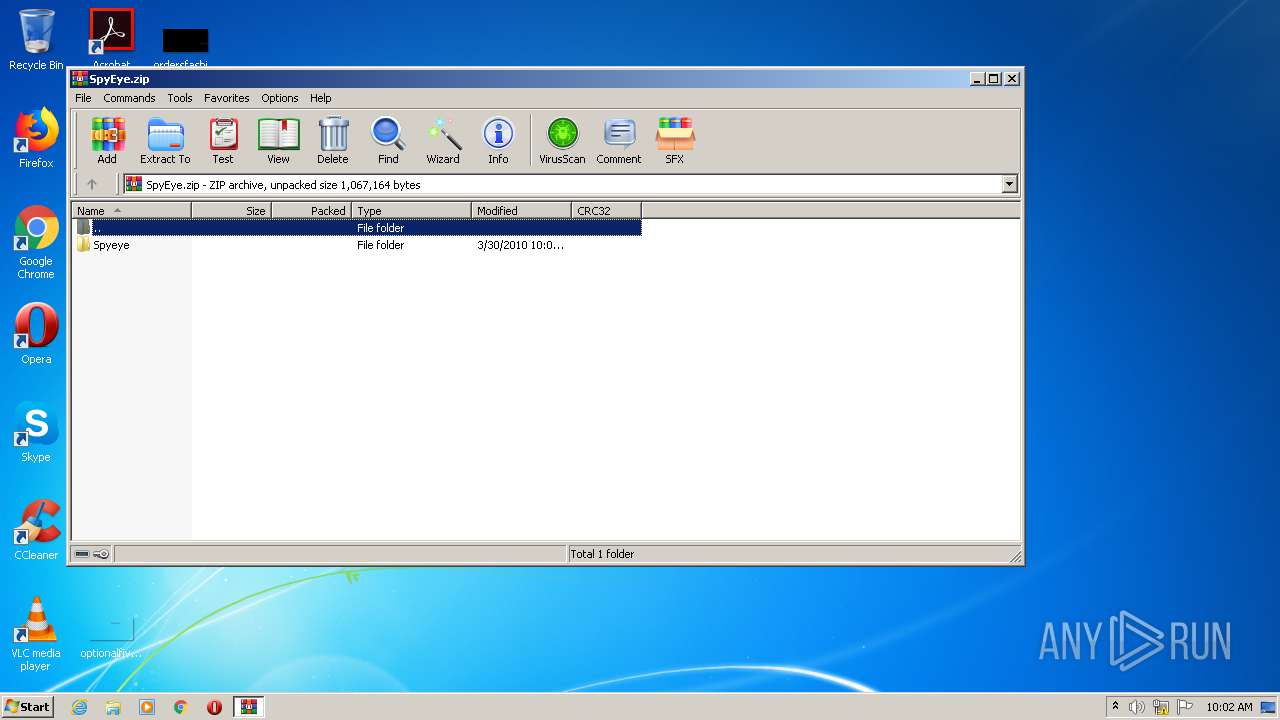
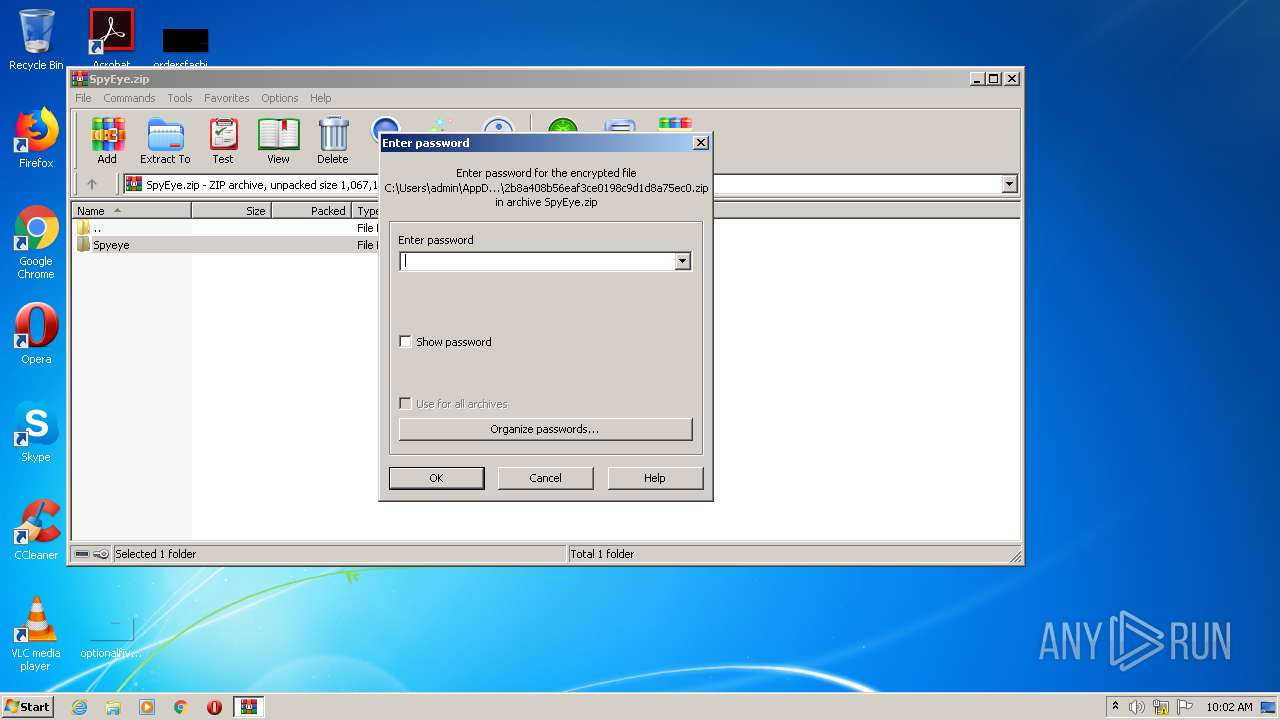
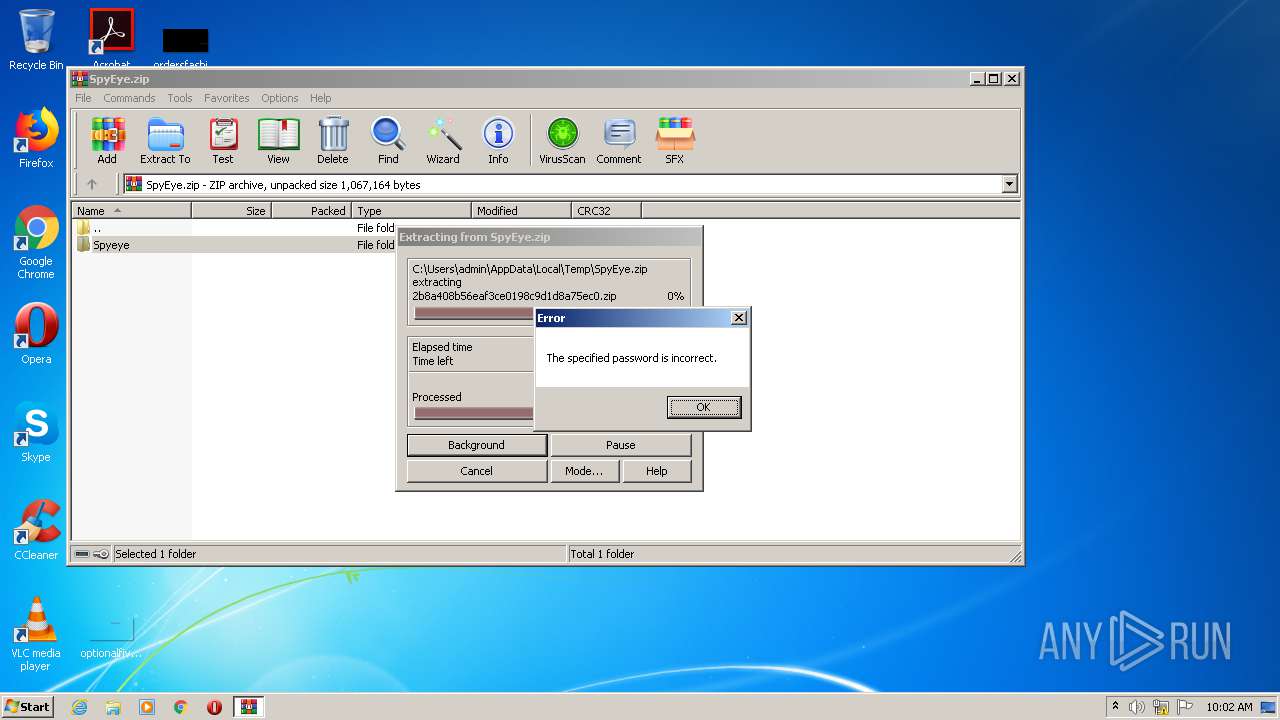
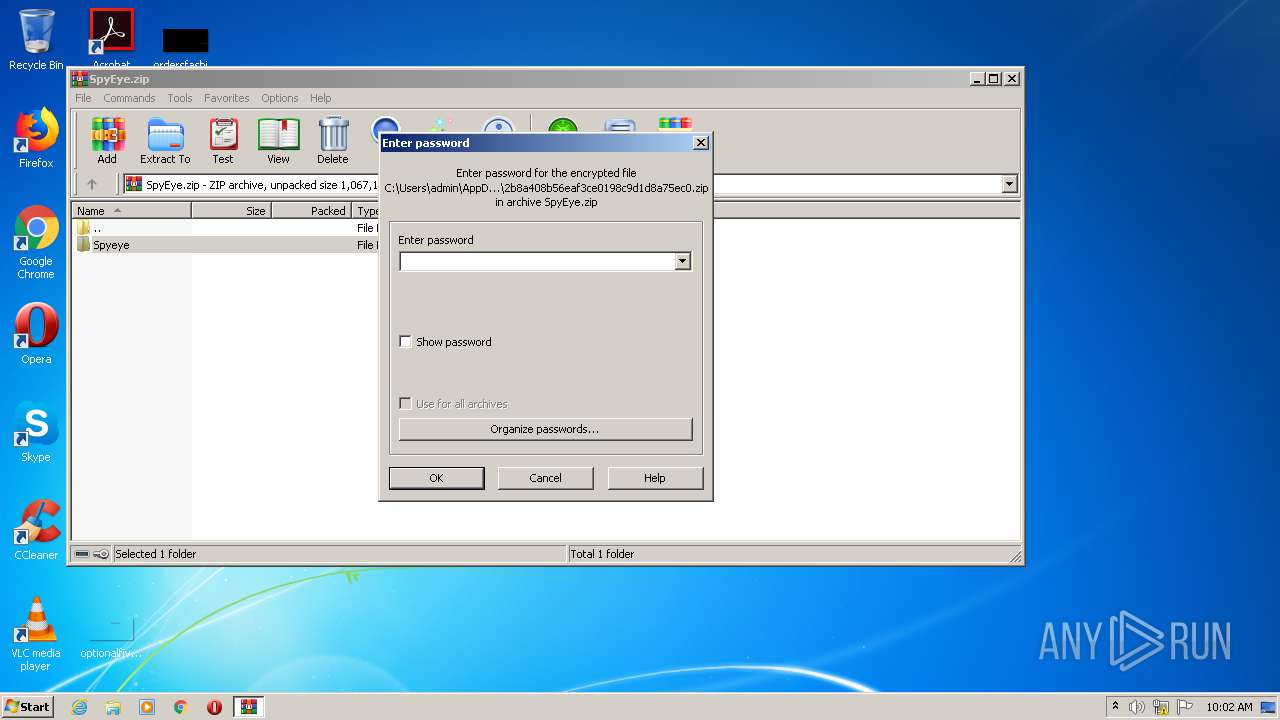
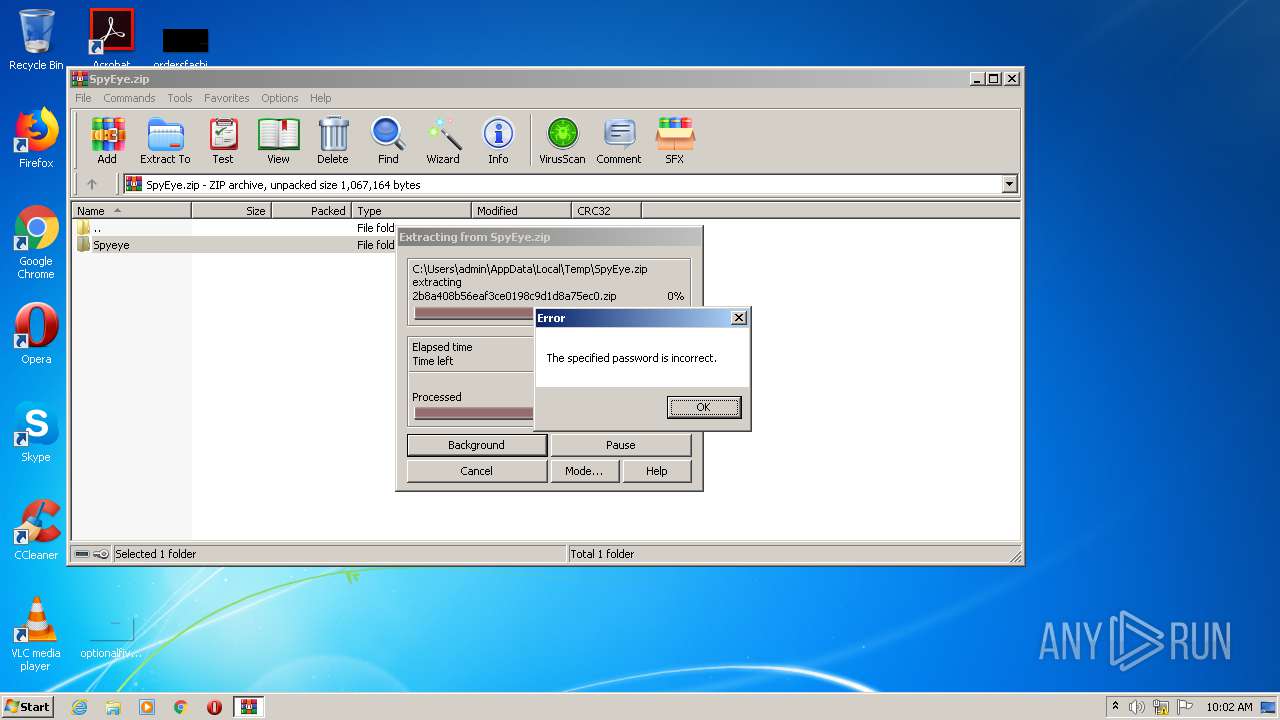
| download: | SpyEye.zip |
| Full analysis: | https://app.any.run/tasks/2dfe65e3-dc76-456c-9e28-05829f90f2cf |
| Verdict: | Malicious activity |
| Analysis date: | October 16, 2020, 09:02:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 2E0BB844572DE2E88CBD23D76101BD16 |
| SHA1: | 8152E5A5187413EE20B36F4F059C47D594590A3C |
| SHA256: | FA3B854F0E4C0D35CA9A5647BC6935EE1E6A3920D9B951C51B2CB7BC1588C904 |
| SSDEEP: | 24576:xx83QwgESJLldWfsqI4/rWhZPG44yuJoy7SHoIO1:IAwg7+sqI4/OZ/To7iox1 |
MALICIOUS
Application was dropped or rewritten from another process
- malware.exe (PID: 984)
- malware.exe (PID: 3328)
- malware.exe (PID: 3880)
- malware.exe (PID: 1948)
- malware.exe (PID: 3312)
- malware.exe (PID: 3032)
- malware.exe (PID: 3044)
- malware.exe (PID: 3320)
- malware.exe (PID: 1836)
- malware.exe (PID: 3348)
- malware.exe (PID: 1500)
- cleansweep.exe (PID: 2088)
Changes the autorun value in the registry
- explorer.exe (PID: 392)
Application was injected by another process
- dwm.exe (PID: 128)
- ctfmon.exe (PID: 688)
- taskeng.exe (PID: 1996)
- explorer.exe (PID: 392)
- taskhost.exe (PID: 1980)
Runs injected code in another process
- explorer.exe (PID: 392)
- cleansweep.exe (PID: 2088)
SUSPICIOUS
Reads Internet Cache Settings
- taskhost.exe (PID: 1980)
- explorer.exe (PID: 392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4092)
- malware.exe (PID: 3880)
- WinRAR.exe (PID: 2604)
- WinRAR.exe (PID: 2820)
- WinRAR.exe (PID: 4004)
- WinRAR.exe (PID: 3676)
- WinRAR.exe (PID: 2516)
Creates files in the user directory
- explorer.exe (PID: 392)
INFO
Manual execution by user
- WinRAR.exe (PID: 3196)
- malware.exe (PID: 3328)
- malware.exe (PID: 984)
- WinRAR.exe (PID: 4092)
- WinRAR.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2010:03:30 22:05:25 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Spyeye/ |
Total processes
69
Monitored processes
26
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 688 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 984 | "C:\Users\admin\Desktop\malware.exe" | C:\Users\admin\Desktop\malware.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
| 1500 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2516.47485\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2516.47485\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2516.47219\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2516.47219\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1948 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2604.41202\malware.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2604.41202\malware.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1980 | "taskhost.exe" | C:\Windows\System32\taskhost.exe | services.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1996 | taskeng.exe {9FFF9F18-B475-4F9C-BA26-08811E66DE84} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2088 | "C:\cleansweep.exe\cleansweep.exe" | C:\cleansweep.exe\cleansweep.exe | — | malware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft CleanSweep Exit code: 0 Version: 1, 1, 3, 14 Modules
| |||||||||||||||
Total events
8 237
Read events
7 739
Write events
487
Delete events
11
Modification events
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SpyEye.zip | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (392) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (392) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
15
Suspicious files
11
Text files
0
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | explorer.exe | C:\Users\admin\Desktop\Spyeye | — | |
MD5:— | SHA256:— | |||
| 3196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3196.33072\malware.exe | — | |
MD5:— | SHA256:— | |||
| 3936 | WinRAR.exe | C:\Users\admin\Desktop\Spyeye\__rzi_3936.37944 | — | |
MD5:— | SHA256:— | |||
| 2452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2452.28469\Spyeye\d64ca15261c53279a7288616b3cb1a92.zip | compressed | |
MD5:DF56431376AEBC88228098ECF2A03BD7 | SHA256:9866A9B24EBBE307D7C14AB08361D44AF22A83C7EA124BAE975CB3B0FFDBC882 | |||
| 2452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2452.28469\Spyeye\7779f923da8c1418764fecc7d1ba86cf.zip | compressed | |
MD5:D5E3F04C2A786F8C1C979B3403733356 | SHA256:4CE9B8B4785483AED81B2FCD8563AF683A8239D7DF2CBE2089A2E95D6C2F0C08 | |||
| 2452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2452.28469\Spyeye\2b8a408b56eaf3ce0198c9d1d8a75ec0.zip | compressed | |
MD5:46AFF61C6E52847E67B4247BDD6AED72 | SHA256:F21428B9856F55A5B582A1D248A200AC5D110599C2295CC0B88C4B741A2C20D3 | |||
| 2452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2452.28469\Spyeye\97c73a29ab07f04458f5e8834f8db1ba.zip | compressed | |
MD5:5C95F9A56FCE2A136C9E010E76984138 | SHA256:21FC957FFA13598B69799AEEB1E0C739D330912151BC6D284A268CFCA83A992D | |||
| 392 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Spyeye.lnk | lnk | |
MD5:— | SHA256:— | |||
| 392 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\2b8a408b56eaf3ce0198c9d1d8a75ec0.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
| 392 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\97c73a29ab07f04458f5e8834f8db1ba.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
3
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | explorer.exe | GET | 200 | 104.75.89.181:80 | http://www.microsoft.com/ | NL | html | 1020 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
392 | explorer.exe | 104.75.89.181:80 | www.microsoft.com | Akamai Technologies, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.secureantibot.net |
| unknown |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
392 | explorer.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User Agent (Microsoft Internet Explorer) |
392 | explorer.exe | A Network Trojan was detected | ET POLICY Microsoft user-agent automated process response to automated request |
Process | Message |
|---|---|
malware.exe | *Dropper* : BOT_VERSION = 10060, PID = 984, szModuleFileName = "C:\Users\admin\Desktop\malware.exe" |
malware.exe | *Dropper* : BOT_VERSION = 10060, PID = 3328, szModuleFileName = "C:\Users\admin\Desktop\malware.exe" |