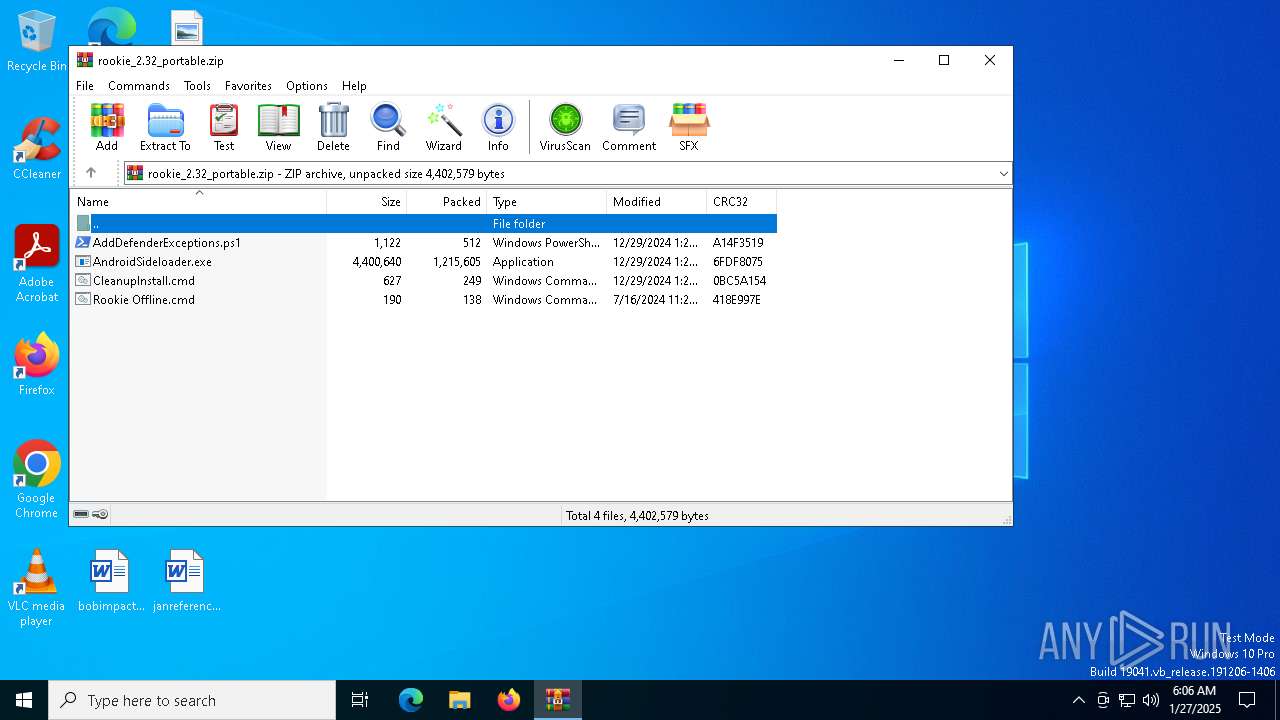
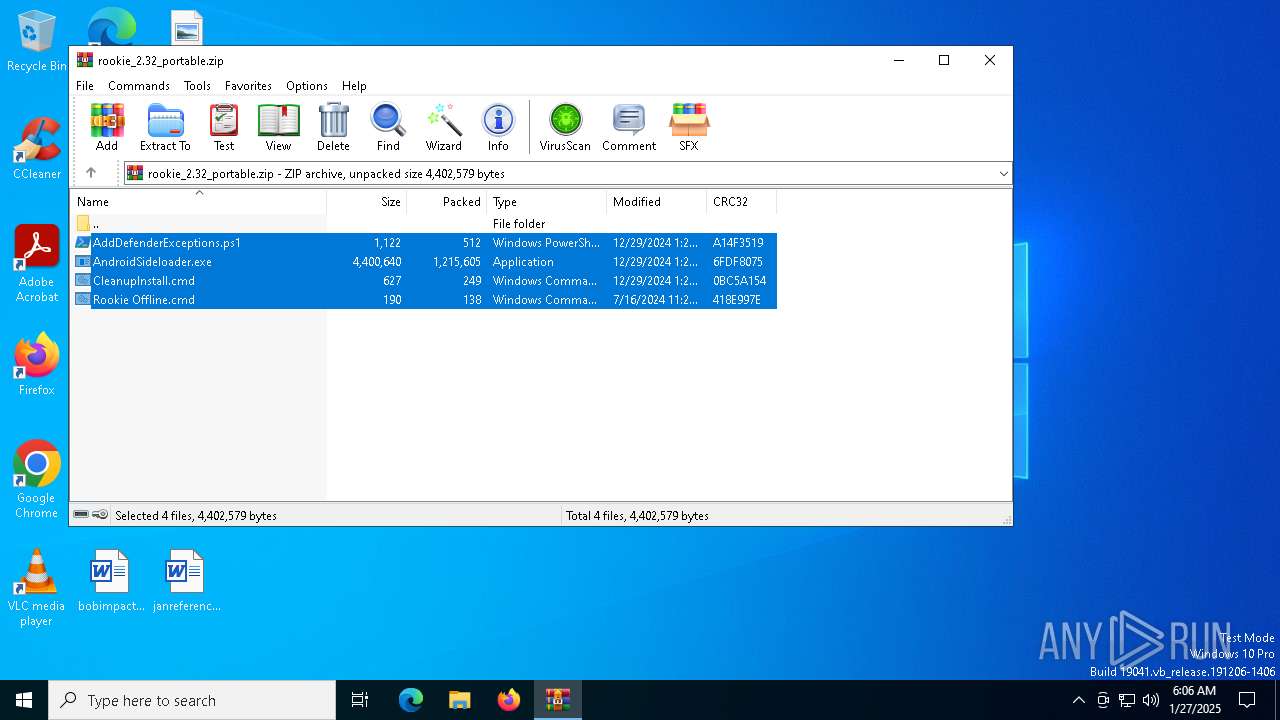
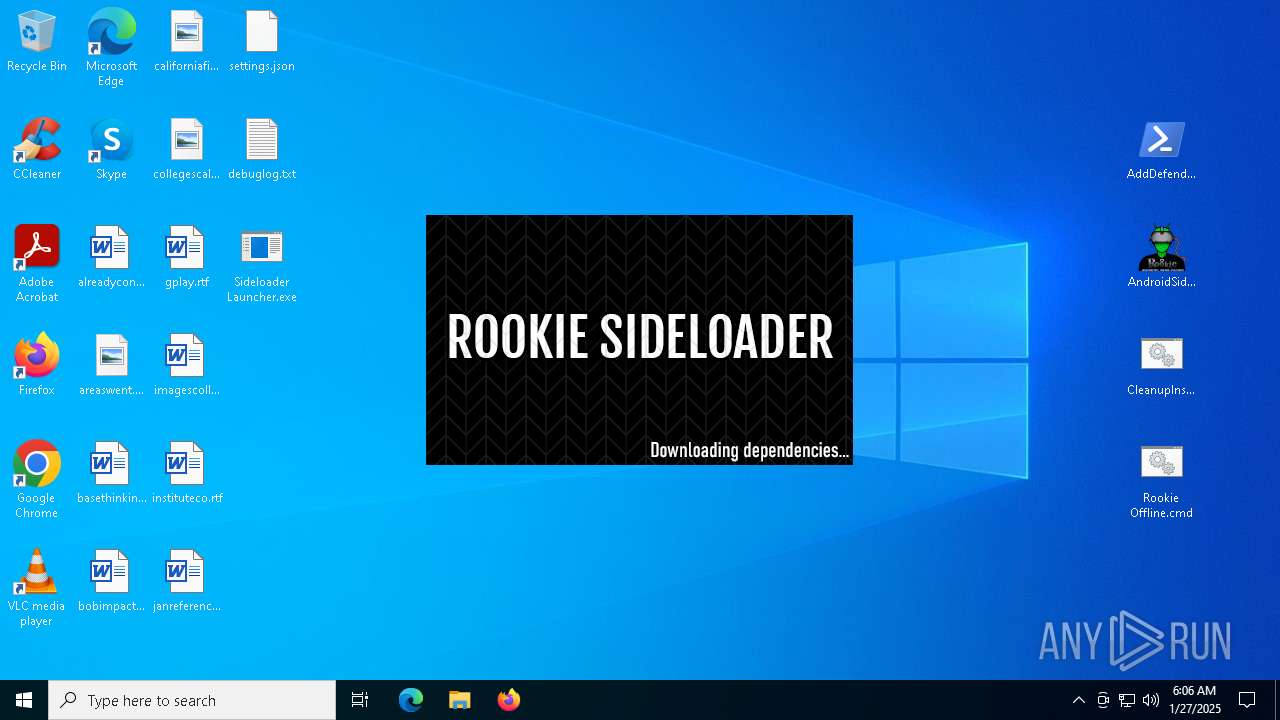
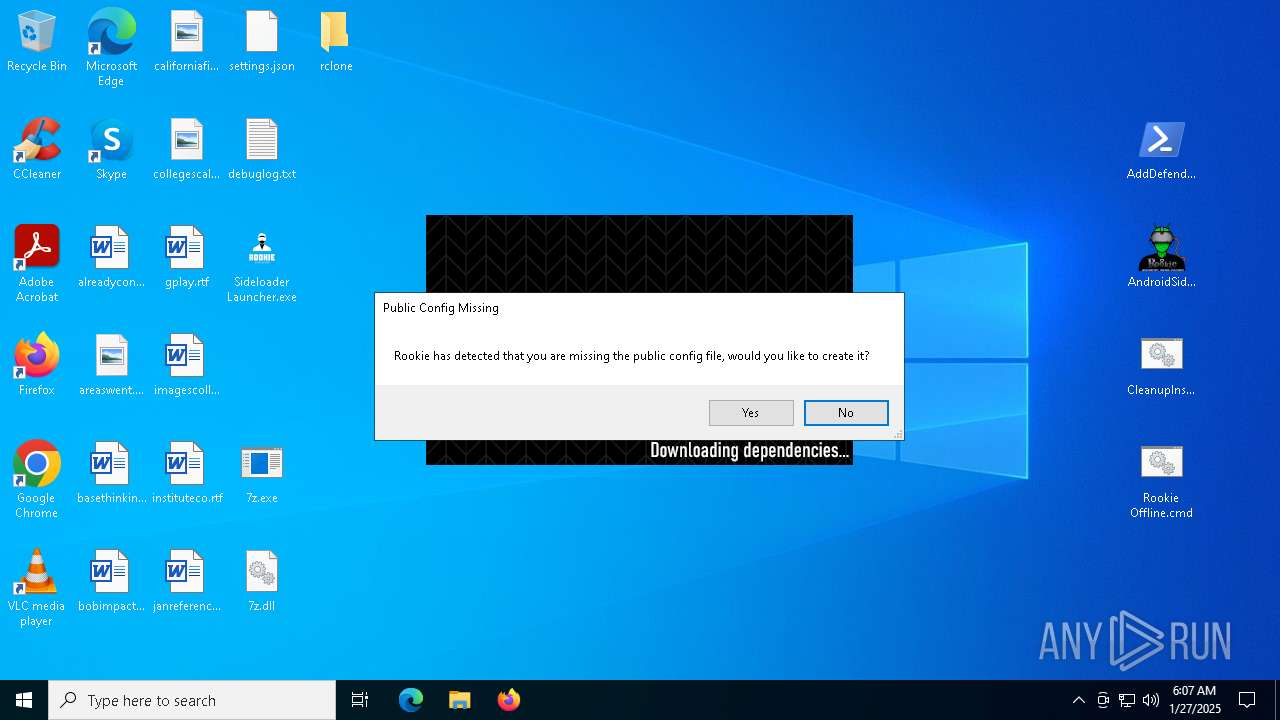
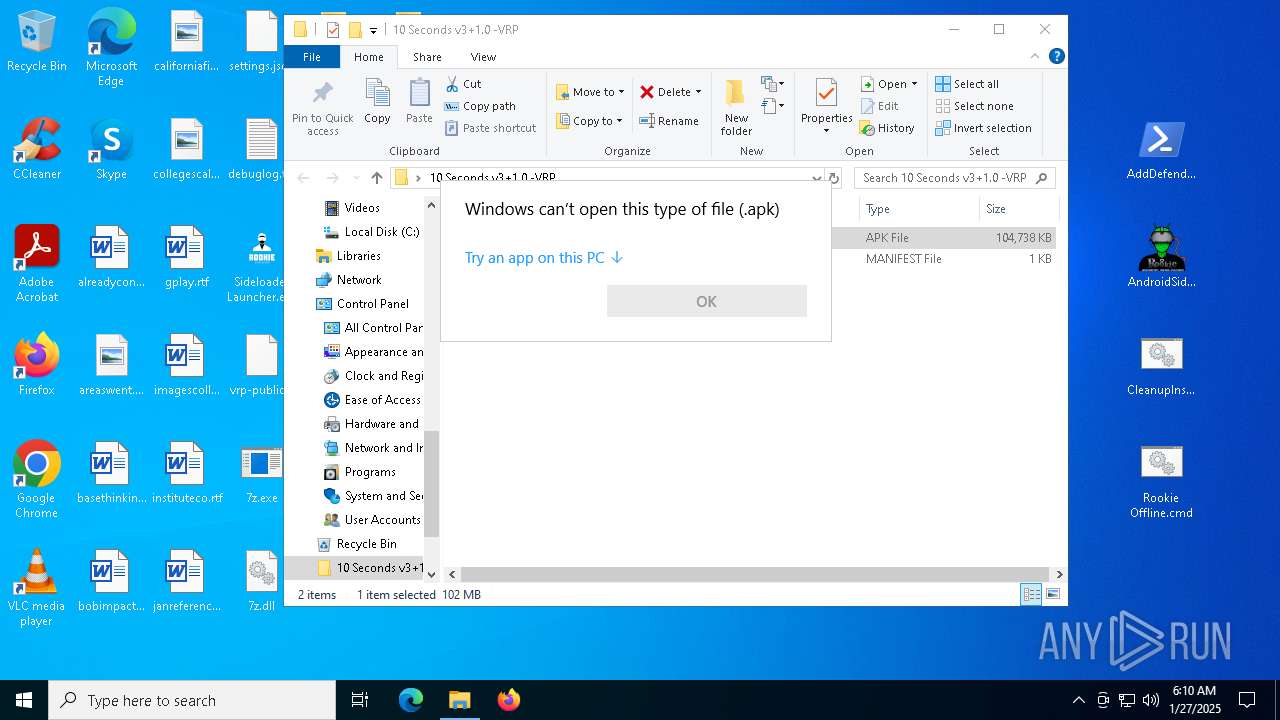
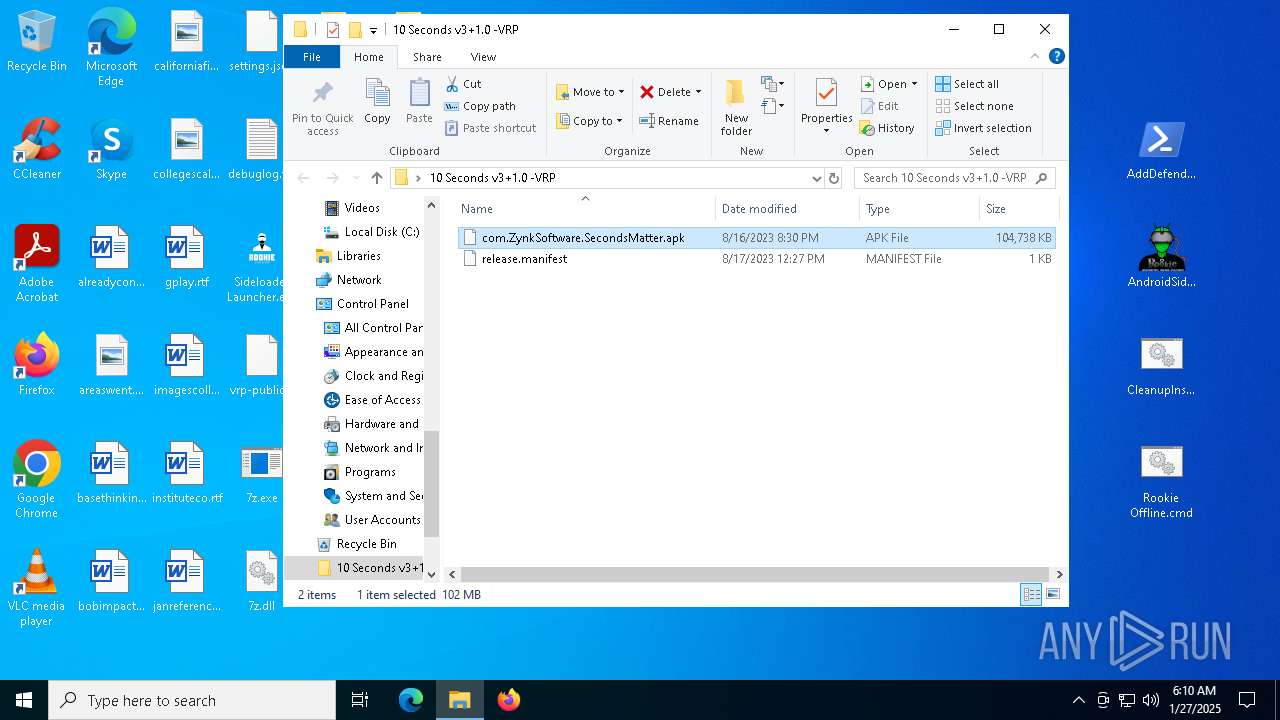
| download: | /downloads/rookie/rookie_2.32_portable.zip |
| Full analysis: | https://app.any.run/tasks/1a913e9c-75ae-4adf-b6d8-a654b825492e |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2025, 06:06:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BBFC3B69AAFDC0DC459DDCAB949EE998 |
| SHA1: | 96F26DEDB42C4D1EA582FF544D35FF54EE24E61A |
| SHA256: | FB79B00054E8ED1FB900C114E9E0610D3DA5B98AABF026771FA99352EDED9201 |
| SSDEEP: | 49152:aBY/MytD2RiE6oRtZDdKgviNWUxcA0fYilCaU9Rkdxli6txH+3KVKvnlokLge568:aBY0C2vddXvK0EaARkdpuBvnqcnLGLJk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6584)
SUSPICIOUS
Reads security settings of Internet Explorer
- AndroidSideloader.exe (PID: 128)
- AndroidSideloader.exe (PID: 6748)
- AndroidSideloader.exe (PID: 3584)
- Sideloader Launcher.exe (PID: 5200)
Executable content was dropped or overwritten
- AndroidSideloader.exe (PID: 128)
- 7z.exe (PID: 4400)
Drops 7-zip archiver for unpacking
- AndroidSideloader.exe (PID: 128)
Application launched itself
- adb.exe (PID: 3620)
- adb.exe (PID: 1344)
- adb.exe (PID: 6060)
RCLONE has been detected
- rclone.exe (PID: 6860)
- rclone.exe (PID: 7104)
- rclone.exe (PID: 1304)
- rclone.exe (PID: 4592)
- rclone.exe (PID: 4668)
- rclone.exe (PID: 5036)
- rclone.exe (PID: 1520)
There is functionality for VM detection antiVM strings (YARA)
- rclone.exe (PID: 1304)
INFO
Manual execution by a user
- AndroidSideloader.exe (PID: 128)
- AndroidSideloader.exe (PID: 6748)
- WinRAR.exe (PID: 6344)
- Sideloader Launcher.exe (PID: 5200)
Disables trace logs
- AndroidSideloader.exe (PID: 128)
- AndroidSideloader.exe (PID: 6748)
- AndroidSideloader.exe (PID: 3584)
Reads the computer name
- 7z.exe (PID: 4400)
- AndroidSideloader.exe (PID: 128)
- 7z.exe (PID: 4672)
- rclone.exe (PID: 7104)
- adb.exe (PID: 6792)
- rclone.exe (PID: 6860)
- rclone.exe (PID: 1304)
- 7z.exe (PID: 2736)
- 7z.exe (PID: 6244)
- AndroidSideloader.exe (PID: 6748)
- rclone.exe (PID: 4668)
- 7z.exe (PID: 936)
- adb.exe (PID: 4076)
- rclone.exe (PID: 4592)
- AndroidSideloader.exe (PID: 3584)
- adb.exe (PID: 6924)
- Sideloader Launcher.exe (PID: 5200)
- rclone.exe (PID: 5036)
- rclone.exe (PID: 1520)
- 7z.exe (PID: 2728)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6584)
The sample compiled with english language support
- 7z.exe (PID: 4400)
- AndroidSideloader.exe (PID: 128)
Reads the software policy settings
- AndroidSideloader.exe (PID: 128)
- rclone.exe (PID: 7104)
- rclone.exe (PID: 1304)
- AndroidSideloader.exe (PID: 6748)
- rclone.exe (PID: 4668)
- AndroidSideloader.exe (PID: 3584)
- rclone.exe (PID: 1520)
Checks supported languages
- 7z.exe (PID: 4400)
- AndroidSideloader.exe (PID: 128)
- 7z.exe (PID: 4672)
- adb.exe (PID: 6156)
- adb.exe (PID: 6792)
- rclone.exe (PID: 6860)
- rclone.exe (PID: 7104)
- 7z.exe (PID: 2736)
- adb.exe (PID: 3620)
- adb.exe (PID: 5912)
- adb.exe (PID: 1080)
- adb.exe (PID: 1904)
- adb.exe (PID: 3040)
- adb.exe (PID: 6152)
- rclone.exe (PID: 1304)
- adb.exe (PID: 236)
- adb.exe (PID: 4944)
- adb.exe (PID: 4136)
- adb.exe (PID: 6428)
- adb.exe (PID: 5652)
- adb.exe (PID: 6856)
- AndroidSideloader.exe (PID: 6748)
- adb.exe (PID: 1344)
- adb.exe (PID: 6532)
- 7z.exe (PID: 6244)
- adb.exe (PID: 6912)
- rclone.exe (PID: 4592)
- rclone.exe (PID: 4668)
- 7z.exe (PID: 936)
- adb.exe (PID: 4076)
- Sideloader Launcher.exe (PID: 5200)
- adb.exe (PID: 1144)
- adb.exe (PID: 6924)
- adb.exe (PID: 3612)
- AndroidSideloader.exe (PID: 3584)
- adb.exe (PID: 6060)
- rclone.exe (PID: 5036)
- rclone.exe (PID: 1520)
- 7z.exe (PID: 2728)
Checks proxy server information
- AndroidSideloader.exe (PID: 128)
- AndroidSideloader.exe (PID: 6748)
- AndroidSideloader.exe (PID: 3584)
Reads the machine GUID from the registry
- AndroidSideloader.exe (PID: 128)
- rclone.exe (PID: 7104)
- rclone.exe (PID: 1304)
- AndroidSideloader.exe (PID: 6748)
- rclone.exe (PID: 4668)
- AndroidSideloader.exe (PID: 3584)
- rclone.exe (PID: 1520)
Create files in a temporary directory
- rclone.exe (PID: 7104)
- adb.exe (PID: 6792)
- rclone.exe (PID: 1304)
- rclone.exe (PID: 4668)
- rclone.exe (PID: 1520)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4400)
Application based on Golang
- rclone.exe (PID: 1304)
Process checks computer location settings
- Sideloader Launcher.exe (PID: 5200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:16 13:27:44 |
| ZipCRC: | 0x418e997e |
| ZipCompressedSize: | 138 |
| ZipUncompressedSize: | 190 |
| ZipFileName: | Rookie Offline.cmd |
Total processes
205
Monitored processes
75
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
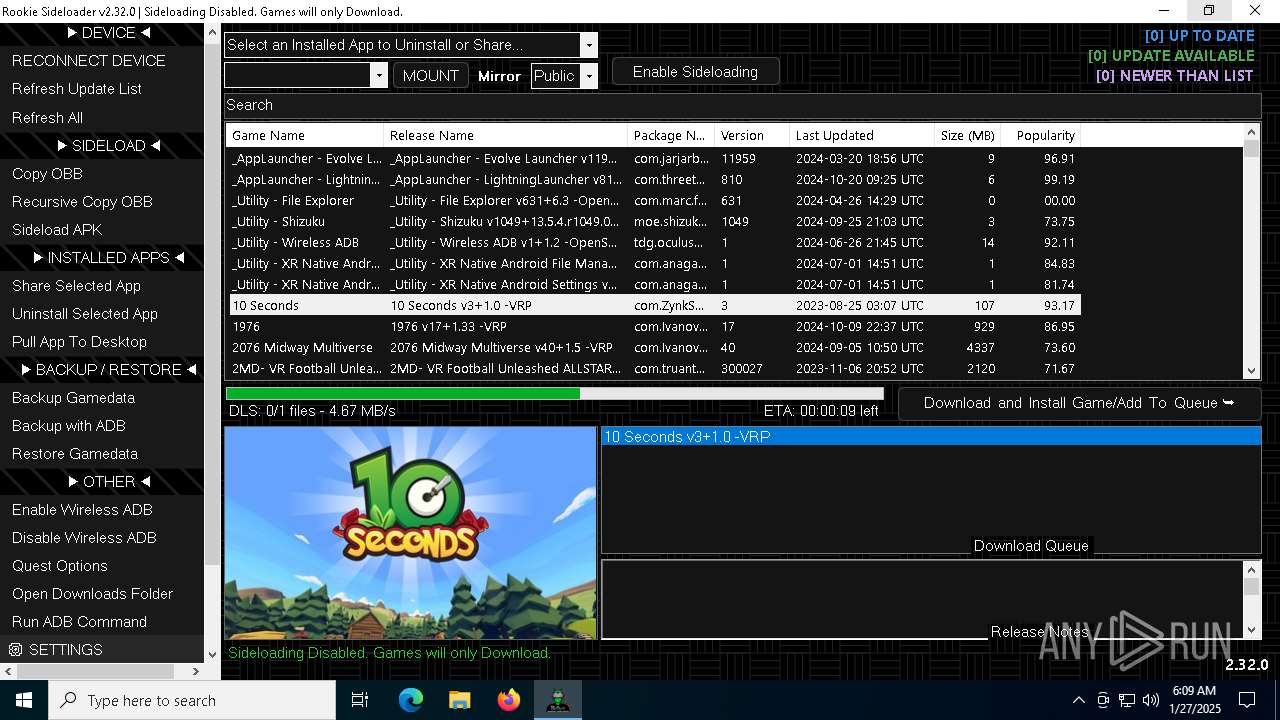
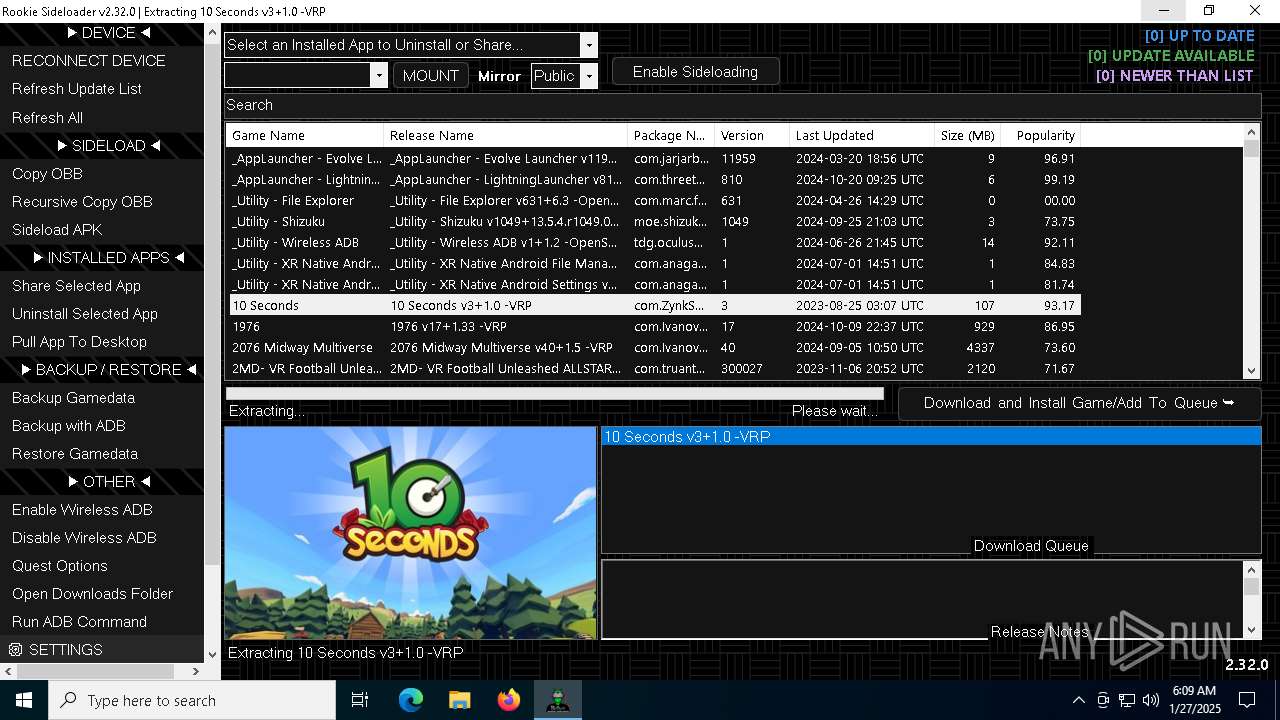
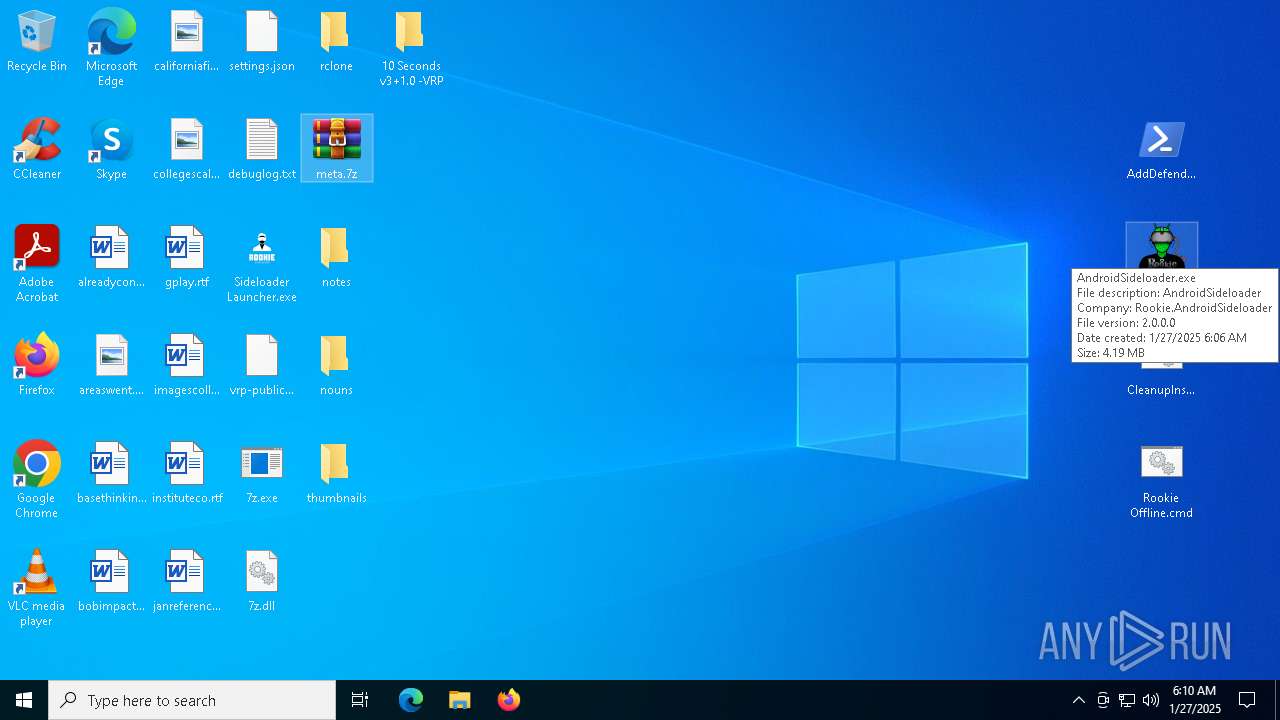
| 128 | "C:\Users\admin\Desktop\AndroidSideloader.exe" | C:\Users\admin\Desktop\AndroidSideloader.exe | explorer.exe | ||||||||||||
User: admin Company: Rookie.AndroidSideloader Integrity Level: MEDIUM Description: AndroidSideloader Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 236 | "C:\RSL\platform-tools\adb.exe" devices | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "7z.exe" x "C:\Users\admin\Desktop\meta.7z" -y -o"C:\Users\admin\Desktop\meta" -p"gL59VfgPxoHR" -bsp1 | C:\Users\admin\Desktop\7z.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Version: 24.09 Modules
| |||||||||||||||
| 1080 | "C:\RSL\platform-tools\adb.exe" devices | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1144 | "C:\RSL\platform-tools\adb.exe" kill-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1304 | "C:\Users\admin\Desktop\rclone\rclone.exe" copy ":http:/8c621d6563ab6bbb1145f83c652fbd8d/" "C:\Users\admin\Desktop\8c621d6563ab6bbb1145f83c652fbd8d" --transfers 1 --multi-thread-streams 0 --progress --rc --inplace --http-url https://go.vrpyourself.online/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\Desktop\rclone\rclone.exe | AndroidSideloader.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.68.2 Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 282
Read events
37 243
Write events
39
Delete events
0
Modification events
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rookie_2.32_portable.zip | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6584) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
17
Suspicious files
3
Text files
4 112
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 128 | AndroidSideloader.exe | C:\Users\admin\Desktop\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6584.31885\Rookie Offline.cmd | text | |
MD5:83B85F3A19C77666117DB1DFBBFD782B | SHA256:5286FC09CBBC098A5DA63096676B180BD7FD28DCD96A79F41F4D92784CC262D1 | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6584.31885\AddDefenderExceptions.ps1 | text | |
MD5:EDDAAD261ACC56C1F0FC2467954A9267 | SHA256:947EA0B0397B44D41DE337A82A93E8C1260B08818F21FAB5A488610427A0EC62 | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6584.31885\AndroidSideloader.exe | executable | |
MD5:CDBFBC77E7C60F173663AF77A173EBBE | SHA256:6DE2C00CE9C348CBEAAE800FA1DFCDA96F55C53FD9310BBBCCDFE3E700BF2C8E | |||
| 6584 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6584.31885\CleanupInstall.cmd | text | |
MD5:9AE44CEBBDE4F44C27801BBF93494C1D | SHA256:57FC69317DE4E7B75A6D45C6037572738F6B48766A6C0D8A47A4F4A4CC533281 | |||
| 128 | AndroidSideloader.exe | C:\Users\admin\Desktop\debuglog.txt | text | |
MD5:9E523DE05B1B58B28B4CFC549673DEB1 | SHA256:2593C2E96070F734773B6CAD98C94B5911BF9A2E19150C900FC050CC6F271ED5 | |||
| 128 | AndroidSideloader.exe | C:\Users\admin\Desktop\settings.json | binary | |
MD5:26ABE5EC3FAF47E1D36ED07877B93DEF | SHA256:220E67206EB3ECF15CC87380856AC87C7D1814FE4754056BD5B8B9EC934D5D66 | |||
| 4400 | 7z.exe | C:\RSL\platform-tools\mke2fs.conf | text | |
MD5:699098CA95F87BA48BB94A3E848549B3 | SHA256:AD58A58DCDD24D85055814CA9CAC67DB89D4E67C434E96774BDCE0D0A007D067 | |||
| 128 | AndroidSideloader.exe | C:\Users\admin\Desktop\7z.dll | executable | |
MD5:C4AABD70DC28C9516809B775A30FDD3F | SHA256:882063948D675EE41B5AE68DB3E84879350EC81CF88D15B9BABF2FA08E332863 | |||
| 128 | AndroidSideloader.exe | C:\Users\admin\Desktop\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
53
DNS requests
27
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6412 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6412 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2040 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 23.216.77.40:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
128 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
128 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6748 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3584 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |