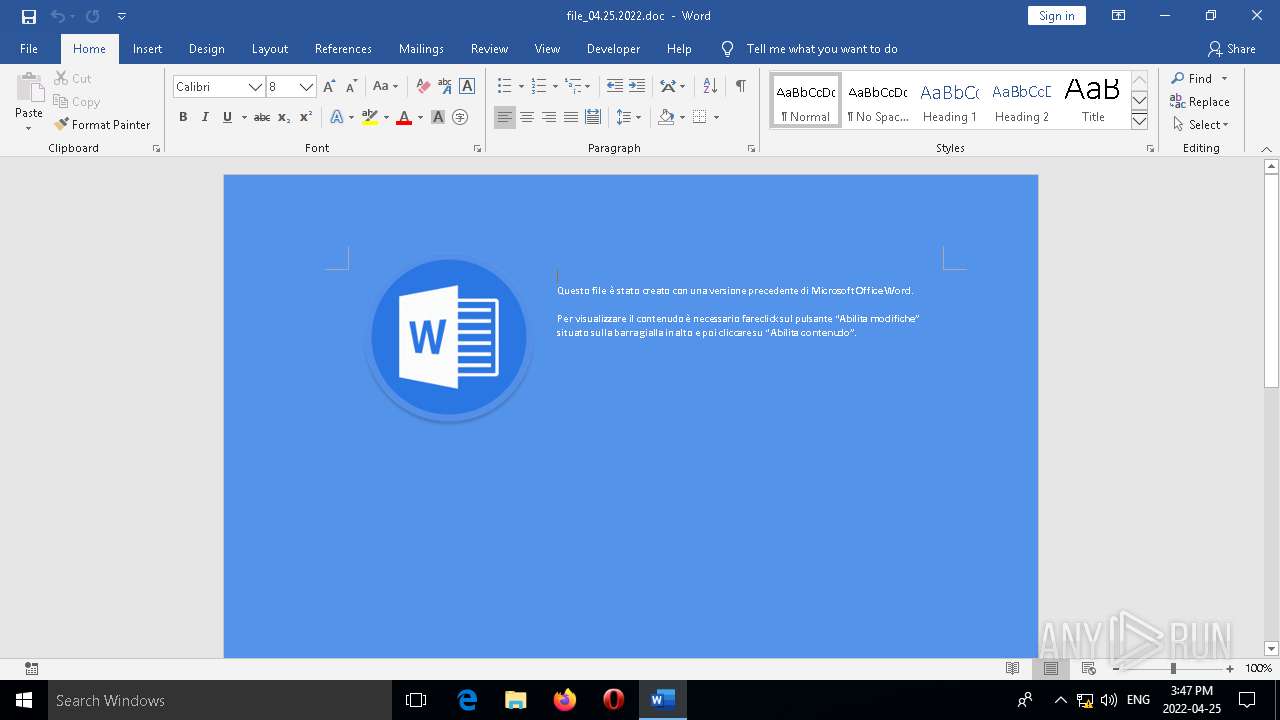
| File name: | file_04.25.2022.doc |
| Full analysis: | https://app.any.run/tasks/2b1985f1-e3a6-4b05-be34-60b00d7f1ad2 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2022, 19:46:57 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3B57AF4B7A0511167D6883A12298F2FC |
| SHA1: | 4EEE968CA5985805A494F0F507B874573390627E |
| SHA256: | FA54B01AAE86CCF77A3007A75358B2CEA9B40DF255C25E4C4785958CD8B6FC54 |
| SSDEEP: | 24576:NTzfBaJ6WwlTMpyJ0nSJXZTlCeNuhw0GhM61r/qus/mSQVoax:BlVWOTMpyJ0neZjua0Gh5ux/mQax |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2412)
Drops executable file immediately after starts
- WINWORD.EXE (PID: 2412)
SUSPICIOUS
Reads the date of Windows installation
- WINWORD.EXE (PID: 2412)
Reads default file associations for system extensions
- WINWORD.EXE (PID: 2412)
Drops a file with a compile date too recent
- WINWORD.EXE (PID: 2412)
INFO
Checks supported languages
- WINWORD.EXE (PID: 2412)
Reads the computer name
- WINWORD.EXE (PID: 2412)
Reads CPU info
- WINWORD.EXE (PID: 2412)
Reads settings of System Certificates
- WINWORD.EXE (PID: 2412)
Reads Environment values
- WINWORD.EXE (PID: 2412)
Reads the software policy settings
- WINWORD.EXE (PID: 2412)
Creates files in the user directory
- WINWORD.EXE (PID: 2412)
Checks Windows Trust Settings
- WINWORD.EXE (PID: 2412)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 2412)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
Total processes
91
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2412 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\file_04.25.2022.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
Total events
7 014
Read events
6 822
Write events
160
Delete events
32
Modification events
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E04000000000000000500000000000000 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\2412 |
| Operation: | write | Name: | 0 |
Value: 0B0E100A1971CA3DD60A489ED22BF680F11942230046E9C6C9F4D39B96EC016A0410240044FA5D64A89E01008500A907556E6B6E6F776E00 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (2412) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
16
Text files
7
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Word\~WRL0001.tmp | — | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\Desktop\~$le_04.25.2022.doc | pgc | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\file_04.25.2022.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF16fc27.TMP | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Word\file_04.25.2022309557411186487983\file_04.25.2022((Unsaved-309557073215211728)).asd | document | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yFF0C.tmp.exe | executable | |
MD5:— | SHA256:— | |||
| 2412 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{3BB3D8F8-29C7-4C7B-B9E0-422B0D155301}.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 40.125.122.176:443 | https://sls.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.16299.0/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.16299.98&MK=DELL&MD=DELL | US | — | — | whitelisted |
2608 | svchost.exe | GET | 200 | 51.124.78.146:443 | https://settings-win.data.microsoft.com/settings/v3.0/WSD/Sediment?os=windows&sampleId=5720&osVer=10.0.16299.431.amd64fre.rs3_release_svc_escrow.180502-1908&appVer=2.0.0.0 | GB | binary | 68 b | whitelisted |
2412 | WINWORD.EXE | GET | 200 | 13.107.43.16:443 | https://config.edge.skype.com/config/v2/Office/word/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bCA71190A-D63D-480A-9ED2-2BF680F11942%7d&LabMachine=false | US | text | 164 Kb | malicious |
5804 | sihclient.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | der | 813 b | whitelisted |
— | — | GET | 200 | 40.125.122.176:443 | https://sls.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.16299.0/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.16299.98&MK=DELL&MD=DELL | US | compressed | 24.8 Kb | whitelisted |
2412 | WINWORD.EXE | POST | 200 | 13.69.239.73:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | IE | binary | 9 b | whitelisted |
2412 | WINWORD.EXE | POST | 200 | 13.69.239.73:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | IE | binary | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | Microsoft Corporation | GB | whitelisted |
5804 | sihclient.exe | 2.18.233.62:80 | — | Akamai International B.V. | — | whitelisted |
2412 | WINWORD.EXE | 13.107.43.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
2412 | WINWORD.EXE | 13.69.239.73:443 | self.events.data.microsoft.com | Microsoft Corporation | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | 15:47:08 Opening archive C:\Users\admin\Desktop\file_04.25.2022.doc/svc32.dll
|
WINWORD.EXE | 15:47:08 File svc32.dll size=4ce00...
|
WINWORD.EXE | 15:47:08 Running EXE C:\Users\admin\AppData\Local\Temp\yFF0C.tmp.exe
|