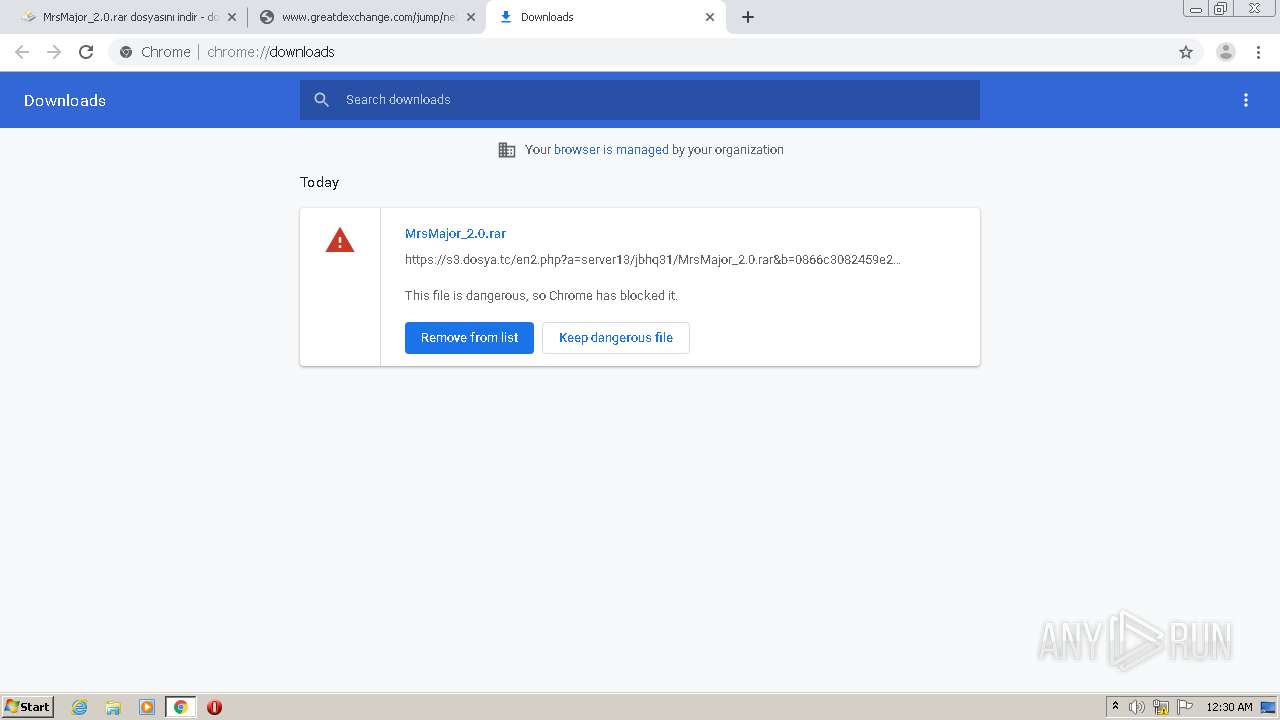
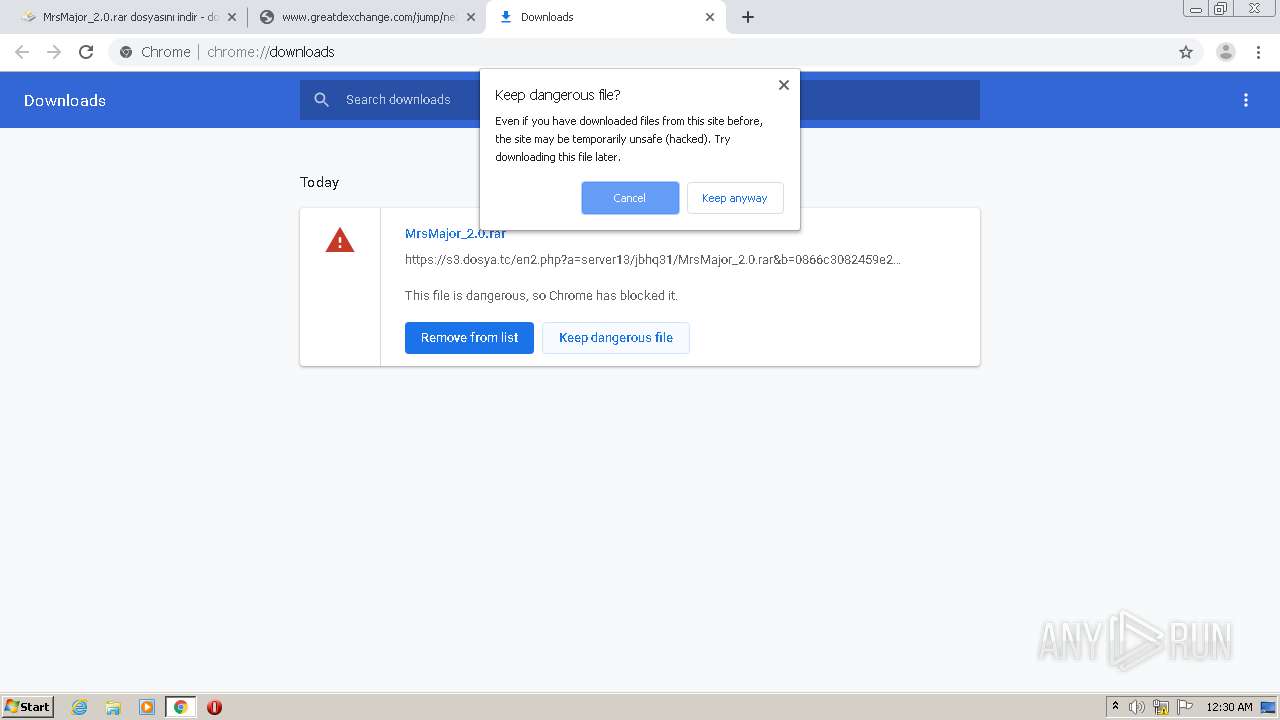
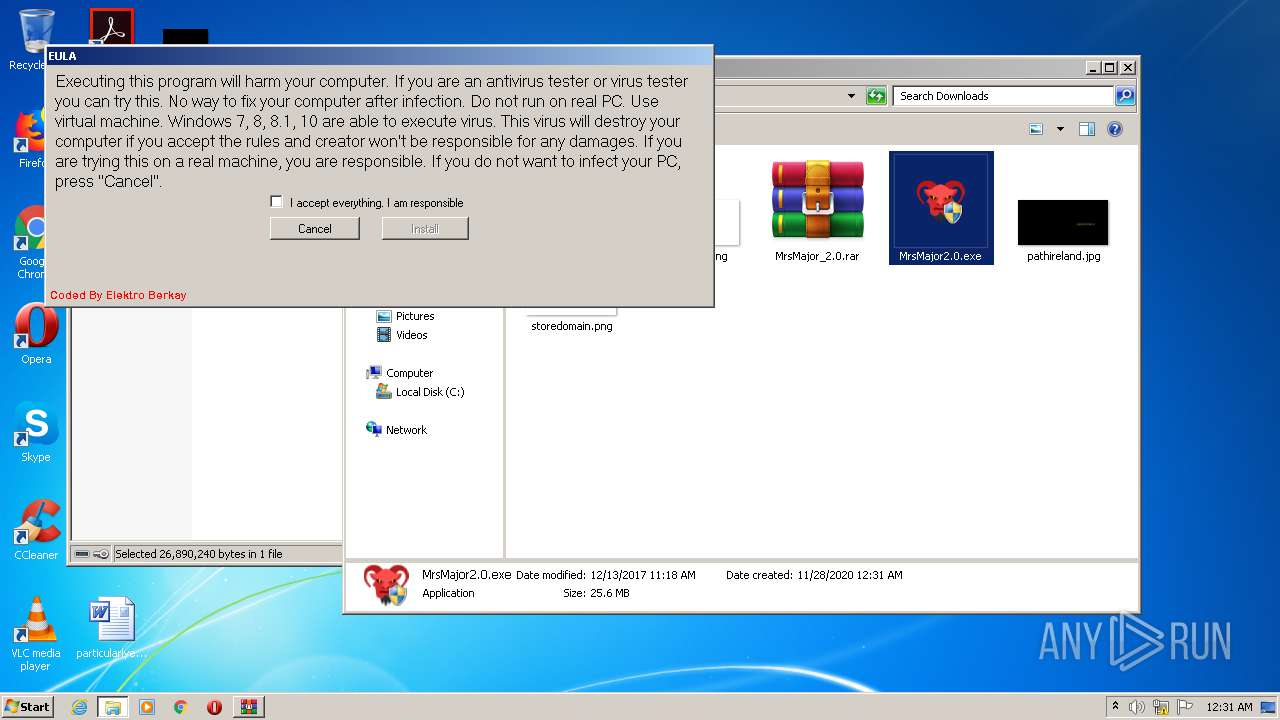
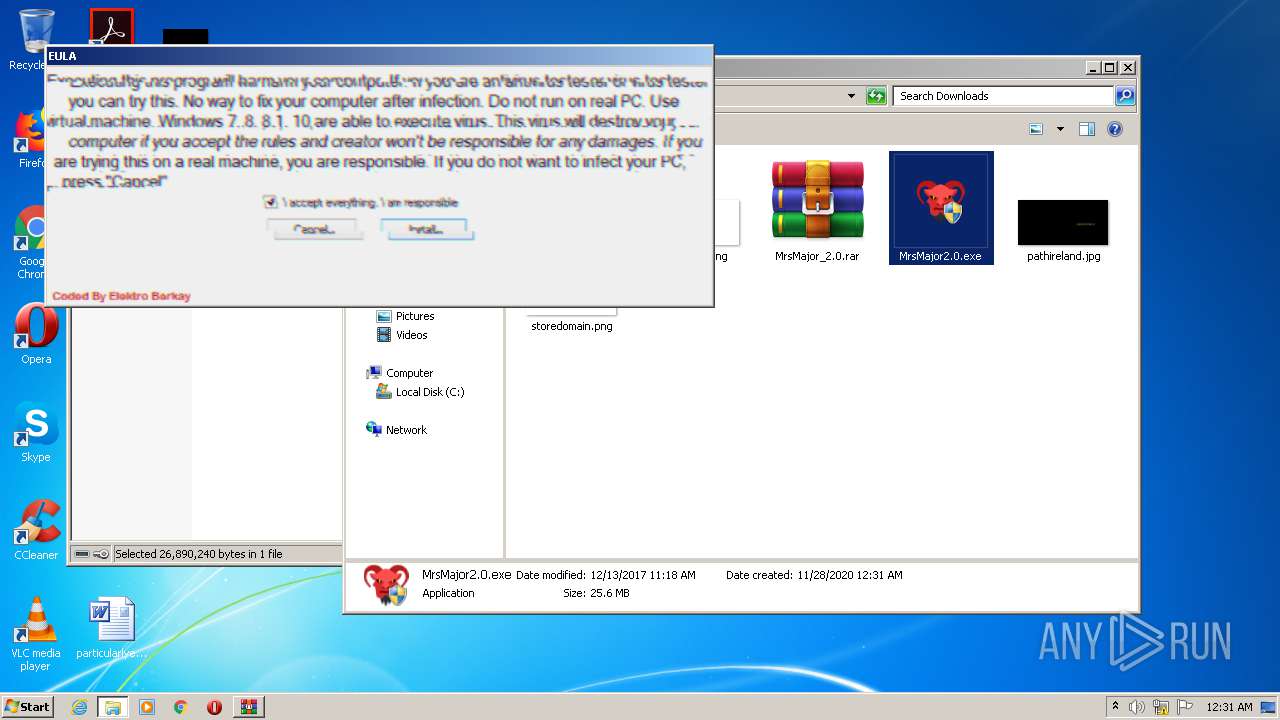
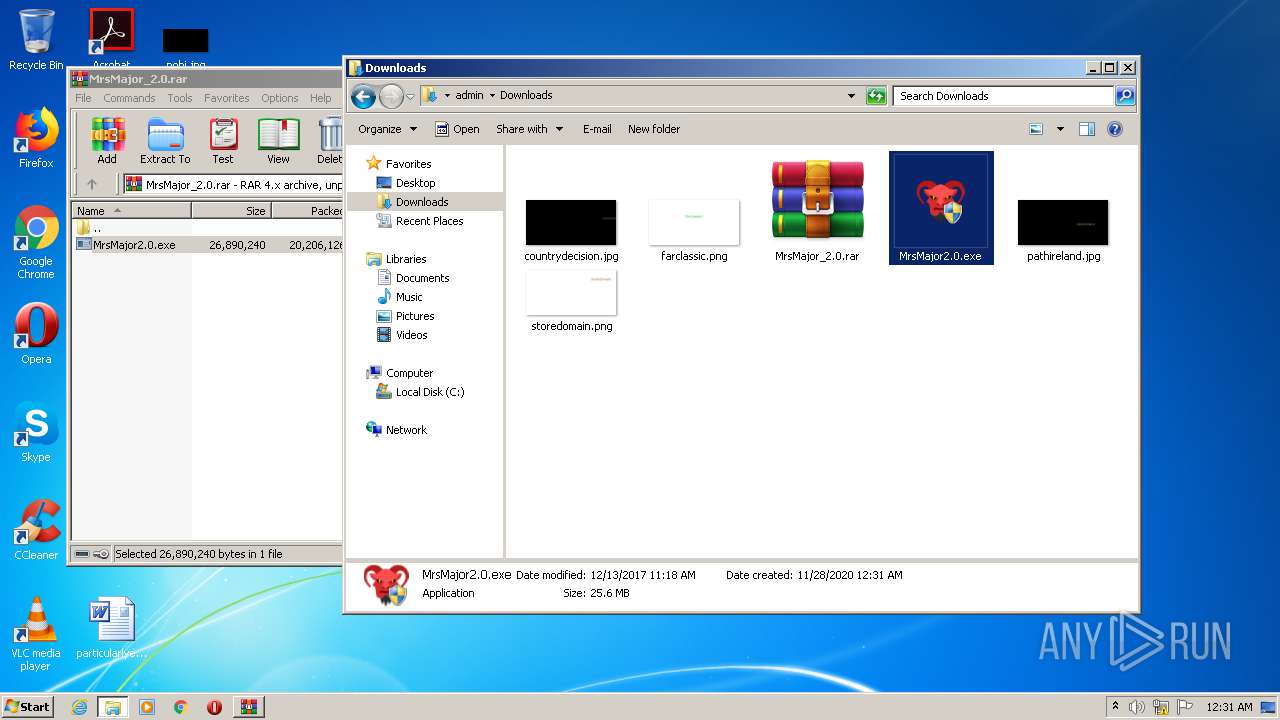
| URL: | https://s3.dosya.tc/server13/jbhq31/MrsMajor_2.0.rar.html |
| Full analysis: | https://app.any.run/tasks/03d098f9-4cbd-45a2-87af-db4ed9ccf765 |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2020, 00:29:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D9C62D230742C29C376F040F545D4345 |
| SHA1: | 6EBA94845075CF4B5874DFE3E5AB1709097BBD32 |
| SHA256: | FA95B4338F98BD41F22C57D718A034410E099BCBC66444C24A5EFCEF6F6D952D |
| SSDEEP: | 3:N805LXPei7cvVaLQn:205L/eAcs8n |
MALICIOUS
Drops executable file immediately after starts
- MrsMajor2.0.exe (PID: 3240)
- wscript.exe (PID: 3644)
- cmd.exe (PID: 1704)
Application was dropped or rewritten from another process
- MrsMajor2.0.exe (PID: 2152)
- eula32.exe (PID: 3784)
- notmuch.exe (PID: 3024)
- GetReady.exe (PID: 568)
- MrsMajor2.0.exe (PID: 3240)
Changes the login/logoff helper path in the registry
- wscript.exe (PID: 3644)
Changes the autorun value in the registry
- wscript.exe (PID: 3644)
Disables registry editing tools (regedit)
- wscript.exe (PID: 3644)
Disables Windows Defender
- wscript.exe (PID: 3644)
SUSPICIOUS
Drops a file that was compiled in debug mode
- MrsMajor2.0.exe (PID: 3240)
- wscript.exe (PID: 3644)
Executable content was dropped or overwritten
- MrsMajor2.0.exe (PID: 3240)
- wscript.exe (PID: 3644)
- cmd.exe (PID: 1704)
Executes scripts
- MrsMajor2.0.exe (PID: 3240)
Creates files in the program directory
- wscript.exe (PID: 3644)
Creates a directory in Program Files
- wscript.exe (PID: 3644)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 1704)
Starts CMD.EXE for commands execution
- GetReady.exe (PID: 568)
- wscript.exe (PID: 3644)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 1708)
Reads the hosts file
- chrome.exe (PID: 1708)
- chrome.exe (PID: 2472)
Manual execution by user
- MrsMajor2.0.exe (PID: 3240)
- WinRAR.exe (PID: 2744)
- MrsMajor2.0.exe (PID: 2152)
- explorer.exe (PID: 3244)
Application launched itself
- chrome.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
33
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16483221900705706196 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2184 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 568 | "C:\Program Files\MicrosoftWindowsServicesEtc\GetReady.exe" | C:\Program Files\MicrosoftWindowsServicesEtc\GetReady.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1221605239 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=544561759956208849 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3528 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2432 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4457552050846435273 --mojo-platform-channel-handle=4112 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x71b1a9d0,0x71b1a9e0,0x71b1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3151978340008586482 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3892 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17238377402506121116 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2920 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1704 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\1\3504.bat "C:\Program Files\MicrosoftWindowsServicesEtc\GetReady.exe"" | C:\Windows\system32\cmd.exe | GetReady.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,7673574096430949604,12494334695125320614,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=995893585401314672 --mojo-platform-channel-handle=1488 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 300
Read events
1 203
Write events
94
Delete events
3
Modification events
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2472-13250997002778000 |
Value: 259 | |||
Executable files
30
Suspicious files
44
Text files
132
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FC19A0B-9A8.pma | — | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c79e7093-cdcd-4677-818d-3517012a464d.tmp | — | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF13efd2.TMP | text | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF13efc2.TMP | text | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2472 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF13f178.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
42
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1708 | chrome.exe | GET | 302 | 195.201.198.238:80 | http://s3.dosya.tc/en2.php?a=server13/jbhq31/MrsMajor_2.0.rar&b=0866c3082459e263de7e56ba854ceb19 | RU | html | 285 b | suspicious |
1708 | chrome.exe | GET | 200 | 35.201.103.0:80 | http://www.greatdexchange.com/jump/next.php?r=81231 | US | html | 2.56 Kb | whitelisted |
1708 | chrome.exe | GET | 302 | 35.201.103.0:80 | http://www.greatdexchange.com/jump/next.php?stamat=m%7C%2CgtiF6Y2JqB1dQO0dEdHP3xP.13b%2C2t5FkDDYpjxJXsMWHSh7wOBWkZ8R17bPUToGGoZfYrTxGOoFVPEMSLvXhzUJ0yu9S0cj0ymA6GIdXZUJ-3MOuw%2C%2C&cbrandom=0.6326786739291053&cbtitle=&cbiframe=0&cbWidth=1280&cbHeight=620&cbdescription=&cbkeywords=&cbref= | US | binary | 1 b | whitelisted |
1708 | chrome.exe | GET | 204 | 35.201.103.0:80 | http://www.greatdexchange.com/script/i.php?stamat=m%7C%2C%2CQ2Nq9id3tGU3Bf9GH0dEdHP3xP.01a%2C1BJKI440k_keuJoRoSuWrZnZWZ7cLmyyMGH9GT6ljncSeF8XZRPLeD70rO0EIN2W0U6Cow7DZ3FwUlXXNedHXdGWobBi8rtzTDHzMM44f92WWX7GJEsbPo1psyFDr6_H-W2JtJSOzT8rrePh_ZeiYuAyzgdFho-fvbWzmxYpU8VEsj9oDHRb4gkmPPDcAGuwPjR_TW0Ki_eC3JkaCOVxyf9TUpoEsaM073SxFL1lWEqQcPtsSzpgnF3ITjS3NYQ5n3_xjxMpqF95RI4BIgyqXkRfEXicpYpaKUkZ0D9HzoZR2KQ0avtEt0q4MzLsfZ9Tas3DAPOZB7tExAZpK1OWbJwg_lfFogYoE7c36xT1chptAU406Trrlnk5CNgl-PG2NZGcob6-B6F6e_HSKioXBgQjP6Un4DsOeL7bZMcXKViE8SlfBcF9iXNLRjOtehuA | US | binary | 1 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1708 | chrome.exe | 172.217.18.98:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 173.194.200.139:443 | www.google-analytics.com | Google Inc. | US | unknown |
1708 | chrome.exe | 172.217.16.161:443 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 74.125.133.155:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
1708 | chrome.exe | 172.217.21.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 195.201.198.238:80 | s3.dosya.tc | Awanti Ltd. | RU | suspicious |
1708 | chrome.exe | 35.201.103.0:80 | www.greatdexchange.com | Google Inc. | US | suspicious |
1708 | chrome.exe | 172.217.6.206:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 139.45.196.146:443 | pushlommy.com | — | US | suspicious |
1708 | chrome.exe | 216.58.212.130:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3.dosya.tc |
| suspicious |
accounts.google.com |
| shared |
pushlommy.com |
| suspicious |
pagead2.googlesyndication.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
my.rtmark.net |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
adservice.google.se |
| whitelisted |
partner.googleadservices.com |
| whitelisted |
adservice.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1708 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.tc domain |