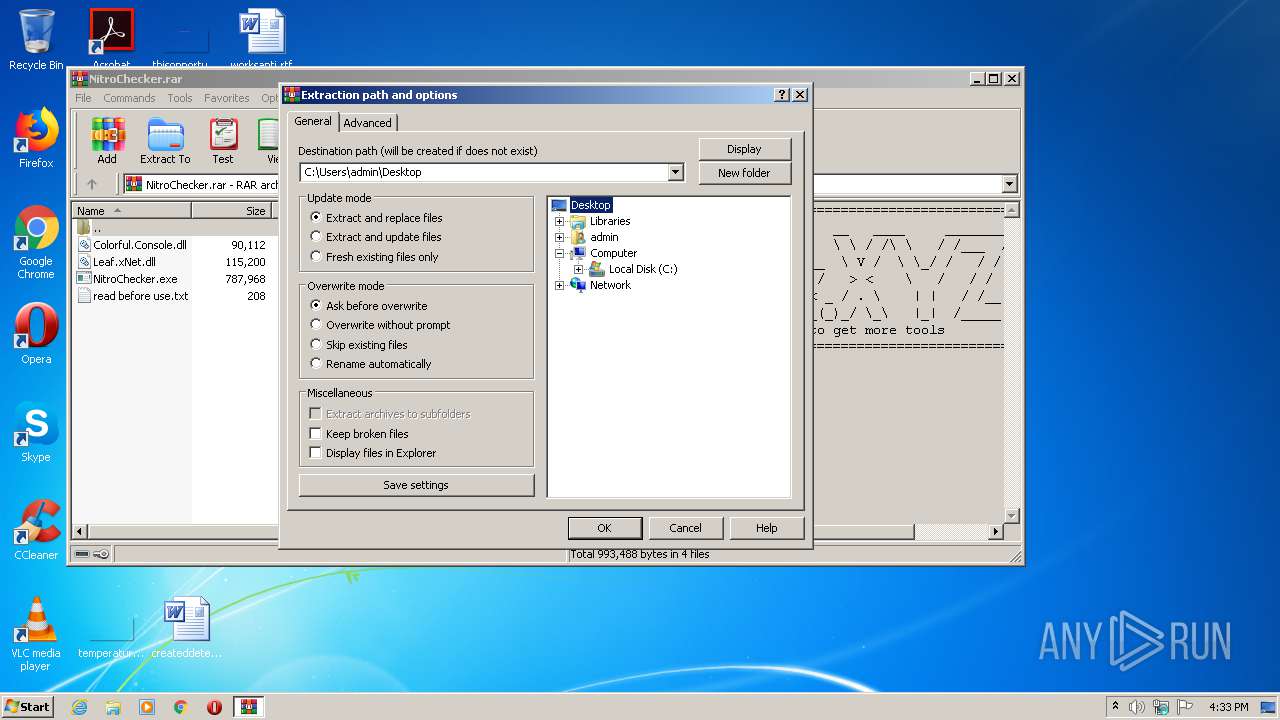
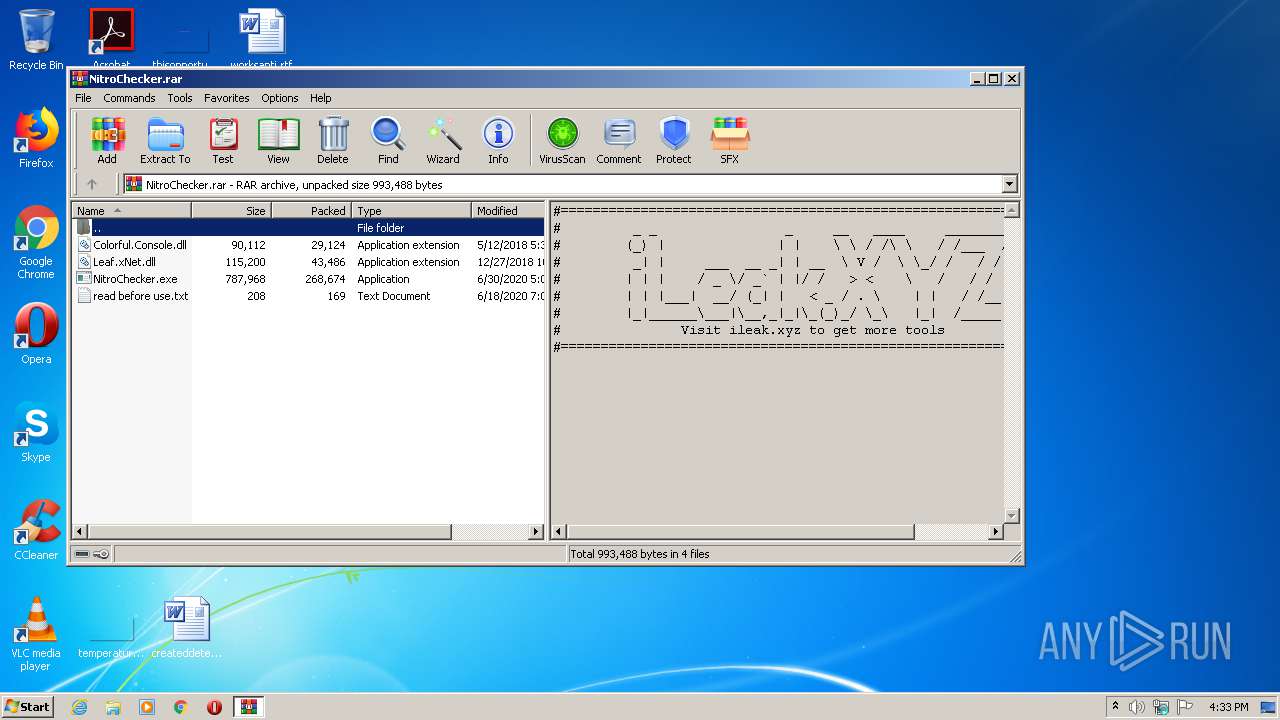
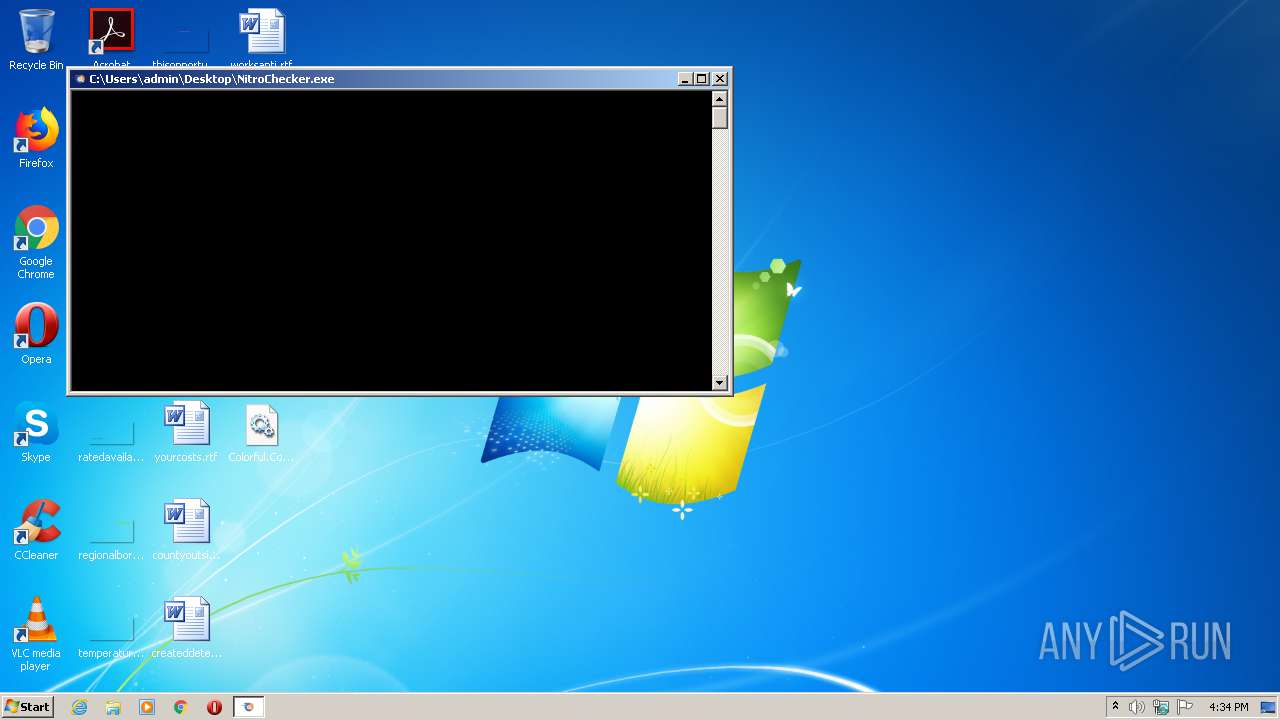
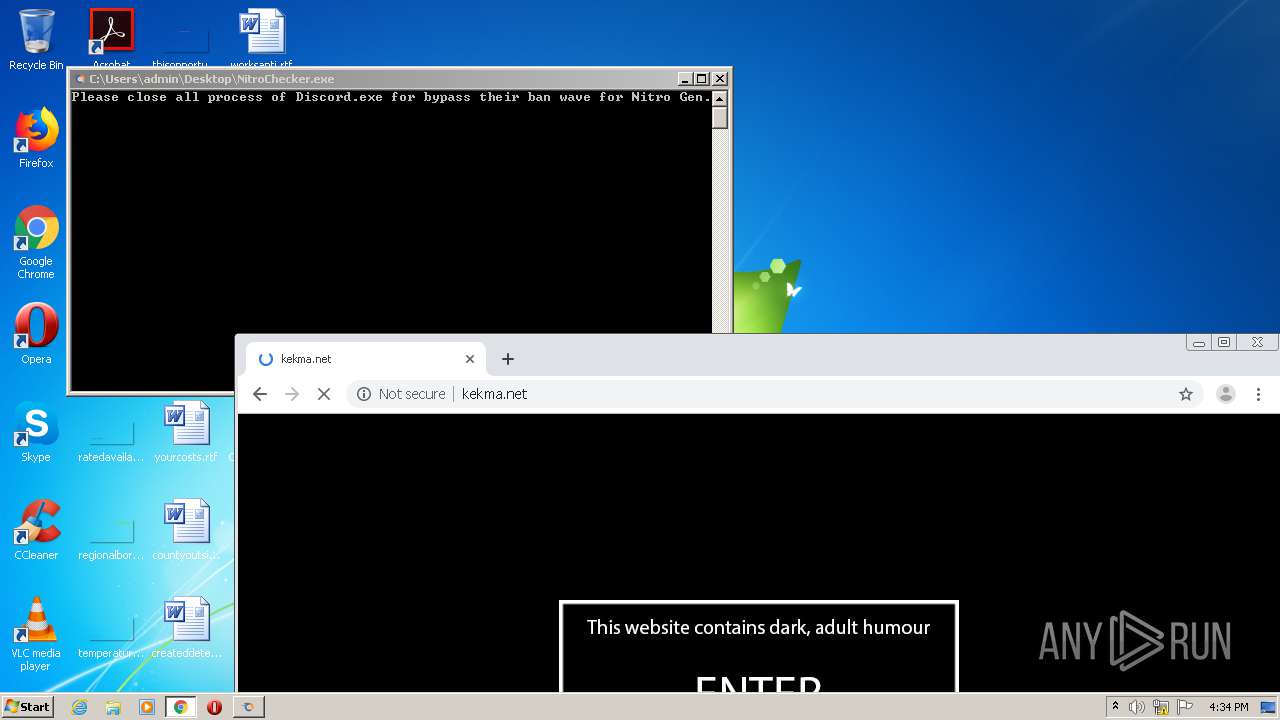
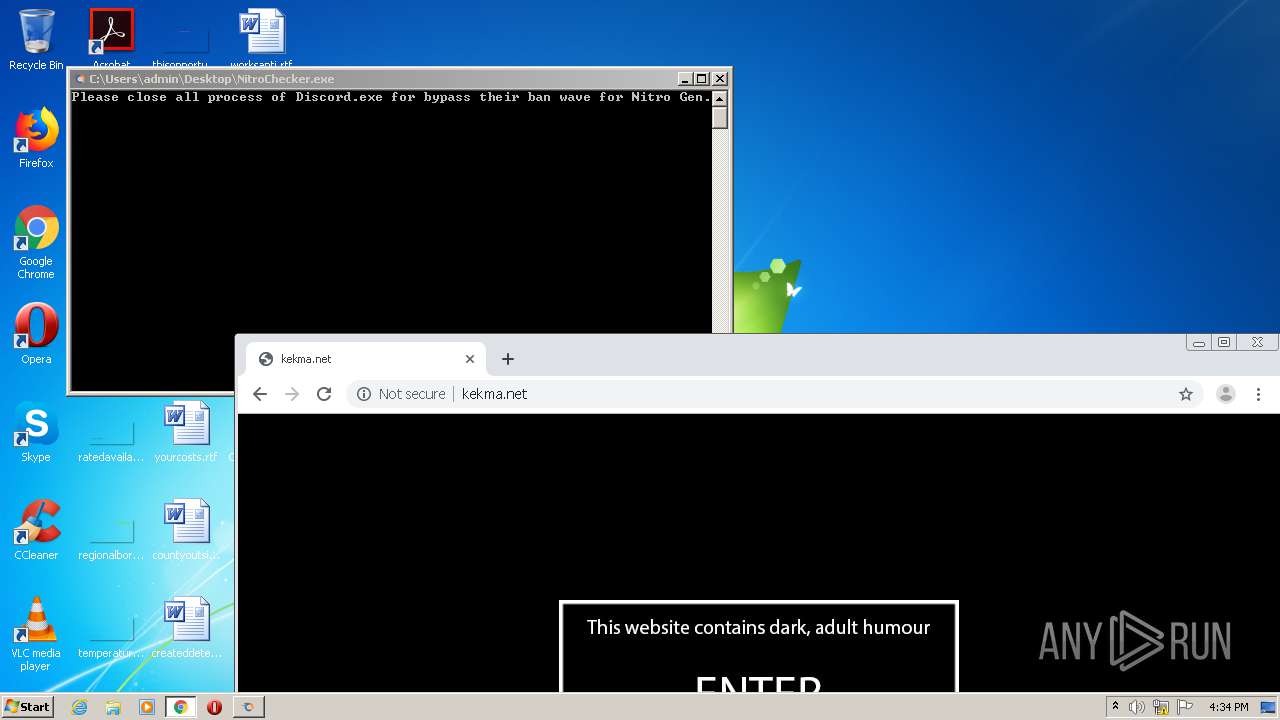
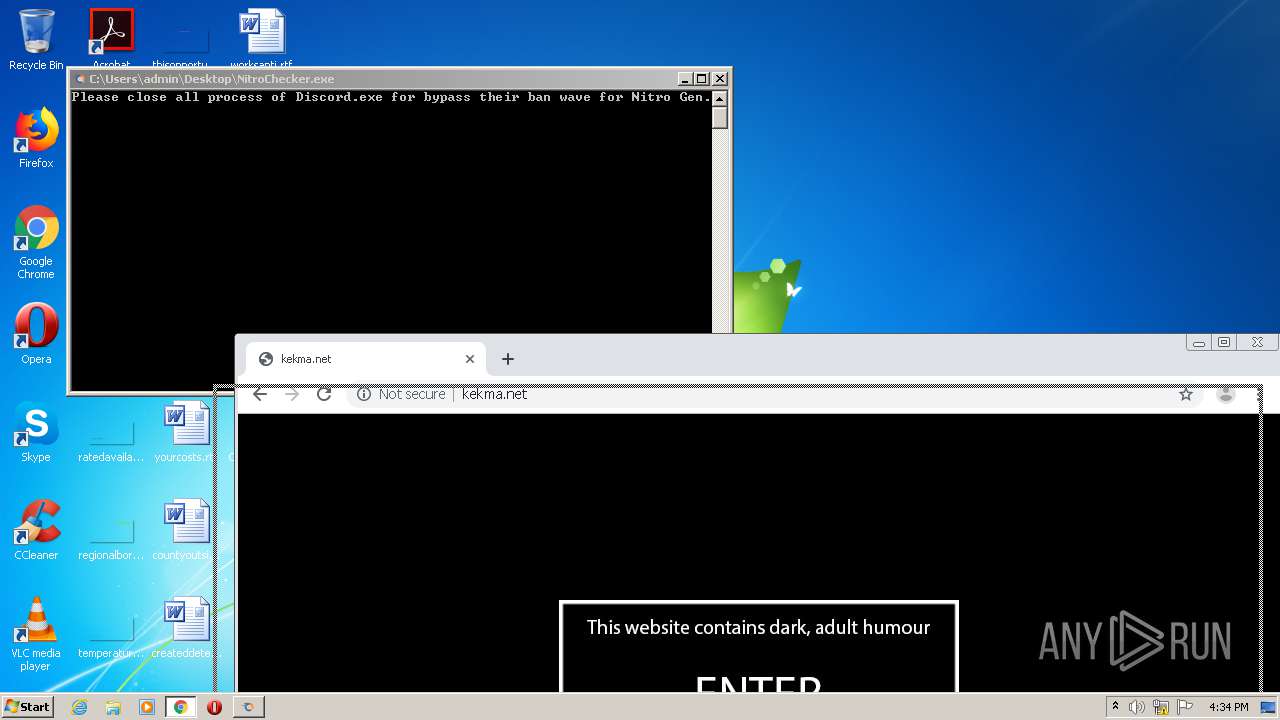
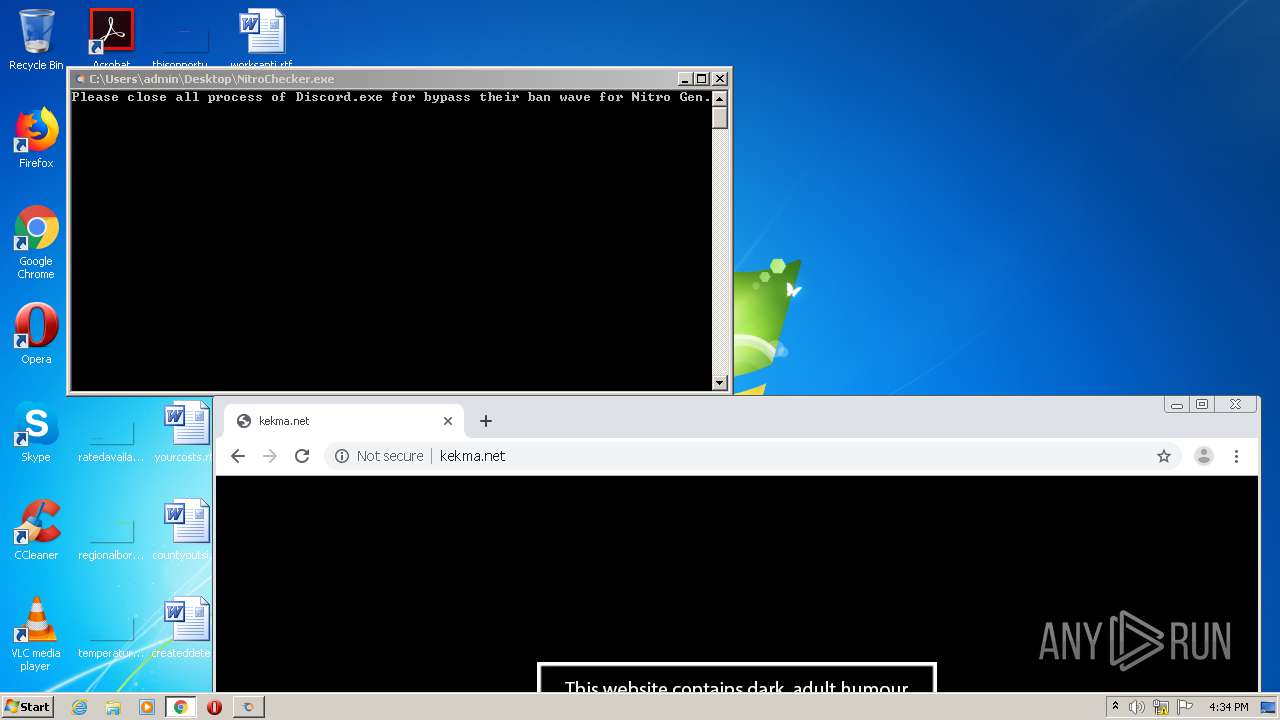
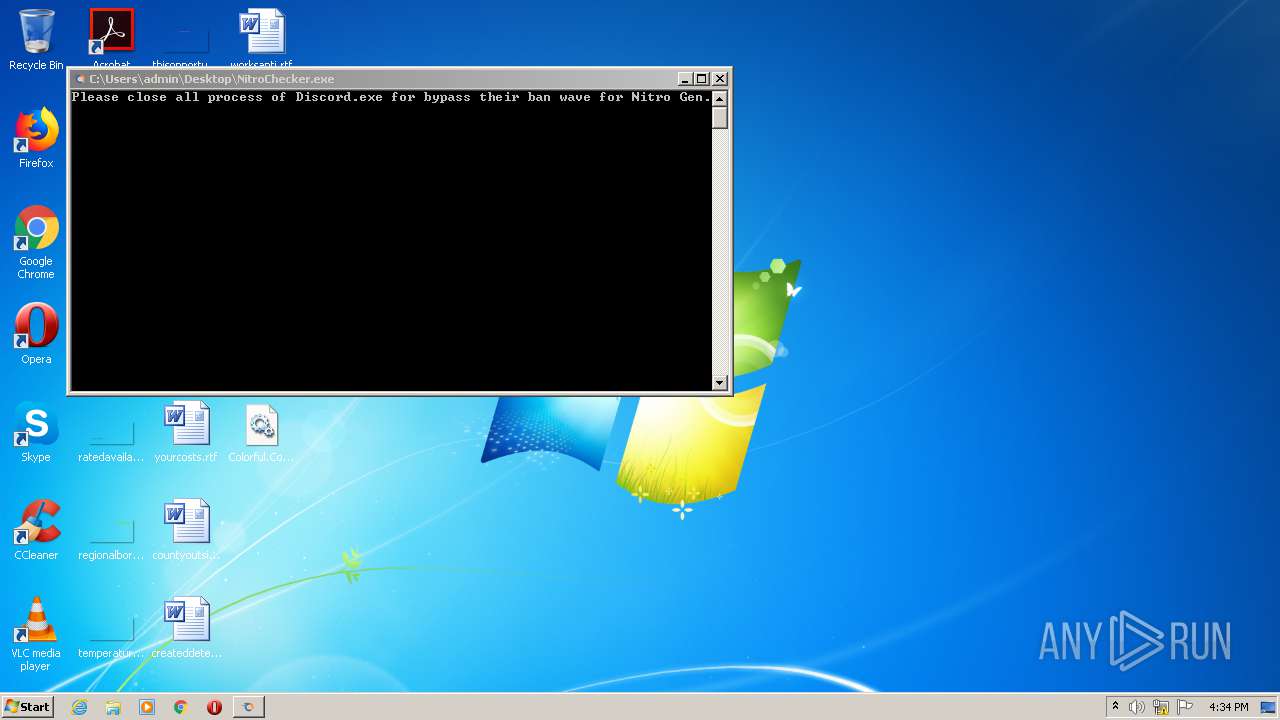
| File name: | NitroChecker.rar |
| Full analysis: | https://app.any.run/tasks/9a0f7196-12a0-4482-b8a0-f037c93e68ea |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 15:32:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 923258D156C73408096E4460495A5F51 |
| SHA1: | FB2B59ABB19FA5436ABCD5E86A4736032AD309AD |
| SHA256: | FA6120A66024635548A04C7DD26E8A5429B6790D28B732A441A1BF0A3CD41B03 |
| SSDEEP: | 6144:2GagEoL3CyjsZR24Rfo70YXyfQgN+Nq1eJirDjL4TNg0LoWpW5gS:2ebsbfo7ZXyfJVoJtO4WmS |
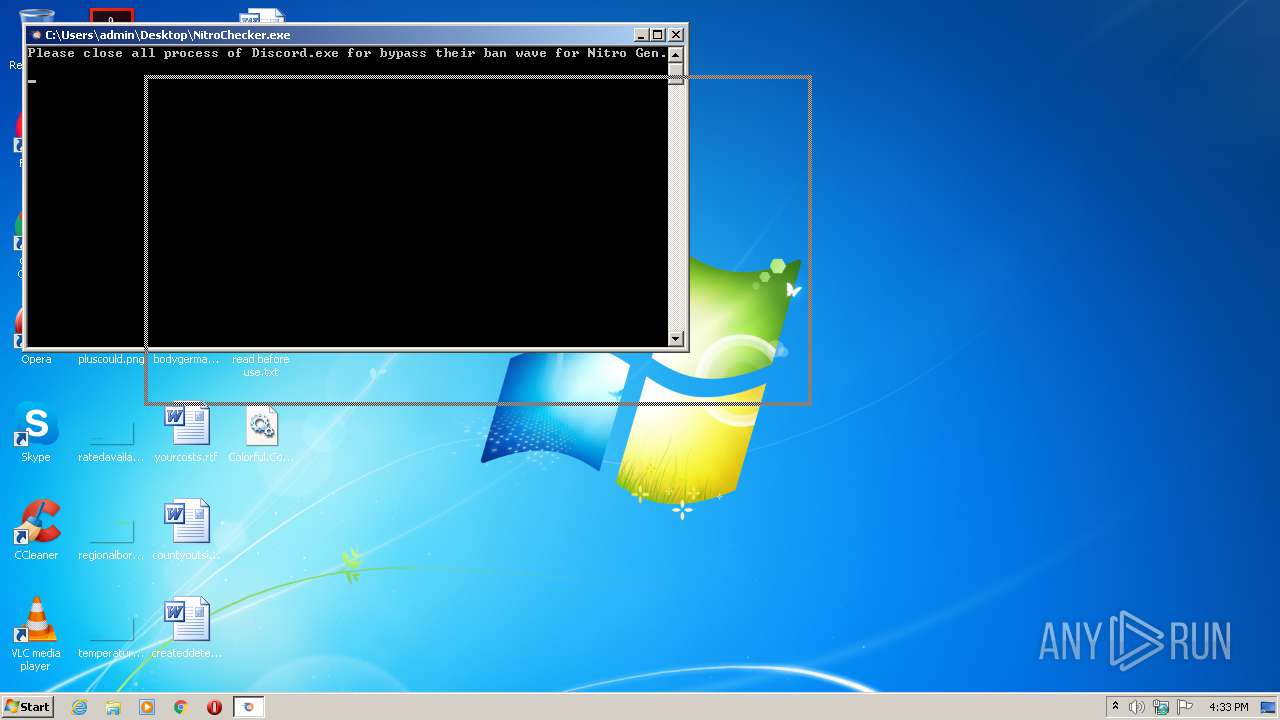
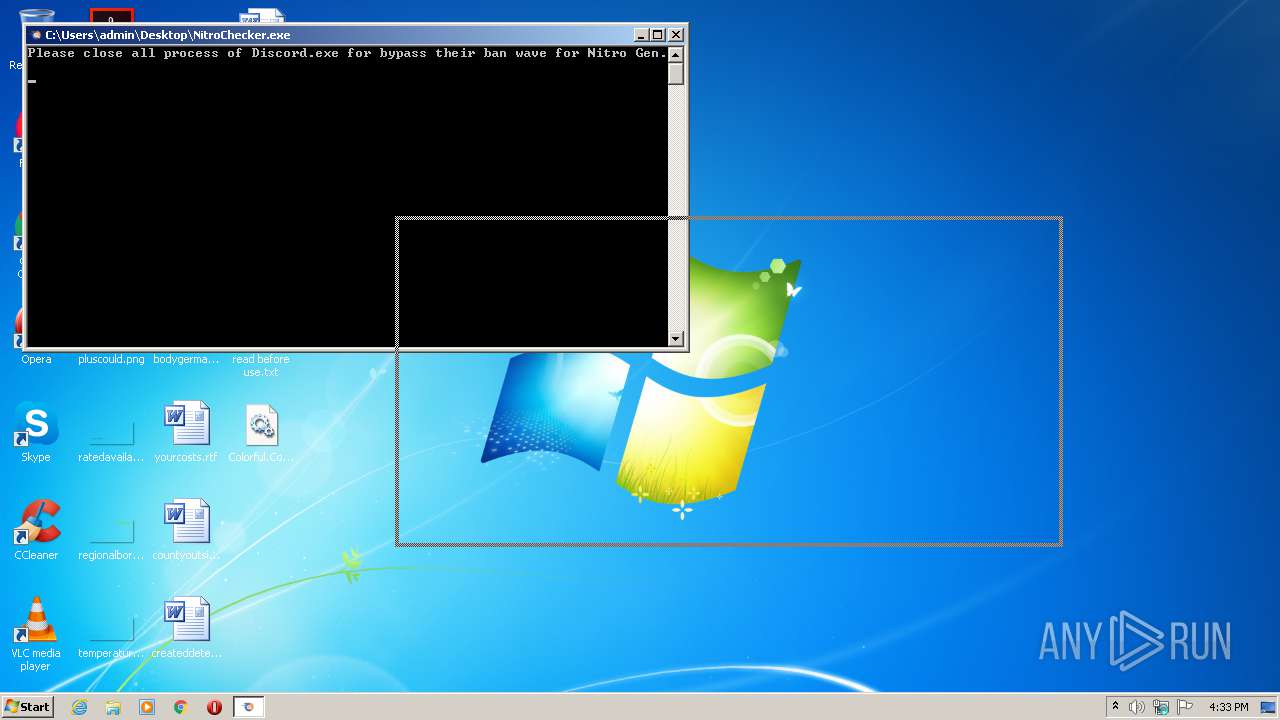
MALICIOUS
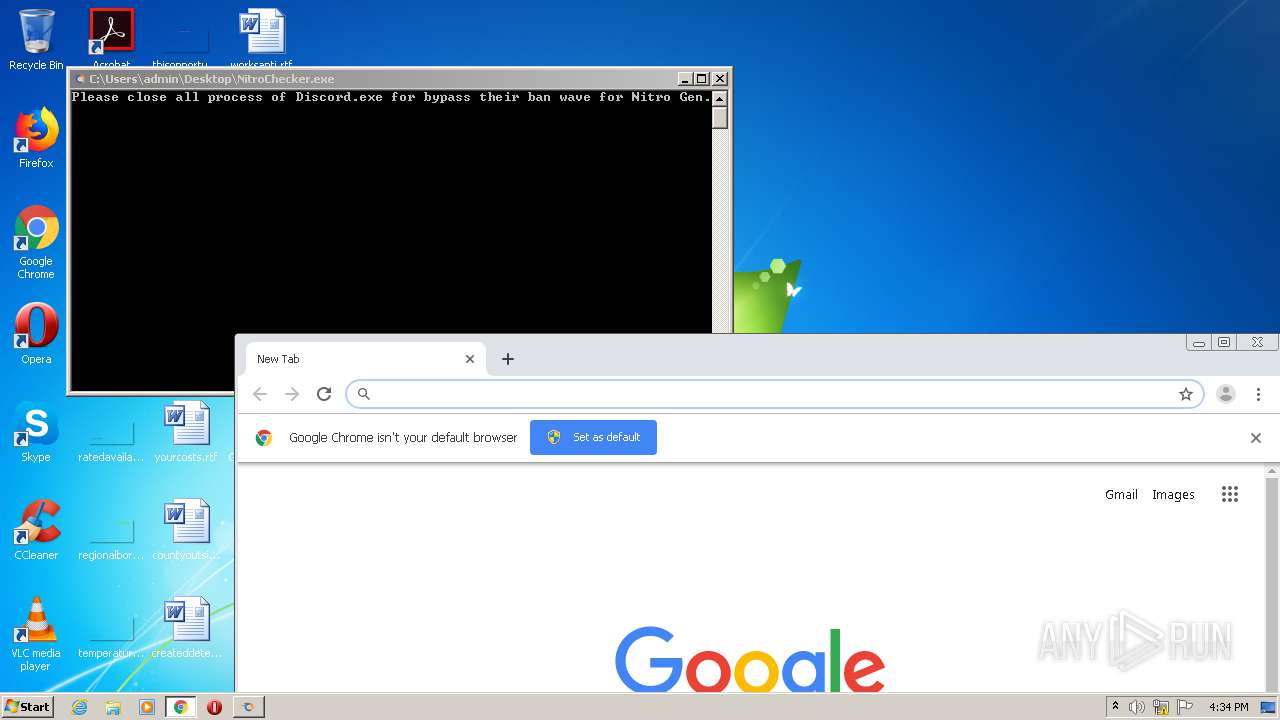
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3460)
Application was dropped or rewritten from another process
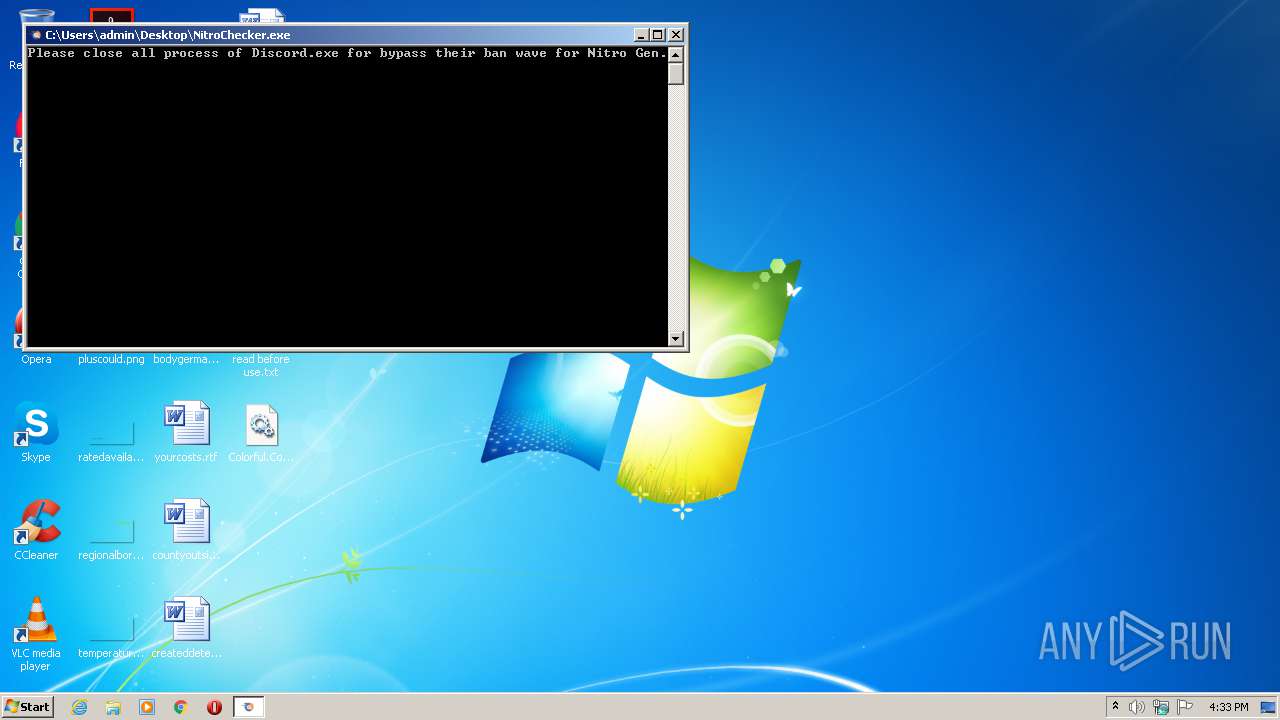
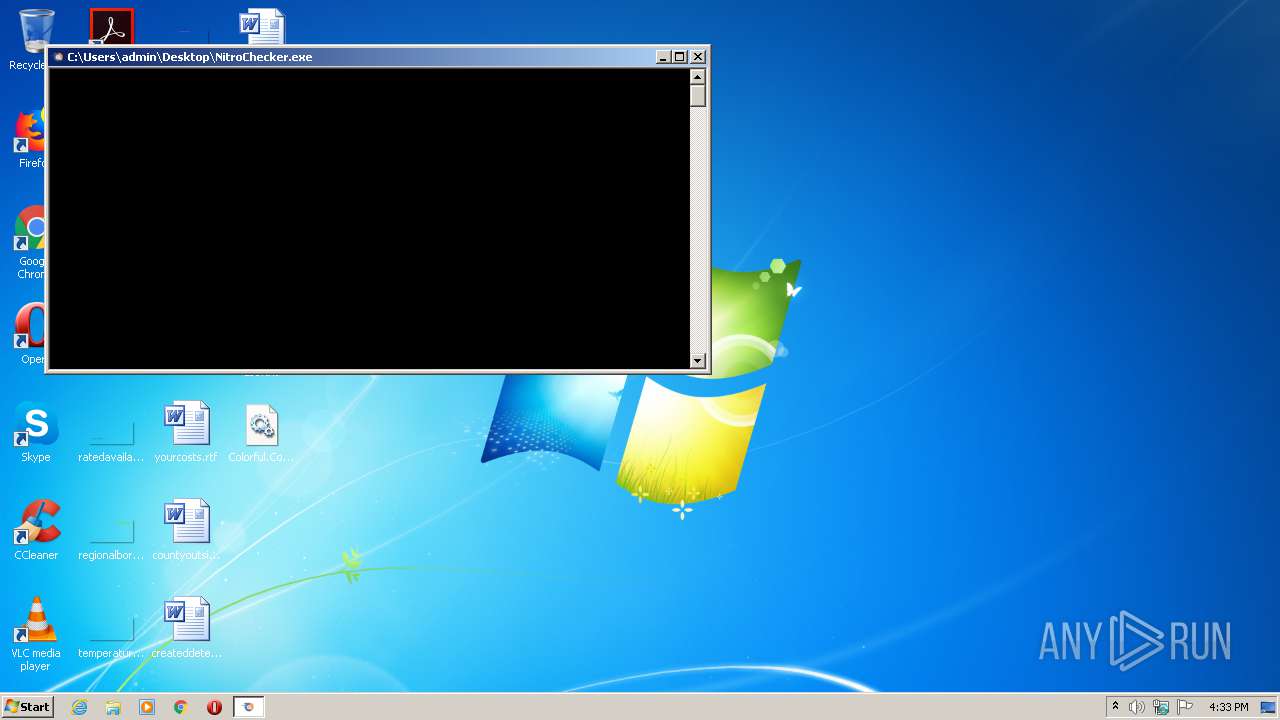
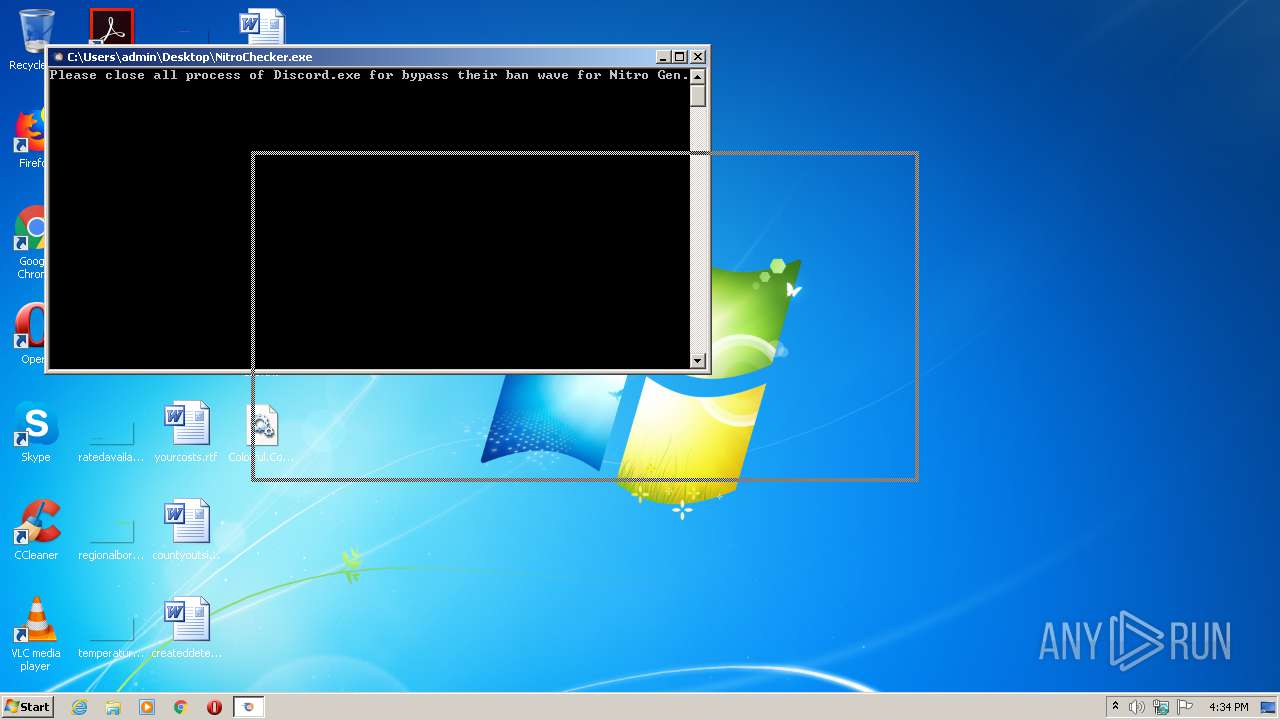
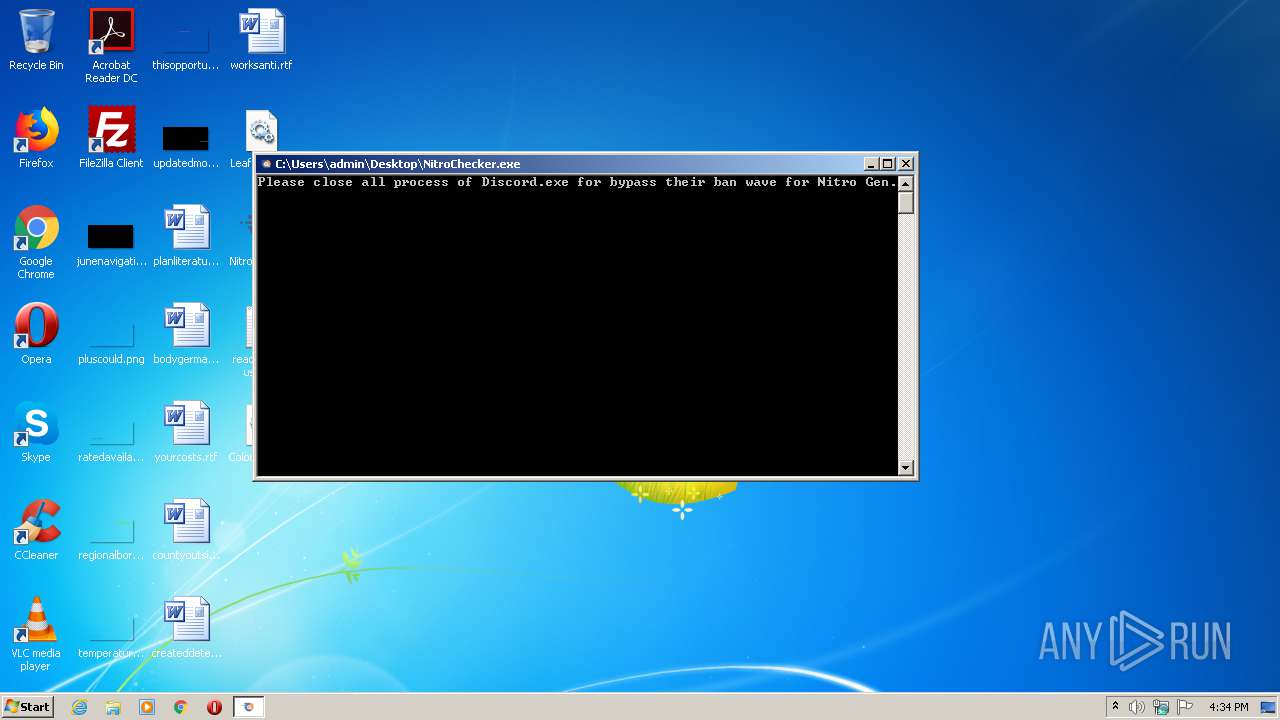
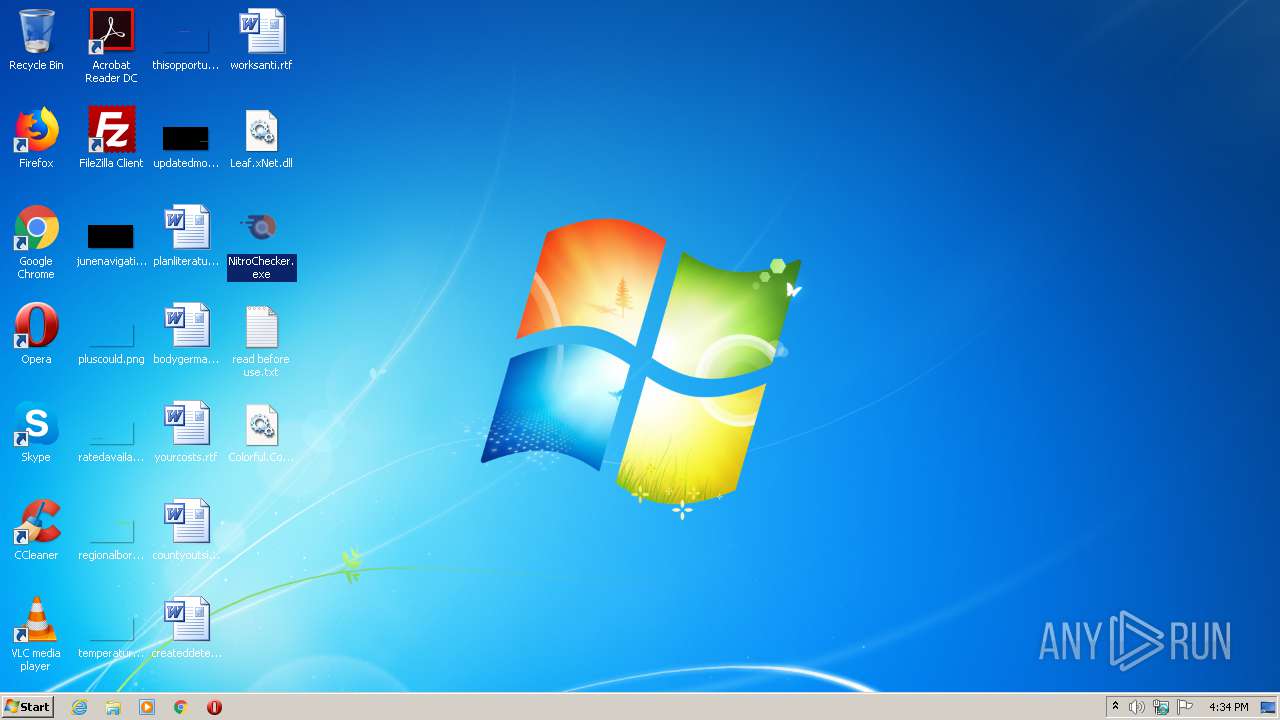
- NitroChecker.exe (PID: 2724)
- NitroChecker.exe (PID: 1816)
- NitroChecker.exe (PID: 1164)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2496)
INFO
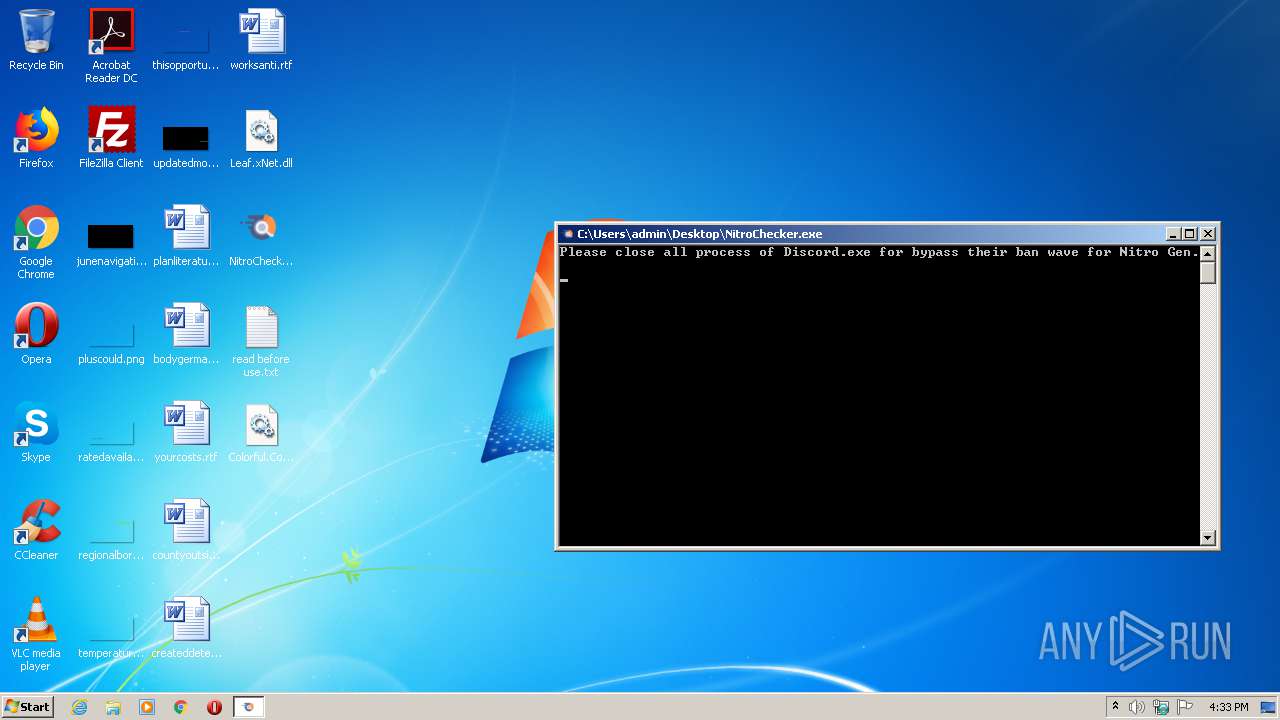
Manual execution by user
- NitroChecker.exe (PID: 2724)
- NitroChecker.exe (PID: 1816)
- NitroChecker.exe (PID: 1164)
- chrome.exe (PID: 1008)
Reads the hosts file
- chrome.exe (PID: 1008)
- chrome.exe (PID: 3652)
Application launched itself
- chrome.exe (PID: 1008)
Reads settings of System Certificates
- chrome.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
60
Monitored processes
19
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,16611159132903271309,6160504393698400242,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6133851492125886814 --mojo-platform-channel-handle=1048 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\NitroChecker.exe" | C:\Users\admin\Desktop\NitroChecker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NitroChecker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,16611159132903271309,6160504393698400242,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7889362230039667039 --mojo-platform-channel-handle=3508 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16611159132903271309,6160504393698400242,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3551821457269662182 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2424 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\Desktop\NitroChecker.exe" | C:\Users\admin\Desktop\NitroChecker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NitroChecker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,16611159132903271309,6160504393698400242,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10175090953825074083 --mojo-platform-channel-handle=3436 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2496 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NitroChecker.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2608 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2724 | "C:\Users\admin\Desktop\NitroChecker.exe" | C:\Users\admin\Desktop\NitroChecker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NitroChecker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
818
Read events
724
Write events
89
Delete events
5
Modification events
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NitroChecker.rar | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2496) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
3
Suspicious files
34
Text files
83
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFed954.TMP | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2b13e2d1-89a8-4030-9094-337f5c7d799e.tmp | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RFed9a2.TMP | text | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1008 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
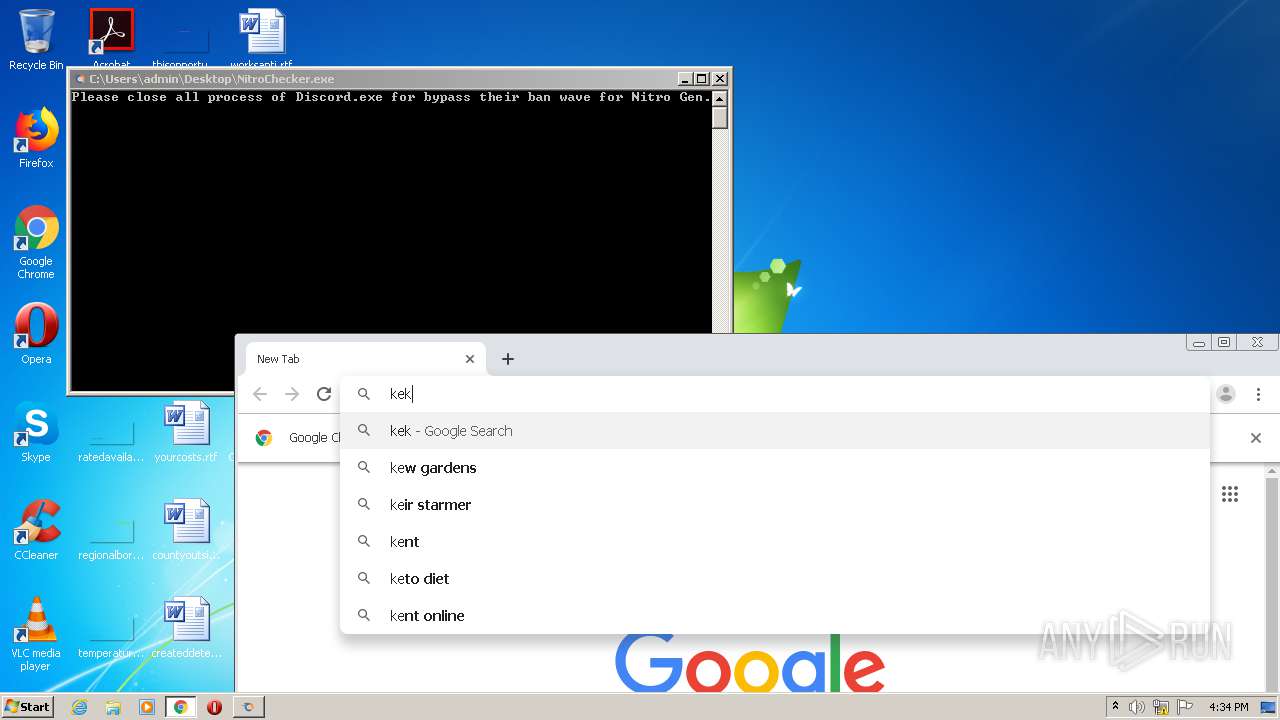
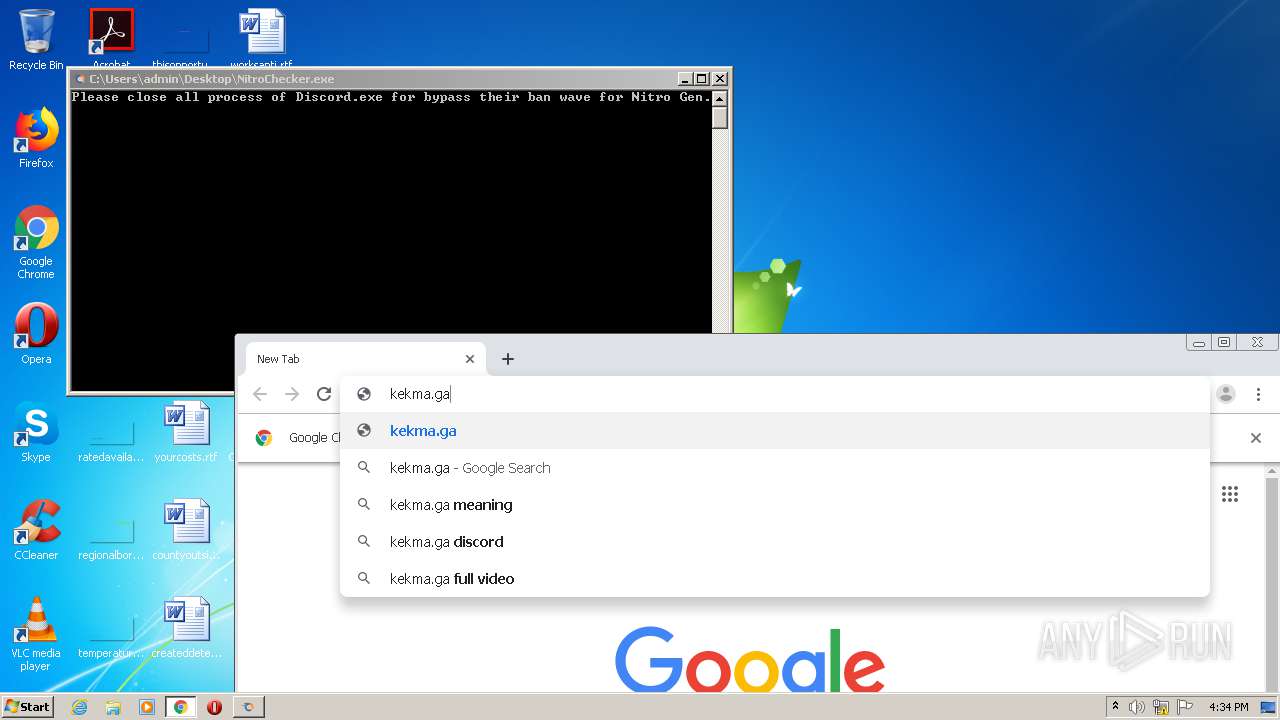
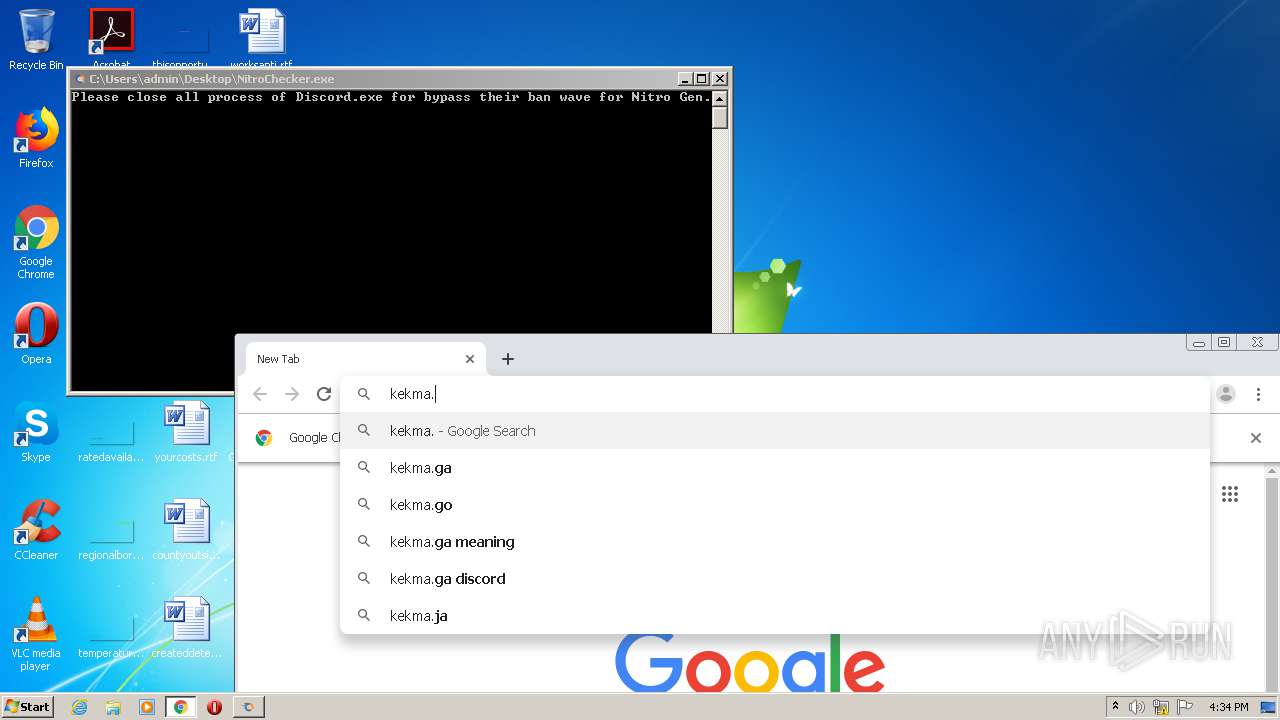
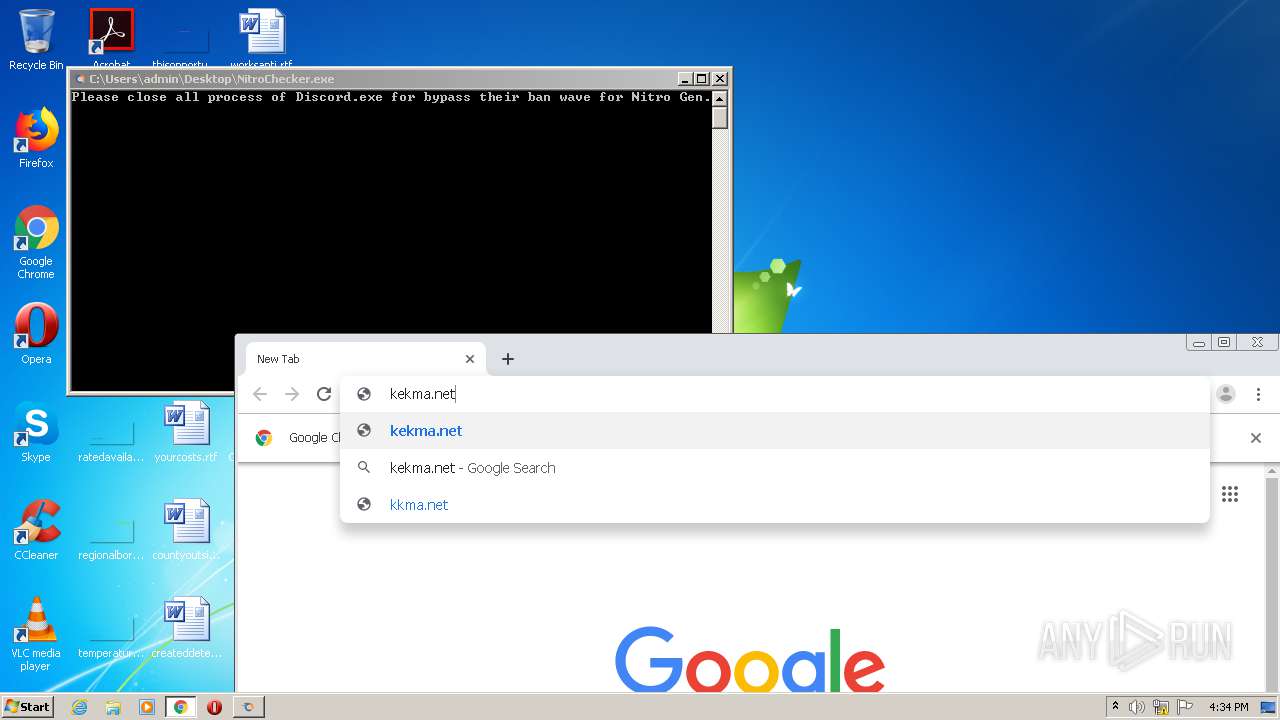
3652 | chrome.exe | GET | — | 104.31.73.96:80 | http://kekma.net/zzart.mp4 | US | — | — | malicious |
3652 | chrome.exe | GET | — | 104.31.73.96:80 | http://kekma.net/scream.mp3 | US | — | — | malicious |
3652 | chrome.exe | GET | 200 | 104.31.73.96:80 | http://kekma.net/ | US | html | 1.24 Kb | malicious |
3652 | chrome.exe | GET | 200 | 104.31.73.96:80 | http://kekma.net/styles.css | US | text | 435 b | malicious |
3652 | chrome.exe | GET | — | 104.31.73.96:80 | http://kekma.net/zzart.mp4 | US | — | — | malicious |
3652 | chrome.exe | GET | 404 | 104.31.73.96:80 | http://kekma.net/favicon.ico | US | html | 193 b | malicious |
3652 | chrome.exe | GET | 206 | 104.31.73.96:80 | http://kekma.net/rape.mp3 | US | mp3 | 284 Kb | malicious |
3652 | chrome.exe | GET | 206 | 104.31.73.96:80 | http://kekma.net/scream.mp3 | US | mp3 | 646 Kb | malicious |
3652 | chrome.exe | GET | 200 | 104.31.73.96:80 | http://kekma.net/swasticock2.png | US | image | 28.7 Kb | malicious |
3652 | chrome.exe | GET | 200 | 104.31.73.96:80 | http://kekma.net/button.jpg | US | image | 31.4 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3652 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 216.58.207.74:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 216.58.208.46:443 | apis.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.23.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 172.217.18.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3652 | chrome.exe | 172.217.18.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3652 | chrome.exe | 104.31.73.96:80 | kekma.net | Cloudflare Inc | US | shared |
3652 | chrome.exe | 209.197.3.24:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients2.google.com |
| whitelisted |