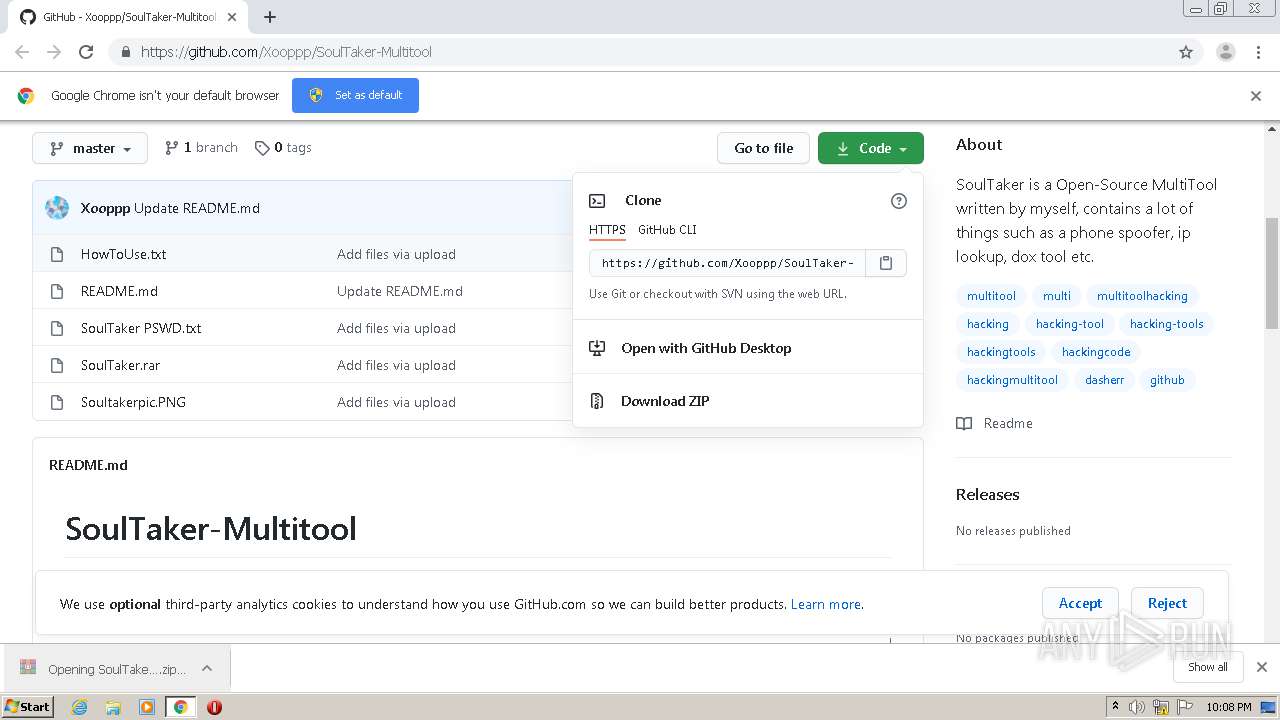
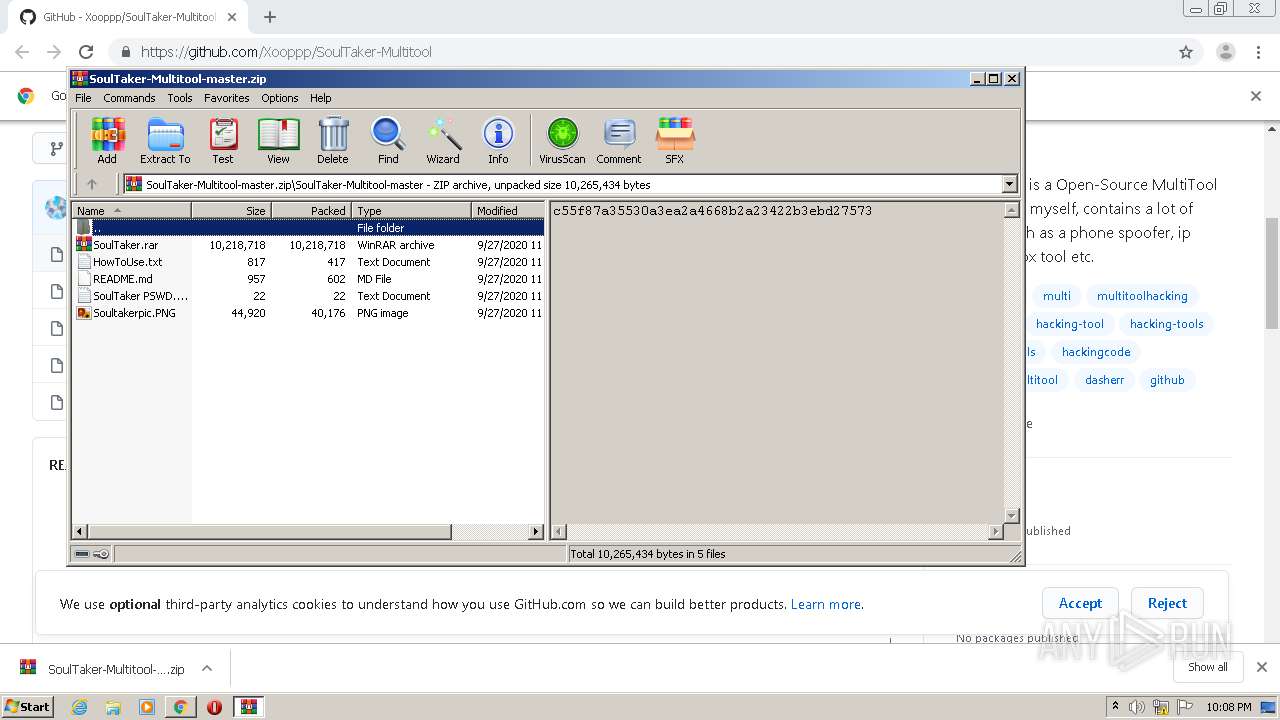
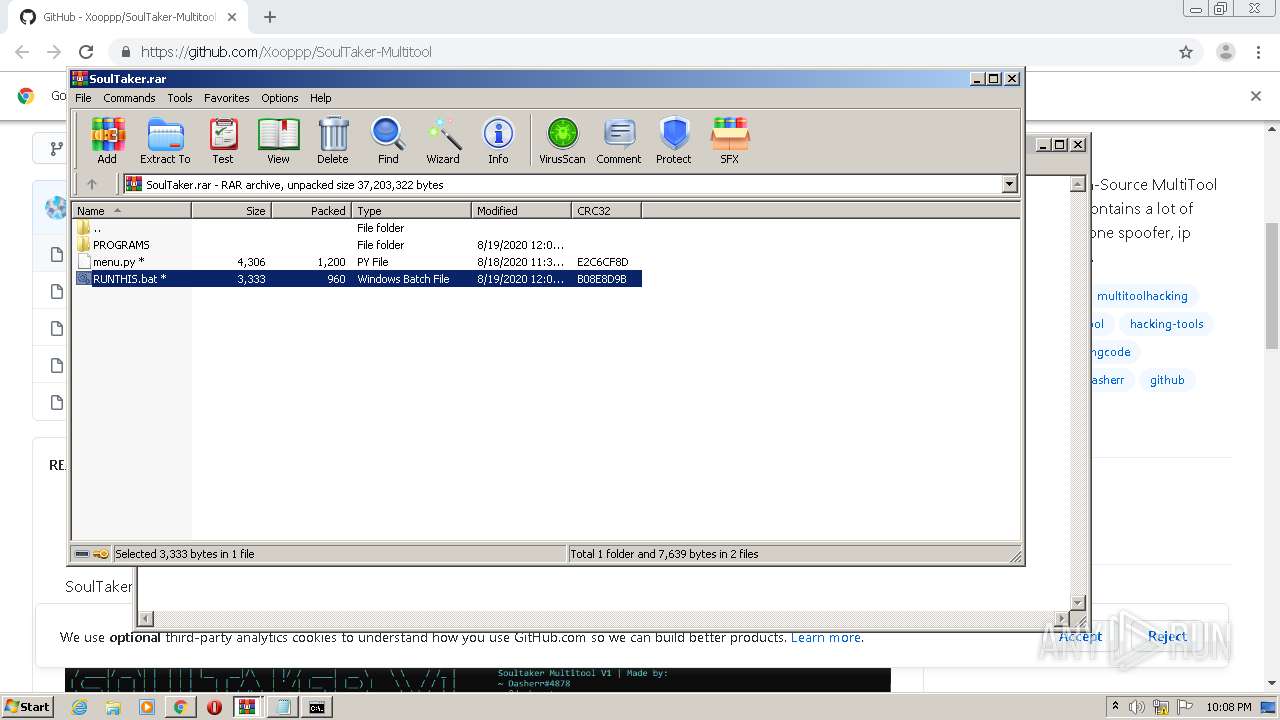
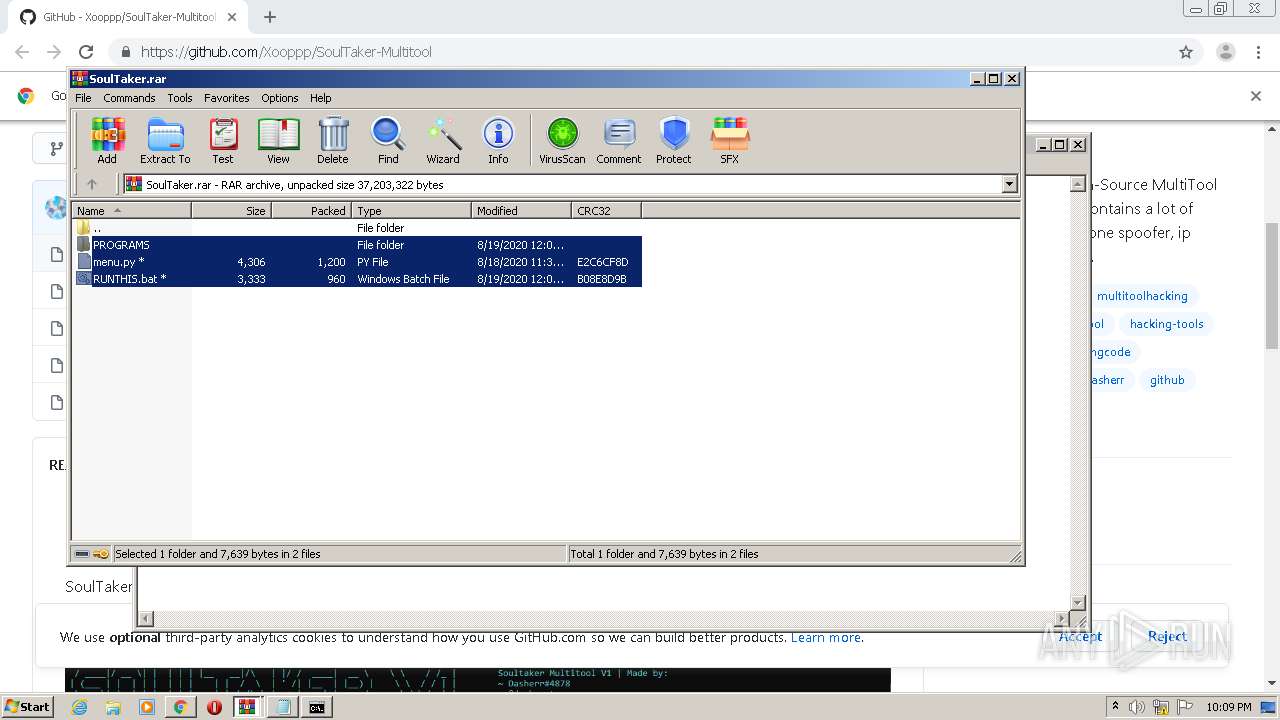
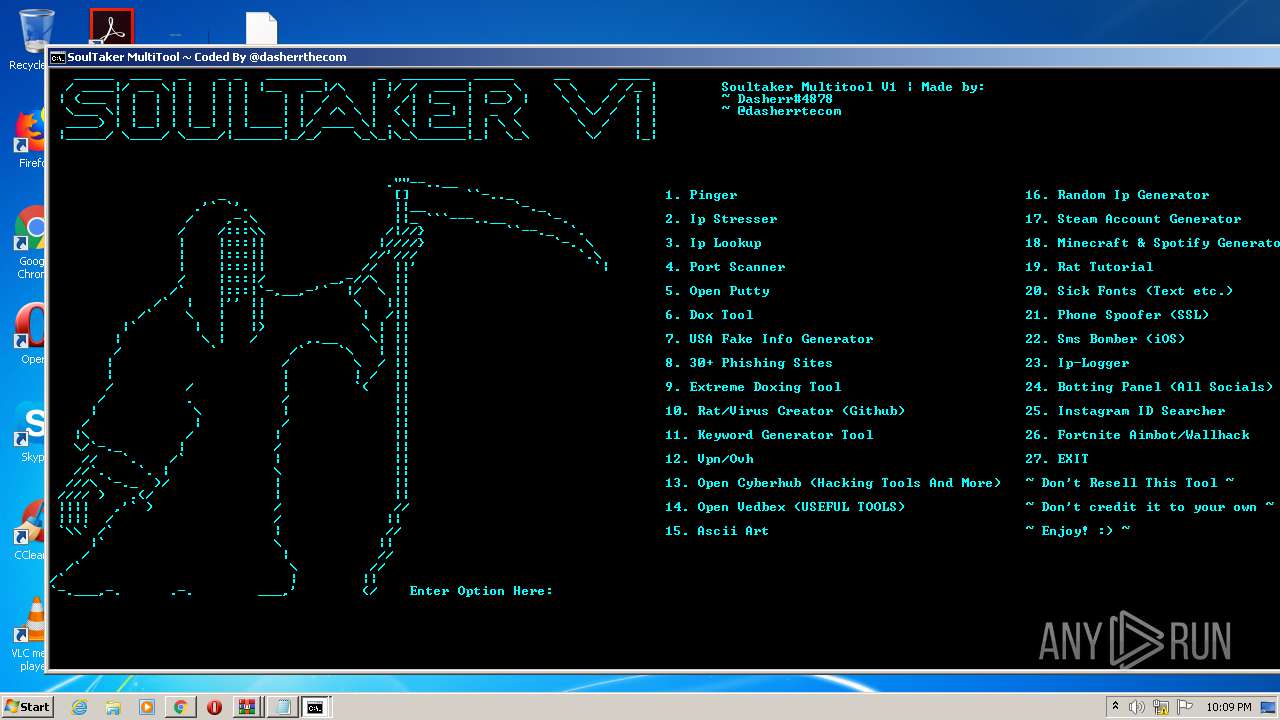
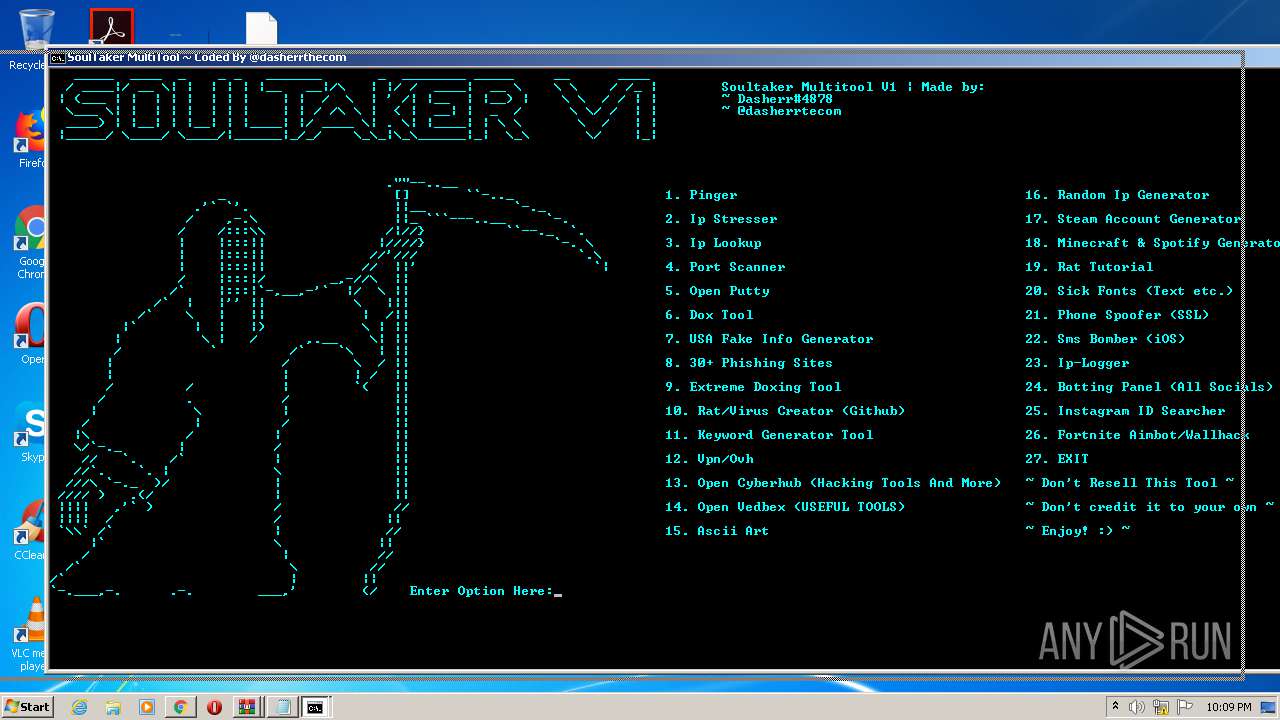
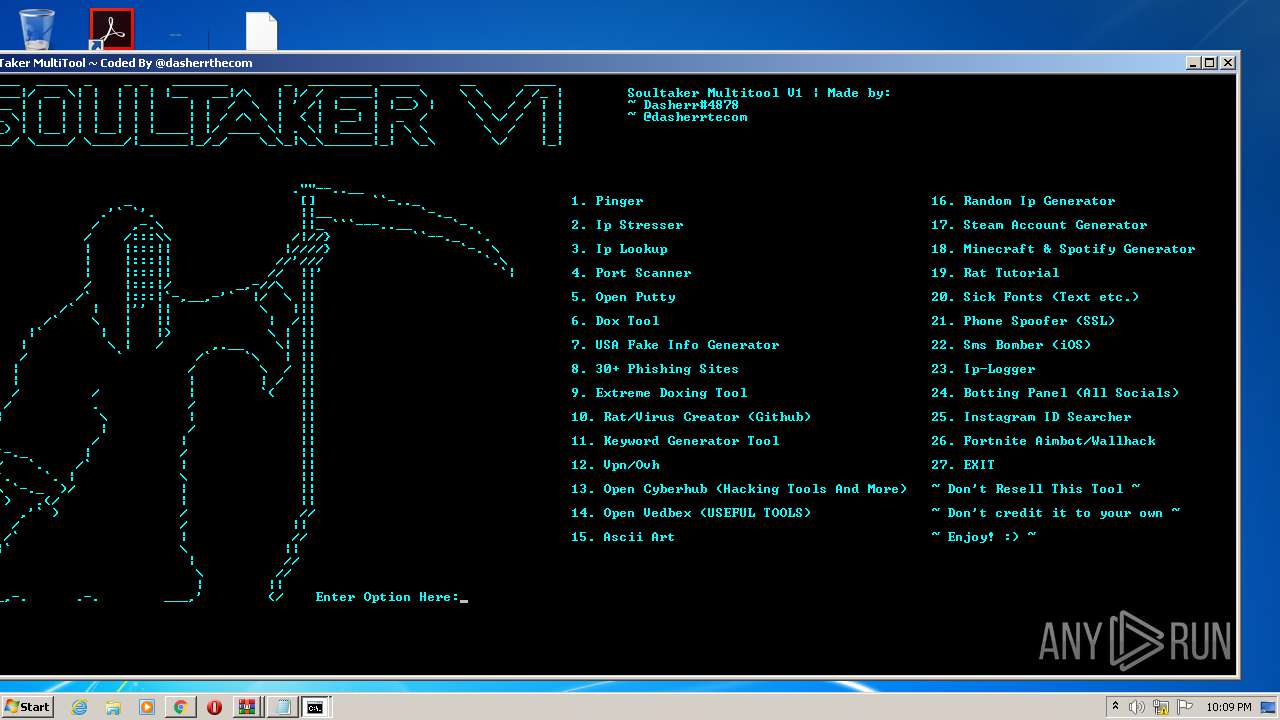
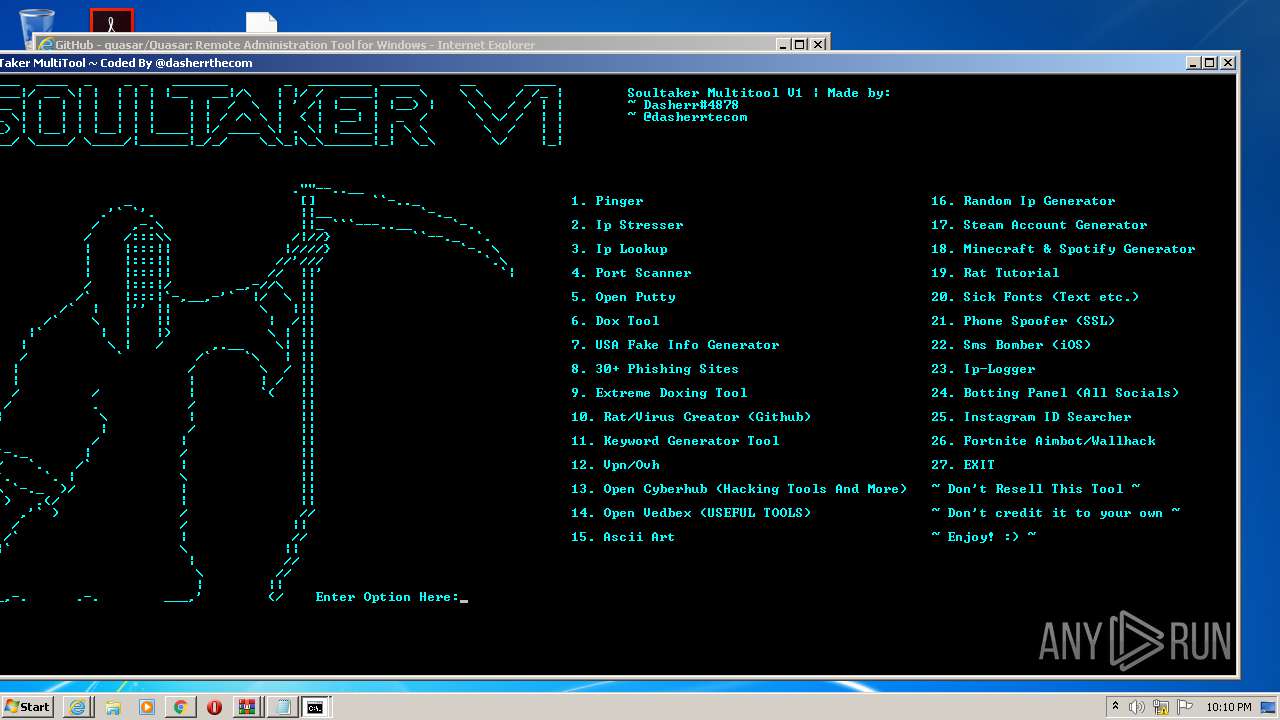
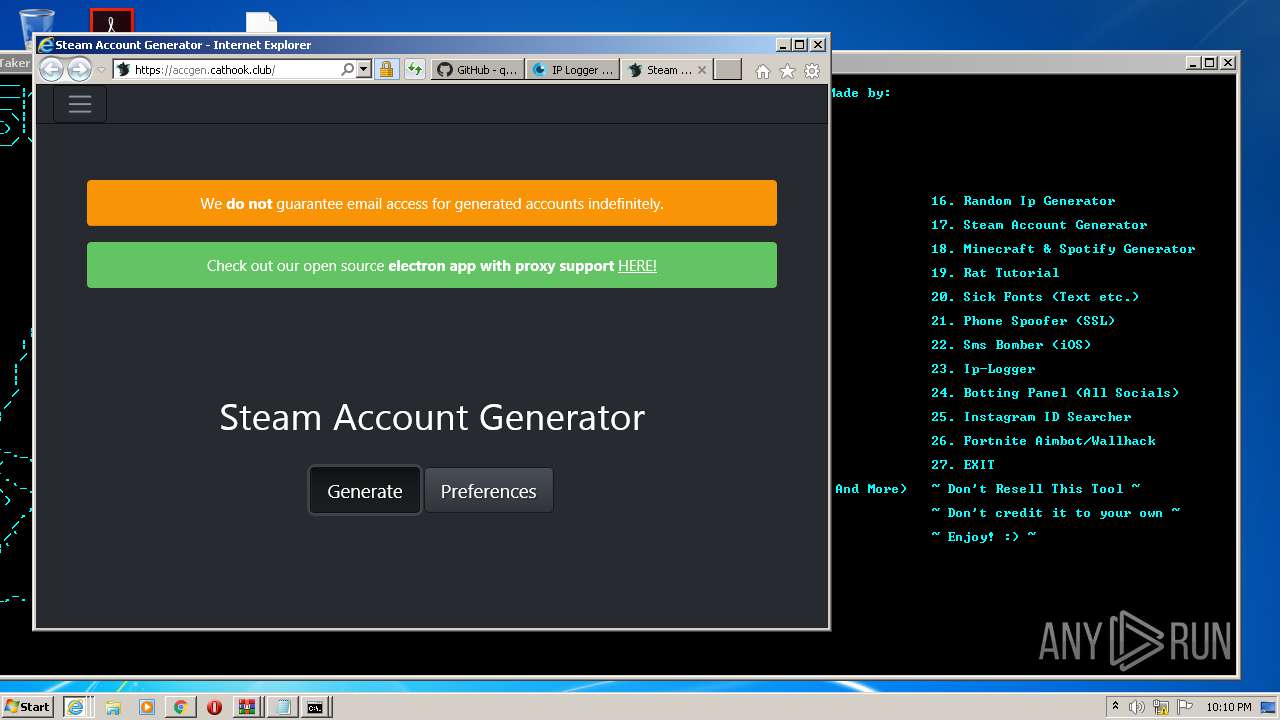
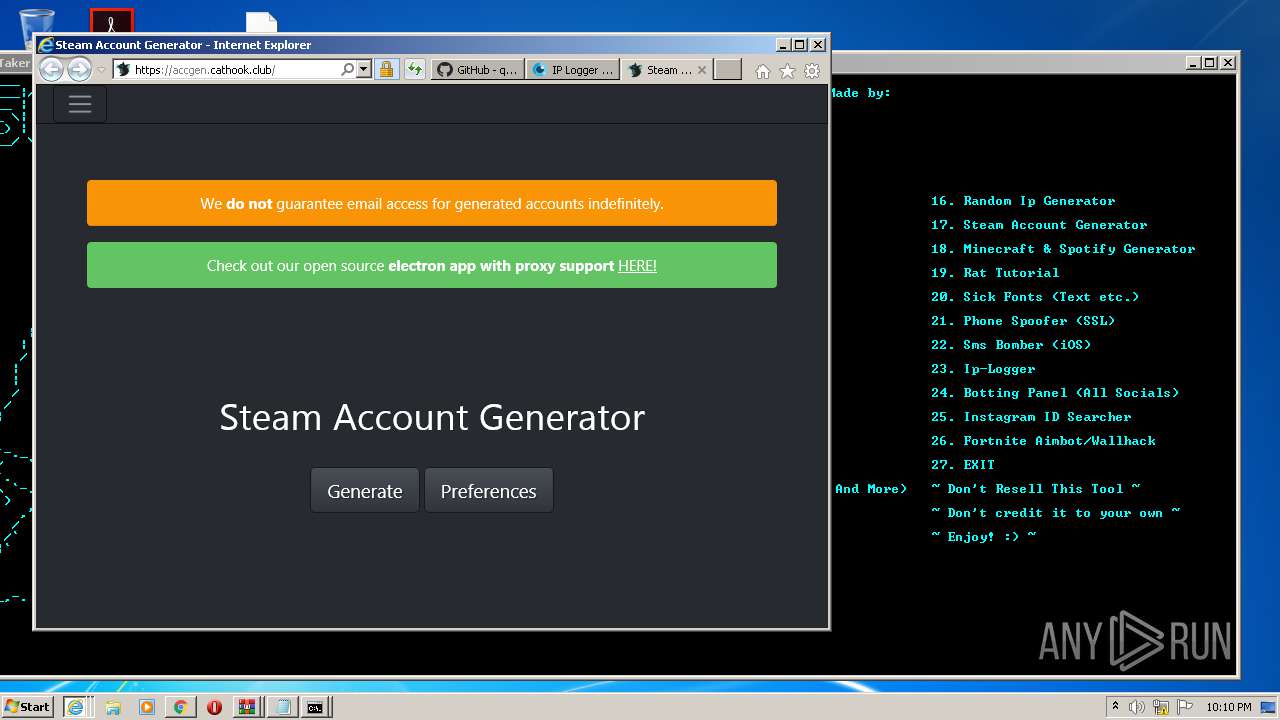
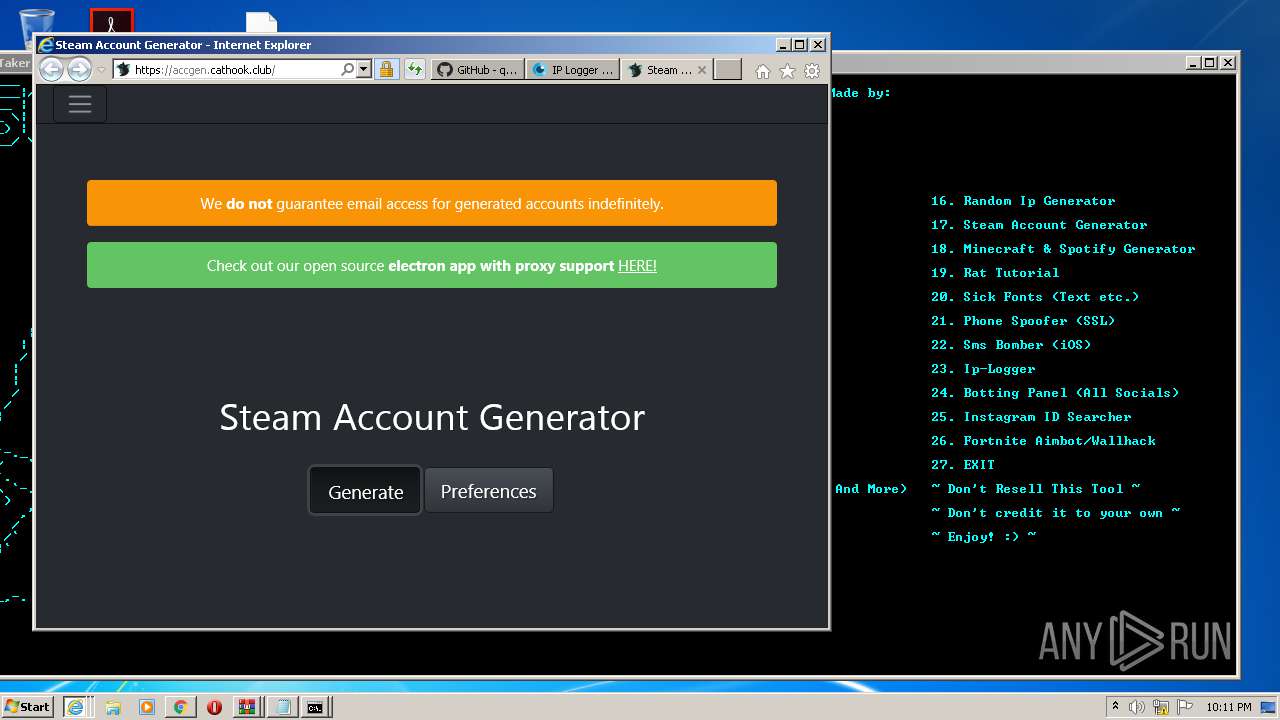
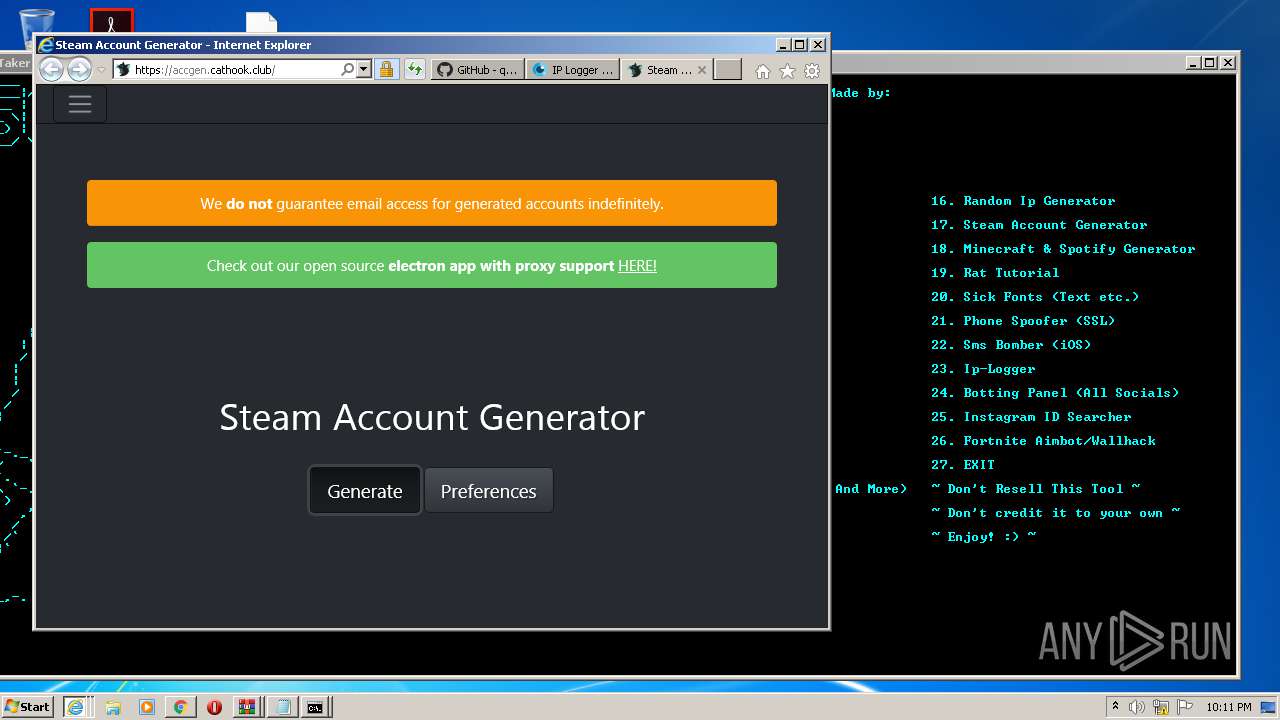
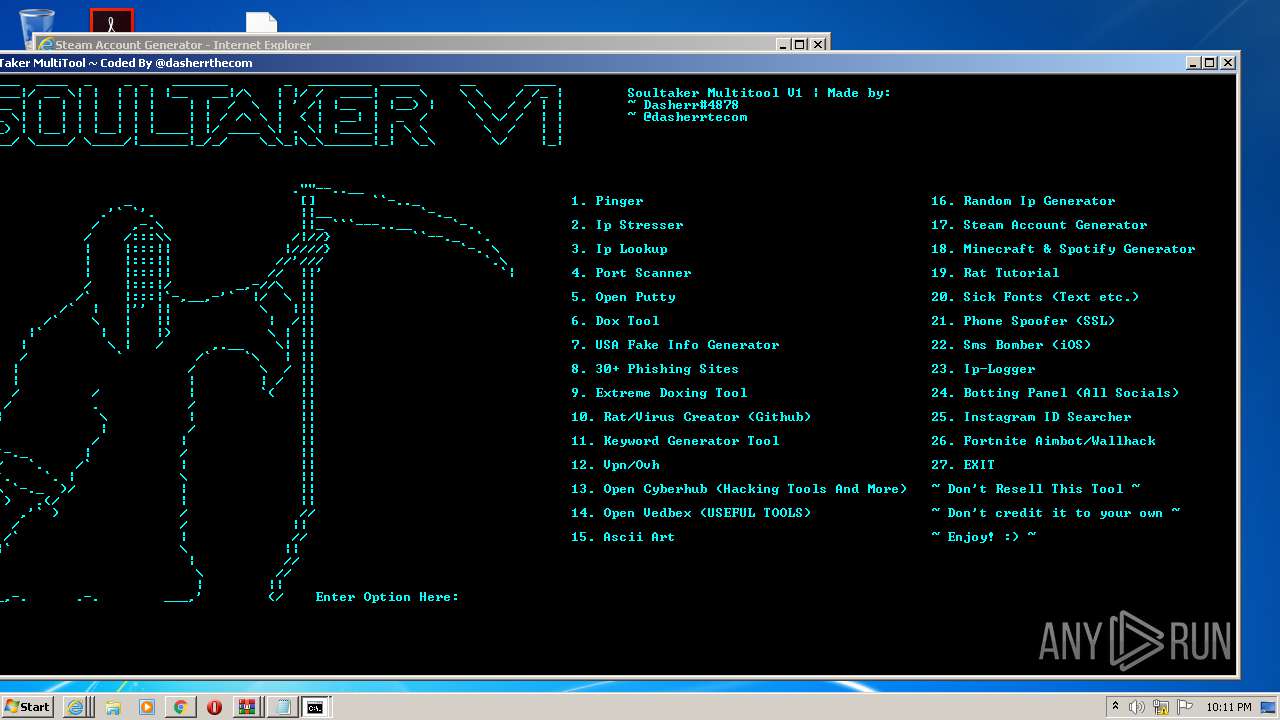
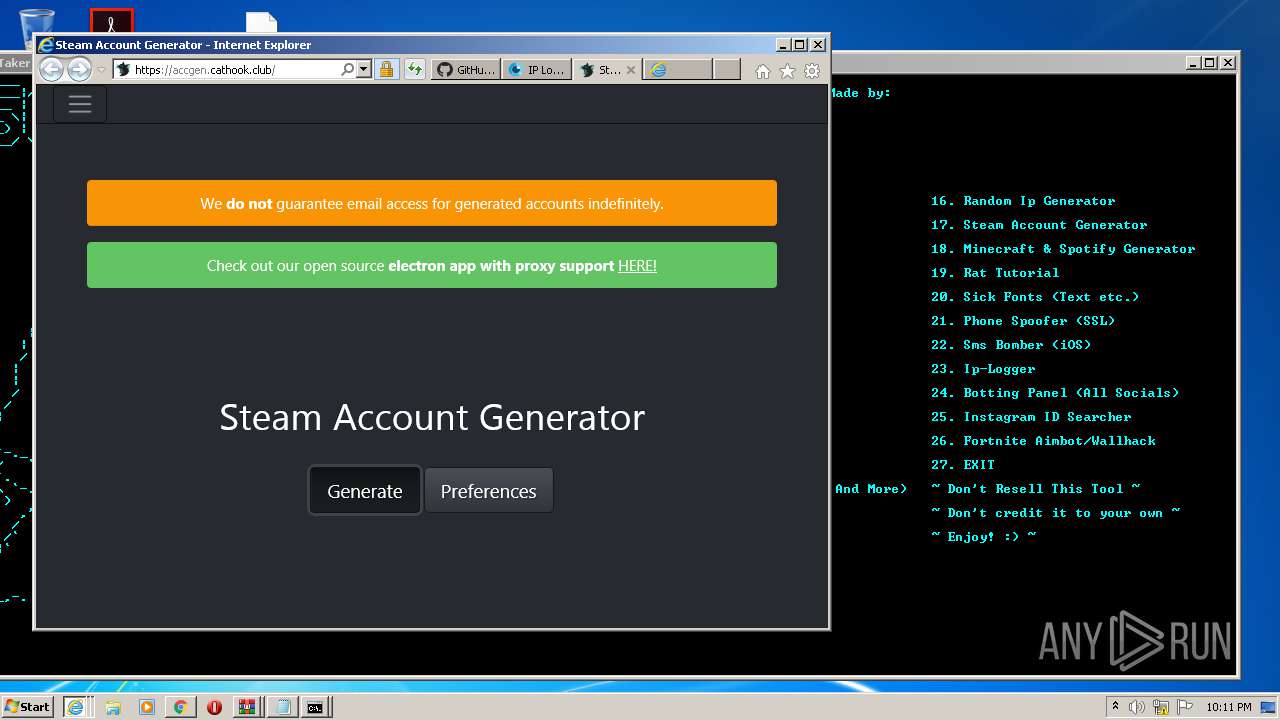
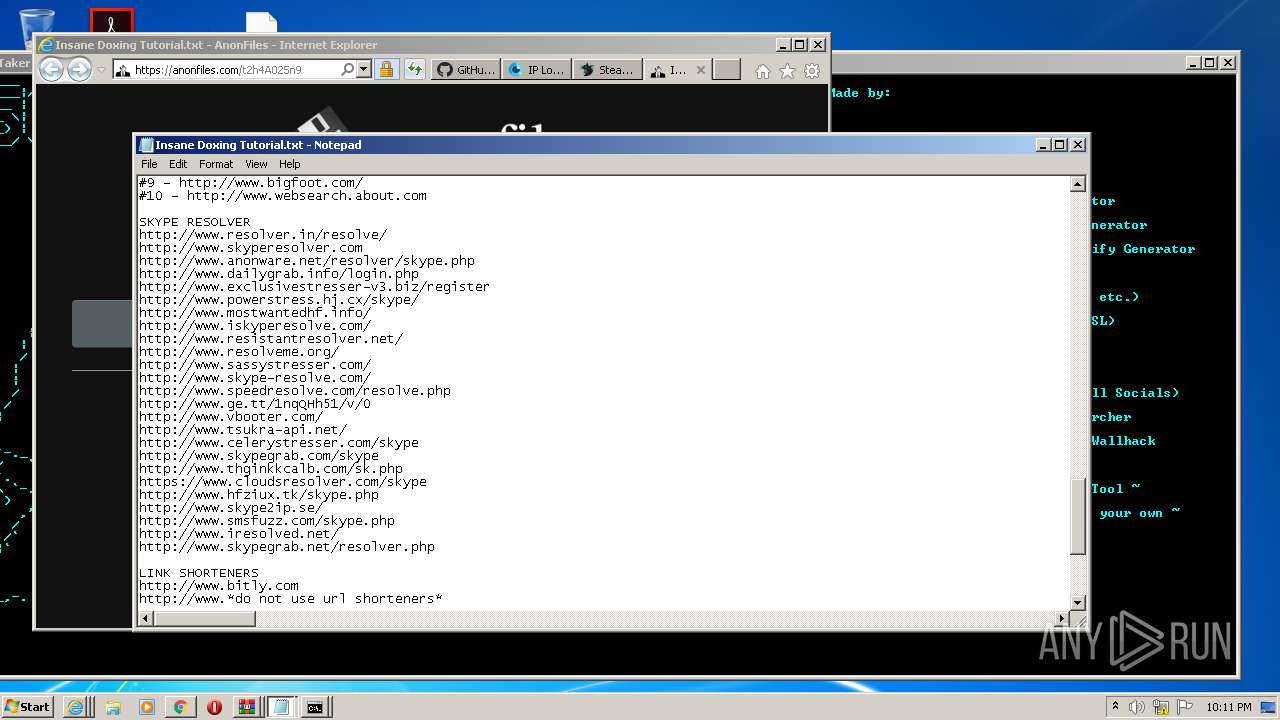
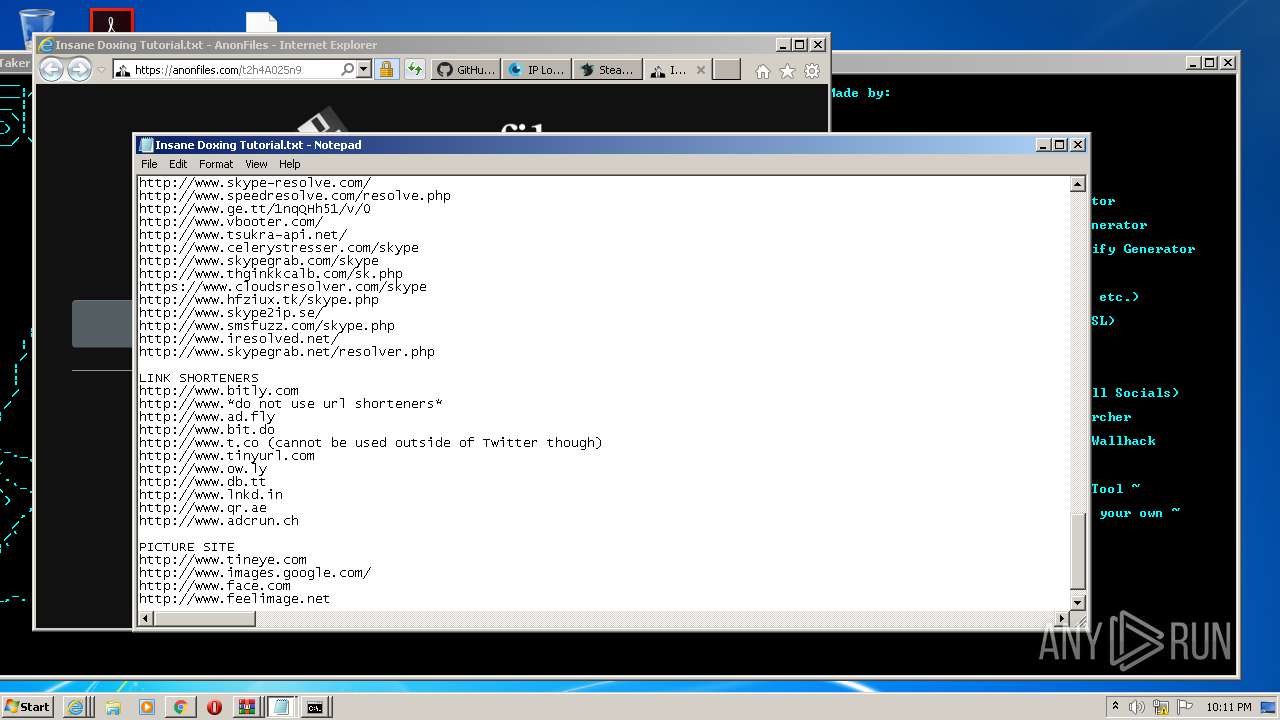
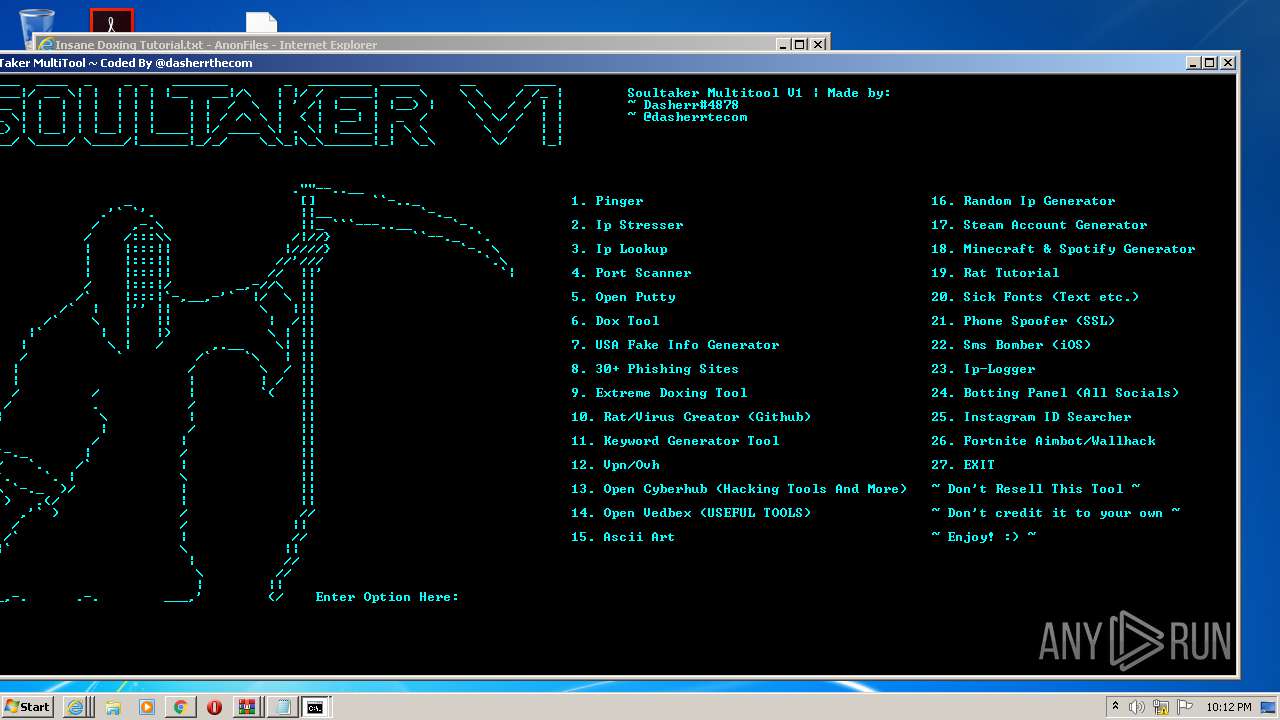
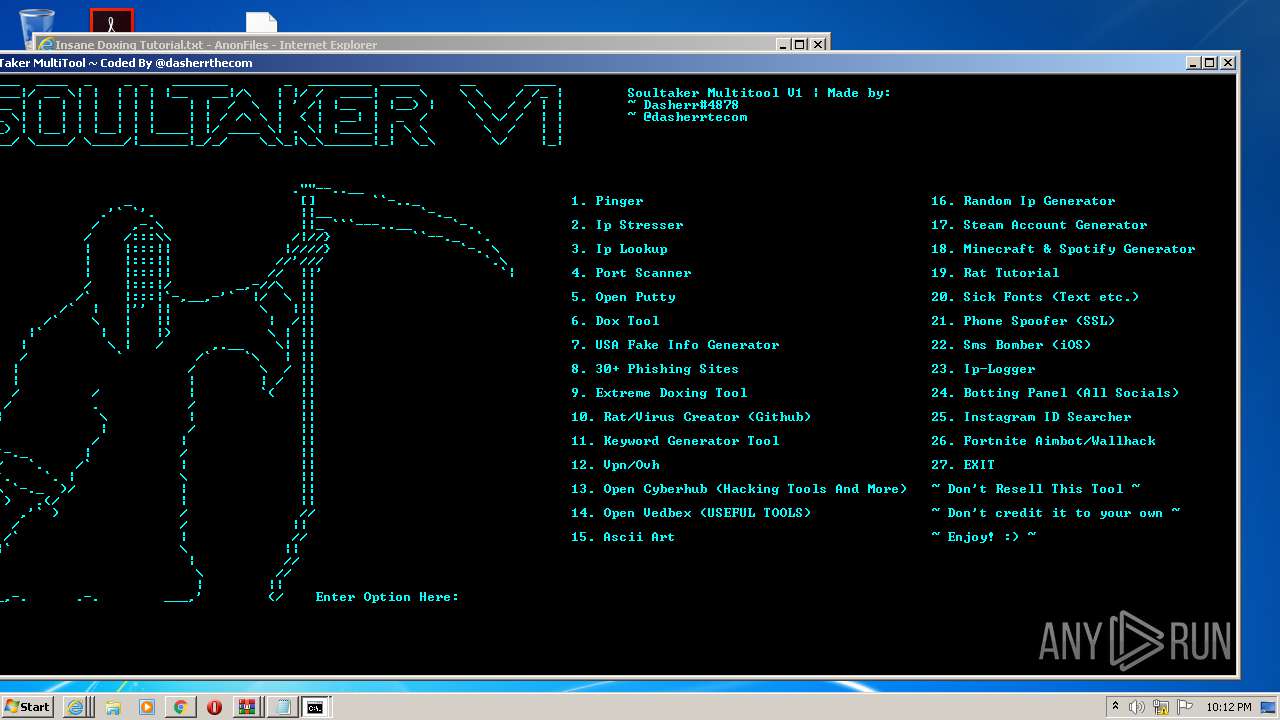
| URL: | https://github.com/Xooppp/SoulTaker-Multitool |
| Full analysis: | https://app.any.run/tasks/5784ac3d-c7f8-4f4a-adab-8d4d049b0cb6 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2020, 22:07:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4B024C37F64FF8FA143268E996E62E83 |
| SHA1: | E7BBA1D535129D2B30CAB46B45BE69DDB094A303 |
| SHA256: | FA8986DA5CF3D0D9262DA3F54B4B9F80AE519B8C7DB44DB0D1CEE5DBFF3F8E65 |
| SSDEEP: | 3:N8tEdVVzLJB1fS:2uNLRq |
MALICIOUS
Application was dropped or rewritten from another process
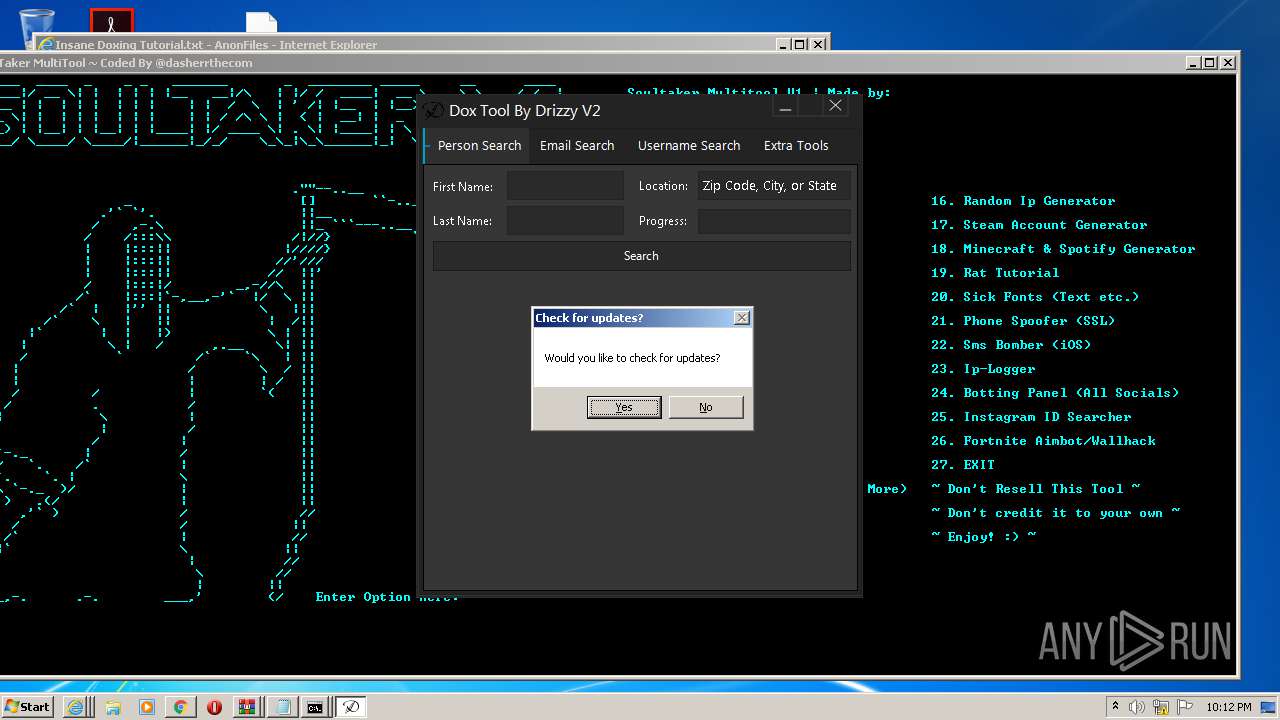
- Dox_Tool_V2.exe (PID: 2920)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1320)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2536)
Executed via COM
- explorer.exe (PID: 1964)
- explorer.exe (PID: 4036)
- explorer.exe (PID: 588)
- explorer.exe (PID: 1948)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2640)
Application launched itself
- WinRAR.exe (PID: 3600)
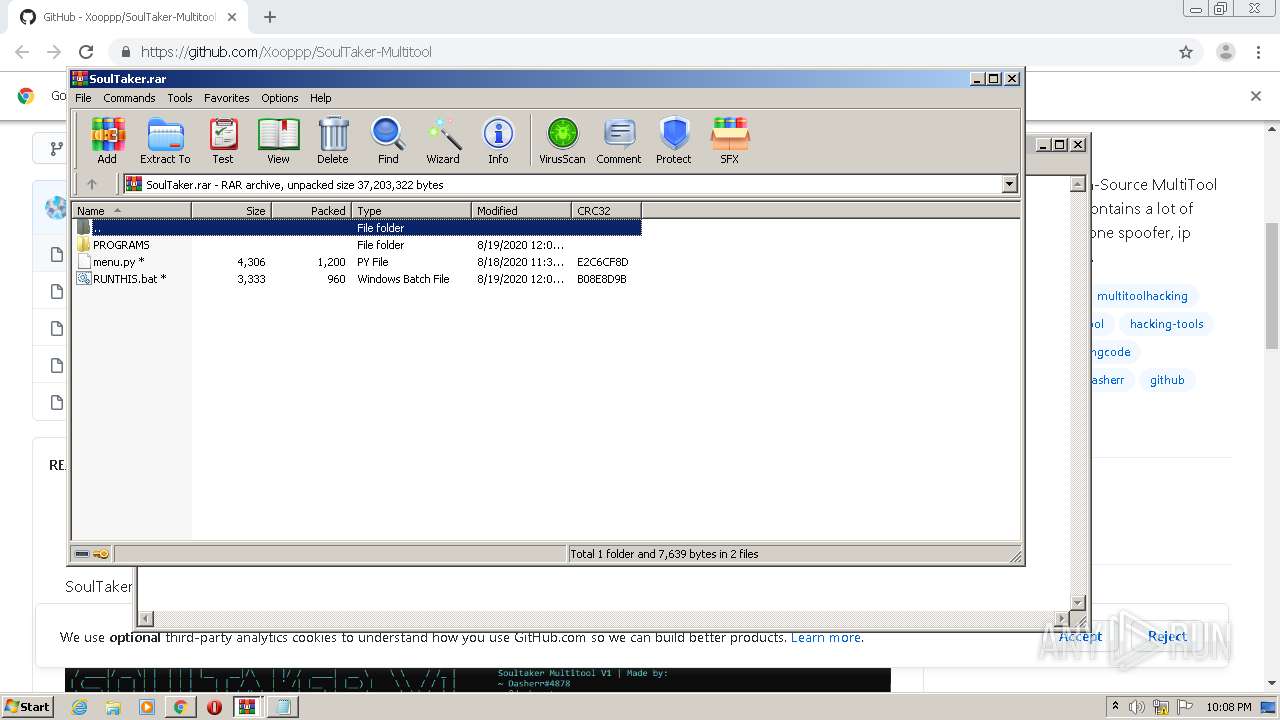
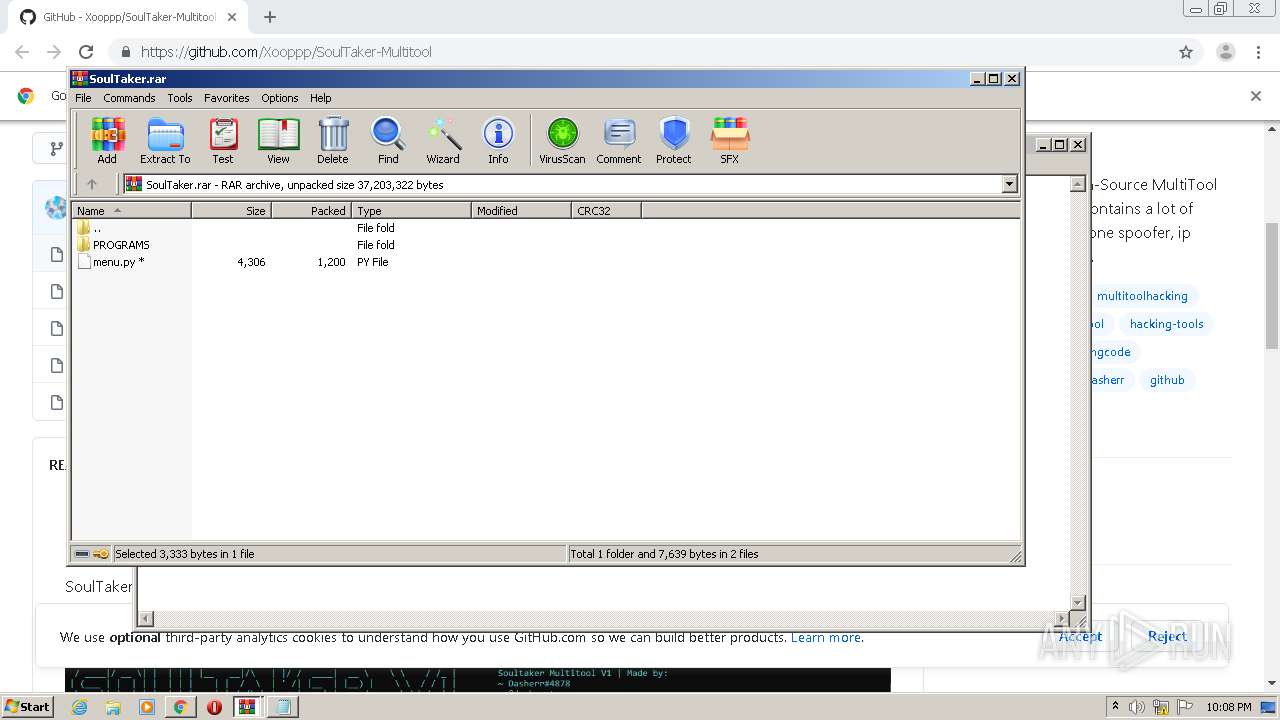
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2648)
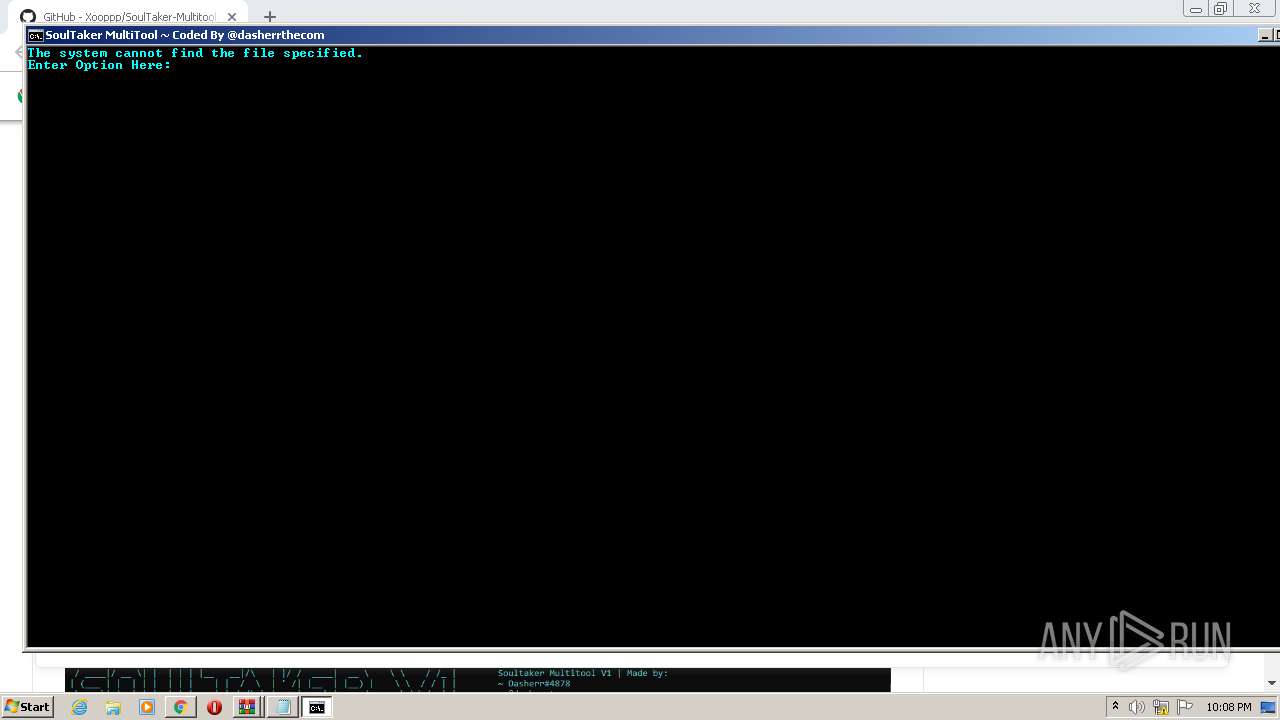
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2648)
Starts Internet Explorer
- explorer.exe (PID: 1964)
INFO
Application launched itself
- chrome.exe (PID: 2536)
- iexplore.exe (PID: 2600)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2648)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 2648)
Reads Internet Cache Settings
- chrome.exe (PID: 2536)
- iexplore.exe (PID: 2600)
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 1784)
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 3420)
Reads the hosts file
- chrome.exe (PID: 2536)
- chrome.exe (PID: 1340)
Changes internet zones settings
- iexplore.exe (PID: 2600)
Reads settings of System Certificates
- iexplore.exe (PID: 404)
- chrome.exe (PID: 1340)
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 2600)
- iexplore.exe (PID: 3420)
Manual execution by user
- cmd.exe (PID: 2100)
Creates files in the user directory
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 1784)
- iexplore.exe (PID: 2600)
- iexplore.exe (PID: 3420)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2640)
Reads internet explorer settings
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 1784)
- iexplore.exe (PID: 3420)
Changes settings of System certificates
- iexplore.exe (PID: 2600)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2600)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
50
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1076,10805985419034098665,13415155109684473820,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9595824306469374022 --mojo-platform-channel-handle=1080 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2600 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 588 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2600 CREDAT:3282185 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
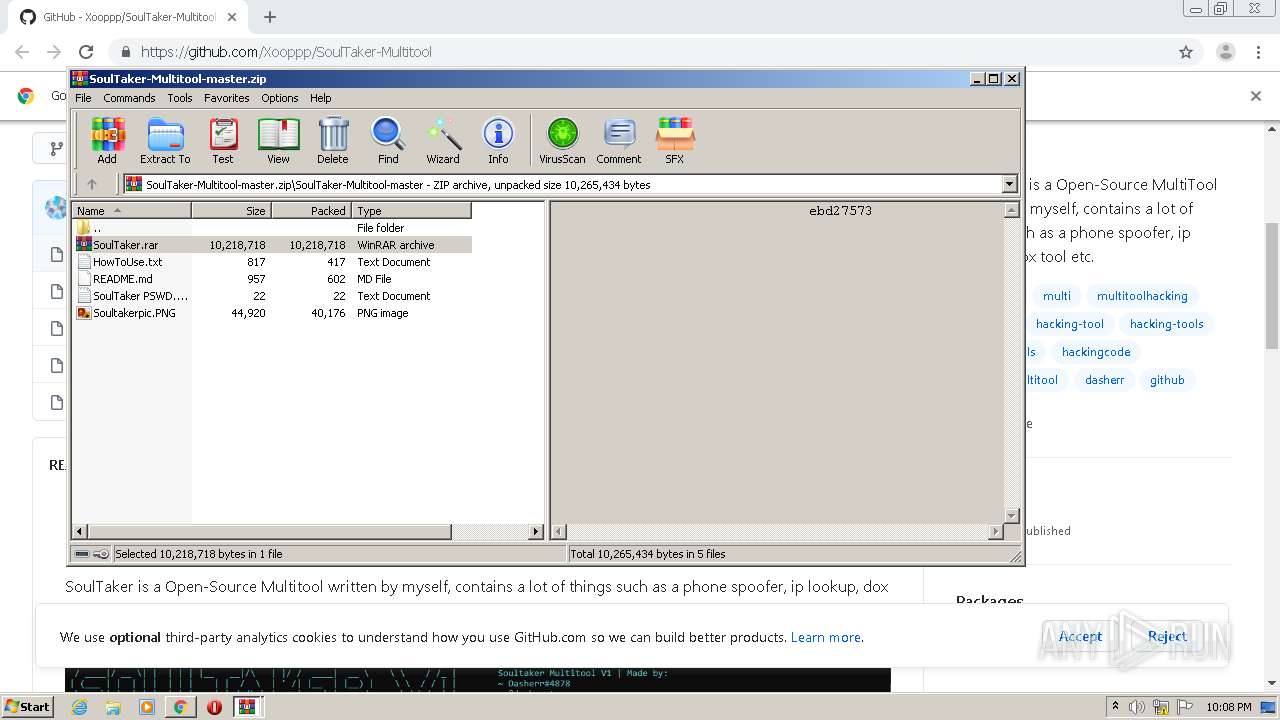
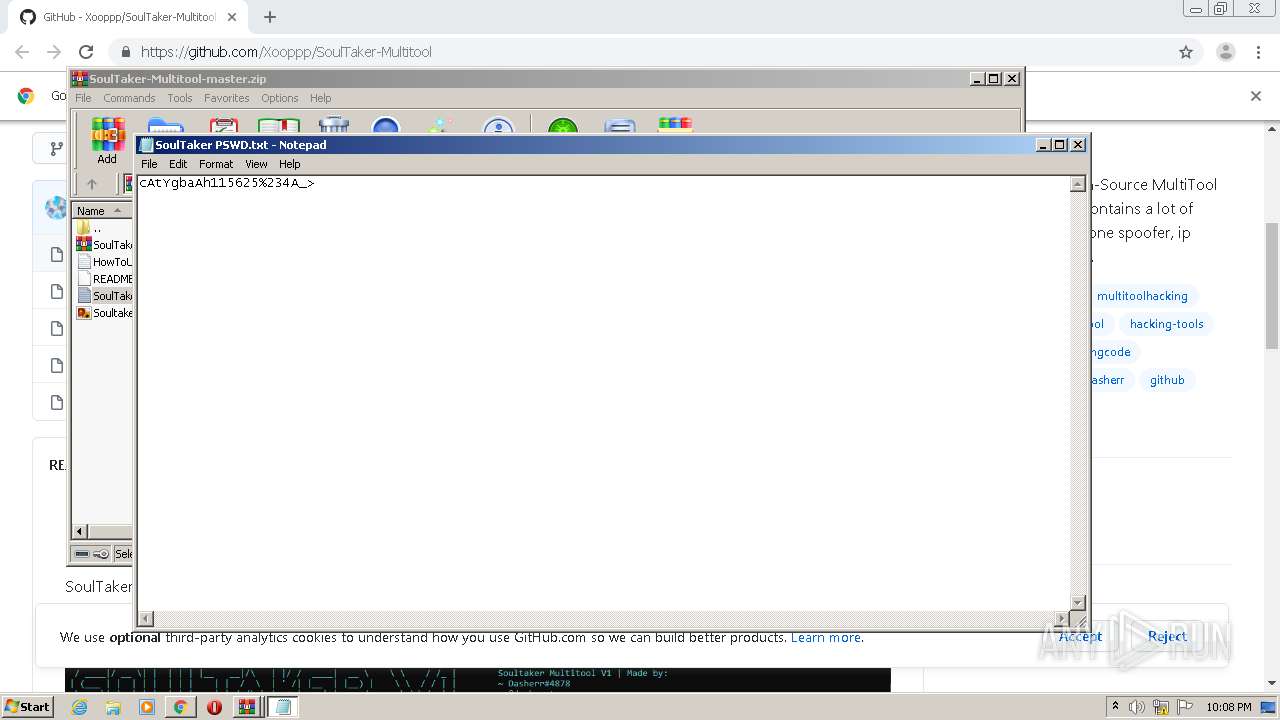
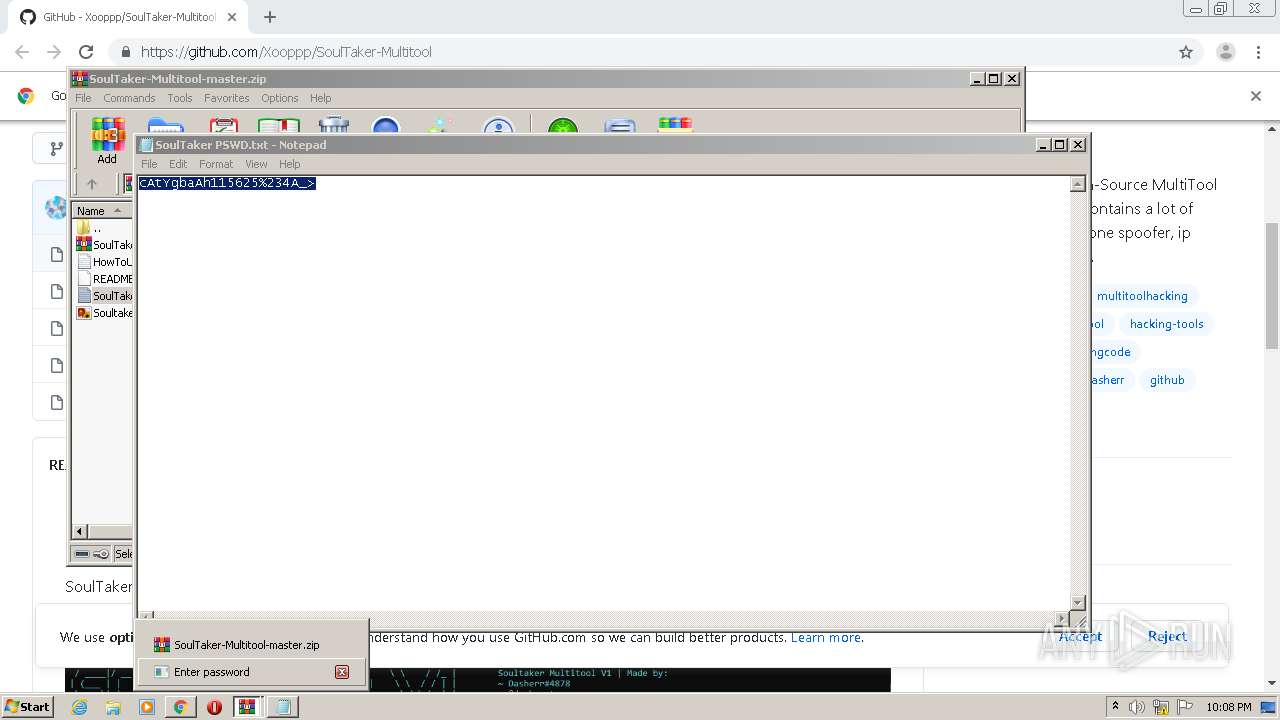
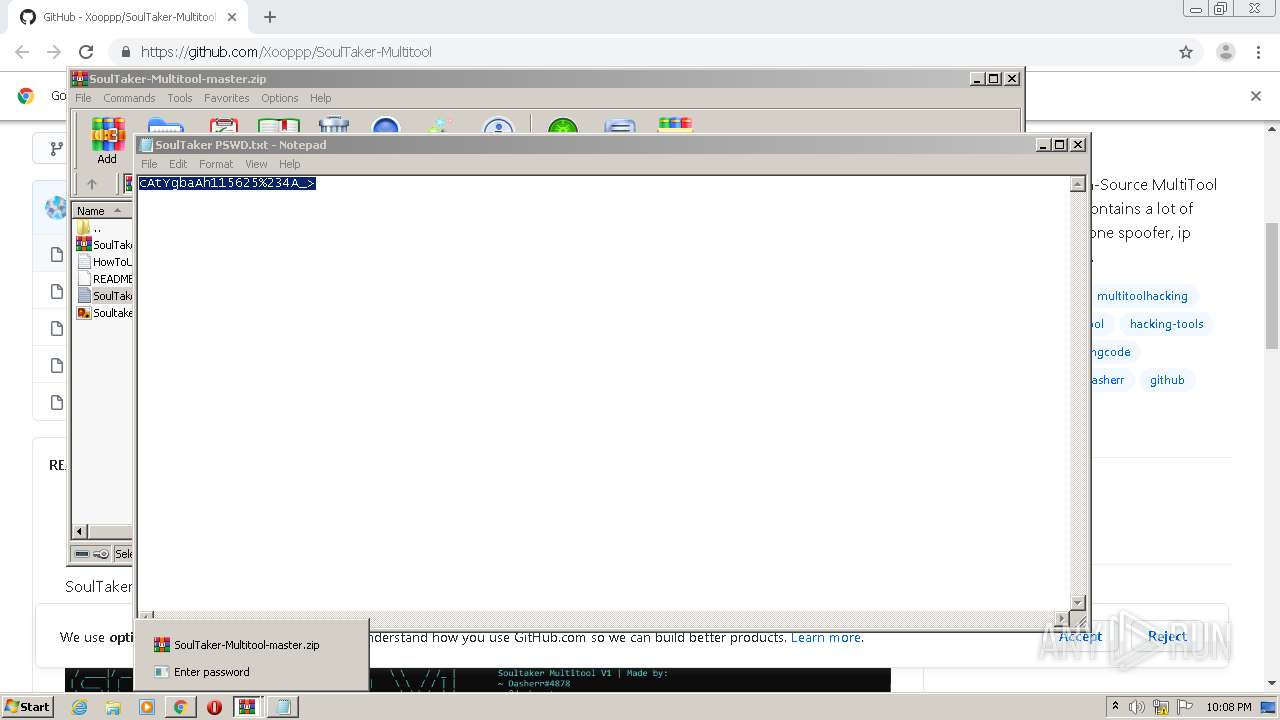
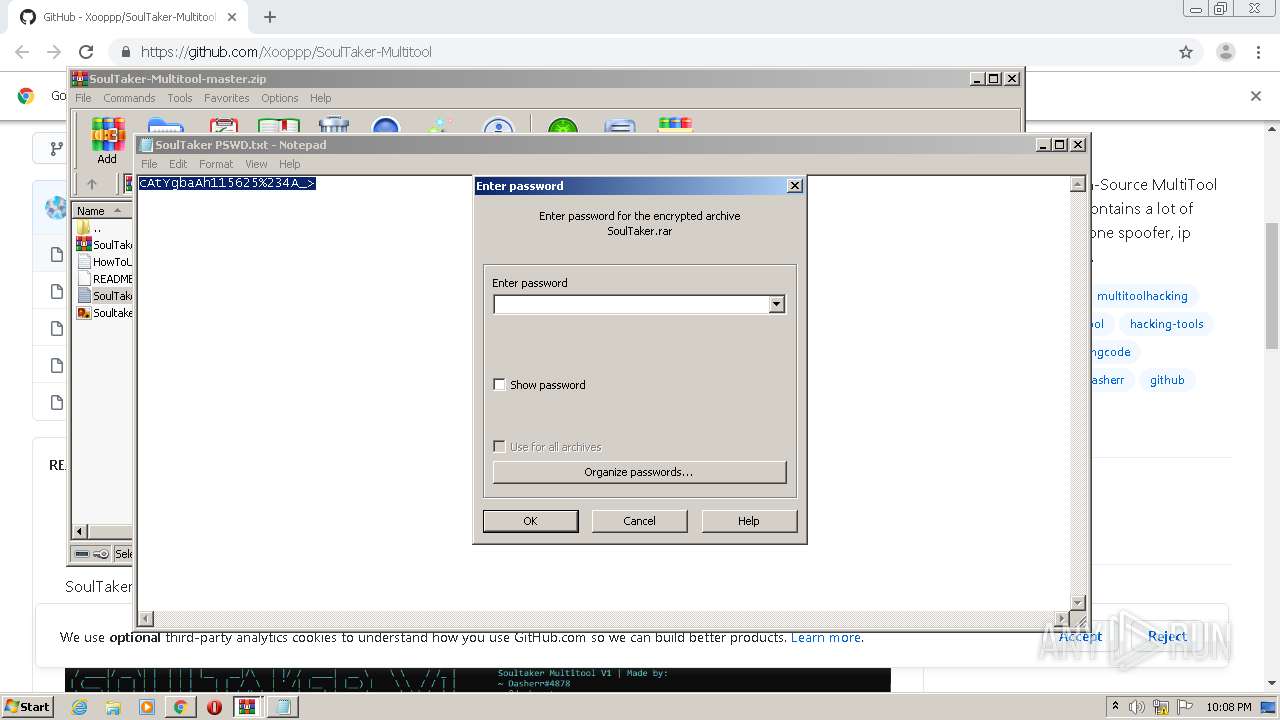
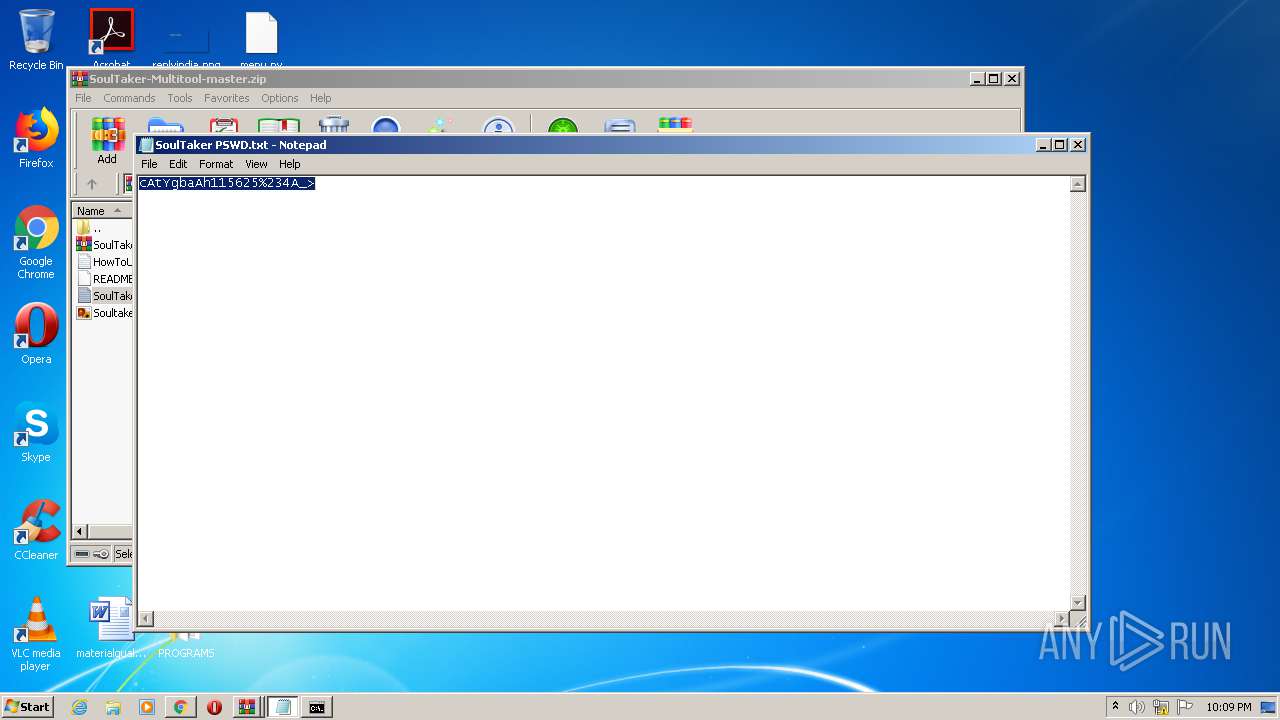
| 956 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3600.33647\SoulTaker PSWD.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
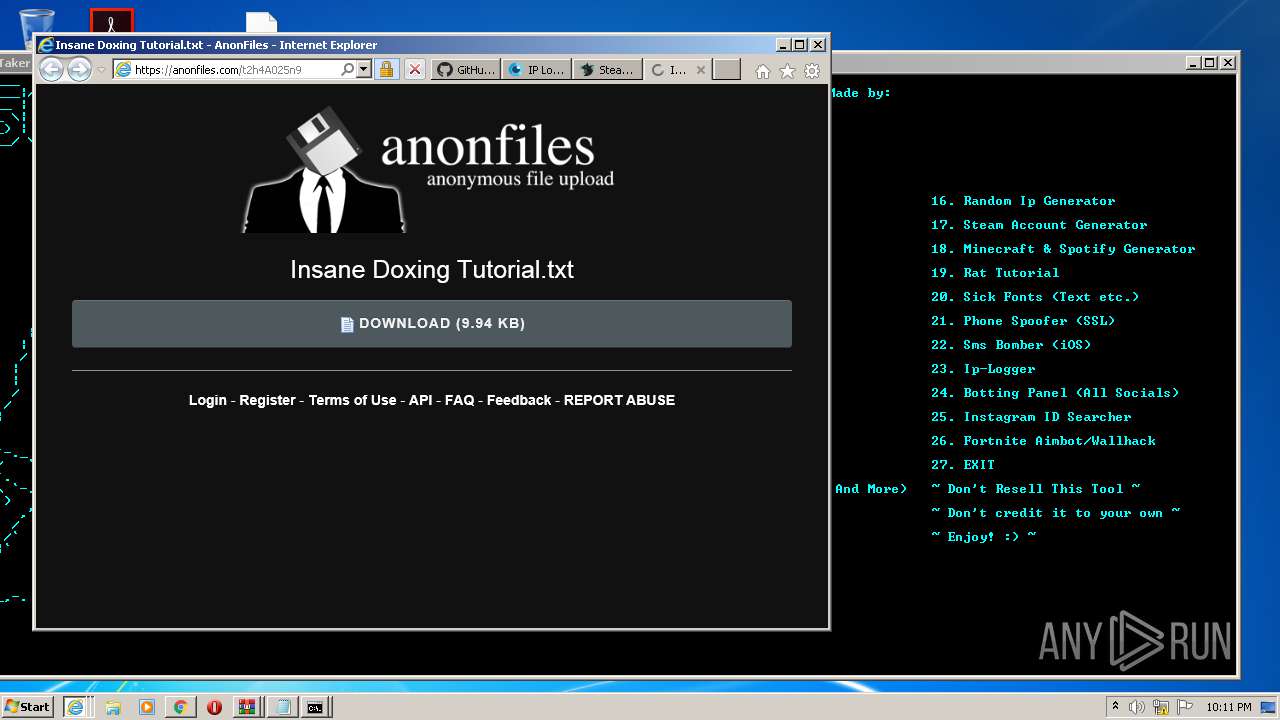
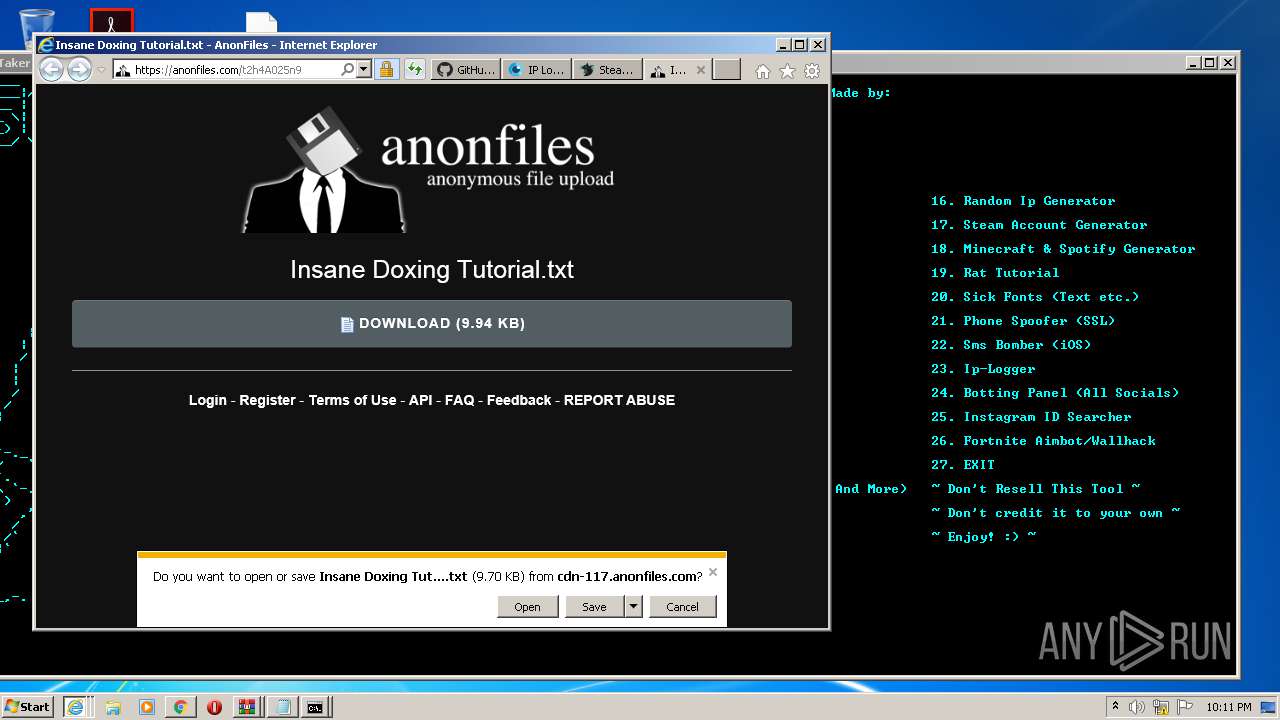
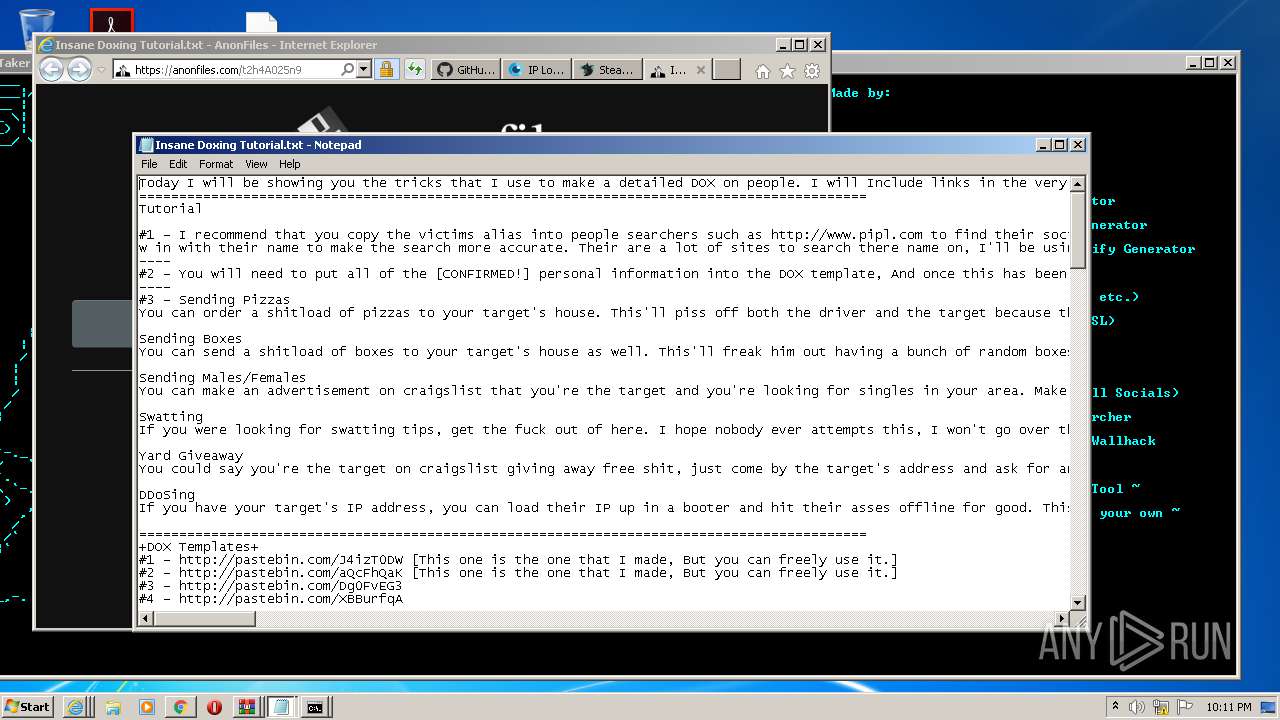
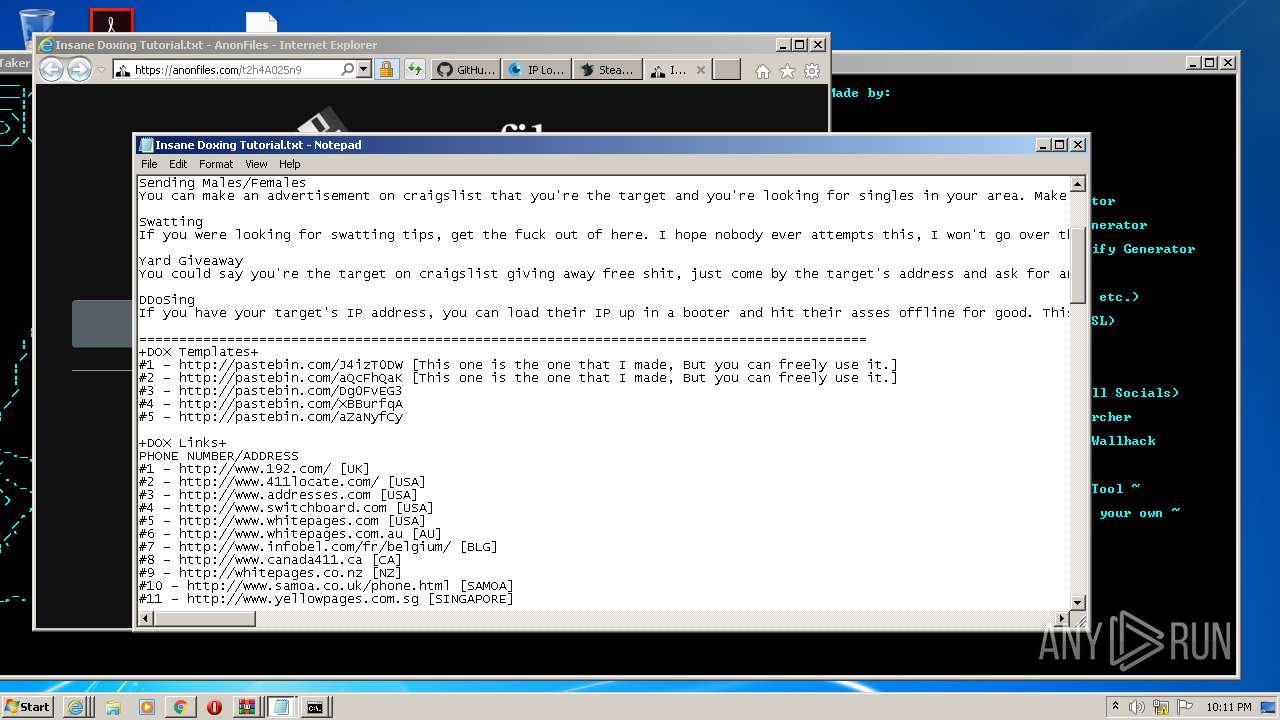
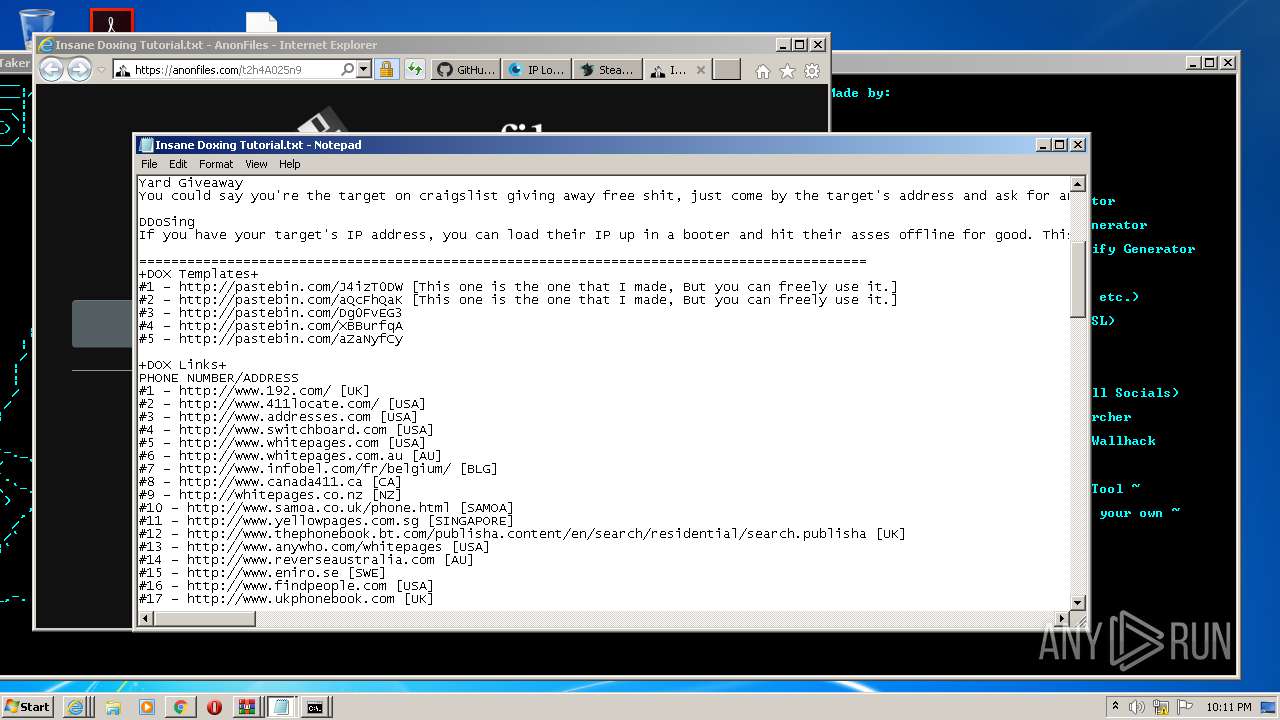
| 976 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Insane Doxing Tutorial.txt | C:\Windows\system32\NOTEPAD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIb2648.35704\RUNTHIS.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,10805985419034098665,13415155109684473820,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14307574369165838417 --mojo-platform-channel-handle=3596 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,10805985419034098665,13415155109684473820,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1574888009547754773 --mojo-platform-channel-handle=4120 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1320 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 110
Read events
4 675
Write events
425
Delete events
10
Modification events
| (PID) Process: | (2144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2536-13249174046071500 |
Value: 259 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2536-13249174046071500 |
Value: 259 | |||
Executable files
5
Suspicious files
188
Text files
672
Unknown types
79
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FA5C91E-9E8.pma | — | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b239a2e6-716e-4f79-bf8a-7c04e7434821.tmp | — | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF12400e.TMP | text | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF1240e9.TMP | text | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | text | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF1242fc.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
72
TCP/UDP connections
214
DNS requests
105
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1340 | chrome.exe | GET | 302 | 216.58.212.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZDM4QUFXaVZ5bThYeHlpdXd5bzU1RzRQUQ/8220.313.1.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 524 b | whitelisted |
1784 | iexplore.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1d2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT4YwNSyUnwC88de5a5l4eUO%2BLQewQUsd0yXei3N3LSzlzOJv5HeeIBCOkCEQC%2FMA4I7UmbBAoAAAAAYUwS | US | der | 472 b | whitelisted |
1784 | iexplore.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1d2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT4YwNSyUnwC88de5a5l4eUO%2BLQewQUsd0yXei3N3LSzlzOJv5HeeIBCOkCEQCectgGwoAG2wkAAAAAL%2B3d | US | der | 472 b | whitelisted |
1340 | chrome.exe | GET | 200 | 173.194.163.108:80 | http://r6---sn-5go7yne6.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZDM4QUFXaVZ5bThYeHlpdXd5bzU1RzRQUQ/8220.313.1.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=i8&mip=196.244.192.6&mm=28&mn=sn-5go7yne6&ms=nvh&mt=1604700320&mv=m&mvi=6&pl=24&shardbypass=yes | US | crx | 839 Kb | whitelisted |
1784 | iexplore.exe | GET | 200 | 23.55.163.61:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | US | der | 1.37 Kb | whitelisted |
1784 | iexplore.exe | GET | 200 | 23.55.163.77:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | US | der | 1.37 Kb | whitelisted |
1784 | iexplore.exe | GET | 200 | 23.55.163.48:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgRcoldVaFXxn6rjVoDjZ5aWKg%3D%3D | US | der | 527 b | whitelisted |
1784 | iexplore.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEEpsSX8krXFHAgAAAAB%2FFIg%3D | US | der | 471 b | whitelisted |
404 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
404 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAVXyAsoJoOhewoRRJMpa3k%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1340 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1340 | chrome.exe | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
1340 | chrome.exe | 140.82.121.4:443 | github.com | — | US | malicious |
1340 | chrome.exe | 185.199.108.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
1340 | chrome.exe | 172.217.18.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1340 | chrome.exe | 151.101.128.133:443 | avatars0.githubusercontent.com | Fastly | US | suspicious |
1340 | chrome.exe | 216.58.206.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
— | — | 140.82.121.4:443 | github.com | — | US | malicious |
1340 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1340 | chrome.exe | 216.58.212.161:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
github.githubassets.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
avatars0.githubusercontent.com |
| whitelisted |
avatars1.githubusercontent.com |
| whitelisted |
avatars2.githubusercontent.com |
| whitelisted |
avatars3.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1784 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1784 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1784 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
1784 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2600 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2600 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2600 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2600 | iexplore.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
15 ETPRO signatures available at the full report