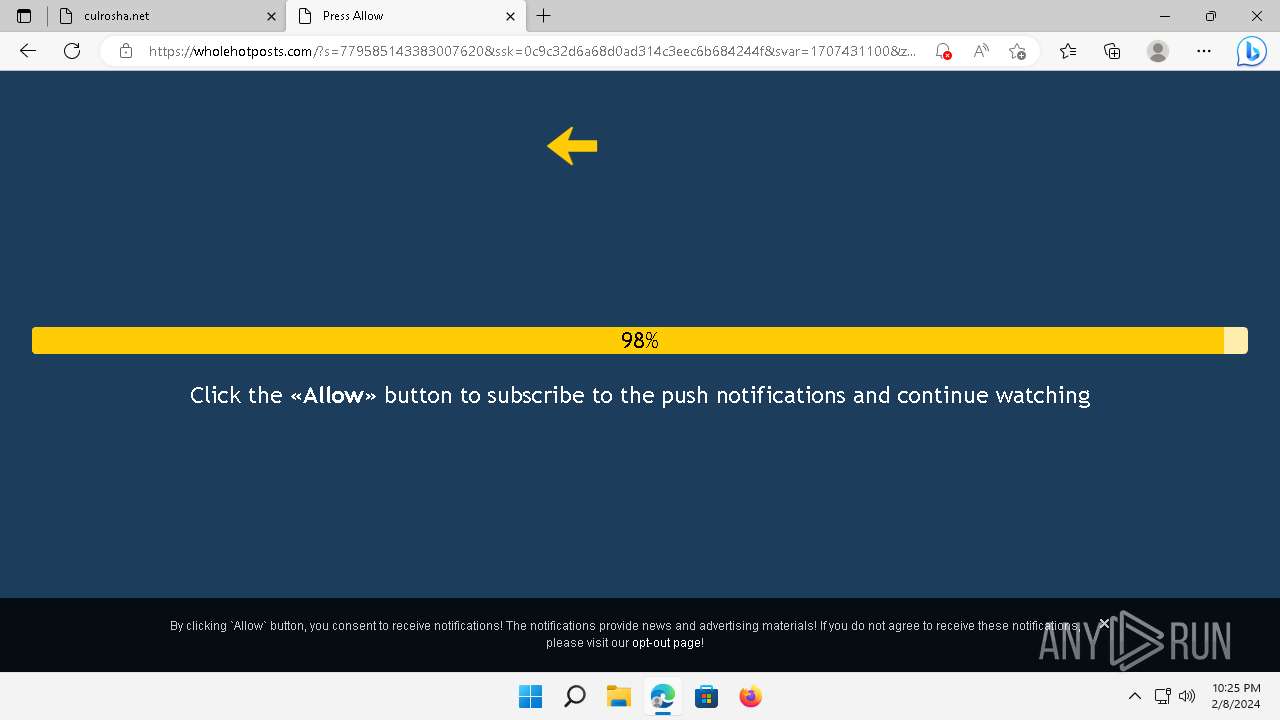
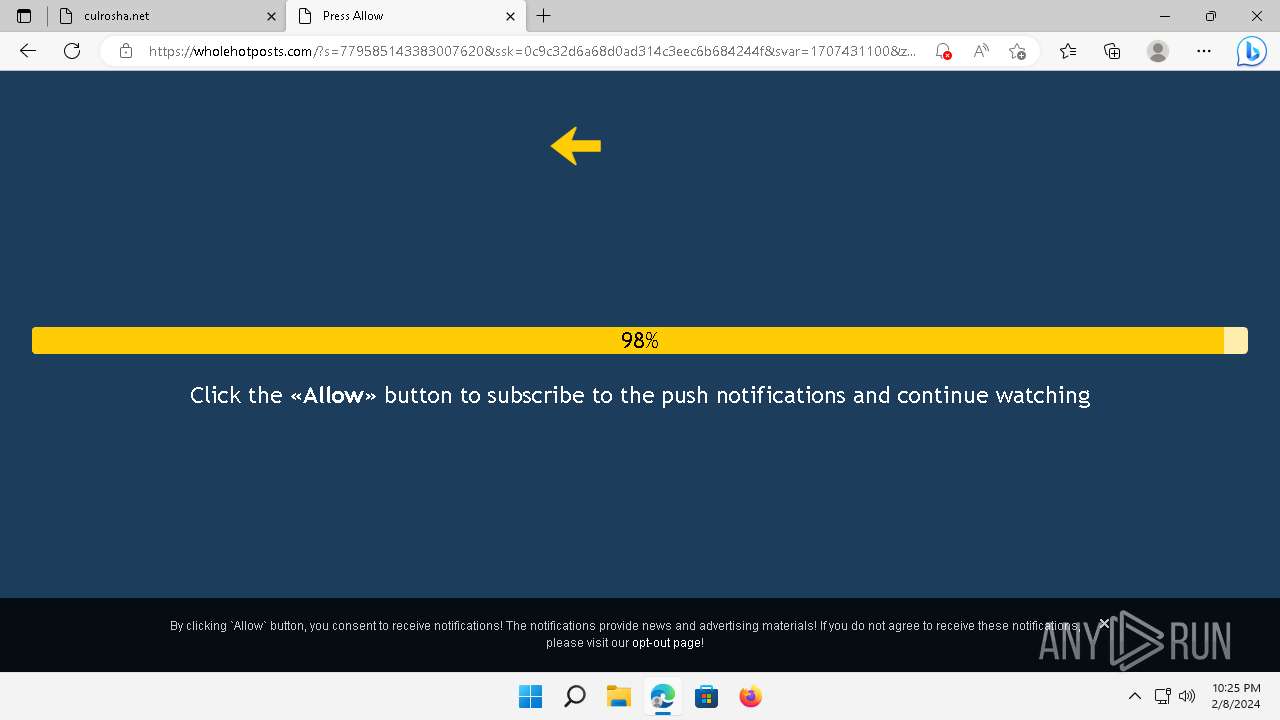
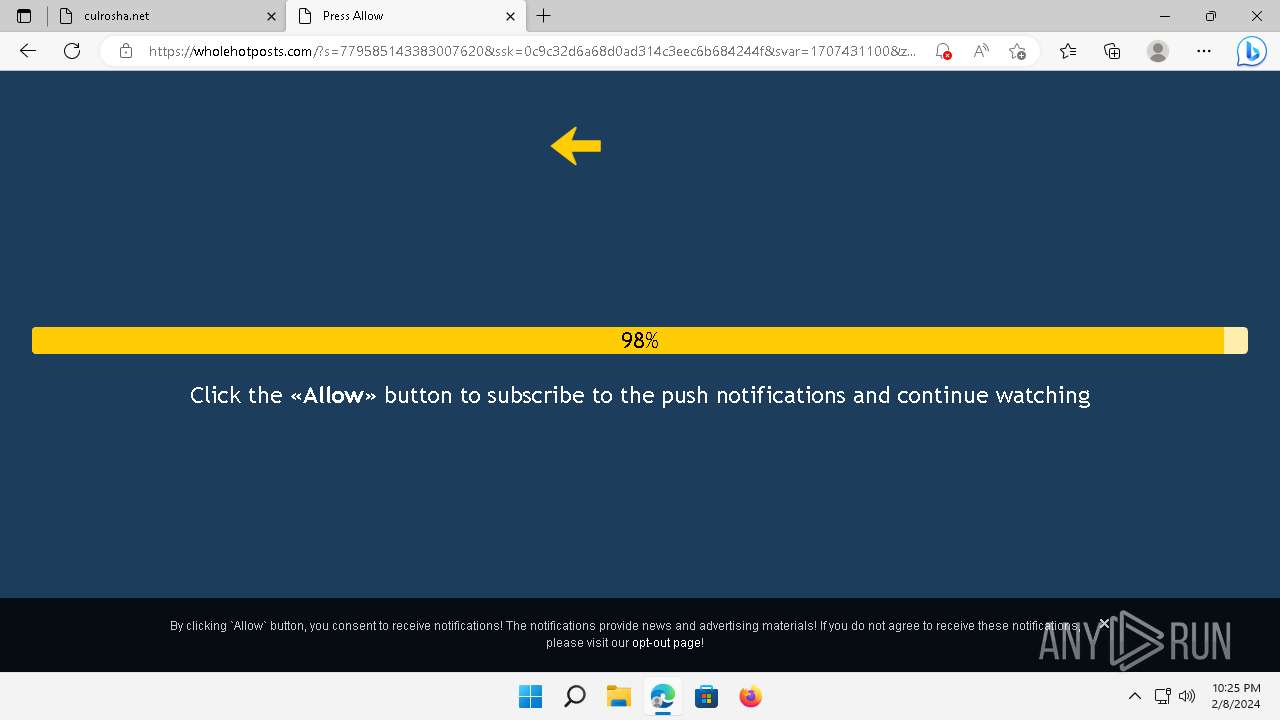
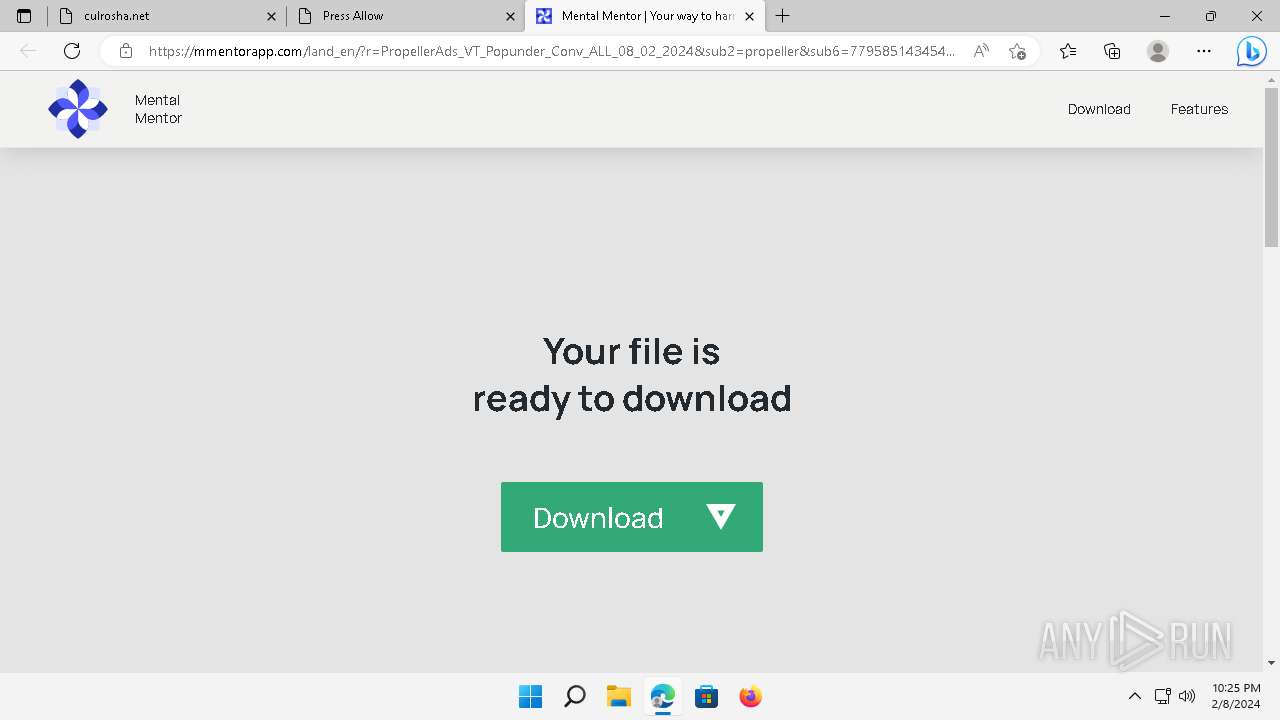
| URL: | culrosha.net |
| Full analysis: | https://app.any.run/tasks/4ec36aab-3e5a-4f91-9dbd-edab9bd9afc7 |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2024, 22:24:19 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MD5: | 3B765E69A3FE1B8D9EFA0E260CFAEAEA |
| SHA1: | BCFED9E5C2886C35FBCD893885B5C4B59E9816DA |
| SHA256: | F9ED48C2862F617EB03C33485772FDC3EAC64B47E7F8ACBEC59C8F59E5EAC240 |
| SSDEEP: | 3:p8/0n:pA0n |
MALICIOUS
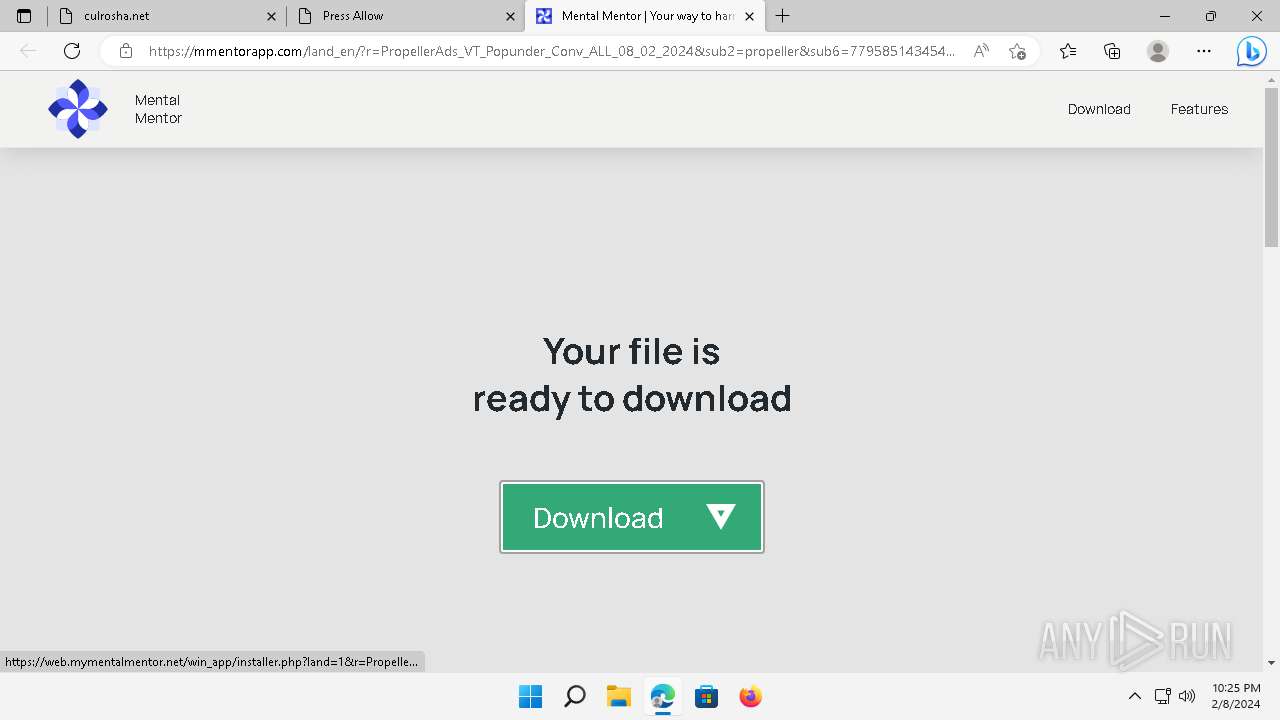
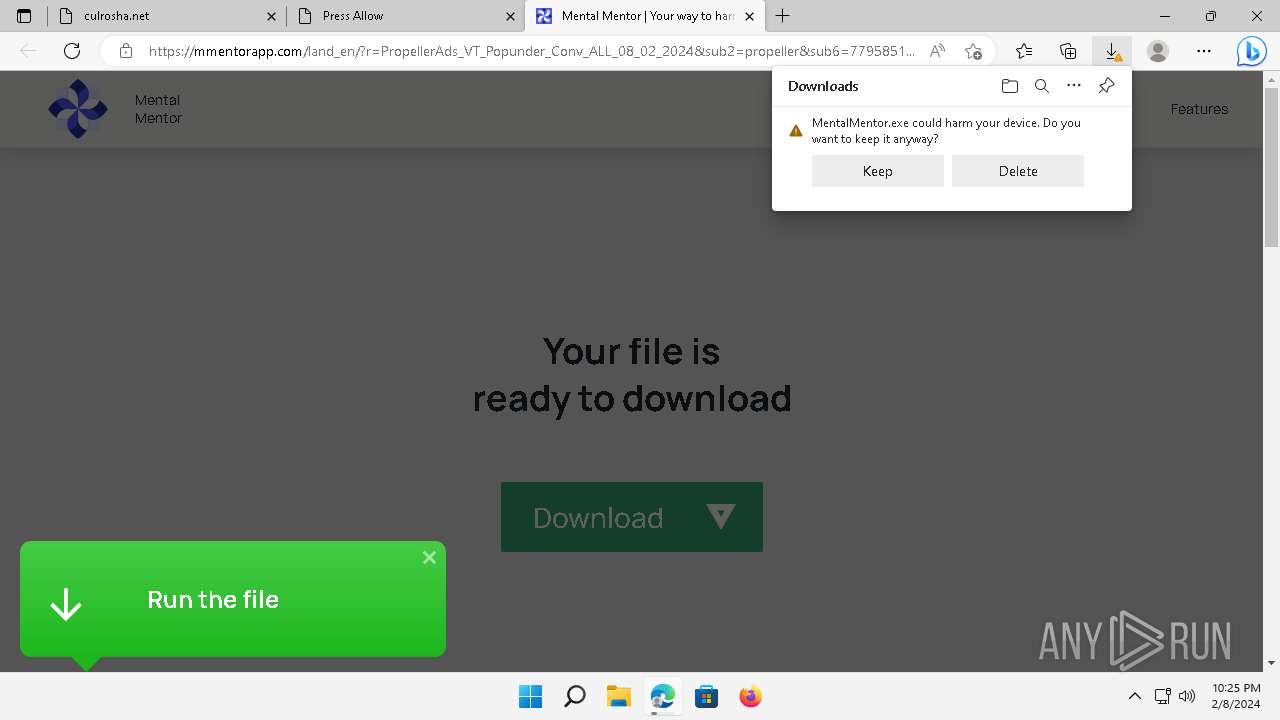
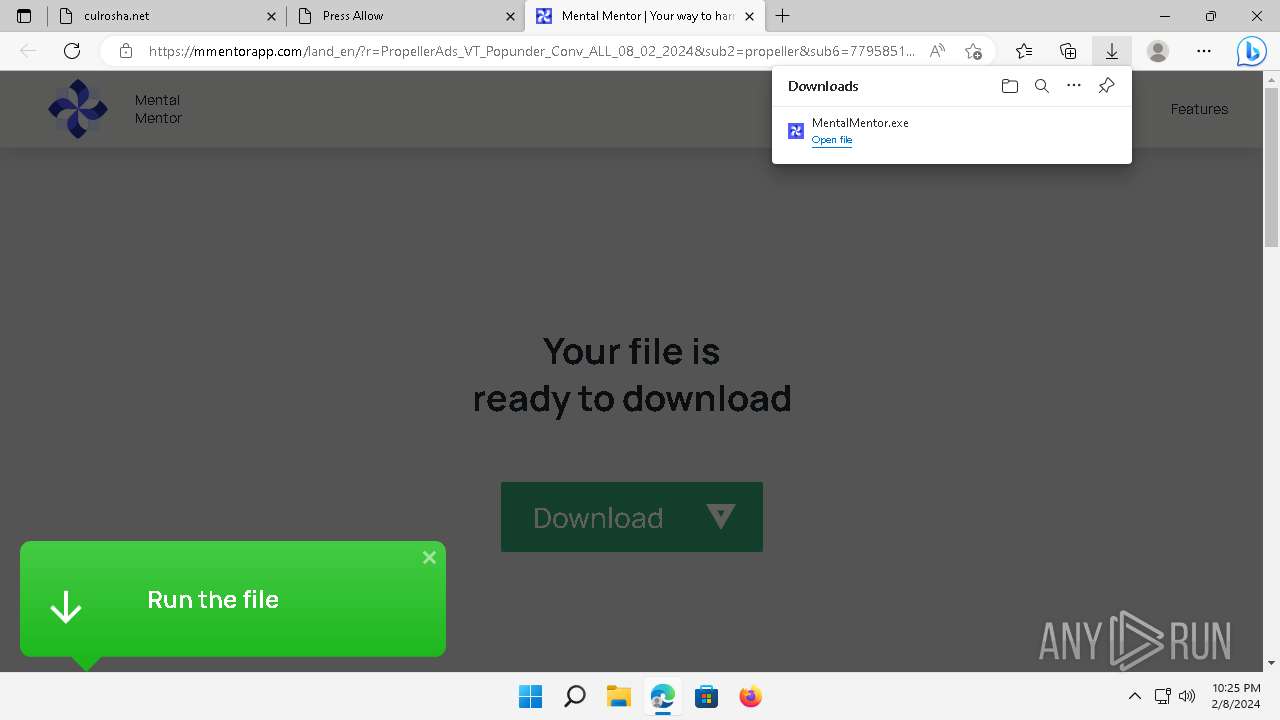
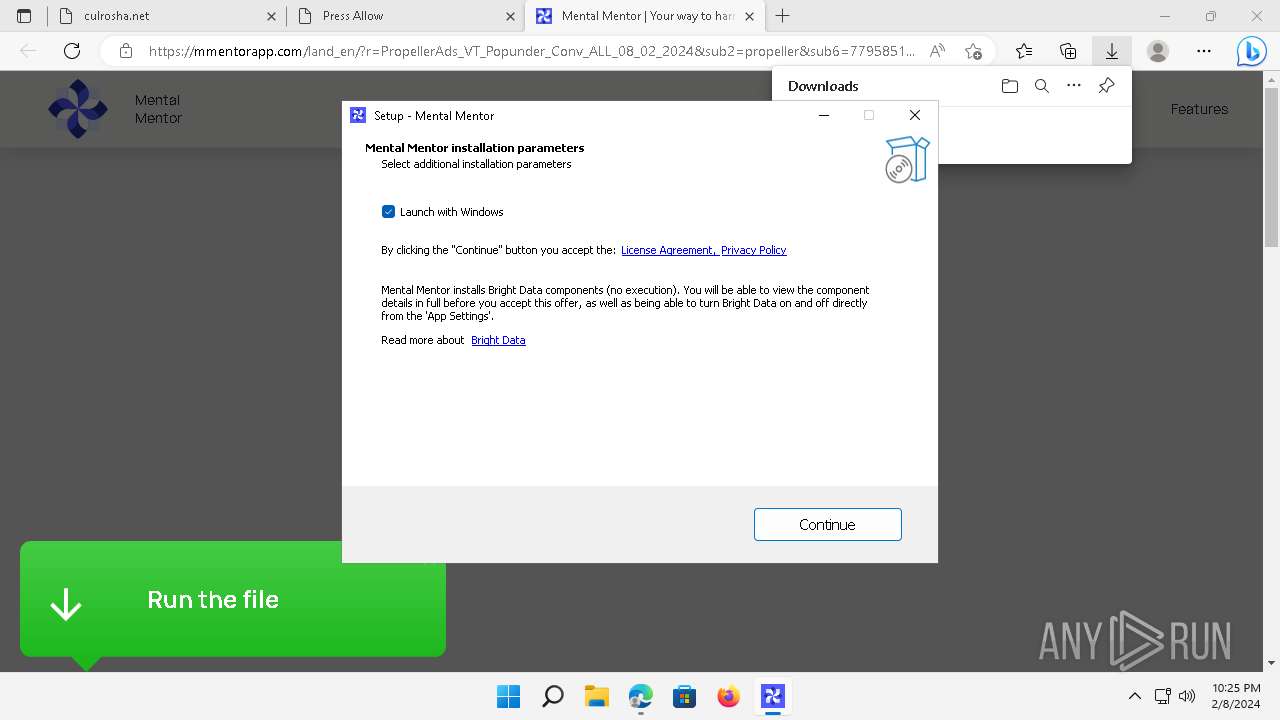
Drops the executable file immediately after the start
- MentalMentor.exe (PID: 6176)
- MentalMentor.tmp (PID: 608)
SUSPICIOUS
Reads the date of Windows installation
- MentalMentor.tmp (PID: 7128)
Executable content was dropped or overwritten
- MentalMentor.exe (PID: 6176)
- MentalMentor.tmp (PID: 608)
Reads the Windows owner or organization settings
- MentalMentor.tmp (PID: 608)
INFO
Application launched itself
- msedge.exe (PID: 5492)
Reads settings of System Certificates
- explorer.exe (PID: 4208)
Checks proxy server information
- explorer.exe (PID: 4208)
Checks supported languages
- MentalMentor.tmp (PID: 7128)
- MentalMentor.exe (PID: 6176)
- MentalMentor.tmp (PID: 608)
Reads the computer name
- MentalMentor.tmp (PID: 7128)
- MentalMentor.tmp (PID: 608)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4208)
Reads the Internet Settings
- explorer.exe (PID: 4208)
Create files in a temporary directory
- MentalMentor.exe (PID: 6176)
- MentalMentor.tmp (PID: 608)
Reads the machine GUID from the registry
- MentalMentor.tmp (PID: 608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
140
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | "C:\Users\admin\AppData\Local\Temp\is-N39UA.tmp\MentalMentor.tmp" /SL5="$502AE,2485361,845312,C:\Users\admin\Downloads\MentalMentor.exe" /SPAWNWND=$40022 /NOTIFYWND=$4028A | C:\Users\admin\AppData\Local\Temp\is-N39UA.tmp\MentalMentor.tmp | MentalMentor.exe | ||||||||||||
User: admin Company: Mental Mentor Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=111.0.5563.149 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=111.0.1661.62 --initial-client-data=0x114,0x118,0x11c,0xf0,0x128,0x7ff87ecab5f8,0x7ff87ecab608,0x7ff87ecab618 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 4208 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.22000.184 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5492 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "culrosha.net" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 6176 | "C:\Users\admin\Downloads\MentalMentor.exe" /SPAWNWND=$40022 /NOTIFYWND=$4028A | C:\Users\admin\Downloads\MentalMentor.exe | MentalMentor.tmp | ||||||||||||
User: admin Company: Mental Mentor Integrity Level: HIGH Description: Mental Mentor Setup Exit code: 0 Version: 1.0.3 Modules
| |||||||||||||||
| 7128 | "C:\Users\admin\AppData\Local\Temp\is-80CIJ.tmp\MentalMentor.tmp" /SL5="$4028A,2485361,845312,C:\Users\admin\Downloads\MentalMentor.exe" | C:\Users\admin\AppData\Local\Temp\is-80CIJ.tmp\MentalMentor.tmp | — | MentalMentor.exe | |||||||||||
User: admin Company: Mental Mentor Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
935
Read events
918
Write events
16
Delete events
1
Modification events
| (PID) Process: | (5492) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5492) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5492) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5492) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000F000000230000000DE11100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF00F356ADB82DDA0100000000 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000E7010000B6030000ABB6AE017B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000F000000240000000DE11100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF00F356ADB82DDA0100000000 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000E7010000B7030000ABB6AE017B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000F000000240000008DA91200000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF00F356ADB82DDA0100000000 | |||
| (PID) Process: | (4208) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000E7010000B70300002B7FAF017B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F007200650072000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B000000830000001C2736004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:3BA81BFAB5865A66309AA97D51DA831F | SHA256:E82365C7BE287704992CF9322966552D83DF37CBB9C5520108D9651270AC226D | |||
| 4208 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:84418143D4EA6C829486C2E0B588D9BB | SHA256:94941FD0417BF809EADC4CDA6234B1C07E8AA8403D2E264858A2747CFBFF02E3 | |||
| 608 | MentalMentor.tmp | C:\Users\admin\AppData\Local\Temp\is-1CNVB.tmp\idp.dll | executable | |
MD5:59FD376F6E67CF49BFB0AC6724140E72 | SHA256:88D2DA3783C9EF9B2C9F20224A399FE3607581F338DAEA94F68606A760CC06D5 | |||
| 608 | MentalMentor.tmp | C:\Users\admin\mentalmentor\settings\temp\install_config | binary | |
MD5:C5DC6C840F412CEF4138E0E627E2A28B | SHA256:2CDEB7F2A7173A59A6250BF3B70B51DD184E117A4D75A469B406B524D2D109E6 | |||
| 6176 | MentalMentor.exe | C:\Users\admin\AppData\Local\Temp\is-N39UA.tmp\MentalMentor.tmp | executable | |
MD5:45F499D08E2D25346D5EB2500ED37451 | SHA256:A451FE73D34CF289D39474E4DD10A9B62ED40F5756F8539A0ED1C658805342D9 | |||
| 608 | MentalMentor.tmp | C:\Users\admin\AppData\Local\Temp\is-1CNVB.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4208 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 4208 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:949FED1E11F10018496168583A194A41 | SHA256:172360B6C6B71B64A5D9CF2E04F9127A308B75BB3D97078C729FAB6D667516F2 | |||
| 608 | MentalMentor.tmp | C:\Users\admin\AppData\Local\Temp\is-1CNVB.tmp\mentor-inno-lib.dll | executable | |
MD5:D1E04ECA13E794B83E70010791E2F531 | SHA256:94BF0E63BC2DDDBAEA656E45F0585309CCF622C2C6416E063D9C6F640F496360 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
97
DNS requests
137
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
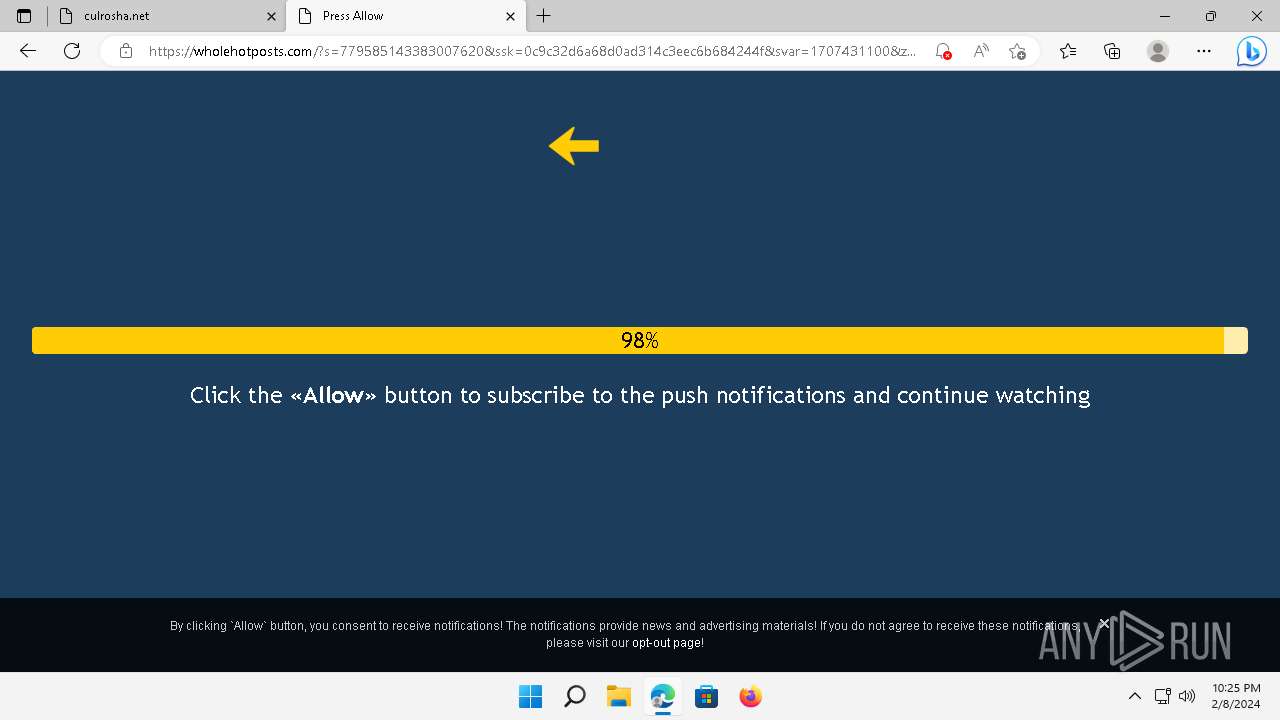
2664 | msedge.exe | GET | 204 | 139.45.197.245:80 | http://culrosha.net/favicon.ico | unknown | text | 8 b | unknown |
4208 | explorer.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9ae4749e0b26ffa9 | unknown | compressed | 4.66 Kb | unknown |
2664 | msedge.exe | GET | 200 | 139.45.197.245:80 | http://culrosha.net/ | unknown | text | 8 b | unknown |
3752 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1412 | svchost.exe | GET | 200 | 2.16.164.35:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | text | 22 b | unknown |
— | — | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5d2d1572e881002d | unknown | compressed | 65.2 Kb | unknown |
5944 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707937855&P2=404&P3=2&P4=UWXqnOZDfC9FOiEJDumOIvvqw0wyEpLEXgAAZ4o3WTli32kXbXBFDsxeVlugQc2%2fmqTD123OQCw7wQ2YK8OJFg%3d%3d | unknown | — | — | unknown |
2664 | msedge.exe | GET | 200 | 139.45.197.245:80 | http://culrosha.net/4/6911541 | unknown | html | 724 b | unknown |
5944 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707937855&P2=404&P3=2&P4=UWXqnOZDfC9FOiEJDumOIvvqw0wyEpLEXgAAZ4o3WTli32kXbXBFDsxeVlugQc2%2fmqTD123OQCw7wQ2YK8OJFg%3d%3d | unknown | binary | 1.09 Kb | unknown |
5944 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707937855&P2=404&P3=2&P4=UWXqnOZDfC9FOiEJDumOIvvqw0wyEpLEXgAAZ4o3WTli32kXbXBFDsxeVlugQc2%2fmqTD123OQCw7wQ2YK8OJFg%3d%3d | unknown | binary | 1.75 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4588 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2664 | msedge.exe | 13.107.43.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2664 | msedge.exe | 94.245.104.56:443 | api.edgeoffer.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2664 | msedge.exe | 139.45.197.245:80 | culrosha.net | RETN Limited | GB | unknown |
4208 | explorer.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2664 | msedge.exe | 131.253.33.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5180 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
2664 | msedge.exe | 104.126.37.160:443 | edgeservices.bing.com | Akamai International B.V. | DE | unknown |
2664 | msedge.exe | 152.199.21.175:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
1412 | svchost.exe | 2.16.164.42:80 | — | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.edgeoffer.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
culrosha.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www2.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1412 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
2664 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2664 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
Process | Message |
|---|---|
msedge.exe | [0208/222427.782:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|