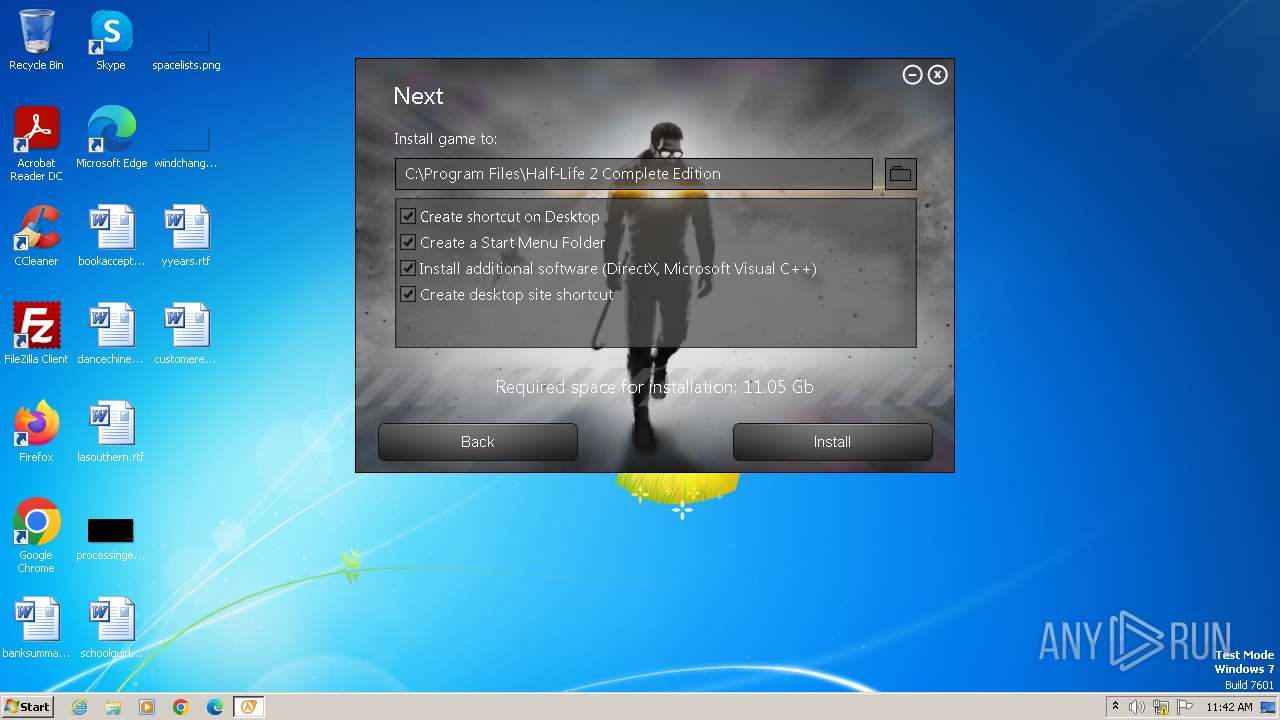
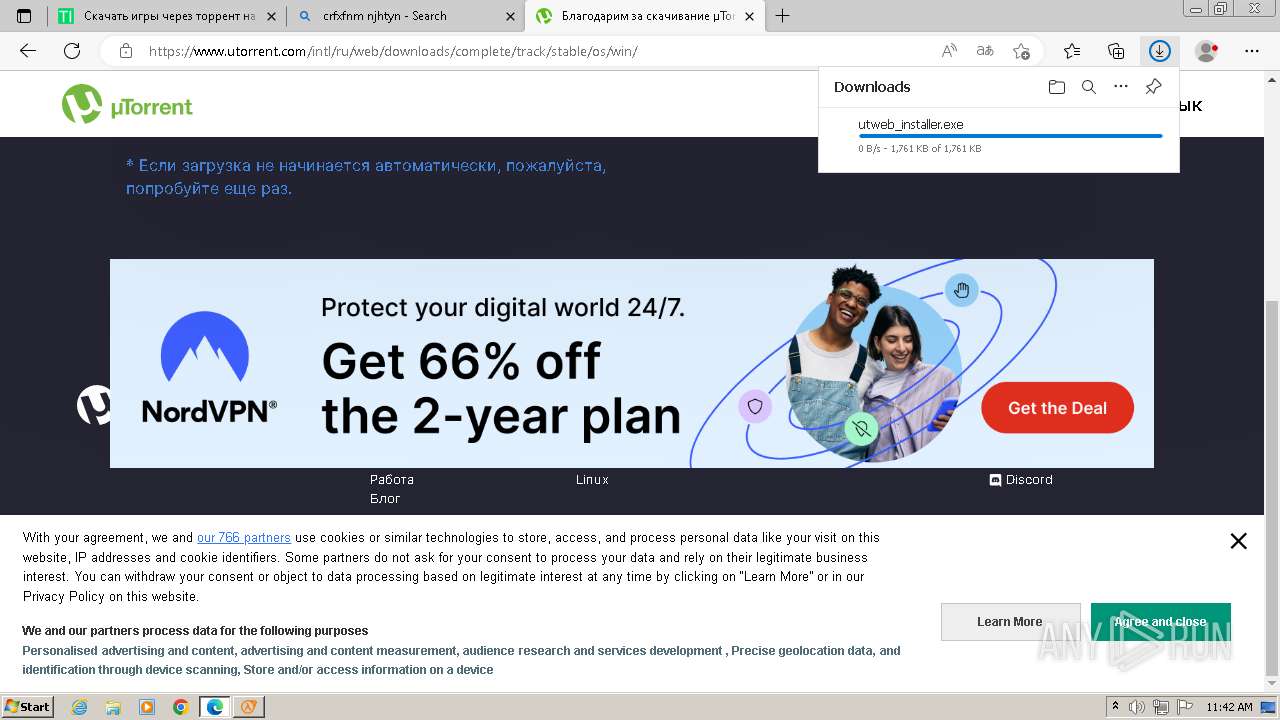
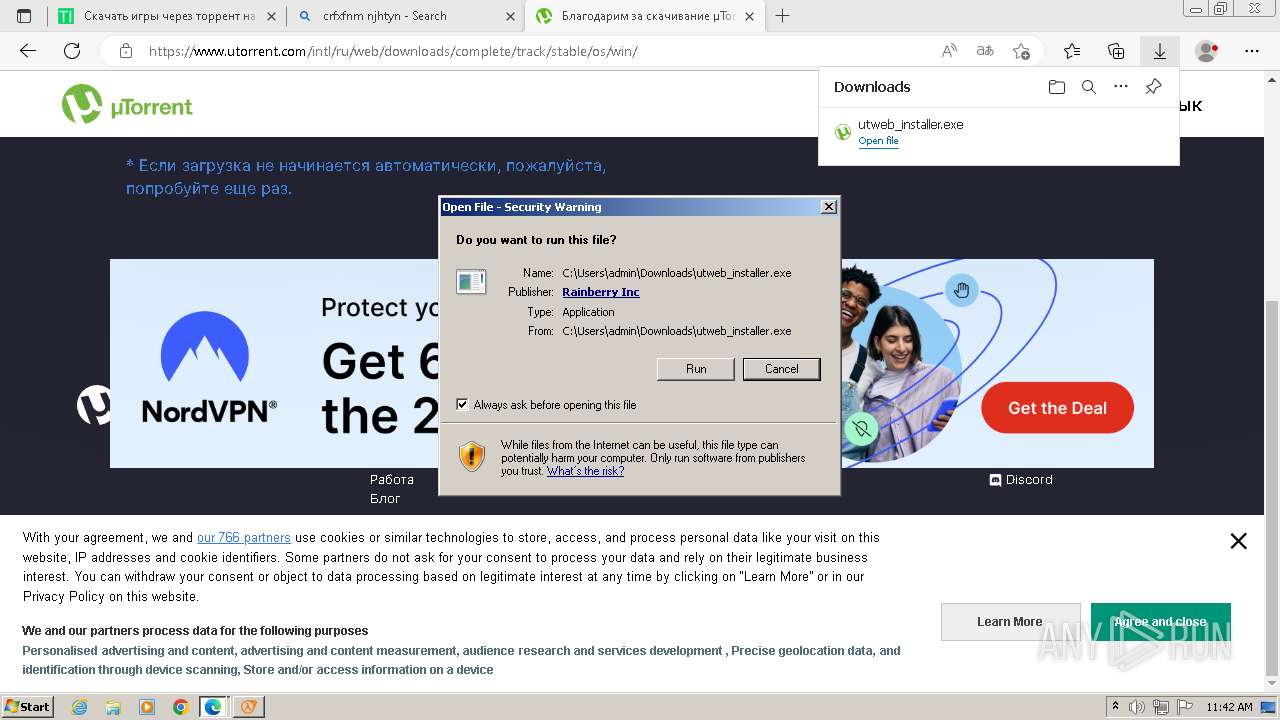
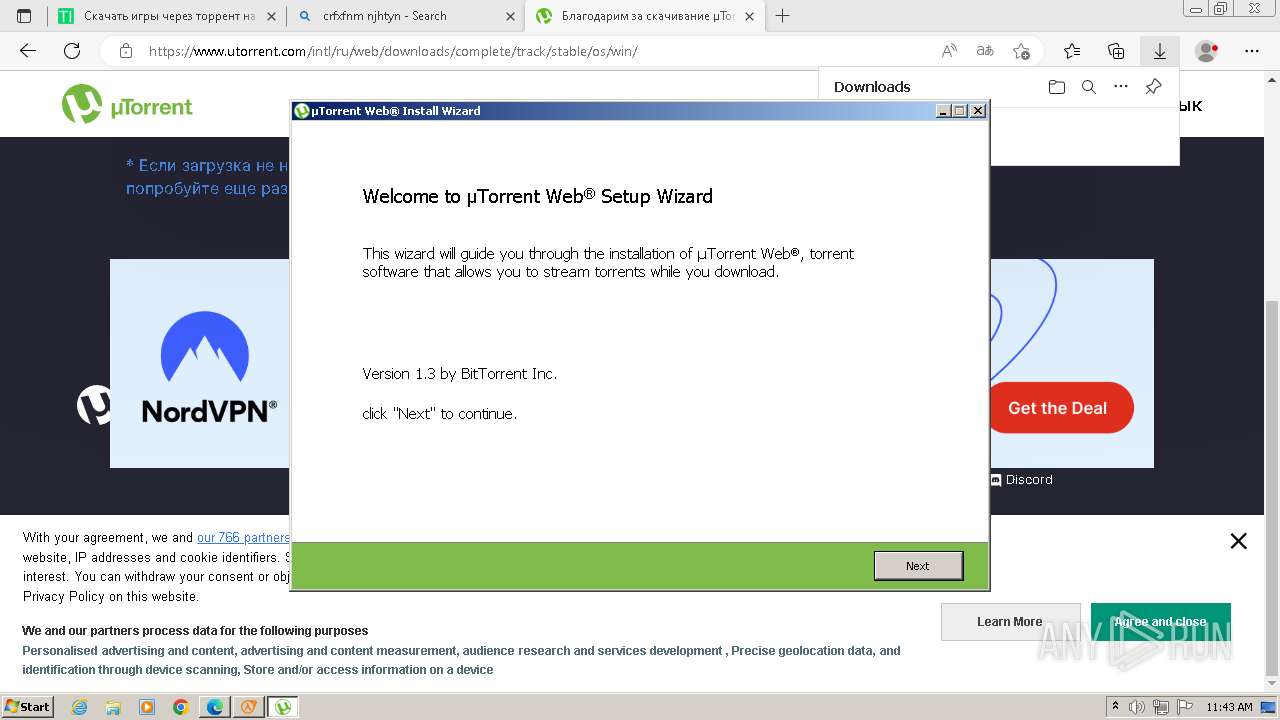
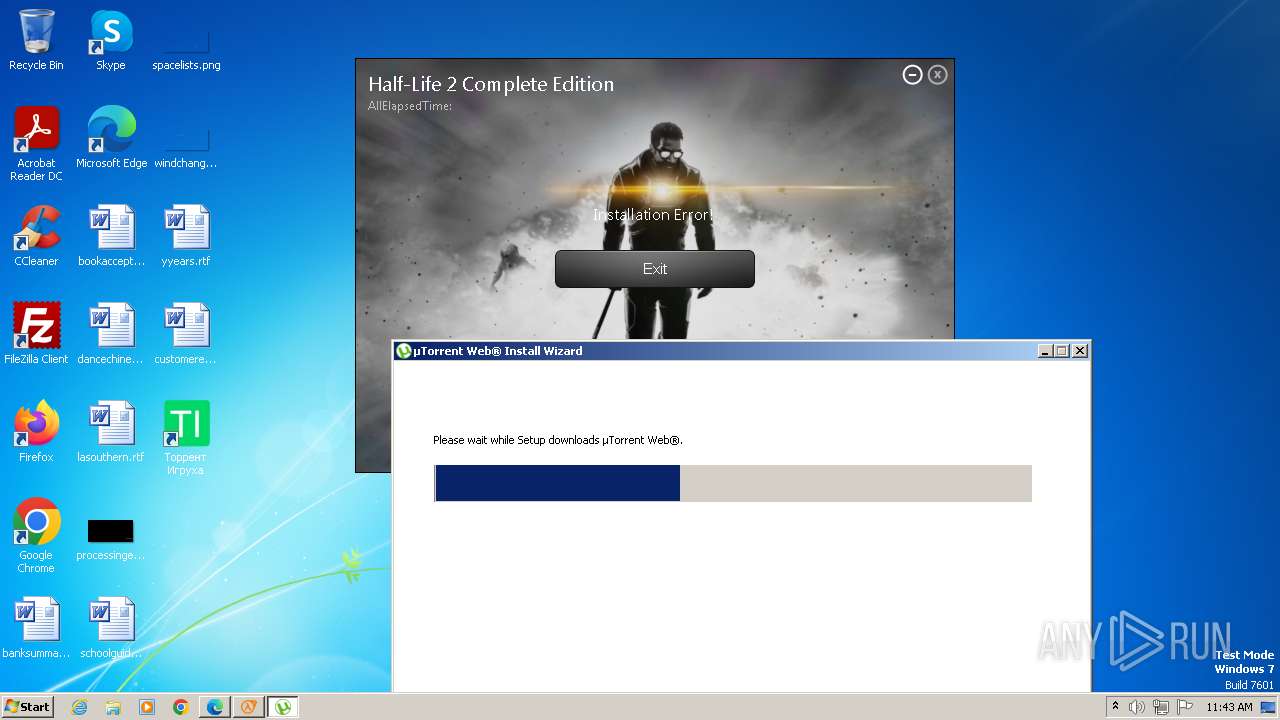
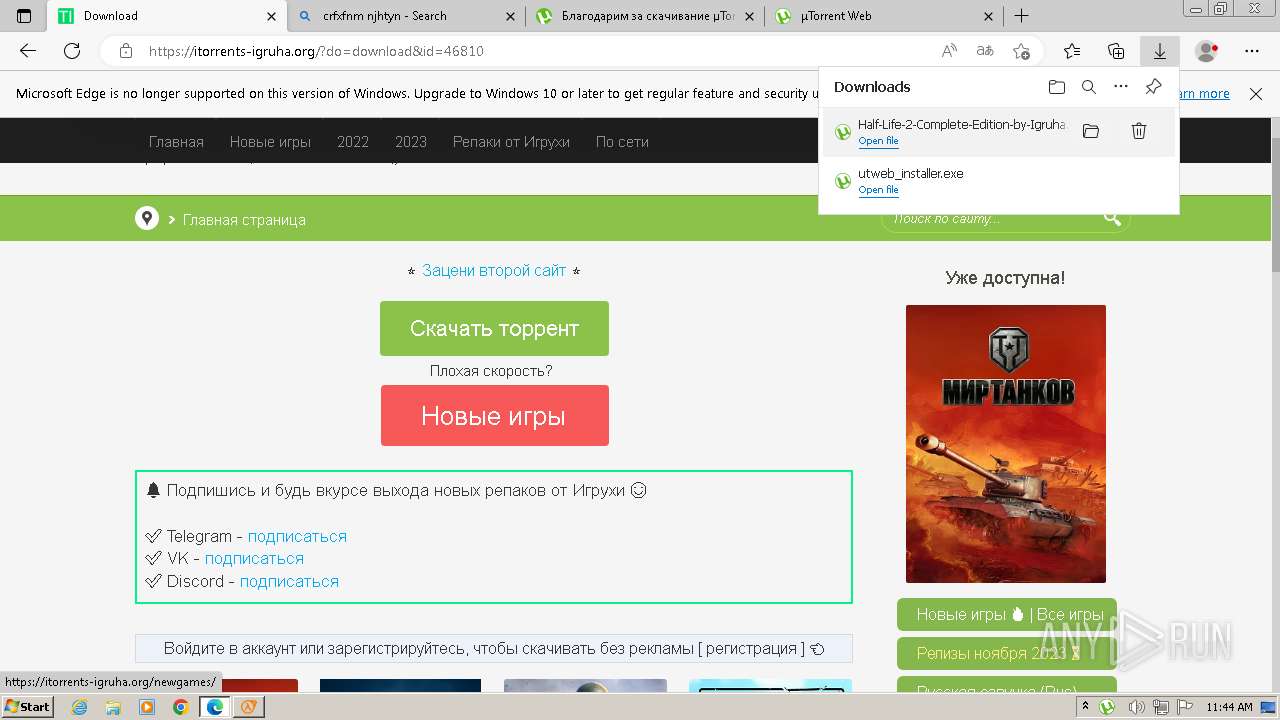
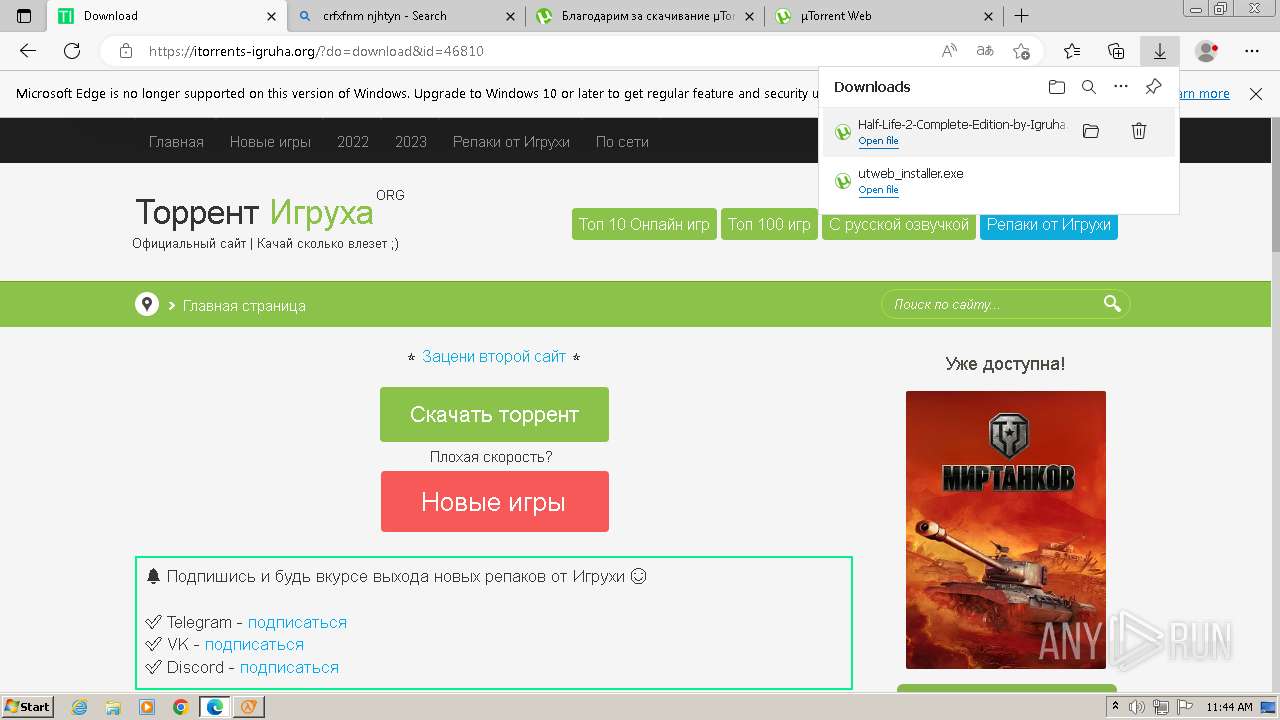
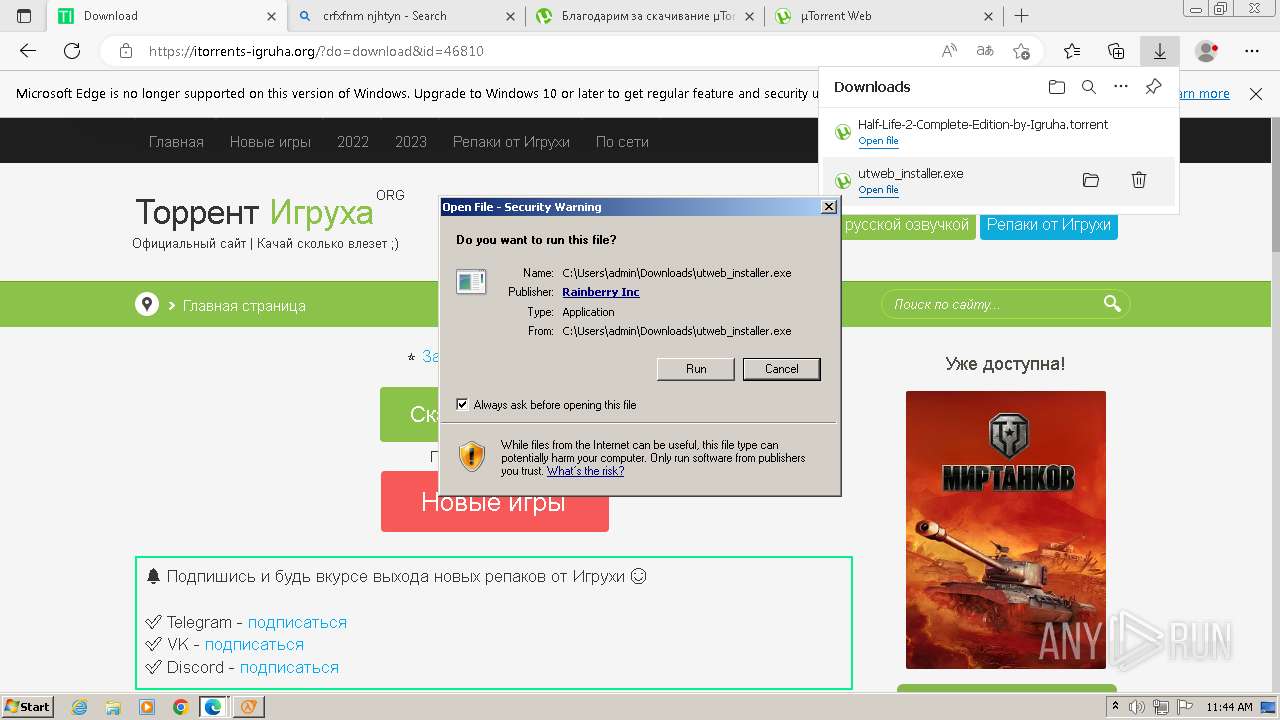
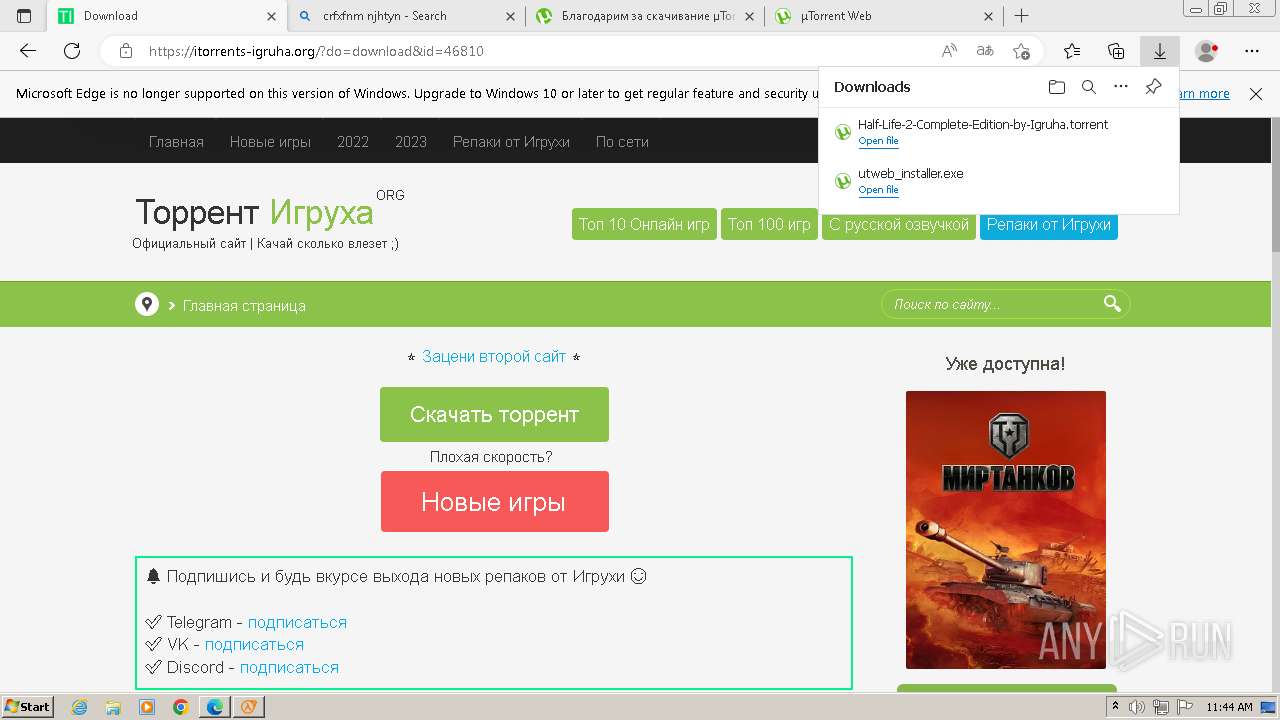
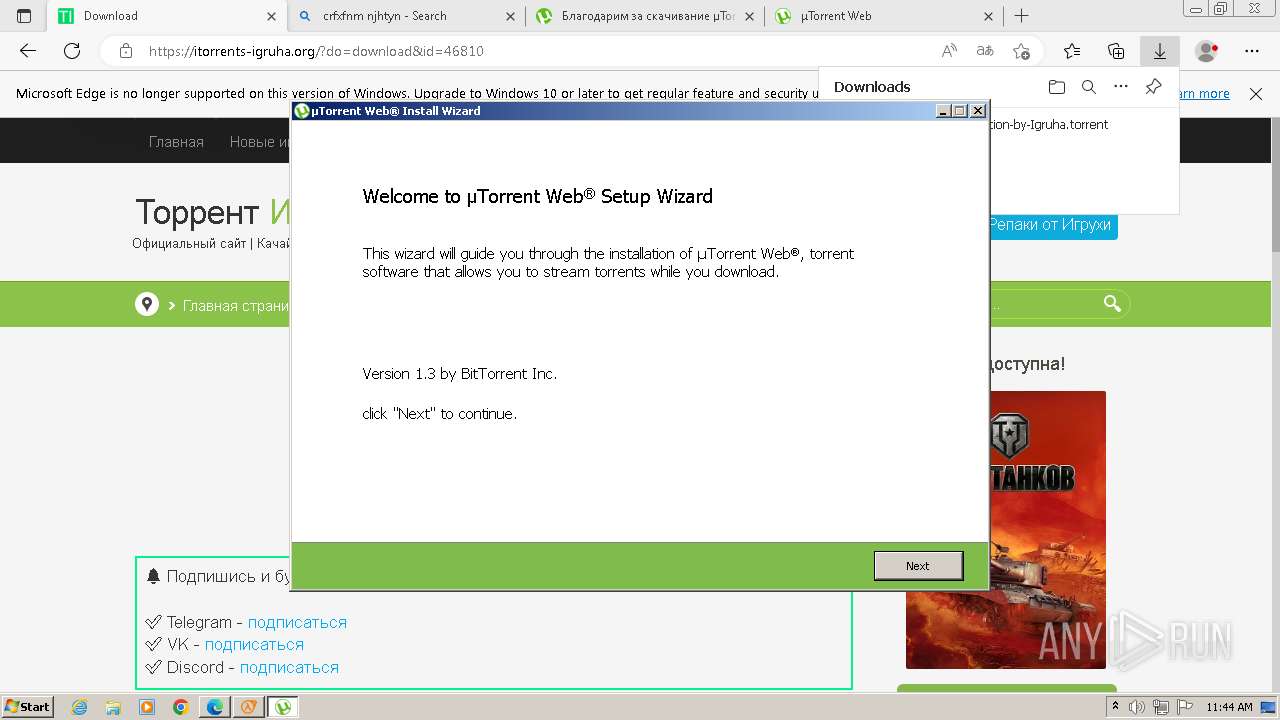
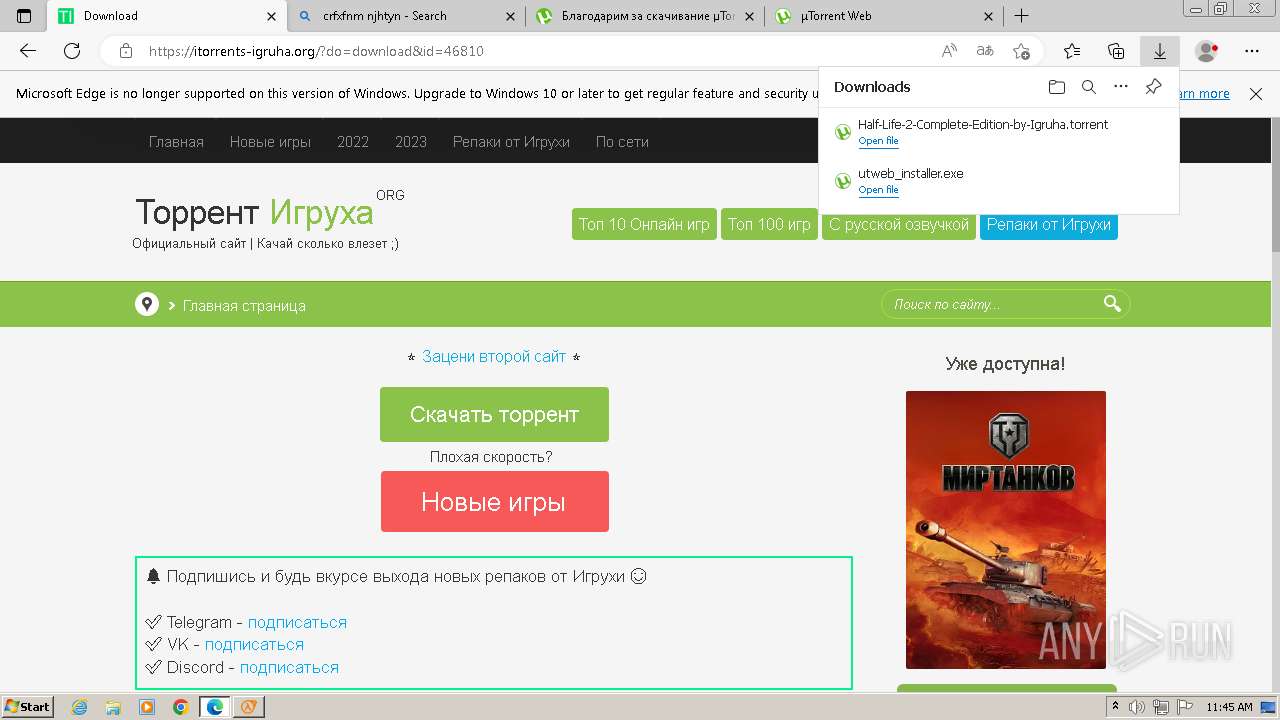
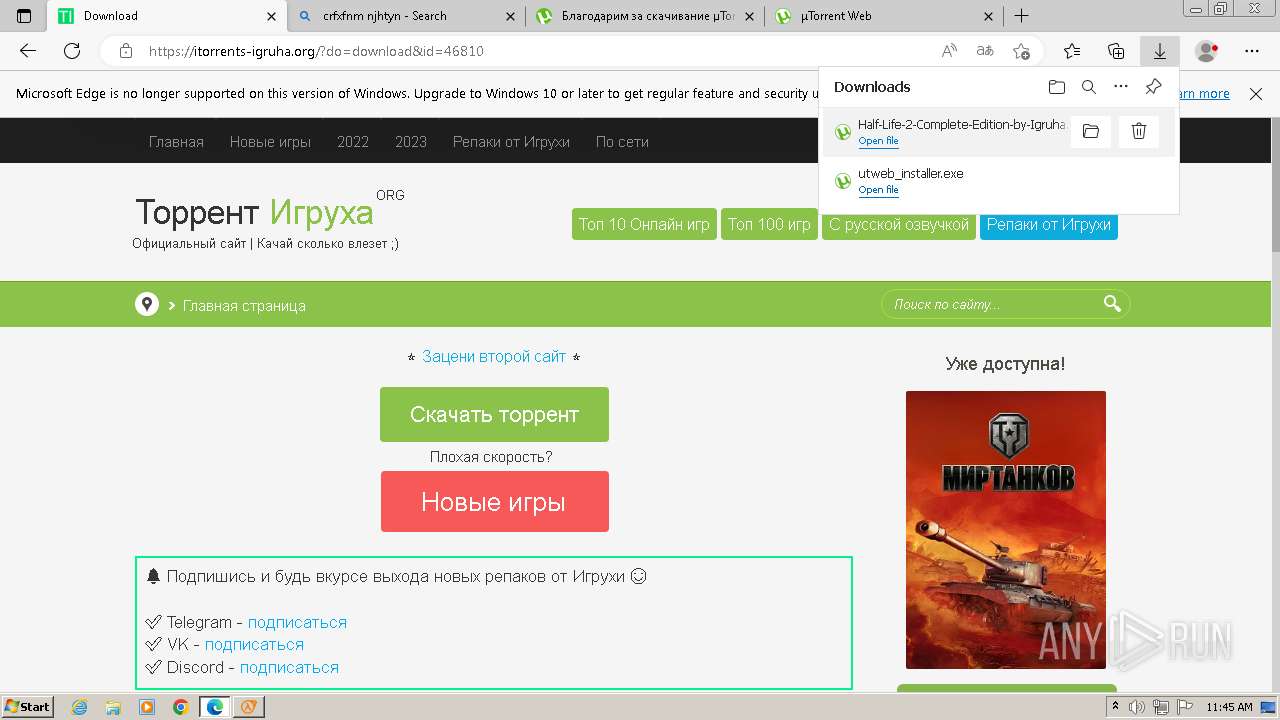
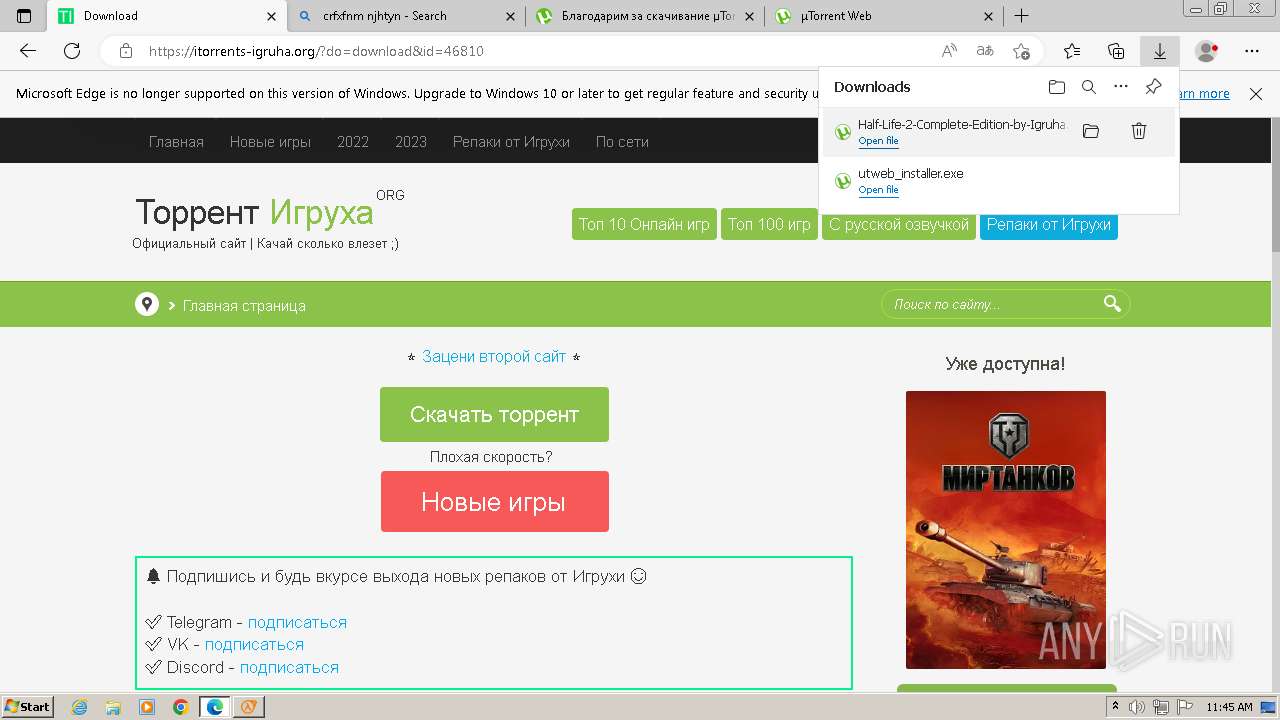
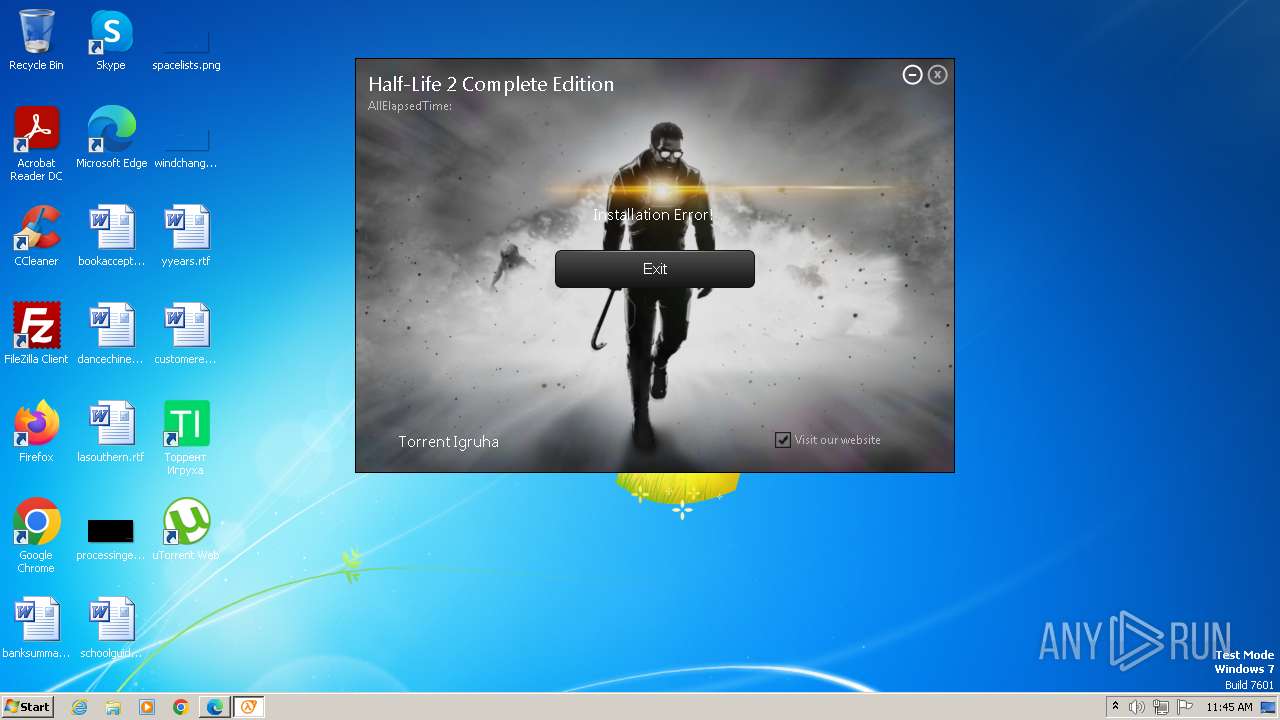
| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/d403feac-4a19-420f-bcf0-e4c89d3905b9 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2023, 11:41:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EA58C12B25C48FEA01EEE390ED06C84A |
| SHA1: | DF28A8077121C74EFE33A0617F8CC030C654F3C6 |
| SHA256: | FA757528FDF828A3C372A2C12A4BACA687CED0D1F7E4C5F7A69183ADDC575A46 |
| SSDEEP: | 98304:QJyEM7ncqFIG7xn8Oy2uyCNxIHCrrHk+4kq65I+G6fs8IN1DGfma5E7vVpKYFNMV:VYv3eg |
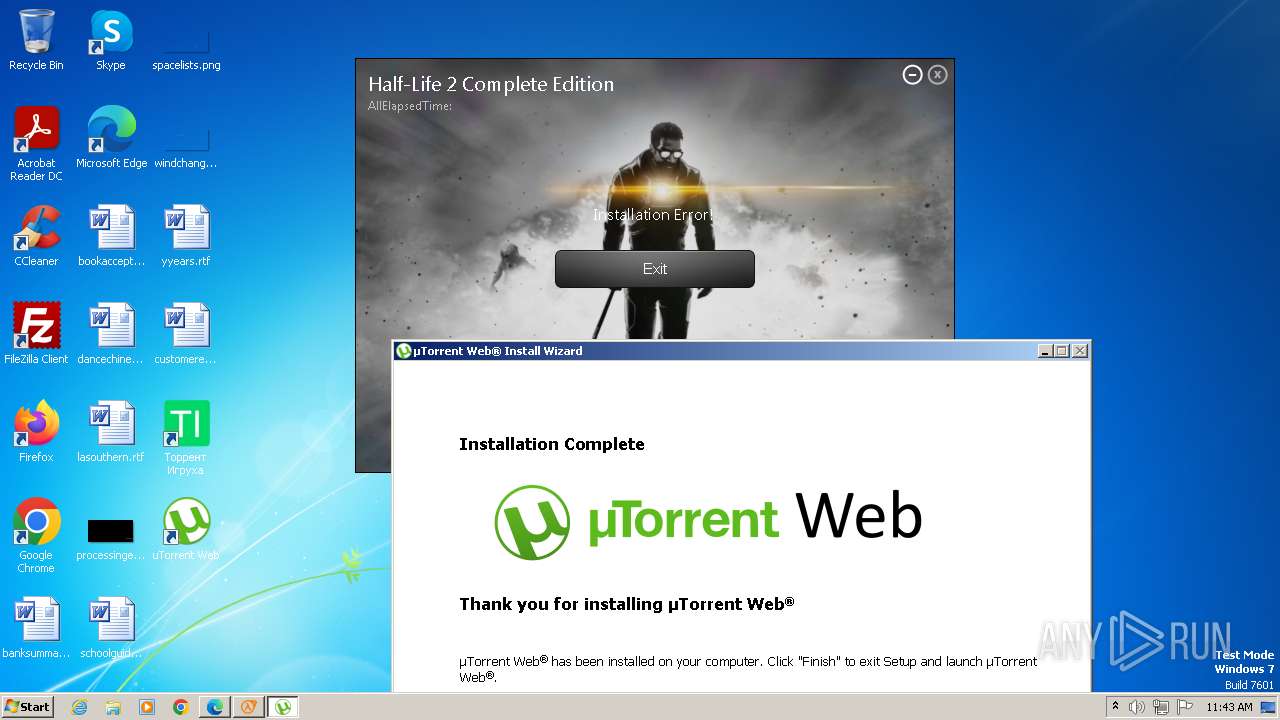
MALICIOUS
Drops the executable file immediately after the start
- setup.exe (PID: 2720)
- setup.tmp (PID: 3352)
- unins000.exe (PID: 924)
- _iu14D2N.tmp (PID: 3068)
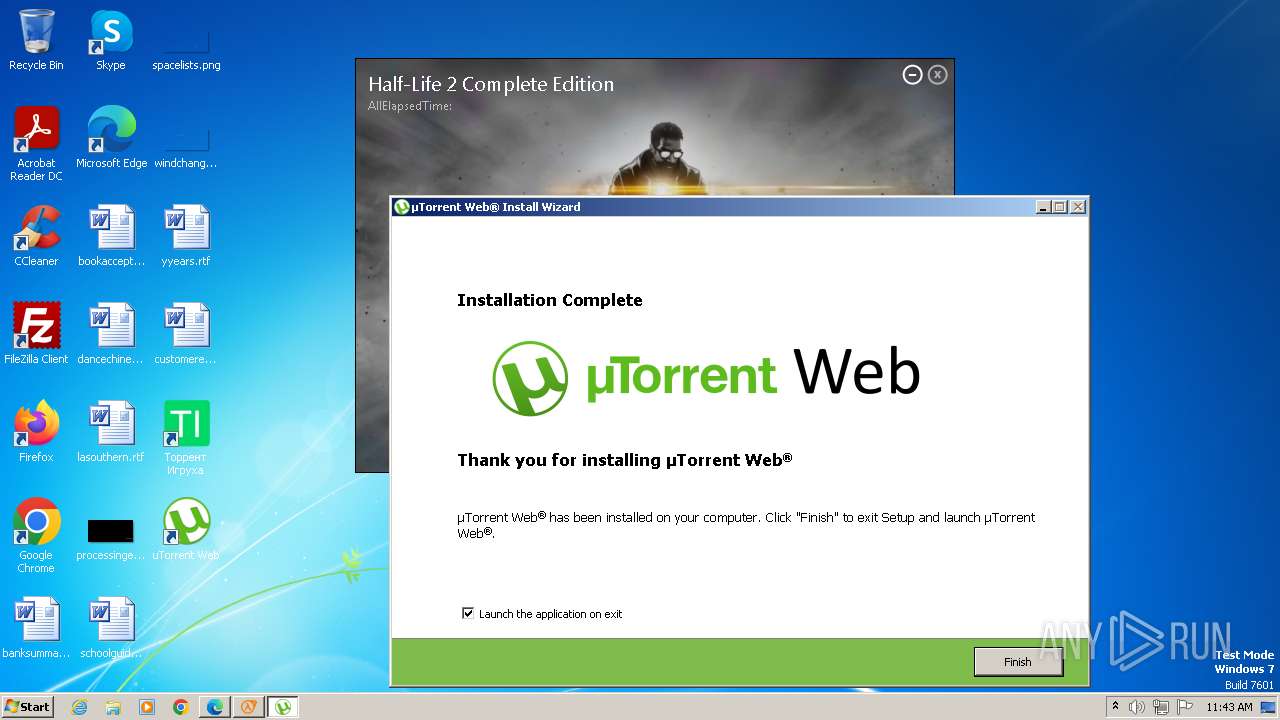
- utweb_installer.exe (PID: 1036)
- utweb_installer.exe (PID: 3948)
- utweb_installer.tmp (PID: 3700)
- utweb_installer.exe (PID: 3364)
- utweb.exe (PID: 2472)
- utweb_installer.exe (PID: 2080)
- utweb_installer.exe (PID: 2156)
- utweb_installer.tmp (PID: 3096)
SUSPICIOUS
Process drops legitimate windows executable
- setup.tmp (PID: 3352)
- _iu14D2N.tmp (PID: 3068)
- utweb_installer.exe (PID: 3364)
Reads the Windows owner or organization settings
- setup.tmp (PID: 3352)
- _iu14D2N.tmp (PID: 3068)
- utweb_installer.tmp (PID: 3700)
- utweb_installer.tmp (PID: 3096)
Starts application with an unusual extension
- unins000.exe (PID: 924)
Starts itself from another location
- unins000.exe (PID: 924)
The process creates files with name similar to system file names
- utweb_installer.exe (PID: 3364)
Malware-specific behavior (creating "System.dll" in Temp)
- utweb_installer.exe (PID: 3364)
Reads settings of System Certificates
- utweb_installer.tmp (PID: 3700)
- utweb.exe (PID: 2472)
- helper.exe (PID: 272)
- utweb_installer.tmp (PID: 3096)
Reads the Internet Settings
- utweb_installer.tmp (PID: 3700)
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
- utweb_installer.exe (PID: 3364)
- utweb_installer.tmp (PID: 3096)
- setup.tmp (PID: 3352)
Checks Windows Trust Settings
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
Reads security settings of Internet Explorer
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
Connects to unusual port
- utweb.exe (PID: 2472)
INFO
Checks supported languages
- setup.exe (PID: 2720)
- setup.tmp (PID: 3352)
- unins000.exe (PID: 924)
- _iu14D2N.tmp (PID: 3068)
- wmpnscfg.exe (PID: 2448)
- wmpnscfg.exe (PID: 3572)
- utweb_installer.exe (PID: 1036)
- utweb_installer.tmp (PID: 752)
- utweb_installer.exe (PID: 3948)
- utweb_installer.tmp (PID: 3700)
- utweb_installer.exe (PID: 3364)
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
- helper.exe (PID: 272)
- utweb.exe (PID: 3916)
- utweb.exe (PID: 2092)
- utweb.exe (PID: 2924)
- utweb.exe (PID: 2080)
- utweb.exe (PID: 3628)
- utweb.exe (PID: 2780)
- utweb.exe (PID: 2092)
- utweb.exe (PID: 3448)
- utweb.exe (PID: 3184)
- utweb.exe (PID: 1376)
- utweb.exe (PID: 1868)
- utweb.exe (PID: 732)
- utweb.exe (PID: 3628)
- utweb.exe (PID: 1824)
- utweb_installer.exe (PID: 2156)
- utweb_installer.tmp (PID: 3500)
- utweb.exe (PID: 3992)
- utweb_installer.exe (PID: 2080)
- utweb.exe (PID: 3860)
- utweb.exe (PID: 2448)
- utweb_installer.tmp (PID: 3096)
- utweb.exe (PID: 3228)
- utweb.exe (PID: 3336)
- utweb.exe (PID: 2436)
- utweb.exe (PID: 1856)
- utweb.exe (PID: 3964)
- utweb.exe (PID: 2096)
- utweb.exe (PID: 1948)
- utweb.exe (PID: 2992)
- utweb.exe (PID: 3280)
Create files in a temporary directory
- setup.exe (PID: 2720)
- setup.tmp (PID: 3352)
- unins000.exe (PID: 924)
- _iu14D2N.tmp (PID: 3068)
- utweb_installer.exe (PID: 1036)
- utweb_installer.exe (PID: 3948)
- utweb_installer.tmp (PID: 3700)
- utweb_installer.exe (PID: 3364)
- utweb_installer.exe (PID: 2080)
- utweb_installer.exe (PID: 2156)
- utweb_installer.tmp (PID: 3096)
Reads the computer name
- setup.tmp (PID: 3352)
- wmpnscfg.exe (PID: 2448)
- wmpnscfg.exe (PID: 3572)
- utweb_installer.tmp (PID: 752)
- utweb_installer.exe (PID: 3364)
- utweb_installer.tmp (PID: 3700)
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
- helper.exe (PID: 272)
- utweb_installer.tmp (PID: 3500)
- utweb_installer.tmp (PID: 3096)
Creates files in the program directory
- setup.tmp (PID: 3352)
- saBSI.exe (PID: 2436)
Manual execution by a user
- msedge.exe (PID: 2412)
- wmpnscfg.exe (PID: 3572)
- wmpnscfg.exe (PID: 2448)
- utweb.exe (PID: 2092)
- utweb.exe (PID: 2080)
- utweb.exe (PID: 3184)
Application launched itself
- msedge.exe (PID: 2412)
- msedge.exe (PID: 2156)
- msedge.exe (PID: 528)
Drops the executable file immediately after the start
- msedge.exe (PID: 2304)
- msedge.exe (PID: 2412)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2448)
- wmpnscfg.exe (PID: 3572)
- utweb_installer.tmp (PID: 3700)
- utweb_installer.exe (PID: 3364)
- saBSI.exe (PID: 2436)
- utweb.exe (PID: 2472)
- utweb_installer.tmp (PID: 3096)
The process uses the downloaded file
- msedge.exe (PID: 3696)
- msedge.exe (PID: 2412)
- msedge.exe (PID: 2156)
- msedge.exe (PID: 3416)
Creates files or folders in the user directory
- utweb_installer.exe (PID: 3364)
- utweb.exe (PID: 2472)
- helper.exe (PID: 272)
Checks proxy server information
- utweb_installer.exe (PID: 3364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:10:02 07:04:04+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 158208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.5 |
| ProductVersionNumber: | 1.0.0.5 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
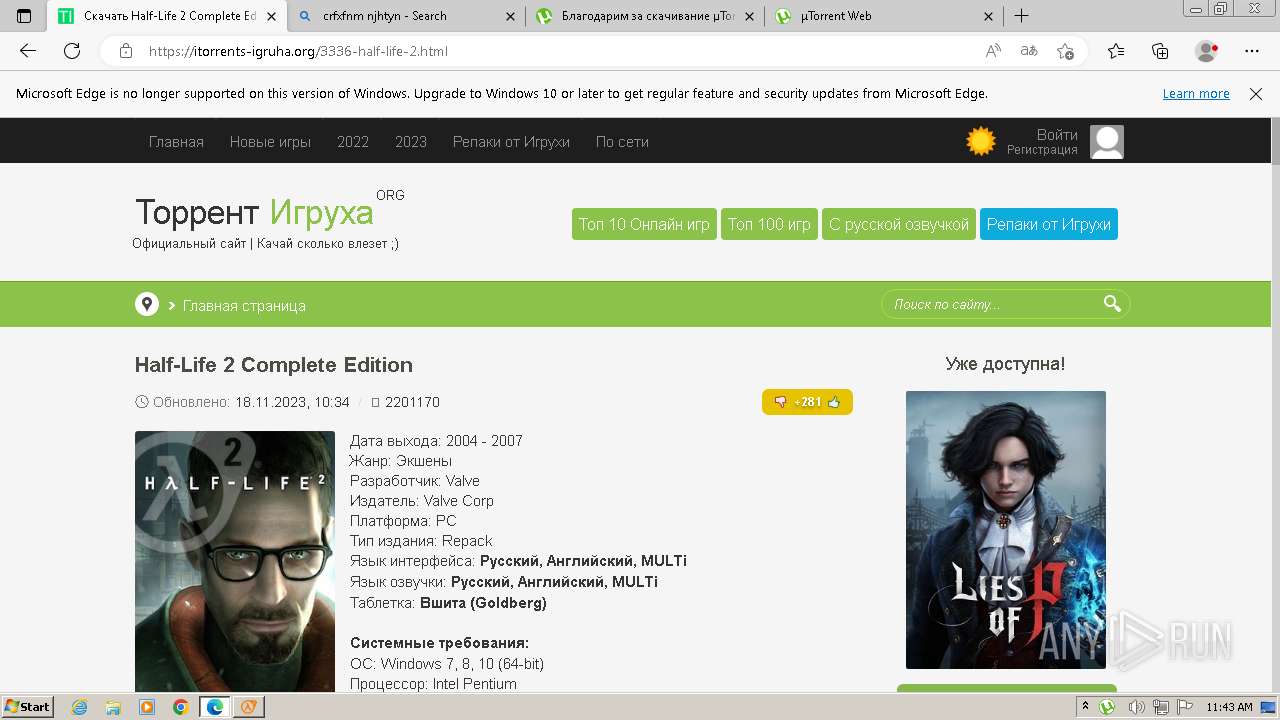
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | torrent-igruha.org |
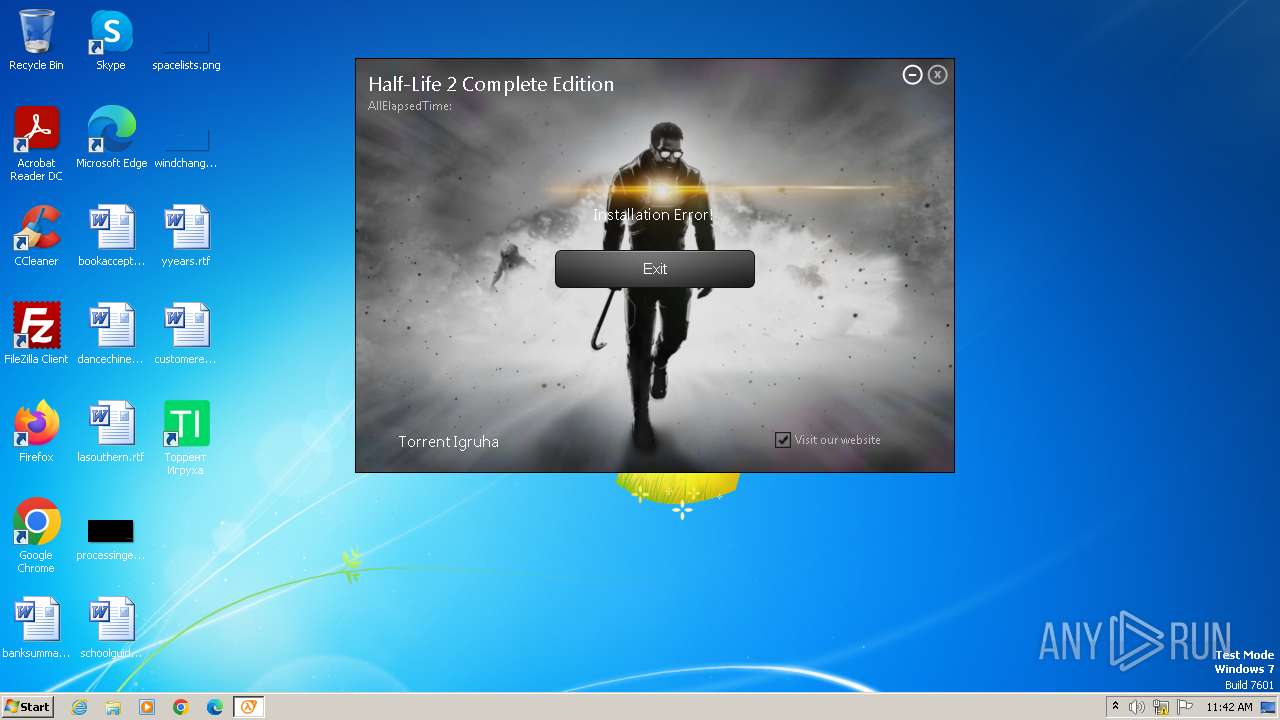
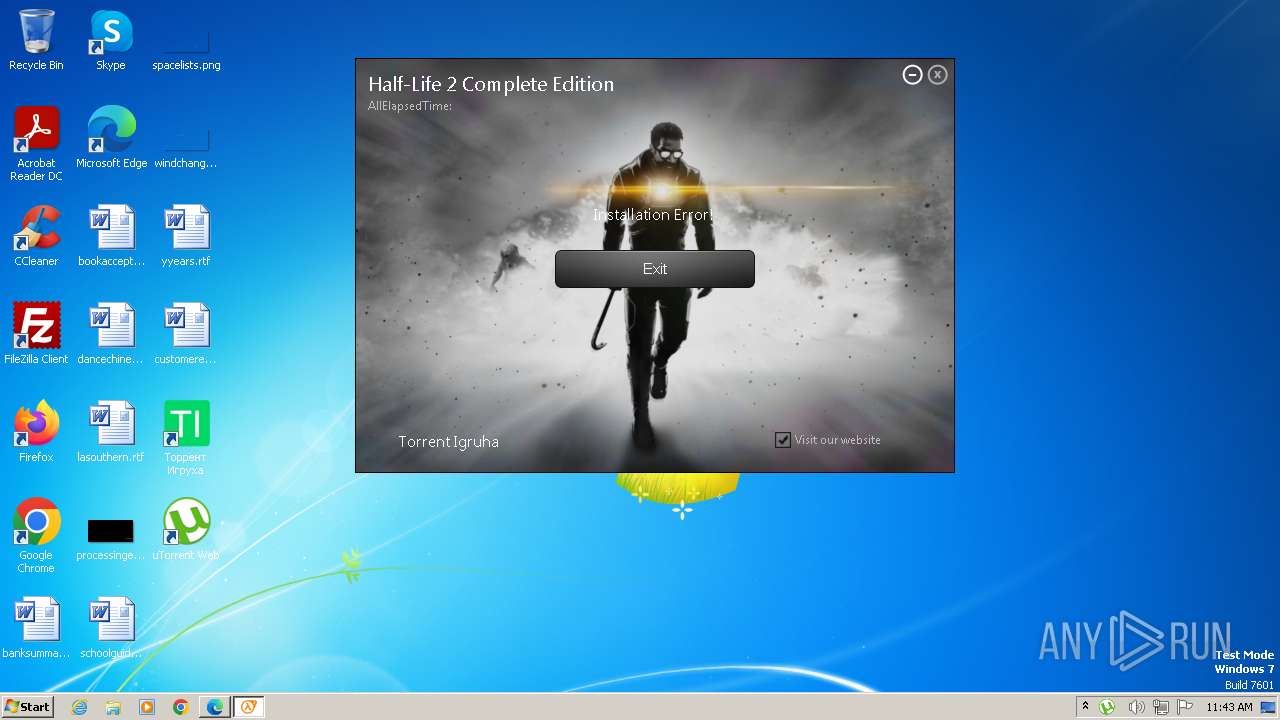
| FileDescription: | Half-Life 2 Complete Edition Setup |
| FileVersion: | 1.0.0.5 |
| LegalCopyright: | |
| ProductName: | Half-Life 2 Complete Edition |
| ProductVersion: | 1.0.0.5 |
Total processes
155
Monitored processes
102
Malicious processes
13
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6a4af598,0x6a4af5a8,0x6a4af5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 148 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=5036 --field-trial-handle=1320,i,8027975798276810197,5424669894995782367,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 240 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1648 --field-trial-handle=1320,i,8027975798276810197,5424669894995782367,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 272 | helper/helper.exe 49440 -- ut_web/1.4.0.5714 hval/745a97b0be8aee11a82612a9866c77de | C:\Users\admin\AppData\Roaming\uTorrent Web\helper\helper.exe | utweb.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Helper Exit code: 0 Version: 2.1.6.2679 Modules
| |||||||||||||||
| 284 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4164 --field-trial-handle=1320,i,8027975798276810197,5424669894995782367,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 528 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://ti-url.com/half-life-2-complete-edition | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 732 | "C:\Users\admin\AppData\Roaming\uTorrent Web\utweb.exe" "C:\Users\admin\Downloads\Half-Life-2-Complete-Edition-by-Igruha.torrent" /SHELLASSOC | C:\Users\admin\AppData\Roaming\uTorrent Web\utweb.exe | — | msedge.exe | |||||||||||
User: admin Company: Rainberry Inc. Integrity Level: MEDIUM Description: µTorrent Web Exit code: 0 Version: 1.4.0.5714 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\is-FI5UU.tmp\utweb_installer.tmp" /SL5="$B0184,902222,823296,C:\Users\admin\Downloads\utweb_installer.exe" | C:\Users\admin\AppData\Local\Temp\is-FI5UU.tmp\utweb_installer.tmp | — | utweb_installer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Half-Life 2 Complete Edition\unins000.exe" /VERYSILENT | C:\Program Files\Half-Life 2 Complete Edition\unins000.exe | — | setup.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=6272 --field-trial-handle=1320,i,8027975798276810197,5424669894995782367,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
30 562
Read events
30 348
Write events
186
Delete events
28
Modification events
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Half-Life 2 Complete Edition_is1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Program Files\Half-Life 2 Complete Edition\Half-Life 2 Episode Two.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Program Files\Half-Life 2 Complete Edition\Half-Life 2 Episode One.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Program Files\Half-Life 2 Complete Edition\Half-Life 2 Lost Coast.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Program Files\Half-Life 2 Complete Edition\Half-Life Source.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete value | Name: | C:\Program Files\Half-Life 2 Complete Edition\hl2.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (3068) _iu14D2N.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2412) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2412) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2412) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
Executable files
100
Suspicious files
1 570
Text files
207
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\cls.ini | — | |
MD5:— | SHA256:— | |||
| 2720 | setup.exe | C:\Users\admin\AppData\Local\Temp\is-9URC8.tmp\setup.tmp | executable | |
MD5:A3DA0CC6F148DD70E8E8443E5C1BCF00 | SHA256:3991D7614A9EBFBE4FDF8A94F6B73AC0EEF0BA5FFA3F5071CFDEE4728BD07271 | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\b2p.dll | executable | |
MD5:AB35386487B343E3E82DBD2671FF9DAB | SHA256:C3729545522FCFF70DB61046C0EFD962DF047D40E3B5CCD2272866540FC872B2 | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\CallbackCtrl.dll | executable | |
MD5:F07E819BA2E46A897CFABF816D7557B2 | SHA256:68F42A7823ED7EE88A5C59020AC52D4BBCADF1036611E96E470D986C8FAA172D | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\Russian.ini | text | |
MD5:C2F6F1038DE8369B2E31067EA4D48536 | SHA256:1CFA41921DCE01991640DB414D4955B1A6DC6D6FA4F4333CA7552E2E8B81391E | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\WinTB.dll | executable | |
MD5:A2EEE508E6A51C6335650532E05AC550 | SHA256:75FB2984E1B06F4278FB7B3C77E9FEC84E02A3B4BF82D35120F8CBE7BDBC76BF | |||
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\arc.ini | text | |
MD5:377AED8F1AD08D80DCBD1A631A128EEB | SHA256:0AB838CA04CDF7052CA730F8375B46A8C1785FA8F9383F04A7024C40C4CA8DD6 | |||
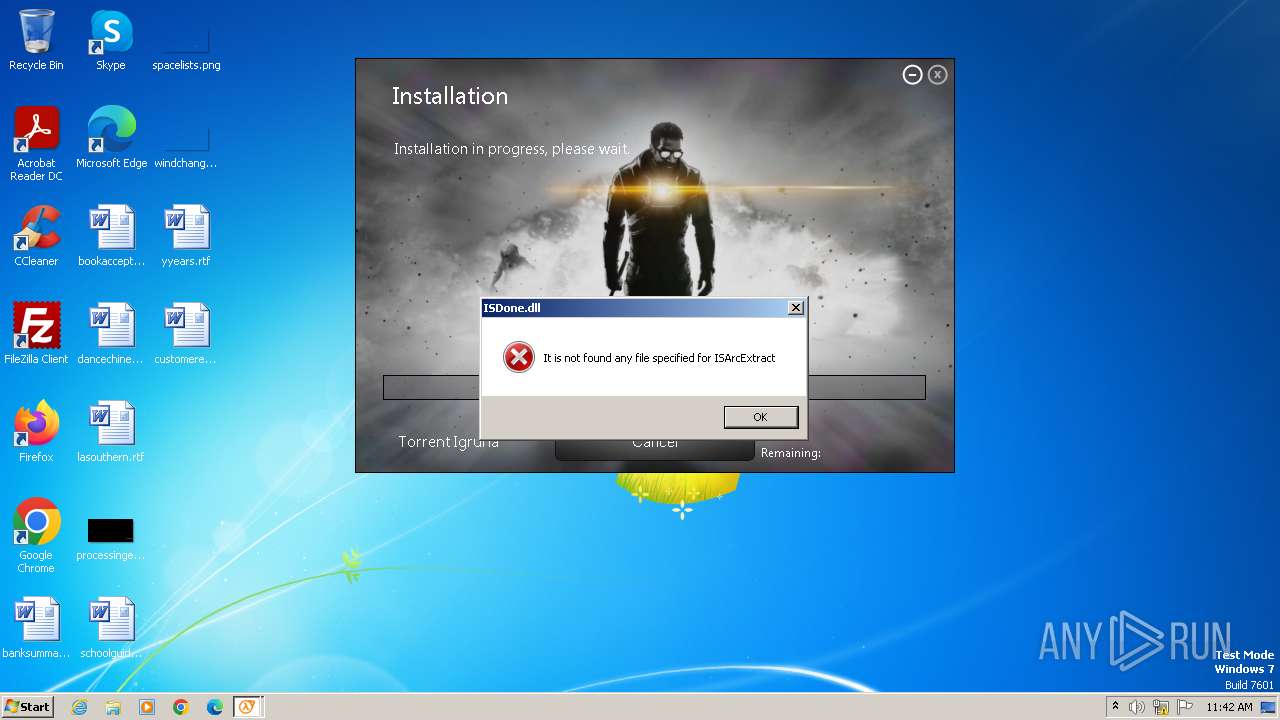
| 3352 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-2SJDB.tmp\ISDone.dll | executable | |
MD5:4FEAFA8B5E8CDB349125C8AF0AC43974 | SHA256:BB8A0245DCC5C10A1C7181BAD509B65959855009A8105863EF14F2BB5B38AC71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
2 709
DNS requests
298
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
272 | helper.exe | POST | 200 | 52.0.78.86:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
272 | helper.exe | POST | 200 | 52.0.78.86:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
272 | helper.exe | POST | 200 | 52.0.78.86:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2472 | utweb.exe | POST | 200 | 35.171.94.184:80 | http://i-4103.b-5714.utw.bench.utorrent.com/e?i=4103 | unknown | binary | 21 b | unknown |
2472 | utweb.exe | POST | 200 | 52.0.78.86:80 | http://i-4103.b-5714.utw.bench.utorrent.com/e?i=4103 | unknown | binary | 21 b | unknown |
272 | helper.exe | POST | 200 | 52.0.78.86:80 | http://i-5600.b-2679.helper.bench.utorrent.com/e.php?i=5600 | unknown | binary | 21 b | unknown |
2472 | utweb.exe | POST | 200 | 52.200.190.154:80 | http://i-4103.b-5714.utw.bench.utorrent.com/e?i=4103 | unknown | binary | 21 b | unknown |
2472 | utweb.exe | POST | 200 | 52.0.78.86:80 | http://i-4103.b-5714.utw.bench.utorrent.com/e?i=4103 | unknown | binary | 21 b | unknown |
3364 | utweb_installer.exe | POST | 200 | 50.19.196.255:80 | http://i-4101.b-5714.utweb.bench.utorrent.com/e?i=4101 | unknown | binary | 21 b | unknown |
2472 | utweb.exe | GET | — | 178.79.242.16:80 | http://btinstall-artifacts.bittorrent.com/helper_ui/helper_web_ui.btinstall | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2412 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2304 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2304 | msedge.exe | 172.67.71.140:443 | itorrents-igruha.org | — | — | unknown |
2304 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2304 | msedge.exe | 104.26.12.145:443 | ti-url.com | CLOUDFLARENET | US | unknown |
2304 | msedge.exe | 20.105.95.163:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
ti-url.com |
| unknown |
edge.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
itorrents-igruha.org |
| unknown |
data-edge.smartscreen.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
arc.msn.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3364 | utweb_installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3364 | utweb_installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2472 | utweb.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
2472 | utweb.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
2472 | utweb.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2304 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
2304 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
2472 | utweb.exe | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |
2472 | utweb.exe | Potential Corporate Privacy Violation | GPL P2P BitTorrent transfer |
2472 | utweb.exe | Potential Corporate Privacy Violation | GPL P2P BitTorrent transfer |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-NEBDF.tmp\component0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|