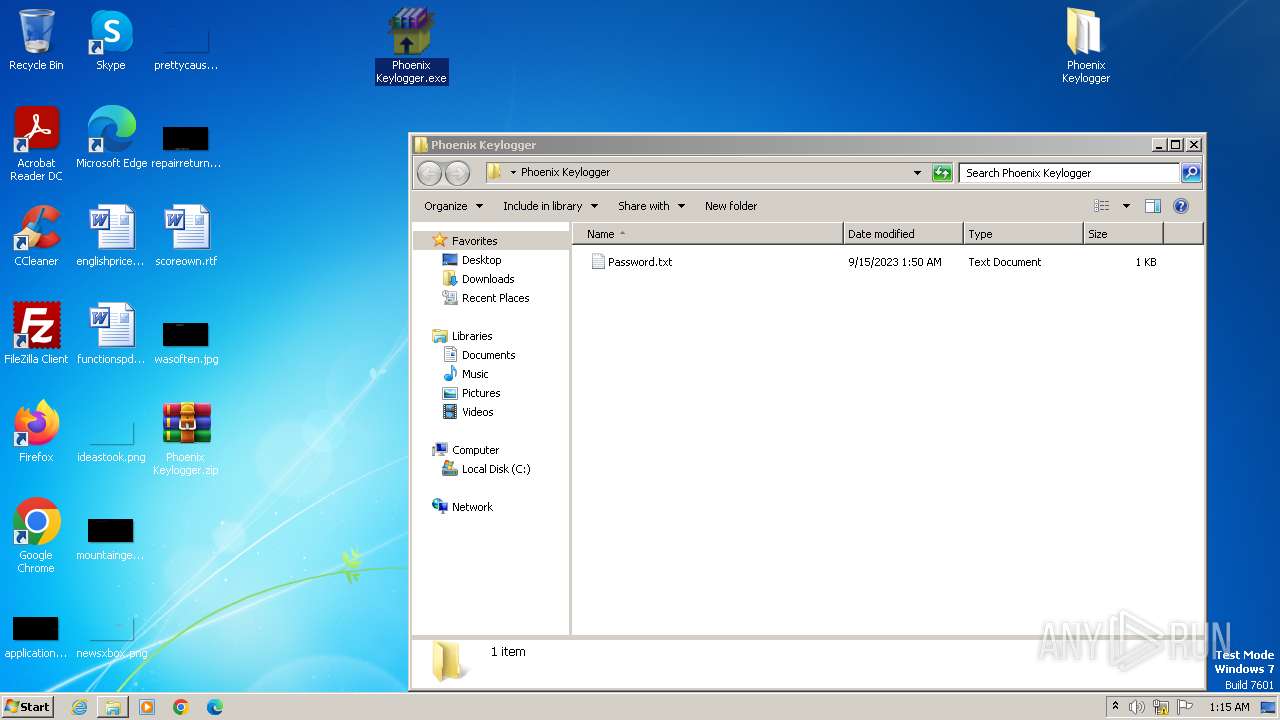
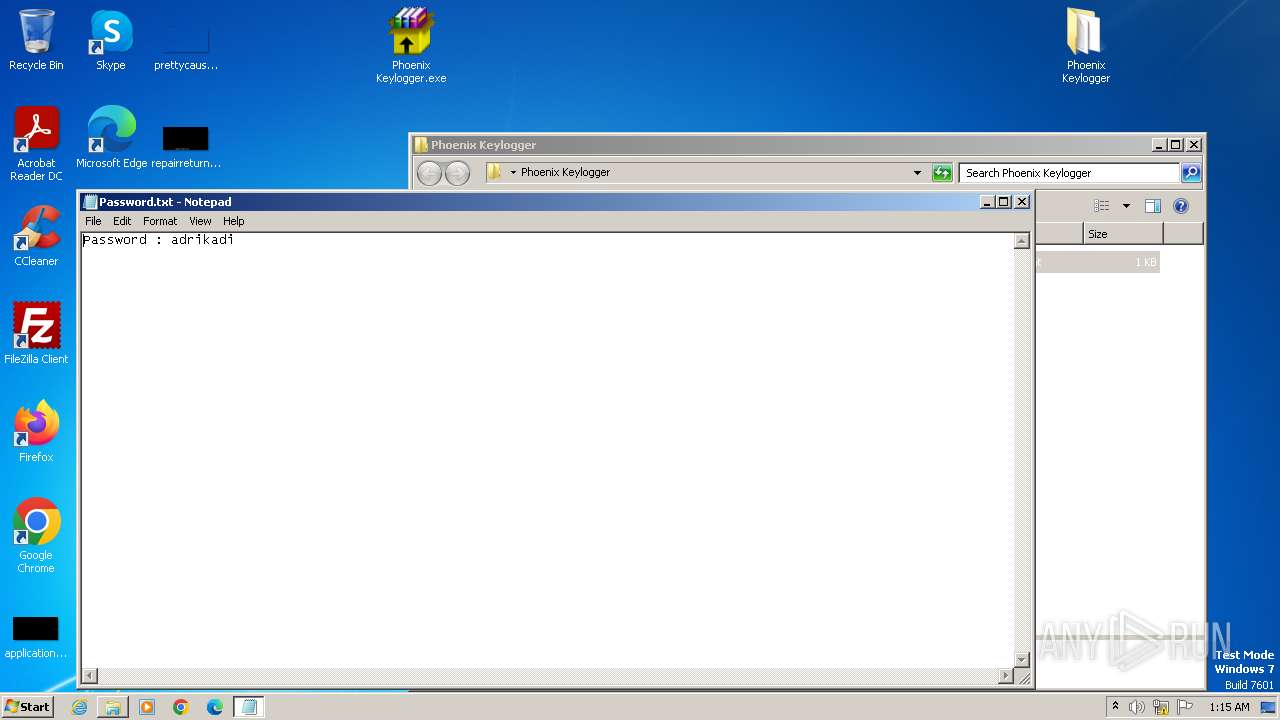
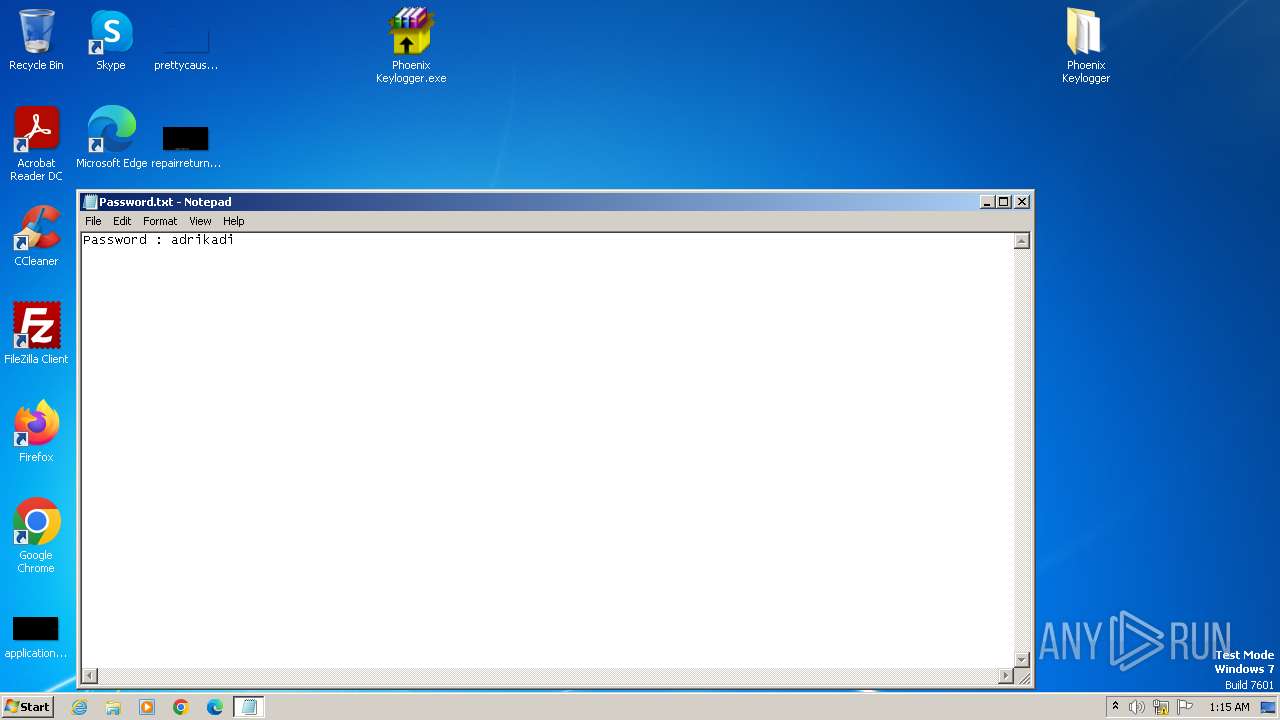
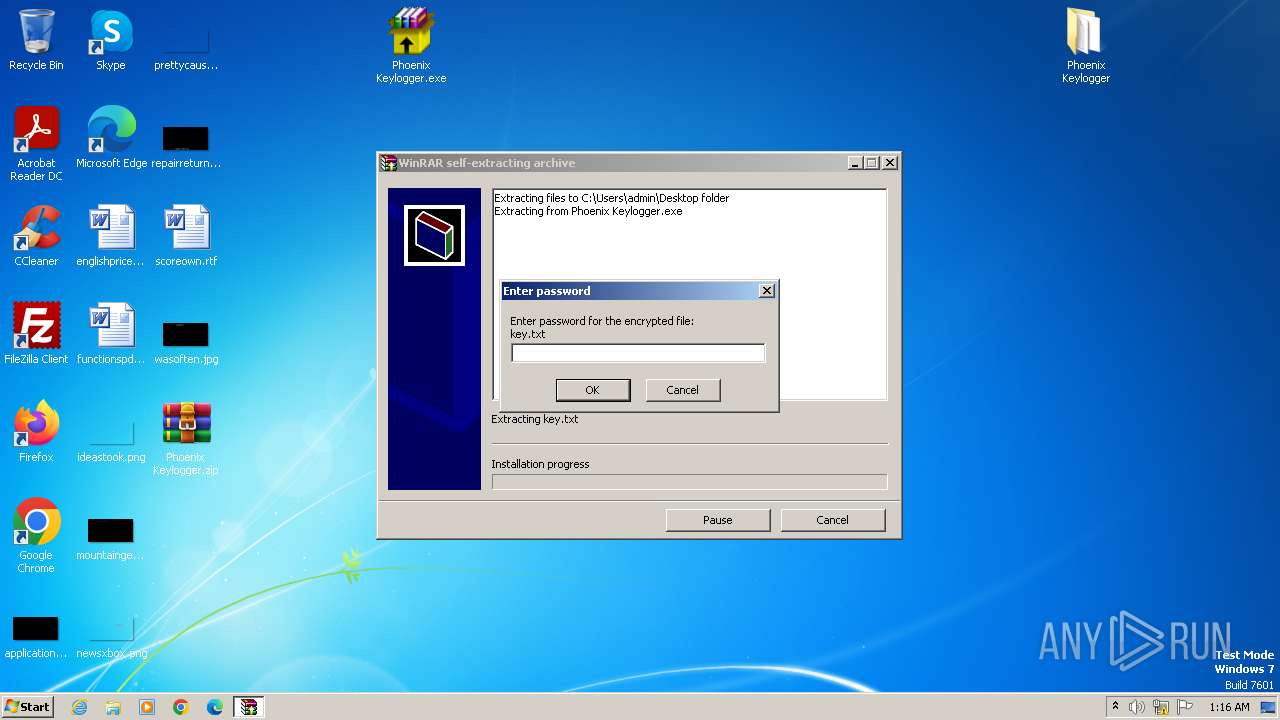
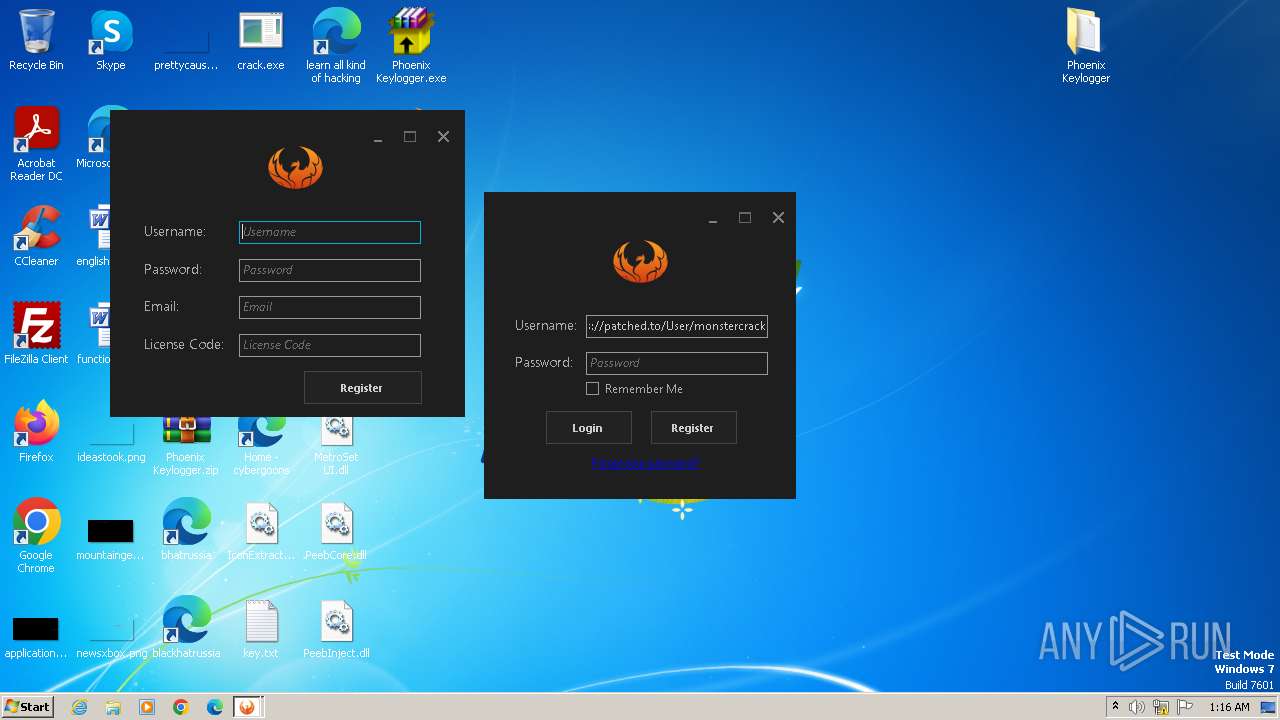
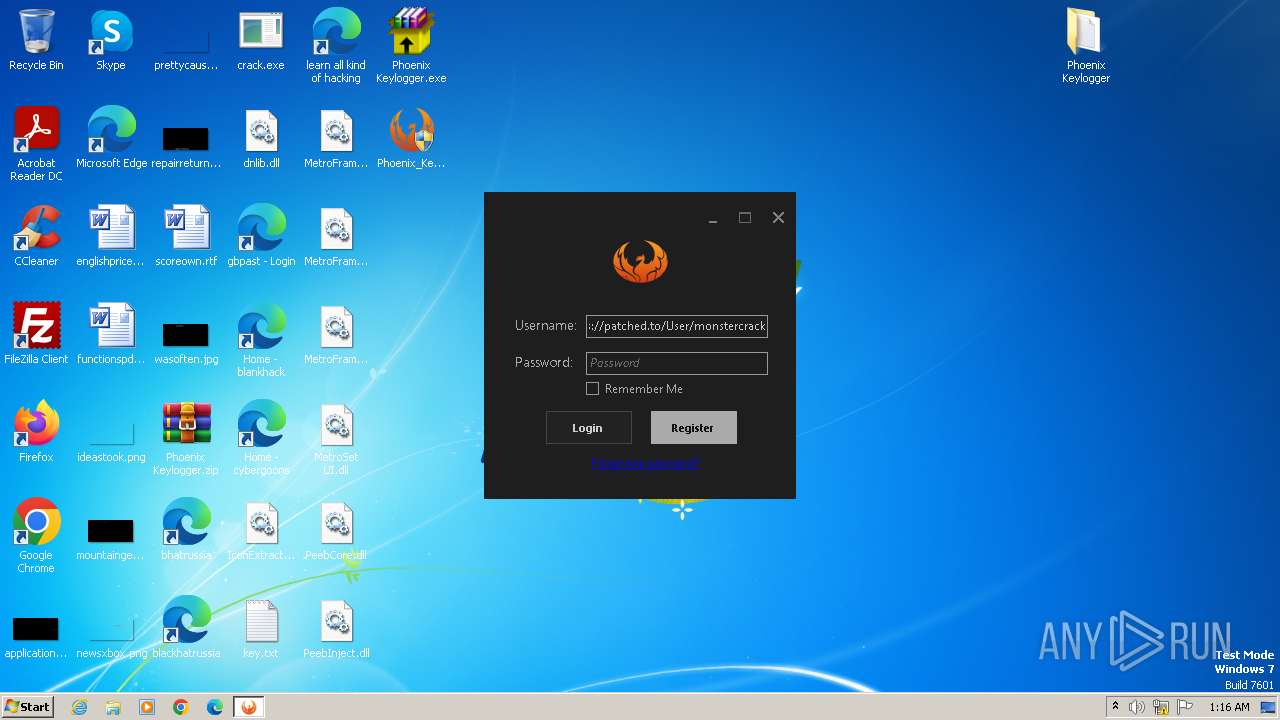
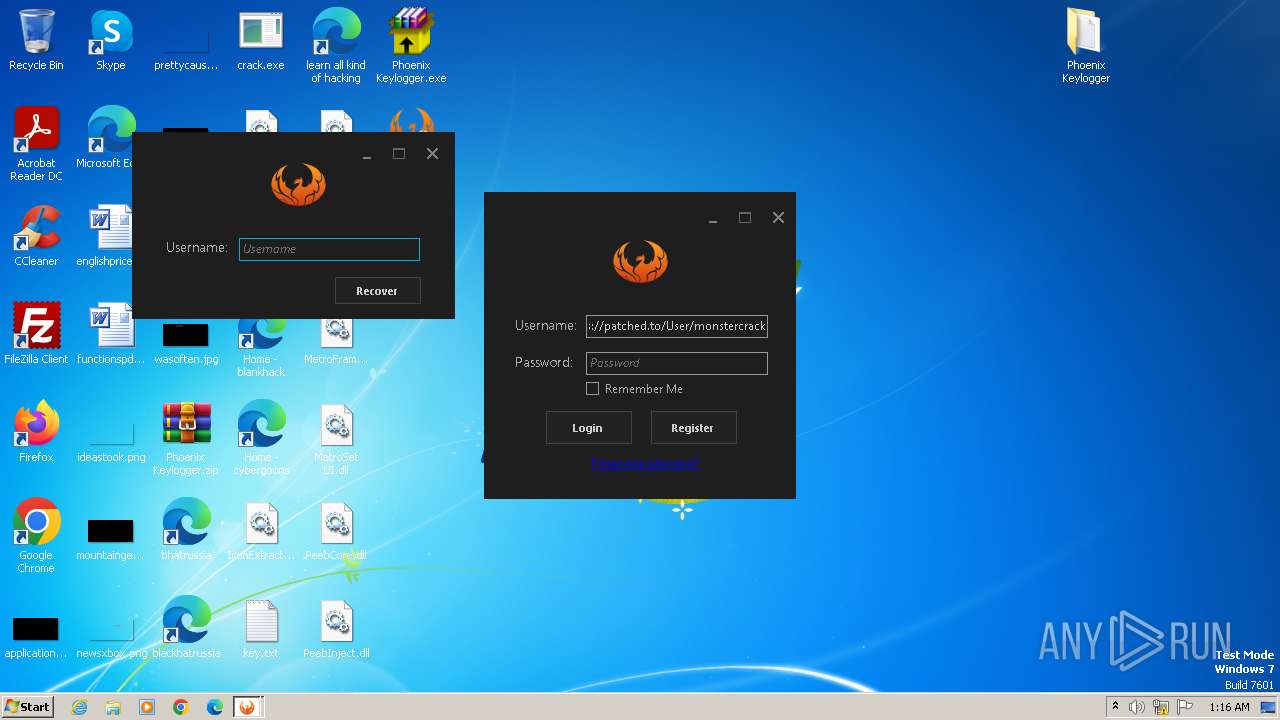
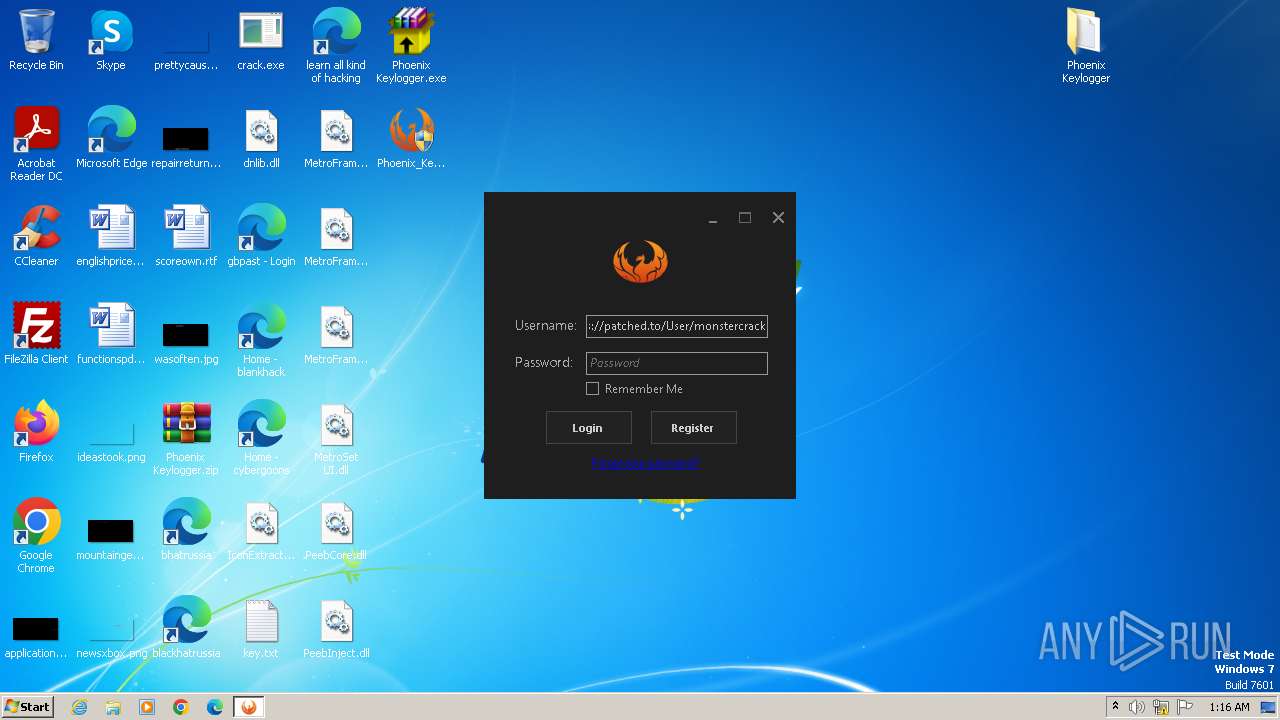
| File name: | Phoenix Keylogger.zip |
| Full analysis: | https://app.any.run/tasks/a3b1bda4-2ced-4a90-82c5-29b0f82151db |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 01:15:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 47089A706EF8E29EE77CC8B83795ED90 |
| SHA1: | 8BD560ADBD322081639E9E8421C4B4D0BA276F8D |
| SHA256: | FBAAF92F4048FB147754D282C2F9BA4923480AEF9C751C2C8813A7DA44AA9865 |
| SSDEEP: | 98304:Xu2m3xWjluefWhO2aE61anv76QJ4zudUio73z4b6IBH3WyiEvEXP4/5ZNhUFUpGd:1D9gKDI8a4S15FYSXwvMXF4 |
MALICIOUS
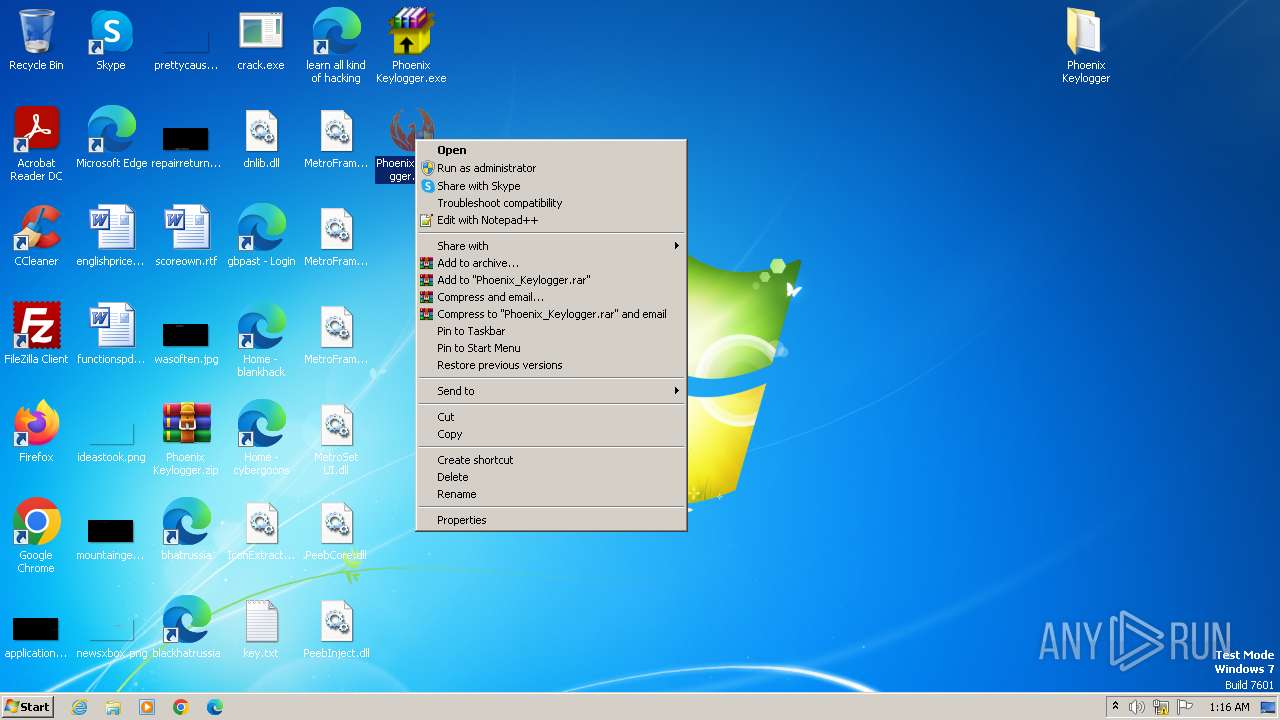
Drops the executable file immediately after the start
- crack.exe (PID: 2520)
- Phoenix_Keylogger.exe (PID: 3608)
- Phoenix Keylogger.exe (PID: 1608)
Create files in the Startup directory
- crack.exe (PID: 2520)
SUSPICIOUS
Reads Microsoft Outlook installation path
- Phoenix Keylogger.exe (PID: 1608)
Reads Internet Explorer settings
- Phoenix Keylogger.exe (PID: 1608)
- Phoenix_Keylogger.exe (PID: 3608)
Reads the Internet Settings
- Phoenix Keylogger.exe (PID: 1608)
INFO
Manual execution by a user
- notepad.exe (PID: 1864)
- Phoenix Keylogger.exe (PID: 1608)
- Phoenix_Keylogger.exe (PID: 3608)
- crack.exe (PID: 984)
- notepad.exe (PID: 3760)
Reads the machine GUID from the registry
- Phoenix Keylogger.exe (PID: 1608)
- crack.exe (PID: 2520)
- crack.exe (PID: 984)
- Phoenix_Keylogger.exe (PID: 3608)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2144)
Checks supported languages
- Phoenix Keylogger.exe (PID: 1608)
- crack.exe (PID: 2520)
- Phoenix_Keylogger.exe (PID: 3608)
- crack.exe (PID: 984)
Creates files or folders in the user directory
- crack.exe (PID: 2520)
Checks proxy server information
- Phoenix Keylogger.exe (PID: 1608)
Reads the computer name
- Phoenix_Keylogger.exe (PID: 3608)
- crack.exe (PID: 2520)
- crack.exe (PID: 984)
- Phoenix Keylogger.exe (PID: 1608)
Create files in a temporary directory
- Phoenix_Keylogger.exe (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:15 01:50:20 |
| ZipCRC: | 0xa1b24adb |
| ZipCompressedSize: | 19 |
| ZipUncompressedSize: | 19 |
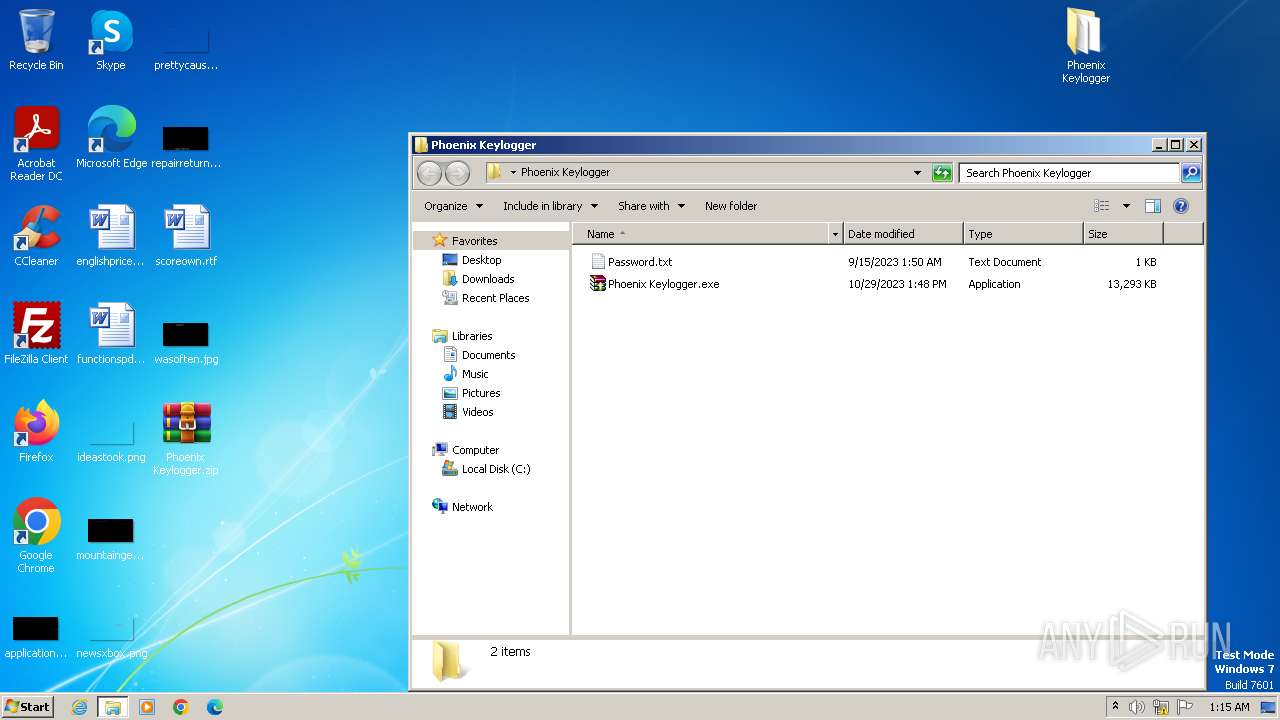
| ZipFileName: | Phoenix Keylogger/Password.txt |
Total processes
56
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\crack.exe" | C:\Users\admin\Desktop\crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1608 | "C:\Users\admin\Desktop\Phoenix Keylogger.exe" | C:\Users\admin\Desktop\Phoenix Keylogger.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
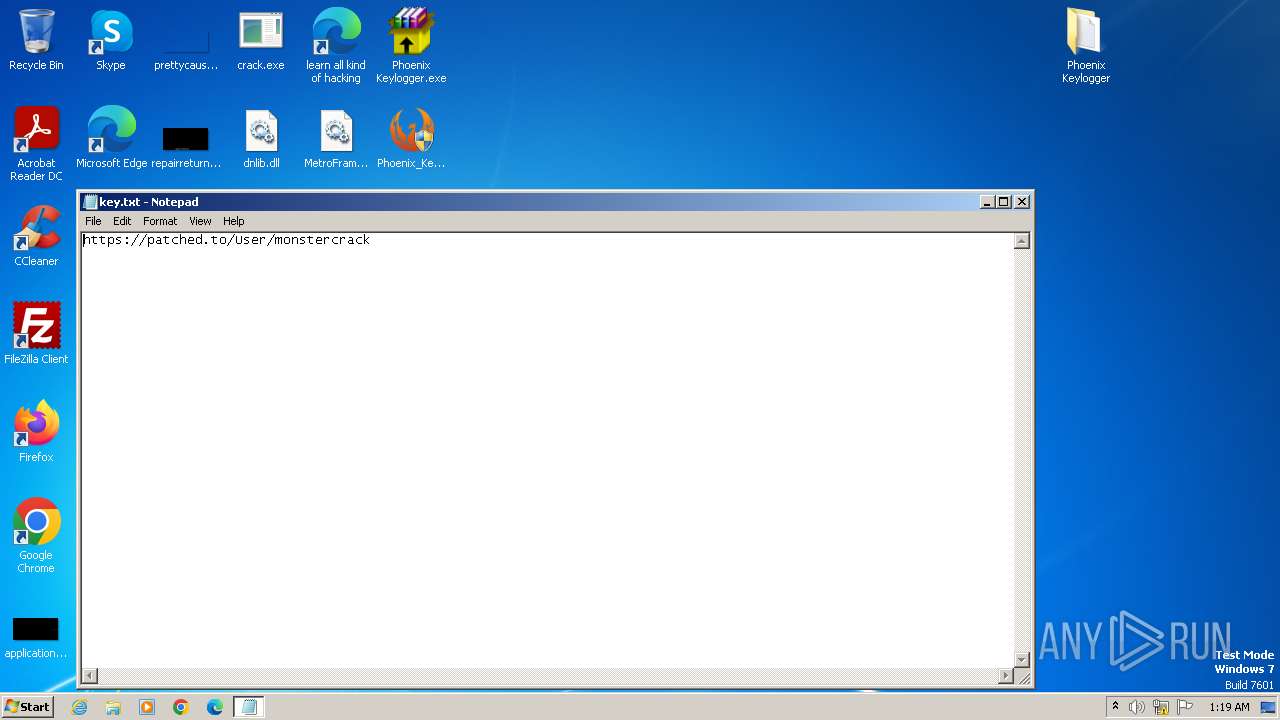
| 1864 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Phoenix Keylogger\Password.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Phoenix Keylogger.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2520 | "C:\Users\admin\Desktop\crack.exe" | C:\Users\admin\Desktop\crack.exe | Phoenix Keylogger.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\Desktop\Phoenix_Keylogger.exe" | C:\Users\admin\Desktop\Phoenix_Keylogger.exe | explorer.exe | ||||||||||||
User: admin Company: Phoenix Keylogger Integrity Level: HIGH Description: Phoenix Keylogger Exit code: 4294967295 Version: 2.1.0.0 Modules
| |||||||||||||||
| 3760 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\key.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 641
Read events
1 612
Write events
29
Delete events
0
Modification events
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
20
Suspicious files
7
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2144.42384\Phoenix Keylogger\Phoenix Keylogger.exe | executable | |
MD5:B36E6664467C33A83FB27582C3AD7B47 | SHA256:0F36B3D2BA6A8F5C88E2C6746AB01728A7124612DDD23094E8F520DD790763E6 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\Phoenix_Keylogger.exe | executable | |
MD5:321DE682F6FCB7C88CDD83479A0CEBA1 | SHA256:DCEBBEA9617554DB744B97DCE95B5B55154130F1CDE5E155B677D20CFE2D712E | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\dnlib.dll | executable | |
MD5:754A721EE1F1869394EC24212BBD7F30 | SHA256:A07EAF627F7CE270B0622DAD29BFCD6F8A9BC49701802F4ED2455FFEE7BC7307 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\bhatrussia.url | binary | |
MD5:96CEC2FF3BC1281C3B541D549538C9FB | SHA256:CD064A6F7AA46315DEA10E6D73BC0416C4954BC8C3FEE19A39A2C88C49F3E8AE | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\MetroFramework.Fonts.dll | executable | |
MD5:65EF4B23060128743CEF937A43B82AA3 | SHA256:C843869AACA5135C2D47296985F35C71CA8AF4431288D04D481C4E46CC93EE26 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\gbpast - Login.url | binary | |
MD5:4A4F5BE9370E206241BB73BFC2367F3C | SHA256:210F2EE620FE51ACDBE59BBA7BB4ACBDE397034818B09156F6F0874B016A5B18 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\IconExtractor.dll | executable | |
MD5:36B46C48D2FBCDF839F0BB96BA20B386 | SHA256:02707BE9D1E86187D99ED2DC91DF6335D093FBEC1EE4B65B5DC16161615EC2F9 | |||
| 1608 | Phoenix Keylogger.exe | C:\Users\admin\Desktop\PeebCore.dll | executable | |
MD5:128A51A403DDD07999E03E3A36D96579 | SHA256:90F882851DF247E60CEF36644E63A7927B243FC8F81B5CCB1ECFF8E9564D81F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |