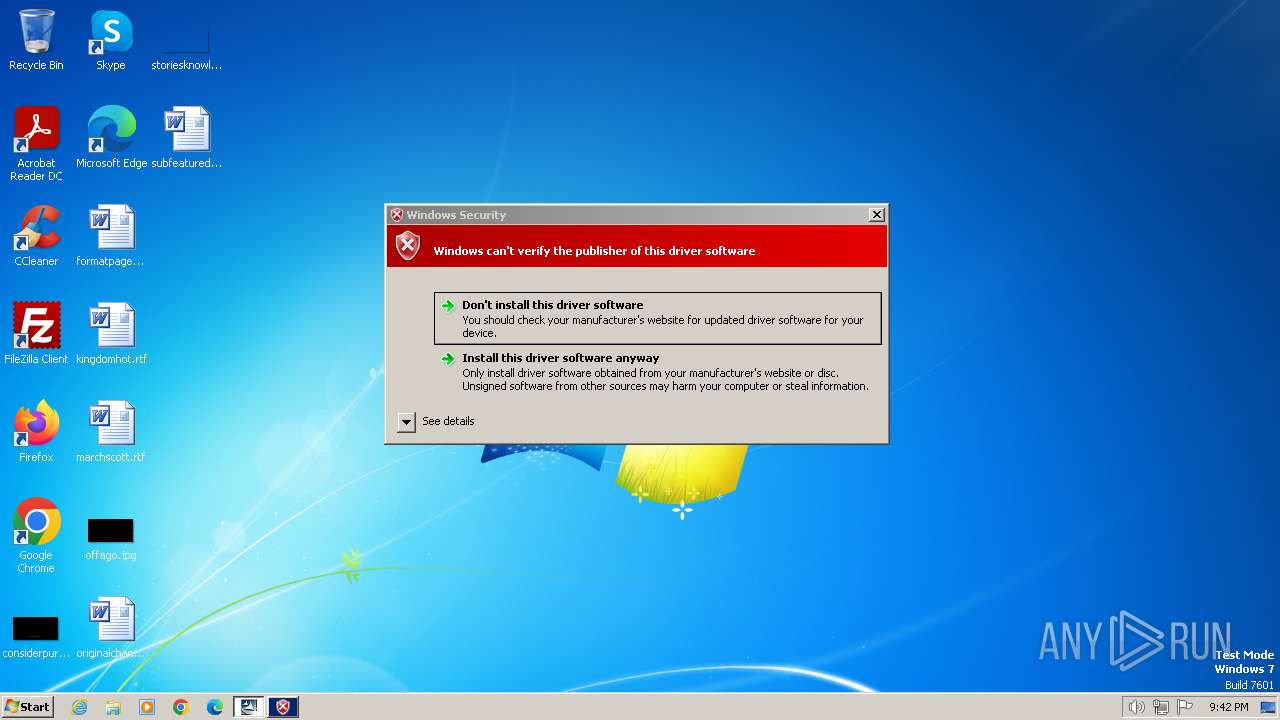
| File name: | DPPFP50W01.exe |
| Full analysis: | https://app.any.run/tasks/97e47390-9d69-4272-b6c0-49a651503503 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2024, 21:41:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | FB0C82BE9882ABFA6341631179B73817 |
| SHA1: | 4CC472154B5153D330DA6D7CF230D82E0F209FB3 |
| SHA256: | FAC44591FCDF75447AD1D99653C7B652C52A3EAD2CD4AC434A6603D7B2D8DCB8 |
| SSDEEP: | 98304:CrjJlFOxC4aDyXBGQ4qgPP4U2HELPeDETDQvav315RSDDn2o9P9Zfh9QQ5v3aqRO:gwVV+BEk1P7/9 |
MALICIOUS
Drops the executable file immediately after the start
- DPPFP50W01.exe (PID: 3392)
- Setup.exe (PID: 1848)
- DPPFP50W01.exe (PID: 3996)
- drvinst.exe (PID: 3984)
- _INS5576._MP (PID: 1816)
Creates a writable file in the system directory
- _INS5576._MP (PID: 1816)
- drvinst.exe (PID: 3984)
SUSPICIOUS
Application launched itself
- DPPFP50W01.exe (PID: 3392)
Searches for installed software
- DPPFP50W01.exe (PID: 3996)
- dllhost.exe (PID: 2596)
Executable content was dropped or overwritten
- DPPFP50W01.exe (PID: 3996)
- Setup.exe (PID: 1848)
- _INS5576._MP (PID: 1816)
- drvinst.exe (PID: 3984)
Creates/Modifies COM task schedule object
- DPPFP50W01.exe (PID: 3996)
Executes as Windows Service
- VSSVC.exe (PID: 2688)
Process drops legitimate windows executable
- DPPFP50W01.exe (PID: 3996)
- _INS5576._MP (PID: 1816)
Drops a system driver (possible attempt to evade defenses)
- DPPFP50W01.exe (PID: 3996)
- _INS5576._MP (PID: 1816)
The process drops C-runtime libraries
- DPPFP50W01.exe (PID: 3996)
Starts application with an unusual extension
- Setup.exe (PID: 1848)
Creates files in the driver directory
- drvinst.exe (PID: 3984)
- _INS5576._MP (PID: 1816)
Checks Windows Trust Settings
- drvinst.exe (PID: 3984)
Creates a software uninstall entry
- _INS5576._MP (PID: 1816)
Creates file in the systems drive root
- _ISDel.exe (PID: 2112)
INFO
Checks supported languages
- DPPFP50W01.exe (PID: 3392)
- DPPFP50W01.exe (PID: 3996)
- Redist.exe (PID: 2336)
- _INS5576._MP (PID: 1816)
- _ISDel.exe (PID: 2112)
- drvinst.exe (PID: 3984)
- Setup.exe (PID: 1848)
- mildrv.exe (PID: 2632)
Reads the computer name
- DPPFP50W01.exe (PID: 3392)
- DPPFP50W01.exe (PID: 3996)
- _INS5576._MP (PID: 1816)
- _ISDel.exe (PID: 2112)
- Setup.exe (PID: 1848)
- drvinst.exe (PID: 3984)
- mildrv.exe (PID: 2632)
Create files in a temporary directory
- DPPFP50W01.exe (PID: 3996)
- Setup.exe (PID: 1848)
- _INS5576._MP (PID: 1816)
Creates files in the program directory
- DPPFP50W01.exe (PID: 3996)
- _INS5576._MP (PID: 1816)
Reads the machine GUID from the registry
- DPPFP50W01.exe (PID: 3996)
- drvinst.exe (PID: 3984)
Creates files or folders in the user directory
- DPPFP50W01.exe (PID: 3996)
Reads the software policy settings
- drvinst.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2002:12:02 18:31:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 58880 |
| InitializedDataSize: | 43008 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb1cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.1.100.1248 |
| ProductVersionNumber: | 7.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | InstallShield Software Corporation |
| FileDescription: | InstallShield (R) Setup Launcher |
| InternalName: | ISPNickel |
| OriginalFileName: | Setup.exe |
| FileVersion: | 7, 01, 100, 1248 |
| LegalCopyright: | Copyright (C) 1990-2002 InstallShield Software Corporation |
| ProductName: | InstallShield (R) |
| ProductVersion: | 7, 01 |
| OLESelfRegister: | - |
Total processes
50
Monitored processes
12
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1816 | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5576._MP | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5576._MP | Setup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield Engine Exit code: 0 Version: 5, 53, 168, 0 Modules
| |||||||||||||||
| 1848 | setup.exe REDISTRIBUTION RESPONSEFILE="C:\Windows\temp\dpp-fp50\response.txt" -s | C:\Windows\Temp\dpp-fp50\Redist\Matrox\Setup.exe | Redist.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: 32-bit Setup Launcher Exit code: 0 Version: 5, 52, 164, 0 Modules
| |||||||||||||||
| 2112 | C:\Windows\Temp\dpp-fp50\Redist\Matrox\_ISDEL.EXE | C:\Windows\Temp\dpp-fp50\Redist\Matrox\_ISDel.exe | — | Setup.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: 32-bit InstallShield Deleter. Exit code: 0 Version: 5, 51, 138, 0 Modules
| |||||||||||||||
| 2336 | C:\Windows\Temp\dpp-fp50\Redist\Matrox\Redist.exe REDISTRIBUTION RESPONSEFILE="C:\Windows\temp\dpp-fp50\response.txt" -s | C:\Windows\Temp\dpp-fp50\Redist\Matrox\Redist.exe | — | DPPFP50W01.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2596 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | c:\PROGRA~1\MATROX~1\drivers\vga\drivernt\mildrv.exe mtxdma 0 -pcmemorysize=2097152 -noinfo | C:\Program Files\Matrox Imaging\drivers\VGA\drivernt\mildrv.exe | — | _INS5576._MP | |||||||||||
User: admin Integrity Level: HIGH Description: mildrv MFC Application Exit code: 0 Version: 1, 0, 0, 6 Modules
| |||||||||||||||
| 2688 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3088 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 10 Global\{111e36d7-1165-7190-7382-164e4058d912} Global\{23ced1b2-a78f-010b-41cb-b72c9e69c151} C:\Windows\System32\DriverStore\Temp\{29100710-699e-51c1-b631-673e02ccd720}\oemsetup.inf C:\Windows\System32\DriverStore\Temp\{29100710-699e-51c1-b631-673e02ccd720}\DPPFP50.CAT | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Temp\DPPFP50W01.exe" | C:\Users\admin\AppData\Local\Temp\DPPFP50W01.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield (R) Setup Launcher Version: 7, 01, 100, 1248 Modules
| |||||||||||||||
| 3984 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{52f742a4-5548-7f22-5e5c-f000a73be15c}\oemsetup.inf" "0" "607d98887" "000003DC" "WinSta0\Default" "000004B0" "208" "C:\Windows\Temp\DPP-FP50" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 162
Read events
7 715
Write events
443
Delete events
4
Modification events
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F4817E4B-04B6-11D3-8862-00C04F72F303}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2068-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{AA7E2066-CB55-11D2-8094-00104B1F9838}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{CC096170-E2CB-11D2-80C8-00104B1F6CEA}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B11-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B13-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B12-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B10-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B16-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3996) DPPFP50W01.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{8C3C1B15-E59D-11D2-B40B-00A024B9DDDD}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
224
Suspicious files
80
Text files
131
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\ISPackFiles.ini | text | |
MD5:E0A11DA95202FFD0FA848A7805762D0E | SHA256:10E0604BC985324F367F813371A3E12CF1626E016866739241FB2706F305437F | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\bye29CA.tmp\Disk1\data1.hdr | hdr | |
MD5:591AB9680BE76F8B92CFC5A0F96B0B07 | SHA256:A41034F3647F919557388C8B9FAFD290A55BE6A5B0D01B227DF8C8521DE0F1F3 | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\bye29CA.tmp\Disk1\data1.cab | compressed | |
MD5:93604B99933333F936A8038B9537D66B | SHA256:76D11AEA6EB052CF06052FAB3B3058F138B5FB645B2B1B219E569C3032A75CCD | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\bye29CA.tmp\Disk1\setup.ini | ini | |
MD5:EA92C2EAF833DF7302F55F2FAD9E0412 | SHA256:B474DF06D25C34ADEC7DCFF33533DCED9A43BA24FC8EE1A5BCFEDC169C08749C | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\set2A0B.tmp | ex_ | |
MD5:43FFFEF9A91B39FED4196111BAC39640 | SHA256:D6FCCDBE022BE8D79DD40FA3D1BC29C284C19A3471CC5B7DB7657496C1381D61 | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\isp2A0A.tmp\temp.000 | executable | |
MD5:E148C1132A32CCD424DE346F2FFEAD1F | SHA256:04E326274A3F687E7640A0219A53B7F59D61CA6E6F7320FDE5D2EB7FA01290C5 | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\set2AA9.tmp | ex_ | |
MD5:43FFFEF9A91B39FED4196111BAC39640 | SHA256:D6FCCDBE022BE8D79DD40FA3D1BC29C284C19A3471CC5B7DB7657496C1381D61 | |||
| 3996 | DPPFP50W01.exe | C:\Program Files\Common Files\InstallShield\Professional\RunTime\0701\Intel32\isp2AA8.tmp\Setup.dll | executable | |
MD5:E148C1132A32CCD424DE346F2FFEAD1F | SHA256:04E326274A3F687E7640A0219A53B7F59D61CA6E6F7320FDE5D2EB7FA01290C5 | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\_isdelet.ini | text | |
MD5:36DE13DD51C51C8BFD25A16864C02978 | SHA256:0EDB2E4379A6804BFBFCE9F2F3EC0006A0B500C5EA55F3D6A04543EC371DFD03 | |||
| 3996 | DPPFP50W01.exe | C:\Users\admin\AppData\Local\Temp\bye29CA.tmp\Disk1\setup.exe | executable | |
MD5:5B2065FA6F2EC63FE28BE26FDB7B0480 | SHA256:E25CADC80EA5163E0F1C6FD703479469D9F23B47ADE244FAC5F22BCDB01B39BD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |