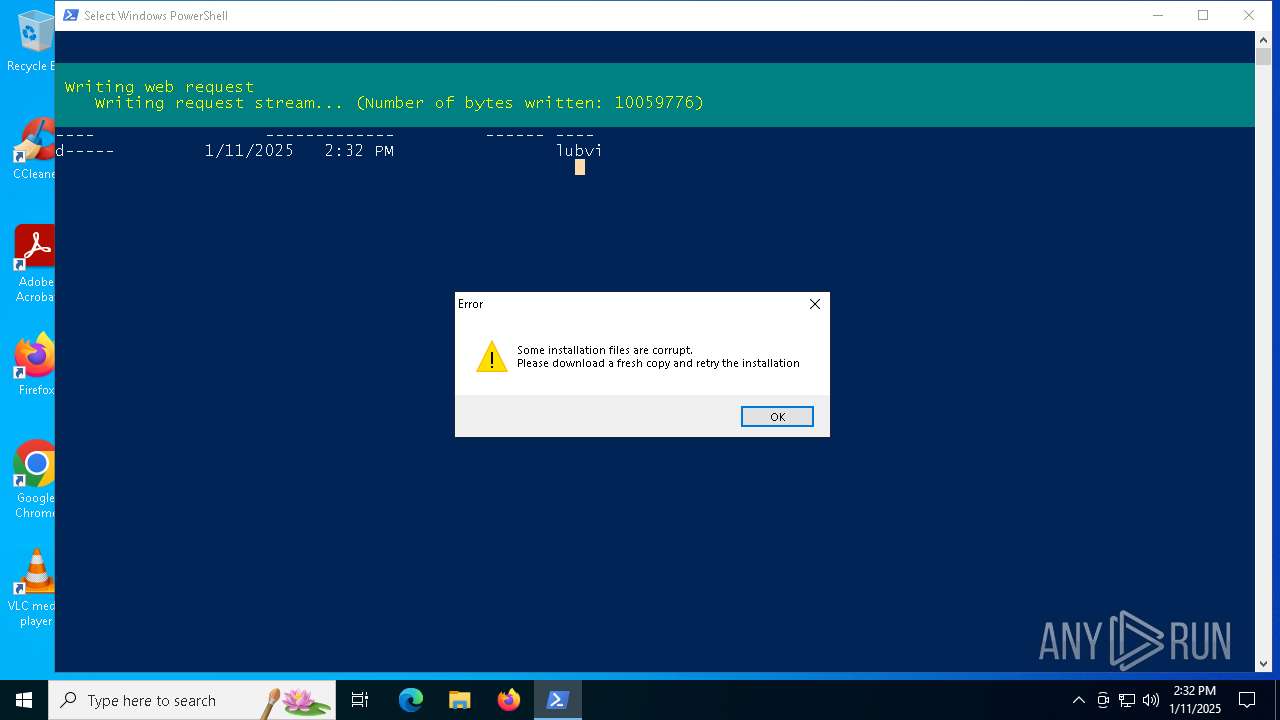
| File name: | toto.txt |
| Full analysis: | https://app.any.run/tasks/172eee8c-e532-4bbd-a682-2de2f79859ed |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 14:31:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | A54ADA657EFBBE1395598AAE1BDAC1F9 |
| SHA1: | A7887658EEBBA20BD97E43010AC5FFD5B972A273 |
| SHA256: | FA9CF901BD2C9359D2EFC09F8ADB1BAA12AE56B841BA06DD057CEFD58C778316 |
| SSDEEP: | 12:qrz69RqrrSuzlGp5BzGLp2AzG3PCt4K/oMntX:mz6Xqzzlf12A63PCtz/l |
MALICIOUS
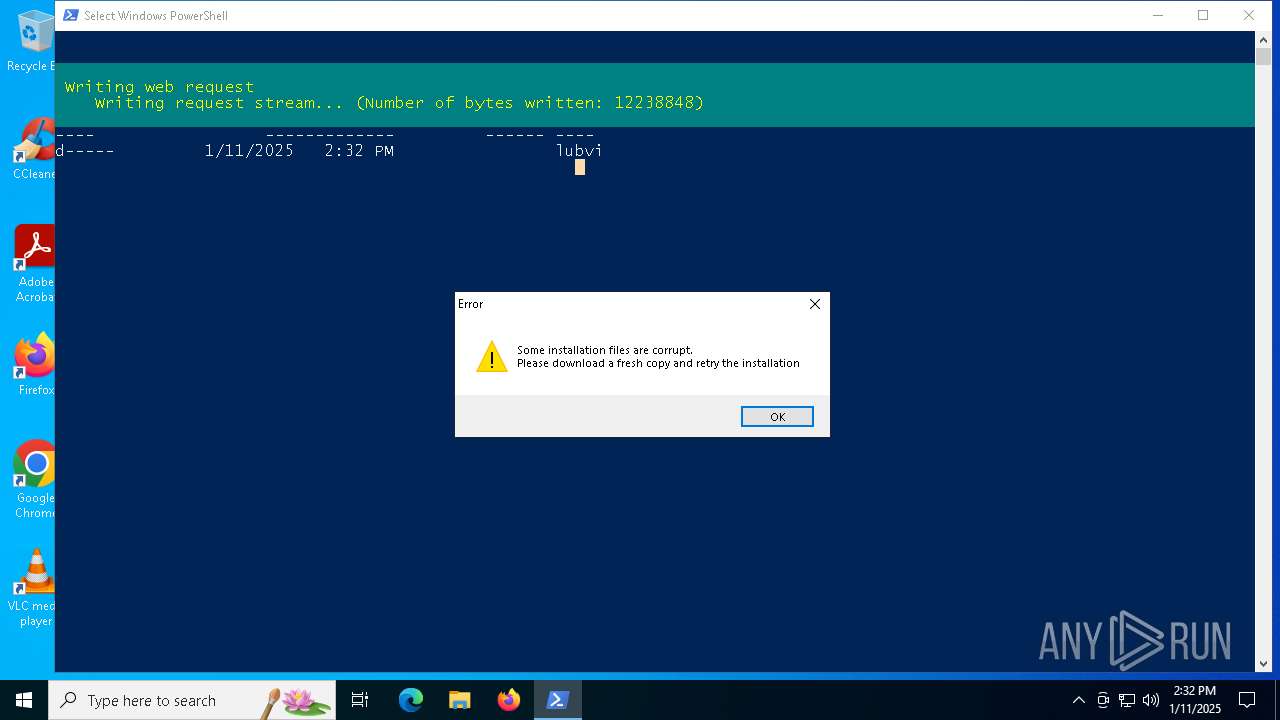
Bypass execution policy to execute commands
- powershell.exe (PID: 776)
SUSPICIOUS
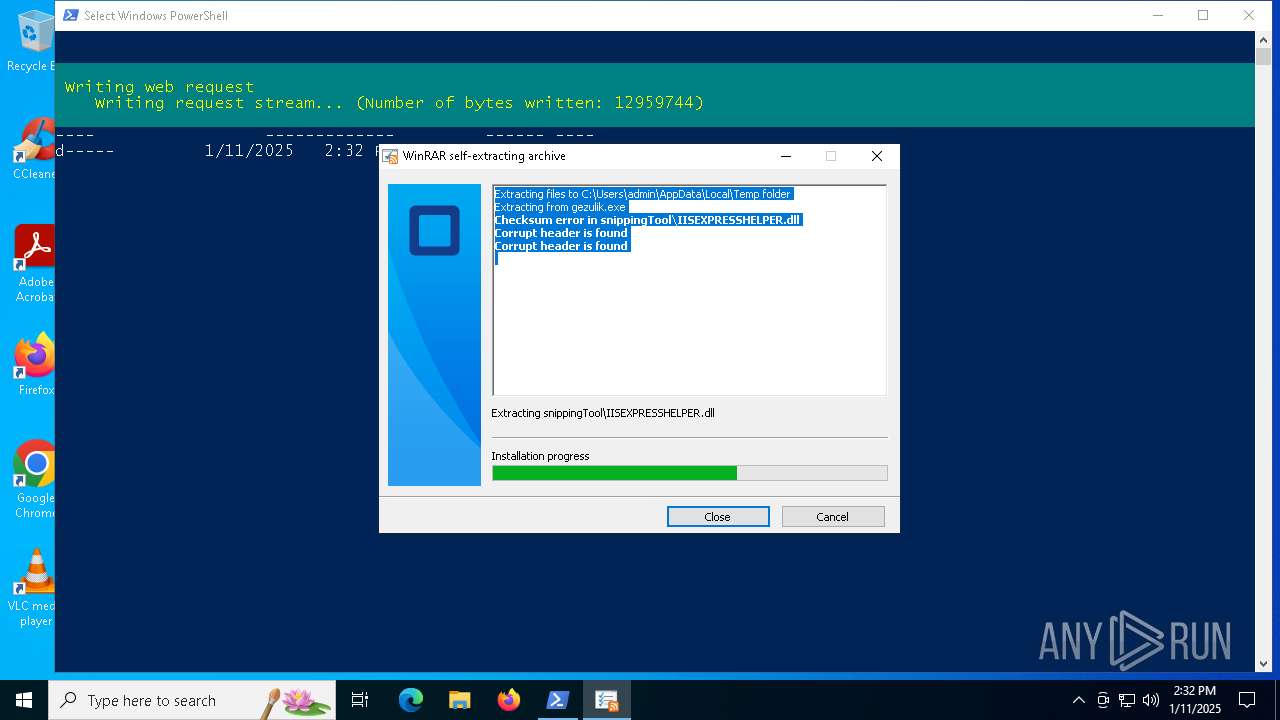
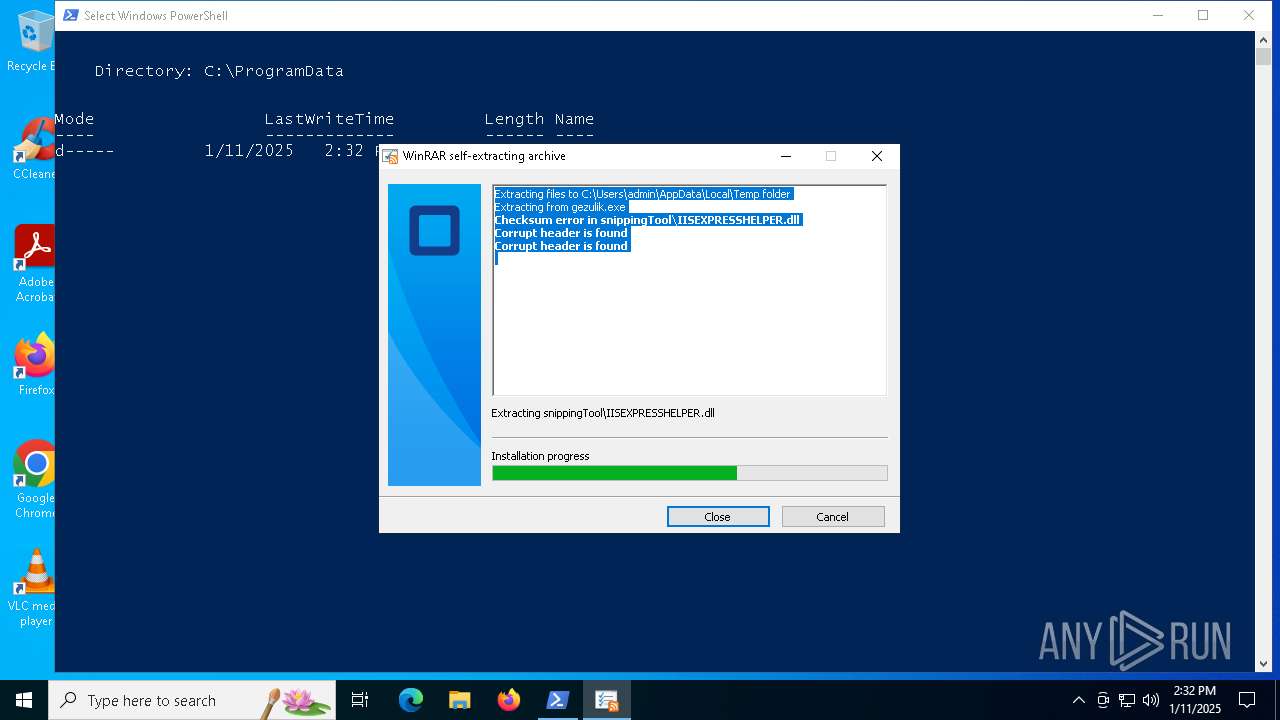
Executable content was dropped or overwritten
- gezulik.exe (PID: 5872)
Process drops legitimate windows executable
- gezulik.exe (PID: 5872)
The process creates files with name similar to system file names
- gezulik.exe (PID: 5872)
Checks for external IP
- svchost.exe (PID: 2192)
- powershell.exe (PID: 776)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
- powershell.exe (PID: 776)
INFO
Disables trace logs
- powershell.exe (PID: 776)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 776)
Creates files in the program directory
- powershell.exe (PID: 776)
Checks supported languages
- gezulik.exe (PID: 5872)
Checks proxy server information
- powershell.exe (PID: 776)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 776)
Manual execution by a user
- gezulik.exe (PID: 5872)
Reads the computer name
- gezulik.exe (PID: 5872)
The sample compiled with english language support
- gezulik.exe (PID: 5872)
The sample compiled with czech language support
- gezulik.exe (PID: 5872)
Create files in a temporary directory
- gezulik.exe (PID: 5872)
The sample compiled with german language support
- gezulik.exe (PID: 5872)
The sample compiled with spanish language support
- gezulik.exe (PID: 5872)
The sample compiled with french language support
- gezulik.exe (PID: 5872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
119
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\toto.txt.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | "C:\Users\admin\Desktop\gezulik.exe" | C:\Users\admin\Desktop\gezulik.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
5 409
Read events
5 409
Write events
0
Delete events
0
Modification events
Executable files
55
Suspicious files
4
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\appobj.dll | executable | |
MD5:971466DFB298309F7DABF093B81C8E82 | SHA256:4E27A4E640B86FEF338FA4B7D23AFEB946F1A27AF610EEA1D59FE7F3BEFBE9E1 | |||
| 776 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:B766390915EC2F7D9295D0C832817CC4 | SHA256:4BEBABC60AA268419B57A34B2F2B8F75F4DA9B172820D3E0F50471896261A2B3 | |||
| 776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vra3sqy4.54p.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\asptlb.tlb | executable | |
MD5:FC0BCCC6D7715F1BDED31752F1ED72D2 | SHA256:B78FC0174D6A4572D5ACE60D9679C353526277C1DE248011B7B9076382463E14 | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\appcmd.xml | text | |
MD5:A1ABF60ADD7C54A1A444E83B523F8095 | SHA256:24C63A00A384D26A929C3285E41822631A846C5C69627360DEC267B35C55410A | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\asp.dll | executable | |
MD5:D94F556AD07E47A347439DC6488B8A04 | SHA256:7F11DF3CE4EBC7C132AE4161FD920D251CEE735553152F78914FFADD022457C9 | |||
| 776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jjvlq5kk.ysm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\Asp.Net Core Module\V2\aspnetcorev2.dll | executable | |
MD5:E45A9A54EAB83DBC58FC4FFDAF839676 | SHA256:0AF349794847805F33C13A65E482A2ACF76E404C6C5184D7A5EE19504EAF446E | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\Asp.Net Core Module\V2\17.0.22116\aspnetcorev2_outofprocess.dll | executable | |
MD5:AF6F62F19D015485A11FE4074EBD15C8 | SHA256:E28A89660326DCB55D2C39BDC0B160B183BE4533E896891EA5A110A74E8AB565 | |||
| 5872 | gezulik.exe | C:\Users\admin\AppData\Local\Temp\snippingTool\aspnetcore.dll | executable | |
MD5:0C05B2C489B4C497114E39B9F6FFB8A8 | SHA256:452E8B9FC6069EDFDF47017BD523F2475BBA0AE3FAF60A00624B590514E55BED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1460 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1460 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 147.45.47.123:443 | https://human-cldf.com/gamdos.zip | unknown | compressed | 14.5 Mb | unknown |
— | — | GET | 200 | 172.67.167.249:443 | https://iplogger.co/1EwuL4 | unknown | image | 116 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1460 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.31:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1460 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1460 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
human-cldf.com |
| unknown |
iplogger.co |
| shared |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
776 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 23 |
2 ETPRO signatures available at the full report