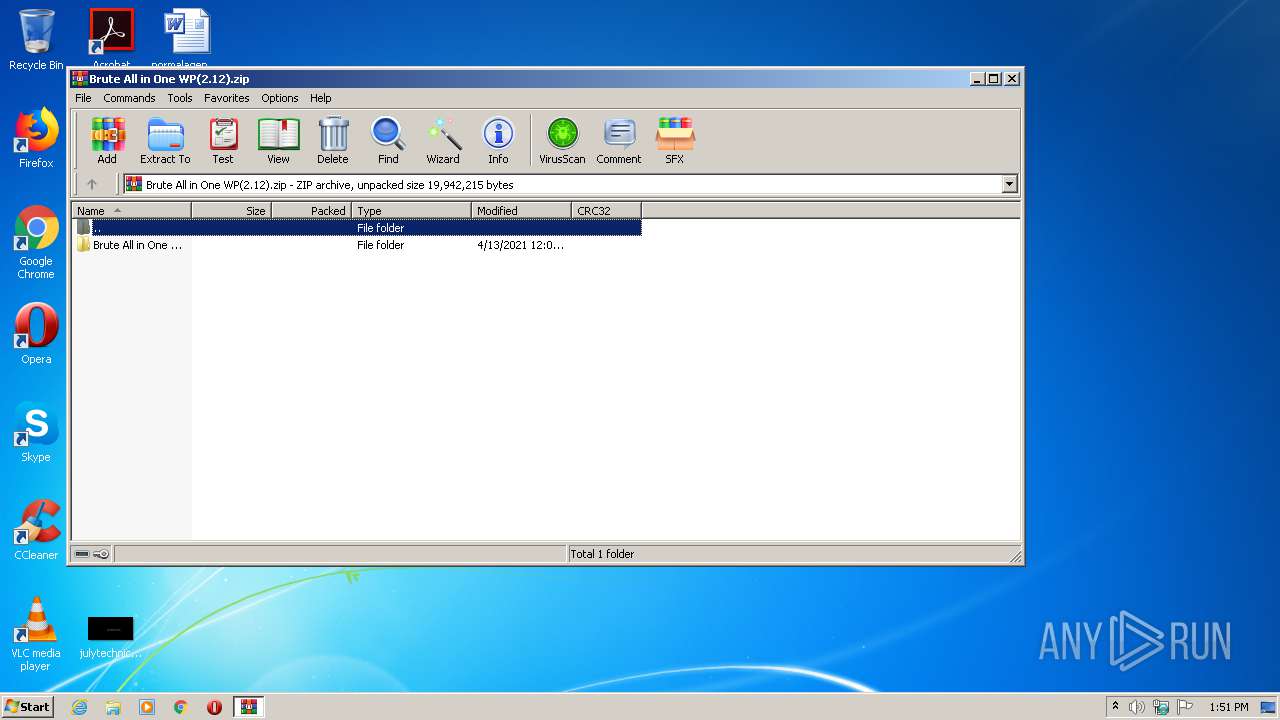
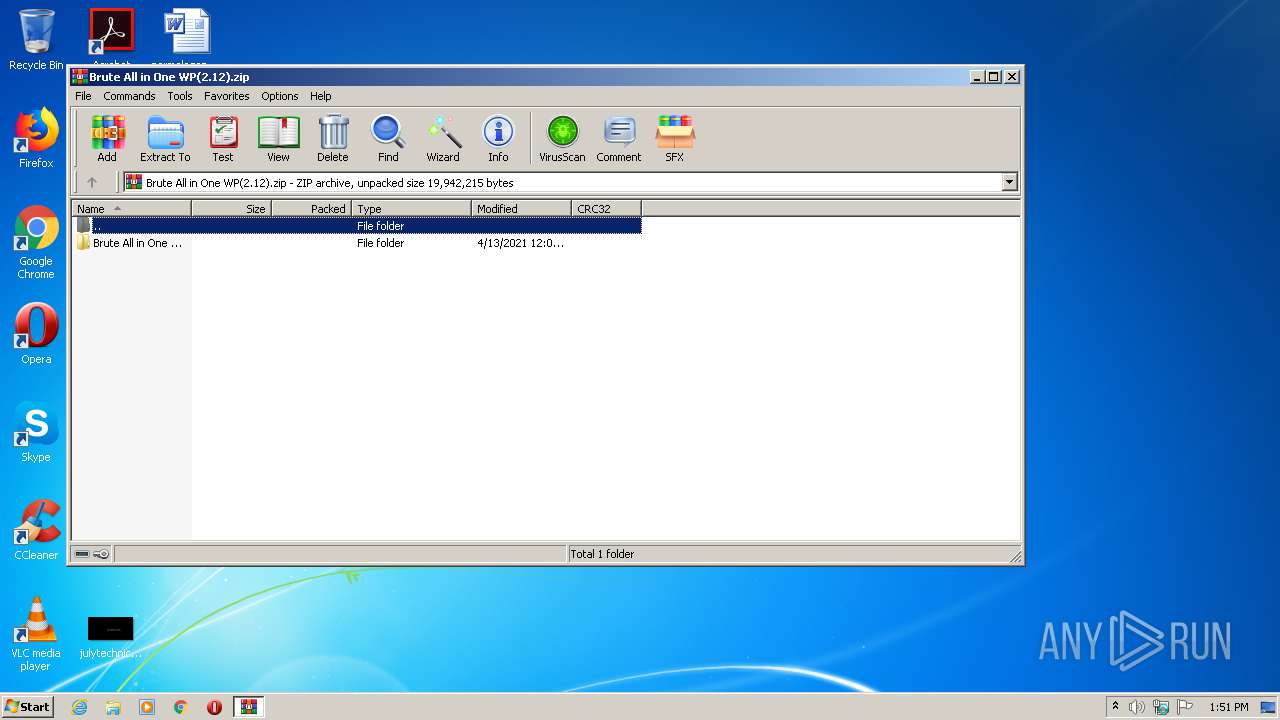
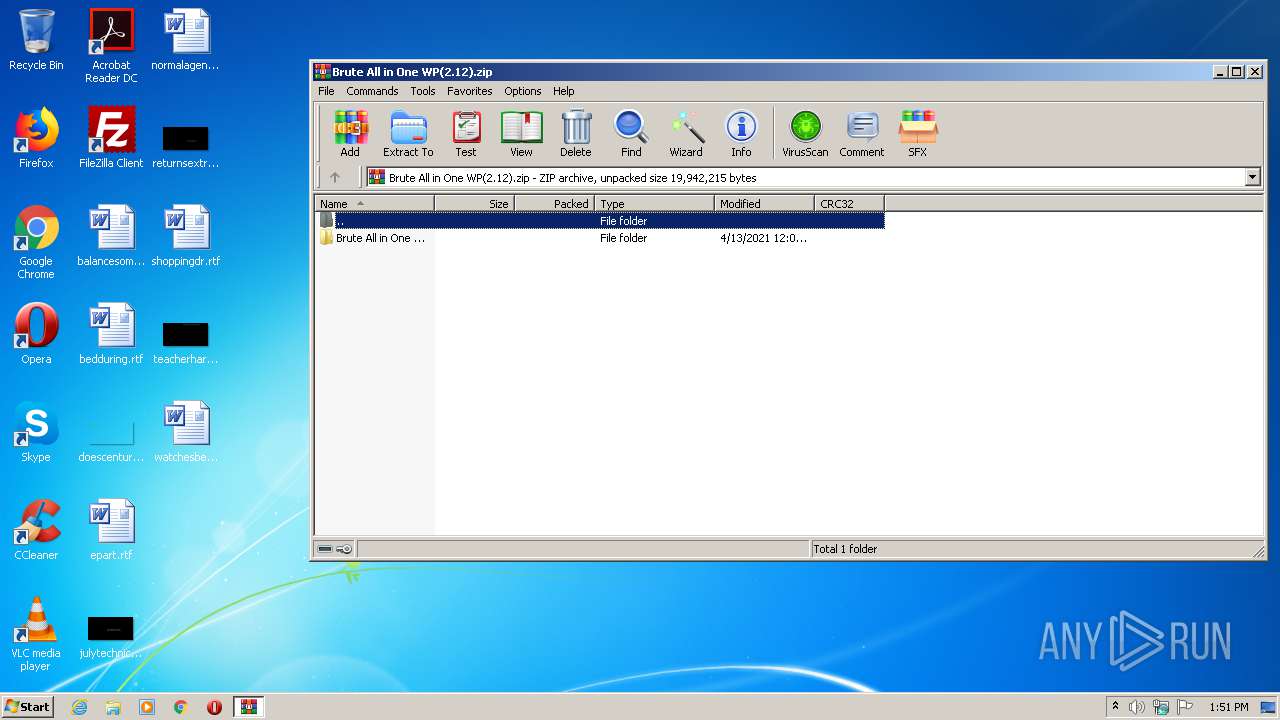
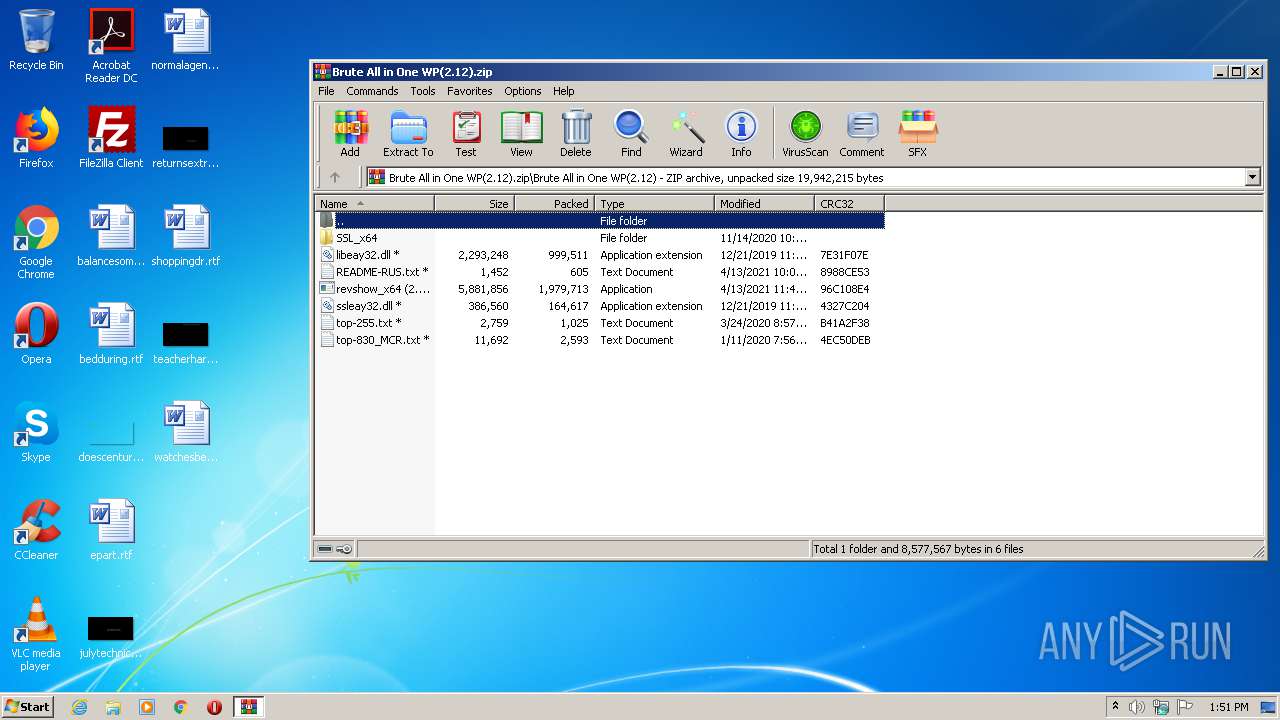
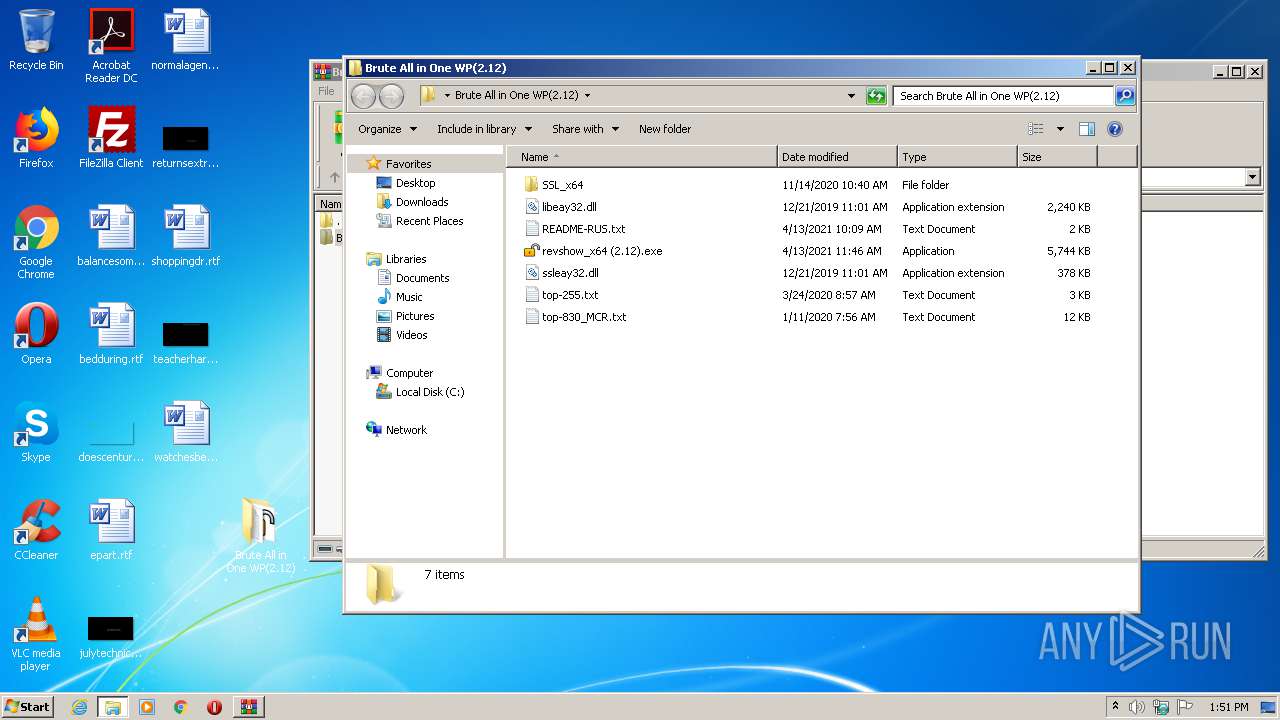
| File name: | Brute All in One WP(2.12).zip |
| Full analysis: | https://app.any.run/tasks/5465a711-8b29-4e48-a9a1-e56cdab24281 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2021, 12:51:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 0A5DACE7D173FC7EDA18298E91F8DAC6 |
| SHA1: | 6B02DD45E9604AD2639BD5980DE60851E885AA17 |
| SHA256: | FBA2A569710A329D7D1DE082BC8394C8F04DB4B09013D1B58CC0287922B3FB13 |
| SSDEEP: | 196608:qkgJR6KTbwOryk26d85vbdyPqLizdKrvZlsv9Ss2kZe8IKqCOiHl3/AG1/2U21Xz:/4zwwYw8hB4qL0dKrvkJCKN5FPAGtb2p |
MALICIOUS
No malicious indicators.SUSPICIOUS
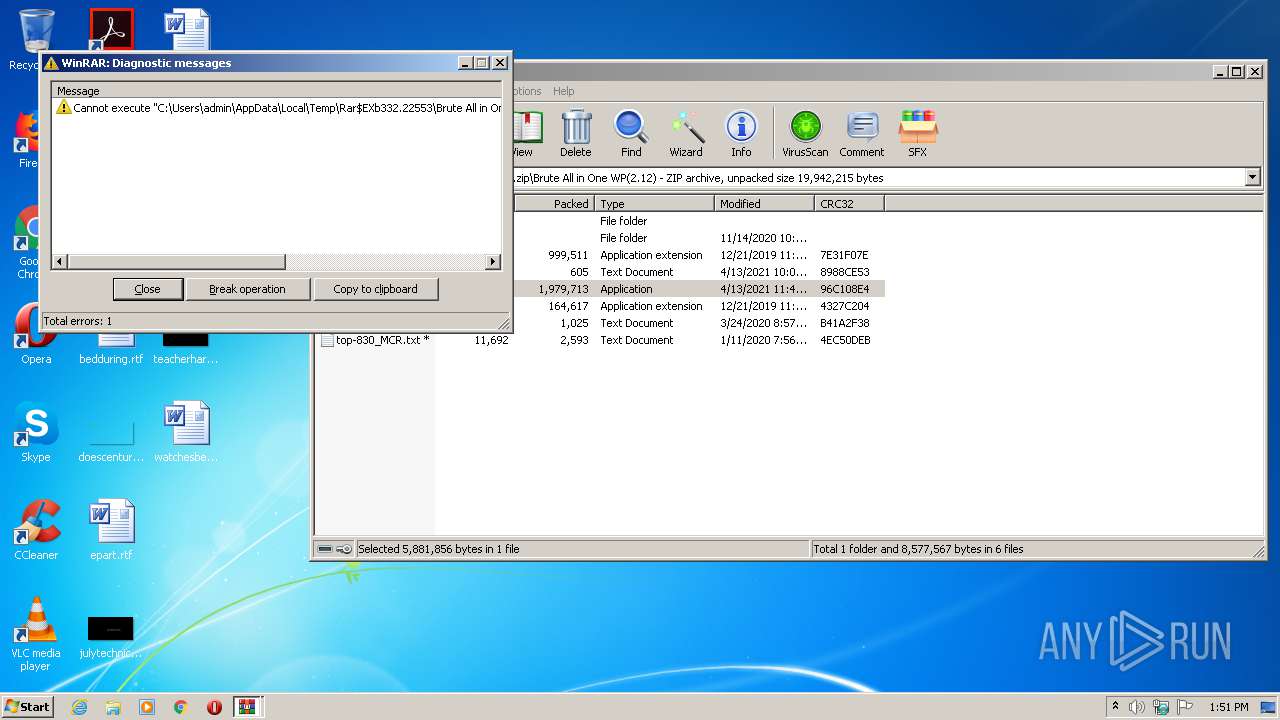
Drops a file with too old compile date
- WinRAR.exe (PID: 332)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 332)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 332)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 332)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Brute All in One WP(2.12)/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:04:13 14:04:28 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
39
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
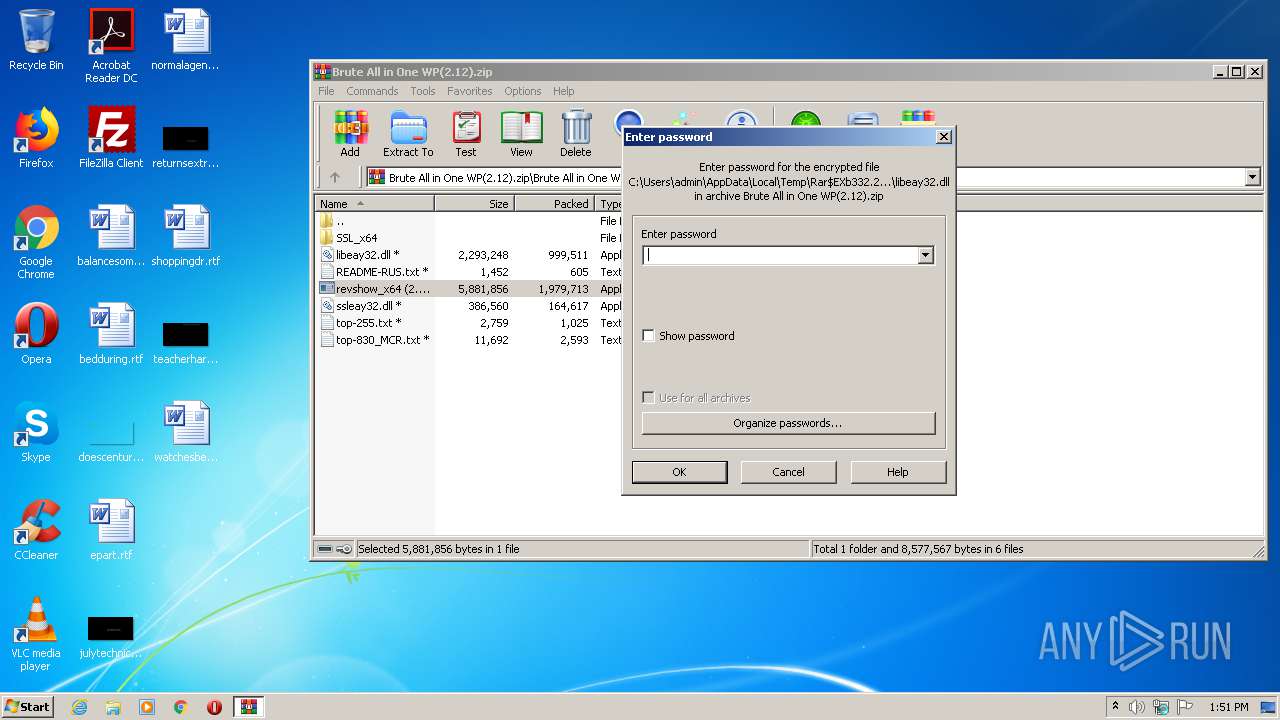
| 332 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Brute All in One WP(2.12).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
447
Read events
430
Write events
17
Delete events
0
Modification events
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Brute All in One WP(2.12).zip | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
10
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\SSL_x64\libcrypto-x64.dll | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\SSL_x64\libeay32.dll | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\SSL_x64\ssleay32.dll | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\SSL_x64\vcredist_x64.exe | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\top-255.txt | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb332.23824\Brute All in One WP(2.12)\top-830_MCR.txt | — | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb332.22553\Brute All in One WP(2.12)\SSL_x64\ssleay32.dll | executable | |
MD5:1B4BD6105C83C1FFDEF00DE19F57B4BA | SHA256:142DF21458EA642A83AA60C8DCA1AEF71F4EA1073EDC7E9BA1904CCE3FD2A5F3 | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb332.22553\Brute All in One WP(2.12)\top-830_MCR.txt | text | |
MD5:84ED69555D298C4CB1C2B5689D0A977D | SHA256:4F55B144271A6269506B75C39672F16B63D21C2457A420DD2DD89996239DCBC8 | |||
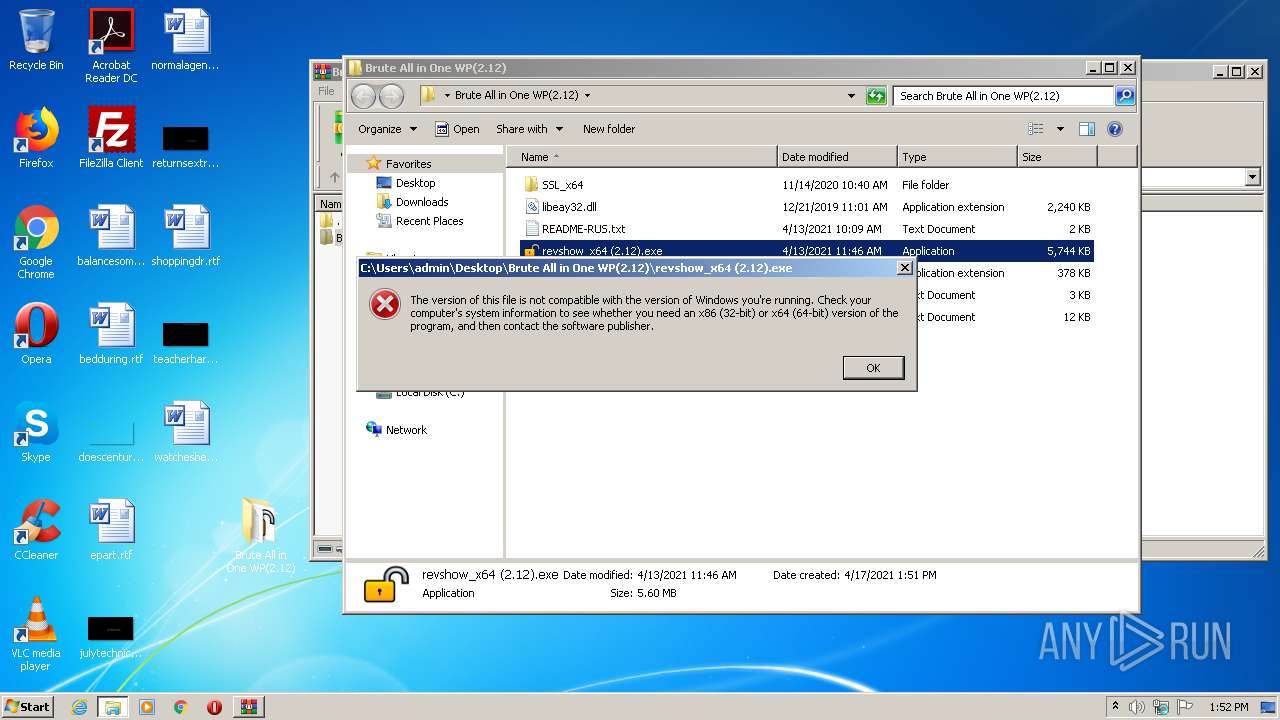
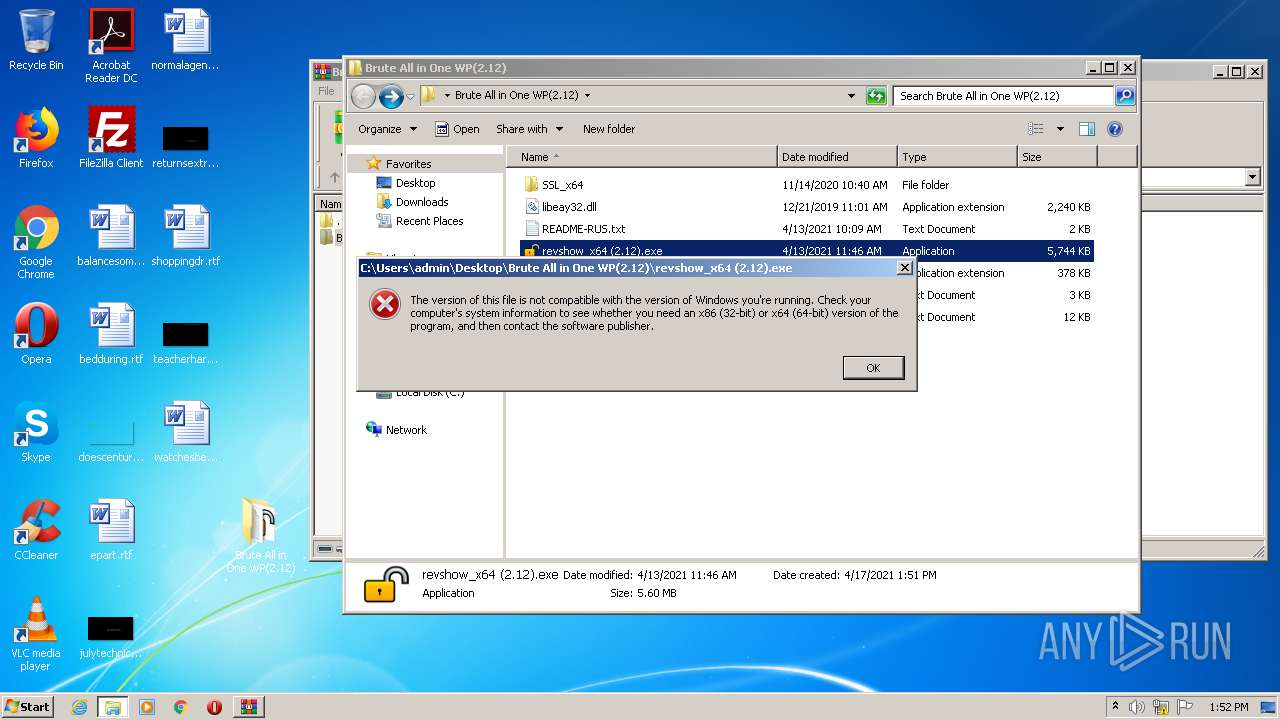
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb332.22553\Brute All in One WP(2.12)\revshow_x64 (2.12).exe | executable | |
MD5:— | SHA256:— | |||
| 332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb332.22553\Brute All in One WP(2.12)\SSL_x64\libcrypto-x64.dll | executable | |
MD5:21E2F30EB8D82918CC4CA75F18A2CCE3 | SHA256:2EB03A6ADF6BBB6F87562D8070C6F2B7F65DE55ED0BC54E66E5079985A7ED600 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report