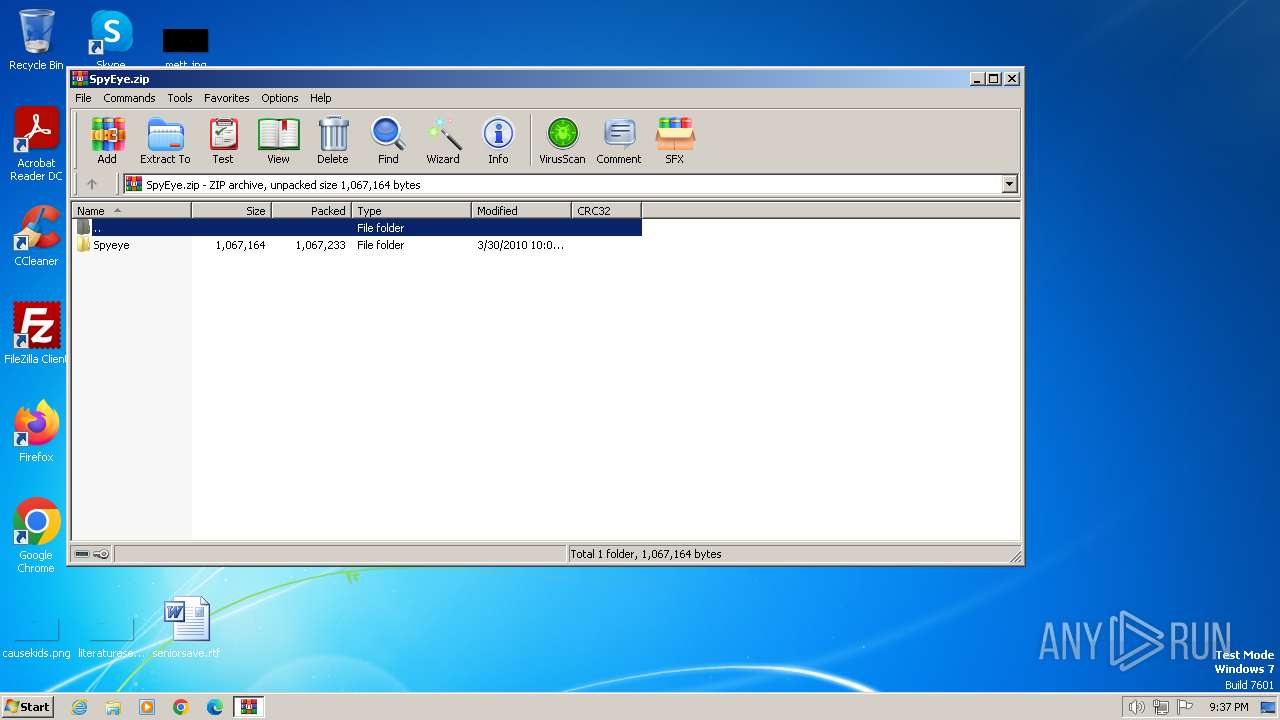
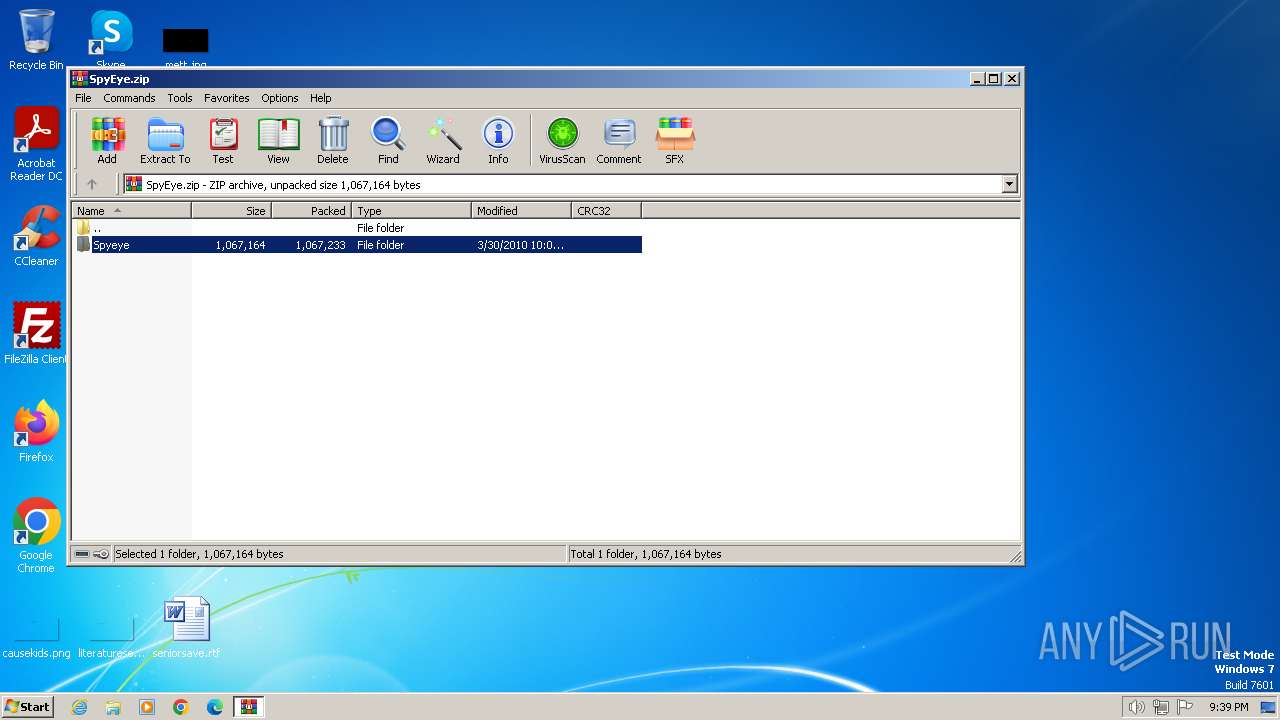
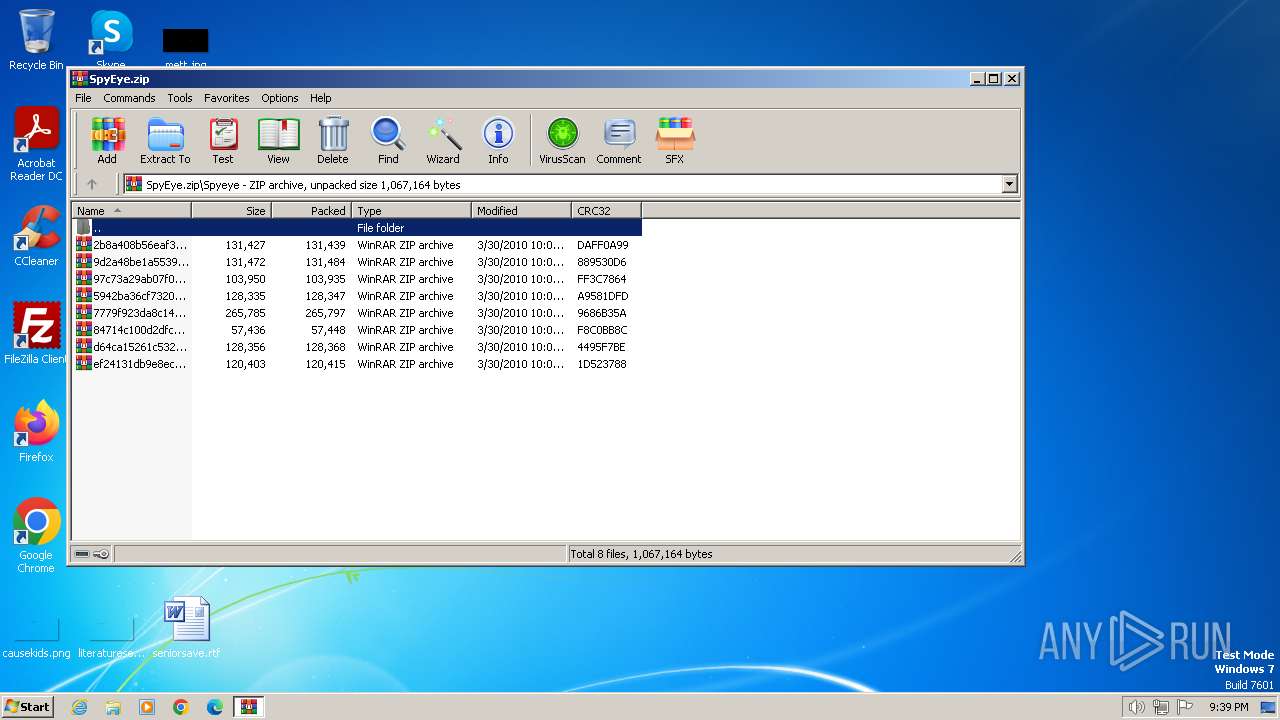
| File name: | SpyEye.zip |
| Full analysis: | https://app.any.run/tasks/8d1bea9e-7ba4-40fb-8866-d46d80b8fc91 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2024, 20:37:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2E0BB844572DE2E88CBD23D76101BD16 |
| SHA1: | 8152E5A5187413EE20B36F4F059C47D594590A3C |
| SHA256: | FA3B854F0E4C0D35CA9A5647BC6935EE1E6A3920D9B951C51B2CB7BC1588C904 |
| SSDEEP: | 49152:3+2ArNe+6ESSXXK9tR2V9h0RTn51GafS4/lixHa6g07DsBBTPvy5/5OaCiHeZu0x:O2ggGXX4tRAh0RT5Hp8a6/7DsBBTHyip |
MALICIOUS
Runs injected code in another process
- malware.exe (PID: 1808)
- cleansweep.exe (PID: 3612)
Application was injected by another process
- taskeng.exe (PID: 300)
- explorer.exe (PID: 1164)
Actions looks like stealing of personal data
- cleansweep.exe (PID: 3612)
Steals credentials from Web Browsers
- cleansweep.exe (PID: 3612)
Changes the autorun value in the registry
- explorer.exe (PID: 1164)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 668)
- WinRAR.exe (PID: 3604)
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 696)
- WinRAR.exe (PID: 1308)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 668)
- WinRAR.exe (PID: 696)
- WinRAR.exe (PID: 1308)
The process checks if it is being run in the virtual environment
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 1308)
- WinRAR.exe (PID: 696)
Application launched itself
- WinRAR.exe (PID: 668)
- WinRAR.exe (PID: 3604)
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 696)
Starts a Microsoft application from unusual location
- malware.exe (PID: 2556)
- malware.exe (PID: 1428)
- malware.exe (PID: 1852)
- malware.exe (PID: 1864)
The process executes via Task Scheduler
- cleansweep.exe (PID: 3612)
Reads the Internet Settings
- cleansweep.exe (PID: 3612)
Creates file in the systems drive root
- taskeng.exe (PID: 300)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2740)
- WinRAR.exe (PID: 696)
- WinRAR.exe (PID: 1308)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 668)
- WinRAR.exe (PID: 3604)
- WinRAR.exe (PID: 696)
- WinRAR.exe (PID: 2740)
- taskeng.exe (PID: 300)
- WinRAR.exe (PID: 1308)
Checks supported languages
- malware.exe (PID: 1428)
- malware.exe (PID: 2556)
- cleansweep.exe (PID: 3612)
- malware.exe (PID: 1852)
- malware.exe (PID: 1864)
- malware.exe (PID: 1808)
Reads the computer name
- cleansweep.exe (PID: 3612)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Checks proxy server information
- explorer.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2010:03:30 22:05:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Spyeye/ |
Total processes
45
Monitored processes
13
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | taskeng.exe {CE1452CD-5E82-4DCD-B0CC-498574D17563} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\SpyEye.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 696 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb3604.40489\ef24131db9e8ec83e551c0a8ba2b2f56.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1308 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb696.44806\84714c100d2dfc88629531f6456b8276.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1428 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.31848\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.31848\malware.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa696.41702\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa696.41702\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1852 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1308.45472\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1308.45472\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
| 1864 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1308.45869\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1308.45869\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
| 2556 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.30089\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.30089\malware.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
Total events
20 183
Read events
19 976
Write events
198
Delete events
9
Modification events
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SpyEye.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
3
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.30089\malware.ex~ | executable | |
MD5:2B8A408B56EAF3CE0198C9D1D8A75EC0 | SHA256:966BA7601BECFFB361A55F02D02FC129903D19BE45E793946361383106F521DA | |||
| 2740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.31848\malware.ex~ | executable | |
MD5:2B8A408B56EAF3CE0198C9D1D8A75EC0 | SHA256:966BA7601BECFFB361A55F02D02FC129903D19BE45E793946361383106F521DA | |||
| 668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb668.28088\2b8a408b56eaf3ce0198c9d1d8a75ec0.zip | compressed | |
MD5:46AFF61C6E52847E67B4247BDD6AED72 | SHA256:F21428B9856F55A5B582A1D248A200AC5D110599C2295CC0B88C4B741A2C20D3 | |||
| 300 | taskeng.exe | C:\cleansweep.exe\config.bin | mp3 | |
MD5:17F88B1ED8EA8B35248FF700FC98F85F | SHA256:B980B80B2ED8026C80C8D432D082CE0802043E69BFEA7E79C4570ACD19CF2132 | |||
| 696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb696.44806\84714c100d2dfc88629531f6456b8276.zip | compressed | |
MD5:025B3F8DAEE3729A8D4D2D130C82CF11 | SHA256:EFB13BEBBC32CD6A1612265FF00E505F19924C4D1E7203D084374C34FDDA5F93 | |||
| 2740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.30089\malware.exe | executable | |
MD5:15F994B0886F7D7C547E24859B991C33 | SHA256:DF192E9020C411A26BF28D47B4EB859F5E375013EF250E46B86A930AE67D6BAE | |||
| 2740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.31848\malware.exe | executable | |
MD5:15F994B0886F7D7C547E24859B991C33 | SHA256:DF192E9020C411A26BF28D47B4EB859F5E375013EF250E46B86A930AE67D6BAE | |||
| 3604 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3604.40489\ef24131db9e8ec83e551c0a8ba2b2f56.zip | compressed | |
MD5:DD31B1FAC48EEE5127089D2A9A9C0074 | SHA256:1DB1FEE9BB8672E0A02FBD18F084D9C4FB2C5213B61A4580B173A03AA5D07E9B | |||
| 2740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2740.33031\malware.ex~ | executable | |
MD5:2B8A408B56EAF3CE0198C9D1D8A75EC0 | SHA256:966BA7601BECFFB361A55F02D02FC129903D19BE45E793946361383106F521DA | |||
| 1308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1308.45472\malware.exe | executable | |
MD5:84714C100D2DFC88629531F6456B8276 | SHA256:861AA9C5DDCB5284E1BA4E5D7EBACFA297567C353446506EE4B4E39C84454B09 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1164 | explorer.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
276 | taskhost.exe | 208.109.219.106:58 | — | AS-26496-GO-DADDY-COM-LLC | US | unknown |
1164 | explorer.exe | 49.13.77.253:80 | romanticdateonline.com | Hetzner Online GmbH | DE | unknown |
1164 | explorer.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
romanticdateonline.com |
| unknown |
dns.msftncsi.com |
| shared |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | explorer.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User Agent (Microsoft Internet Explorer) |
Process | Message |
|---|---|
malware.exe | *Dropper* : BOT_VERSION = 10060, PID = 2556, szModuleFileName = "C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.30089\malware.exe" |
malware.exe | *Dropper* : BOT_VERSION = 10060, PID = 1428, szModuleFileName = "C:\Users\admin\AppData\Local\Temp\Rar$EXa2740.31848\malware.exe" |