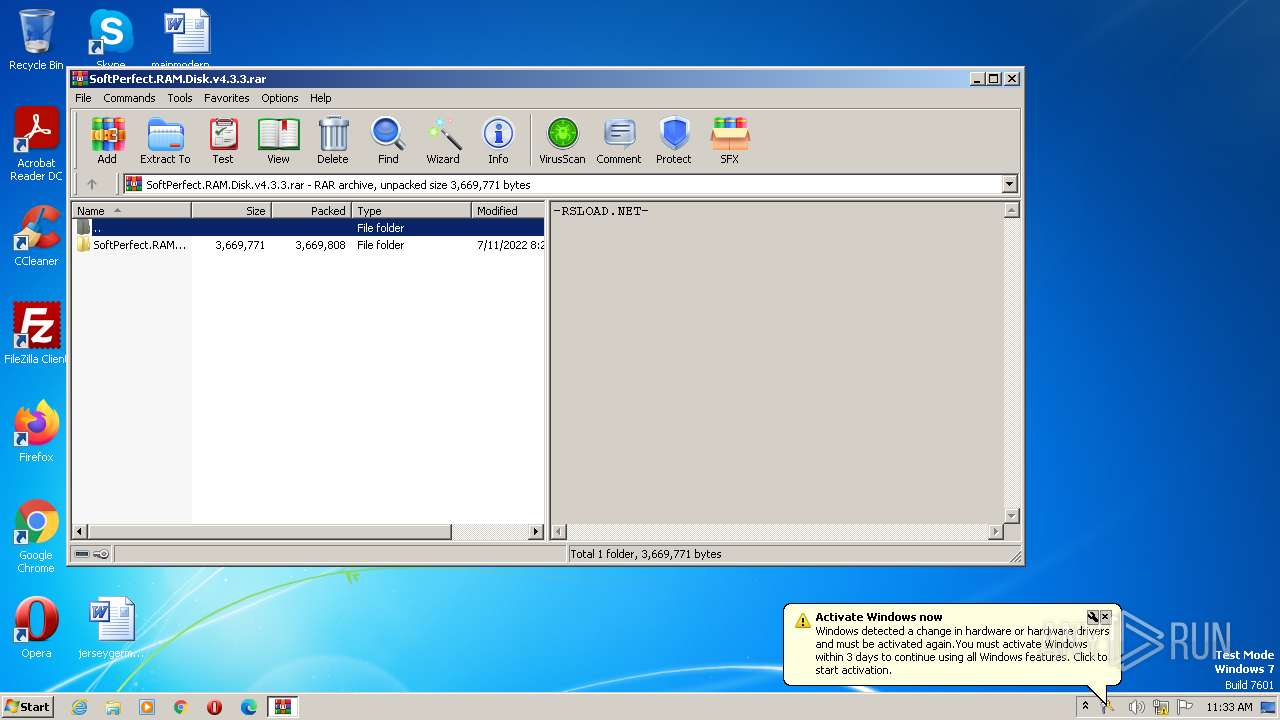
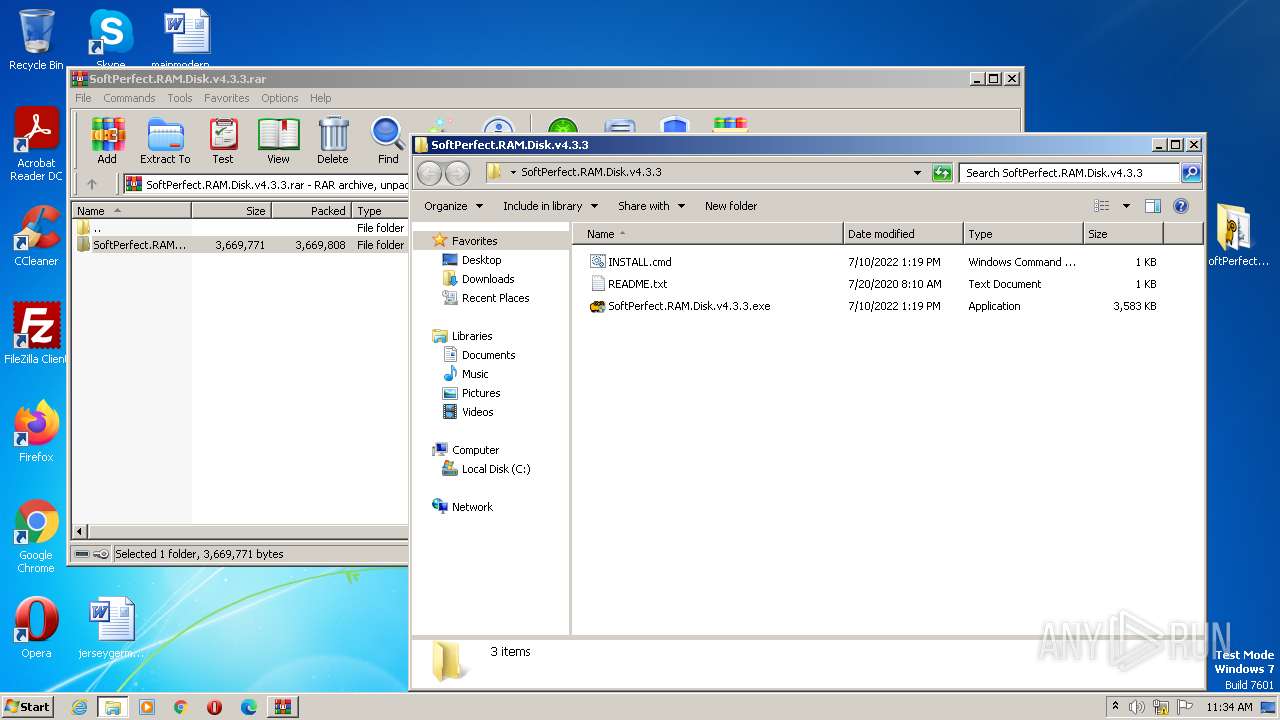
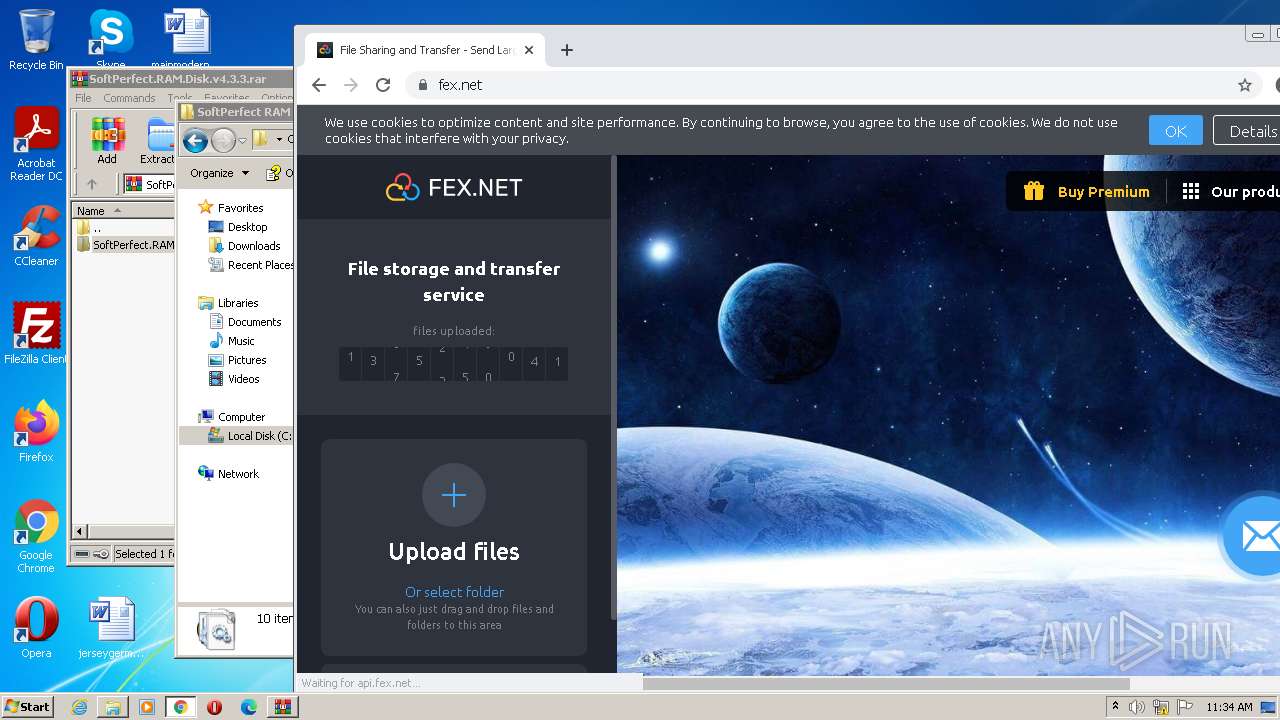
| File name: | SoftPerfect.RAM.Disk.v4.3.3.rar |
| Full analysis: | https://app.any.run/tasks/41b41709-0dc0-4216-8e71-33d4ed99235d |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2023, 10:33:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
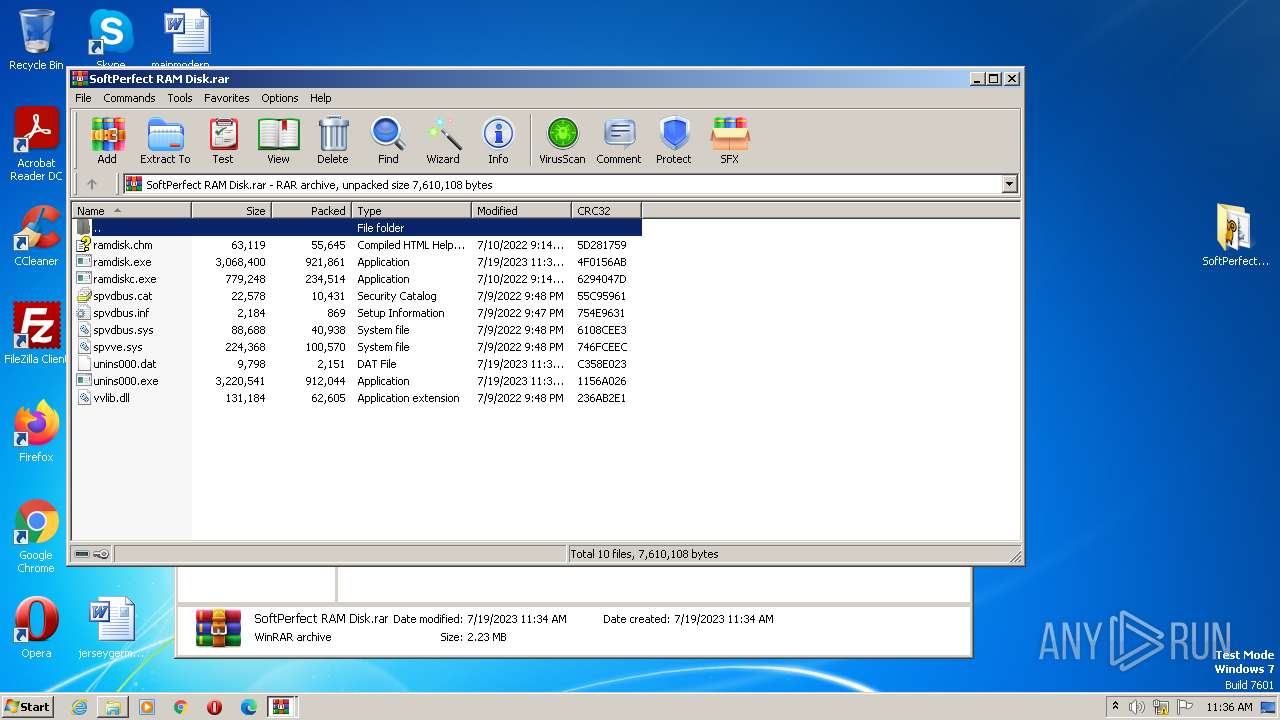
| File info: | RAR archive data, v5 |
| MD5: | 09067BE8C984AE010598334C6C794D7D |
| SHA1: | CDF2E6B6D907E6403ED085C051E32287B14D65C1 |
| SHA256: | FB59B0CD2EDEA44BD1B4E6FDA6536DBF747809966DA7D4729FA899831DD52A10 |
| SSDEEP: | 98304:BCV+c/gBq542Y+p+o8QYNyuwPlJFVhW+SAMDX5jHF:A+WgWZY+p+QuMlJFVEH39jl |
MALICIOUS
Application was dropped or rewritten from another process
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 1424)
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- package.exe (PID: 3188)
- ramdisk.exe (PID: 1996)
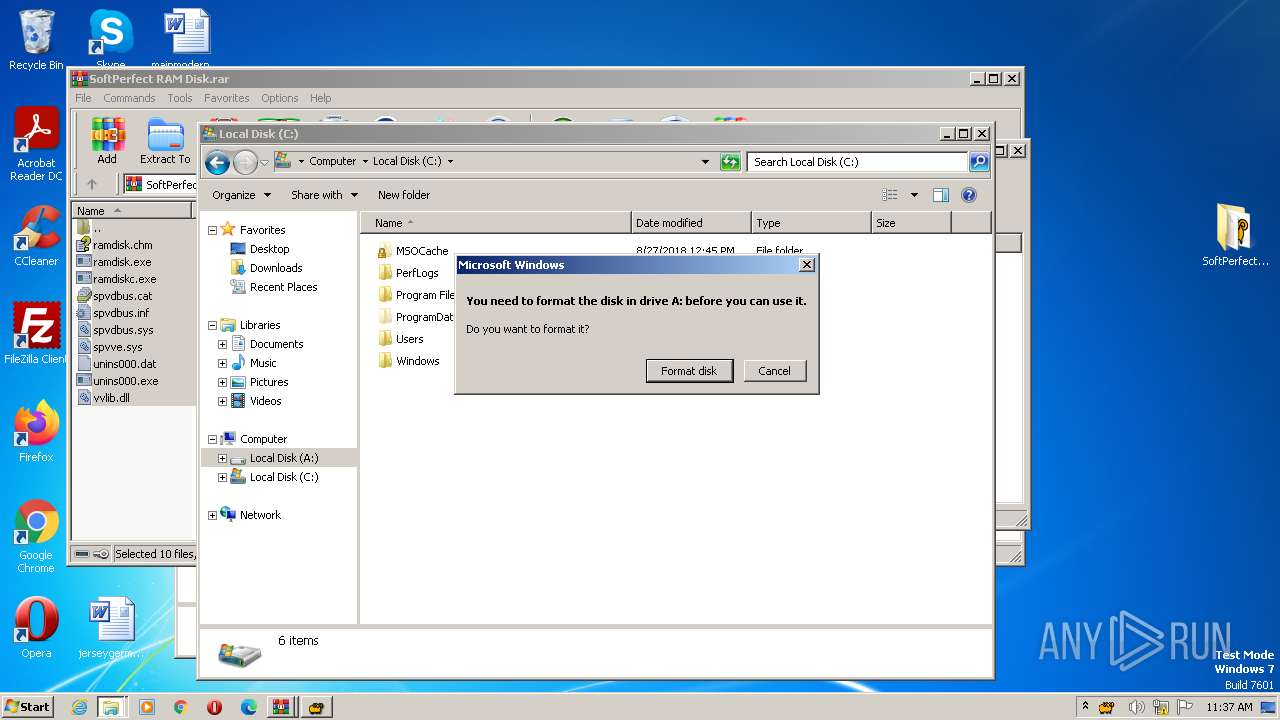
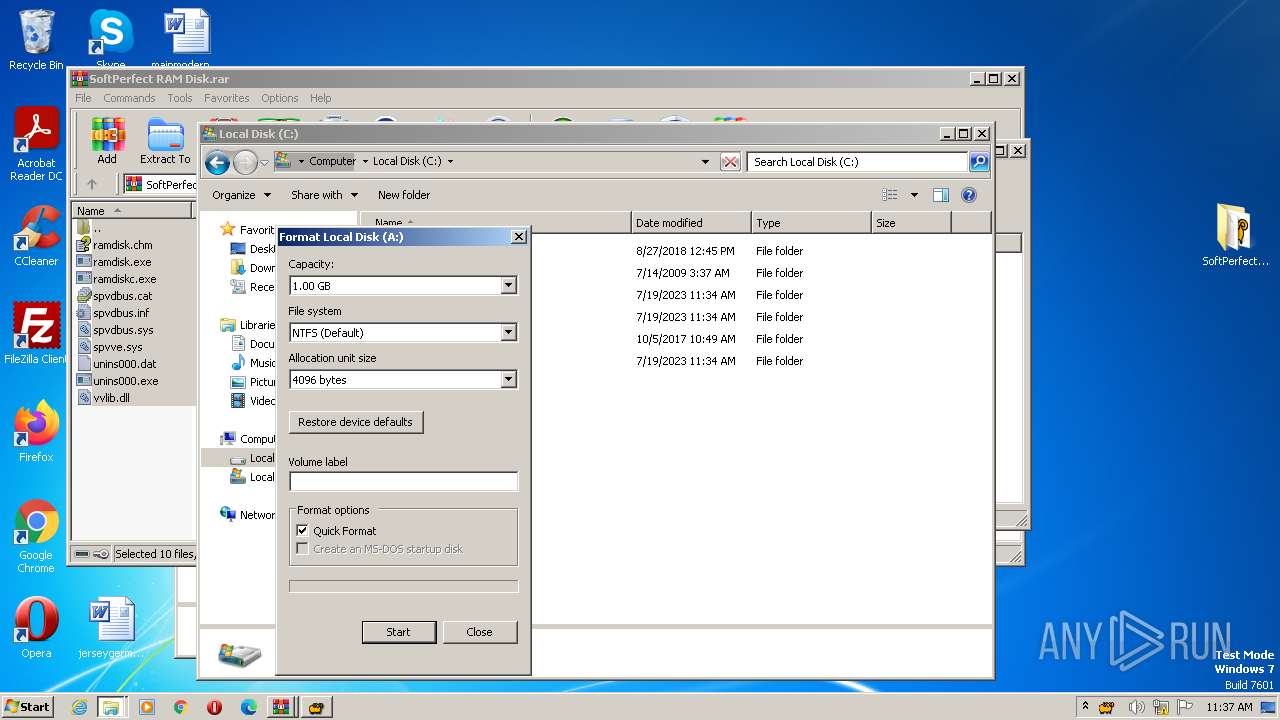
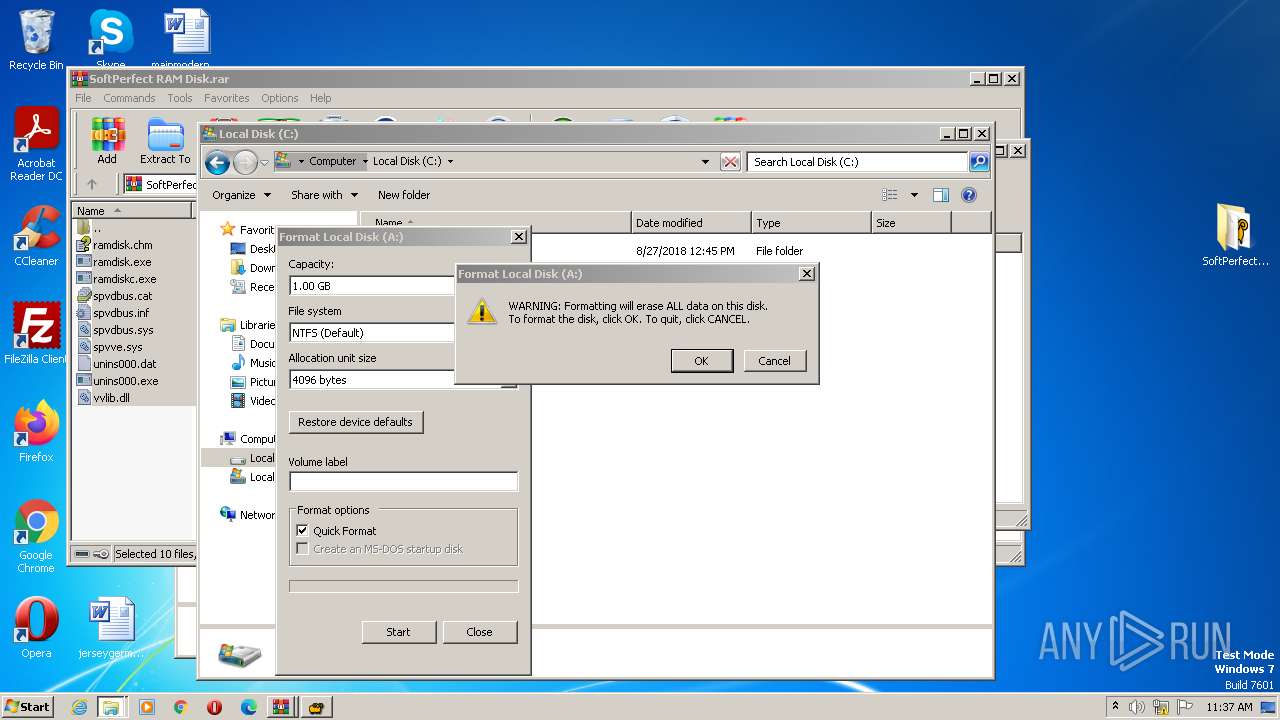
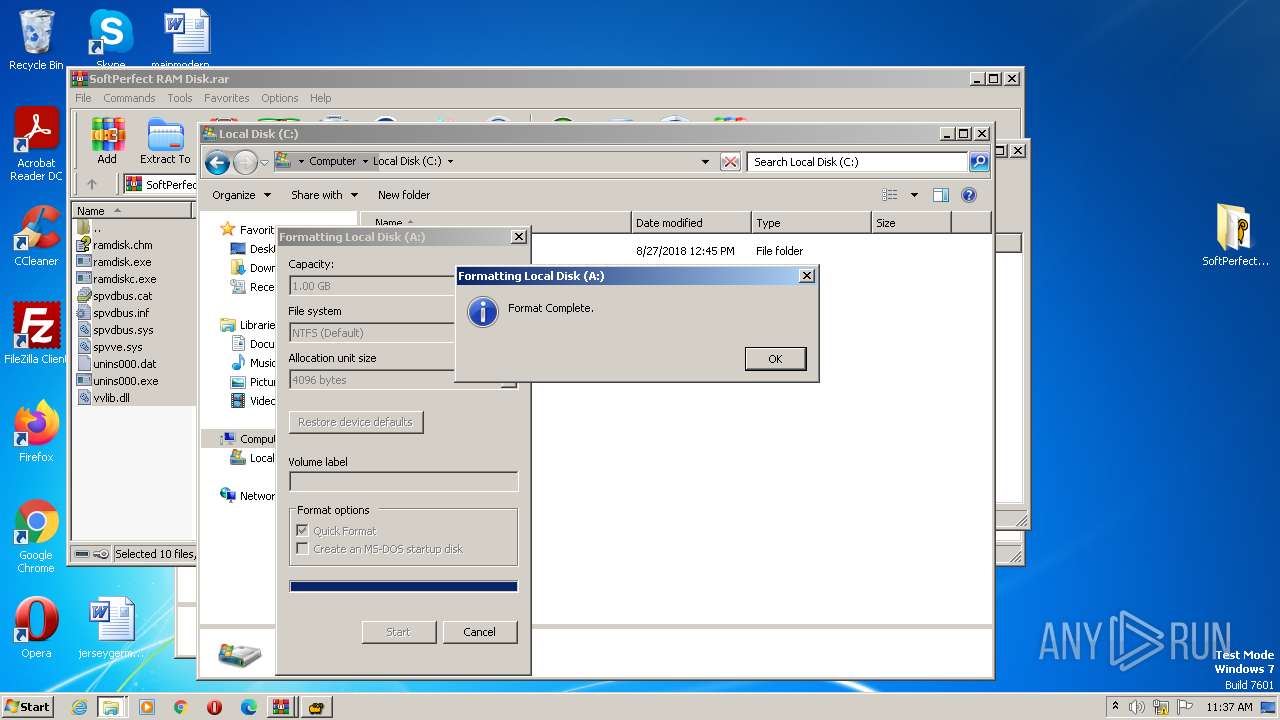
Creates a writable file the system directory
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Loads dropped or rewritten executable
- ramdisk.exe (PID: 1996)
SUSPICIOUS
Reads the Internet Settings
- explorer.exe (PID: 1312)
Executable content was dropped or overwritten
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- package.exe (PID: 3188)
- package.tmp (PID: 3724)
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
- explorer.exe (PID: 1312)
Reads the Windows owner or organization settings
- package.tmp (PID: 3724)
Drops a system driver (possible attempt to evade defenses)
- package.tmp (PID: 3724)
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
- explorer.exe (PID: 1312)
- WinRAR.exe (PID: 3168)
Creates files in the driver directory
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Reads security settings of Internet Explorer
- ramdisk.exe (PID: 1996)
Adds/modifies Windows certificates
- package.tmp (PID: 3724)
Checks Windows Trust Settings
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Reads settings of System Certificates
- ramdisk.exe (PID: 1996)
Executes as Windows Service
- VSSVC.exe (PID: 564)
Image mount is detect
- drvinst.exe (PID: 3108)
The process creates files with name similar to system file names
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
Searches for installed software
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
Application launched itself
- WinRAR.exe (PID: 1348)
INFO
Reads the computer name
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- package.tmp (PID: 3724)
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Create files in a temporary directory
- package.exe (PID: 3188)
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- package.tmp (PID: 3724)
- ramdisk.exe (PID: 1996)
The process checks LSA protection
- package.tmp (PID: 3724)
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- VSSVC.exe (PID: 564)
- drvinst.exe (PID: 3108)
Manual execution by a user
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 1424)
- WinRAR.exe (PID: 1348)
- chrome.exe (PID: 1420)
Checks supported languages
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- package.exe (PID: 3188)
- package.tmp (PID: 3724)
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3396)
- WinRAR.exe (PID: 3168)
Creates files in the program directory
- package.tmp (PID: 3724)
- SoftPerfect.RAM.Disk.v4.3.3.exe (PID: 3120)
- WinRAR.exe (PID: 2572)
Application was dropped or rewritten from another process
- package.tmp (PID: 3724)
Reads the machine GUID from the registry
- ramdisk.exe (PID: 1996)
- drvinst.exe (PID: 3172)
- drvinst.exe (PID: 3108)
Application launched itself
- chrome.exe (PID: 1420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
96
Monitored processes
41
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\system32\certutil.exe" -addstore TrustedPublisher "C:\Users\admin\AppData\Local\Temp\is-F2CO4.tmp\SOFTPERFECT-SHA256.cer" | C:\Windows\System32\certutil.exe | — | package.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 564 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1312 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
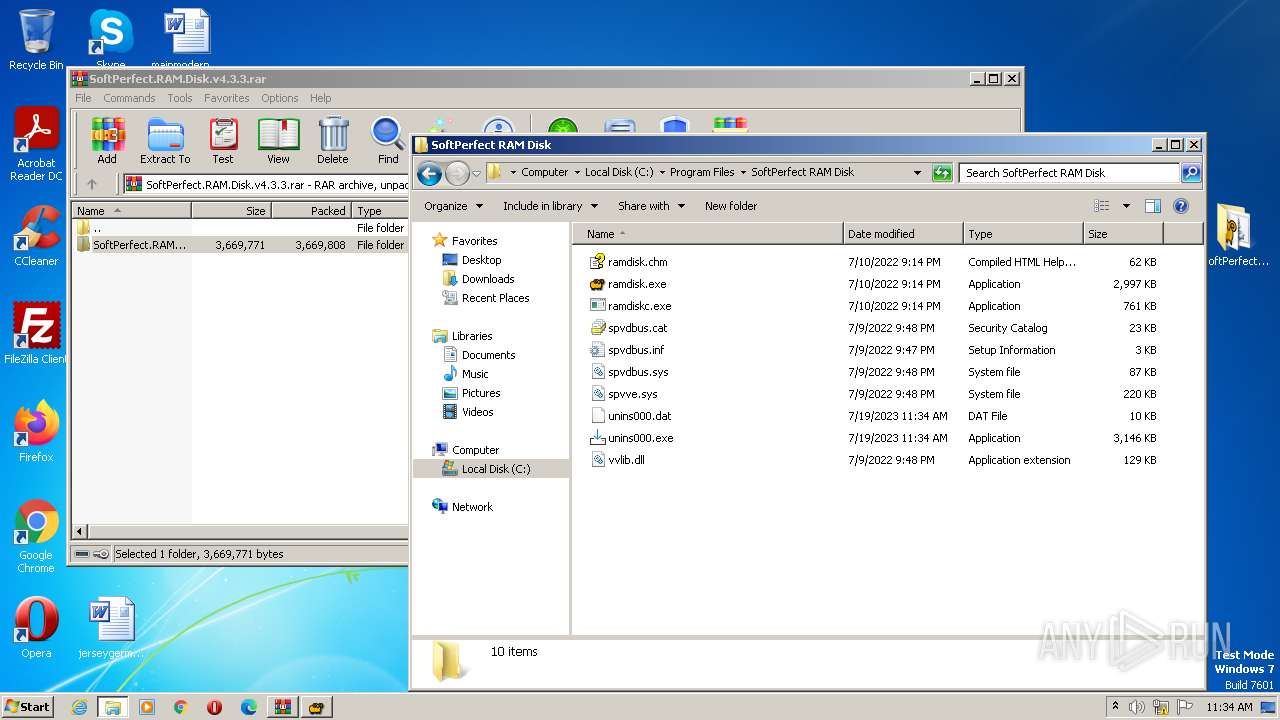
| 1348 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- "SoftPerfect RAM Disk.rar" "C:\Program Files\SoftPerfect RAM Disk\spvdbus.inf" "C:\Program Files\SoftPerfect RAM Disk\spvdbus.sys" "C:\Program Files\SoftPerfect RAM Disk\spvve.sys" "C:\Program Files\SoftPerfect RAM Disk\unins000.dat" "C:\Program Files\SoftPerfect RAM Disk\unins000.exe" "C:\Program Files\SoftPerfect RAM Disk\vvlib.dll" "C:\Program Files\SoftPerfect RAM Disk\ramdisk.chm" "C:\Program Files\SoftPerfect RAM Disk\ramdisk.exe" "C:\Program Files\SoftPerfect RAM Disk\ramdiskc.exe" "C:\Program Files\SoftPerfect RAM Disk\spvdbus.cat" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1424 | "C:\Users\admin\Desktop\SoftPerfect.RAM.Disk.v4.3.3\SoftPerfect.RAM.Disk.v4.3.3.exe" | C:\Users\admin\Desktop\SoftPerfect.RAM.Disk.v4.3.3\SoftPerfect.RAM.Disk.v4.3.3.exe | — | explorer.exe | |||||||||||
User: admin Company: SoftPerfect Pty Ltd, Australia Integrity Level: MEDIUM Description: SoftPerfect RAM Disk v4.3.3 Exit code: 3221226540 Version: 4.3.3.0 Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5076500294943419027,3469805085183020287,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | |||||||||||||||
| 1864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,5076500294943419027,3469805085183020287,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3692 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 | |||||||||||||||
| 1996 | "C:\Program Files\SoftPerfect RAM Disk\ramdisk.exe" /install | C:\Program Files\SoftPerfect RAM Disk\ramdisk.exe | package.tmp | ||||||||||||
User: admin Company: SoftPerfect Pty Ltd Integrity Level: HIGH Description: RAM Disk GUI Exit code: 0 Version: 4.3.3.0 Modules
| |||||||||||||||
| 2012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1036,5076500294943419027,3469805085183020287,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1324 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
23 750
Read events
23 440
Write events
301
Delete events
9
Modification events
| (PID) Process: | (1312) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D00000000020000000000106600000001000020000000822A0AA37BD64DCF095E29F2164E703AE1EF09DC1955E37D2B5F07EC0D9DC876000000000E8000000002000020000000F6E5170D8E8A54BFA6283D84BEAC0836AD43E5CA79E0A347C63795856F407CCD30000000DB0B43955438667F03B8BCD40CBCD0EABF1FBC25F8908345B213D91299A931295DA98D90C9DD2FE8B8A74D8FEACAC4CA400000008AA373F50207B8273EF7C69FA9F8561955D51D29923A7A8A80A32E3F89E7449663AE1558D12A01F64A3ADE7CB625A4122DEA863FC64BC78A4C38008A4C7E43A5 | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1312) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\JvaENE\JvaENE.rkr |
Value: 000000000700000005000000408A0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFA0B93321CCFAD80100000000 | |||
Executable files
51
Suspicious files
221
Text files
154
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | SoftPerfect.RAM.Disk.v4.3.3.exe | C:\Users\admin\AppData\Local\Temp\nsu442.tmp\package.exe | executable | |
MD5:5A9621B6429957AD95D860F083C99BBE | SHA256:C057347EFEFD0D1865A7A9541B38F70B7C2BFF9F79B256119CFCBD0868A87DF8 | |||
| 3724 | package.tmp | C:\Program Files\SoftPerfect RAM Disk\ramdisk.exe | executable | |
MD5:CF9EF9C5A05D6B880829B995446C396B | SHA256:A1F430C4299BE70AF3FCDEF0C042527BFB10C095EDFC53F6F07A040D023A1216 | |||
| 3396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3396.31912\SoftPerfect.RAM.Disk.v4.3.3\SoftPerfect.RAM.Disk.v4.3.3.exe | executable | |
MD5:048771183BC9B038CA6DCFFDFA76CCF6 | SHA256:138E2955000790387907575416FC72F9CD479D36B125C02E88D1560980F5DF4E | |||
| 3724 | package.tmp | C:\Program Files\SoftPerfect RAM Disk\ramdiskc.exe | executable | |
MD5:BB0570EB93D1213BD80C2BF111D1BA89 | SHA256:6B1A2BA0DEE178E0FEC80A86B56601468DE52C0F5E175378C6943F17229A08F6 | |||
| 3724 | package.tmp | C:\Program Files\SoftPerfect RAM Disk\is-1JNLT.tmp | binary | |
MD5:8A1778C82DC1DF5C7ACC7386643F6C8A | SHA256:33947498255120E7C816FC34F73ECC95AAEB15664E075749AB919F169A743F1B | |||
| 3188 | package.exe | C:\Users\admin\AppData\Local\Temp\is-G4UP7.tmp\package.tmp | executable | |
MD5:A553416EEA92A030550E92CCC6C03A2F | SHA256:72EEB5A3F401DDB18711E12CC896F4E5CEDFF86B35F2F4A844CC4568787868F2 | |||
| 3396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3396.31912\SoftPerfect.RAM.Disk.v4.3.3\INSTALL.cmd | text | |
MD5:93415BFBC48BA0F6431BABCCE1C4166B | SHA256:E0BDEE2467574CB7B1C1FAEA8D9F9E1EBAE4D0D6B45C2992ADBA37DF2ED5AC9A | |||
| 3724 | package.tmp | C:\Program Files\SoftPerfect RAM Disk\unins000.exe | executable | |
MD5:9F132F8EA26C2C50C420E5CBED12AFE5 | SHA256:90297C9629FE634A07F7623E9ECDAE4EC7CACD9A887D295915111AEB077F8087 | |||
| 3396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3396.31912\SoftPerfect.RAM.Disk.v4.3.3\README.txt | text | |
MD5:139F91F43B6A7499EDB7CE1DEF710C06 | SHA256:5A9D30F1C1A1D3B7AE67A465070E196A157FA995C7064B7D8748CA9EE8BD3A2D | |||
| 3724 | package.tmp | C:\Users\admin\AppData\Local\Temp\is-F2CO4.tmp\SOFTPERFECT-SHA1.cer | binary | |
MD5:AC082F394BB0FE6A21728C26CB9894EE | SHA256:AF4685F575A5F4D3043B0A2925920A859134B57227BB3FFA6445834B9648E375 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
70
DNS requests
28
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lms6amzobyeijpfweyxwnkhs6m_2979/jflookgnkcckhobaglndicnbbgbonegd_2979_all_ac4jcxoro6e2pxwrezxb4qpgtkzq.crx3 | US | — | — | whitelisted |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | binary | 242 Kb | whitelisted |
— | — | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e531e0c2cbaf0694 | US | compressed | 62.3 Kb | whitelisted |
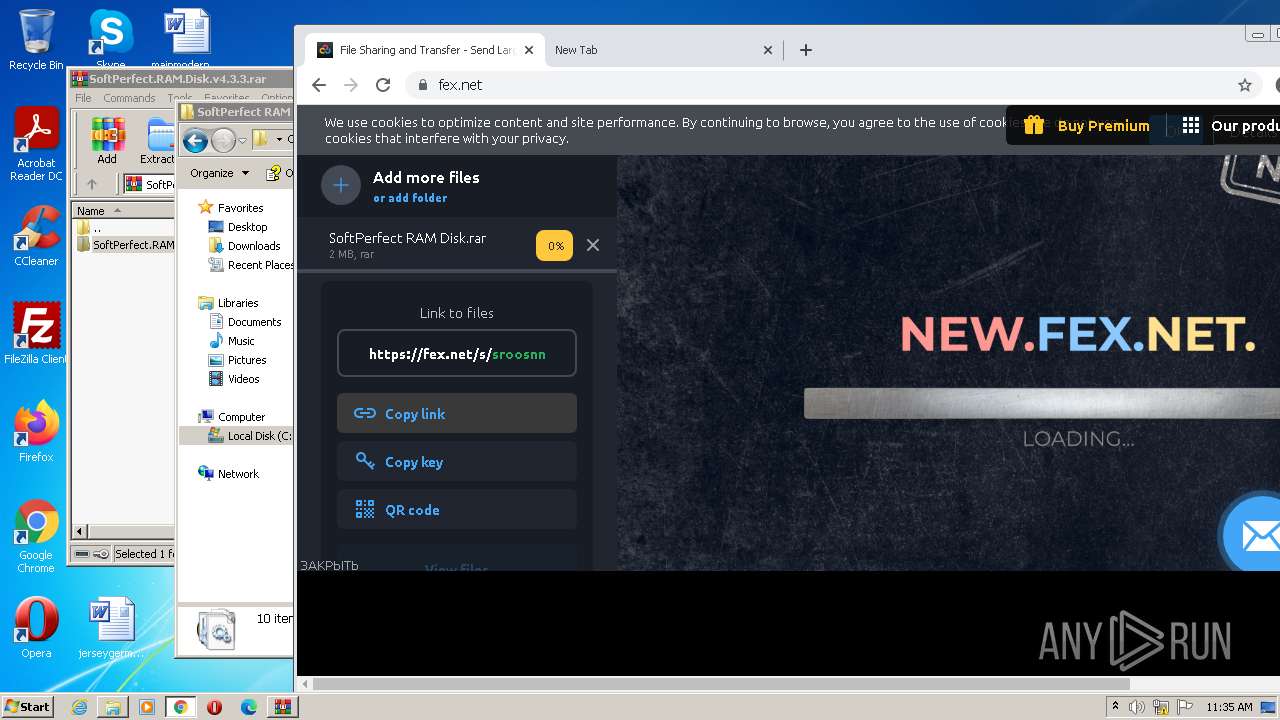
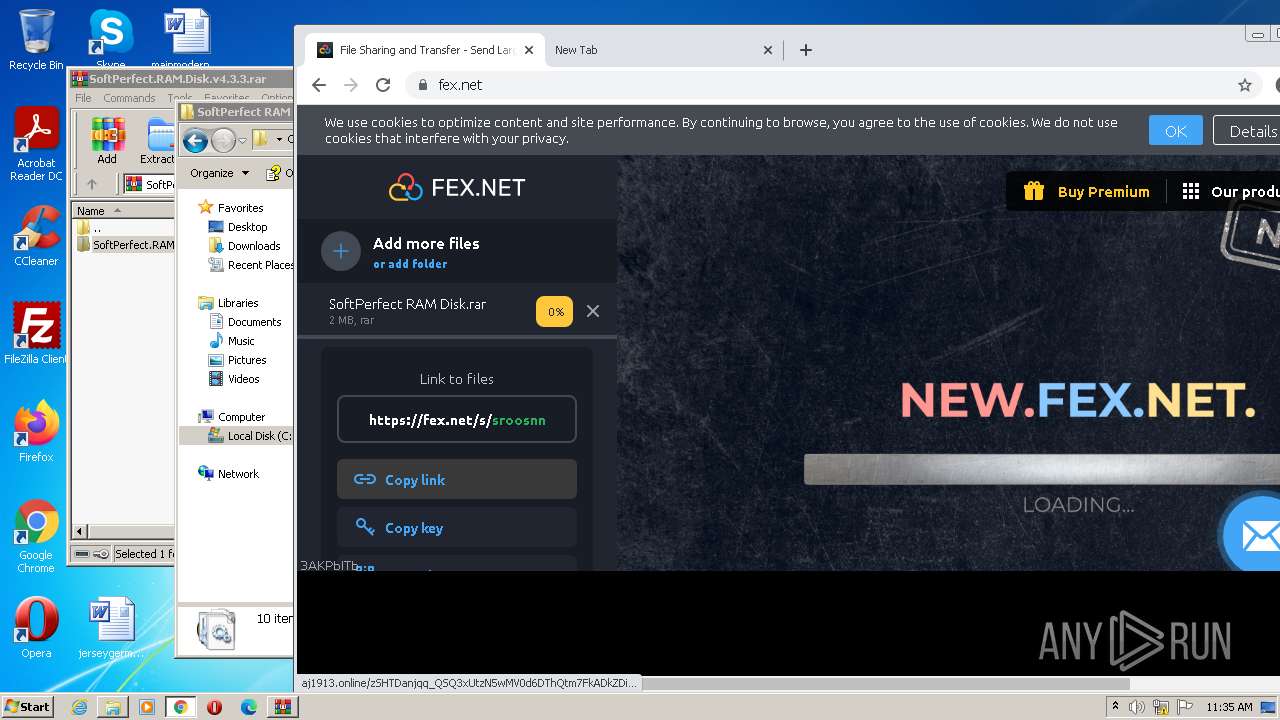
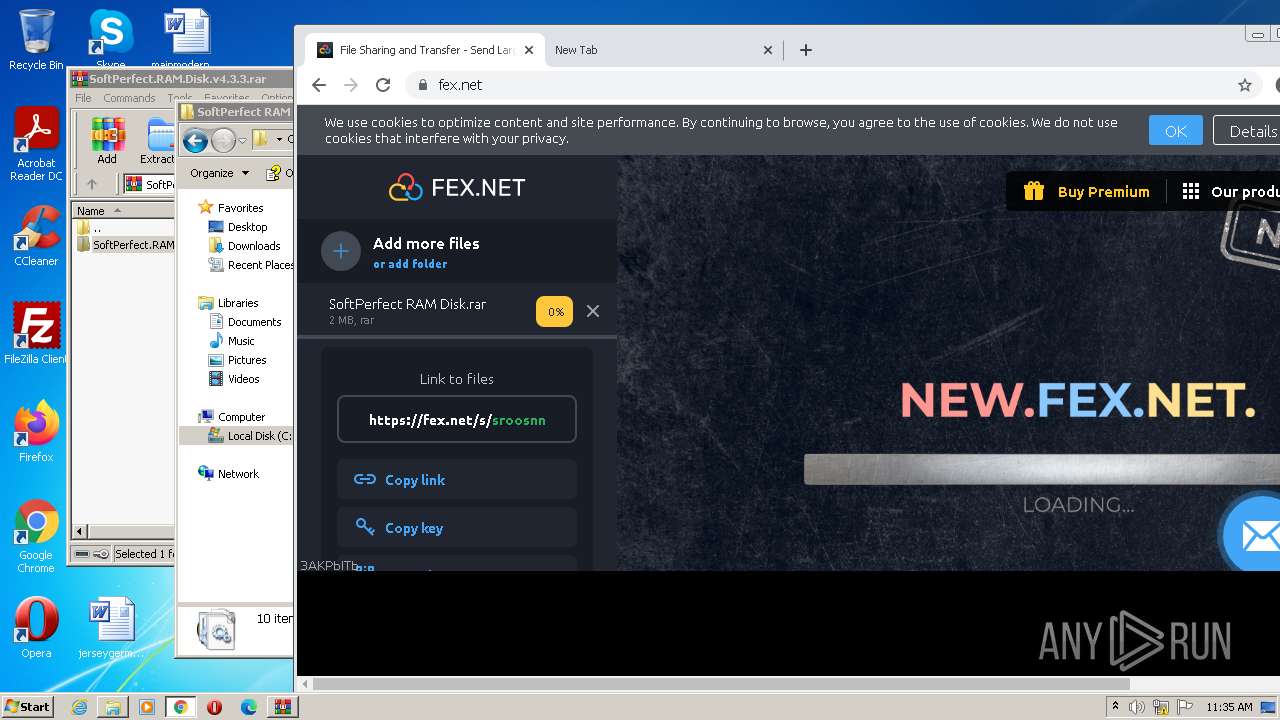
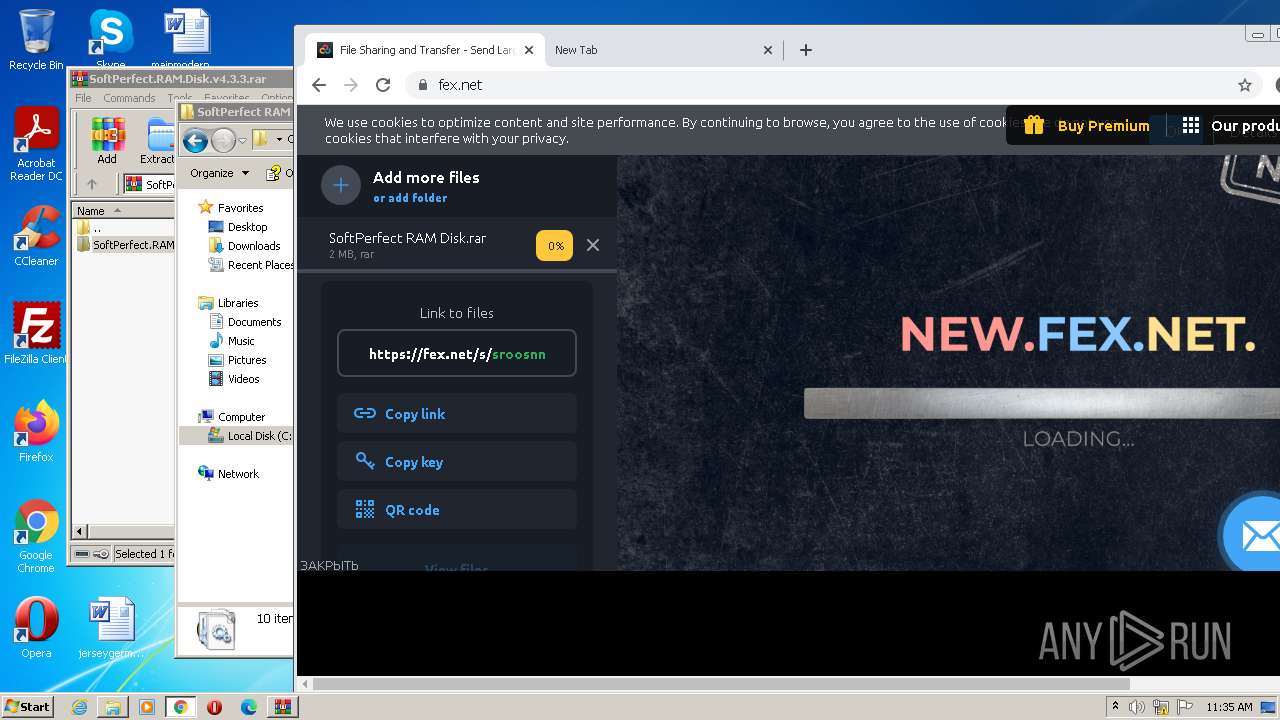
— | — | GET | 301 | 194.106.216.70:80 | http://fex.net/ | UA | html | 185 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1068 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 172.217.18.14:443 | clients2.google.com | GOOGLE | US | whitelisted |
2012 | chrome.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.45:443 | accounts.google.com | GOOGLE | US | suspicious |
— | — | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 194.106.216.70:80 | fex.net | TOV IT-Park | UA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
fex.net |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdn.polyfill.io |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed (fex .net in DNS Lookup) |
— | — | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed (fex .net in TLS SNI) |
— | — | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed (fex .net in TLS SNI) |
1 ETPRO signatures available at the full report