| File name: | noclip.exe |
| Full analysis: | https://app.any.run/tasks/ac476723-1dbf-4edd-88e8-a764dad6dcaf |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 20:38:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | E84E4DA0F16E40521247870311EFD7AC |
| SHA1: | 30683171AAE1E7DD7288E3B1AD7EF1FBDE632365 |
| SHA256: | FA4DA01EF3E3D6ECA87A36BA135E9B2084461A68E975895BC57050F6AB472DEF |
| SSDEEP: | 24576:Z6E1hGOo/pEgu6KxSazUU8w0L+ygU+uQz:0E1KpEgu6KxSazUU8w0L+yRQz |
MALICIOUS
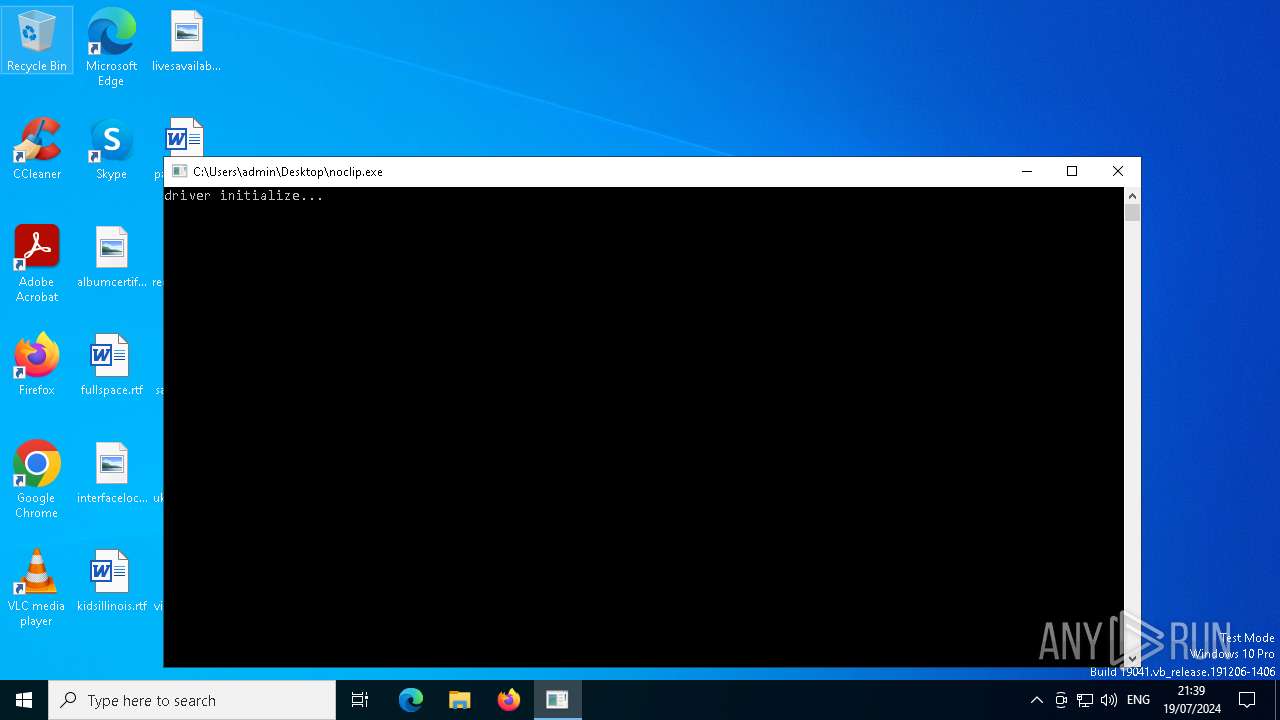
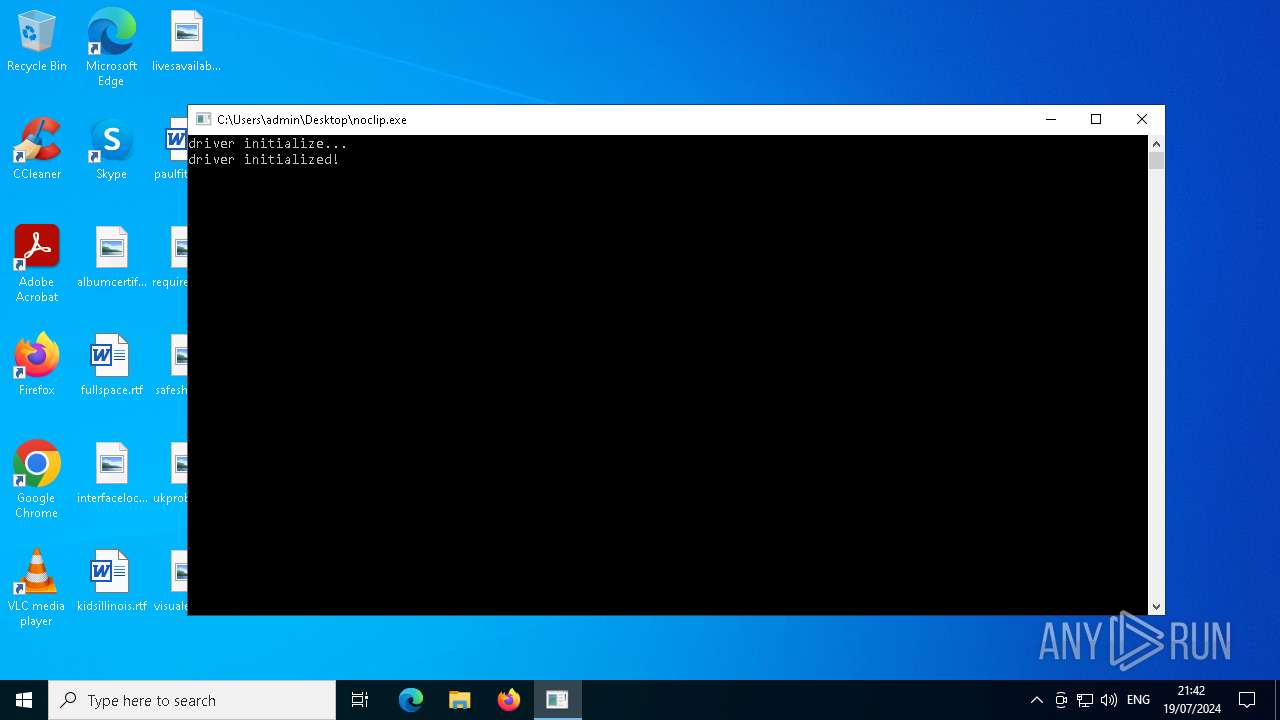
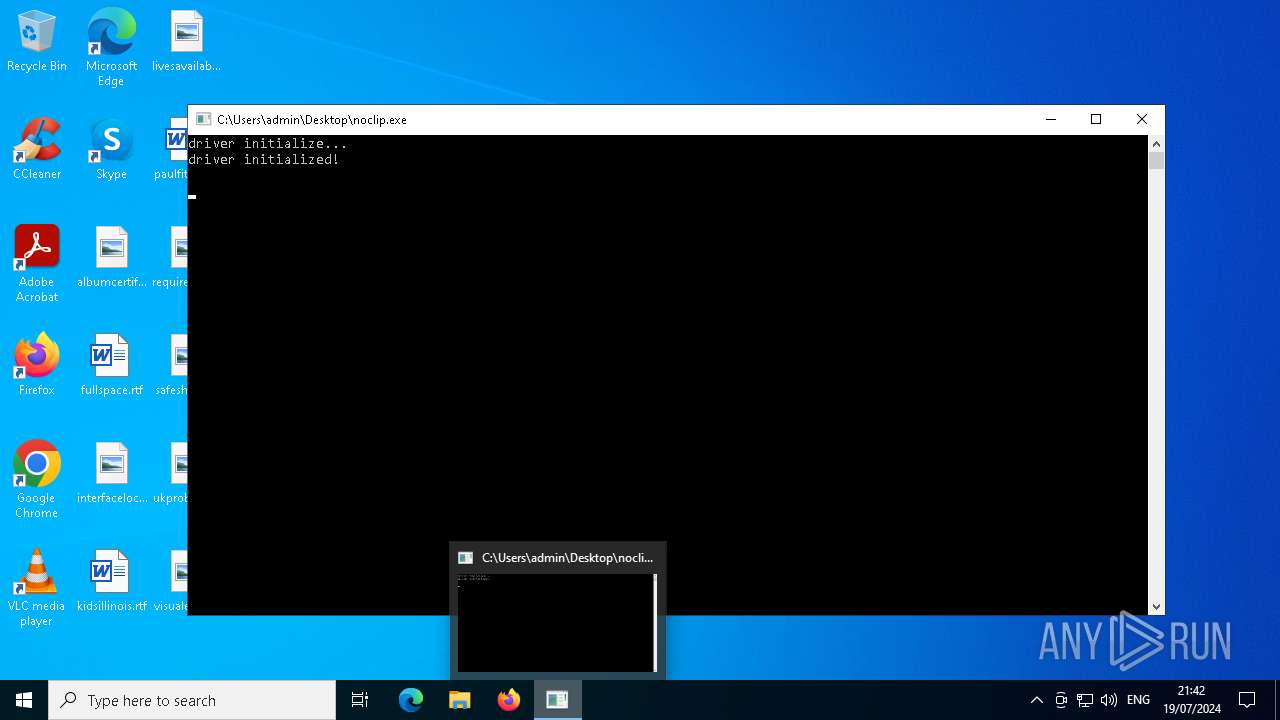
Drops the executable file immediately after the start
- noclip.exe (PID: 4952)
- oOrwm.exe (PID: 6920)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- noclip.exe (PID: 4952)
- oOrwm.exe (PID: 6920)
Reads security settings of Internet Explorer
- noclip.exe (PID: 4952)
Reads the date of Windows installation
- noclip.exe (PID: 4952)
Executable content was dropped or overwritten
- noclip.exe (PID: 4952)
- oOrwm.exe (PID: 6920)
Creates or modifies Windows services
- oOrwm.exe (PID: 6920)
INFO
Reads the computer name
- noclip.exe (PID: 4952)
Checks supported languages
- noclip.exe (PID: 4952)
- oOrwm.exe (PID: 6920)
Reads the machine GUID from the registry
- oOrwm.exe (PID: 6920)
Checks proxy server information
- slui.exe (PID: 2204)
Create files in a temporary directory
- oOrwm.exe (PID: 6920)
Reads the software policy settings
- slui.exe (PID: 2204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:02 21:16:44+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 203776 |
| InitializedDataSize: | 371200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe6ac |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
165
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | noclip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\Desktop\noclip.exe" | C:\Users\admin\Desktop\noclip.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4952 | "C:\Users\admin\Desktop\noclip.exe" | C:\Users\admin\Desktop\noclip.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6920 | "C:\WINDOWS\SoftwareDistribution\Download\oOrwm.exe" -map C:\WINDOWS\SoftwareDistribution\Download\oOrwm.sys | C:\Windows\SoftwareDistribution\Download\oOrwm.exe | noclip.exe | ||||||||||||
User: admin Company: UG North Integrity Level: HIGH Description: Kernel Driver Utility Exit code: 0 Version: 1.0.0.2002 Modules
| |||||||||||||||
| 7196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | oOrwm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7508 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
Total events
4 854
Read events
4 829
Write events
23
Delete events
2
Modification events
| (PID) Process: | (4952) noclip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4952) noclip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4952) noclip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4952) noclip.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\NalDrv |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\NalDrv |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\NalDrv |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\NalDrv |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\Desktop\NalDrv.sys | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCEXP152 |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (6920) oOrwm.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCEXP152 |
| Operation: | write | Name: | Type |
Value: 1 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6920 | oOrwm.exe | C:\Users\admin\AppData\Local\Temp\PROCEXP152.sys | executable | |
MD5:C06DDA757B92E79540551EFD00B99D4B | SHA256:9B6A84F7C40EA51C38CC4D2E93EFB3375E9D98D4894A85941190D94FBE73A4E4 | |||
| 4952 | noclip.exe | C:\WINDOWS\SoftwareDistribution\Download\oOrwm.sys | executable | |
MD5:657C2A27E4038AE1041474FB901540FA | SHA256:19066DF50EB8B7C76D06552CCBD6248A6384A45A7F04500C6DE4AB37149BAC54 | |||
| 4952 | noclip.exe | C:\WINDOWS\SoftwareDistribution\Download\oOrwm.exe | executable | |
MD5:083C6C05AC5875D0B6E997E894CA07BC | SHA256:03AEFD40698CAFBD48138784F362FB9A36F726FB50F262CA40695729F7B553CA | |||
| 6920 | oOrwm.exe | C:\Users\admin\Desktop\NalDrv.sys | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
73
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 20.114.59.183:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | POST | — | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | GET | 200 | 184.86.251.25:443 | https://www.bing.com/client/config?cc=US&setlang=en-US | unknown | binary | 2.15 Kb | unknown |
— | — | POST | — | 20.190.159.2:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | POST | 403 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 384 b | unknown |
— | — | POST | 403 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | — | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | POST | — | 40.126.32.134:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5620 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6156 | backgroundTaskHost.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
2760 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |