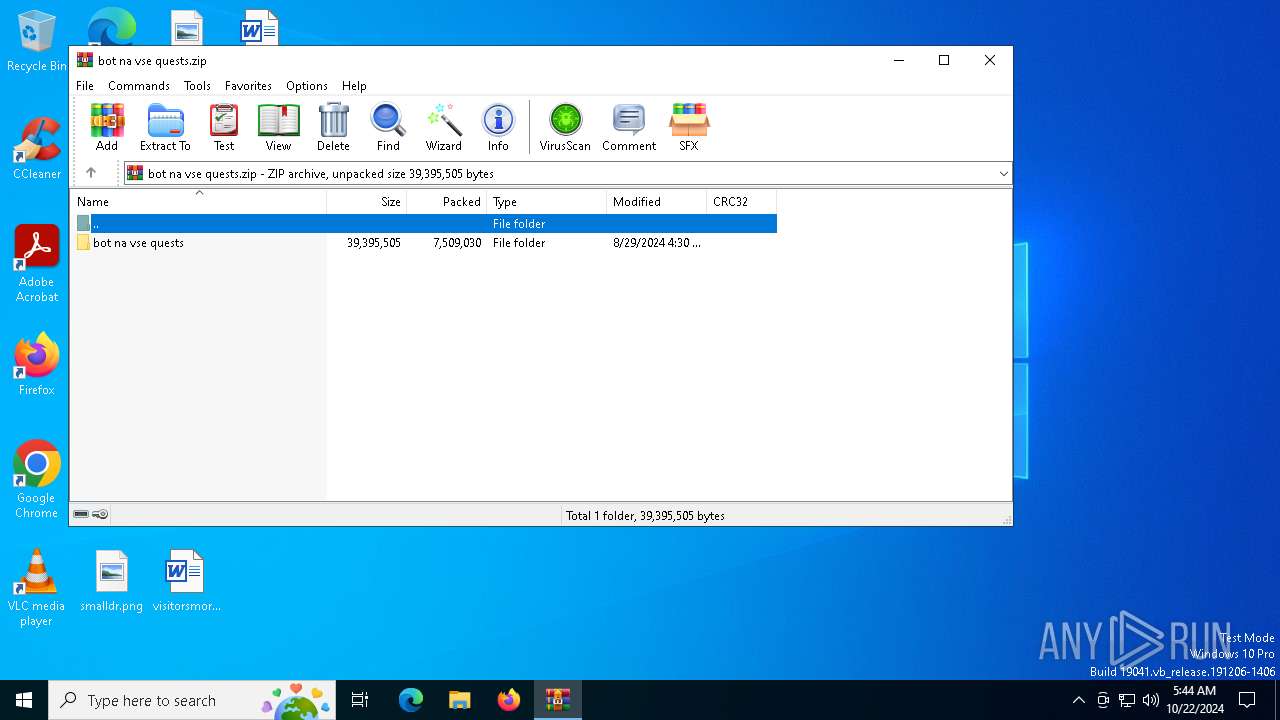
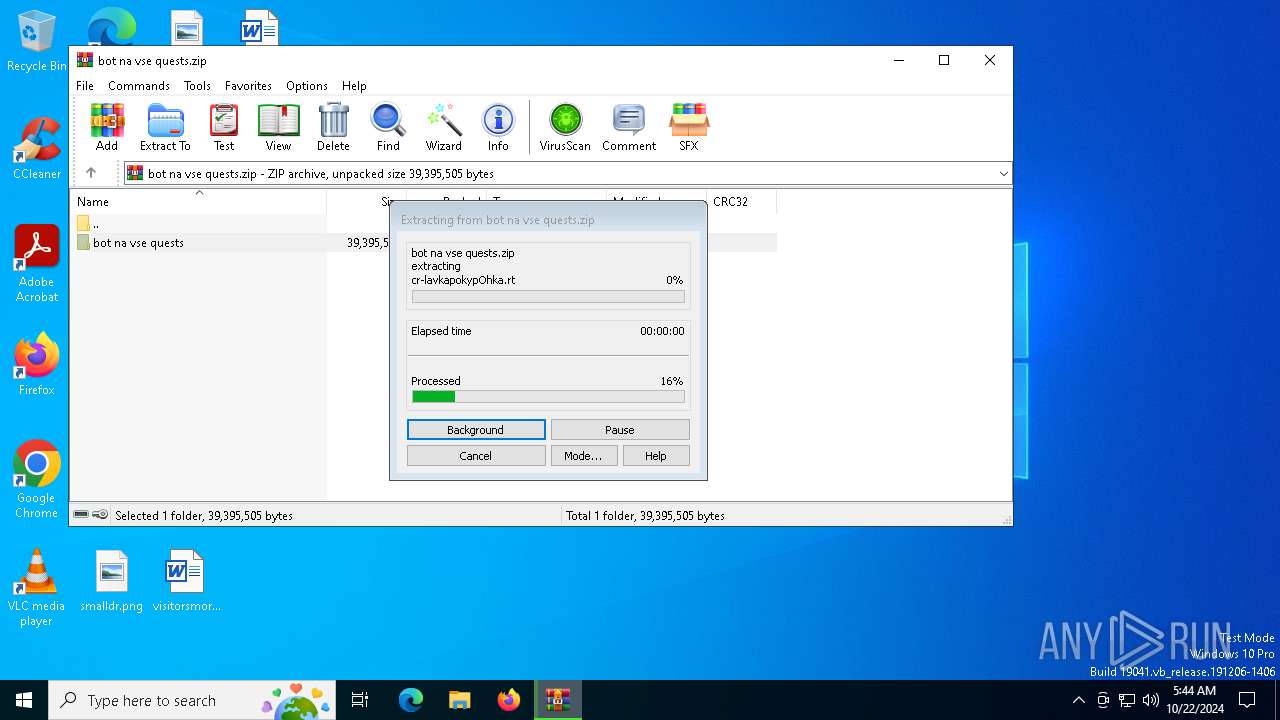
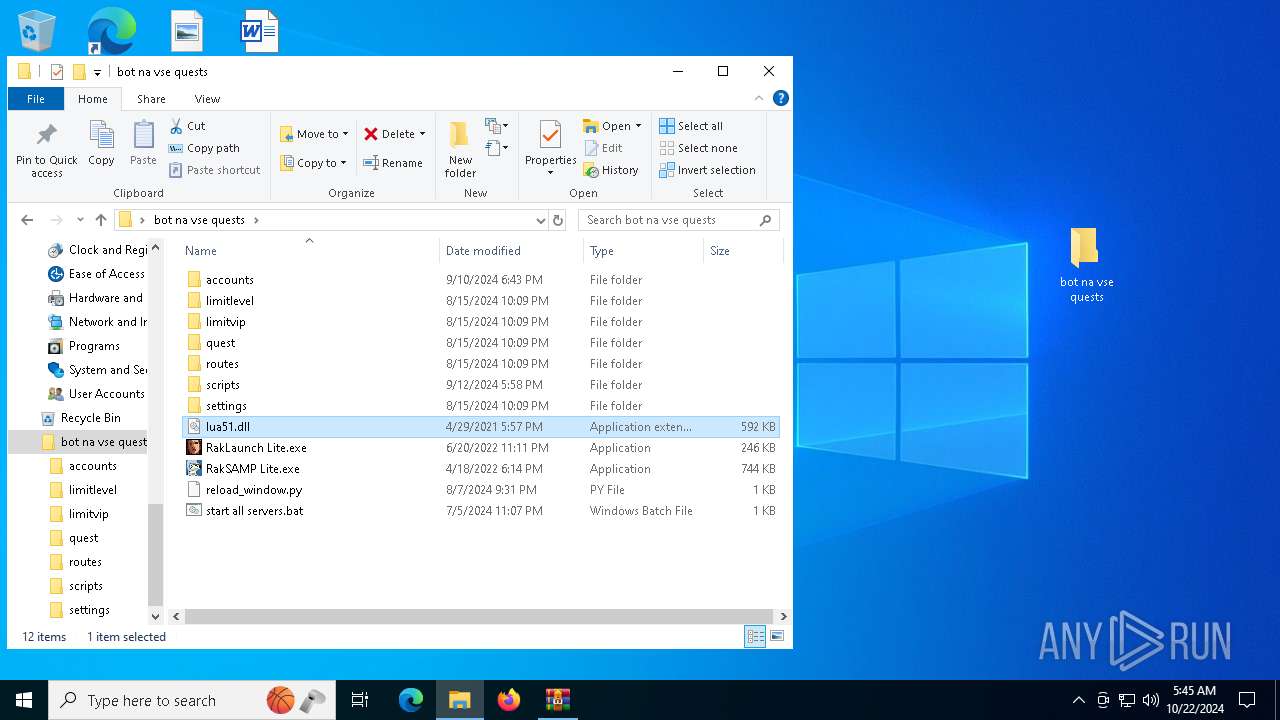
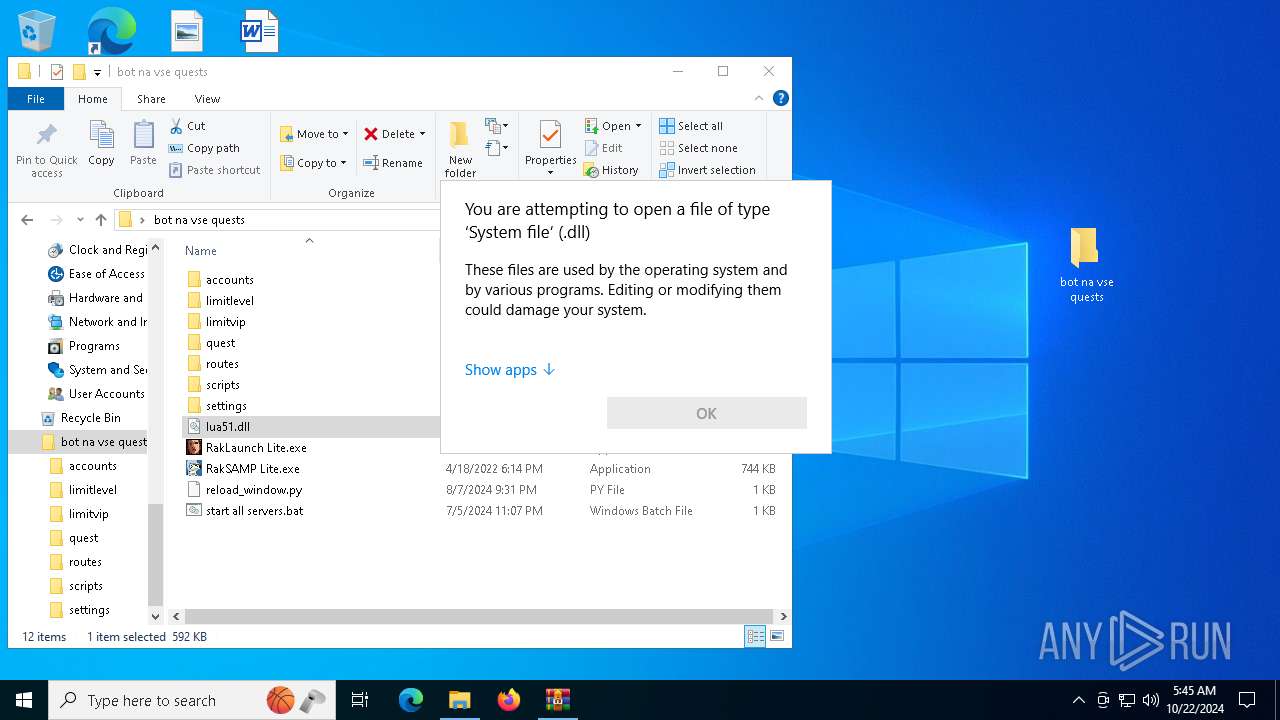
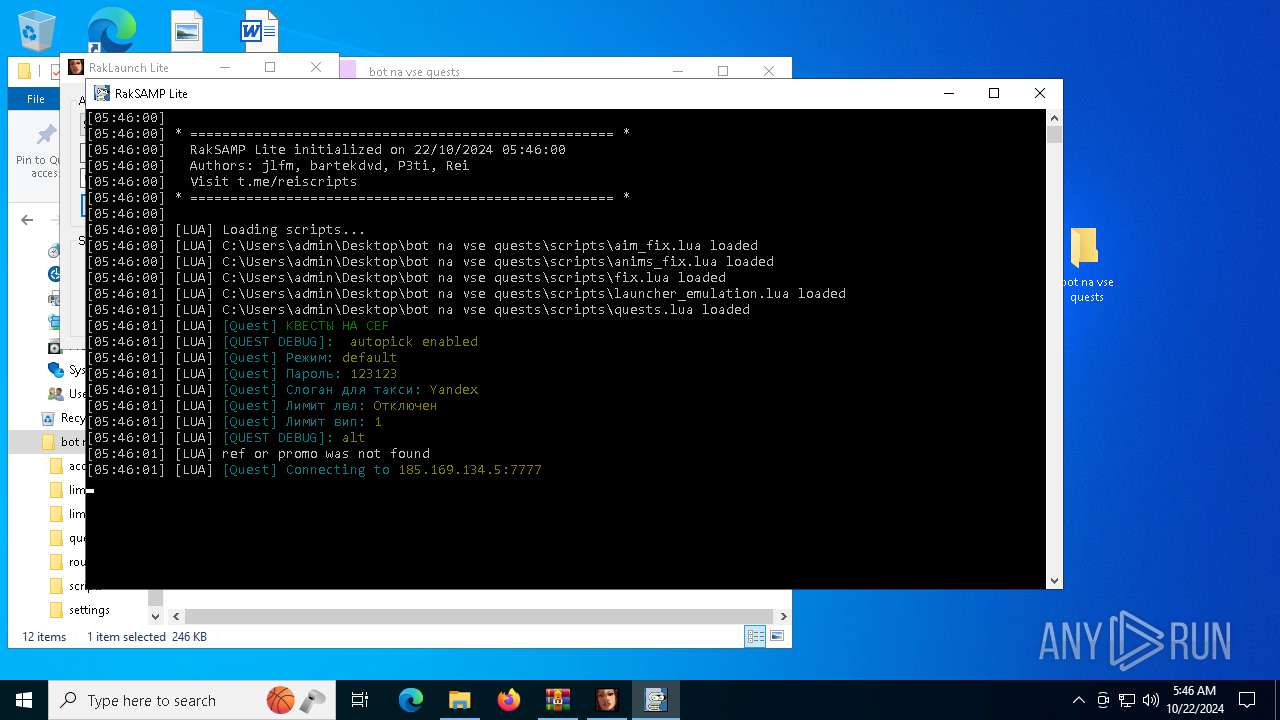
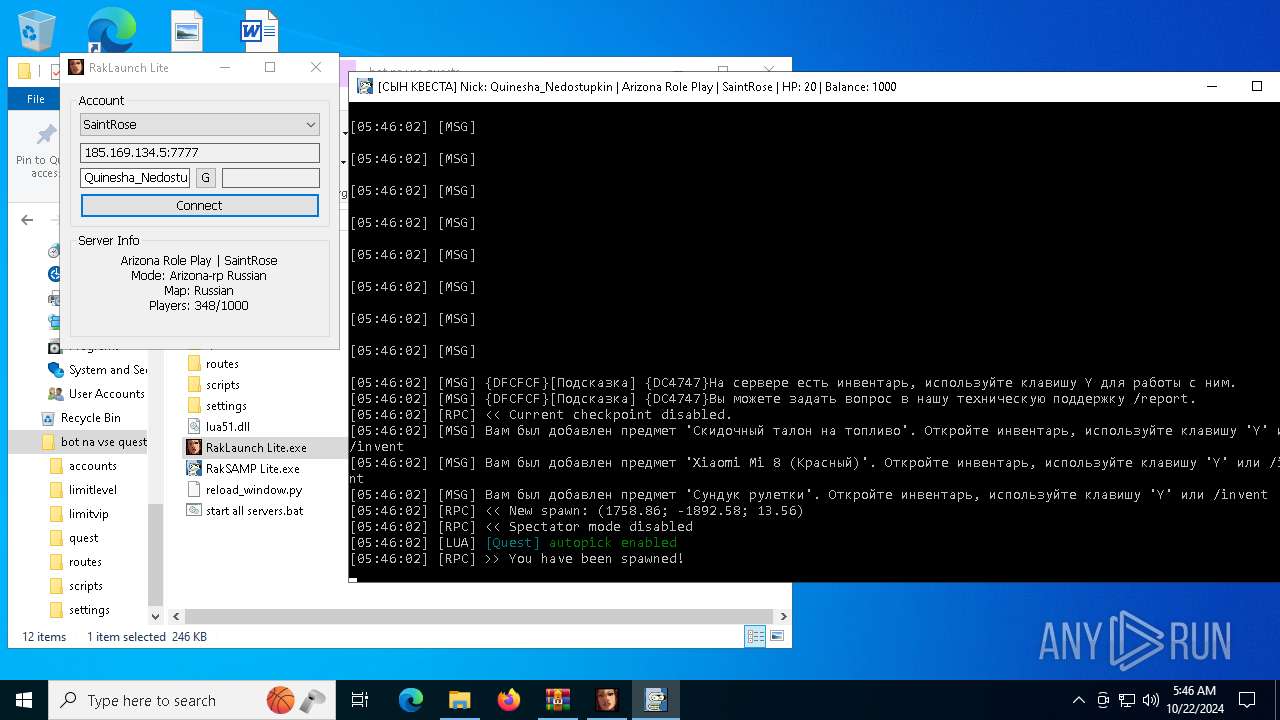
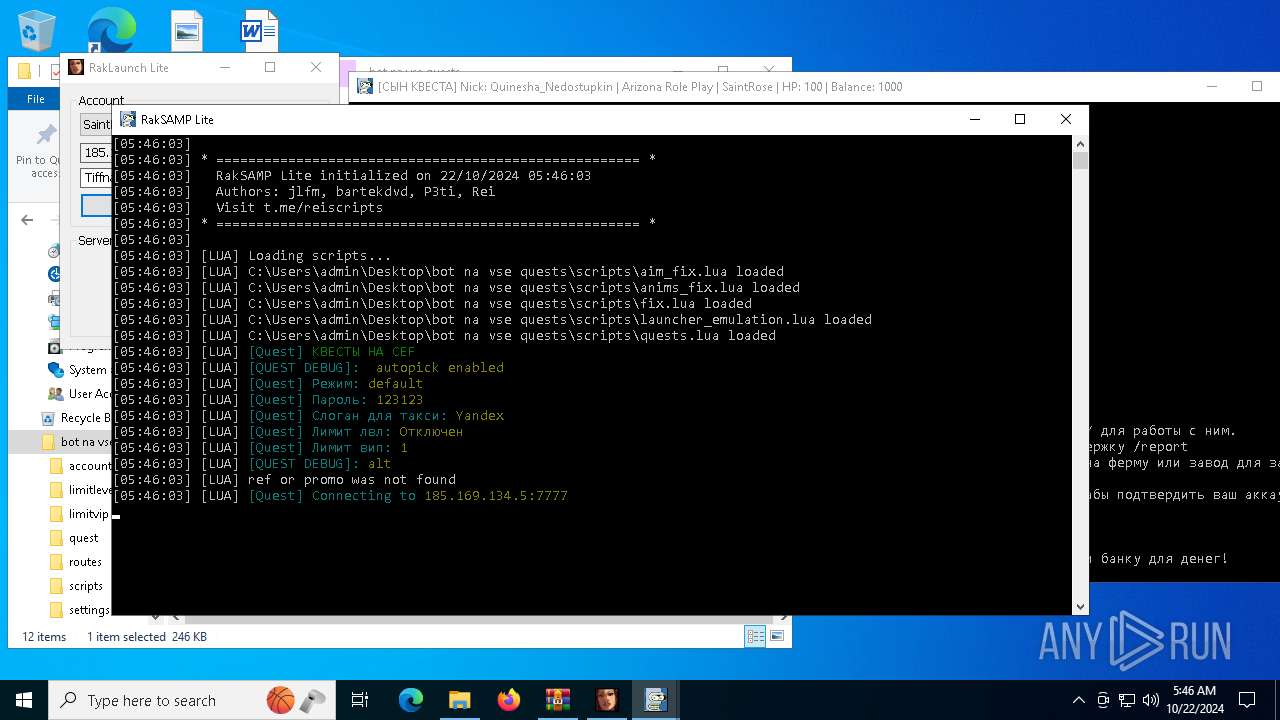
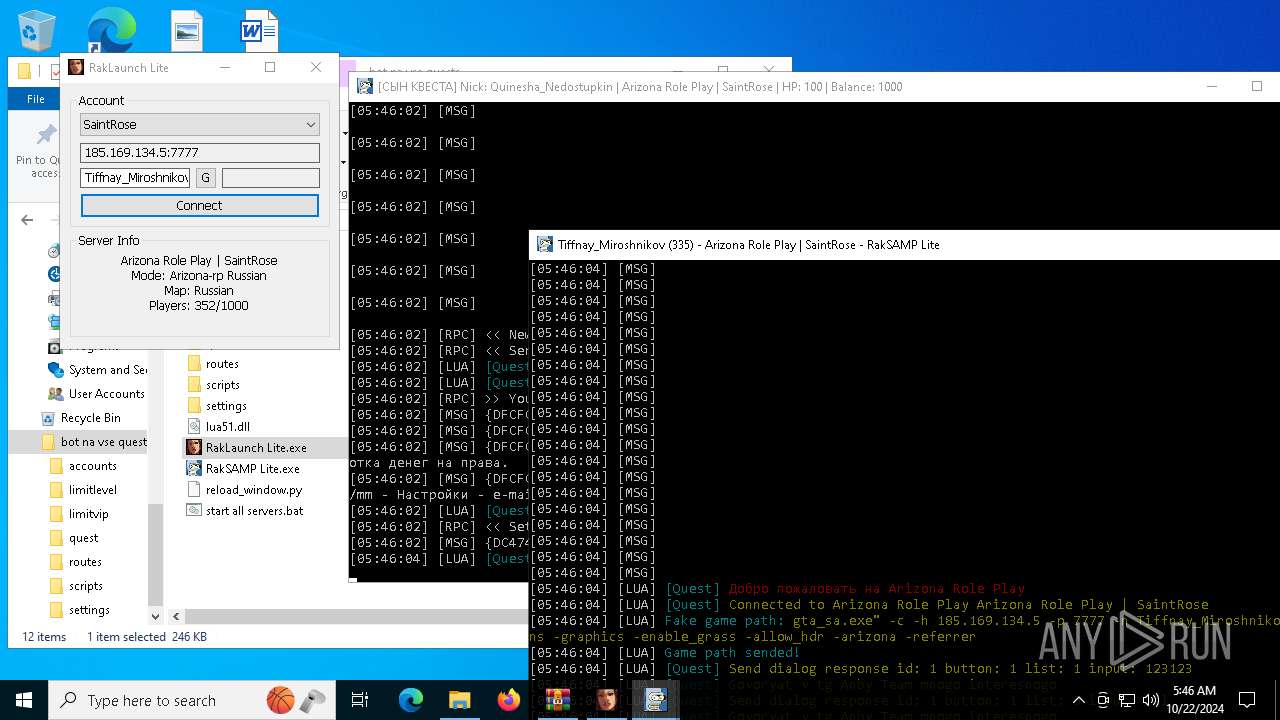
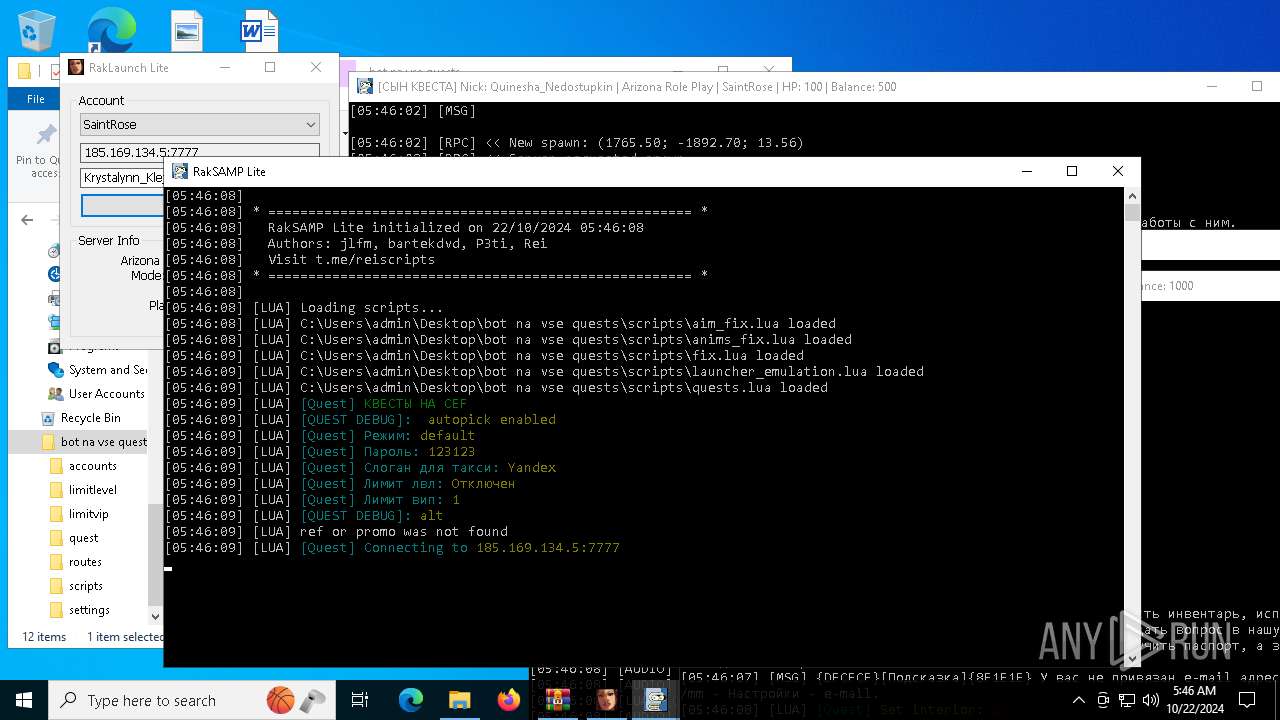
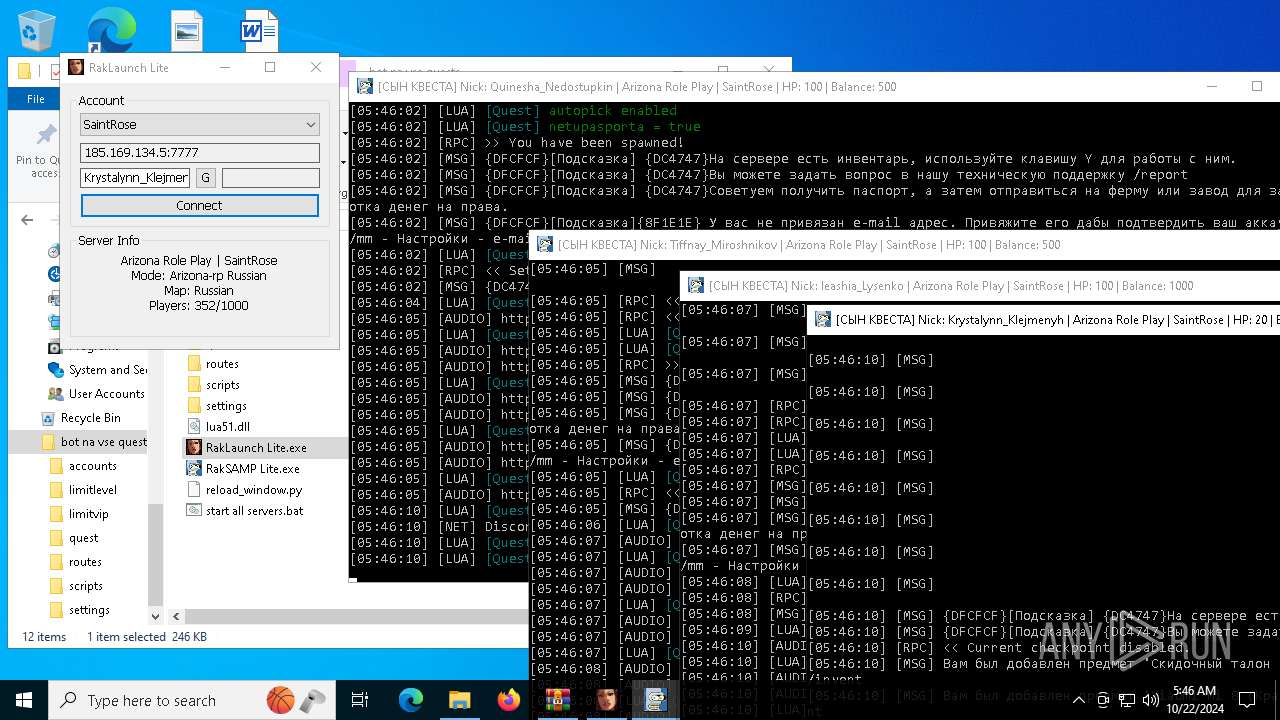
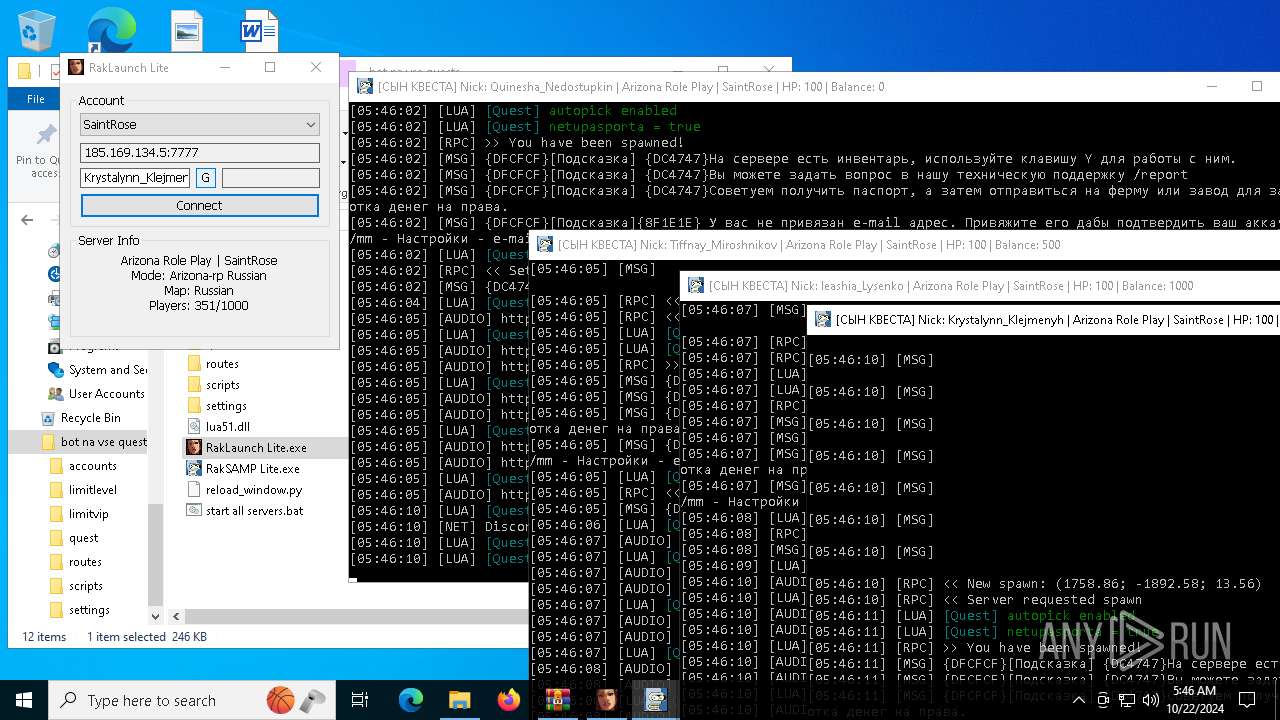
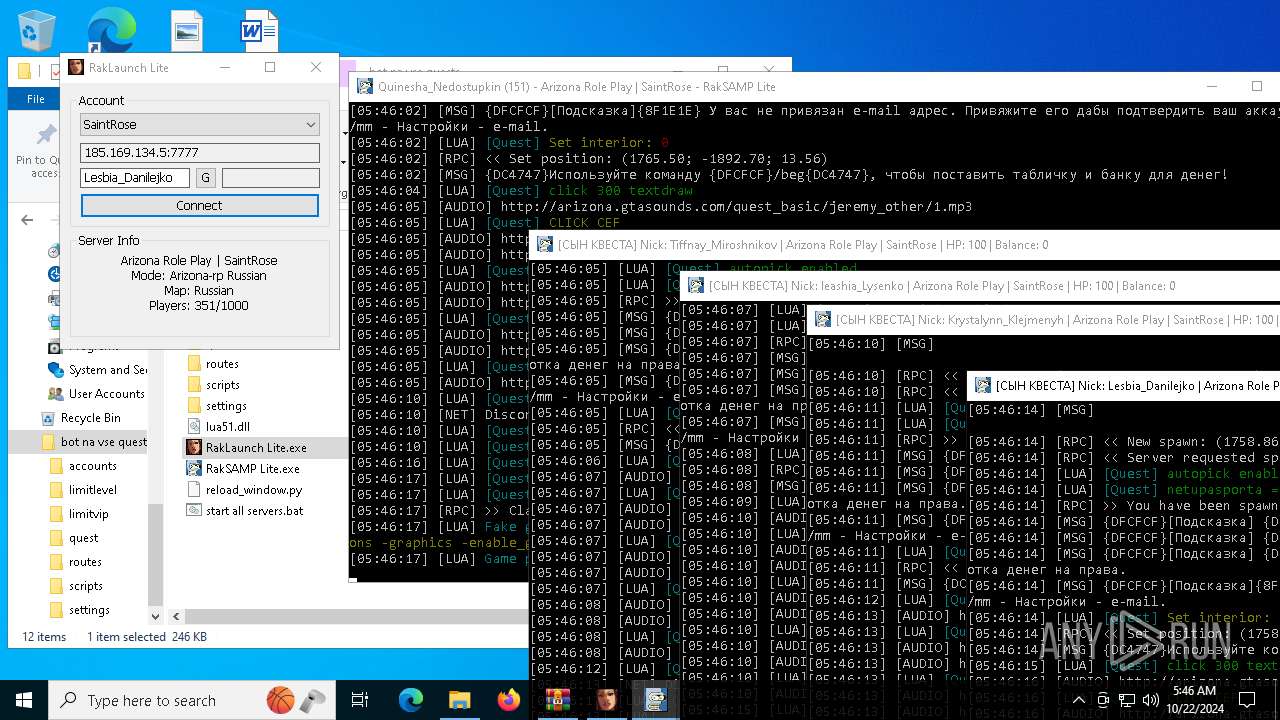
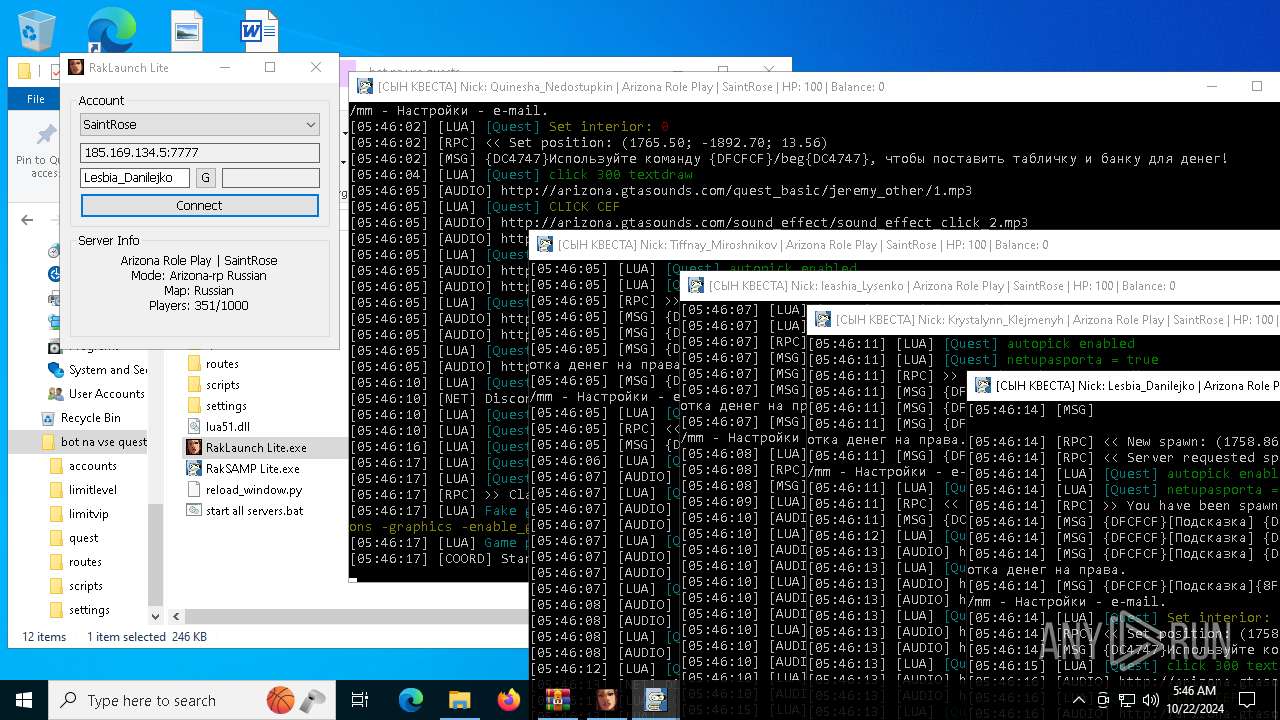
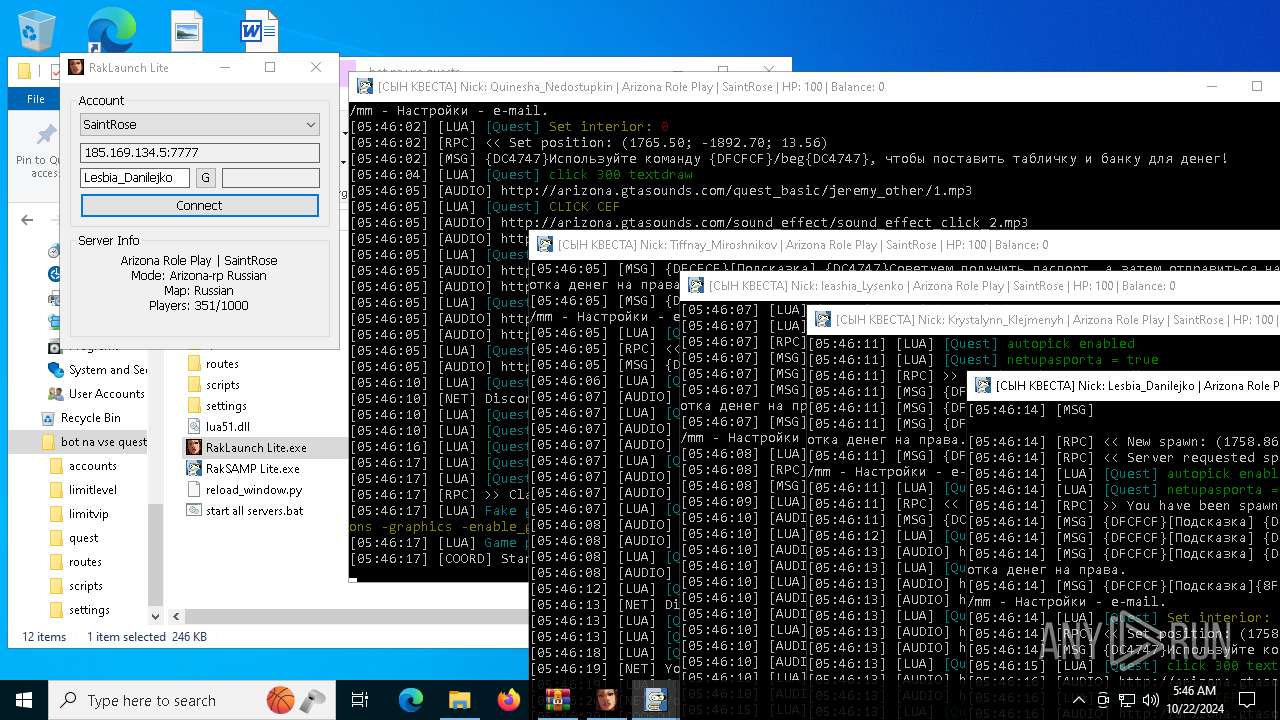
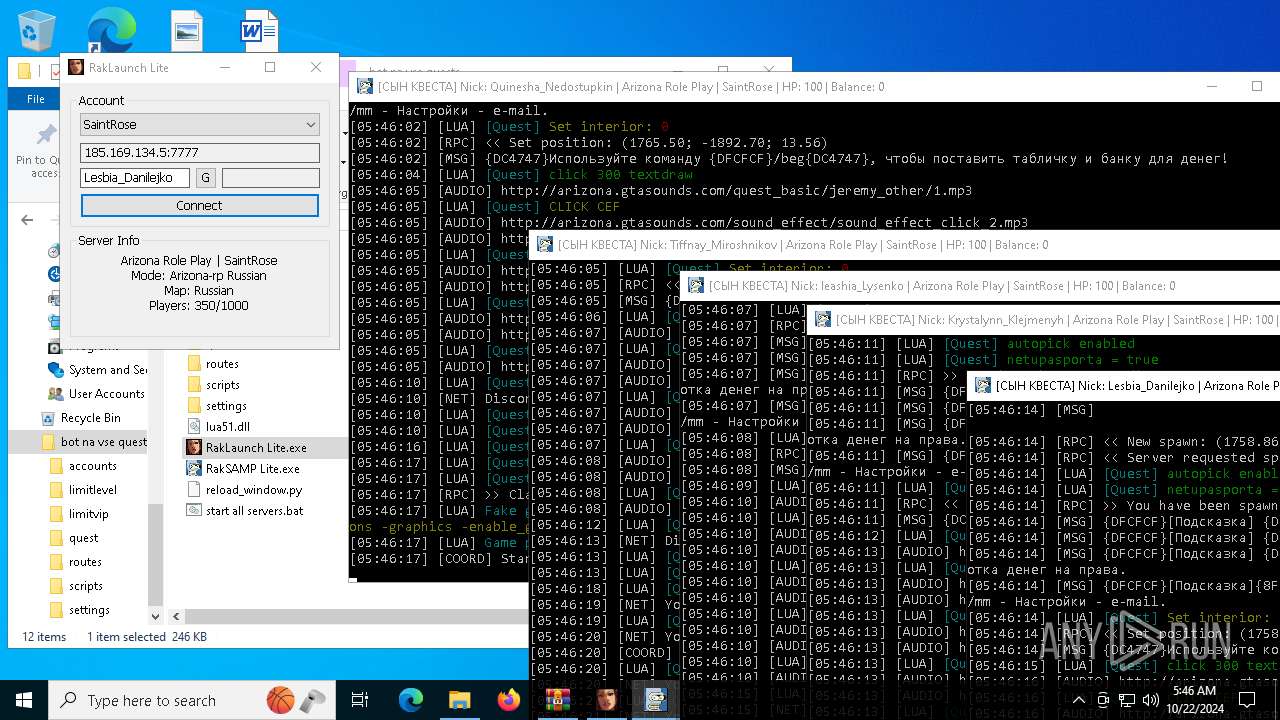
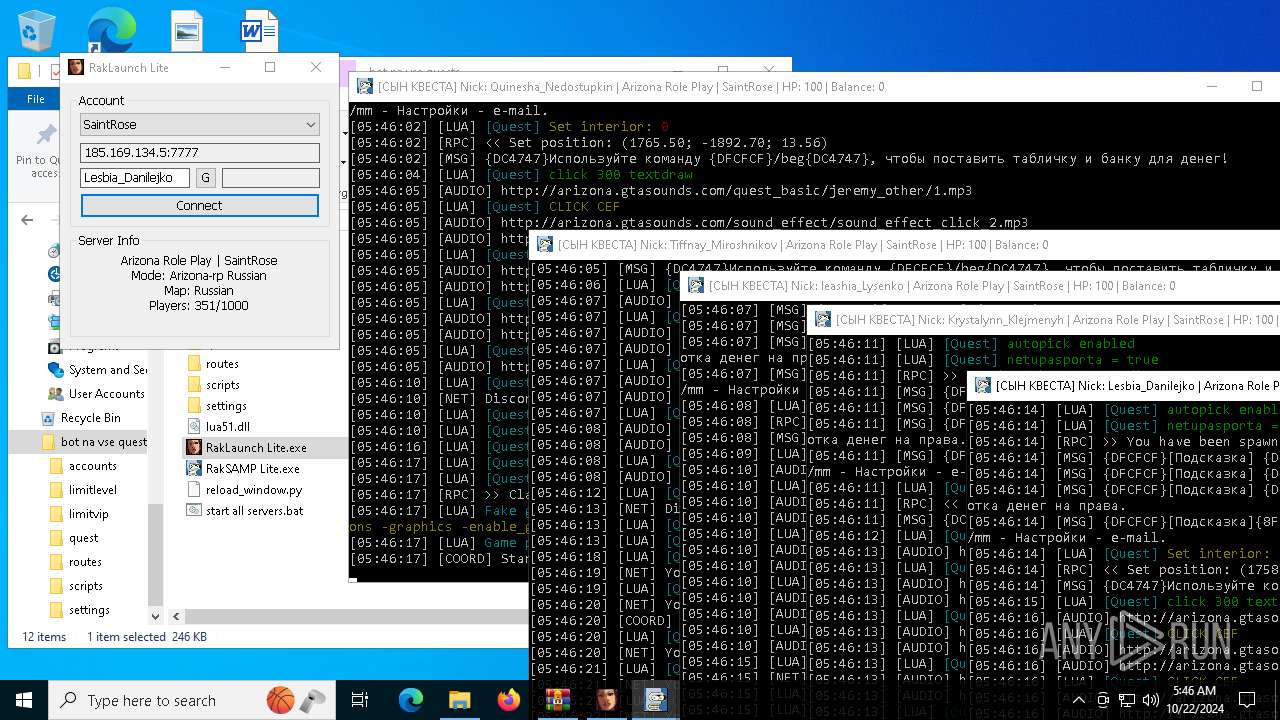
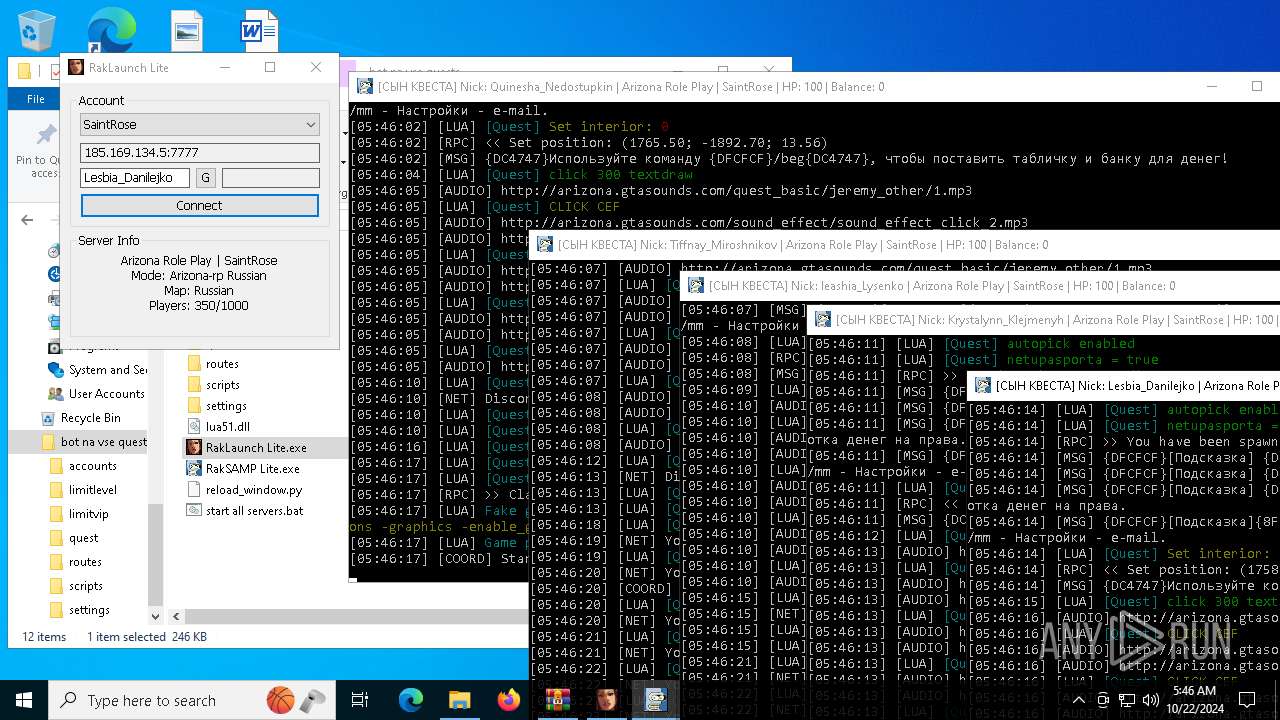
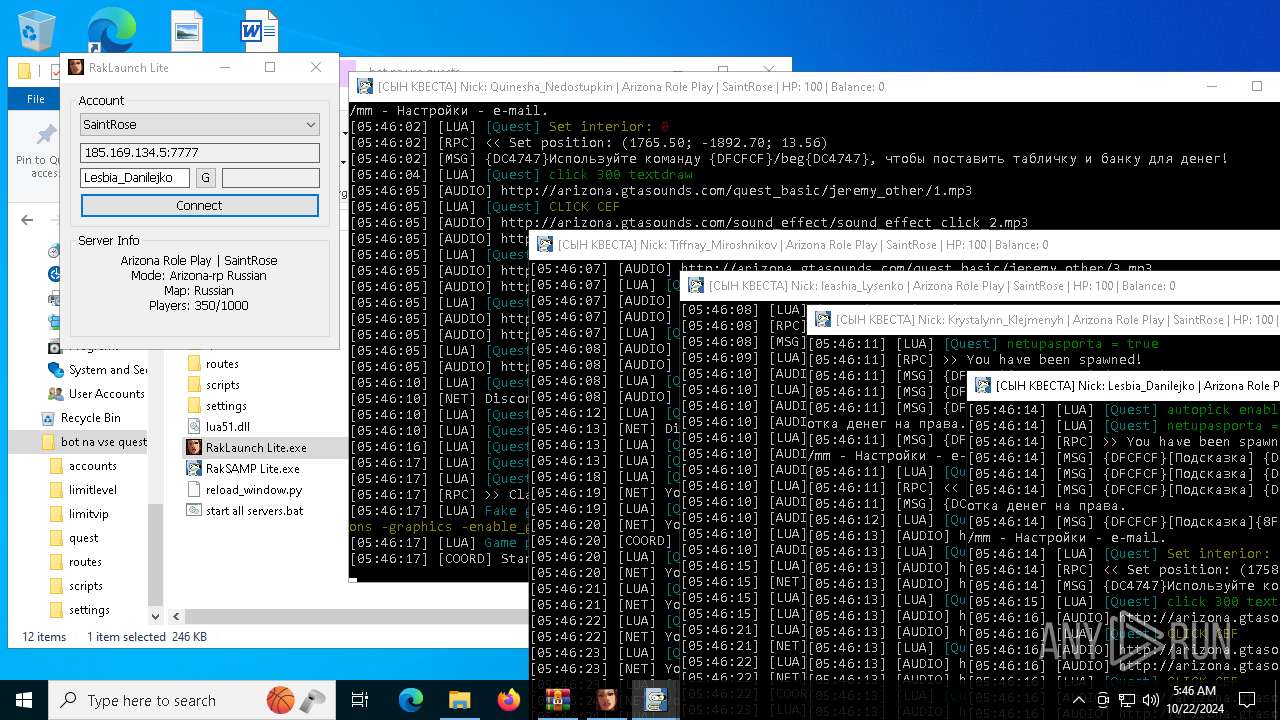
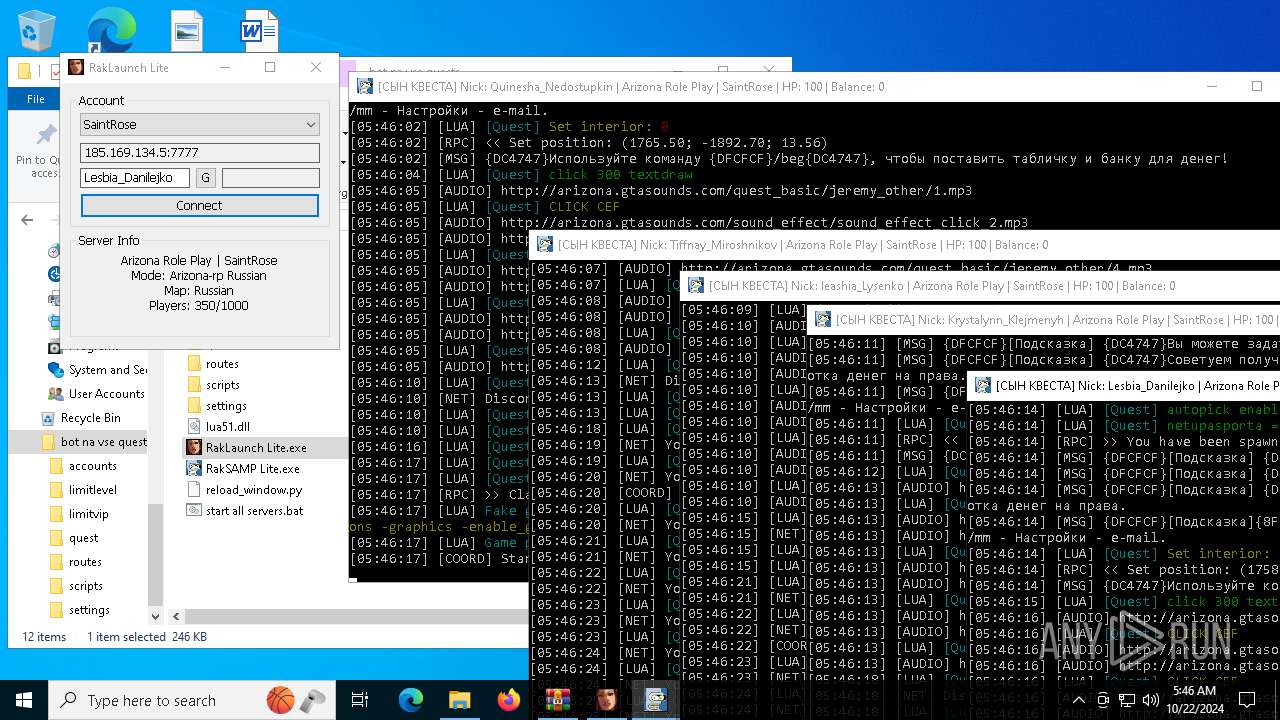
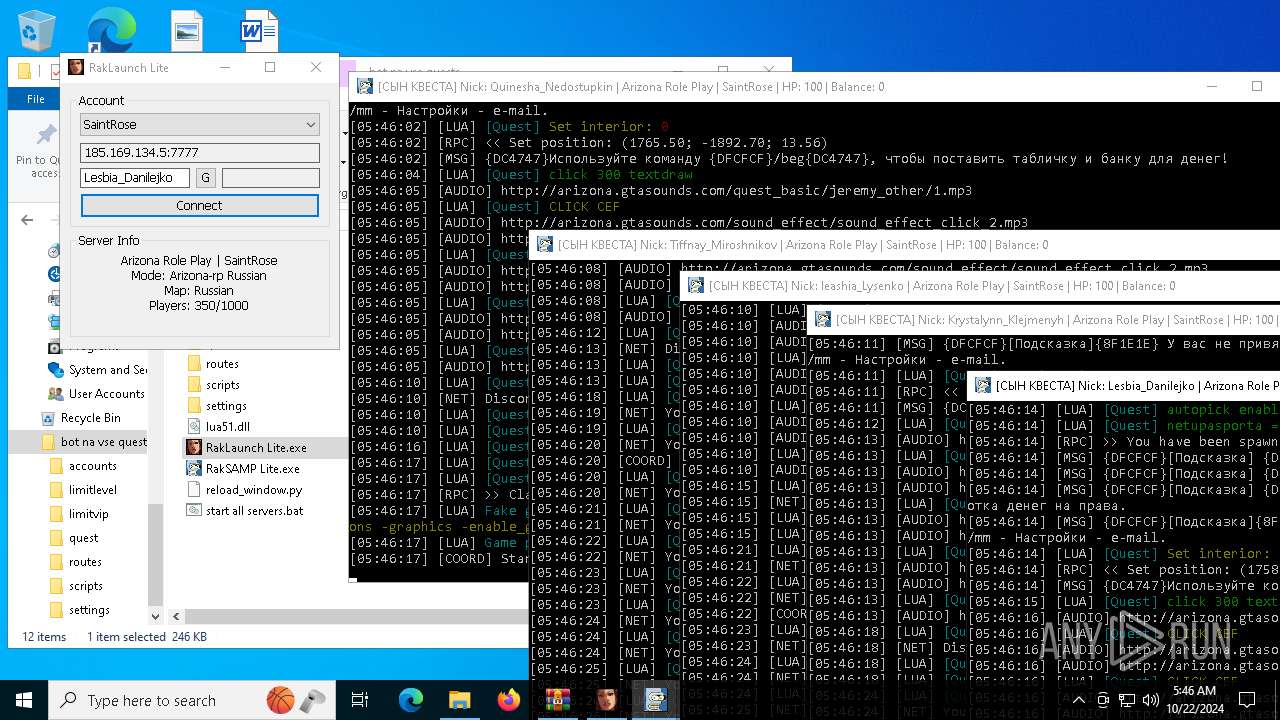
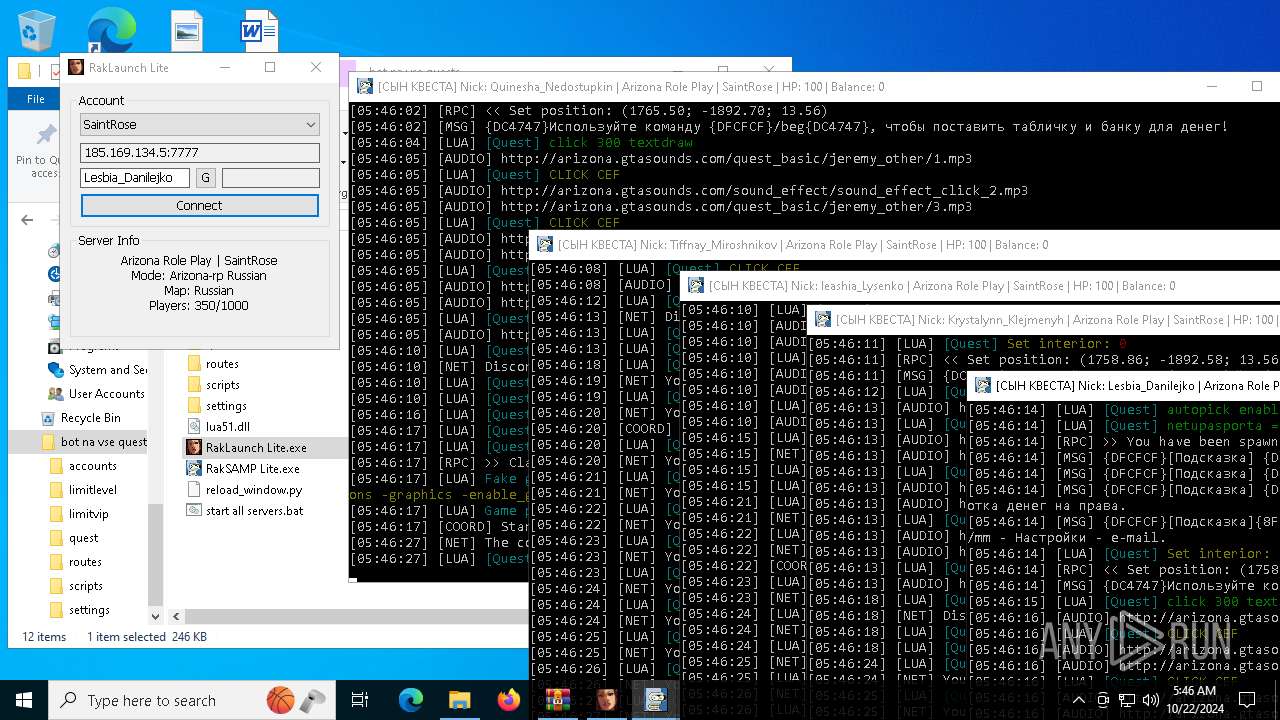
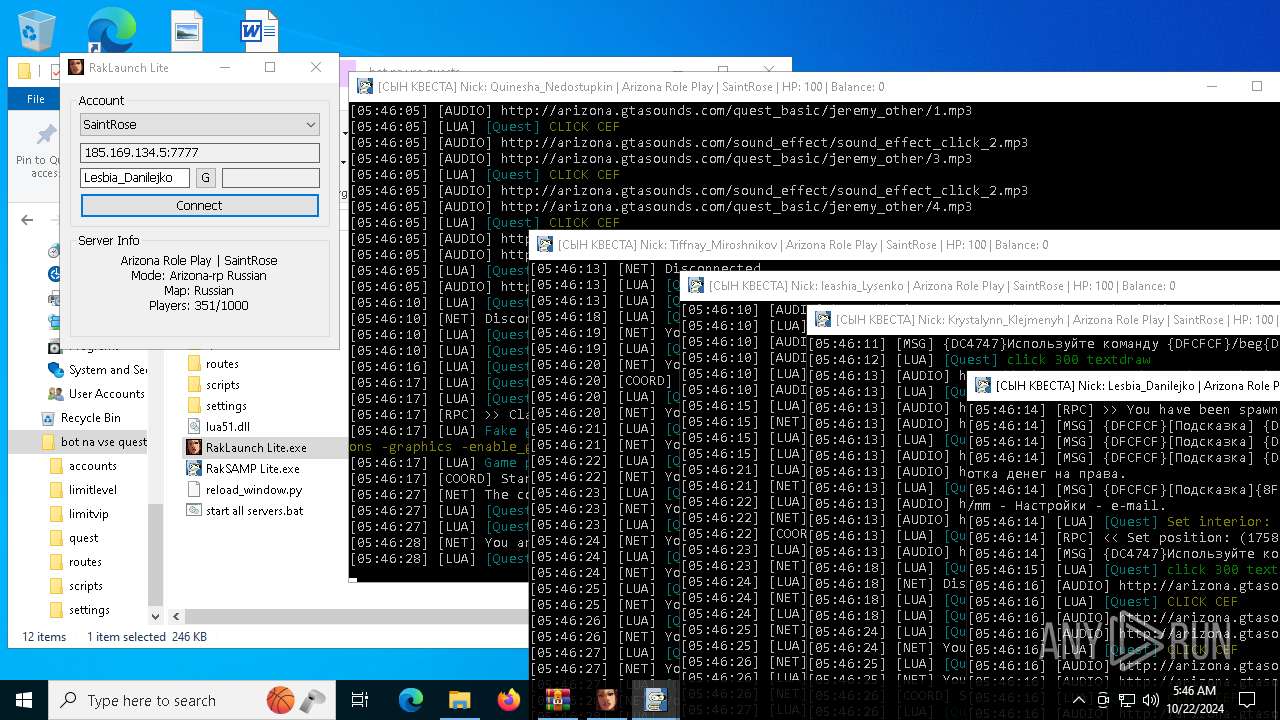
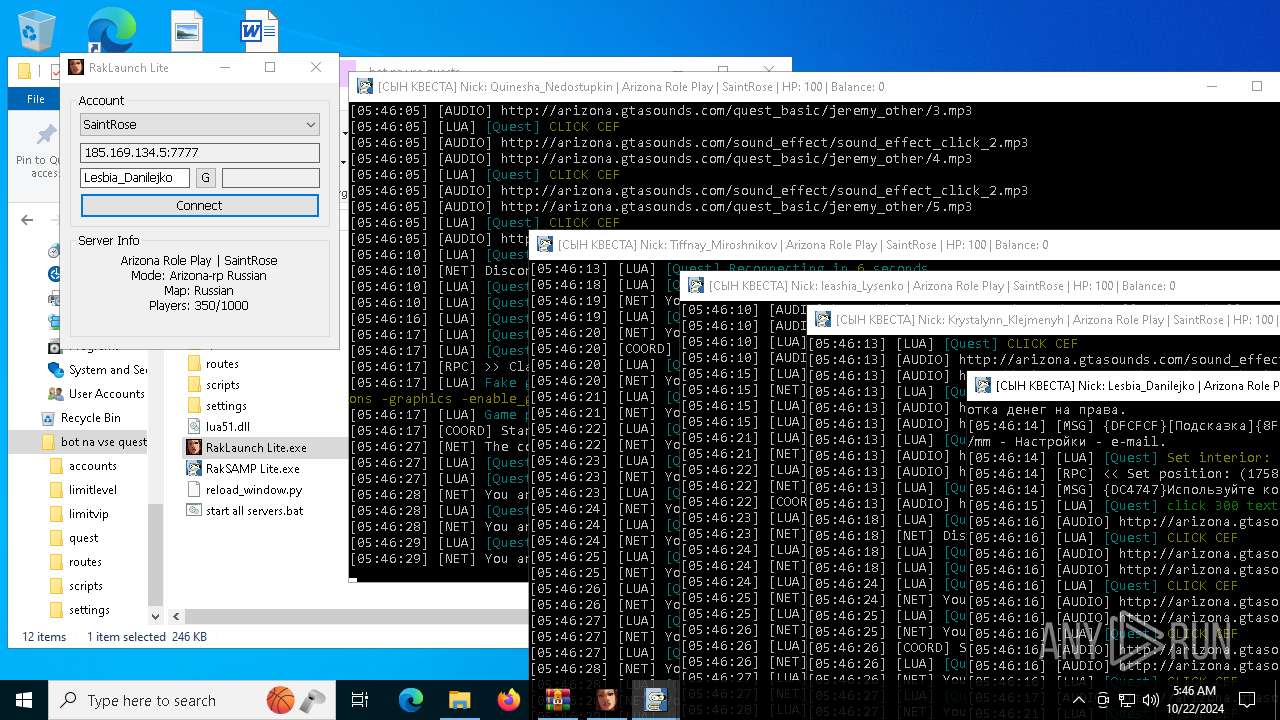
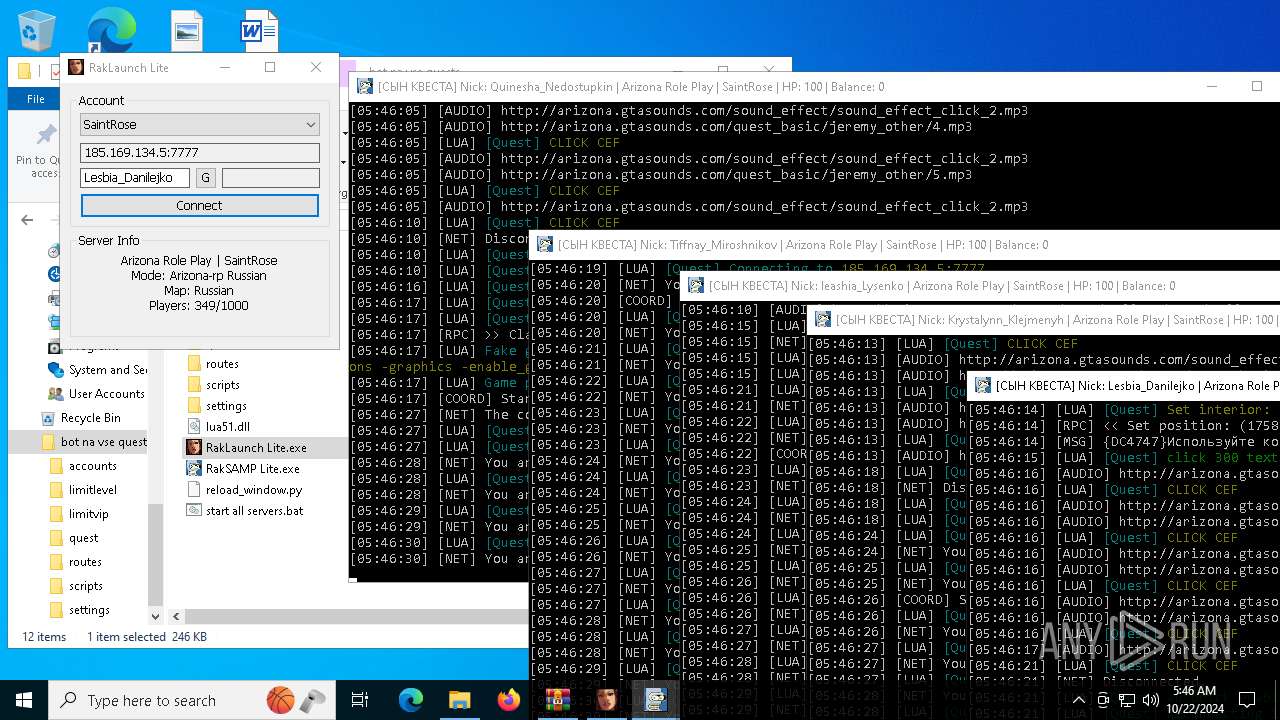
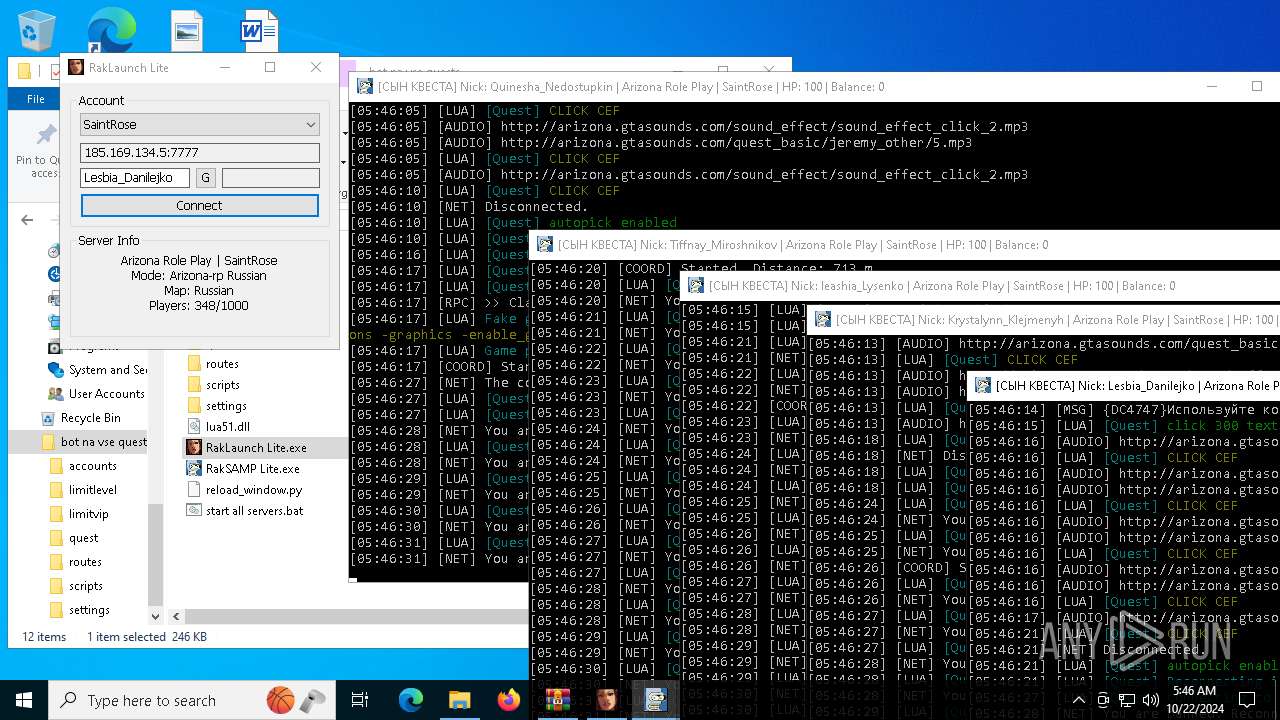
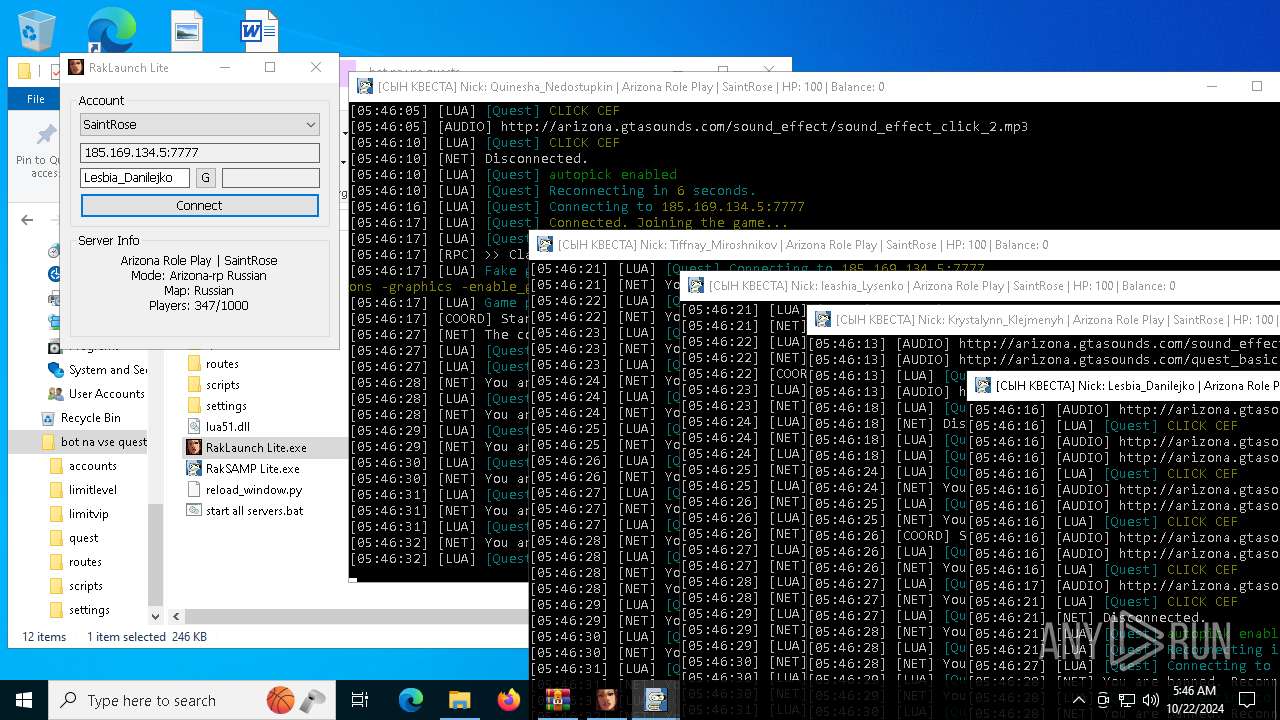
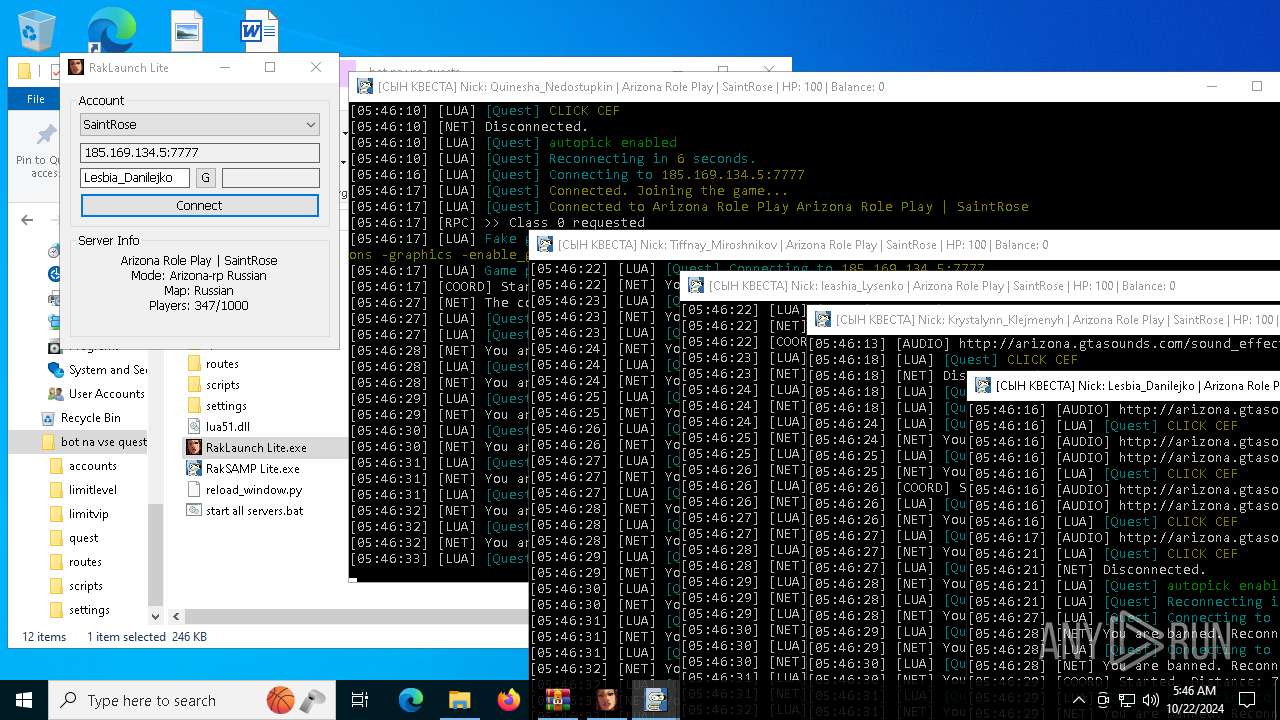
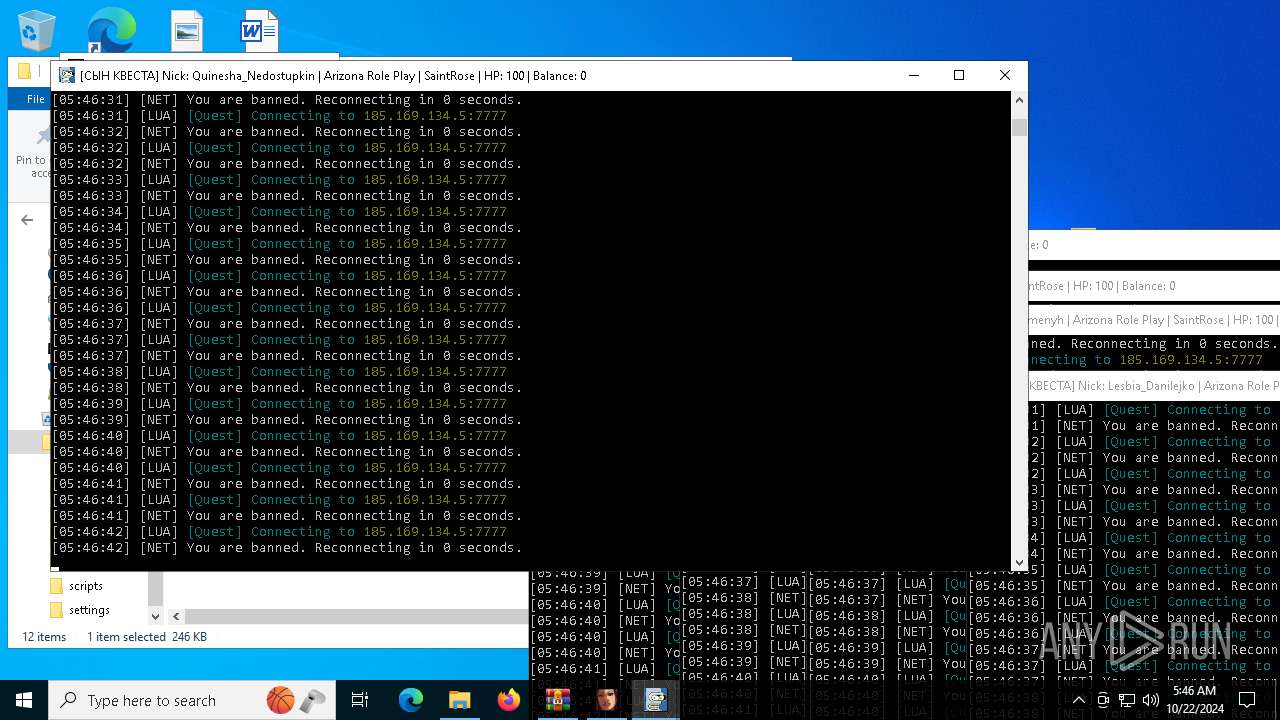
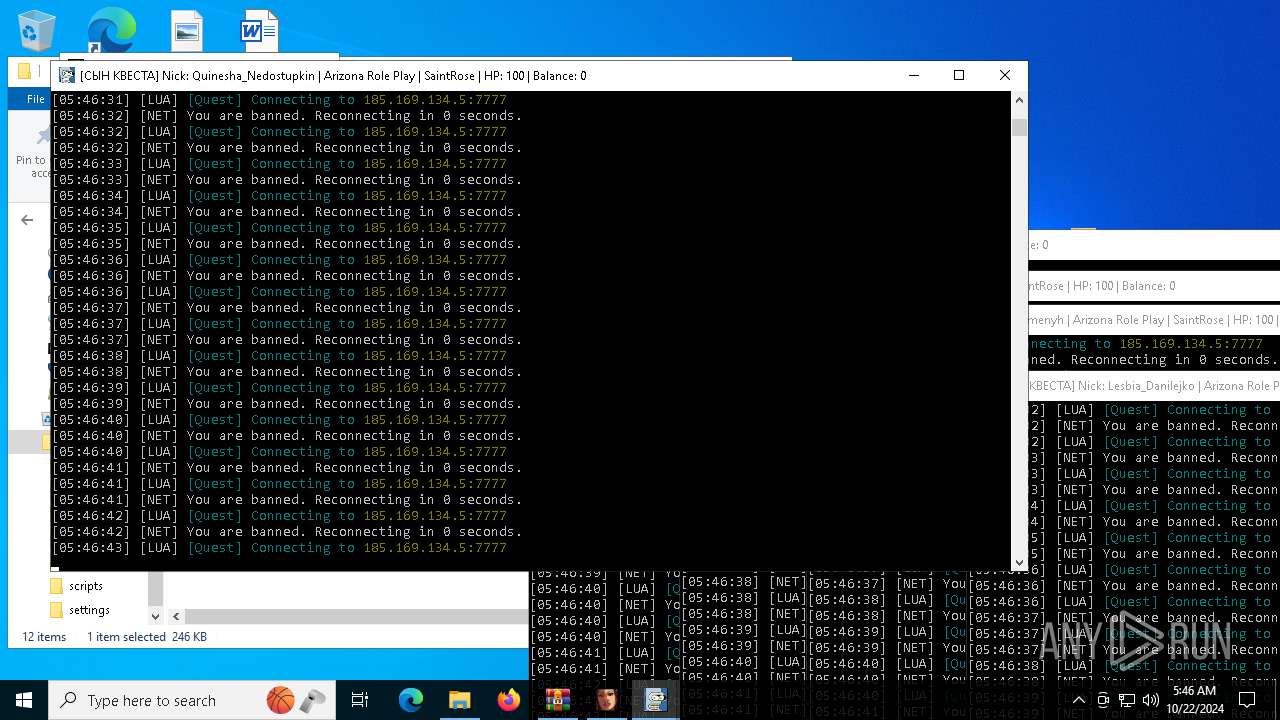
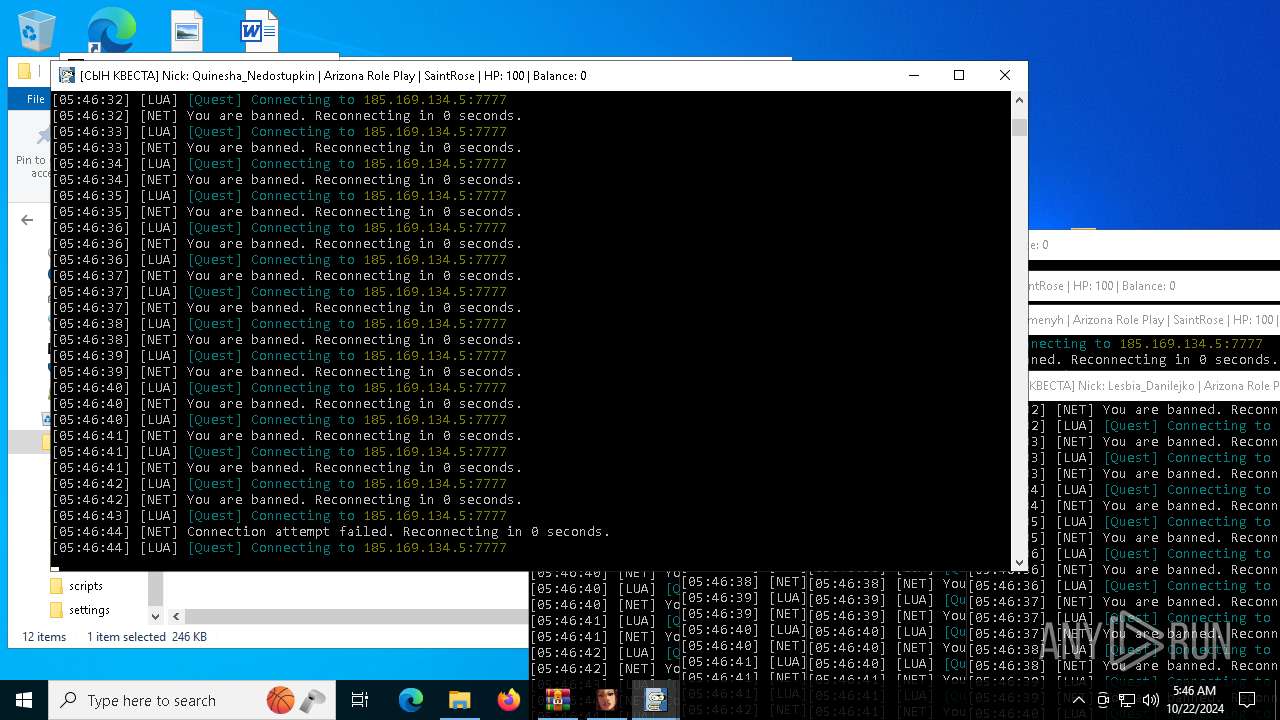
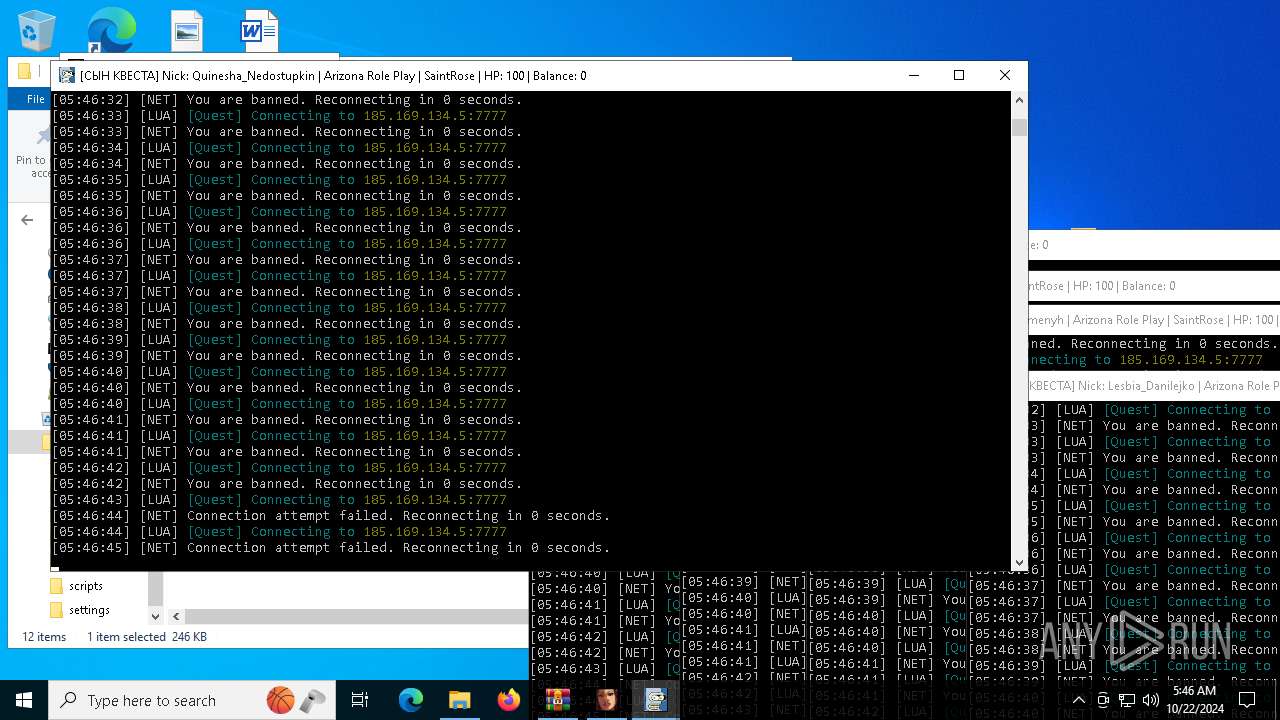
| File name: | bot na vse quests.zip |
| Full analysis: | https://app.any.run/tasks/4501ea28-ff2f-40e4-bbb8-f20bfc81d0fa |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 05:44:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | F50252C3AE9EA8539B64E47707EDE435 |
| SHA1: | 3F147B9E1572E9A5F4535C865D9D725CC3C71AA6 |
| SHA256: | F9D7BE5C4E3E6F4D4E4ECD9B070827DFF8CD05CD2FC1FF2F7BE6E65C79B835AC |
| SSDEEP: | 98304:IlIYYwKkg1a9cIXYPnoWWCNEd9jcAEsBkDTZnVVFgDFqzzYKkygl25uD+DRpPBxa:e7CbQTOoZsG7 |
MALICIOUS
Generic archive extractor
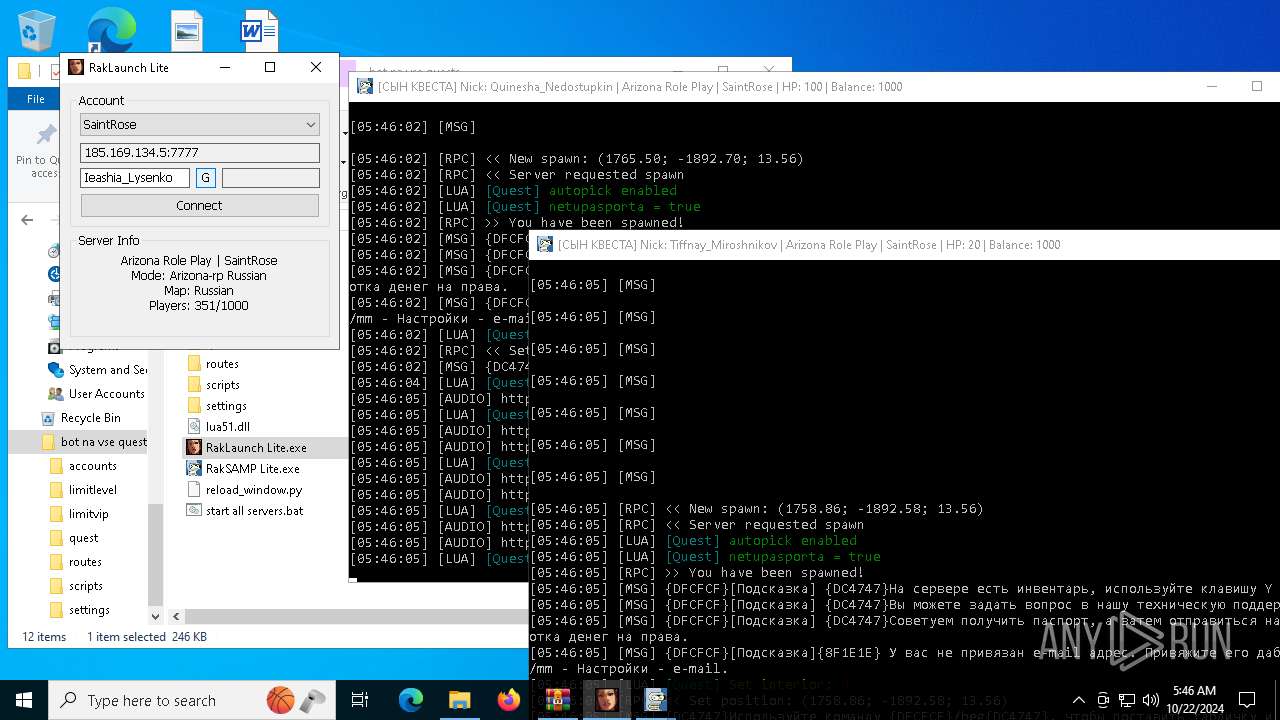
- WinRAR.exe (PID: 6596)
SUSPICIOUS
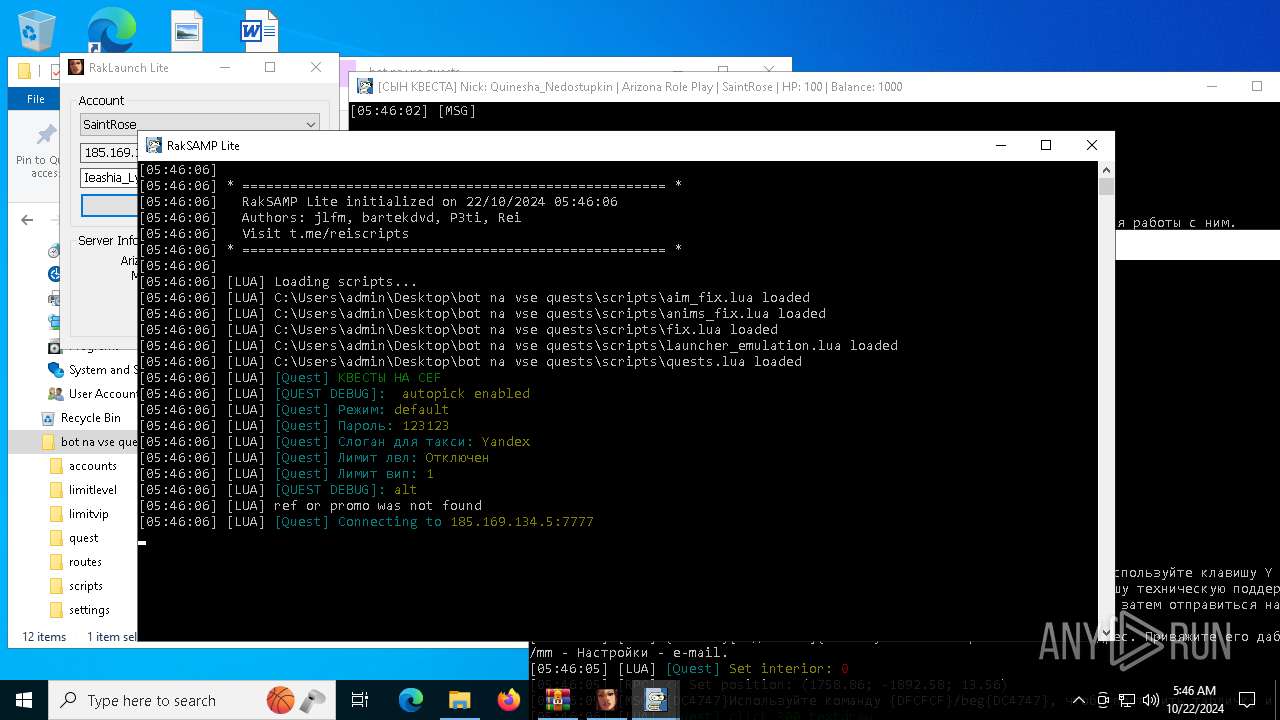
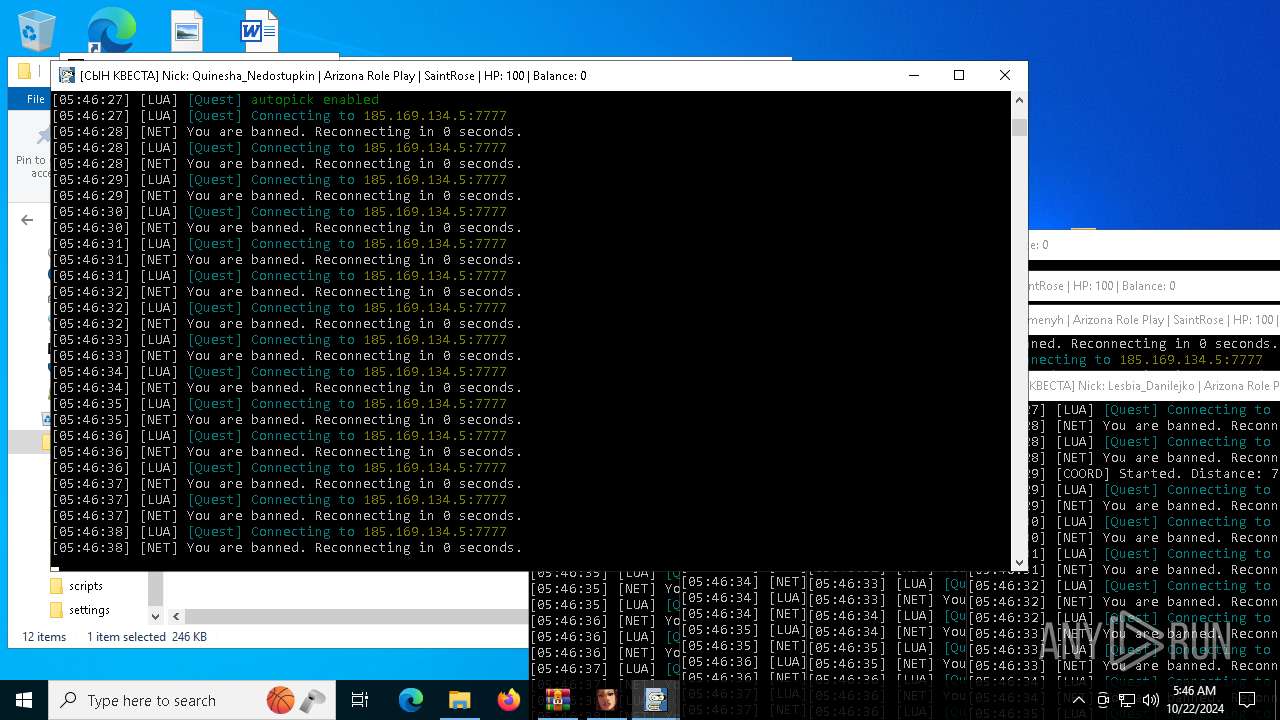
Starts CMD.EXE for commands execution
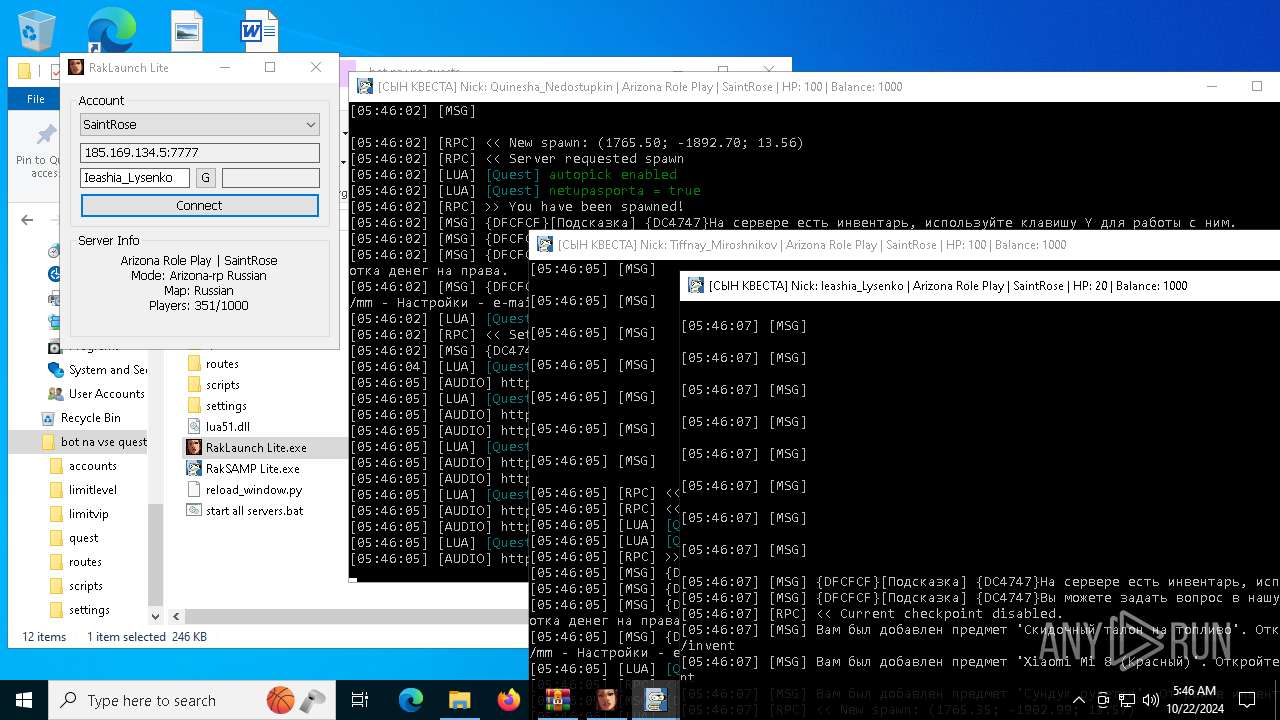
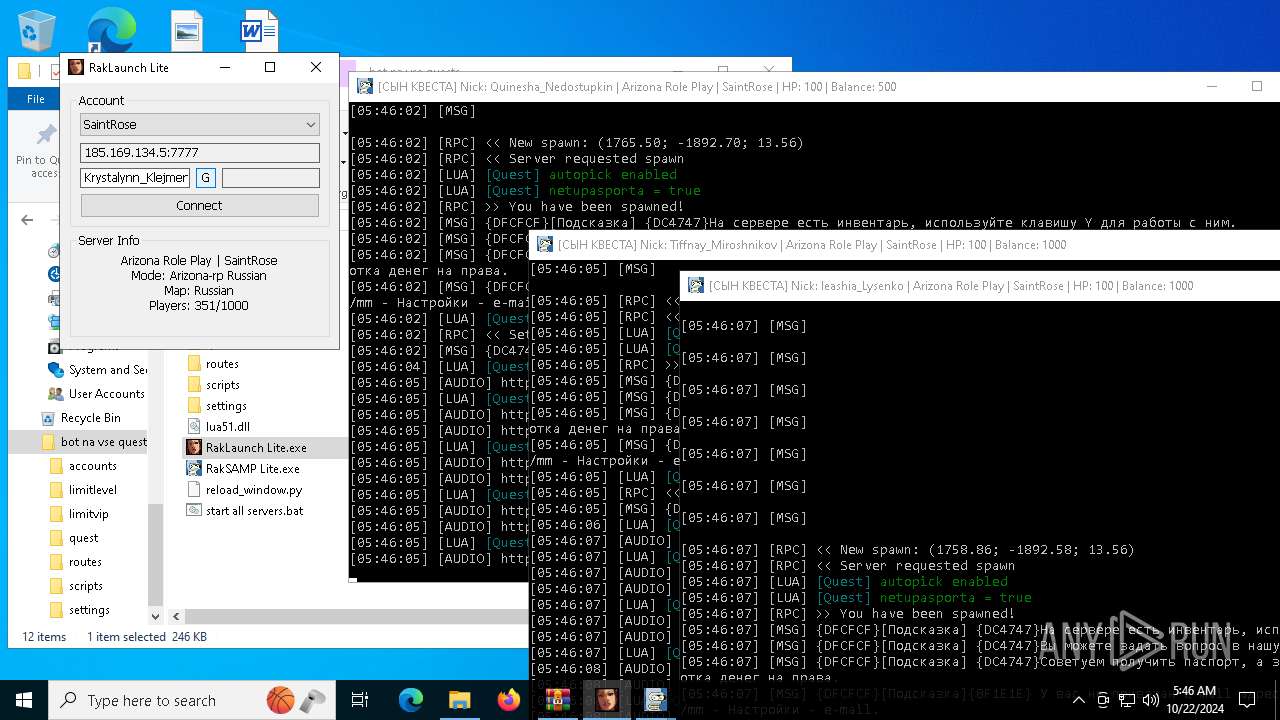
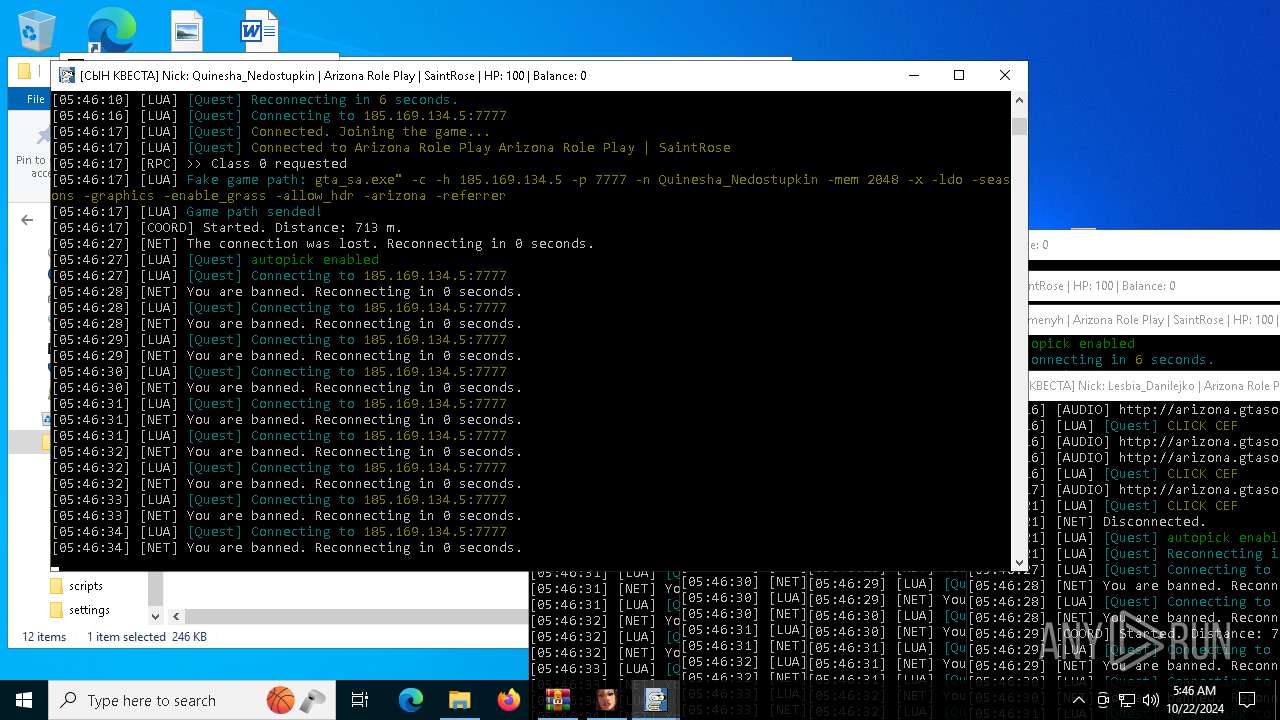
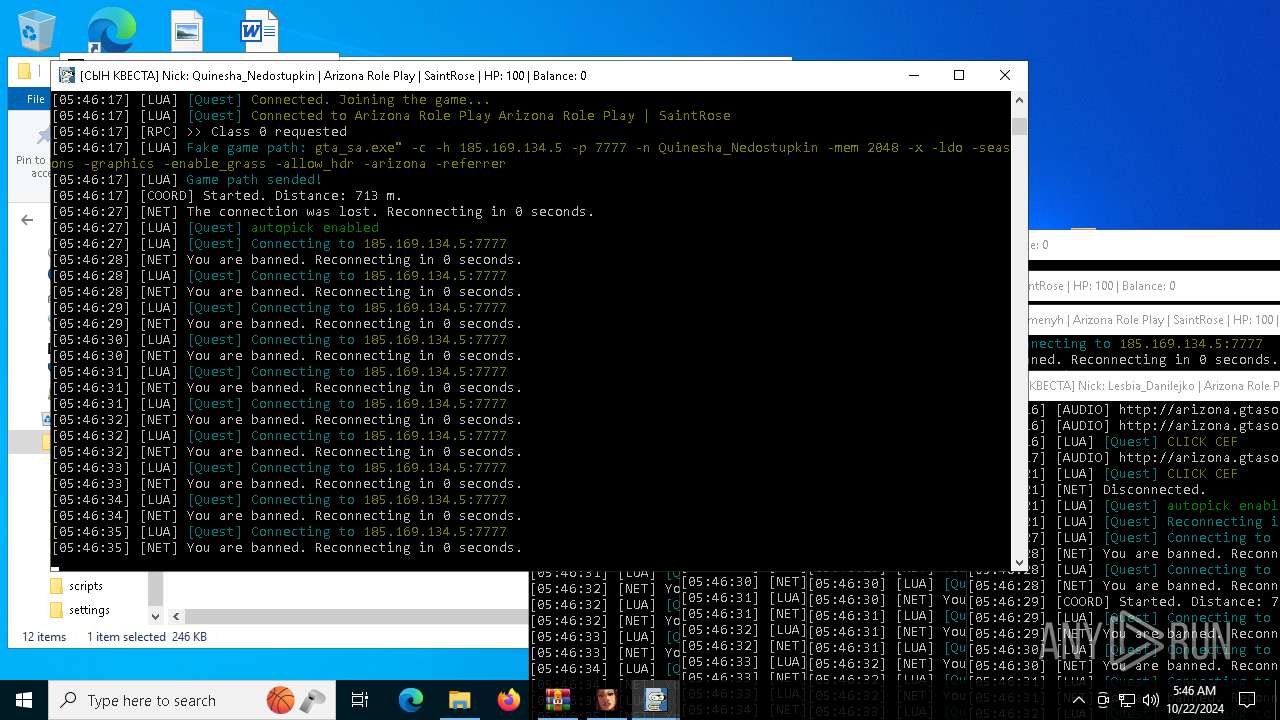
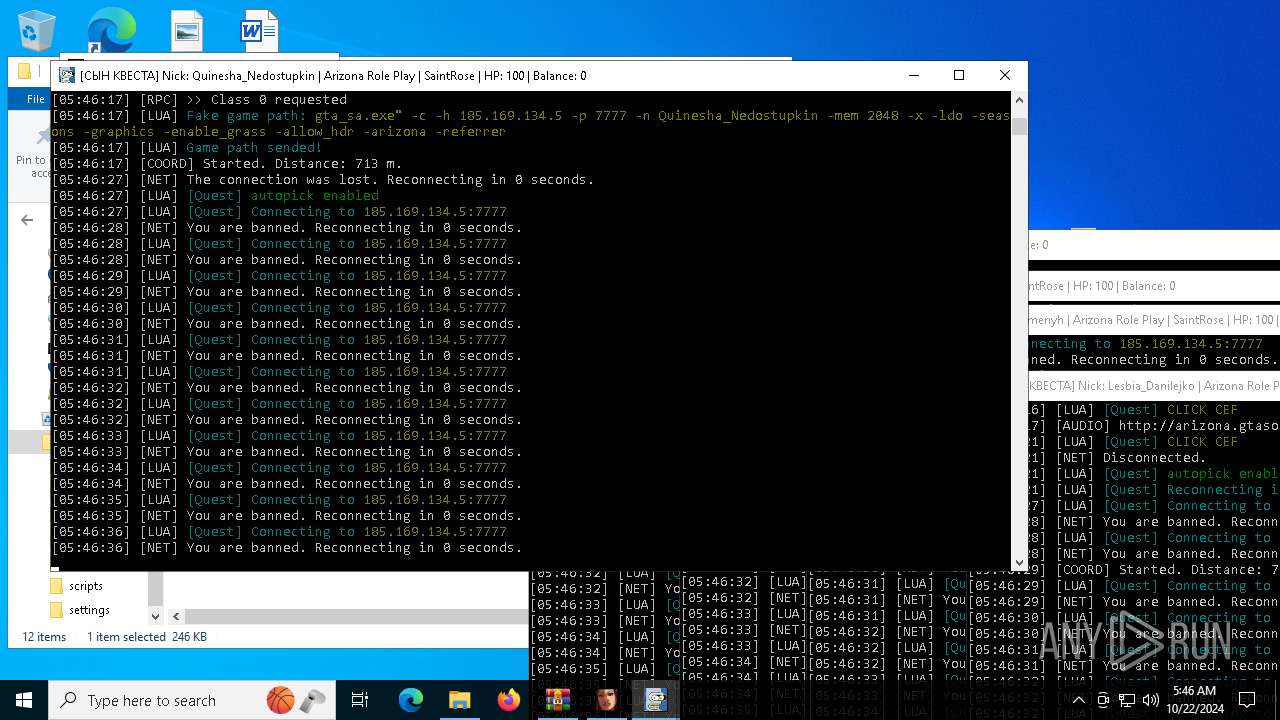
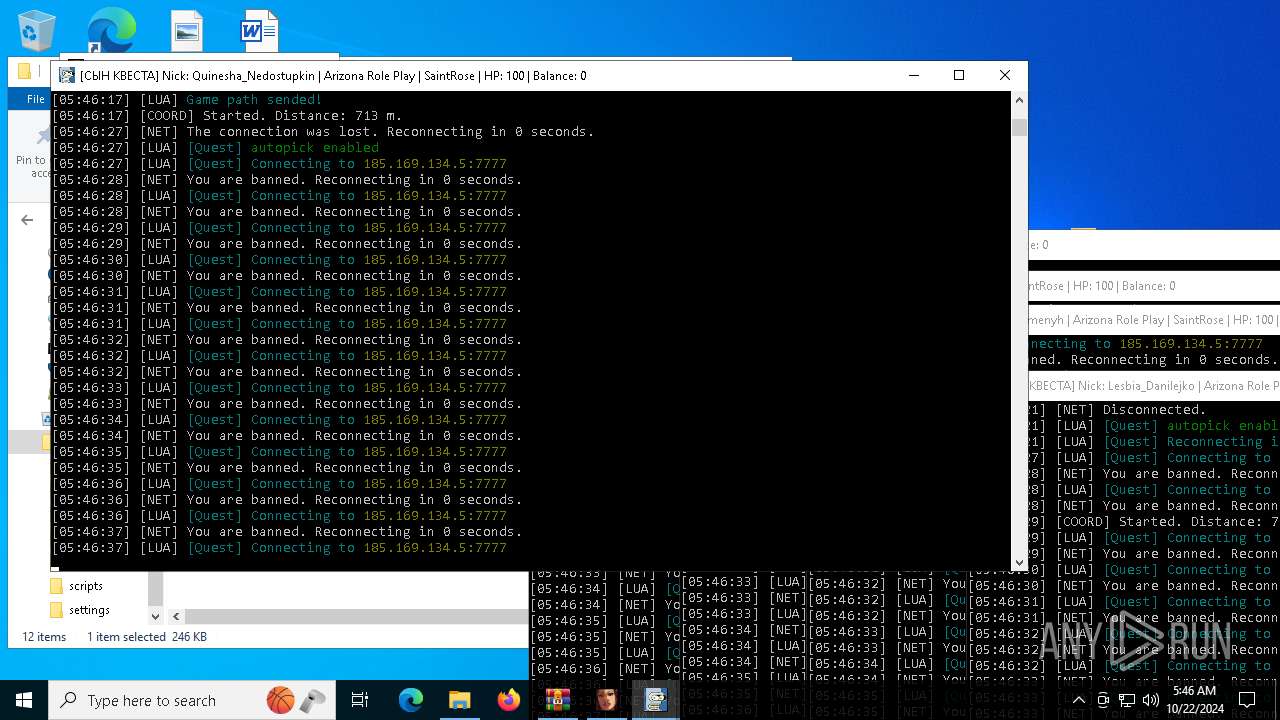
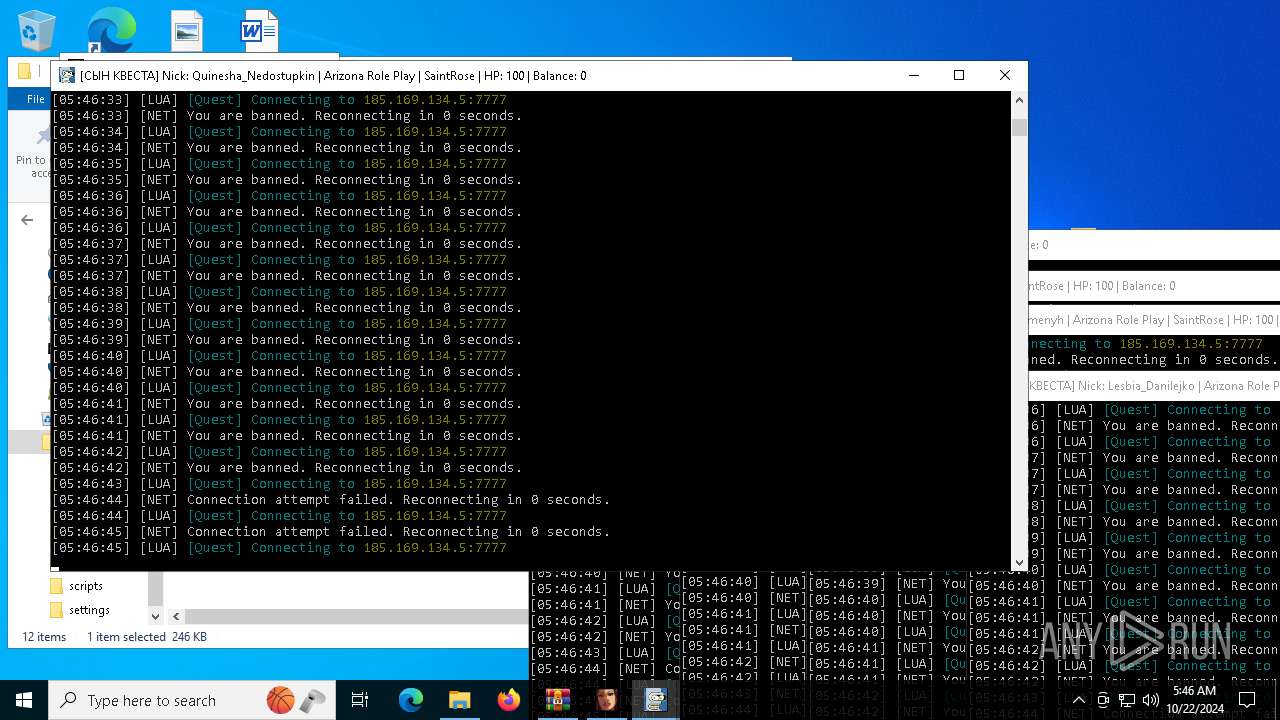
- RakSAMP Lite.exe (PID: 1952)
- RakSAMP Lite.exe (PID: 5788)
- RakSAMP Lite.exe (PID: 6264)
- RakSAMP Lite.exe (PID: 3276)
- RakSAMP Lite.exe (PID: 616)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6596)
The process uses the downloaded file
- WinRAR.exe (PID: 6596)
Manual execution by a user
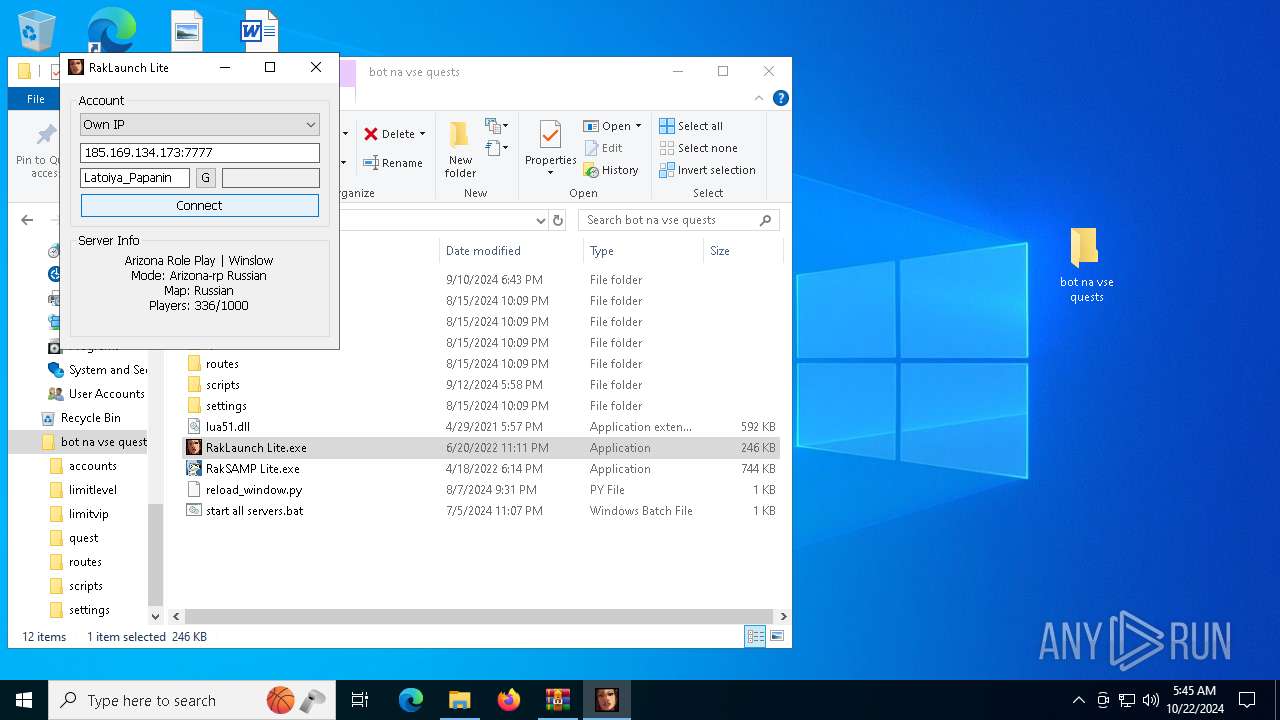
- RakLaunch Lite.exe (PID: 6344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:29 07:30:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bot na vse quests/ |
Total processes
158
Monitored processes
27
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe" -h 185.169.134.5 -p 7777 -n Lesbia_Danilejko -z | C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe | RakLaunch Lite.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 692 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | "C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe" -h 185.169.134.5 -p 7777 -n Quinesha_Nedostupkin -z | C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe | RakLaunch Lite.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\system32\cmd.exe /c color 0 | C:\Windows\SysWOW64\cmd.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2444 | C:\WINDOWS\system32\cmd.exe /c color 0 | C:\Windows\SysWOW64\cmd.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2660 | C:\WINDOWS\system32\cmd.exe /c color 0 | C:\Windows\SysWOW64\cmd.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe" -h 185.169.134.5 -p 7777 -n Krystalynn_Klejmenyh -z | C:\Users\admin\Desktop\bot na vse quests\RakSAMP Lite.exe | RakLaunch Lite.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 236
Read events
5 229
Write events
7
Delete events
0
Modification events
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\bot na vse quests.zip | |||
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6596) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4432) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.dll\OpenWithProgids |
| Operation: | write | Name: | dllfile |
Value: | |||
Executable files
75
Suspicious files
15
Text files
95
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\quest\settings.txt | ini | |
MD5:891C1BF0FCB7200F2ACE466F4D720A23 | SHA256:734143541AB014C85C1E1E7EEF46992F9AFC704BC55C52954128DA9CA9DED161 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\edemgdetopodlv.rt | — | |
MD5:— | SHA256:— | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\lua51.dll | executable | |
MD5:3DFF7448B43FCFB4DC65E0040B0FFB88 | SHA256:FF976F6E965E3793E278FA9BF5E80B9B226A0B3932B9DA764BFFC8E41E6CDB60 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\RakLaunch Lite.exe | executable | |
MD5:7D53985DBCDBED7E32F22934EC1F7B94 | SHA256:7AE2A1E9F328110BAE84CD82158041DE56DD5FCC0A8F5BB3E9378419A3BBEFCB | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route2.rt | text | |
MD5:A0B32D217B5BA60A9C2EBC056EDD56D3 | SHA256:61B508AC172F38146F90B7DFEBD104603A0F9CC044A90106B4240C2B7B94E7C6 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route5.rt | text | |
MD5:3A3A58A0B6D950C490810B3F3E6048D5 | SHA256:B890D6A0705C0F31C4B0FEC618128EF932ADAFE423F5DAC1B1B7ECBCE696FD35 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route3.rt | ini | |
MD5:695B1F12059BE5BDD76AE1A01AD67C0B | SHA256:6B1260EBEACE034625639DA28E6074E0A7C54FB3FB539ADD332AA6ABC8F6774D | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route7.rt | ini | |
MD5:F28E0BFE7988594C99EEECBE1EF0B7E2 | SHA256:C346F62FAF5BC4CB7A8AB8EBBC8A1754EECA57C3E3AC71CE4DF76CDBB1F07291 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route9.rt | text | |
MD5:3333259B67C7C84DB2331F76A558D3AB | SHA256:0B027710BBCEF7B789111B9848F6478962354C785354FFD628EF4811414FD051 | |||
| 6596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6596.20153\bot na vse quests\routes\crafter-route6.rt | text | |
MD5:0D4D01742F406E3AD301F280B6E1334A | SHA256:9A0B30696A208A450176D5F706EADB9AD94CF7220867C5EFB4B04F23E0164A21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
201
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3912 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4088 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4088 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3524 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4376 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4376 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.179:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |