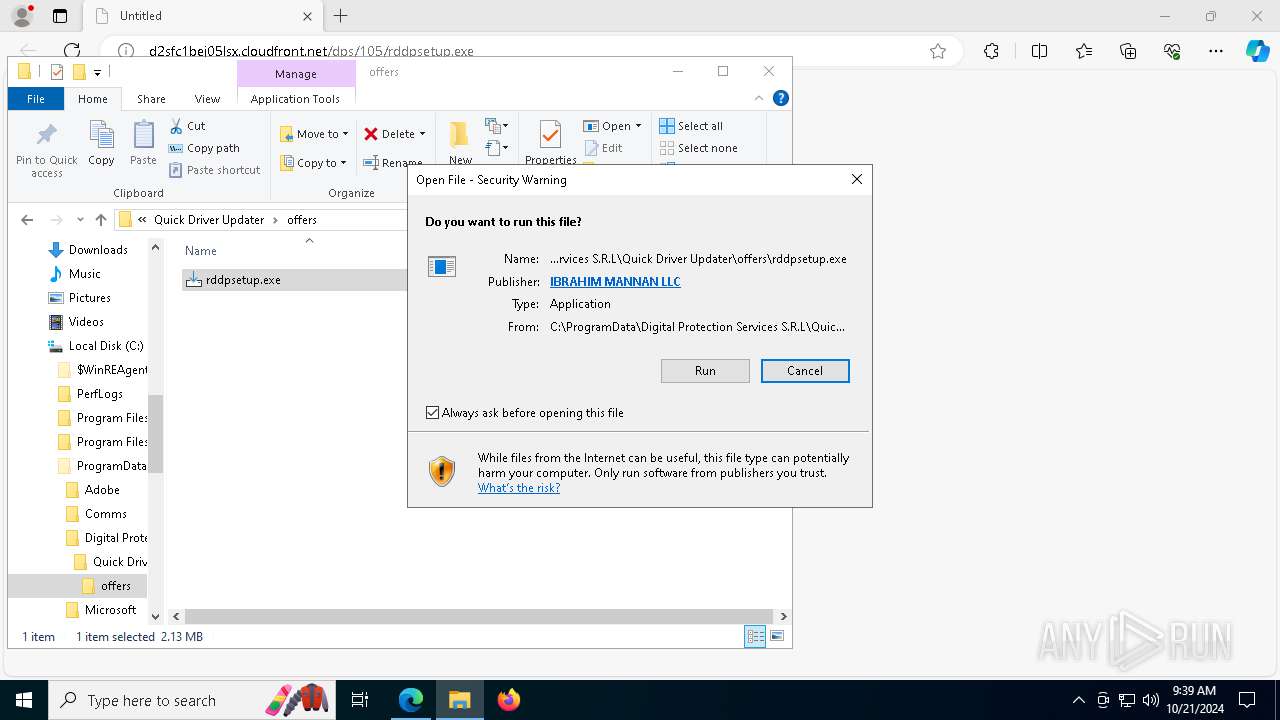
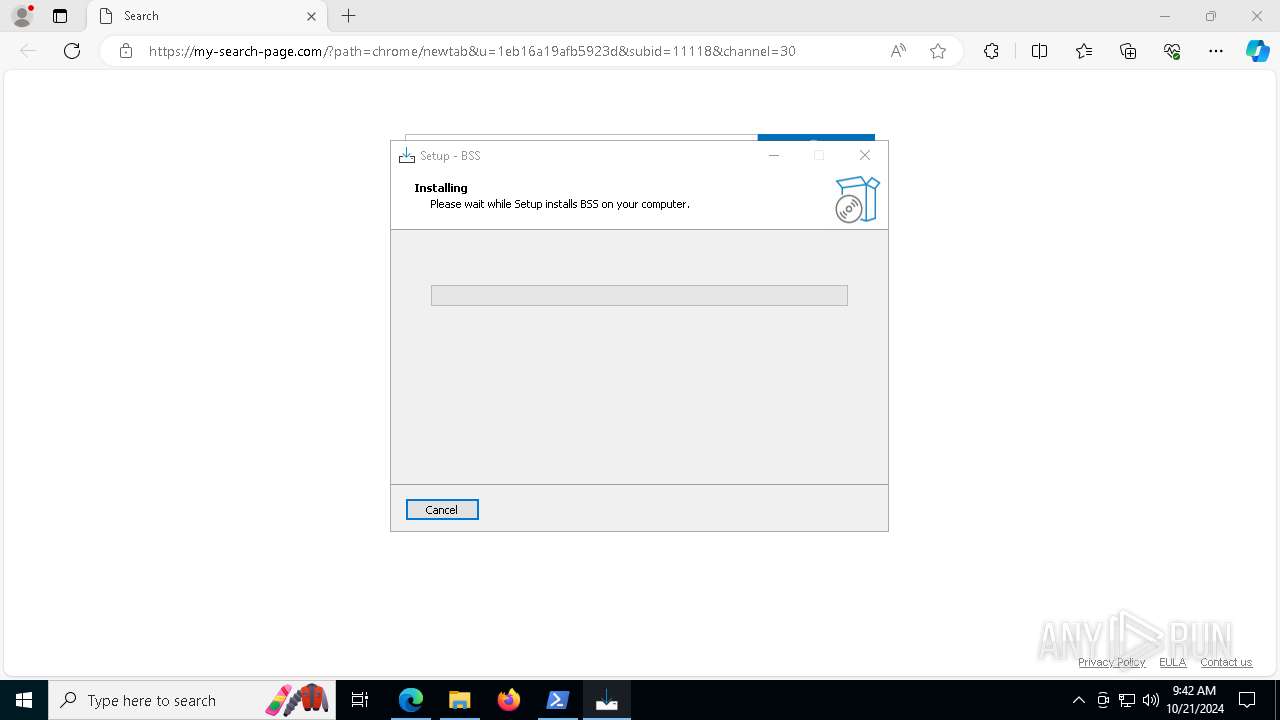
| URL: | d2sfc1bej05lsx.cloudfront.net/dps/105/rddpsetup.exe |
| Full analysis: | https://app.any.run/tasks/6e2e4ed0-78f4-466c-ad54-cc179c6cb2f0 |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2024, 09:37:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
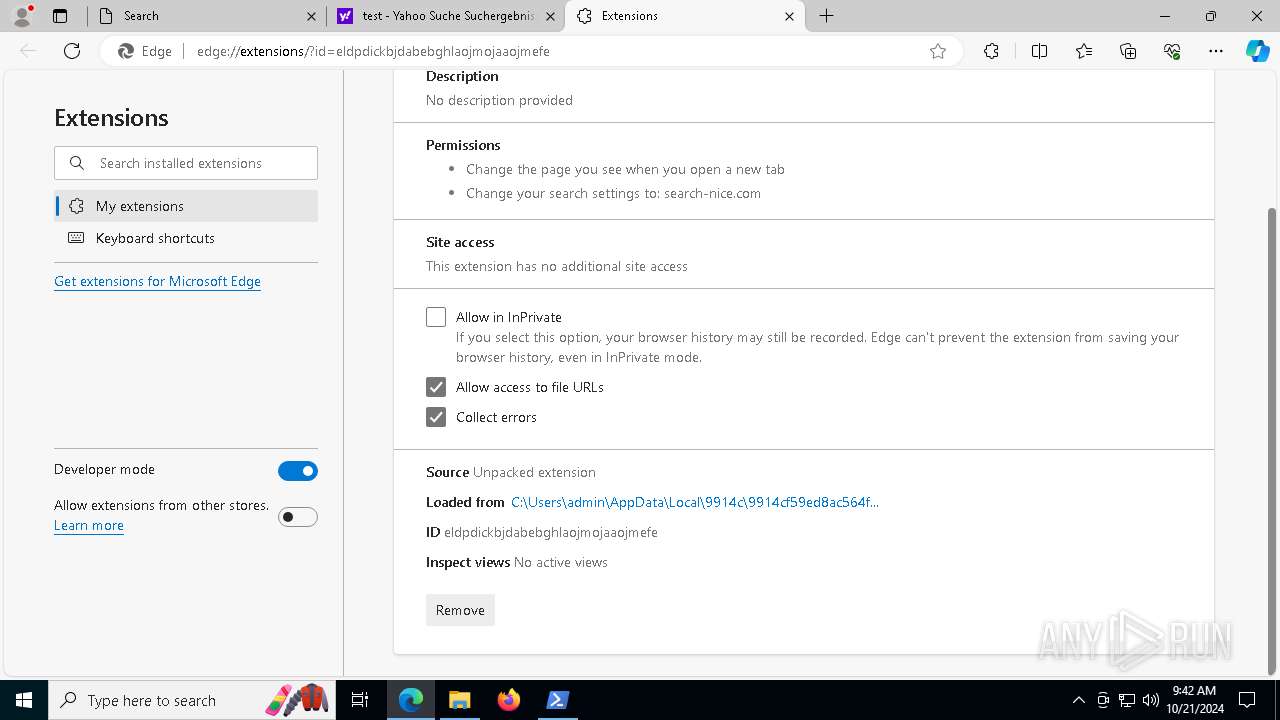
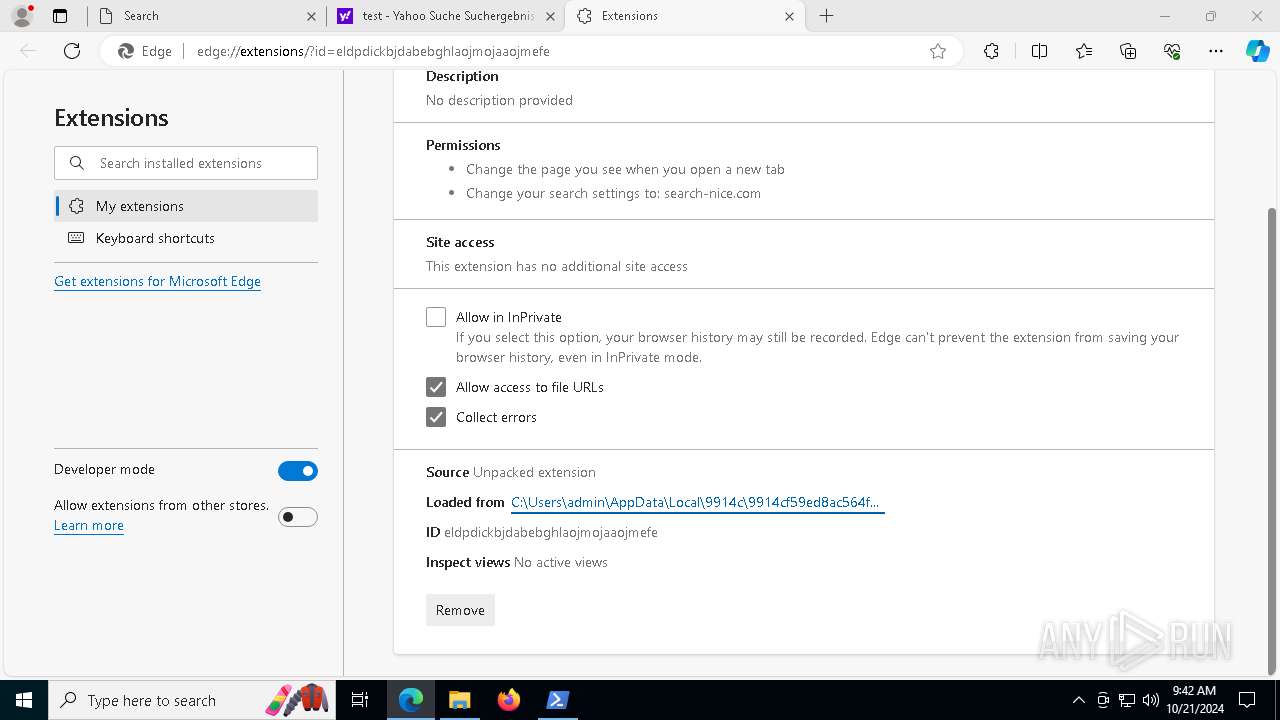
| Tags: | |
| Indicators: | |
| MD5: | BC9BC182B50C1B389DAF73E76ED3A59E |
| SHA1: | BF2E76CEFDFEDD838FFE21572034C1DD63D71811 |
| SHA256: | FA3B6B01DC444E12D5FF06258D975298A9E1E782942E21F3246CACECA6B4FCD7 |
| SSDEEP: | 3:ADkqjJ1+l/0eL7kA:ADkqjJ1n9A |
MALICIOUS
XORed URL has been found (YARA)
- IjvOGQzA.exe (PID: 7500)
SUSPICIOUS
Executable content was dropped or overwritten
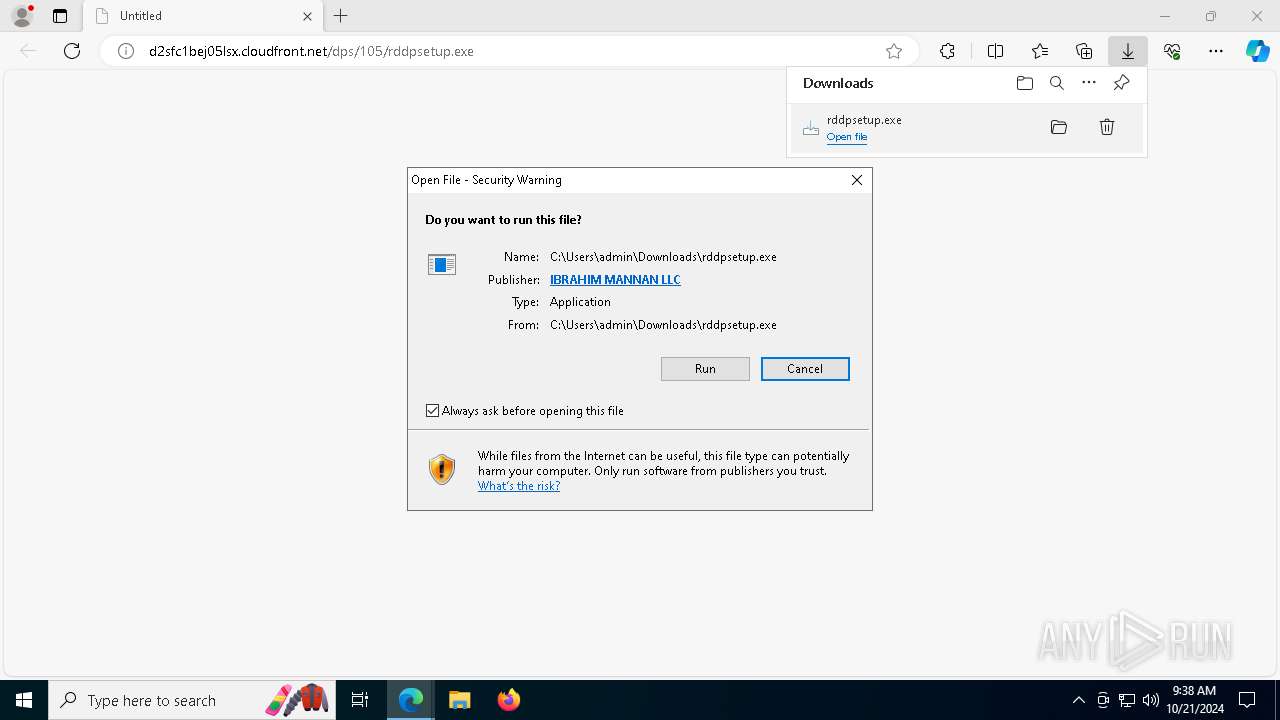
- rddpsetup.exe (PID: 7800)
- rddpsetup.exe (PID: 6176)
- rddpsetup.tmp (PID: 7044)
- rddpsetup.exe (PID: 6852)
- rddpsetup.exe (PID: 7860)
- rddpsetup.tmp (PID: 8188)
- scanner.exe (PID: 2796)
- rddpsetup.exe (PID: 1712)
- rddpsetup.tmp (PID: 7016)
- IjvOGQzA.exe (PID: 7500)
- rddpsetup.exe (PID: 6408)
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
- scanner.exe (PID: 8024)
The executable file from the user directory is run by the CMD process
- scanner.exe (PID: 2796)
- scanner.exe (PID: 4680)
- scanner.exe (PID: 8024)
Starts CMD.EXE for commands execution
- scanner.exe (PID: 2796)
- IjvOGQzA.exe (PID: 7500)
- scanner.exe (PID: 8024)
- 125621226710721 (PID: 7584)
- rddpsetup.tmp (PID: 7016)
Hides command output
- cmd.exe (PID: 6360)
- cmd.exe (PID: 616)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7816)
- cmd.exe (PID: 7780)
The process drops C-runtime libraries
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
Application launched itself
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
Starts application with an unusual extension
- 125621226710721 (PID: 6384)
- powershell.exe (PID: 7780)
- 125621226710721 (PID: 7092)
- powershell.exe (PID: 3568)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 616)
- cmd.exe (PID: 6360)
- 125621226710721 (PID: 7584)
Powershell scripting: start process
- cmd.exe (PID: 6360)
- cmd.exe (PID: 616)
Process drops python dynamic module
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
Process drops legitimate windows executable
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6356)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 3432)
Uses WMIC.EXE
- cmd.exe (PID: 6152)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 7452)
- cmd.exe (PID: 6392)
Executing commands from a ".bat" file
- rddpsetup.tmp (PID: 7016)
INFO
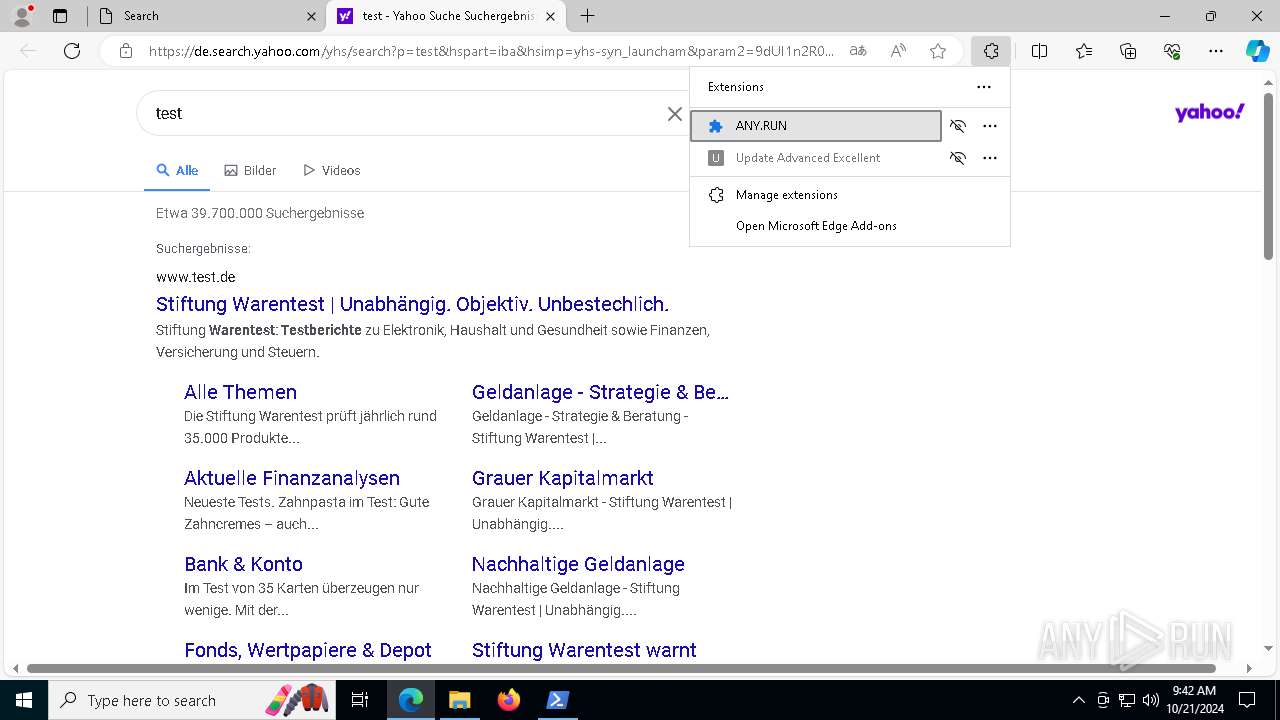
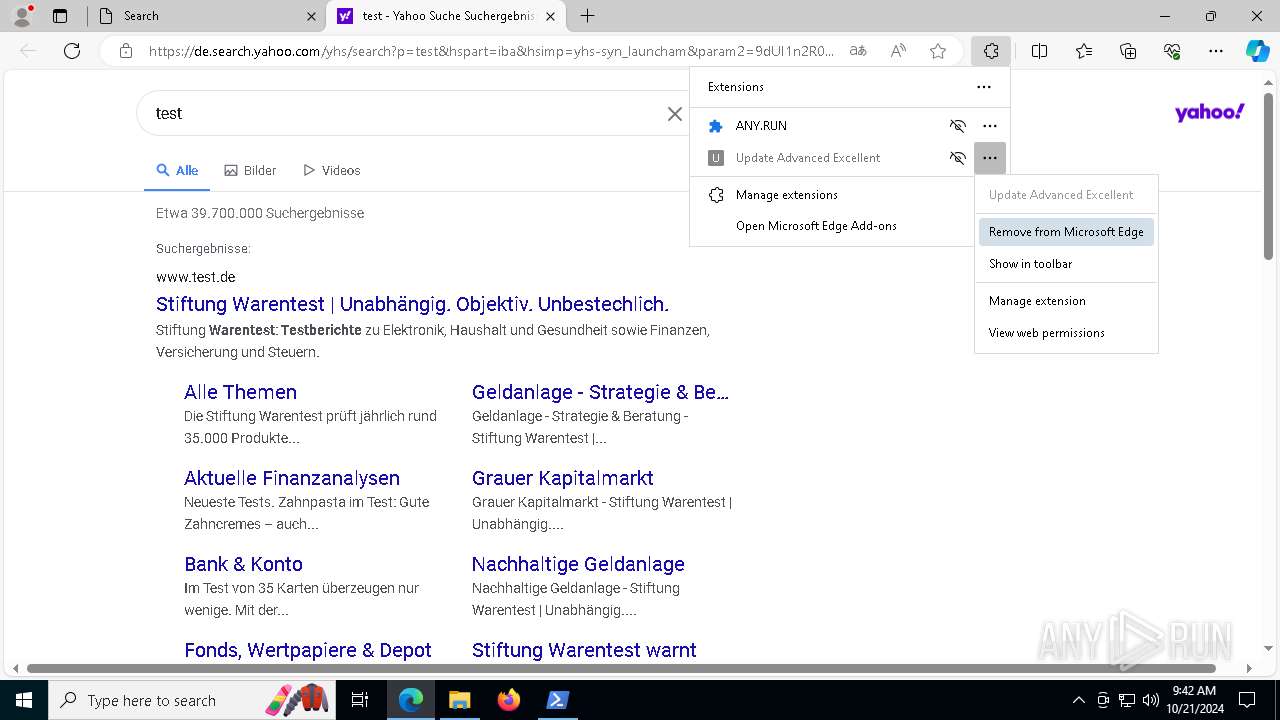
Executable content was dropped or overwritten
- msedge.exe (PID: 5900)
- msedge.exe (PID: 5744)
- msedge.exe (PID: 2124)
Manual execution by a user
- rddpsetup.exe (PID: 6852)
- powershell.exe (PID: 8112)
- msedge.exe (PID: 7200)
The executable file from the user directory is run by the Powershell process
- 125621226710721 (PID: 6384)
- 125621226710721 (PID: 7092)
Application launched itself
- msedge.exe (PID: 5744)
- msedge.exe (PID: 7452)
- msedge.exe (PID: 7200)
- msedge.exe (PID: 3432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7500) IjvOGQzA.exe
Decrypted-URLs (5)http://strowbers.com
https://d1zc3t1odiexza.cloudfront.net/wincap?pxl=
https://delayed-operation.com/scanner.zip
https://delaying-operations.com/scanner.zip
https://dkh3jvcovbitg.cloudfront.net/wincap?macid=
Total processes
310
Monitored processes
166
Malicious processes
11
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "Start-Process -FilePath \"C:\Users\admin\AppData\Local\Temp\125621226710721\" -NoNewWindow -ArgumentList '--s17421926','--ch=d17ef3fb50f78d9a7c2bbc4b4bed160a0167e848','-a','--channel=30' | Wait-Process" 2>nul | C:\Windows\SysWOW64\cmd.exe | — | scanner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5800 --field-trial-handle=2364,i,4950635557980858504,10731496168185357567,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 616 | timeout /t 30 | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 884 | timeout 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 884 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5856 --field-trial-handle=2364,i,4950635557980858504,10731496168185357567,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=6224 --field-trial-handle=2376,i,14027215165886512118,1681531530944894542,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2576 --field-trial-handle=2396,i,16492664174546116099,6133931276256618942,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3216 --field-trial-handle=2244,i,17956282040936468120,17676323260710230684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2648 --field-trial-handle=2244,i,17956282040936468120,17676323260710230684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 15 Version: 122.0.2365.59 | |||||||||||||||
| 1332 | wmic datafile where name="C:\\Program Files\\Mozilla Firefox\\firefox.exe" get Version /value | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
20 937
Read events
20 906
Write events
29
Delete events
2
Modification events
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9ED6F3B08F832F00 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 234C0EB18F832F00 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524818 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9A051C5D-968D-4011-AFDC-ED0A35A63F82} | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 51292BB18F832F00 | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (5744) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
136
Suspicious files
572
Text files
314
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8b510.TMP | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8b510.TMP | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8b510.TMP | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8b520.TMP | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8b520.TMP | — | |
MD5:— | SHA256:— | |||
| 5744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
135
DNS requests
128
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5744 | msedge.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDASfYPg36w3tUzElYg%3D%3D | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6960 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5912 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1729772801&P2=404&P3=2&P4=KkD1wTV2WXf85YCceMXmk9Mb5hb7Z7Mj5tS0WILRhyaG%2fkknyQC20GPFcQ7VdtvmJ2YgYIR3qvcxgwcAzOOX6A%3d%3d | unknown | — | — | whitelisted |
5912 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1729772801&P2=404&P3=2&P4=KkD1wTV2WXf85YCceMXmk9Mb5hb7Z7Mj5tS0WILRhyaG%2fkknyQC20GPFcQ7VdtvmJ2YgYIR3qvcxgwcAzOOX6A%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 184.86.251.16:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5744 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
d2sfc1bej05lsx.cloudfront.net |
| whitelisted |