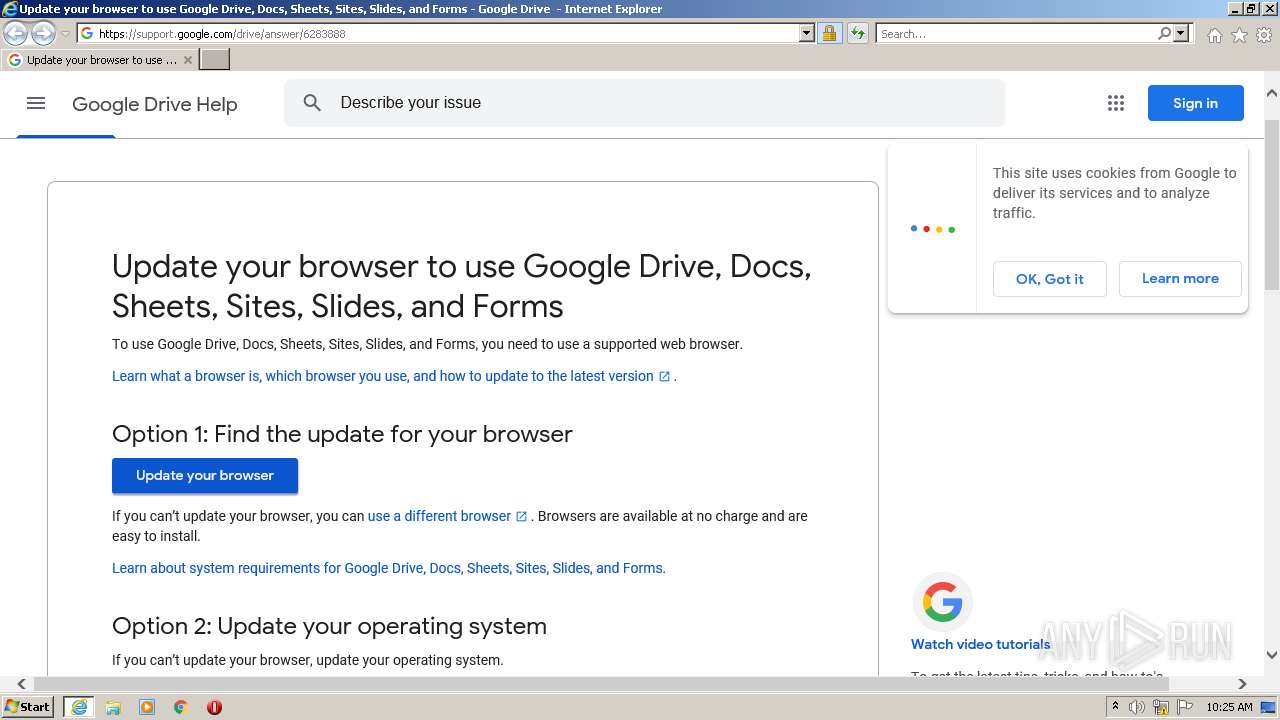
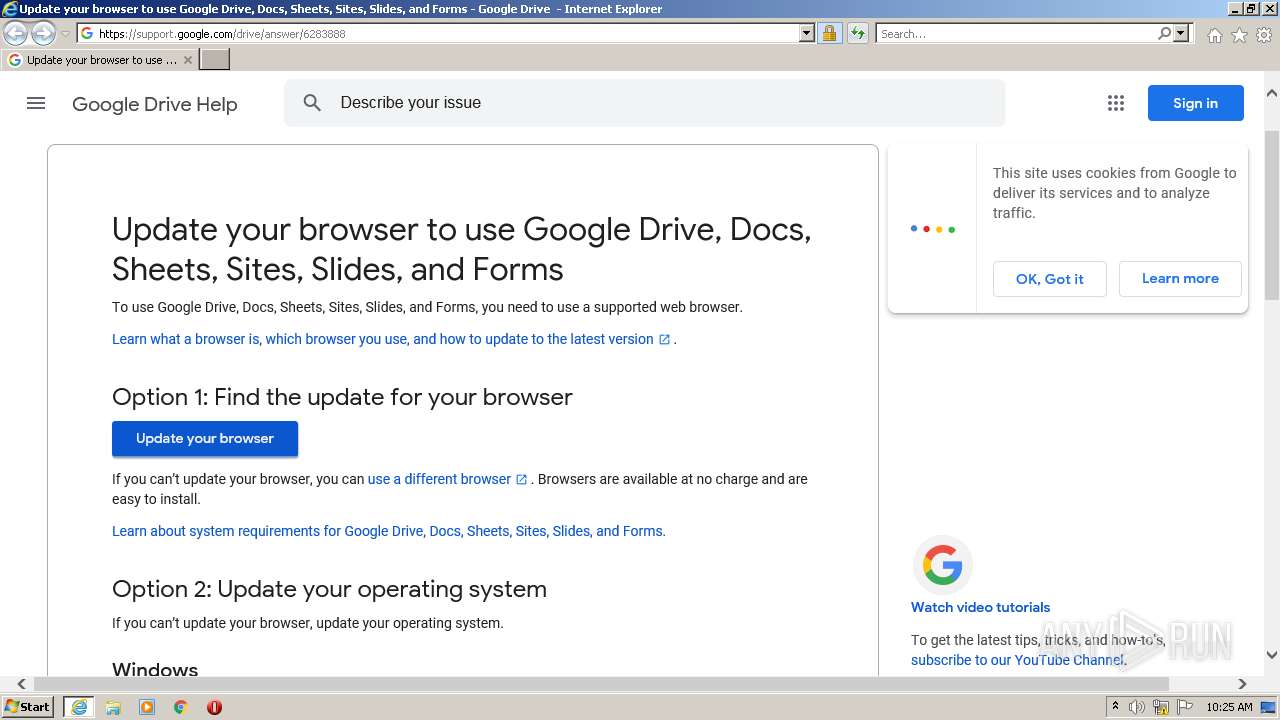
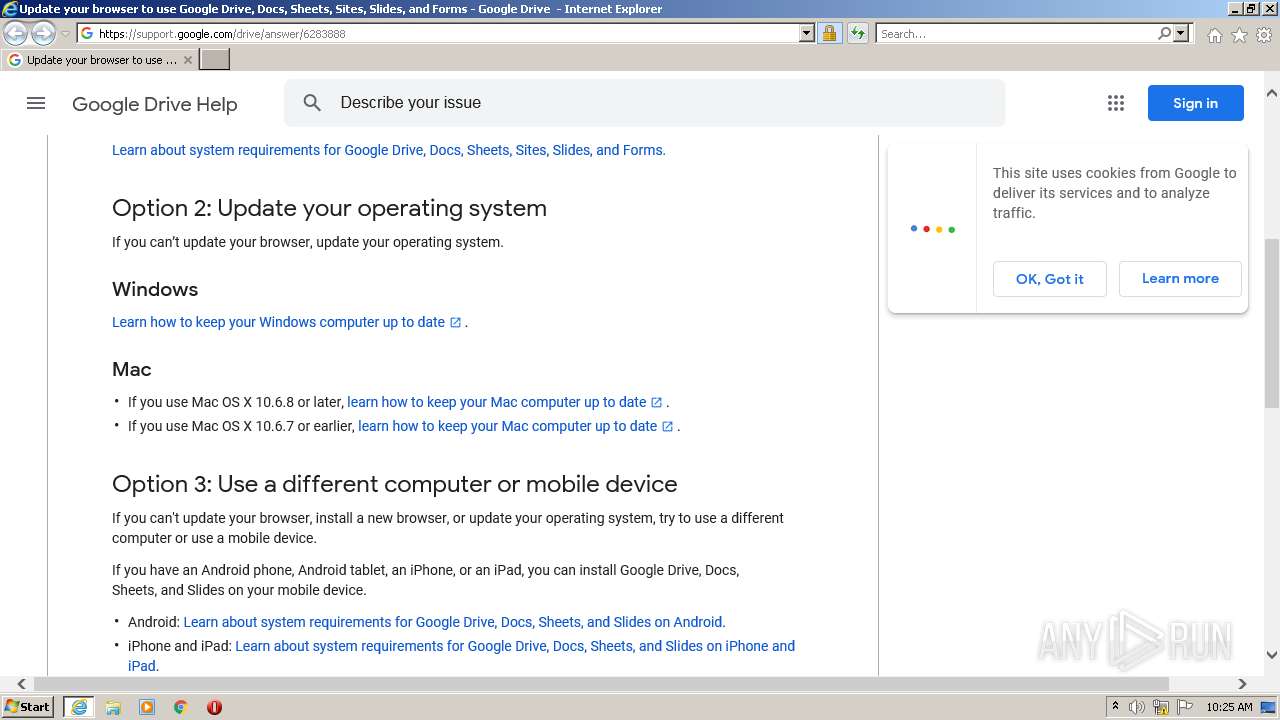
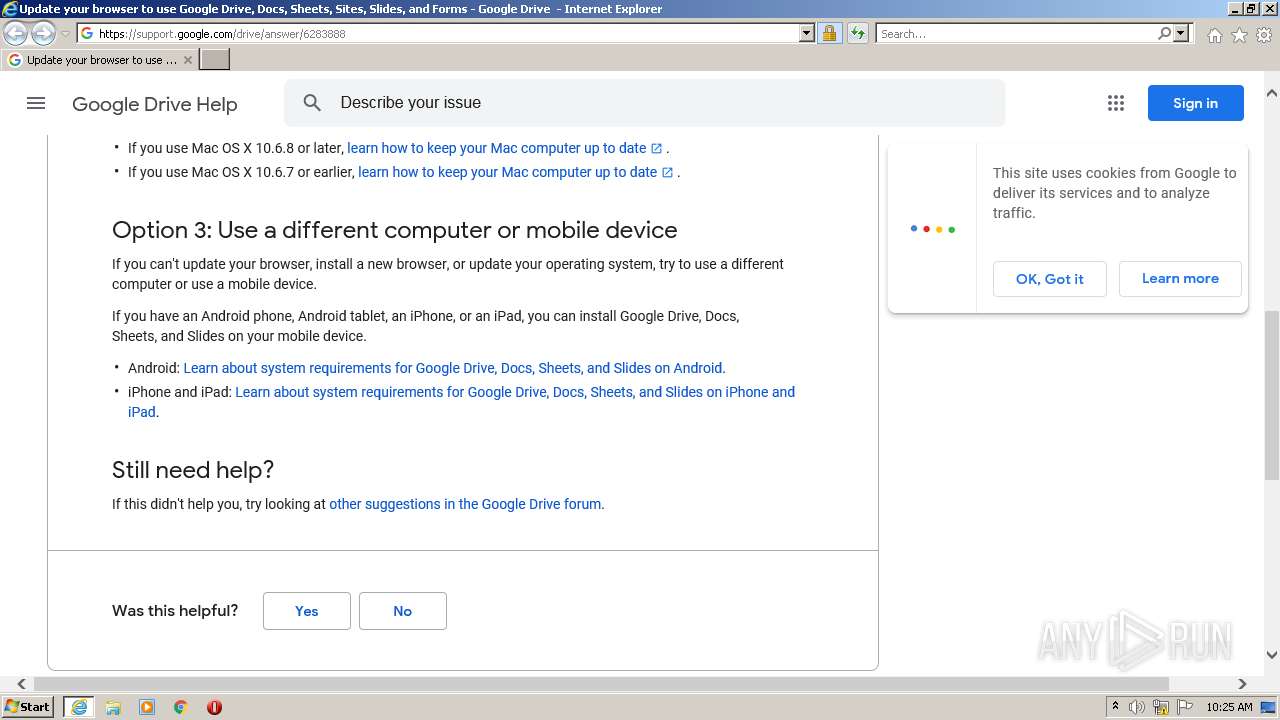
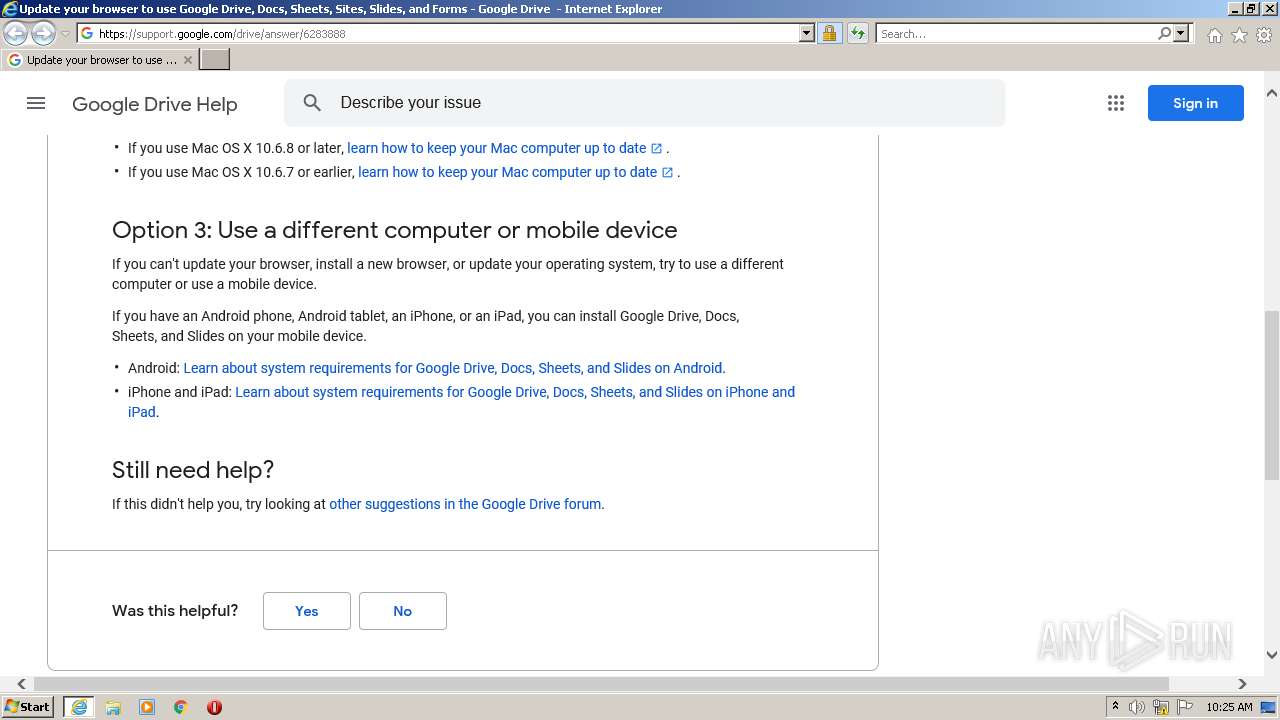
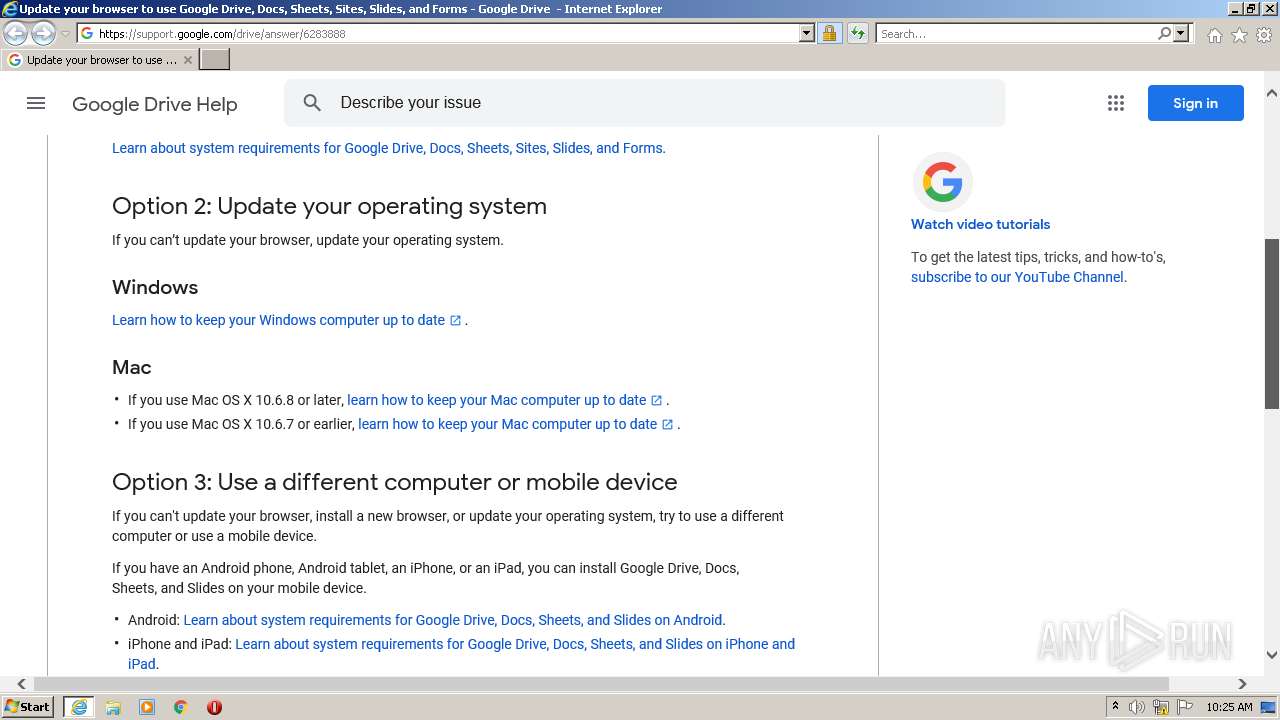
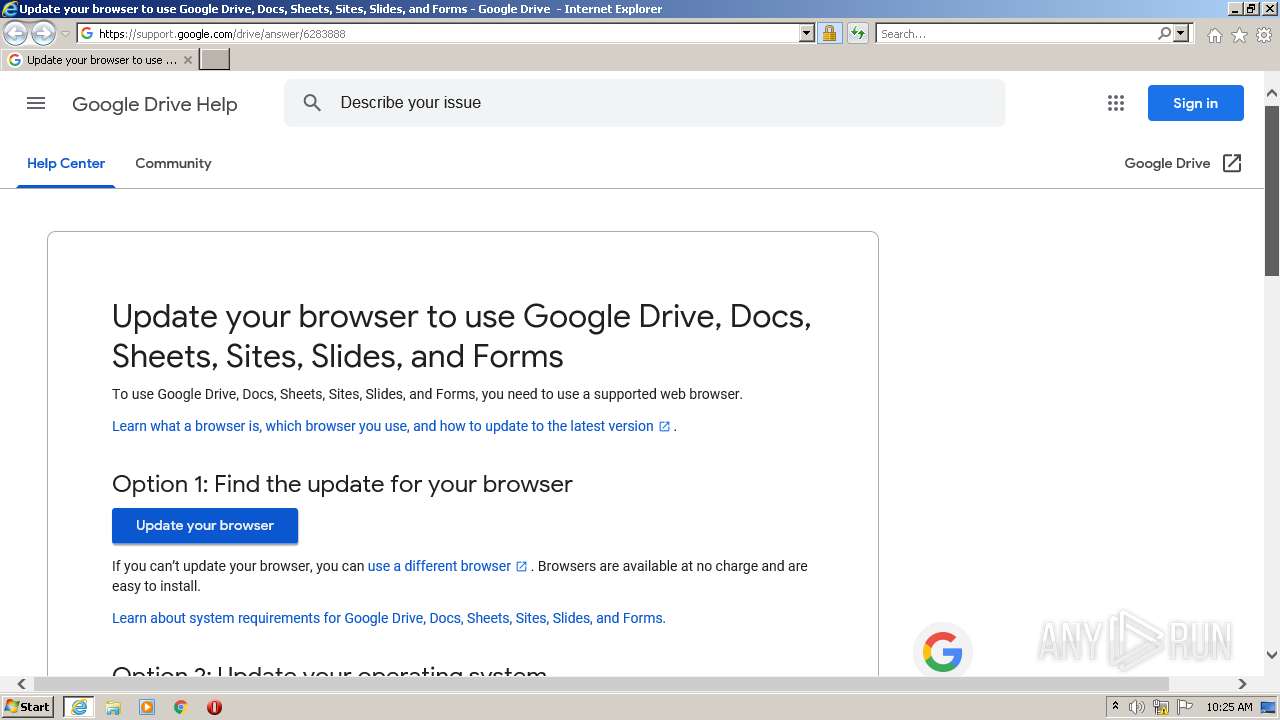
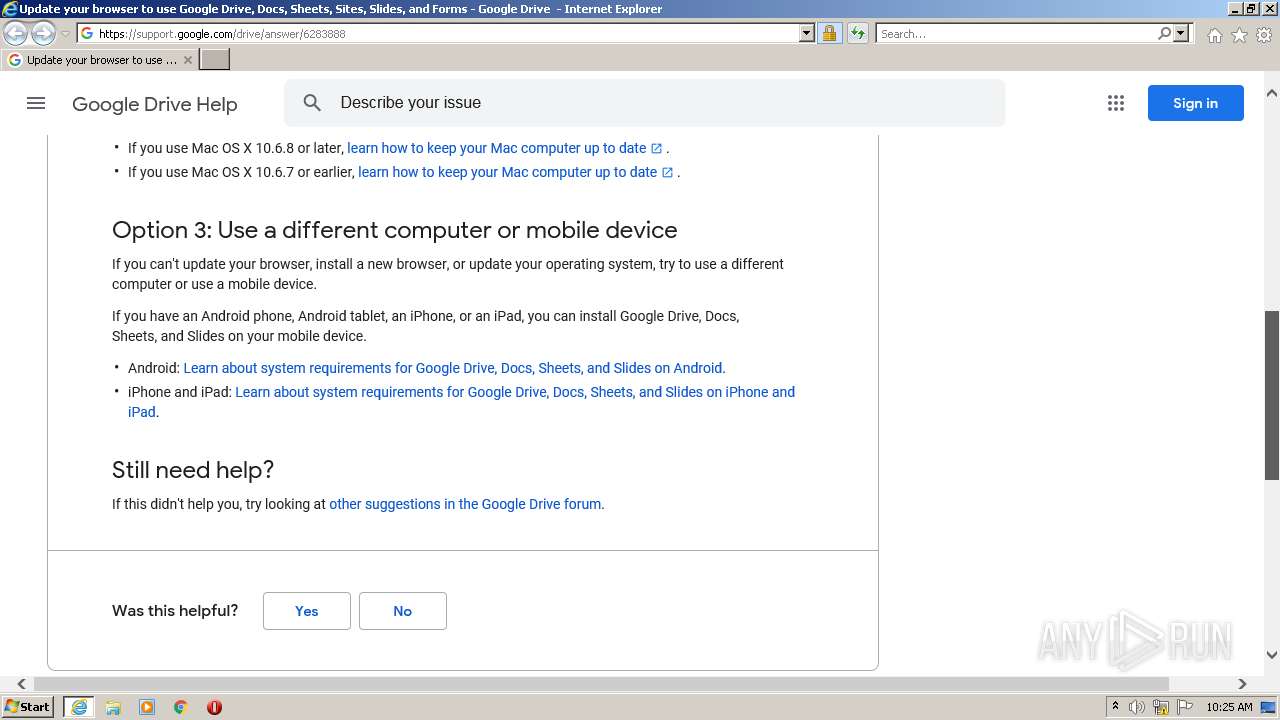
| URL: | https://docs.google.com/forms/d/e/1FAIpQLSeOogYipnGxt275dunPKkmJ35_rJT0vfpCNhKZ9d9LSvA7c-Q/viewform?vc=0&c=0&w=1&flr=0&usp=mail_form_link |
| Full analysis: | https://app.any.run/tasks/f2401328-4228-413d-8c76-a5d5e92ece26 |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2021, 10:25:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D9213060EB709726DFBE5DF0CC6CE3EB |
| SHA1: | F76378137F0CBDC390E7FD2D17587088BE490AC5 |
| SHA256: | FABDA147FEC06B16C7913269906E7BC8E1488E4DE73728048EFD06FD475DBBD3 |
| SSDEEP: | 3:N8SP3ulYabK6k0Q2y8LsQYOBpVTVcqpdSf0OIYAYVDiOQ1Io6z:2SmvuPmgVE7TVppd3OT9pid9C |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 2344)
INFO
Creates files in the user directory
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 2344)
Reads settings of System Certificates
- iexplore.exe (PID: 3732)
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 2344)
Changes settings of System certificates
- iexplore.exe (PID: 3732)
Checks supported languages
- iexplore.exe (PID: 3732)
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 2344)
Changes internet zones settings
- iexplore.exe (PID: 3732)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3732)
Reads the computer name
- iexplore.exe (PID: 3732)
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 2344)
Reads internet explorer settings
- iexplore.exe (PID: 2344)
- iexplore.exe (PID: 3116)
Application launched itself
- iexplore.exe (PID: 3732)
Checks Windows Trust Settings
- iexplore.exe (PID: 2344)
- iexplore.exe (PID: 3116)
- iexplore.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2344 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3732 CREDAT:2888966 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3732 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3732 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://docs.google.com/forms/d/e/1FAIpQLSeOogYipnGxt275dunPKkmJ35_rJT0vfpCNhKZ9d9LSvA7c-Q/viewform?vc=0&c=0&w=1&flr=0&usp=mail_form_link" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
26 132
Read events
25 885
Write events
243
Delete events
4
Modification events
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 402541696 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30931724 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 702549196 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30931724 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3732) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
39
Text files
118
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_30F32374BEBB4A72181B36E407396E90 | binary | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_30F32374BEBB4A72181B36E407396E90 | der | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_76F26EDEF7C1087F80A272B48769819E | der | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\6283888[1].htm | html | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\AQEZI7TV.txt | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\TCZXRM3Q.txt | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2W2CXE1V.txt | text | |
MD5:— | SHA256:— | |||
| 3116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_76F26EDEF7C1087F80A272B48769819E | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
140
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3116 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3732 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3116 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECHMNwkPtKJCCgAAAAEl%2FQo%3D | US | der | 471 b | whitelisted |
2344 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDGvpZUYfPV%2BAoAAAABJf%2Fv | US | der | 472 b | whitelisted |
3116 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCOWH2ozD4foQoAAAABJf86 | US | der | 472 b | whitelisted |
2344 | iexplore.exe | GET | 200 | 2.16.186.9:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSuDNBuvZ6kjzD%2F0CWsMecbxQ%3D%3D | unknown | der | 503 b | shared |
3116 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDDxQmkH%2FlDagoAAAABJgJE | US | der | 472 b | whitelisted |
2344 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGP%2Bj05%2F0P2fCgAAAAEmBeU%3D | US | der | 471 b | whitelisted |
2344 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCynPQ4rdDBoAoAAAABJf7q | US | der | 472 b | whitelisted |
3116 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECiWvl1%2BUB7cCgAAAAEl%2F%2BI%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2344 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3116 | iexplore.exe | 142.250.185.238:443 | docs.google.com | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 8.248.137.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3116 | iexplore.exe | 142.250.185.174:443 | support.google.com | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 172.217.21.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 142.250.181.129:443 | lh3.googleusercontent.com | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 142.250.185.67:443 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 142.250.186.78:443 | apis.google.com | Google Inc. | US | whitelisted |
3116 | iexplore.exe | 142.250.186.164:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docs.google.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
support.google.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
lh3.googleusercontent.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |