| File name: | 666.rar |
| Full analysis: | https://app.any.run/tasks/7edea4ae-cb9f-45e3-bc51-8bcc0f4292d9 |
| Verdict: | Malicious activity |
| Analysis date: | May 04, 2020, 03:12:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B6BDA7D16BBA279B474F7A22DA313ED9 |
| SHA1: | BDF1AA26068EAA34A92F4B5DD07280255FCD61D0 |
| SHA256: | FA3131E269C2C1F8330015543CFFE0F3DC241DC2DB4D75DA4FE1D68ADAC79CAC |
| SSDEEP: | 98304:s3iE8eGUVlIBLaLvRqhtE/5TtBvL6KjbSj+PAewJ64GVp2zAzK1Z9F7E5TvkO:s0eGUYLaLwqZFi64orG1tE51 |
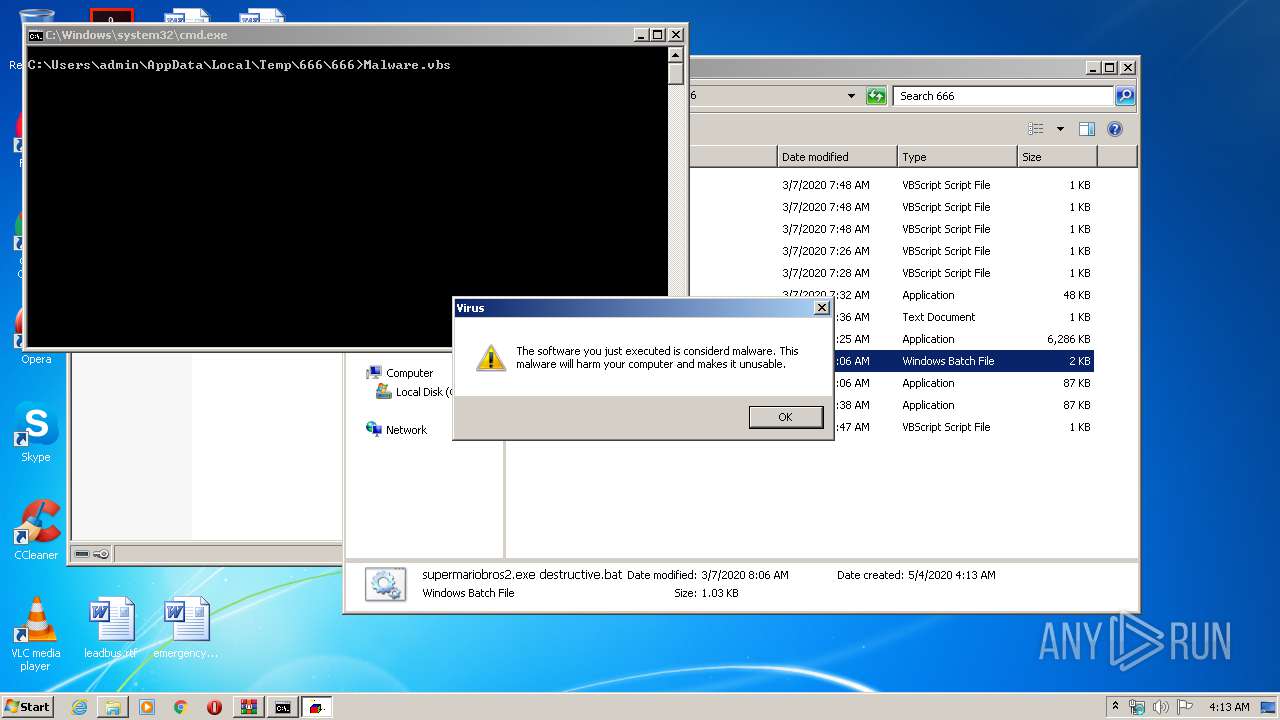
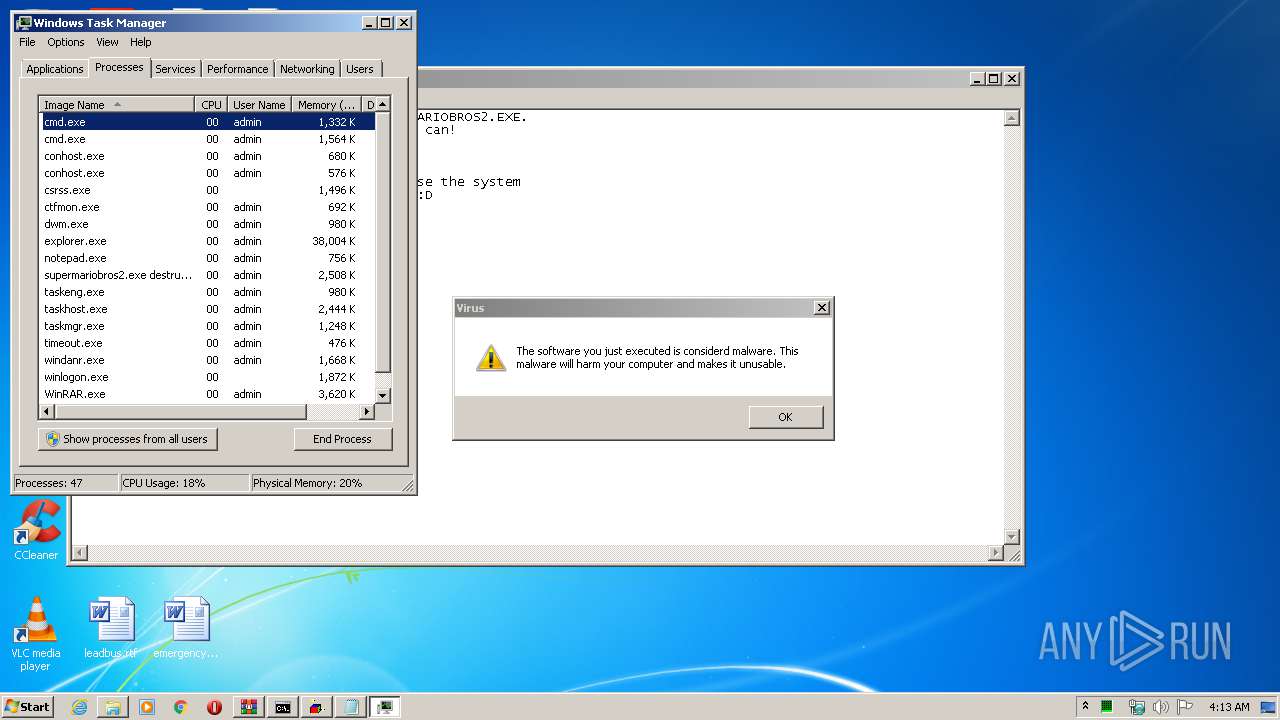
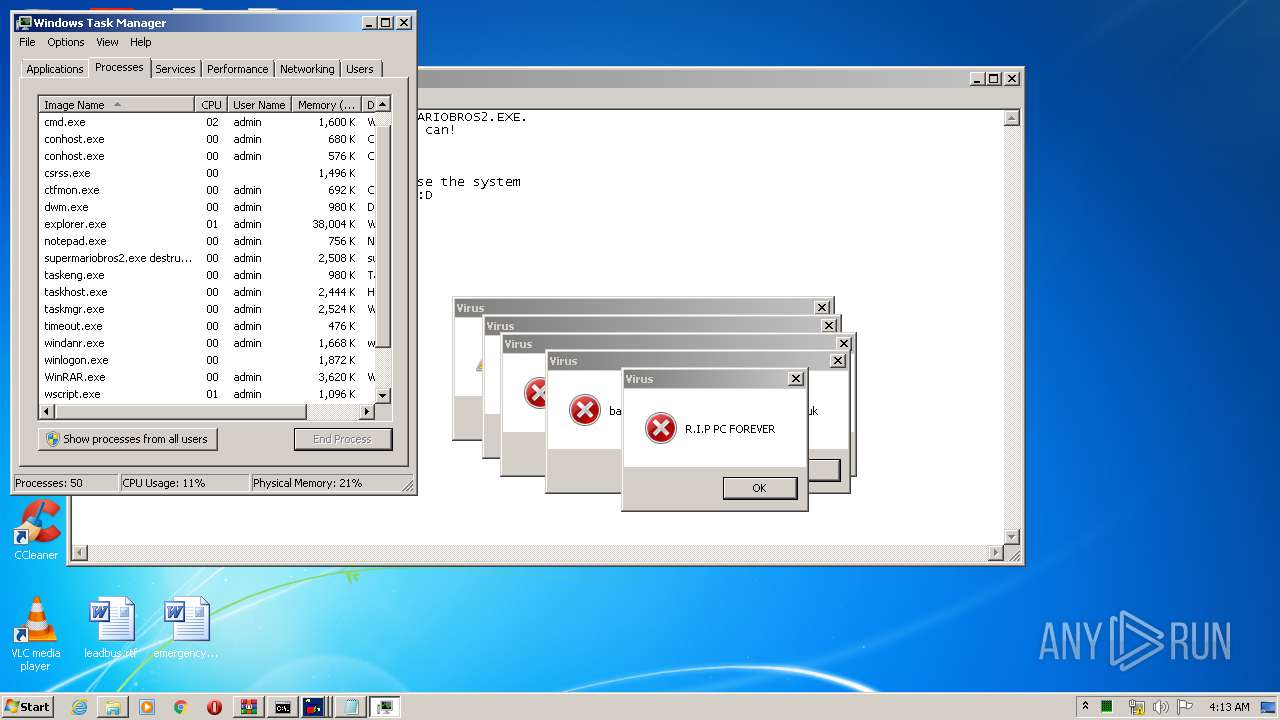
MALICIOUS
Application was dropped or rewritten from another process
- mbr.exe (PID: 4056)
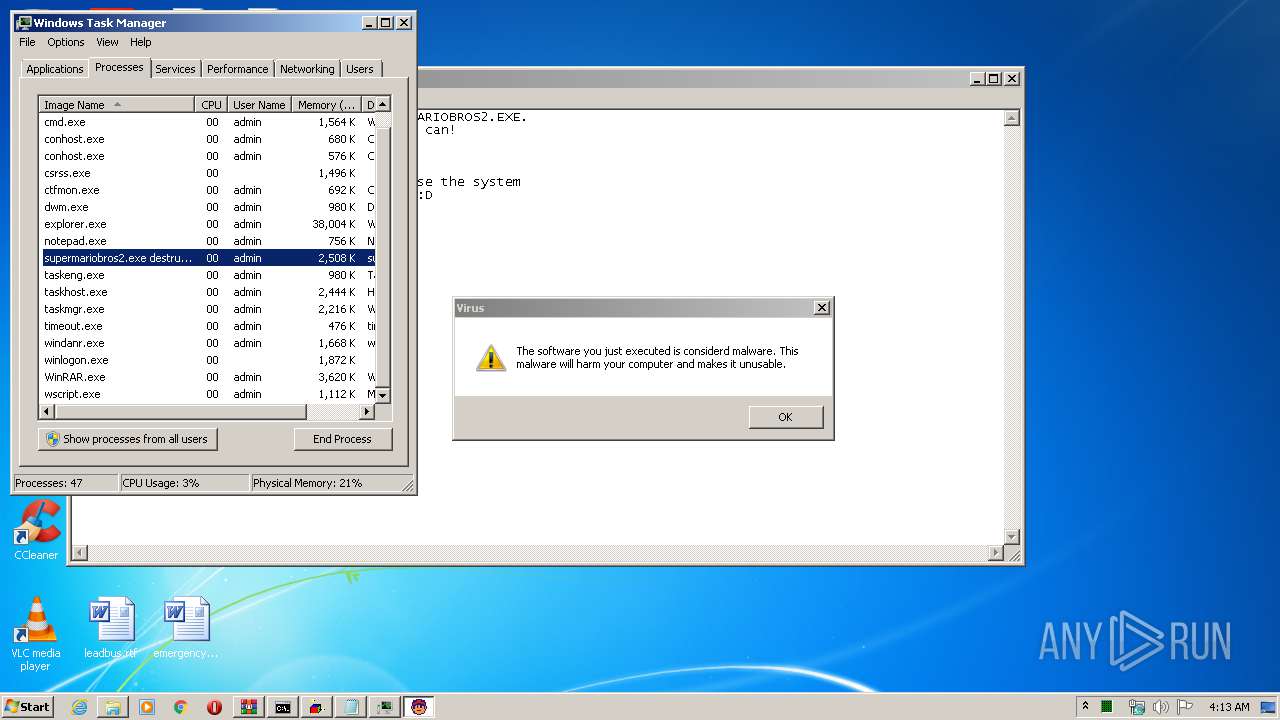
- supermariobros2.exe destructive.exe (PID: 1000)
- mbr.exe (PID: 3100)
- supermariobros2.exe (PID: 4076)
Low-level write access rights to disk partition
- mbr.exe (PID: 3100)
Loads dropped or rewritten executable
- supermariobros2.exe (PID: 4076)
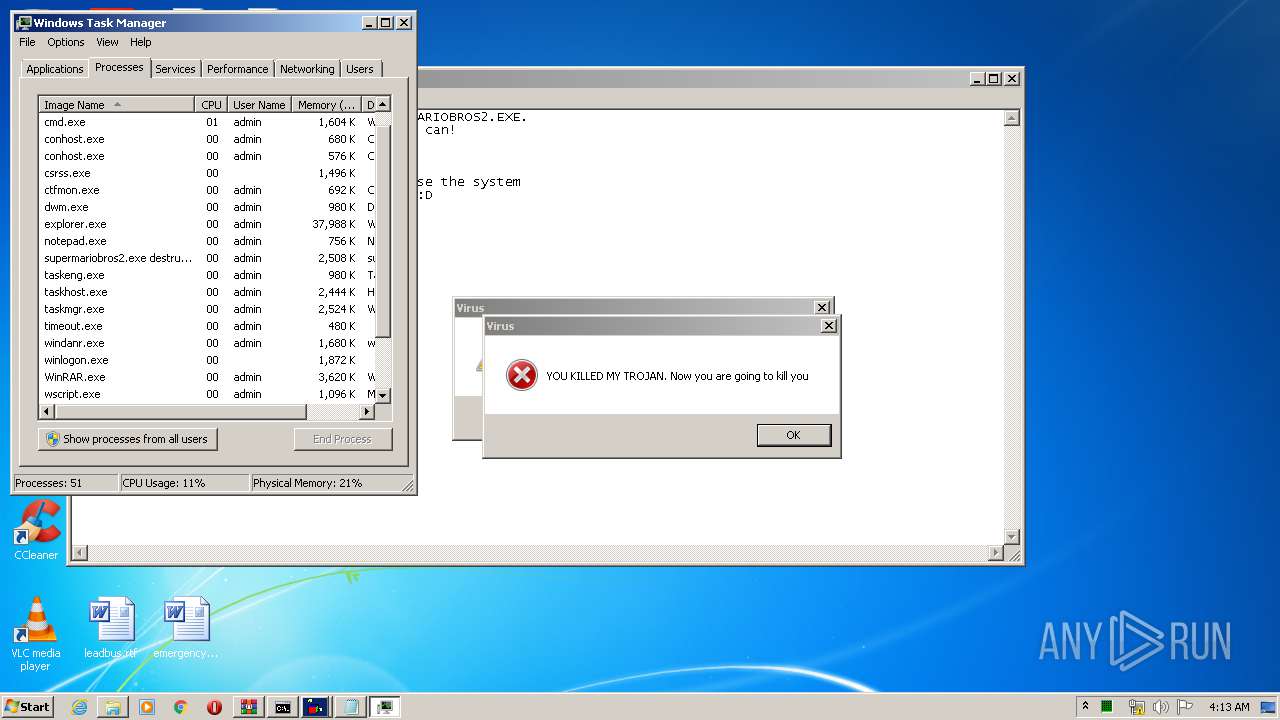
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2348)
- supermariobros2.exe (PID: 4076)
Application launched itself
- mbr.exe (PID: 4056)
Starts CMD.EXE for commands execution
- supermariobros2.exe destructive.exe (PID: 1000)
Executes scripts
- cmd.exe (PID: 2688)
- cmd.exe (PID: 2280)
Low-level read access rights to disk partition
- mbr.exe (PID: 3100)
INFO
Manual execution by user
- supermariobros2.exe destructive.exe (PID: 1000)
- cmd.exe (PID: 2280)
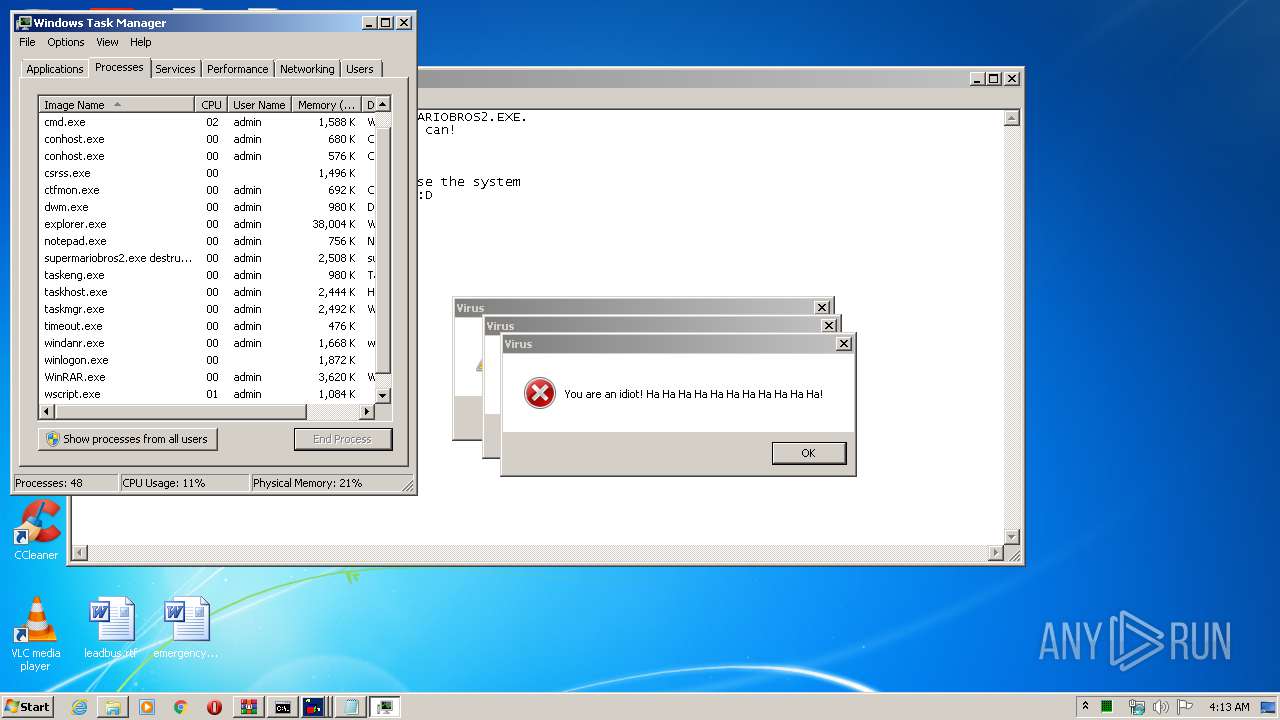
- taskmgr.exe (PID: 2612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
72
Monitored processes
22
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | timeout /t 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | timeout /t 10 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | "C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe destructive.exe" | C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe destructive.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1756 | timeout /t 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | cmd /c ""C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe destructive.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1073807364 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2348 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\666.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.60.0 Modules
| |||||||||||||||
| 2360 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\666\666\Malware2.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2580 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\666\666\Malware.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2612 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\D35C.tmp\D35D.tmp\D36D.bat "C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe destructive.exe"" | C:\Windows\system32\cmd.exe | — | supermariobros2.exe destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 684
Read events
1 635
Write events
49
Delete events
0
Modification events
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\666.rar | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2348) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\666 | |||
Executable files
11
Suspicious files
0
Text files
9
Unknown types
0
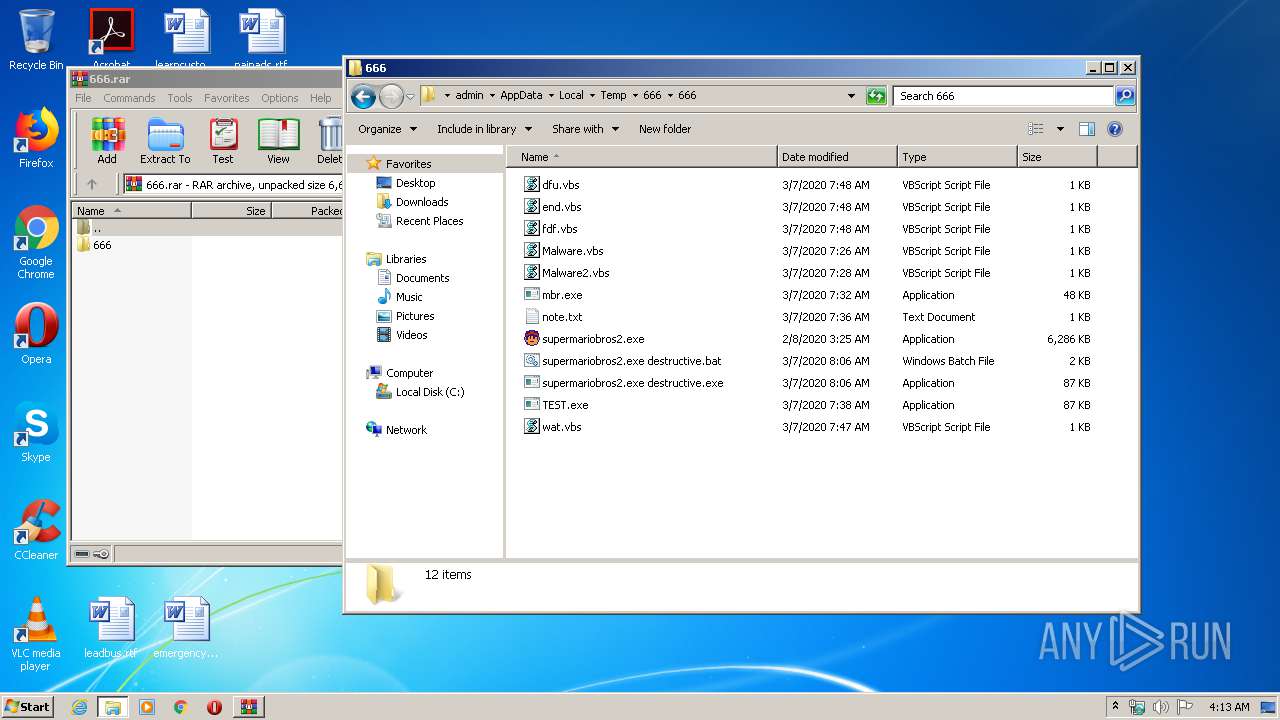
Dropped files
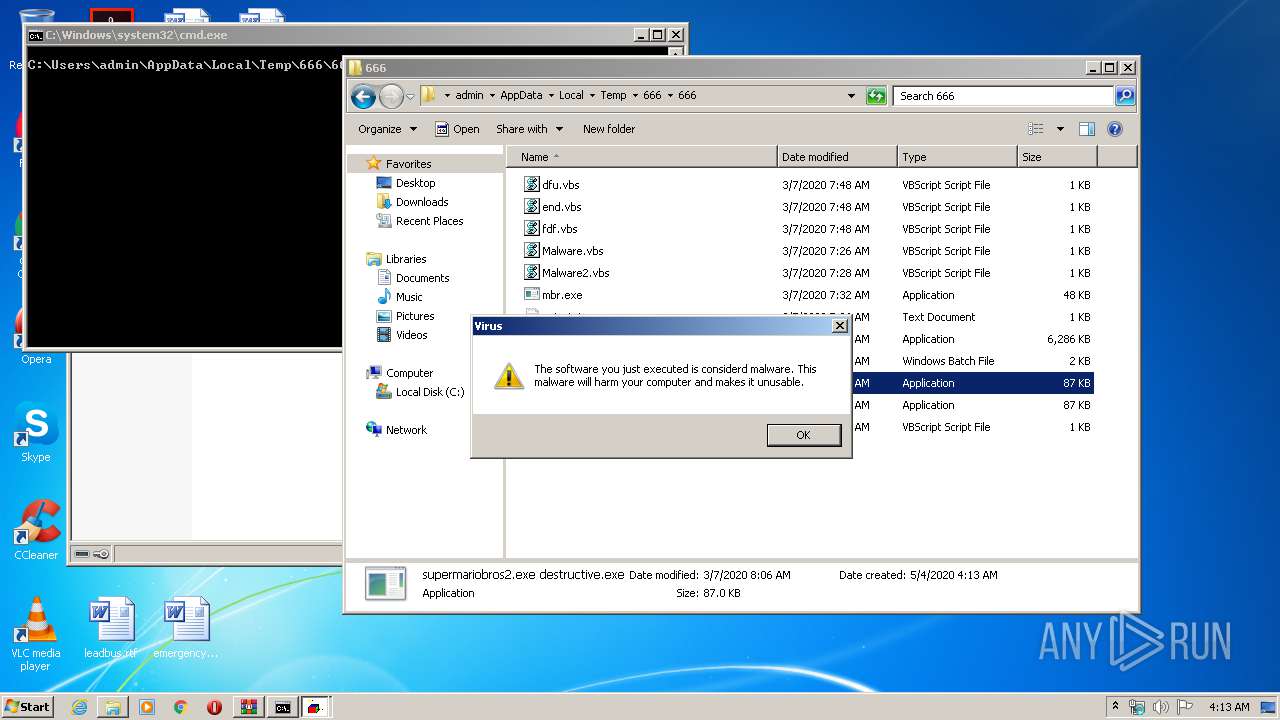
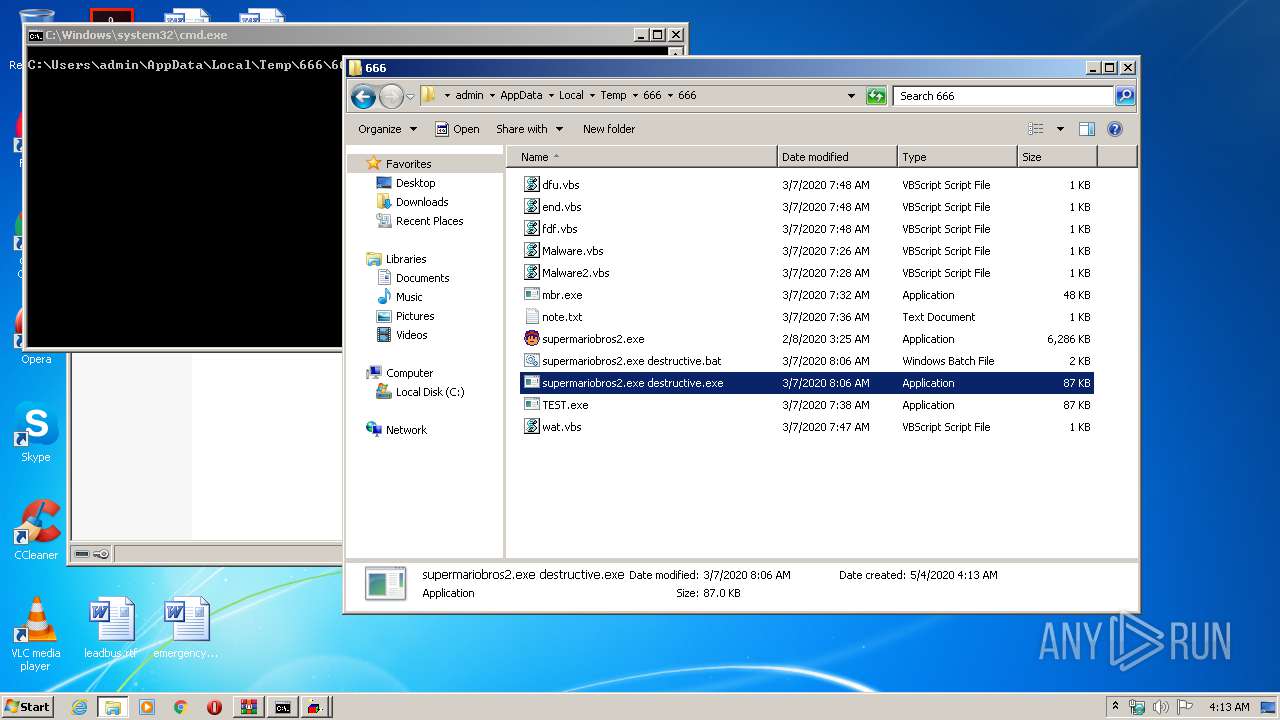
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\end.vbs | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\fdf.vbs | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\Malware.vbs | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\note.txt | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\Malware2.vbs | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\mbr.exe | executable | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\dfu.vbs | text | |
MD5:— | SHA256:— | |||
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe destructive.bat | text | |
MD5:— | SHA256:— | |||
| 1000 | supermariobros2.exe destructive.exe | C:\Users\admin\AppData\Local\Temp\D35C.tmp\D35D.tmp\D36D.bat | text | |
MD5:— | SHA256:— | |||
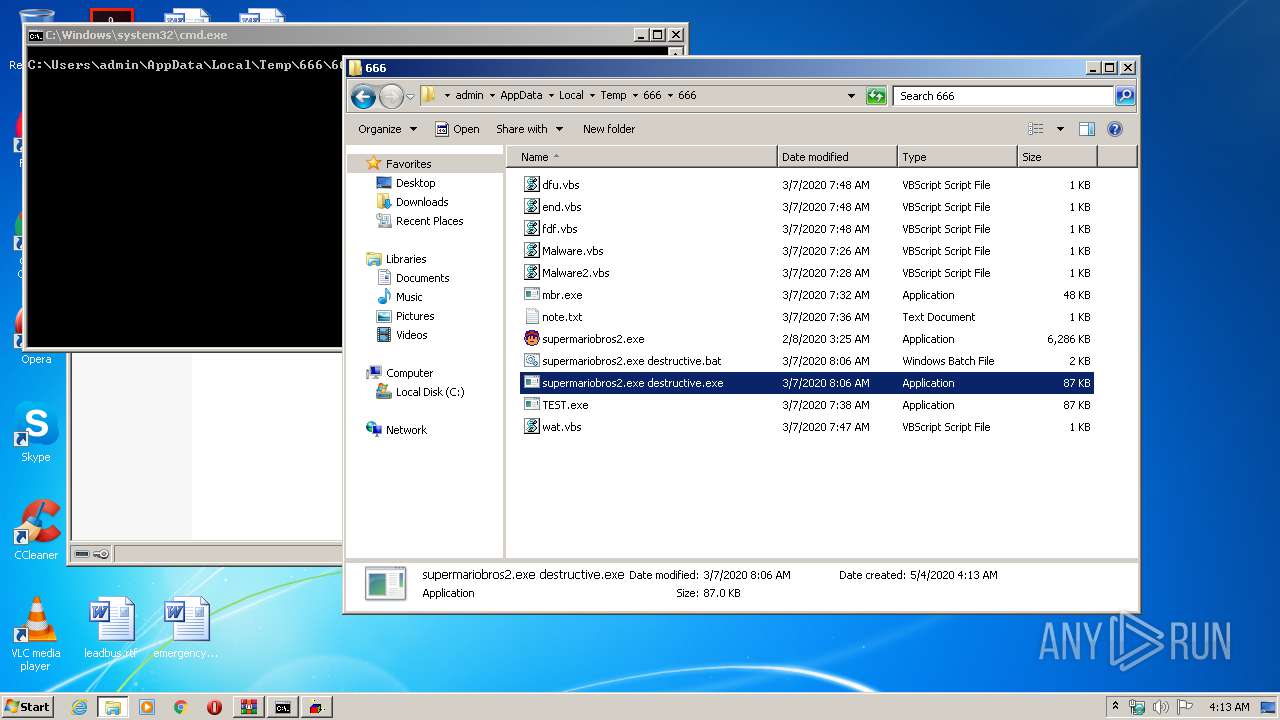
| 2348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\666\666\supermariobros2.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report