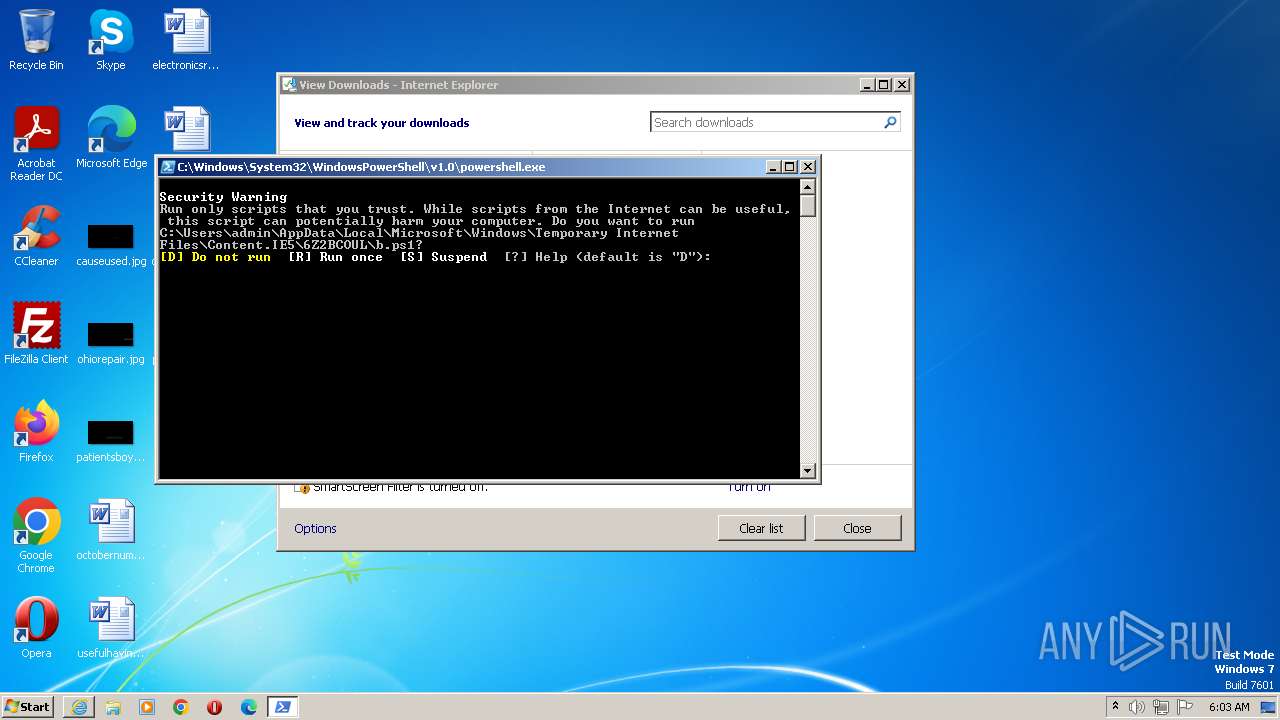
Starts POWERSHELL.EXE for commands execution
- iexplore.exe (PID: 3488)
SUSPICIOUS
Powershell version downgrade attack
- powershell.exe (PID: 848)
The process executes Powershell scripts
- iexplore.exe (PID: 3488)
Reads the Internet Settings
- powershell.exe (PID: 848)
INFO
Application launched itself
- iexplore.exe (PID: 3488)
The process uses the downloaded file
- powershell.exe (PID: 848)
- iexplore.exe (PID: 3488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\b.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3488 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://carrot.threatactor.lol/b.ps1" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 032
Read events
10 915
Write events
117
Delete events
0
Modification events
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3488) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
10
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\b.ps1.gj6z39j.partial | text | |
MD5:E4A7EBACB00BC67B48BDE853E544427F | SHA256:4FC52EB578CF6691316CB0DEEA4D6DFCD383EFF238442538690357CDCFA49751 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\b[1].ps1 | text | |
MD5:E4A7EBACB00BC67B48BDE853E544427F | SHA256:4FC52EB578CF6691316CB0DEEA4D6DFCD383EFF238442538690357CDCFA49751 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:AF0B86F7346D7B3D6AB7AD813A89FE29 | SHA256:522095B5697037AA6FABCC8C539D40EF187C1D4CA278228A04330D783B43FBDA | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2EB9DA2A1E48BEA22740CE5F37233A55 | SHA256:E883FE18229D746F0F78FCC10C5038DFBCAF1CCB59D2D7956068AB75F5846D22 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver5AF.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF505F1F1DD2561981.TMP | binary | |
MD5:A9D2B8424BBBBE421E9B4C3AC104B0A3 | SHA256:F6A963AD9E84FE0C02548C161388D13ECCA9ED5F8D8C33760D59D72055DC4E83 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:9397CB722DAF81E15B1AF946D5D1DAC2 | SHA256:8C6F80D8DA1EC337D7649C174EEF10DACF9E9851267610611E4C0BE6C8D0DA3F | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\b.ps1.gj6z39j.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 67.27.233.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?06b6ce6dc4ac69a5 | US | compressed | 4.70 Kb | whitelisted |
2372 | iexplore.exe | GET | 200 | 52.217.10.216:80 | http://carrot.threatactor.lol/b.ps1 | US | text | 48 b | suspicious |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | binary | 471 b | whitelisted |
— | — | GET | 200 | 67.27.158.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0793fa8ddfdb5d3d | US | compressed | 4.70 Kb | whitelisted |
— | — | GET | 200 | 67.27.233.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f2b60cf70a7af09c | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3488 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
2372 | iexplore.exe | 52.217.10.216:80 | carrot.threatactor.lol | AMAZON-02 | US | suspicious |
— | — | 67.27.233.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
— | — | 67.27.158.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | malicious |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1088 | svchost.exe | 67.27.233.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
carrot.threatactor.lol |
| suspicious |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2372 | iexplore.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
1 ETPRO signatures available at the full report