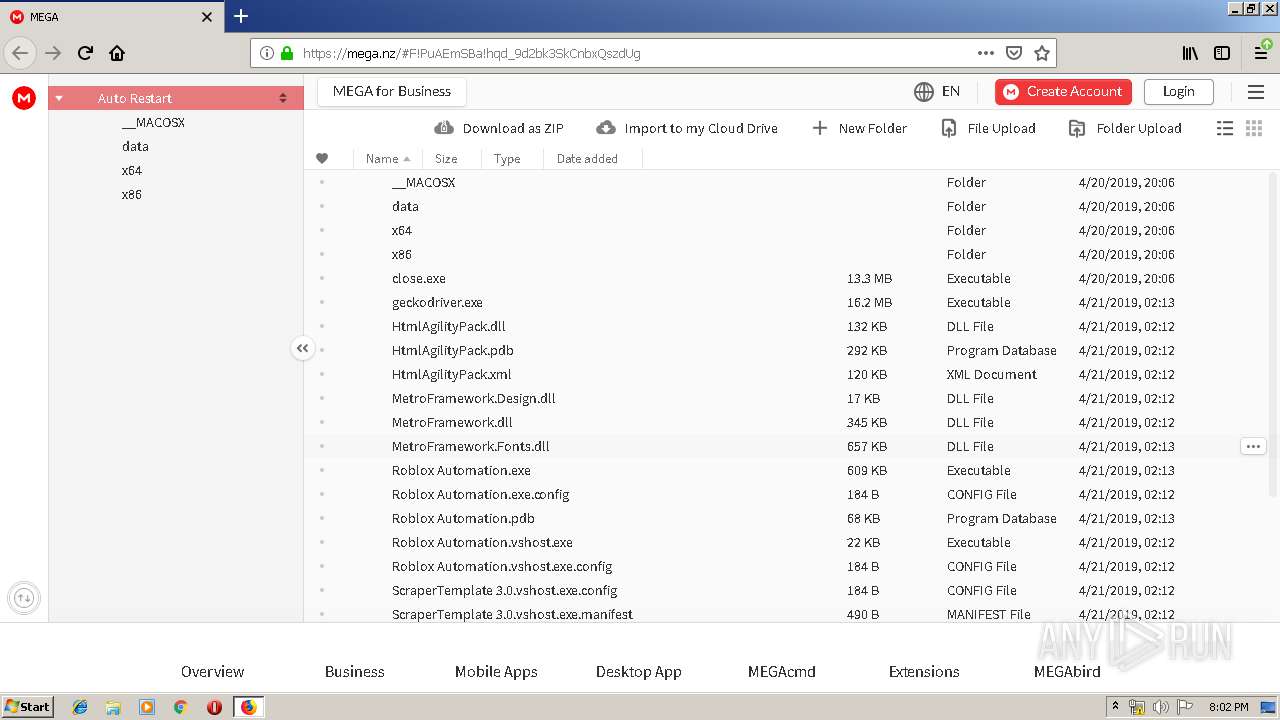
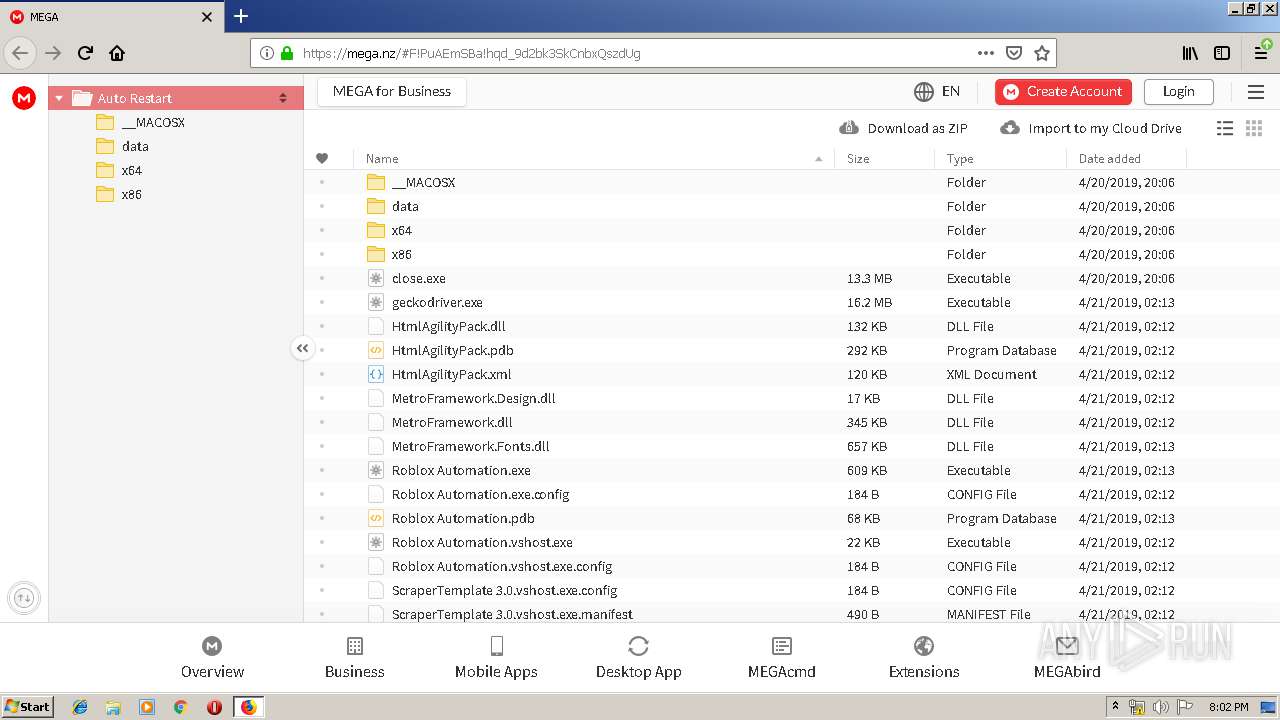
| URL: | https://mega.nz/#F!PuAEmSBa!hqd_9d2bk3SkCnbxQszdUg |
| Full analysis: | https://app.any.run/tasks/bd7d9dd6-ac5e-4710-952f-191aa72a2f17 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2019, 19:00:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1BE99757F6D3E71BA4F71020C1A1A886 |
| SHA1: | 2FE1CC231BF9124382B721CEA7B79B71DCC9F732 |
| SHA256: | FA7293FB946FEA9A51C5C788DCC52A6DF433AE454A59AD960BCAFDF541DF311E |
| SSDEEP: | 3:N8X/iG4vkcMcBXHo/BwC:29bcDXMB3 |
MALICIOUS
Application was dropped or rewritten from another process
- Roblox Automation.exe (PID: 3632)
- close.exe (PID: 3496)
Loads dropped or rewritten executable
- Roblox Automation.exe (PID: 3632)
- SearchProtocolHost.exe (PID: 4012)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 3328)
Executable content was dropped or overwritten
- firefox.exe (PID: 3328)
- WinRAR.exe (PID: 2452)
Creates files in the user directory
- close.exe (PID: 3496)
Reads Environment values
- close.exe (PID: 3496)
INFO
Application launched itself
- firefox.exe (PID: 3328)
Reads CPU info
- firefox.exe (PID: 3328)
Reads Internet Cache Settings
- firefox.exe (PID: 3328)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3328)
Manual execution by user
- close.exe (PID: 3496)
- Roblox Automation.exe (PID: 3632)
Reads settings of System Certificates
- firefox.exe (PID: 3328)
Creates files in the user directory
- firefox.exe (PID: 3328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1652 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3328.20.558155923\702816013" -childID 3 -isForBrowser -prefsHandle 3376 -prefMapHandle 3388 -prefsLen 5824 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3328 "\\.\pipe\gecko-crash-server-pipe.3328" 3400 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3328.13.2065260777\1516410196" -childID 2 -isForBrowser -prefsHandle 2548 -prefMapHandle 2552 -prefsLen 216 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3328 "\\.\pipe\gecko-crash-server-pipe.3328" 2580 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3328.6.1995306759\233697120" -childID 1 -isForBrowser -prefsHandle 1292 -prefMapHandle 1584 -prefsLen 1 -prefMapSize 180950 -schedulerPrefs 0001,2 -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3328 "\\.\pipe\gecko-crash-server-pipe.3328" 1704 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Auto Restart.zip" | C:\Program Files\WinRAR\WinRAR.exe | firefox.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://mega.nz/#F!PuAEmSBa!hqd_9d2bk3SkCnbxQszdUg | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 3424 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3328.0.1491389032\1622747598" -parentBuildID 20190225143501 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - "C:\Users\admin\AppData\LocalLow\Mozilla\Temp-{ce348e4c-7d33-445e-89f9-60108c51bcaf}" 3328 "\\.\pipe\gecko-crash-server-pipe.3328" 1136 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 3496 | "C:\Users\admin\Desktop\Auto Restart\close.exe" | C:\Users\admin\Desktop\Auto Restart\close.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
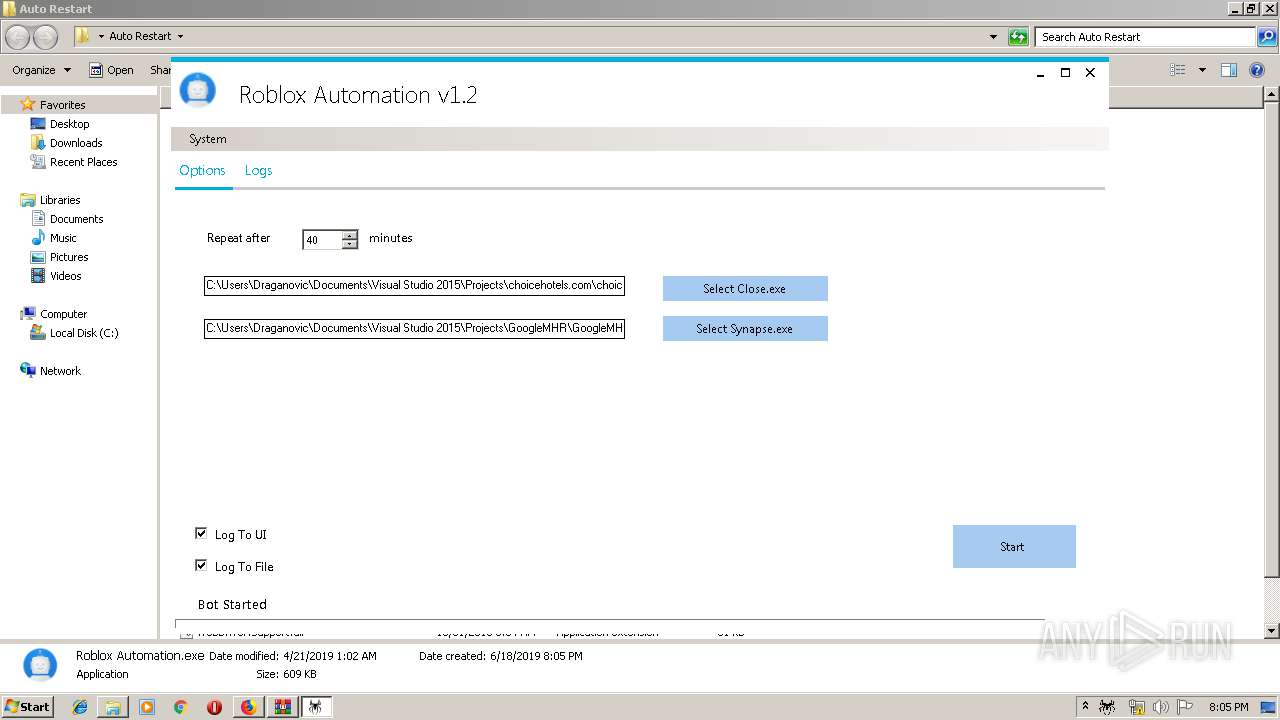
| 3632 | "C:\Users\admin\Desktop\Auto Restart\Roblox Automation.exe" | C:\Users\admin\Desktop\Auto Restart\Roblox Automation.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Roblox_Automation Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4012 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 978
Read events
1 893
Write events
84
Delete events
1
Modification events
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3328) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Auto Restart.zip | |||
Executable files
14
Suspicious files
193
Text files
66
Unknown types
102
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\trash23050 | — | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flashsubdoc-digest256.pset | cdxl | |
MD5:076933FF9904D1110D896E2C525E39E5 | SHA256:4CBBD8CA5215B8D161AEC181A74B694F4E24B001D5B081DC0030ED797A8973E0 | |||
| 3328 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.sbstore | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
119
DNS requests
468
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3328 | firefox.exe | GET | — | 104.86.111.161:80 | http://detectportal.firefox.com/success.txt | NL | — | — | whitelisted |
3328 | firefox.exe | GET | — | 104.86.111.161:80 | http://detectportal.firefox.com/success.txt | NL | — | — | whitelisted |
3328 | firefox.exe | GET | — | 104.86.111.161:80 | http://detectportal.firefox.com/success.txt | NL | — | — | whitelisted |
3328 | firefox.exe | GET | — | 104.86.111.161:80 | http://detectportal.firefox.com/success.txt | NL | — | — | whitelisted |
3328 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3328 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/ | US | der | 471 b | whitelisted |
3328 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/ | US | der | 471 b | whitelisted |
3328 | firefox.exe | GET | — | 104.86.111.161:80 | http://detectportal.firefox.com/success.txt | NL | — | — | whitelisted |
3328 | firefox.exe | POST | 200 | 216.58.213.163:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 471 b | whitelisted |
3328 | firefox.exe | POST | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/ | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3328 | firefox.exe | 35.244.181.201:443 | aus5.mozilla.org | — | US | suspicious |
3328 | firefox.exe | 104.86.111.161:80 | detectportal.firefox.com | Akamai International B.V. | NL | whitelisted |
3328 | firefox.exe | 92.122.122.139:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
3328 | firefox.exe | 34.215.70.240:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3328 | firefox.exe | 34.210.151.118:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3328 | firefox.exe | 216.58.215.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3328 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3328 | firefox.exe | 89.44.169.134:443 | eu.static.mega.co.nz | Datacenter Luxembourg S.A. | LU | suspicious |
3328 | firefox.exe | 52.85.255.23:443 | content-signature.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
3328 | firefox.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mega.nz |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
aus5.mozilla.org |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3496 | close.exe | Misc activity | APP [PTsecurity] SmartAssembly |
3496 | close.exe | Misc activity | APP [PTsecurity] SmartAssembly |
3496 | close.exe | Misc activity | APP [PTsecurity] SmartAssembly |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
Roblox Automation.exe | Native library pre-loader is trying to load native SQLite library "C:\Users\admin\Desktop\Auto Restart\x86\SQLite.Interop.dll"...
|