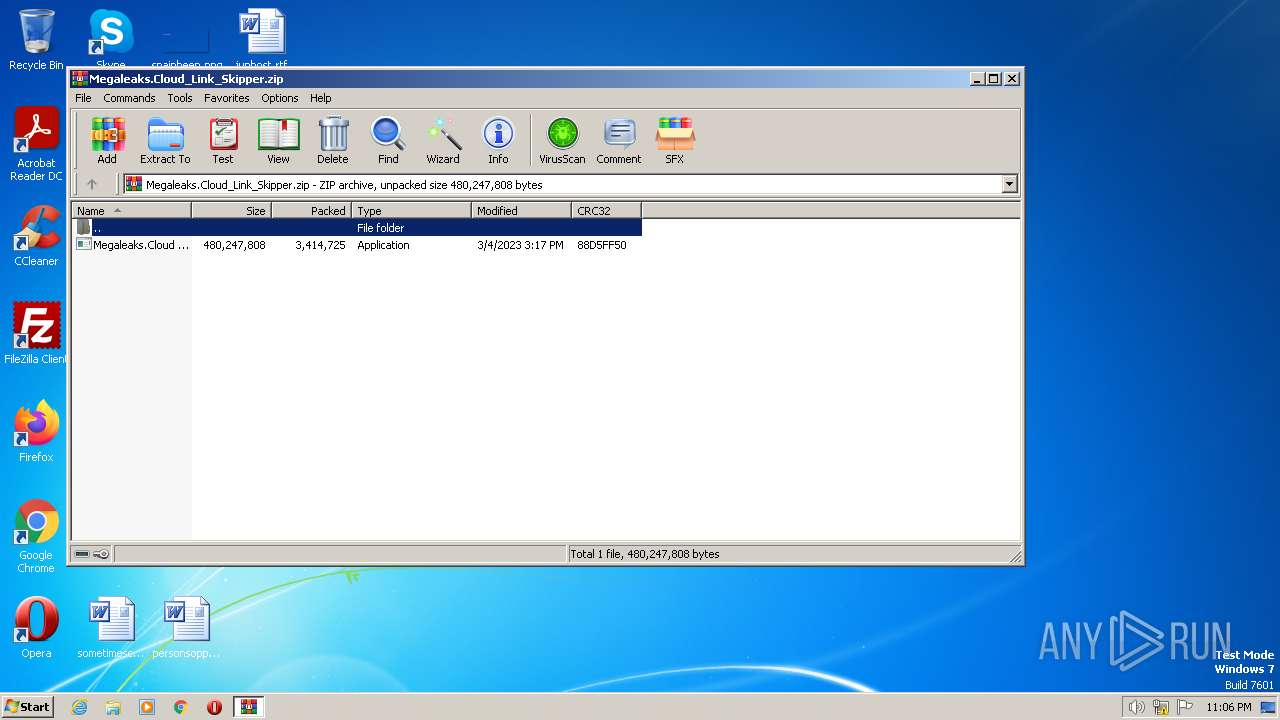
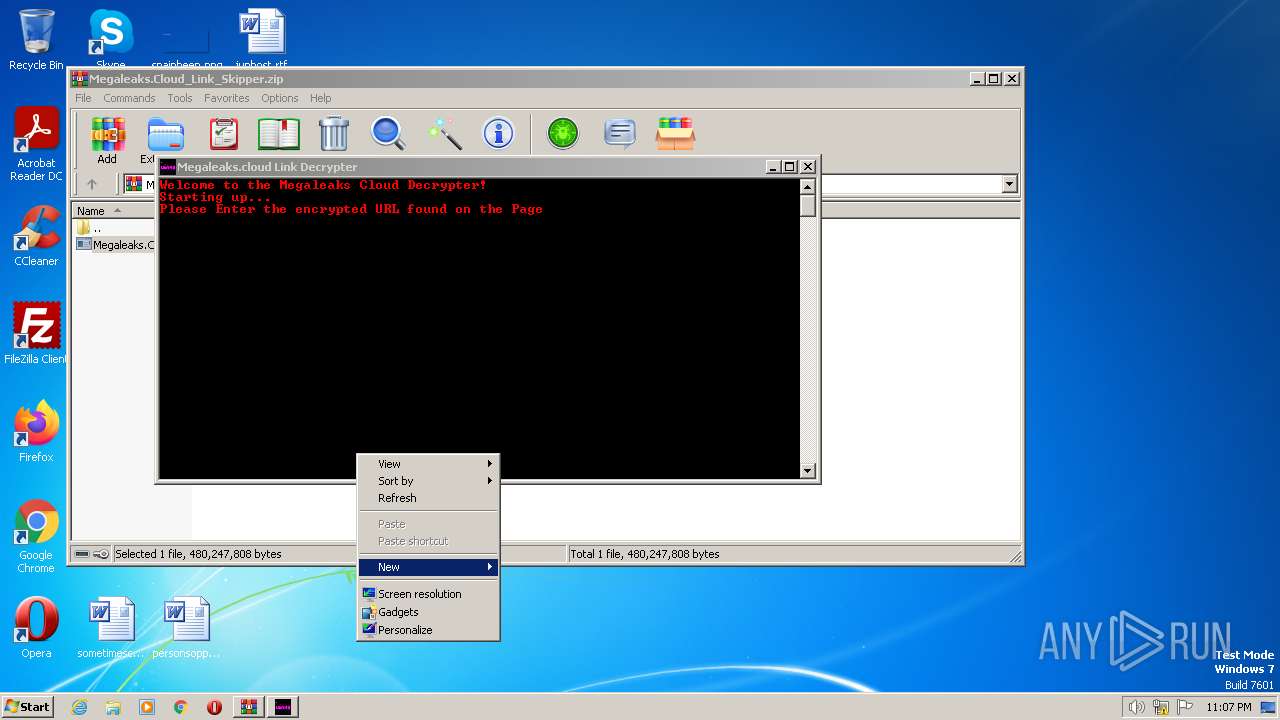
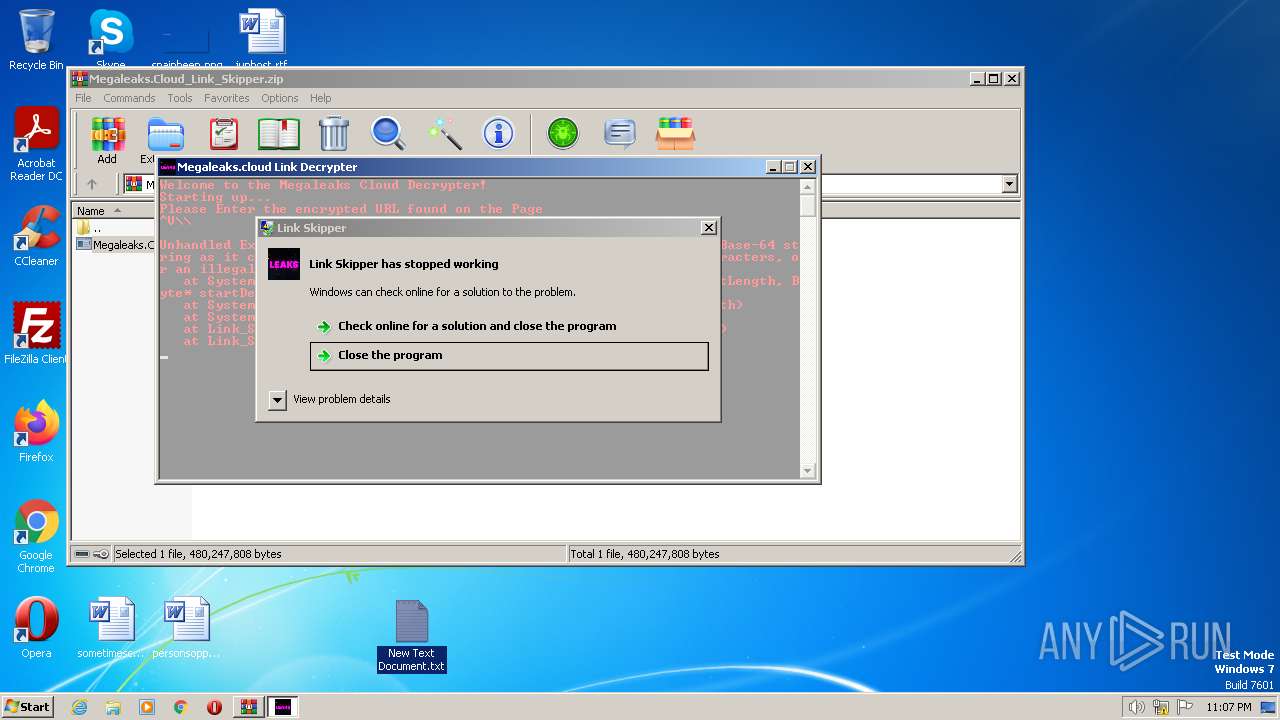
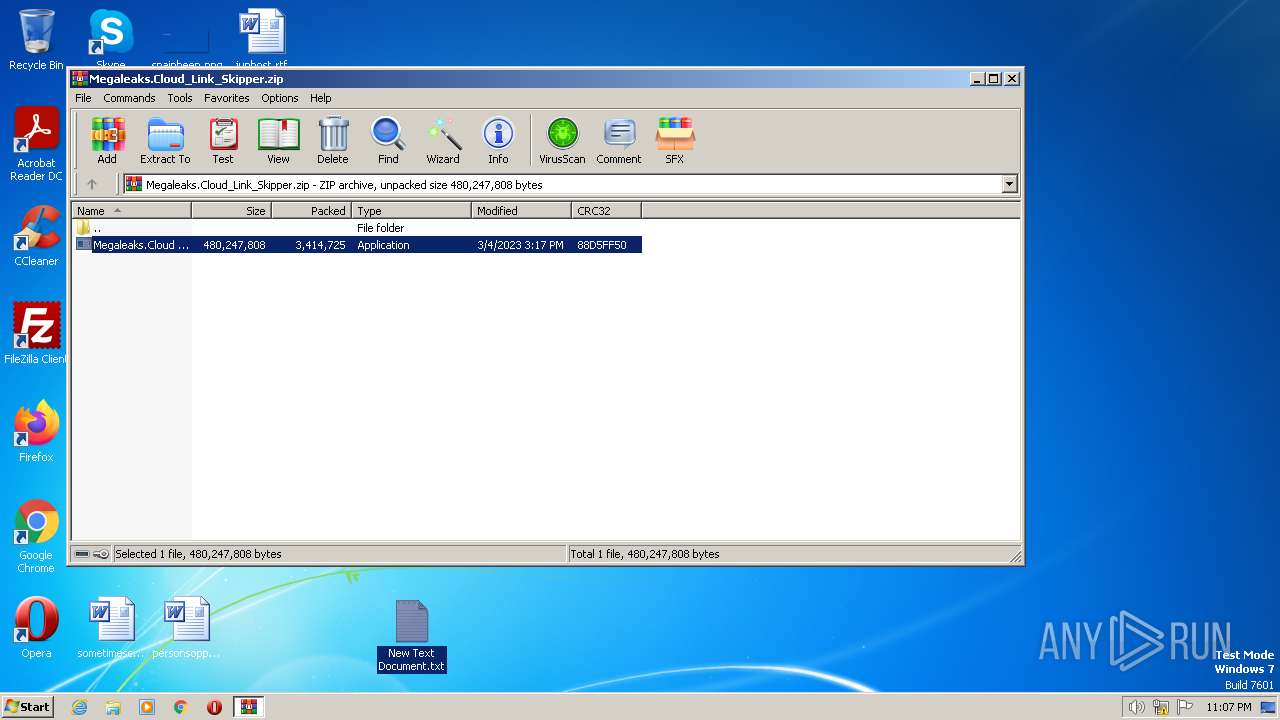
| download: | Megaleaks.Cloud_Link_Skipper.zip |
| Full analysis: | https://app.any.run/tasks/9af8aa74-36a7-4a9c-903f-1242f865c3bb |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2023, 22:06:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C9C505A7797BAC57BBF3C8770EC105FA |
| SHA1: | FE36AAC243915D61BF27C56D75CCED55C0DC071F |
| SHA256: | FA021F6A96120A85F78C1B04D7D84B0D60B07DA478A23704FAC22570A92C772C |
| SSDEEP: | 98304:q8PcklAkfVL1mocYMS82EjQAq7AHnXw7+WaH:eKVwoPpIjrq03w7+WaH |
MALICIOUS
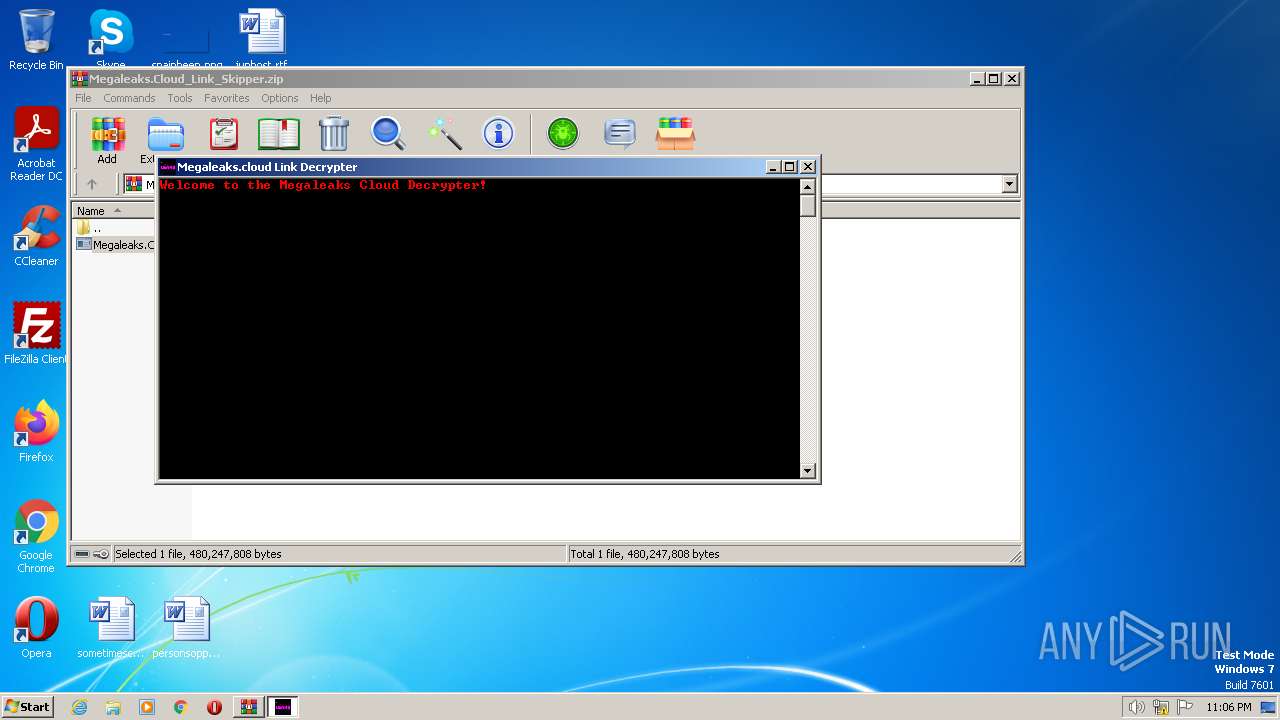
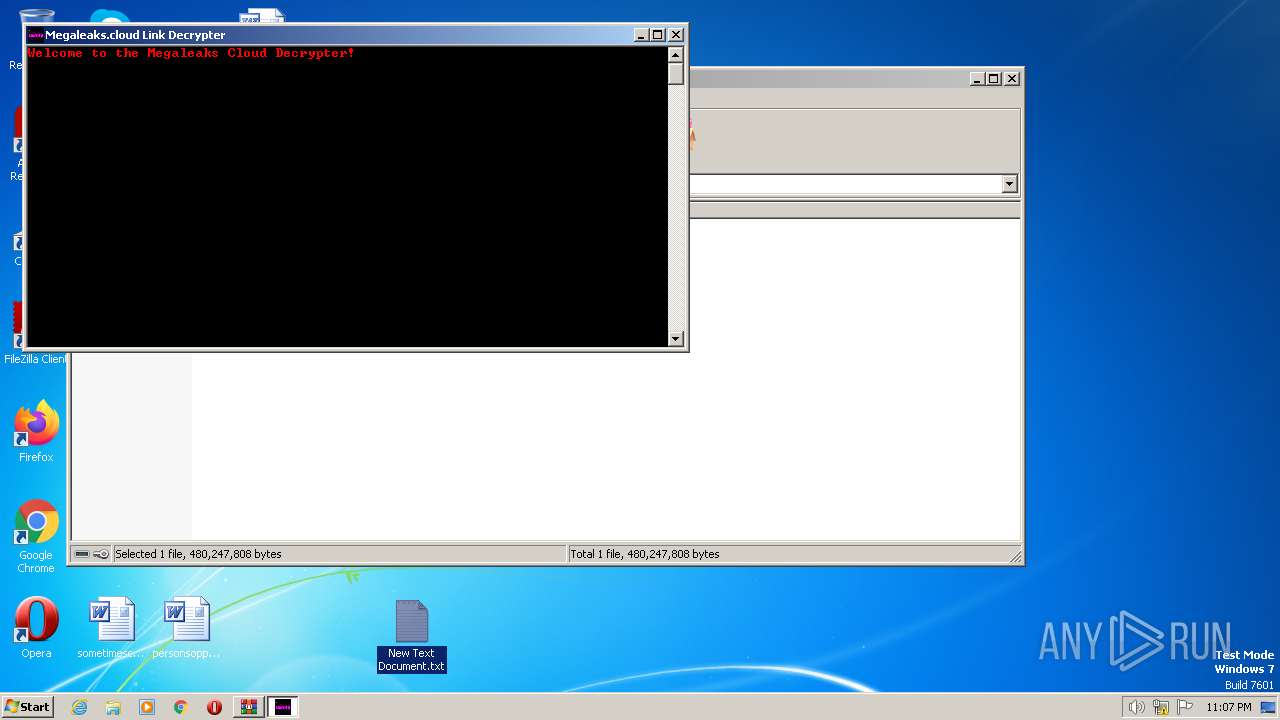
Drops the executable file immediately after the start
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 2500)
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
- cmd.exe (PID: 3320)
SUSPICIOUS
Drops a file with too old compile date
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Executable content was dropped or overwritten
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Reads the Internet Settings
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- powershell.exe (PID: 2936)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
- powershell.exe (PID: 3264)
Starts CMD.EXE for commands execution
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2500)
- cmd.exe (PID: 3320)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2936)
- powershell.exe (PID: 3264)
INFO
Reads the machine GUID from the registry
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Reads the computer name
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Create files in a temporary directory
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- powershell.exe (PID: 2936)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
- powershell.exe (PID: 3264)
Checks supported languages
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
The process checks LSA protection
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- powershell.exe (PID: 2936)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
- powershell.exe (PID: 3264)
Reads security settings of Internet Explorer
- powershell.exe (PID: 2936)
- powershell.exe (PID: 3264)
Reads settings of System Certificates
- powershell.exe (PID: 2936)
- powershell.exe (PID: 3264)
Loads dropped or rewritten executable
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
Reads Environment values
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
- Megaleaks.Cloud Link Skipper.exe (PID: 2088)
Creates files or folders in the user directory
- Megaleaks.Cloud Link Skipper.exe (PID: 2720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Megaleaks.Cloud Link Skipper.exe |
|---|---|
| ZipUncompressedSize: | 480247808 |
| ZipCompressedSize: | 3414725 |
| ZipCRC: | 0x88d5ff50 |
| ZipModifyDate: | 2023:03:04 16:17:10 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
57
Monitored processes
9
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 944 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Megaleaks.Cloud_Link_Skipper.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa944.43010\Megaleaks.Cloud Link Skipper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.43010\Megaleaks.Cloud Link Skipper.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Link Skipper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2500 | "C:\Windows\System32\cmd.exe" /c powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\cmd.exe | — | Megaleaks.Cloud Link Skipper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2720 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa944.38403\Megaleaks.Cloud Link Skipper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.38403\Megaleaks.Cloud Link Skipper.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Link Skipper Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2936 | powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3264 | powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3320 | "C:\Windows\System32\cmd.exe" /c powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\cmd.exe | — | Megaleaks.Cloud Link Skipper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3692 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa944.38403\Megaleaks.Cloud Link Skipper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.38403\Megaleaks.Cloud Link Skipper.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Link Skipper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3940 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa944.43010\Megaleaks.Cloud Link Skipper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.43010\Megaleaks.Cloud Link Skipper.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Link Skipper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
18 084
Read events
17 932
Write events
152
Delete events
0
Modification events
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
16
Suspicious files
8
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.38403\Megaleaks.Cloud Link Skipper.exe | — | |
MD5:— | SHA256:— | |||
| 944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa944.43010\Megaleaks.Cloud Link Skipper.exe | — | |
MD5:— | SHA256:— | |||
| 2720 | Megaleaks.Cloud Link Skipper.exe | C:\Users\admin\AppData\Local\Temp\evb5C42.tmp | executable | |
MD5:— | SHA256:— | |||
| 2720 | Megaleaks.Cloud Link Skipper.exe | C:\Users\admin\AppData\Local\Temp\evb5C41.tmp | executable | |
MD5:— | SHA256:— | |||
| 2720 | Megaleaks.Cloud Link Skipper.exe | C:\Users\admin\AppData\Local\Temp\evb5C53.tmp | executable | |
MD5:— | SHA256:— | |||
| 2720 | Megaleaks.Cloud Link Skipper.exe | C:\Users\admin\AppData\Local\Temp\evb5C52.tmp | executable | |
MD5:— | SHA256:— | |||
| 2088 | Megaleaks.Cloud Link Skipper.exe | C:\Users\admin\AppData\Local\Temp\evbCC4.tmp | executable | |
MD5:— | SHA256:— | |||
| 2936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\0fcitxv3.mo4.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\sgbk5grk.4g3.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2936 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2720 | Megaleaks.Cloud Link Skipper.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
2720 | Megaleaks.Cloud Link Skipper.exe | 162.159.135.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
2088 | Megaleaks.Cloud Link Skipper.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |