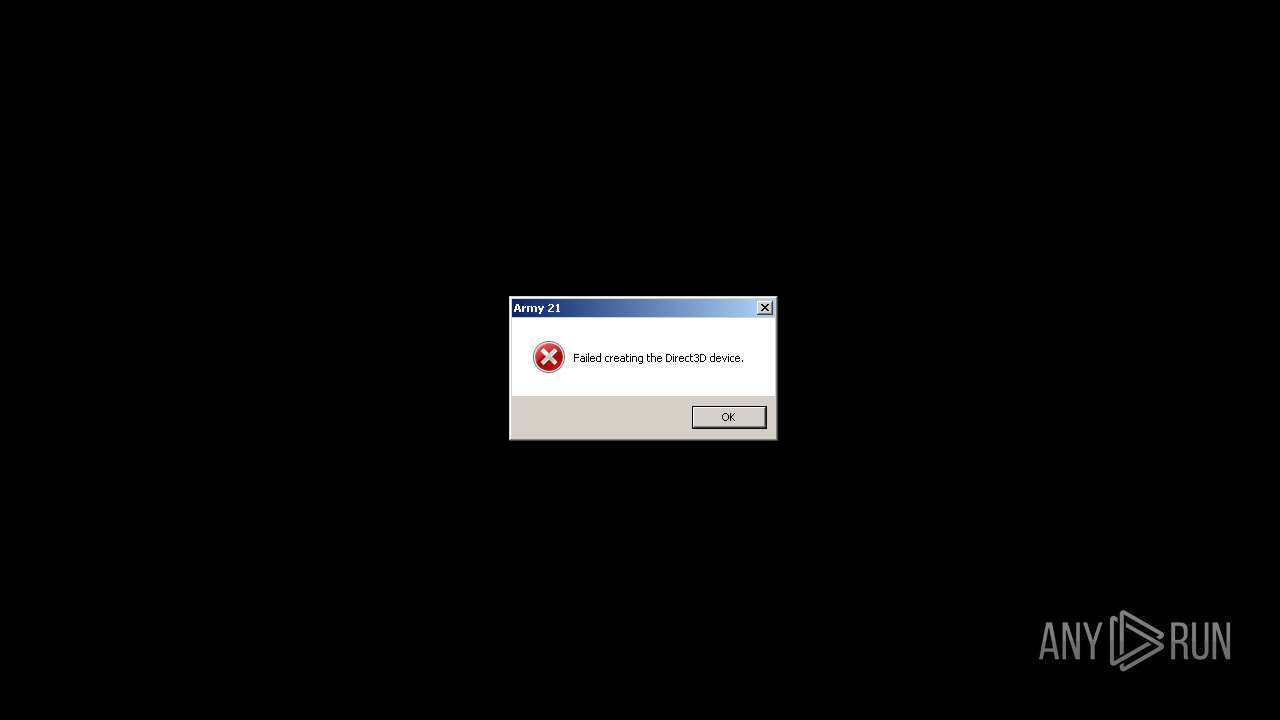
| File name: | army21setup.exe |
| Full analysis: | https://app.any.run/tasks/0cb6f466-567e-44db-8506-206ebb36b634 |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2024, 23:56:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 728AB5561AC358893496145AC5403EEF |
| SHA1: | 503E98DD253CC4BD47840B8C5683B26C7F2A1352 |
| SHA256: | FA3B25BCCB14A4B5A796E1DF8934E4D473D9674D2719D0F4934EEBF903A6063C |
| SSDEEP: | 98304:FpHonq0vlMVyBiyyRb+/tvkv4Sr6ZNOoZw7ue8UZaJD2s9ZtbTO5HlpbsBY3V8fB:udNvWOiHGt+fOb50dniEa |
MALICIOUS
Drops the executable file immediately after the start
- army21setup.exe (PID: 2120)
- army21setup.exe (PID: 2208)
- army21setup.tmp (PID: 2672)
SUSPICIOUS
Executable content was dropped or overwritten
- army21setup.exe (PID: 2120)
- army21setup.exe (PID: 2208)
- army21setup.tmp (PID: 2672)
Process drops legitimate windows executable
- army21setup.tmp (PID: 2672)
Non-standard symbols in registry
- army21setup.tmp (PID: 2672)
Reads the Windows owner or organization settings
- army21setup.tmp (PID: 2672)
The process drops C-runtime libraries
- army21setup.tmp (PID: 2672)
INFO
Create files in a temporary directory
- army21setup.exe (PID: 2120)
- army21setup.exe (PID: 2208)
- army21setup.tmp (PID: 2672)
Checks supported languages
- army21setup.exe (PID: 2120)
- army21setup.tmp (PID: 3956)
- army21setup.exe (PID: 2208)
- army21setup.tmp (PID: 2672)
- army21_cr.exe (PID: 696)
- army21_cr.exe (PID: 2484)
Reads the computer name
- army21setup.tmp (PID: 3956)
- army21_cr.exe (PID: 696)
- army21setup.tmp (PID: 2672)
- army21_cr.exe (PID: 2484)
Manual execution by a user
- army21_cr.exe (PID: 2484)
Creates files or folders in the user directory
- army21_cr.exe (PID: 2484)
- army21setup.tmp (PID: 2672)
- army21_cr.exe (PID: 696)
Creates a software uninstall entry
- army21setup.tmp (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:10:13 08:19:32+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 65024 |
| InitializedDataSize: | 53248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x113bc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Indiegama Pte Ltd |
| FileDescription: | Army 21 Setup |
| FileVersion: | 1.0 |
| LegalCopyright: | Copyright © 2015, Indiegama Pte Ltd |
| ProductName: | Army 21 |
| ProductVersion: | 1.0 |
Total processes
48
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Users\admin\AppData\Roaming\Army 21\army21_cr.exe" | C:\Users\admin\AppData\Roaming\Army 21\army21_cr.exe | army21setup.tmp | ||||||||||||
User: admin Company: Indiegama Pte Ltd Integrity Level: HIGH Description: Army 21 client Exit code: 3221225547 Version: 0, 0, 0, 0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\army21setup.exe" | C:\Users\admin\AppData\Local\Temp\army21setup.exe | explorer.exe | ||||||||||||
User: admin Company: Indiegama Pte Ltd Integrity Level: MEDIUM Description: Army 21 Setup Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\army21setup.exe" /SPAWNWND=$18013E /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\army21setup.exe | army21setup.tmp | ||||||||||||
User: admin Company: Indiegama Pte Ltd Integrity Level: HIGH Description: Army 21 Setup Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\AppData\Roaming\Army 21\army21_cr.exe" | C:\Users\admin\AppData\Roaming\Army 21\army21_cr.exe | explorer.exe | ||||||||||||
User: admin Company: Indiegama Pte Ltd Integrity Level: HIGH Description: Army 21 client Version: 0, 0, 0, 0 Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\is-D64TC.tmp\army21setup.tmp" /SL5="$100130,6007564,119296,C:\Users\admin\AppData\Local\Temp\army21setup.exe" /SPAWNWND=$18013E /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\is-D64TC.tmp\army21setup.tmp | army21setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Local\Temp\is-27FAJ.tmp\army21setup.tmp" /SL5="$E0170,6007564,119296,C:\Users\admin\AppData\Local\Temp\army21setup.exe" | C:\Users\admin\AppData\Local\Temp\is-27FAJ.tmp\army21setup.tmp | — | army21setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
6 285
Read events
6 252
Write events
27
Delete events
6
Modification events
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 700A000048C46BFD348DDA01 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: DCBD070DD91A48BDBF3A670DC5873FAC83E44FBB93632D4C7DE194377A90AA56 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Roaming\Army 21\msvcp120.dll | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: D466F2CDCF48A66EF95B4568BDCF647BF75662D05D4B245E27783A22419C5CC9 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Army 21_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.4 (u) | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Army 21_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\Army 21 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Army 21_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\Army 21\ | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Army 21_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Army 21 | |||
| (PID) Process: | (2672) army21setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Army 21_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
15
Suspicious files
4
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | army21setup.exe | C:\Users\admin\AppData\Local\Temp\is-27FAJ.tmp\army21setup.tmp | executable | |
MD5:— | SHA256:— | |||
| 2208 | army21setup.exe | C:\Users\admin\AppData\Local\Temp\is-D64TC.tmp\army21setup.tmp | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Local\Temp\is-A4V6F.tmp\_isetup\_shfoldr.dll | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\is-NGG67.tmp | — | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\is-8EQ5B.tmp | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\msvcp120.dll | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\is-T5T26.tmp | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\msvcr120.dll | executable | |
MD5:— | SHA256:— | |||
| 2672 | army21setup.tmp | C:\Users\admin\AppData\Roaming\Army 21\is-B08OL.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
masterserver.army21.com |
| unknown |
Threats
Process | Message |
|---|---|
army21_cr.exe | Sat Apr 13 00:56:26 2024 CSettingsAccount::Load parse failed: * Line 1, Column 1
Syntax error: value, object or array expected.
|
army21_cr.exe | Sat Apr 13 00:56:38 2024 CSettingsAccount::Load parse failed: * Line 1, Column 1
Syntax error: value, object or array expected.
|