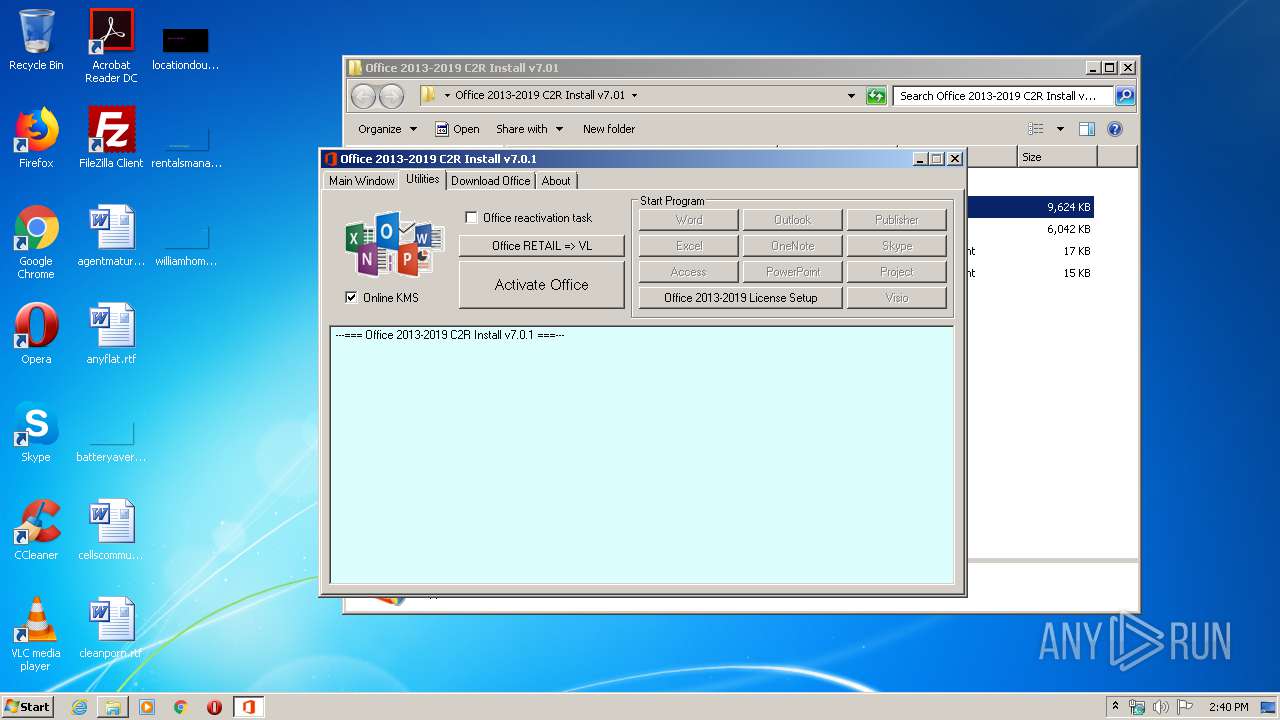
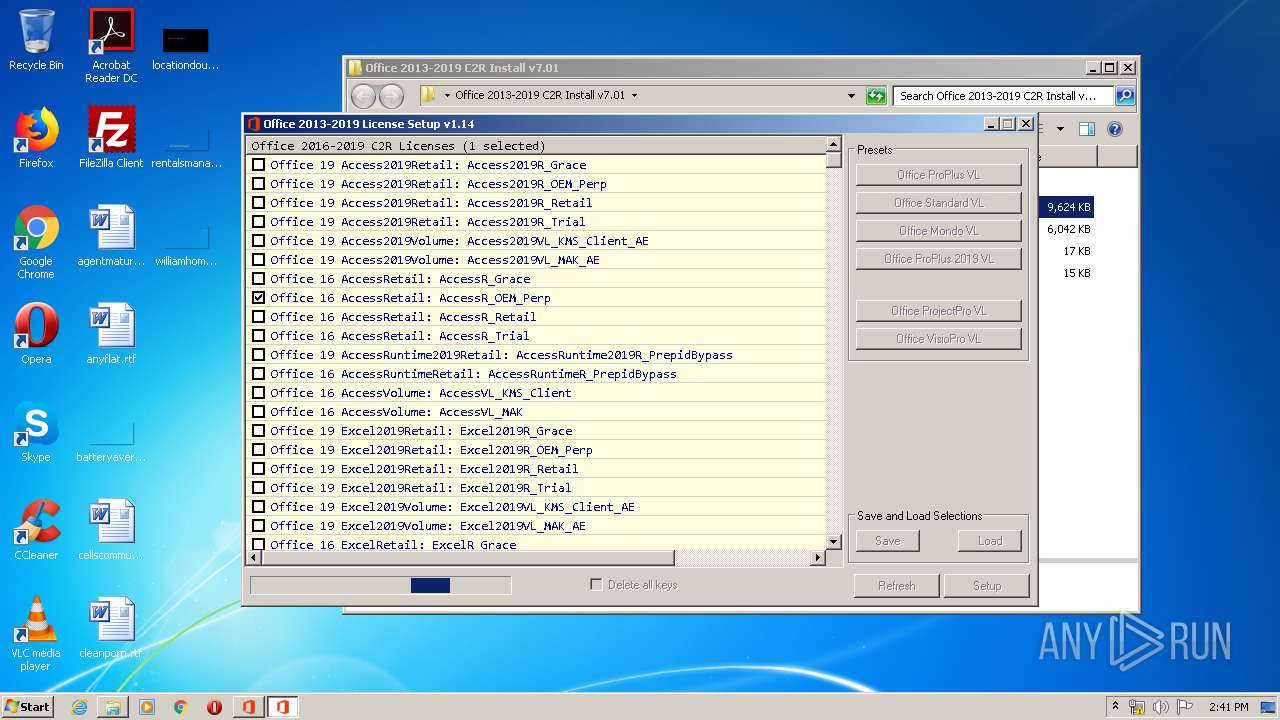
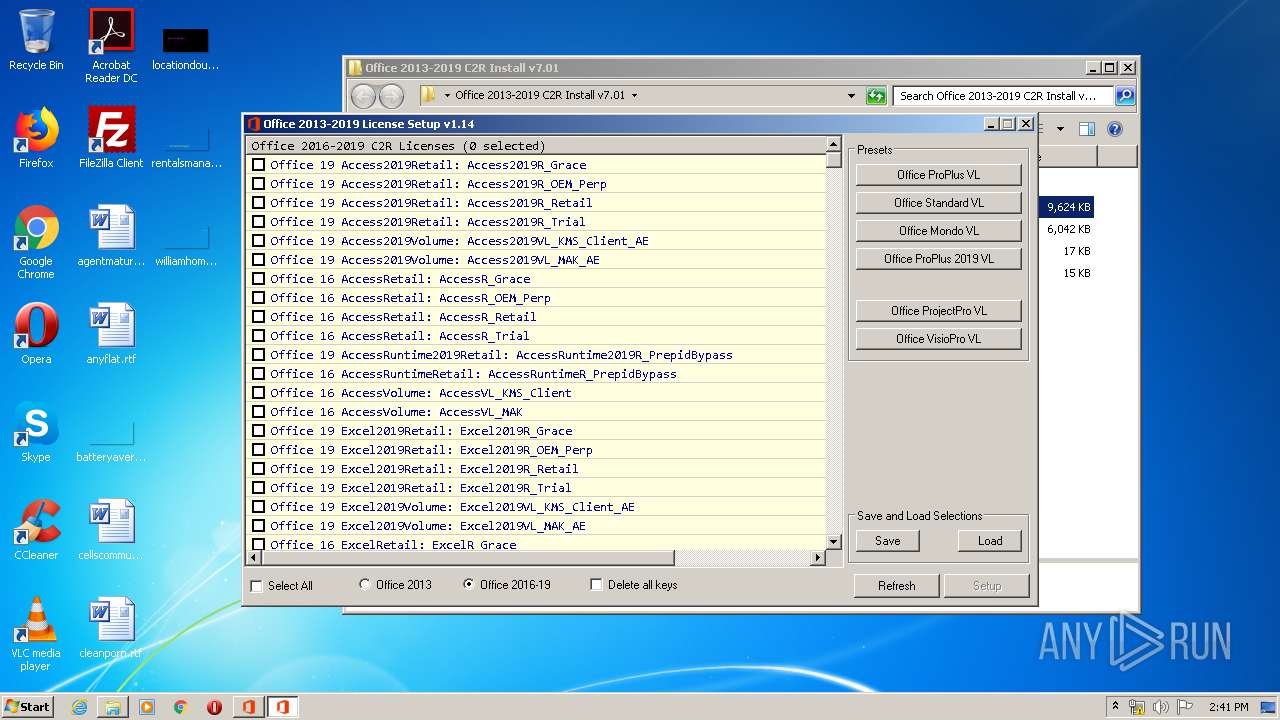
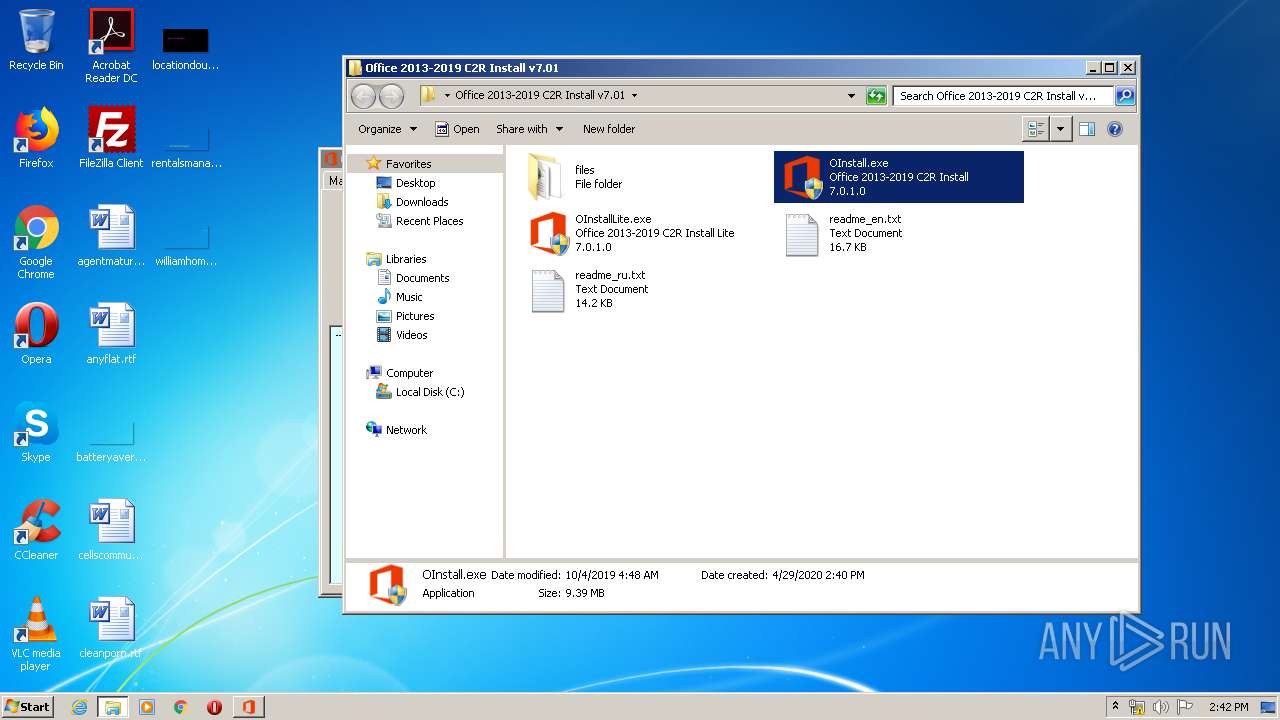
| File name: | Office 2013-2019 C2R Install v7.01.zip |
| Full analysis: | https://app.any.run/tasks/05380f73-b904-4f6e-a0f7-2bb2ee2f91f9 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2020, 13:39:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 7523DB29A1C286527B6DF92E0470CACE |
| SHA1: | 47936553A085E2887D807868BFA0DE1139C1A2AB |
| SHA256: | FA3FB2FF735389654F0D3AF2539D5F220F6C724F4614EB0077325BE99B47B451 |
| SSDEEP: | 393216:8PPWtLfCSjLatvQWbygbQweSQnuMqiIyQ:QWteRD9UHXqiI/ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1848)
- cleanospp.exe (PID: 4092)
Application was dropped or rewritten from another process
- OInstall.exe (PID: 3224)
- O15-16LicSetup.exe (PID: 3168)
- OInstall.exe (PID: 564)
- files.dat (PID: 1564)
- files.dat (PID: 2792)
- cleanospp.exe (PID: 4092)
- test.dat (PID: 1524)
- test.dat (PID: 740)
- test.dat (PID: 3332)
- test.dat (PID: 1840)
- test.dat (PID: 2120)
- test.dat (PID: 1028)
- test.dat (PID: 2552)
Changes settings of System certificates
- cscript.exe (PID: 2724)
SUSPICIOUS
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2628)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 2856)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 2104)
Executes scripts
- cmd.exe (PID: 3300)
- cmd.exe (PID: 1876)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 3772)
- cmd.exe (PID: 1760)
- cmd.exe (PID: 1156)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 984)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 4068)
- cmd.exe (PID: 3260)
- cmd.exe (PID: 2500)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 376)
- cmd.exe (PID: 3928)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 3128)
- cmd.exe (PID: 608)
Executable content was dropped or overwritten
- OInstall.exe (PID: 564)
- WinRAR.exe (PID: 2588)
- O15-16LicSetup.exe (PID: 3168)
- files.dat (PID: 1564)
- files.dat (PID: 2792)
Creates files in the Windows directory
- OInstall.exe (PID: 564)
Starts application with an unusual extension
- cmd.exe (PID: 1116)
- cmd.exe (PID: 3196)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 3172)
- cmd.exe (PID: 3356)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 3712)
- cmd.exe (PID: 3056)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 564)
- O15-16LicSetup.exe (PID: 3168)
Adds / modifies Windows certificates
- cscript.exe (PID: 2724)
INFO
Manual execution by user
- OInstall.exe (PID: 3224)
- OInstall.exe (PID: 564)
Reads Microsoft Office registry keys
- reg.exe (PID: 3928)
- reg.exe (PID: 1900)
- reg.exe (PID: 2380)
Reads settings of System Certificates
- cscript.exe (PID: 2724)
Dropped object may contain Bitcoin addresses
- files.dat (PID: 2792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (40) |
|---|---|---|
| .zip | | | ZIP compressed archive (20) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:12:01 15:55:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Office 2013-2019 C2R Install v7.01/ |
Total processes
169
Monitored processes
86
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | cscript.exe "" //NoLogo /setprt:1688 | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 376 | "C:\Windows\System32\cmd.exe" /D /c cscript.exe "" //NoLogo /remhst | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | cscript.exe ospp.vbs /inslic:client-issuance-stil.xrm-ms | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 480 | cscript.exe ospp.vbs /dstatusall | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 564 | "C:\Users\admin\Desktop\Office 2013-2019 C2R Install v7.01\OInstall.exe" | C:\Users\admin\Desktop\Office 2013-2019 C2R Install v7.01\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Office 2013-2019 C2R Install Exit code: 0 Modules
| |||||||||||||||
| 608 | "C:\Windows\System32\cmd.exe" /D /c cscript.exe "" //NoLogo /act | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 740 | C:\Windows\Temp\test.dat hq1.chinancce.com:1688 -l Windows -6 | C:\Windows\Temp\test.dat | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 780 | cscript.exe ospp.vbs /inslic:client-issuance-root.xrm-ms | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 956 | cscript.exe "" //NoLogo /act | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 984 | "C:\Windows\System32\cmd.exe" /c cscript.exe ospp.vbs /inslic:client-issuance-bridge-office.xrm-ms | C:\Windows\System32\cmd.exe | — | O15-16LicSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 982
Read events
1 611
Write events
1 371
Delete events
0
Modification events
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Office 2013-2019 C2R Install v7.01.zip | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2588) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
19
Suspicious files
0
Text files
1 870
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\OInstallLite.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\OInstall.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\files\Configure.xml | text | |
MD5:8DF529B7A22F39D5C8B142BBF0CE4ADD | SHA256:3A001CDBD75D467D9A21EF6248531169CEB18DA83DAB4B0D57F49C0088B634D4 | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\files\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 1564 | files.dat | C:\Users\admin\AppData\Local\Temp\o15files\AccessR_Grace-ul-oob.xrm-ms | xml | |
MD5:9602E7CC4CB46F3B6E4FA33E158AB0D7 | SHA256:6B14E4026FEF6E824E07310F570E4C820E18AF35849A9037777EA46DBF2B4FFC | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\readme_ru.txt | text | |
MD5:8375B6F91375B1CECAAF4B2CE03E22D7 | SHA256:D794337F806BCF2ECEEA9F60E16F4B76CC149451B80857D27FC864F2B0B5674F | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 1564 | files.dat | C:\Users\admin\AppData\Local\Temp\o15files\AccessR_OEM_Perp-ppd.xrm-ms | xml | |
MD5:2BDA339E2BD24A4BD6AD9A014BD6ECB2 | SHA256:1B480130EE98D24041C6F223CEF3CCB4EA51009FCC53E6AED055DAEE91B62ADB | |||
| 2588 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2588.43839\Office 2013-2019 C2R Install v7.01\readme_en.txt | text | |
MD5:72B161A3666EDAD01AC9F6D6C289B938 | SHA256:F9C03C2F5E0F4E205A4838CE669F1642785ECEFFB11F62BAA6820B84BDE29ADD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
12
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1524 | test.dat | 185.86.180.36:1688 | kms.digiboy.ir | Sindad Netwok Technology Ltd. | IR | unknown |
1524 | test.dat | 162.223.90.90:1688 | kms.digiboy.ir | ColoUp | US | unknown |
3332 | test.dat | 14.157.20.2:1688 | xykz.f3322.org | No.31,Jin-rong Street | CN | unknown |
1840 | test.dat | 185.86.180.36:1688 | kms.digiboy.ir | Sindad Netwok Technology Ltd. | IR | unknown |
1840 | test.dat | 162.223.90.90:1688 | kms.digiboy.ir | ColoUp | US | unknown |
2552 | test.dat | 14.157.20.2:1688 | xykz.f3322.org | No.31,Jin-rong Street | CN | unknown |
1028 | test.dat | 120.25.106.13:1688 | kms.lotro.cc | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kms.digiboy.ir |
| unknown |
dns.msftncsi.com |
| shared |
hq1.chinancce.com |
| unknown |
xykz.f3322.org |
| unknown |
kms.lotro.cc |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |