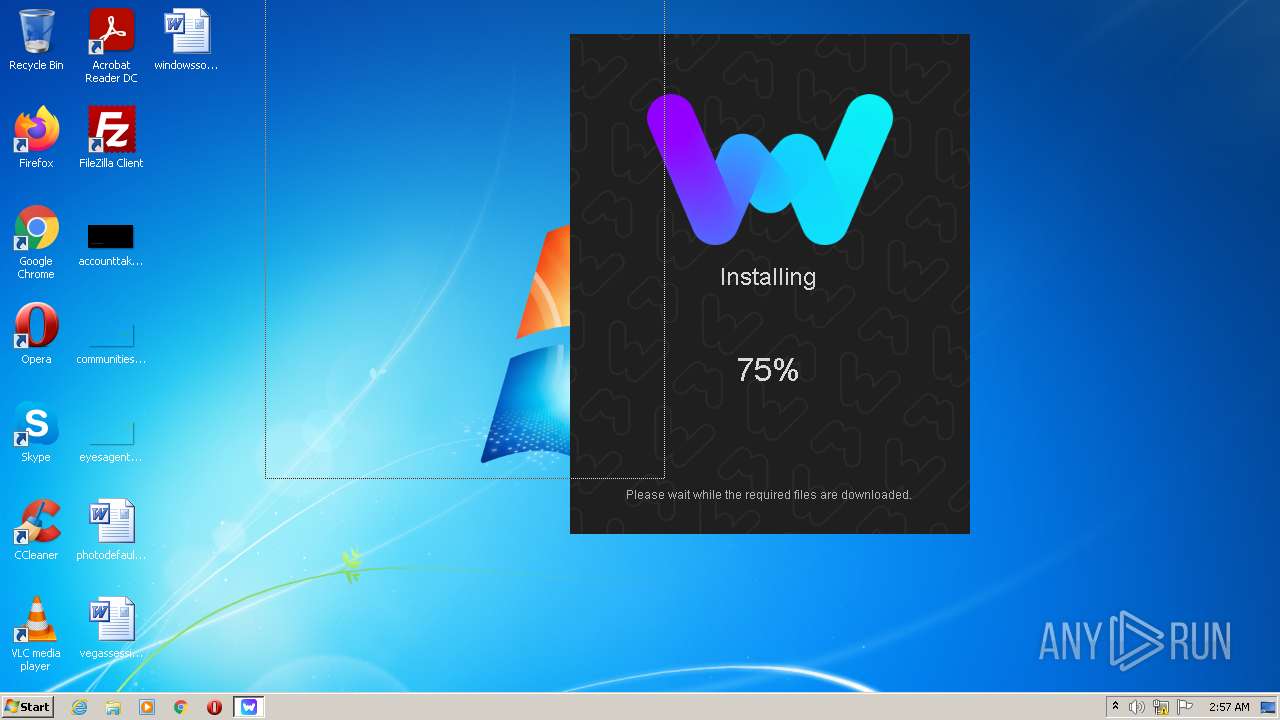
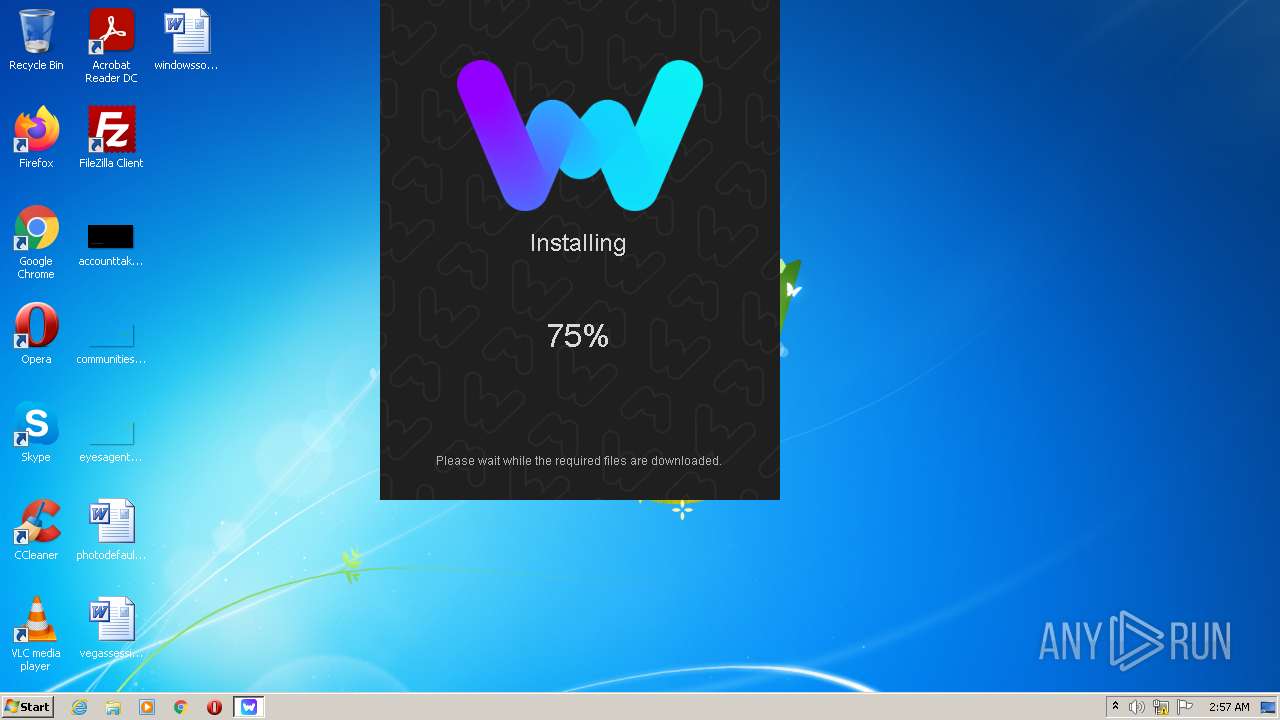
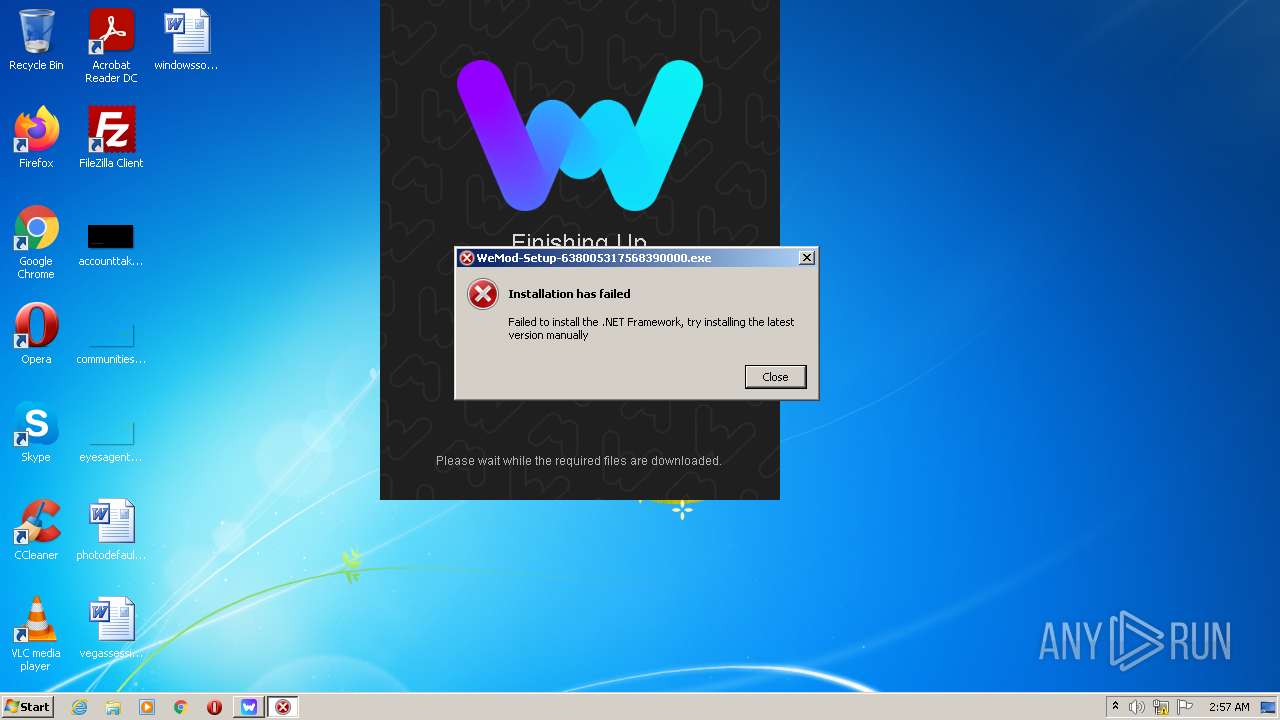
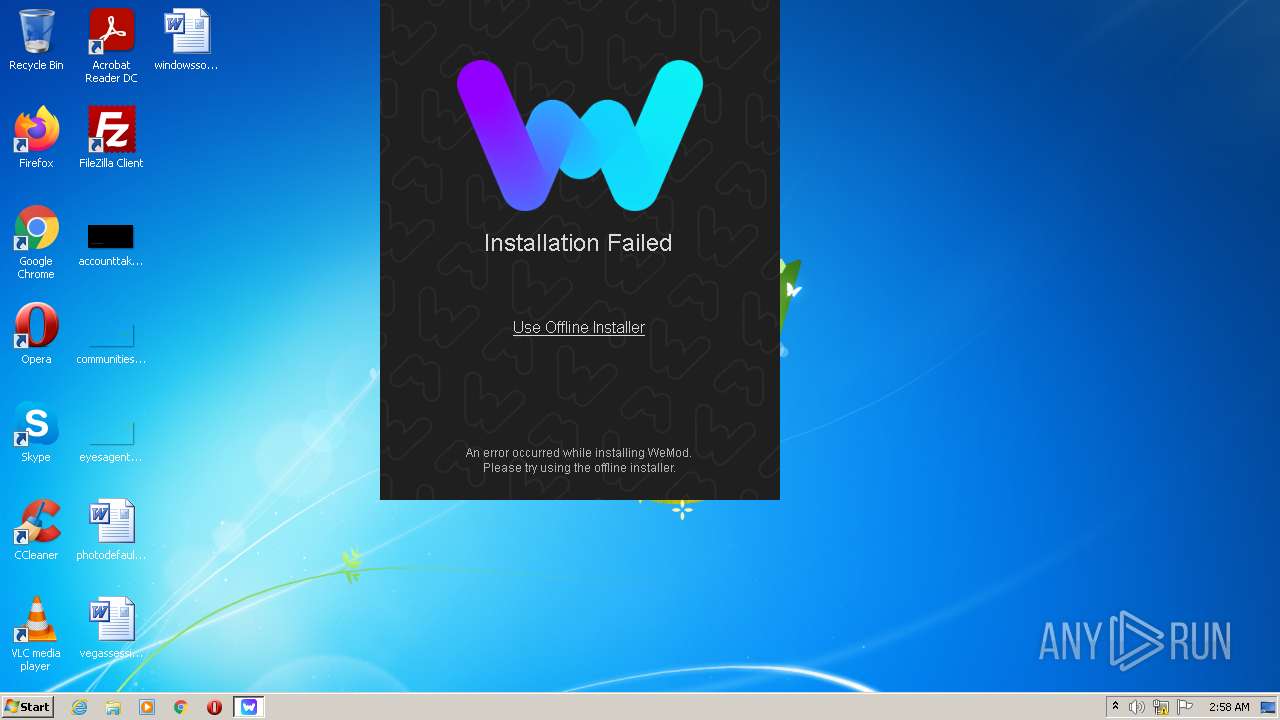
| File name: | Stormworks Build and Rescue Trainer.exe |
| Full analysis: | https://app.any.run/tasks/da088d1c-5ed1-41a9-9ddb-acfc6b596d76 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 01:55:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | C1915EEC47C9029210AEFC8CB6A06E8D |
| SHA1: | 83F58D06009B8509C5E2CEC5597FACC7C6556618 |
| SHA256: | FA59C2DAF95EA7E58416202BAC4C385DC34D057D1D6E0ADA1802C542C6214320 |
| SSDEEP: | 3072:BInO+5DW54ILlCI+4COHPZEoRGxW4ILlCI+4zOHbC:BCPc+IvnB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- Stormworks Build and Rescue Trainer.exe (PID: 296)
- WeMod-Setup-638005317568390000.exe (PID: 3060)
Checks supported languages
- Stormworks Build and Rescue Trainer.exe (PID: 296)
- WeMod-Setup-638005317568390000.exe (PID: 3060)
Reads Environment values
- Stormworks Build and Rescue Trainer.exe (PID: 296)
INFO
Checks Windows Trust Settings
- WeMod-Setup-638005317568390000.exe (PID: 3060)
Reads settings of System Certificates
- Stormworks Build and Rescue Trainer.exe (PID: 296)
- WeMod-Setup-638005317568390000.exe (PID: 3060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2042-Oct-10 23:35:31 |
| Comments: | WeMod Setup |
| CompanyName: | WeMod LLC |
| FileDescription: | WeMod Setup |
| FileVersion: | 7.0.0.0 |
| InternalName: | WeMod-Setup.exe |
| LegalCopyright: | Copyright © WeMod LLC 2021 |
| LegalTrademarks: | - |
| OriginalFilename: | WeMod-Setup.exe |
| ProductName: | WeMod |
| ProductVersion: | 7.0.0.0 |
| Assembly Version: | 7.0.0.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2042-Oct-10 23:35:31 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 8192 | 96228 | 96256 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.41107 |
.rsrc | 106496 | 27604 | 27648 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.62699 |
.reloc | 139264 | 12 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.86364 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
2 | 4.90218 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.95148 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 7.81727 | 10003 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.44608 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1 (#2) | 3.36813 | 856 | UNKNOWN | UNKNOWN | RT_VERSION |
1 (#3) | 5.27339 | 1194 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Users\admin\AppData\Local\Temp\Stormworks Build and Rescue Trainer.exe" | C:\Users\admin\AppData\Local\Temp\Stormworks Build and Rescue Trainer.exe | Explorer.EXE | ||||||||||||
User: admin Company: WeMod LLC Integrity Level: MEDIUM Description: WeMod Setup Exit code: 0 Version: 7.0.0.0 Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\AppData\Local\Temp\WeMod-Setup-638005317568390000.exe" --silent | C:\Users\admin\AppData\Local\Temp\WeMod-Setup-638005317568390000.exe | Stormworks Build and Rescue Trainer.exe | ||||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - Cheats and Mods Exit code: 2148270086 Version: 8.3.6 Modules
| |||||||||||||||
Total events
7 637
Read events
7 567
Write events
70
Delete events
0
Modification events
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (296) Stormworks Build and Rescue Trainer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Stormworks Build and Rescue Trainer_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | Stormworks Build and Rescue Trainer.exe | C:\Users\admin\AppData\Local\Temp\WeMod-Setup-638005317568390000.exe | — | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\Local\Temp\NDPC42E.exe | — | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | der | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3060 | WeMod-Setup-638005317568390000.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3060 | WeMod-Setup-638005317568390000.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3060 | WeMod-Setup-638005317568390000.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?376b692a61f7bf89 | US | compressed | 4.70 Kb | whitelisted |
3060 | WeMod-Setup-638005317568390000.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
296 | Stormworks Build and Rescue Trainer.exe | 172.67.70.173:443 | api.wemod.com | CLOUDFLARENET | US | unknown |
296 | Stormworks Build and Rescue Trainer.exe | 104.26.6.92:443 | api.wemod.com | CLOUDFLARENET | US | suspicious |
3060 | WeMod-Setup-638005317568390000.exe | 172.67.70.173:443 | api.wemod.com | CLOUDFLARENET | US | unknown |
3060 | WeMod-Setup-638005317568390000.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3060 | WeMod-Setup-638005317568390000.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3060 | WeMod-Setup-638005317568390000.exe | 23.35.236.223:443 | download.microsoft.com | AKAMAI-AS | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.wemod.com |
| unknown |
storage-cdn.wemod.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
download.microsoft.com |
| whitelisted |