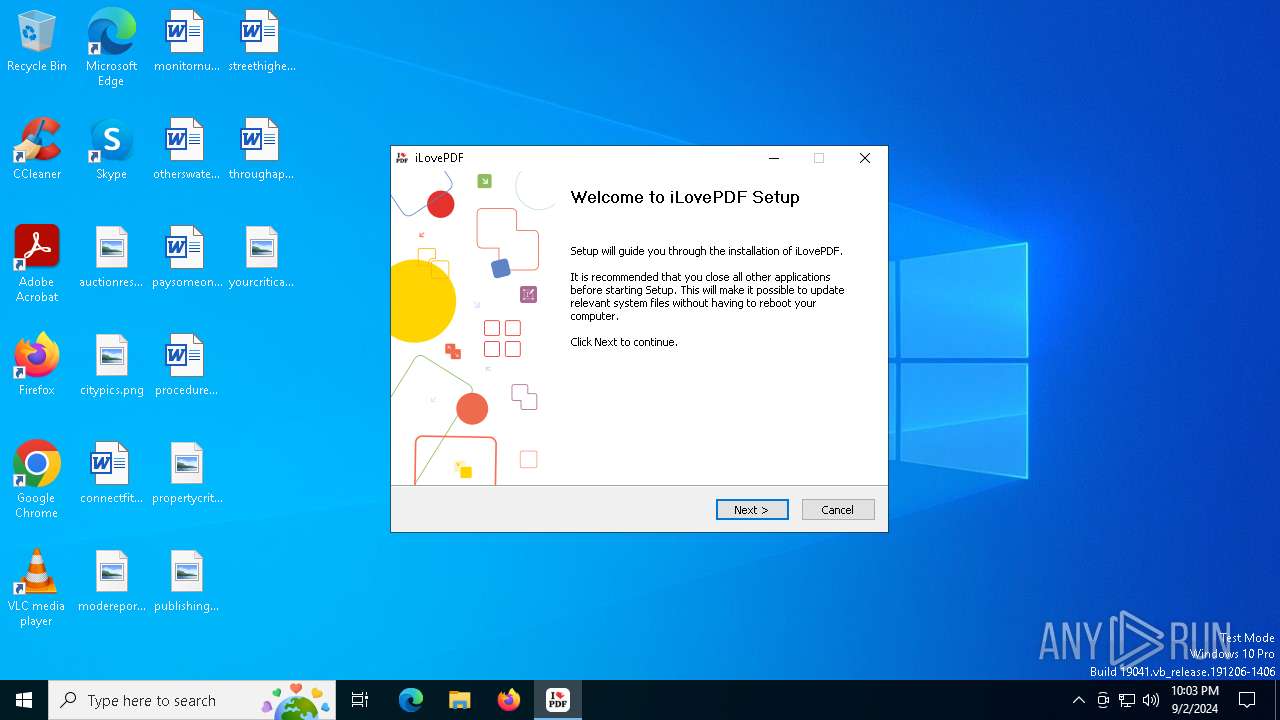
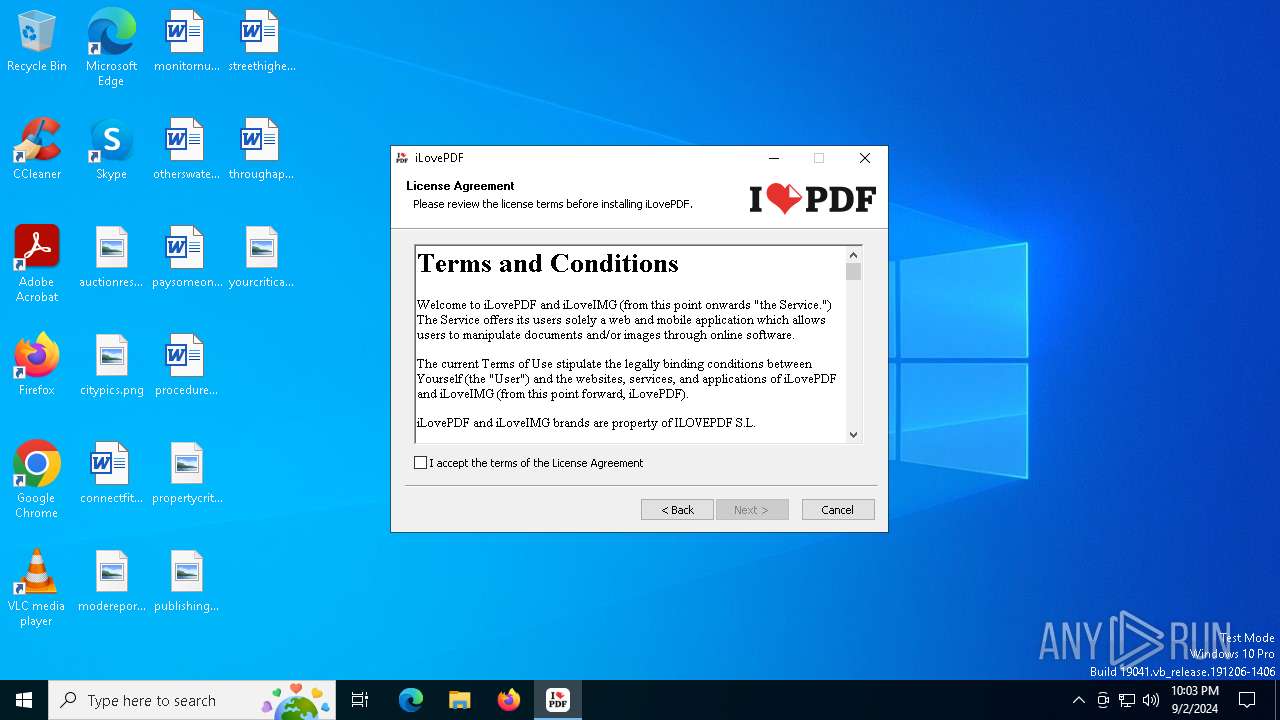
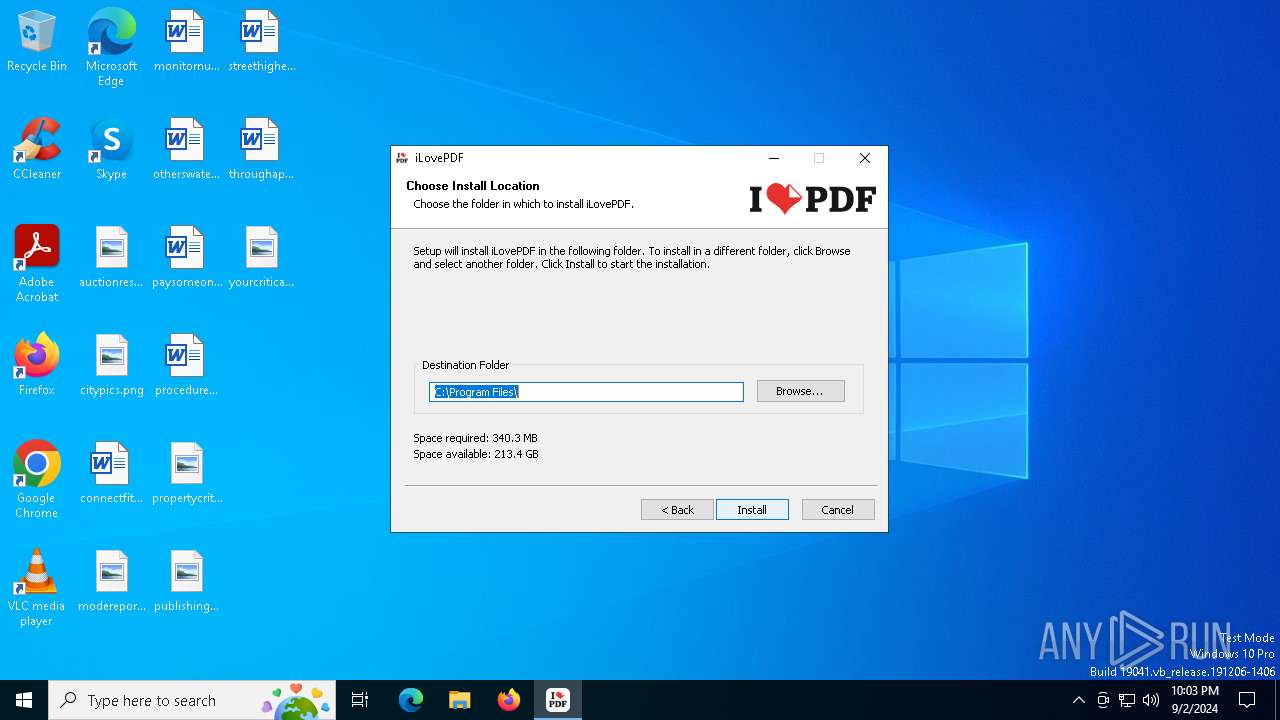
| File name: | iLovePDF Desktop Installer.exe |
| Full analysis: | https://app.any.run/tasks/390bf823-8d21-4a91-9b4c-0ffee6b8a44a |
| Verdict: | Malicious activity |
| Analysis date: | September 02, 2024, 22:02:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 734FB4D6B8598D8B753BC14E3C0923C6 |
| SHA1: | C723B6B064925A76B13A7B5E3509F90C64AB7A4A |
| SHA256: | FA299A5245C5720465DCF5CD5E88C18700C14D19B7A247F965EDF5F22370433B |
| SSDEEP: | 24576:gbe84pLPw9cG1szLSvJwT6VmxLovU21s1LSbJwRMU:qmY9cfqvCWVkPsbIJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- iLovePDF Desktop Installer.exe (PID: 1480)
The process creates files with name similar to system file names
- iLovePDF Desktop Installer.exe (PID: 1480)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5492)
- iLovePDF Desktop Installer.exe (PID: 1480)
Application launched itself
- cmd.exe (PID: 5492)
Reads security settings of Internet Explorer
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Checks Windows Trust Settings
- iLovePDF Desktop Installer.exe (PID: 1480)
Executable content was dropped or overwritten
- iLovePDF Desktop Installer.exe (PID: 1480)
Starts POWERSHELL.EXE for commands execution
- iLovePDF Desktop Installer.exe (PID: 1480)
Process drops legitimate windows executable
- iLovePDF Desktop Installer.exe (PID: 1480)
Reads the date of Windows installation
- iLovePDF Desktop Installer.exe (PID: 1480)
The process drops C-runtime libraries
- iLovePDF Desktop Installer.exe (PID: 1480)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6284)
- cmd.exe (PID: 7128)
- cmd.exe (PID: 5796)
- cmd.exe (PID: 6536)
Detected use of alternative data streams (AltDS)
- iLovePDF.exe (PID: 6372)
Drops 7-zip archiver for unpacking
- iLovePDF Desktop Installer.exe (PID: 1480)
Creates a software uninstall entry
- iLovePDF Desktop Installer.exe (PID: 1480)
INFO
Checks supported languages
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Create files in a temporary directory
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Reads the computer name
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Manual execution by a user
- cmd.exe (PID: 5492)
- iLovePDF.exe (PID: 6372)
Reads the machine GUID from the registry
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Checks proxy server information
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Creates files or folders in the user directory
- iLovePDF Desktop Installer.exe (PID: 1480)
- iLovePDF.exe (PID: 6372)
Reads Environment values
- iLovePDF Desktop Installer.exe (PID: 1480)
Reads the software policy settings
- iLovePDF Desktop Installer.exe (PID: 1480)
Creates files in the program directory
- iLovePDF Desktop Installer.exe (PID: 1480)
The process uses the downloaded file
- iLovePDF Desktop Installer.exe (PID: 1480)
Process checks computer location settings
- iLovePDF Desktop Installer.exe (PID: 1480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
153
Monitored processes
27
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | powershell -Command "& { [xml]$xml = Get-Content -Path C:\Users\admin\AppData\Local\Temp\Updates2.xml; $xml.Updates.SHA1}" ServerManager | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iLovePDF Desktop Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | Reg Load HKU\Temp C:\Users\Default\AppData\Local\Microsoft\Windows\UsrClass.dat | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | Reg Unload HKU\Temp | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\iLovePDF Desktop Installer.exe" | C:\Users\admin\AppData\Local\Temp\iLovePDF Desktop Installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4284 | powershell -Command "& { [xml]$xml = Get-Content -Path C:\Users\admin\AppData\Local\Temp\Updates2.xml; $xml.Updates.UpdateFile.UncompressedSize}" ServerManager | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iLovePDF Desktop Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4344 | powershell -Command "& { [xml]$xml = Get-Content -Path C:\Users\admin\AppData\Local\Temp\Updates2.xml; $xml.Updates.UpdateFile.CompressedSize}" ServerManager | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iLovePDF Desktop Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 983
Read events
34 844
Write events
2 135
Delete events
4
Modification events
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_USERS\Temp\SystemFileAssociations\.pdf\shell\iLovePDF |
| Operation: | write | Name: | Icon |
Value: C:\Program Files\iLovePDF\Icons\iLovePdfApp.ico | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_USERS\Temp\SystemFileAssociations\.pdf\shell\iLovePDF |
| Operation: | write | Name: | MUIVerb |
Value: iLovePDF | |||
| (PID) Process: | (1480) iLovePDF Desktop Installer.exe | Key: | HKEY_USERS\Temp\SystemFileAssociations\.pdf\shell\iLovePDF |
| Operation: | write | Name: | MultiSelectModel |
Value: Player | |||
Executable files
147
Suspicious files
207
Text files
547
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\nsoA225.tmp\license.html | html | |
MD5:E33DF11E6A5EACDD2800341FE3C9C9C2 | SHA256:B9BBD98E5C986628E7106E3BE0B539F4FF97B736444D3A1967CECD02FACA4586 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\nsoA225.tmp\Dialer.dll | executable | |
MD5:ADEA8024C99D7802FA3C9E5D34877AAD | SHA256:242B6AEB759E31B64E014E3DF6B5C478FB309D56B4DF8CDB59B2CD03BFA77DB2 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\nsoA225.tmp\ShellExecAsUser.dll | executable | |
MD5:552CBA3C6C9987E01BE178E1EE22D36B | SHA256:1F17E4D5FFE7B2C9A396EE9932AC5198F0C050241E5F9CCD3A56E576613D8A29 | |||
| 6824 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tvfpwryu.soa.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\nsoA225.tmp\INetC.dll | executable | |
MD5:40D7ECA32B2F4D29DB98715DD45BFAC5 | SHA256:85E03805F90F72257DD41BFDAA186237218BBB0EC410AD3B6576A88EA11DCCB9 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | der | |
MD5:555C400991D7D9F94EA078952EB7416B | SHA256:D54B60BFEDF7F2C61599FC9518EB378DBAC40A6464285C2BDCD74C89B43870B3 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\nsoA225.tmp\nsExec.dll | executable | |
MD5:675C4948E1EFC929EDCABFE67148EDDD | SHA256:1076CA39C449ED1A968021B76EF31F22A5692DFAFEEA29460E8D970A63C59906 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Users\admin\AppData\Local\Temp\Updates2.xml | text | |
MD5:26FBF186273DA078D392EBBF802BCFEE | SHA256:F05C9DF9BDB927F5C60FFA6084A96A31CFE4EE59BE642710DD45162480D62042 | |||
| 4284 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fh52tarj.f4j.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1480 | iLovePDF Desktop Installer.exe | C:\Program Files\iLovePDF\2.1.0.0iLovePDF.7z | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
15
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1480 | iLovePDF Desktop Installer.exe | POST | 200 | 216.58.206.78:80 | http://www.google-analytics.com/collect?&v=1&tid=UA-120929701-1&cid=%7B82b15637-13cc-45c8-b47b-2587db76ad8f%7D&t=event&uid=3251657&cd=INSTALLER%20NSIS&ec=InstallerNSIS&ea=%20START%20INSTALLATION%20&el=2.0.000 | unknown | — | — | unknown |
1480 | iLovePDF Desktop Installer.exe | POST | 200 | 216.58.206.78:80 | http://www.google-analytics.com/collect?&v=1&tid=UA-120929701-1&cid=%7B82b15637-13cc-45c8-b47b-2587db76ad8f%7D&t=event&uid=3251657&cd=INSTALLER%20NSIS&ec=InstallerNSIS&ea=%20START%20&el=2.0.000 | unknown | — | — | unknown |
5476 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1480 | iLovePDF Desktop Installer.exe | POST | 200 | 216.58.206.78:80 | http://www.google-analytics.com/collect?&v=1&tid=UA-120929701-1&cid=%7B82b15637-13cc-45c8-b47b-2587db76ad8f%7D&t=event&uid=3251657&cd=INSTALLER%20NSIS&ec=InstallerNSIS&ea=%20SUCCESSFUL%20%20INSTALLATION%20&el=2.0.000 | unknown | — | — | unknown |
5476 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1480 | iLovePDF Desktop Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | whitelisted |
1828 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3352 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1480 | iLovePDF Desktop Installer.exe | 104.18.35.86:443 | desktopupdate.ilovepdf.com | CLOUDFLARENET | — | whitelisted |
1480 | iLovePDF Desktop Installer.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1828 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1828 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
desktopupdate.ilovepdf.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | iLovePDF Desktop Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1480 | iLovePDF Desktop Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1480 | iLovePDF Desktop Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
Process | Message |
|---|---|
iLovePDF Desktop Installer.exe | ExecShellAsUser: got desktop |
iLovePDF Desktop Installer.exe | ExecShellAsUser: elevated process detected |
iLovePDF Desktop Installer.exe | ExecShellAsUser: thread finished |
iLovePDF Desktop Installer.exe | ExecShellAsUser: DLL_PROCESS_DETACH |