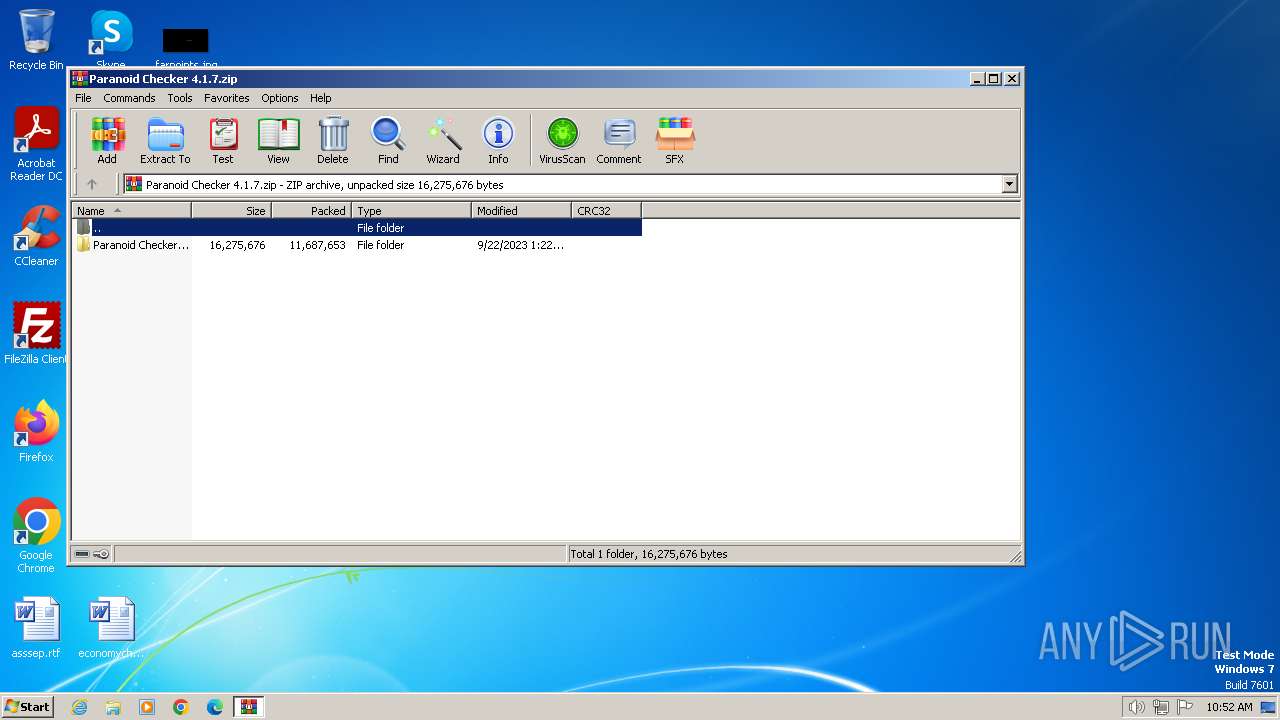
| File name: | Paranoid Checker 4.1.7.zip |
| Full analysis: | https://app.any.run/tasks/265d7bc2-2b17-40ae-9338-badfd16c7e10 |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2024, 10:52:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 604ADFEACE617392A885BAE5BA91DEF9 |
| SHA1: | 75F6FB6DD88F2057850D4DBE6038D22BB068223B |
| SHA256: | FB63A03E752329D09522C7813CB212331AF2D18430B8CD2E9DB937CB555C382D |
| SSDEEP: | 98304:OadcEE9a2ur1GbsJrEjhPT9tQYqKOtPBLRQBdfhRk9f3OwLb4k/N8GDEEIJt0qUr:FrXTmrt86rraVGvJItBhUgX9eXZOYQ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1696)
- Paranoid Checker 4.1.7.exe (PID: 2756)
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1496)
- wscript.exe (PID: 2768)
- wscript.exe (PID: 3016)
- wscript.exe (PID: 3596)
- wscript.exe (PID: 3372)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1696)
Reads security settings of Internet Explorer
- Paranoid Checker 4.1.7.exe (PID: 2756)
- services.exe (PID: 2548)
- msComponentsaves.exe (PID: 2372)
- Paranoid Checker 4.1.7.exe (PID: 392)
- Paranoid Checker 4.1.7.exe (PID: 3060)
Reads the Internet Settings
- Paranoid Checker 4.1.7.exe (PID: 2756)
- wscript.exe (PID: 1496)
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- Paranoid Checker 4.1.7.exe (PID: 392)
- Paranoid Checker 4.1.7.exe (PID: 3060)
- wscript.exe (PID: 3596)
- wscript.exe (PID: 3372)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1496)
- wscript.exe (PID: 3596)
- wscript.exe (PID: 3372)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1496)
- wscript.exe (PID: 3596)
- wscript.exe (PID: 3372)
Executing commands from a ".bat" file
- wscript.exe (PID: 1496)
- wscript.exe (PID: 3596)
- wscript.exe (PID: 3372)
Executed via WMI
- schtasks.exe (PID: 2564)
- schtasks.exe (PID: 3072)
- schtasks.exe (PID: 2900)
- schtasks.exe (PID: 2724)
- schtasks.exe (PID: 2100)
- schtasks.exe (PID: 1340)
- schtasks.exe (PID: 2484)
- schtasks.exe (PID: 568)
- schtasks.exe (PID: 2788)
- schtasks.exe (PID: 3544)
- schtasks.exe (PID: 2972)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 2804)
- schtasks.exe (PID: 2176)
- schtasks.exe (PID: 1596)
- schtasks.exe (PID: 1780)
- schtasks.exe (PID: 1404)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 2560)
- schtasks.exe (PID: 1796)
- schtasks.exe (PID: 924)
- schtasks.exe (PID: 2640)
- schtasks.exe (PID: 2384)
- schtasks.exe (PID: 3800)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 2324)
- schtasks.exe (PID: 3444)
- schtasks.exe (PID: 3528)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 784)
- schtasks.exe (PID: 2748)
- schtasks.exe (PID: 1628)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 3292)
- schtasks.exe (PID: 3128)
- schtasks.exe (PID: 3132)
- schtasks.exe (PID: 3152)
- schtasks.exe (PID: 3112)
- schtasks.exe (PID: 4072)
- schtasks.exe (PID: 1636)
- schtasks.exe (PID: 664)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 2416)
- schtasks.exe (PID: 896)
- schtasks.exe (PID: 3988)
- schtasks.exe (PID: 268)
- schtasks.exe (PID: 572)
- schtasks.exe (PID: 3468)
The process creates files with name similar to system file names
- msComponentsaves.exe (PID: 2372)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 1636)
- schtasks.exe (PID: 2640)
- schtasks.exe (PID: 3152)
- schtasks.exe (PID: 3112)
- schtasks.exe (PID: 4072)
- schtasks.exe (PID: 664)
Starts itself from another location
- msComponentsaves.exe (PID: 2372)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 796)
The process executes VB scripts
- services.exe (PID: 2548)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 3016)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 3016)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 2768)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3016)
- wscript.exe (PID: 2768)
Reads settings of System Certificates
- services.exe (PID: 2548)
INFO
Manual execution by a user
- Paranoid Checker 4.1.7.exe (PID: 2756)
- Paranoid Checker 4.1.7.exe (PID: 392)
- Paranoid Checker 4.1.7.exe (PID: 3060)
Reads the computer name
- Paranoid Checker 4.1.7.exe (PID: 2756)
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- Paranoid Checker 4.1.7.exe (PID: 392)
- msComponentsaves.exe (PID: 3700)
- Paranoid Checker 4.1.7.exe (PID: 3060)
- msComponentsaves.exe (PID: 3920)
Checks supported languages
- Paranoid Checker 4.1.7.exe (PID: 2756)
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- Paranoid Checker 4.1.7.exe (PID: 392)
- Paranoid Checker 4.1.7.exe (PID: 3060)
- msComponentsaves.exe (PID: 3700)
- msComponentsaves.exe (PID: 3920)
Reads the machine GUID from the registry
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- msComponentsaves.exe (PID: 3700)
- msComponentsaves.exe (PID: 3920)
Reads Environment values
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- msComponentsaves.exe (PID: 3700)
- msComponentsaves.exe (PID: 3920)
Reads product name
- msComponentsaves.exe (PID: 2372)
- services.exe (PID: 2548)
- msComponentsaves.exe (PID: 3700)
- msComponentsaves.exe (PID: 3920)
Creates files in the program directory
- msComponentsaves.exe (PID: 2372)
Create files in a temporary directory
- services.exe (PID: 2548)
Reads the software policy settings
- services.exe (PID: 2548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:22 03:22:54 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Paranoid Checker 4.1.7/ |
Total processes
105
Monitored processes
65
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | schtasks.exe /create /tn "SearchFilterHostS" /sc MINUTE /mo 8 /tr "'C:\MSOCache\All Users\SearchFilterHost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Paranoid Checker 4.1.7.exe" | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Paranoid Checker 4.1.7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 10 Modules
| |||||||||||||||
| 568 | schtasks.exe /create /tn "spoolsv" /sc ONLOGON /tr "'C:\MSOCache\All Users\{90140000-0101-040C-0000-0000000FF1CE}-C\spoolsv.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | schtasks.exe /create /tn "SearchFilterHost" /sc ONLOGON /tr "'C:\MSOCache\All Users\SearchFilterHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | schtasks.exe /create /tn "SystemS" /sc MINUTE /mo 5 /tr "'C:\Users\Public\Recorded TV\Sample Media\System.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | schtasks.exe /create /tn "SearchFilterHostS" /sc MINUTE /mo 11 /tr "'C:\MSOCache\All Users\{90140000-00A1-0419-0000-0000000FF1CE}-C\SearchFilterHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | C:\Windows\system32\cmd.exe /c ""C:\ServerwebRefmonitorDhcp\z0DwzT959mUKovxD5GIlvgUprT.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 896 | schtasks.exe /create /tn "conhostc" /sc MINUTE /mo 12 /tr "'C:\ServerwebRefmonitorDhcp\conhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | schtasks.exe /create /tn "msiexec" /sc ONLOGON /tr "'C:\ServerwebRefmonitorDhcp\msiexec.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 703
Read events
17 570
Write events
121
Delete events
12
Modification events
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Paranoid Checker 4.1.7.zip | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
25
Suspicious files
1
Text files
19
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\AlphaFS.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Extreme.Net.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\libGLESv2.dll | — | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\License.dll | text | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Newtonsoft.Json.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Ookii.Dialogs.Wpf.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Paranoid Checker 4.1.7.exe | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\Pastel.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\SMDiagnostics.dll | executable | |
MD5:— | SHA256:— | |||
| 1696 | WinRAR.exe | C:\Users\admin\Desktop\Paranoid Checker 4.1.7\System.ServiceModel.Internals.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2548 | services.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
2548 | services.exe | 49.13.77.253:80 | cw08653.tw1.ru | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
cw08653.tw1.ru |
| unknown |