| URL: | https://github.com/Endermanch/MalwareDatabase/blob/master/ransomwares/7ev3n.zip |
| Full analysis: | https://app.any.run/tasks/8faaf4f9-52e7-4456-9aa5-f3fa9ba1b3dd |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 16:44:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 09DABCD6A4480E01C5F419CC31E01389 |
| SHA1: | C61E9ABD34525CC15EE7D42D569D4BF99EA3ECDA |
| SHA256: | FB31AC008C536DE57C8BECAF2F8463EFFA0C029691DCE6B65819E9D07088FABA |
| SSDEEP: | 3:N8tEdegLaKoEJ3PqkzEHcEie+m/lV:2ufLtfnz+cEizm/lV |
MALICIOUS
Changes the autorun value in the registry
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
- AV.EXE (PID: 2636)
- RtlDriver32.exe (PID: 3972)
Scans artifacts that could help determine the target
- dw20.exe (PID: 7492)
- dw20.exe (PID: 804)
Connects to the CnC server
- DB.EXE (PID: 7208)
- KBDINMARO.exe (PID: 7600)
- DB.EXE (PID: 3268)
- Windowsu.exe (PID: 7312)
- Windowsu.exe (PID: 5572)
- KBDINMARO.exe (PID: 5884)
PONMOCUP has been detected (SURICATA)
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
Modifies hosts file to block updates
- Windowsu.exe (PID: 7312)
SUSPICIOUS
Reads security settings of Internet Explorer
- Endermanch@Ana.exe (PID: 4644)
- EN.EXE (PID: 4772)
- DB.EXE (PID: 7208)
- KBDINMARO.exe (PID: 7600)
- Endermanch@Ana.exe (PID: 5172)
- EN.EXE (PID: 7880)
- DB.EXE (PID: 3268)
- Windowsu.exe (PID: 7312)
- AV.EXE (PID: 2636)
- KBDINMARO.exe (PID: 5884)
- Windowsu.exe (PID: 5572)
Reads the date of Windows installation
- Endermanch@Ana.exe (PID: 4644)
- EN.EXE (PID: 4772)
- dw20.exe (PID: 7492)
- KBDINMARO.exe (PID: 7600)
- Endermanch@Ana.exe (PID: 5172)
- EN.EXE (PID: 7880)
- Windowsu.exe (PID: 7312)
- AV.EXE (PID: 2636)
- Windowsu.exe (PID: 5572)
- KBDINMARO.exe (PID: 5884)
- dw20.exe (PID: 804)
Executable content was dropped or overwritten
- Endermanch@Ana.exe (PID: 4644)
- SB.EXE (PID: 7180)
- DB.EXE (PID: 7208)
- Endermanch@Ana.exe (PID: 5172)
- SB.EXE (PID: 5044)
- DB.EXE (PID: 3268)
- AV.EXE (PID: 2636)
Drops the executable file immediately after the start
- Endermanch@Ana.exe (PID: 4644)
- SB.EXE (PID: 7180)
- DB.EXE (PID: 7208)
- Endermanch@Ana.exe (PID: 5172)
- SB.EXE (PID: 5044)
- DB.EXE (PID: 3268)
- AV.EXE (PID: 2636)
Starts CMD.EXE for commands execution
- EN.EXE (PID: 4772)
- DB.EXE (PID: 7208)
- EN.EXE (PID: 7880)
- DB.EXE (PID: 3268)
Hides command output
- cmd.exe (PID: 1184)
- cmd.exe (PID: 8124)
Reads the BIOS version
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
Executing commands from a ".bat" file
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
The process executes via Task Scheduler
- setup3420925556.exe (PID: 7480)
- PLUGScheduler.exe (PID: 3560)
Contacting a server suspected of hosting an CnC
- DB.EXE (PID: 7208)
- KBDINMARO.exe (PID: 7600)
- DB.EXE (PID: 3268)
- Windowsu.exe (PID: 7312)
- KBDINMARO.exe (PID: 5884)
- Windowsu.exe (PID: 5572)
Process uses IPCONFIG to clear DNS cache
- KBDINMARO.exe (PID: 7600)
- Windowsu.exe (PID: 7312)
- Windowsu.exe (PID: 5572)
- KBDINMARO.exe (PID: 5884)
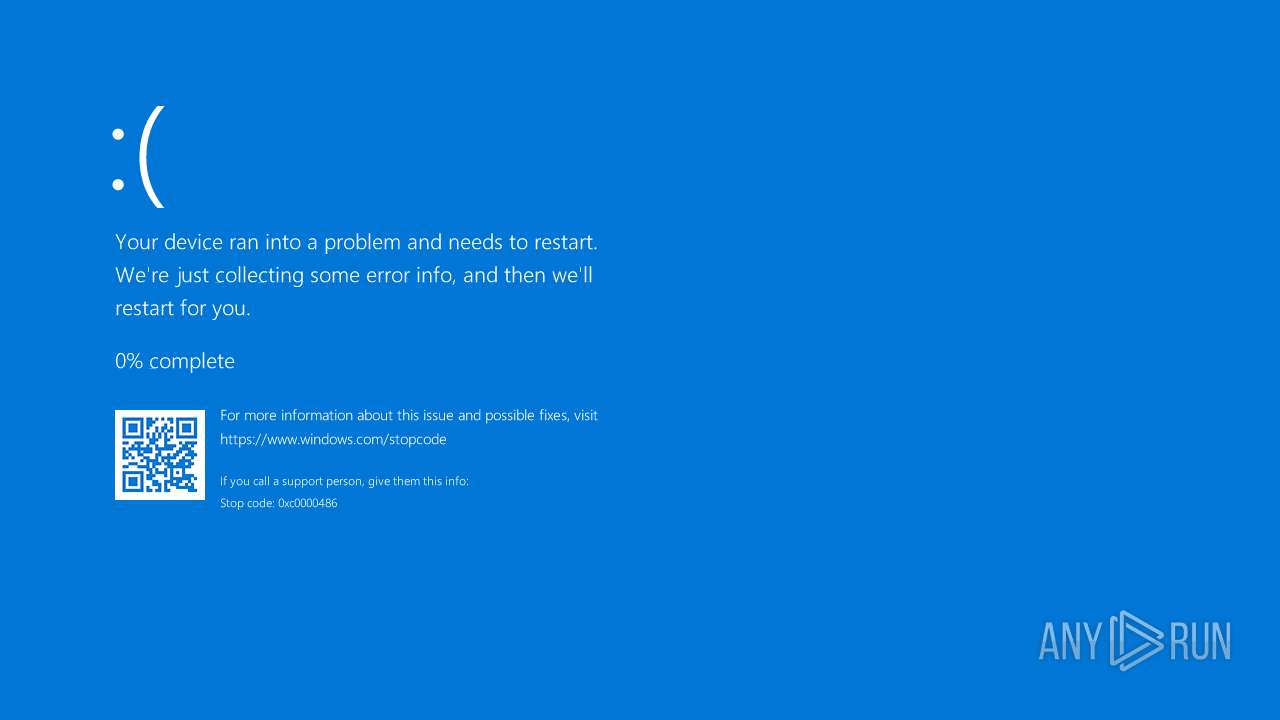
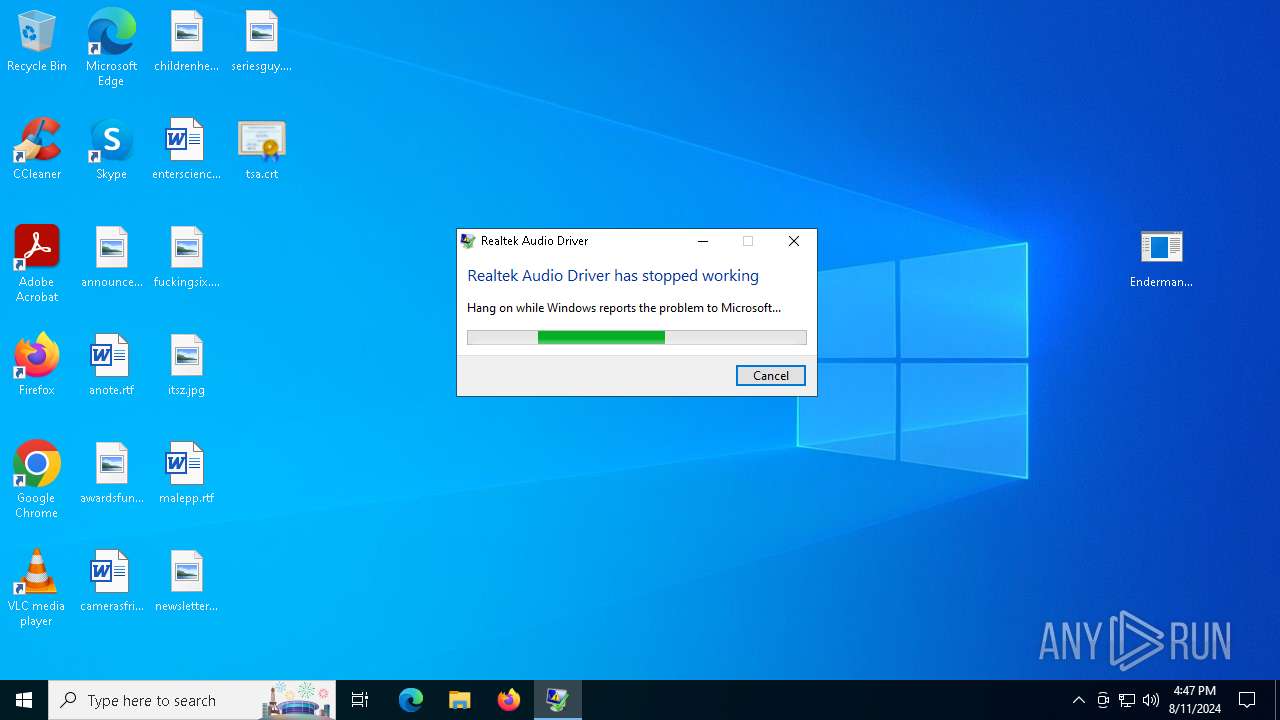
Executes application which crashes
- AV2.EXE (PID: 7184)
- AV2.EXE (PID: 6908)
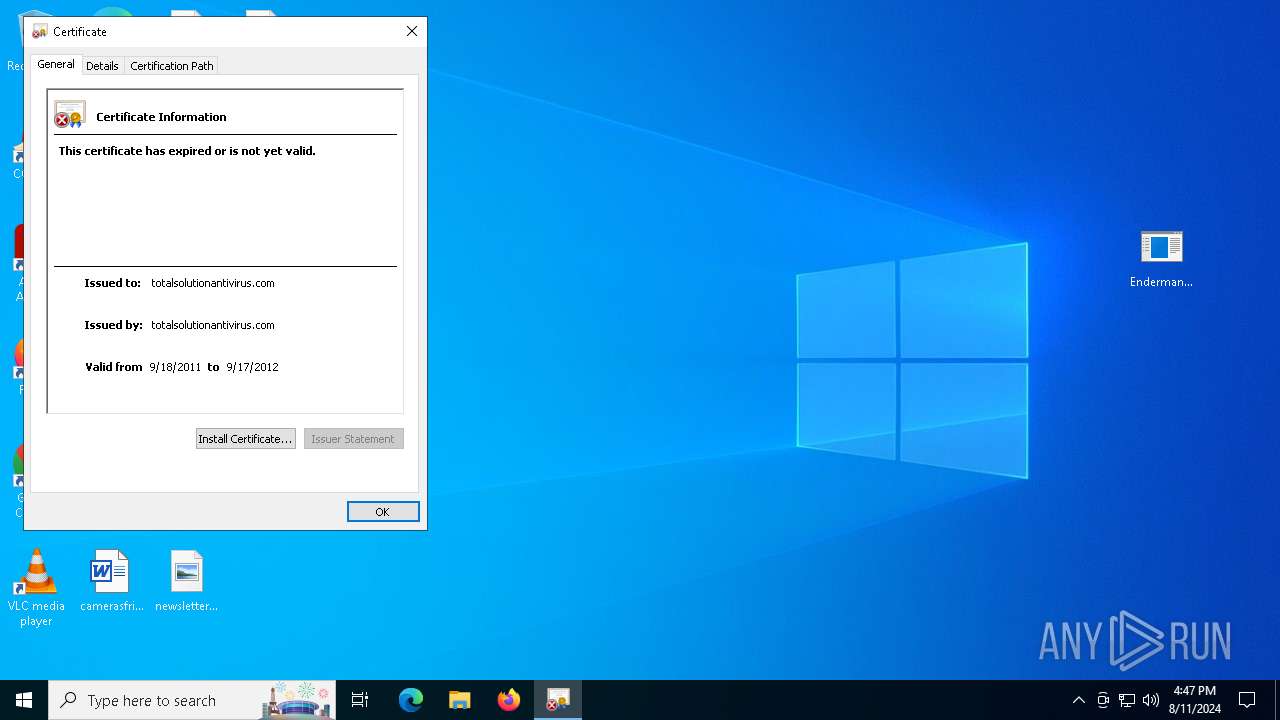
Adds/modifies Windows certificates
- AV.EXE (PID: 2636)
Starts itself from another location
- AV.EXE (PID: 2636)
INFO
The process uses the downloaded file
- chrome.exe (PID: 6460)
- chrome.exe (PID: 7808)
- WinRAR.exe (PID: 8024)
Application launched itself
- chrome.exe (PID: 6460)
Manual execution by a user
- Endermanch@Ana.exe (PID: 4644)
- Endermanch@Ana.exe (PID: 5172)
- Windowsu.exe (PID: 5572)
- KBDINMARO.exe (PID: 5884)
- RtlDriver32.exe (PID: 4076)
- rundll32.exe (PID: 5556)
- mspaint.exe (PID: 5552)
- mspaint.exe (PID: 6080)
Checks supported languages
- Endermanch@Ana.exe (PID: 4644)
- AV2.EXE (PID: 7184)
- AV.EXE (PID: 7188)
- DB.EXE (PID: 7208)
- EN.EXE (PID: 4772)
- SB.EXE (PID: 7180)
- KBDINMARO.exe (PID: 7600)
- dw20.exe (PID: 7492)
- Endermanch@Ana.exe (PID: 5172)
- DB.EXE (PID: 3268)
- AV.EXE (PID: 2636)
- AV2.EXE (PID: 6908)
- EN.EXE (PID: 7880)
- SB.EXE (PID: 5044)
- Windowsu.exe (PID: 7312)
- RtlDriver32.exe (PID: 3972)
- PLUGScheduler.exe (PID: 3560)
- KBDINMARO.exe (PID: 5884)
- RtlDriver32.exe (PID: 4076)
- dw20.exe (PID: 804)
- Windowsu.exe (PID: 5572)
Reads the computer name
- Endermanch@Ana.exe (PID: 4644)
- DB.EXE (PID: 7208)
- EN.EXE (PID: 4772)
- SB.EXE (PID: 7180)
- dw20.exe (PID: 7492)
- KBDINMARO.exe (PID: 7600)
- Endermanch@Ana.exe (PID: 5172)
- DB.EXE (PID: 3268)
- EN.EXE (PID: 7880)
- AV.EXE (PID: 2636)
- Windowsu.exe (PID: 7312)
- RtlDriver32.exe (PID: 3972)
- PLUGScheduler.exe (PID: 3560)
- KBDINMARO.exe (PID: 5884)
- dw20.exe (PID: 804)
- Windowsu.exe (PID: 5572)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8024)
Create files in a temporary directory
- Endermanch@Ana.exe (PID: 4644)
- SB.EXE (PID: 7180)
- EN.EXE (PID: 4772)
- DB.EXE (PID: 7208)
- Endermanch@Ana.exe (PID: 5172)
- EN.EXE (PID: 7880)
- DB.EXE (PID: 3268)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6460)
- EN.EXE (PID: 4772)
- EN.EXE (PID: 7880)
Process checks computer location settings
- Endermanch@Ana.exe (PID: 4644)
- EN.EXE (PID: 4772)
- dw20.exe (PID: 7492)
- KBDINMARO.exe (PID: 7600)
- Endermanch@Ana.exe (PID: 5172)
- EN.EXE (PID: 7880)
- Windowsu.exe (PID: 7312)
- AV.EXE (PID: 2636)
- KBDINMARO.exe (PID: 5884)
- Windowsu.exe (PID: 5572)
- dw20.exe (PID: 804)
Reads Windows Product ID
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
Checks proxy server information
- DB.EXE (PID: 7208)
- EN.EXE (PID: 4772)
- KBDINMARO.exe (PID: 7600)
- dw20.exe (PID: 7492)
- WerFault.exe (PID: 7720)
- DB.EXE (PID: 3268)
- EN.EXE (PID: 7880)
- Windowsu.exe (PID: 7312)
- WerFault.exe (PID: 3272)
- RtlDriver32.exe (PID: 3972)
- Windowsu.exe (PID: 5572)
- KBDINMARO.exe (PID: 5884)
- dw20.exe (PID: 804)
Process checks whether UAC notifications are on
- DB.EXE (PID: 7208)
- DB.EXE (PID: 3268)
Reads the machine GUID from the registry
- AV.EXE (PID: 7188)
- dw20.exe (PID: 7492)
- AV.EXE (PID: 2636)
- RtlDriver32.exe (PID: 3972)
- dw20.exe (PID: 804)
Creates files in the program directory
- dw20.exe (PID: 7492)
- PLUGScheduler.exe (PID: 3560)
- dw20.exe (PID: 804)
Failed to create an executable file in Windows directory
- DB.EXE (PID: 7208)
Creates files or folders in the user directory
- DB.EXE (PID: 7208)
- WerFault.exe (PID: 7720)
- AV.EXE (PID: 2636)
- WerFault.exe (PID: 3272)
Reads Environment values
- dw20.exe (PID: 7492)
- RtlDriver32.exe (PID: 3972)
- dw20.exe (PID: 804)
Reads product name
- dw20.exe (PID: 7492)
- dw20.exe (PID: 804)
Reads CPU info
- dw20.exe (PID: 7492)
- dw20.exe (PID: 804)
Reads the software policy settings
- dw20.exe (PID: 7492)
- WerFault.exe (PID: 7720)
- WerFault.exe (PID: 3272)
- dw20.exe (PID: 804)
- rundll32.exe (PID: 5556)
Disables trace logs
- RtlDriver32.exe (PID: 3972)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 5556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
308
Monitored processes
55
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | dw20.exe -x -s 828 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | RtlDriver32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\WINDOWS\system32\ipconfig.exe" /flushdns | C:\Windows\SysWOW64\ipconfig.exe | — | Windowsu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\system32\cmd.exe" /c del C:\Users\admin\AppData\Local\Temp\EN.EXE > nul | C:\Windows\SysWOW64\cmd.exe | — | EN.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
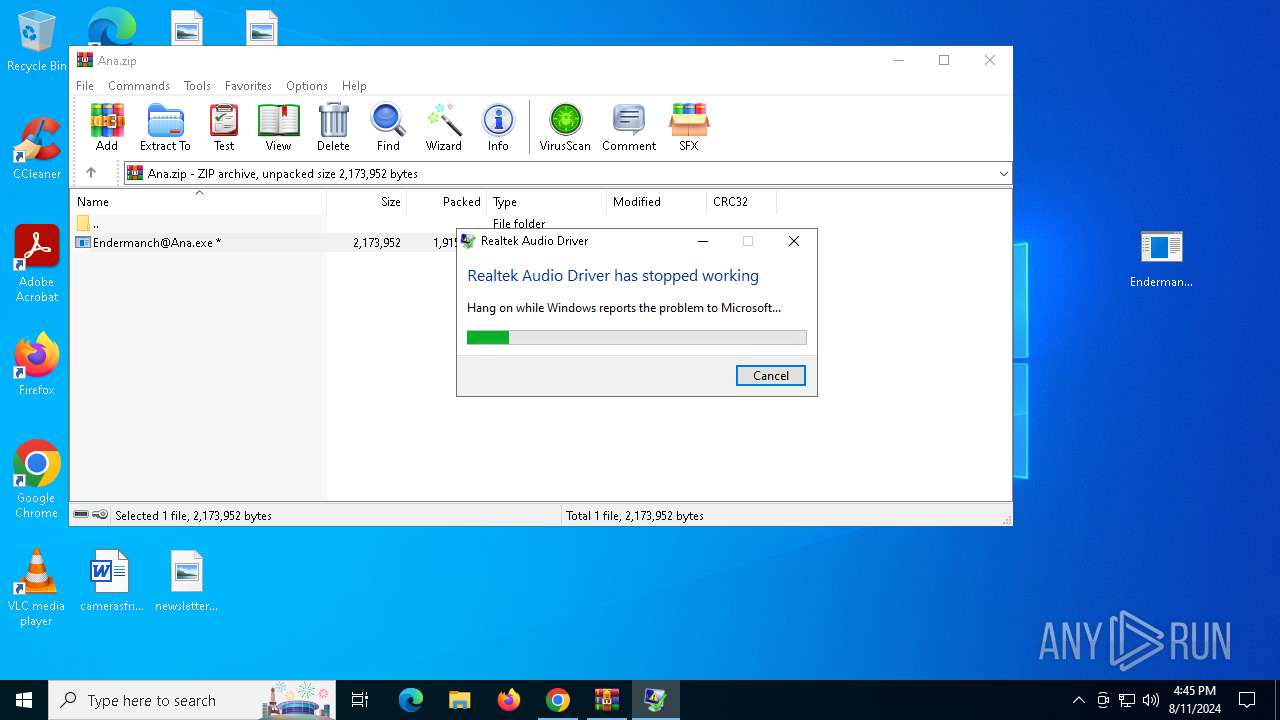
| 2636 | "C:\Users\admin\AppData\Local\Temp\AV.EXE" | C:\Users\admin\AppData\Local\Temp\AV.EXE | Endermanch@Ana.exe | ||||||||||||
User: admin Company: Realtek Inc Integrity Level: HIGH Description: Realtek Audio Driver Exit code: 0 Version: 2.0.5.0 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Local\Temp\DB.EXE" | C:\Users\admin\AppData\Local\Temp\DB.EXE | Endermanch@Ana.exe | ||||||||||||
User: admin Company: Prjfeusek Vdceboszrya Integrity Level: HIGH Description: Internet Connection Wizard Exit code: 0 Version: 6.00.3790.3959 (srv03_sp2_rtm.070216-1710) Modules
| |||||||||||||||
| 3272 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6908 -s 520 | C:\Windows\SysWOW64\WerFault.exe | AV2.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Roaming\RtlDriver32.exe" | C:\Users\admin\AppData\Roaming\RtlDriver32.exe | AV.EXE | ||||||||||||
User: admin Company: Realtek Inc Integrity Level: HIGH Description: Realtek Audio Driver Exit code: 0 Version: 2.0.5.0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Roaming\RtlDriver32.exe" | C:\Users\admin\AppData\Roaming\RtlDriver32.exe | explorer.exe | ||||||||||||
User: admin Company: Realtek Inc Integrity Level: MEDIUM Description: Realtek Audio Driver Exit code: 3762507597 Version: 2.0.5.0 Modules
| |||||||||||||||
Total events
61 230
Read events
60 940
Write events
282
Delete events
8
Modification events
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
16
Suspicious files
81
Text files
30
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe5c06.TMP | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe5c16.TMP | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\5825e0f5-2f55-400e-878f-a600326e2be2.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 6460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
95
DNS requests
68
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3276 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6284 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6236 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7208 | DB.EXE | GET | 404 | 66.96.162.135:80 | http://middlechrist.com/html/license_43EC922A3D0E1F403834ED436BA90C5A686E606FE2C68C471F4CE42C93524A733C47010287CE9159E8D69FE5469D45CA6C2FF9970E4D13204AFCEB8A1C5A9D2924CF3F64589D6F4B3AEC76D3E9738A14F1ADD835BCB38CA101474E71EF1FEBE0D05B64D42BC1DF893E55EC01B14ED11EFA7D0FE3579860B4CE1454B4FD71AD155CE82075E84258727574468CA7B8E4750D0588C28010352C78091FE5FA59B3FCA76E237593366C3FDCE3427F6F805148EB96D9AA98435DD76B4AD29E9BA3051370DA8987DF04ACEB11E09B0ADE1883B3A5A839883C57BC594BA4757D547CFC1704914694CBE42A9D6DB43CCD406389BA07A85C686F3DE5951982B4FF8180099622488A032274C0E5C4E84EDFF2980FB836A6BBE6A566D9F2A64CC15BCFEF6BD599C003C3C0901749C3B5EC7E18CCEF85E04AD5B01EFE1391DA97947F699819576498A45B485C7DA67D259980984C6245CCAEE3379A81A9917916EF6A3D8E44D044C4A57BC9D1222F1AC88AC78A4B0380001058730E154BB8.html | unknown | — | — | malicious |
7208 | DB.EXE | GET | 404 | 66.96.162.135:80 | http://middlechrist.com/html/license_43EC922A3D0E1F403834ED436BA90C5A686E606FE2C68C471F4CE42C93524A733C47010287CE9159E8D69FE5469D45CA6C2FF9970E4D13204AFCEB8A1C5A9D2924CF3F64589D6F4B3AEC76D3E9738A14F1ADD835BCB38CA101474E71EF1FEBE0D05B64D42BC1DF893E55EC01B14ED11EFA7D0FE3579860B4CE1454B4FD71AD155CE82075E84258727574468CA7B8E4750D0588C28010352C78091FE5FA59B3FCA76E237593366C3FDCE3427F6F805148EB96D9AA98435DD76B4AD29E9BA3051370DA8987DF04ACEB11E09B0ADE1883B3A5A839883C57BC594BA4757D547CFC1704914694CBE42A9D6DB43CCD406389BA07A85C686F3DE5951982B4FF8180099622488A032274C0E5C4E84EDFF2980FB836A6BBE6A566D9F2A64CC15BCFEF6BD599C003C3C0901749C3B5EC7E18CCEF85E04AD5B01EFE1391DA97947F699819576498A45B485C7DA67D259980984C6245CCAEE3379A81A9917916EF6A3D8E44D044C4A57BC9D1222F1AC88AC78A4B0380001058730E154BB87F47EE77836AADFEA38D4479E7C0943880301F0EF5A371525DAF3D4DA58D0F2AA0401DF0B6A4CA6C589C87B4B16F6C2B8795175CDA1E7E5BC48E937946834186D28CAF542EE00F88DE893B6DC2E9EA3BD427E0577187739547924D74F6D387CE5BAD5CB90E6100E09F65991998B50E4DEB10C027378426247A4DD000FCB4FD34F0FB164B5F7BCE1903E35C9E35304336AE94370DFD58954280E591D9AFAF895DCBF5E732B9B7F4405F3672DF6504C1CAA4055F0DB1FA123A707583E6CE6D6F5AC3BA097C39B223C4D5200D3985ED3DEE5DEADFAF0E500F4530AB5AF58AE0CF3FC0E763E5ED297B7DD6654B1C5E8151BD3AFE5E2EF952AB5CFD423075C049AA218B84A746B116737A779CBCE20A98C6584588.html | unknown | — | — | malicious |
7600 | KBDINMARO.exe | GET | 200 | 172.67.139.136:80 | http://imagehut4.cn/update/utu.dat | unknown | — | — | malicious |
7884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
7884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
7884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/kfpt3ft3qn5zdit2cqelm5iuke_20240801.659754589.14/obedbbhbpmojnkanicioggnmelmoomoc_20240801.659754589.14_all_ENUS500000_ad7q7ox2phy7bmfr67n2bc3oh2bq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3068 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2424 | RUXIMICS.exe | 52.185.211.133:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2120 | MoUsoCoreWorker.exe | 52.185.211.133:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6460 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6732 | chrome.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
6732 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
6732 | chrome.exe | 185.199.111.154:443 | github.githubassets.com | FASTLY | US | unknown |
6732 | chrome.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
collector.github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6732 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6732 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7208 | DB.EXE | Malware Command and Control Activity Detected | ET MALWARE Ponmocup C2 Post-infection Checkin |
7208 | DB.EXE | A Network Trojan was detected | ET MALWARE Spoofed MSIE 8 User-Agent Likely Ponmocup |
7600 | KBDINMARO.exe | Malware Command and Control Activity Detected | ET MALWARE Request for utu.dat Likely Ponmocup checkin |
7208 | DB.EXE | A Network Trojan was detected | ET MALWARE Spoofed MSIE 8 User-Agent Likely Ponmocup |
7208 | DB.EXE | Malware Command and Control Activity Detected | ET MALWARE Ponmocup C2 Post-infection Checkin |
3268 | DB.EXE | Malware Command and Control Activity Detected | ET MALWARE Ponmocup C2 Post-infection Checkin |
3268 | DB.EXE | A Network Trojan was detected | ET MALWARE Spoofed MSIE 8 User-Agent Likely Ponmocup |
3268 | DB.EXE | Malware Command and Control Activity Detected | ET MALWARE Ponmocup C2 Post-infection Checkin |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV2.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\DB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\EN.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\GB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\SB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\AV2.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\DB.EXE |
Endermanch@Ana.exe | C:\Users\admin\AppData\Local\Temp\EN.EXE |