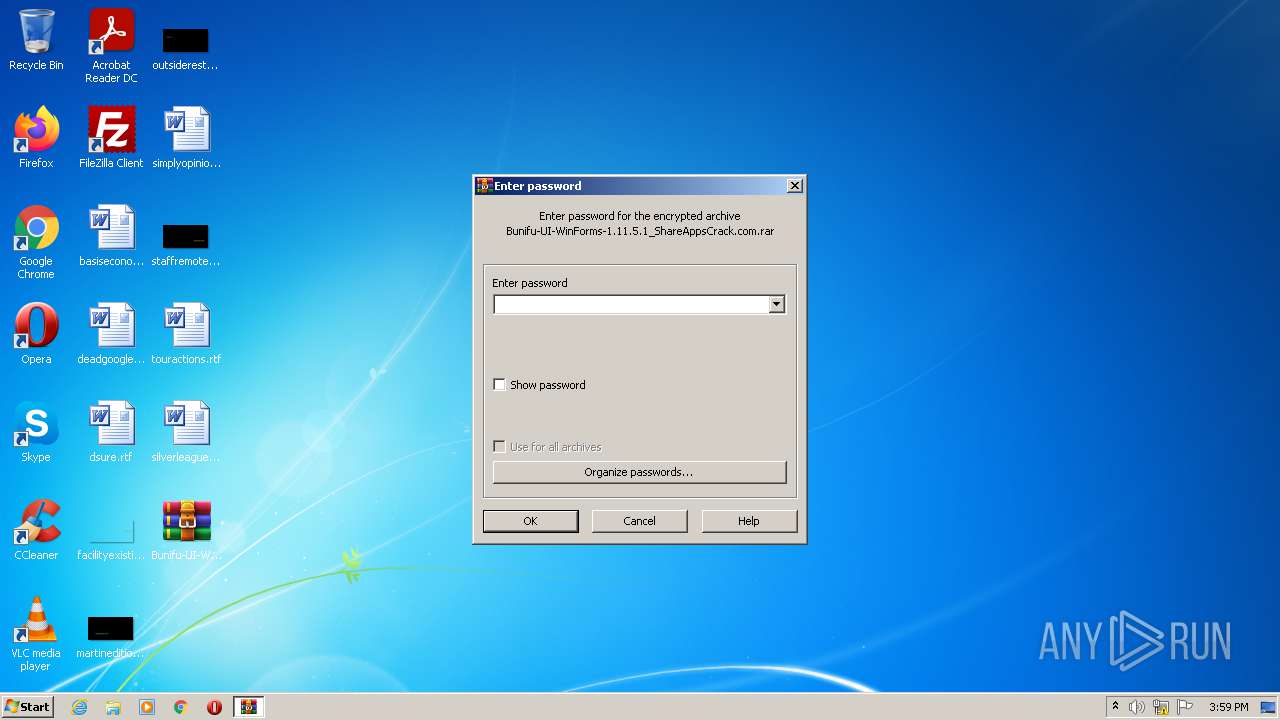
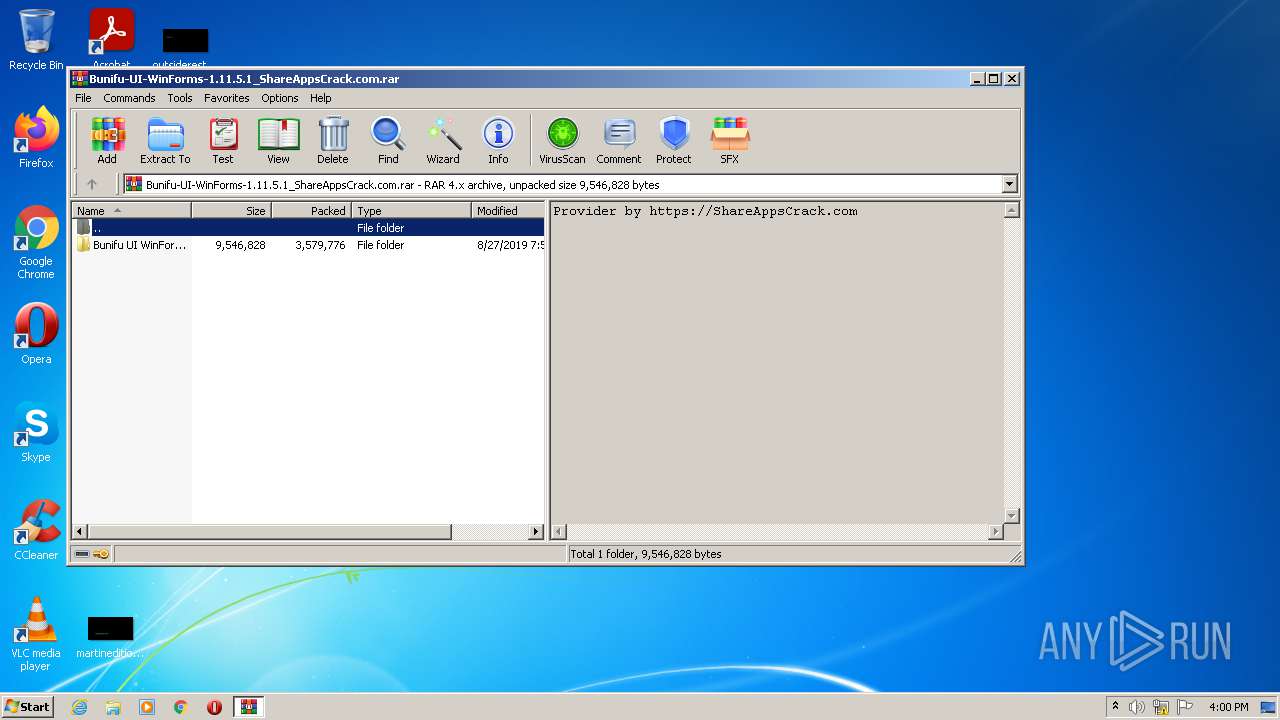
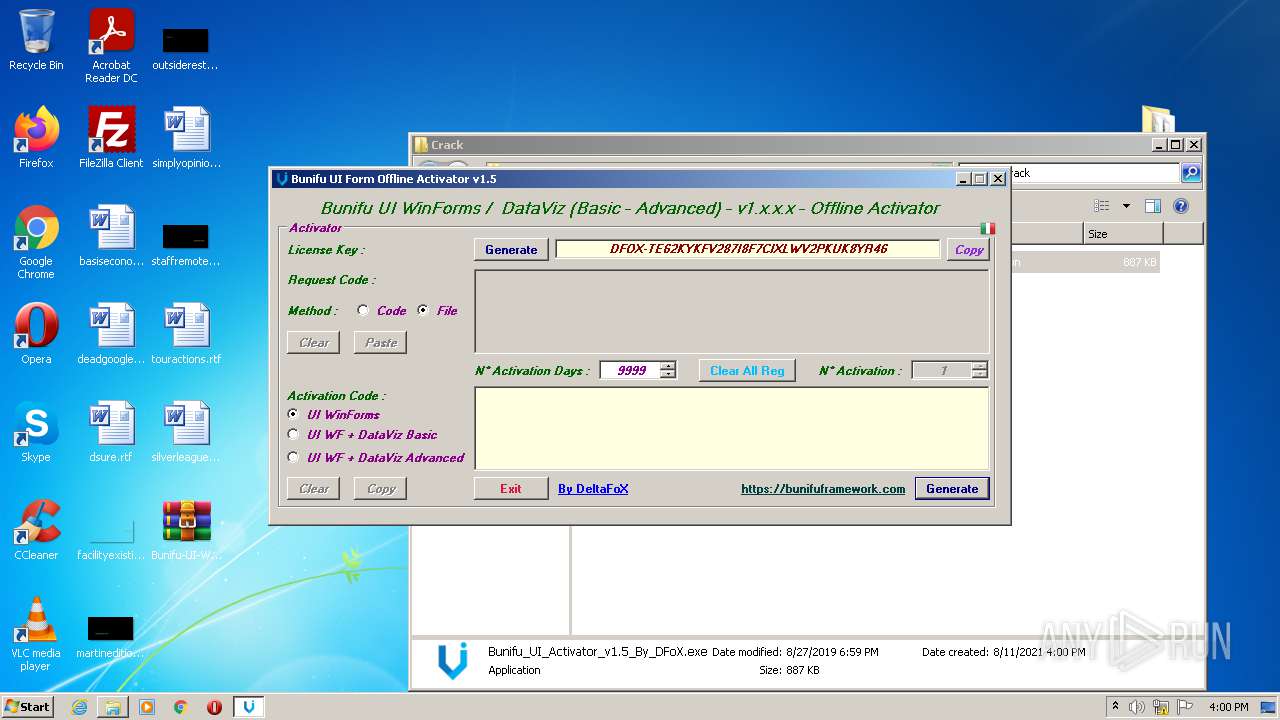
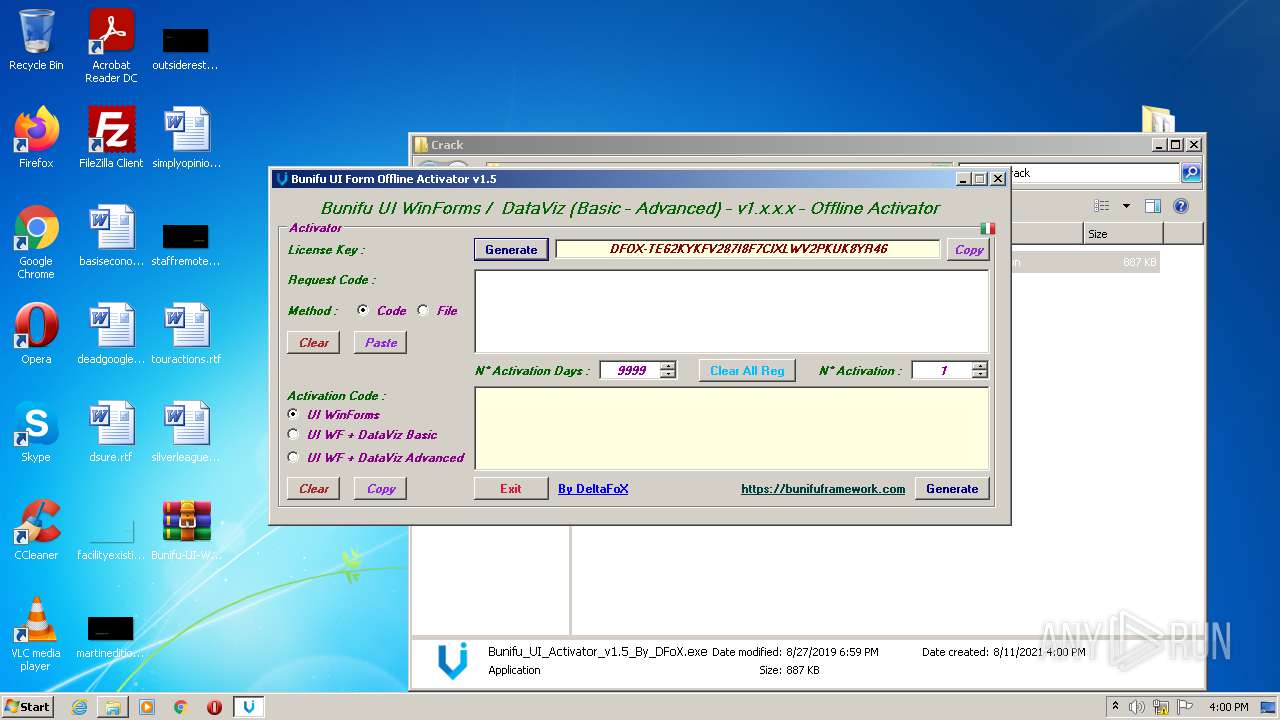
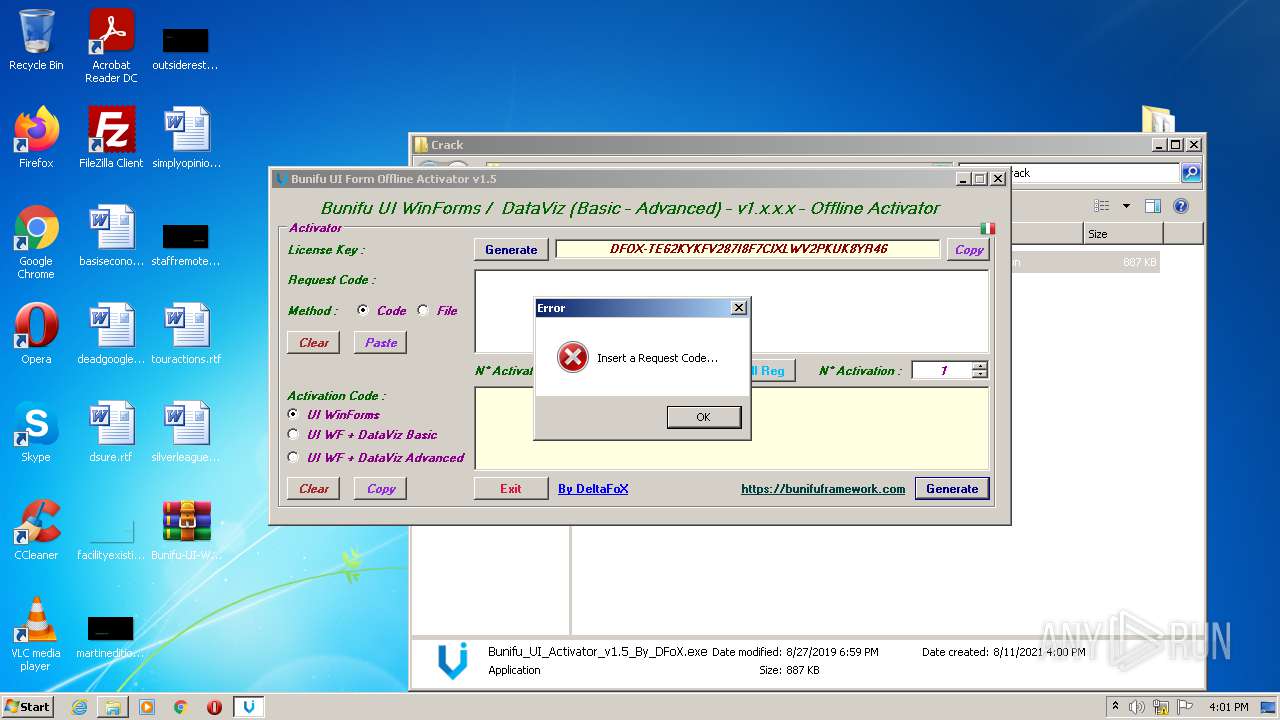
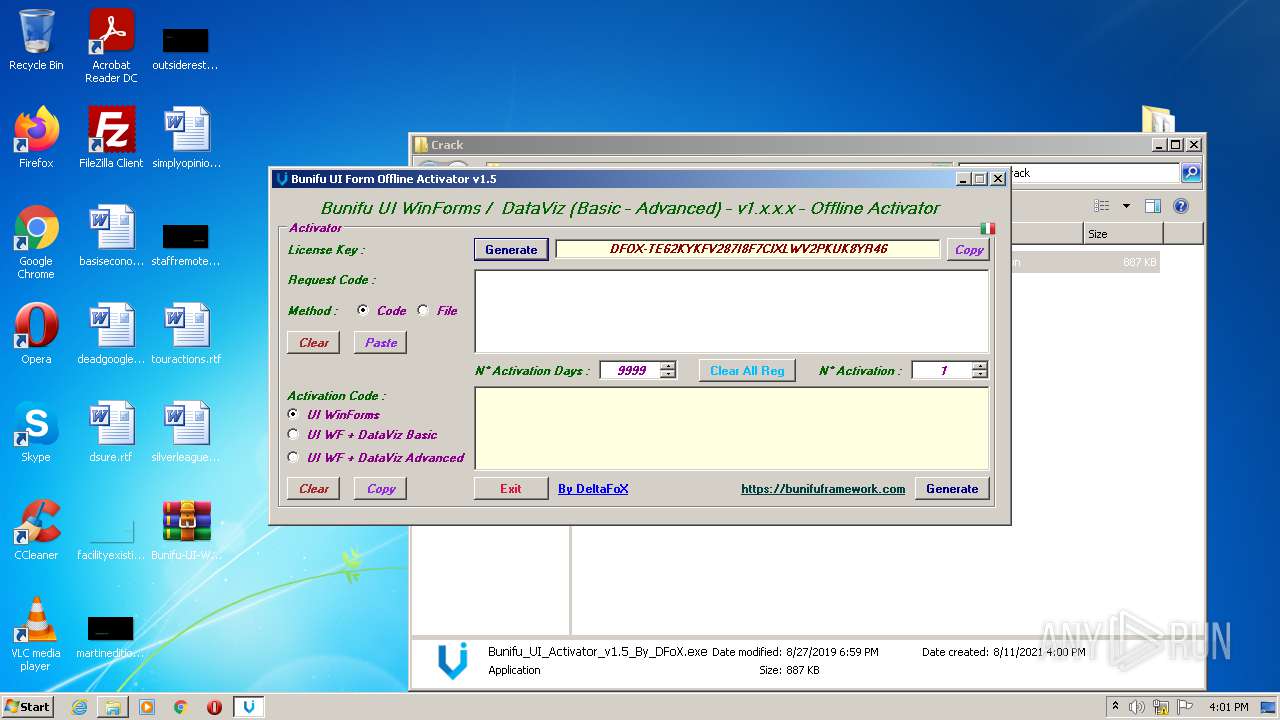
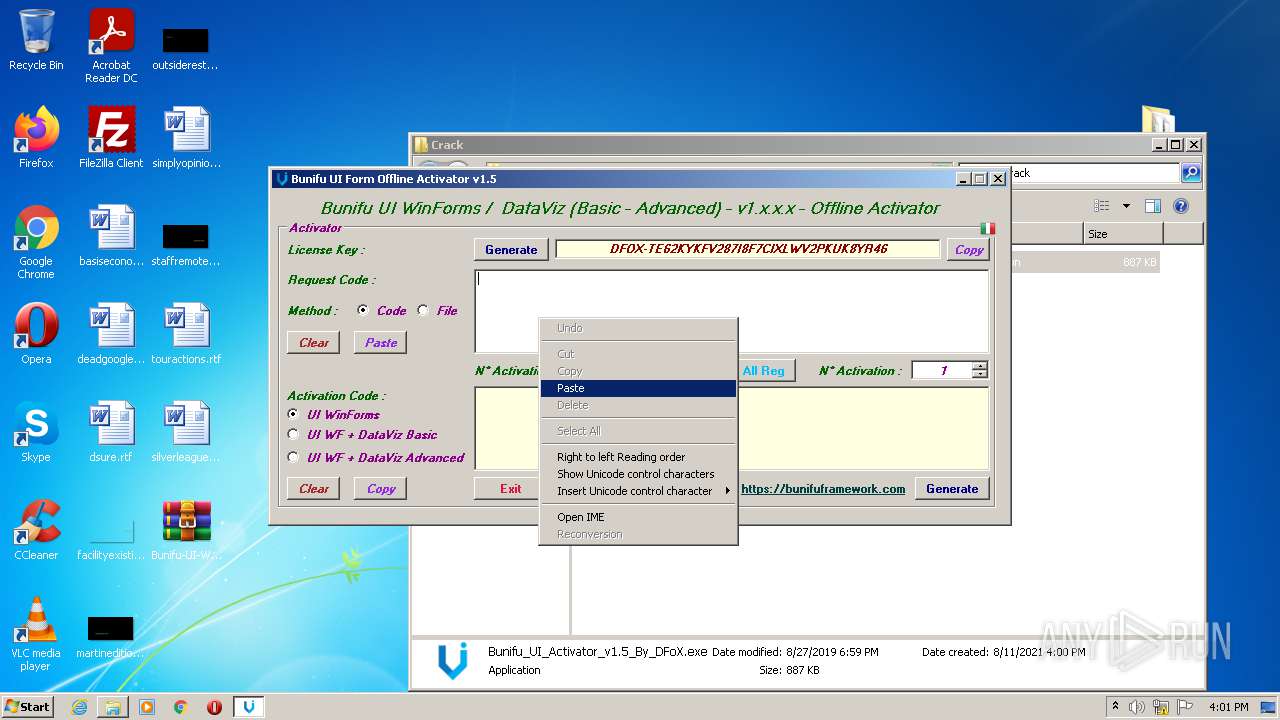
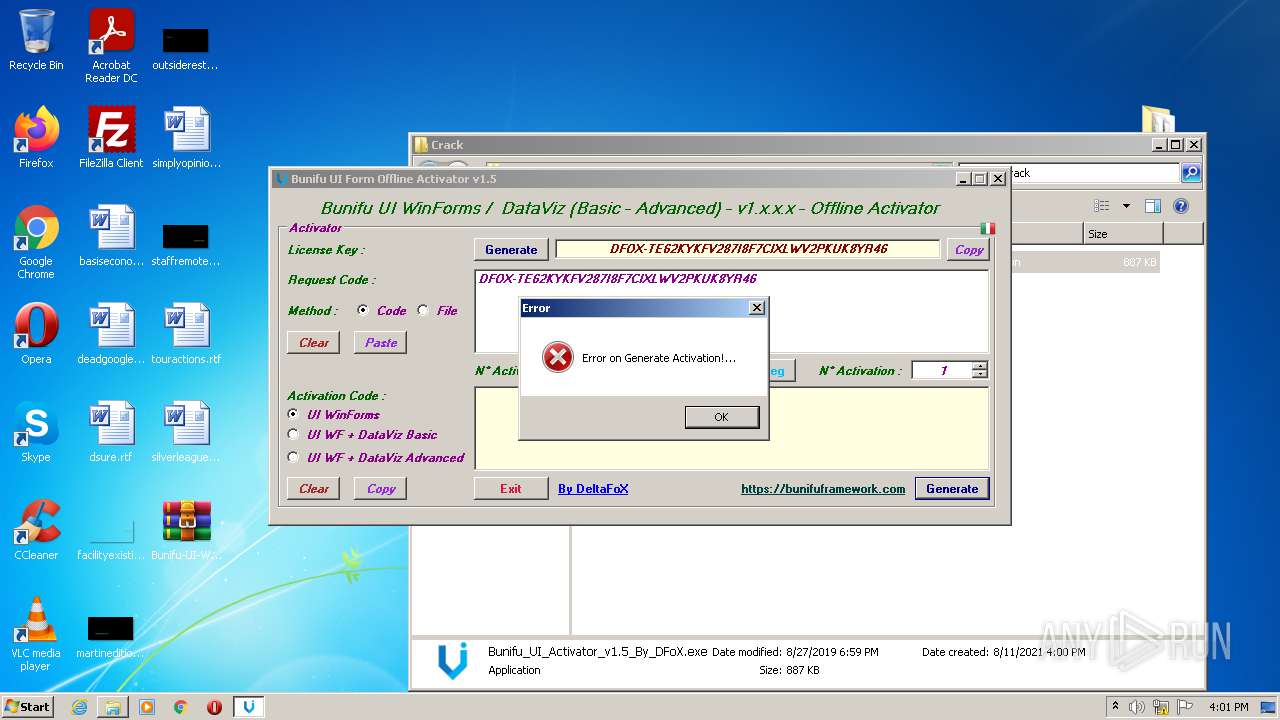
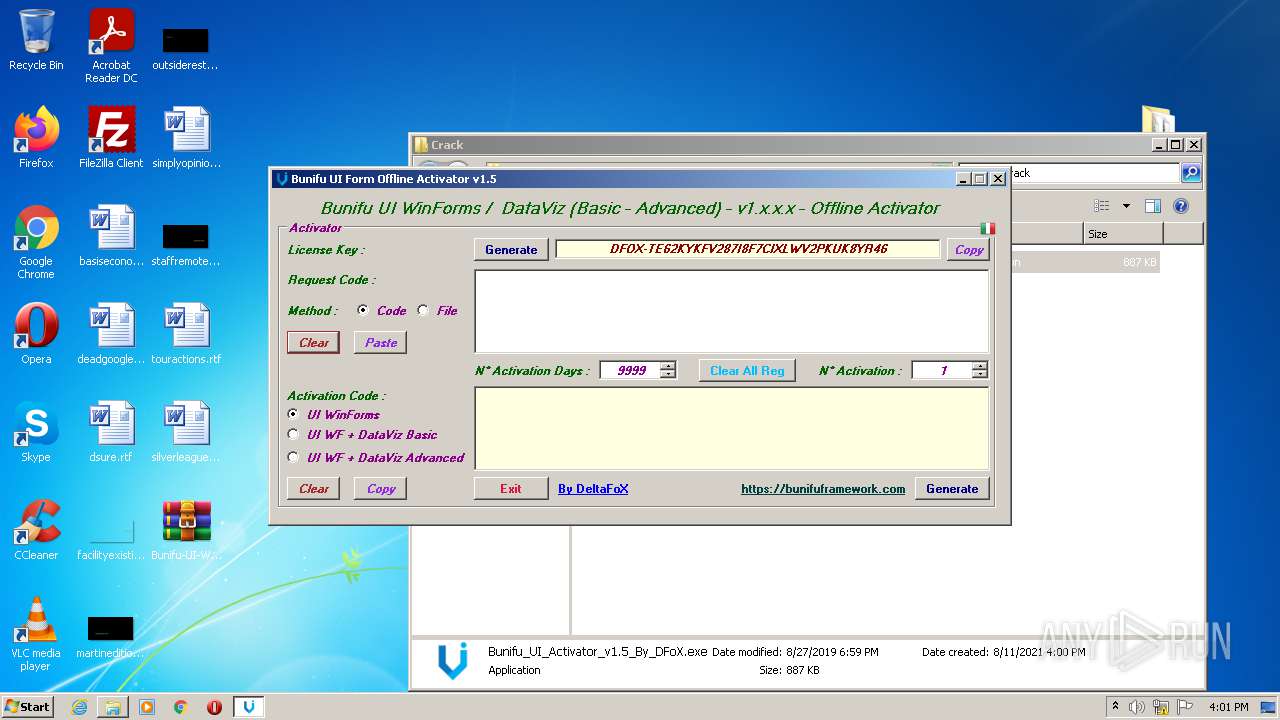
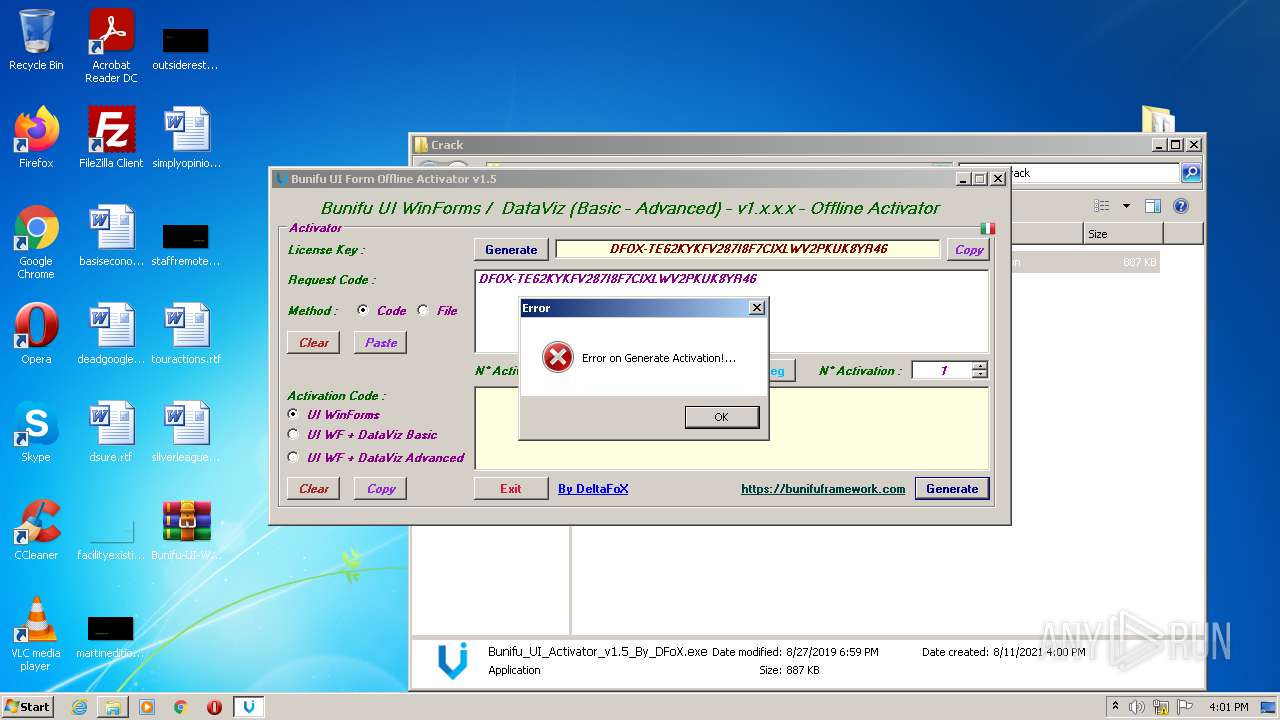
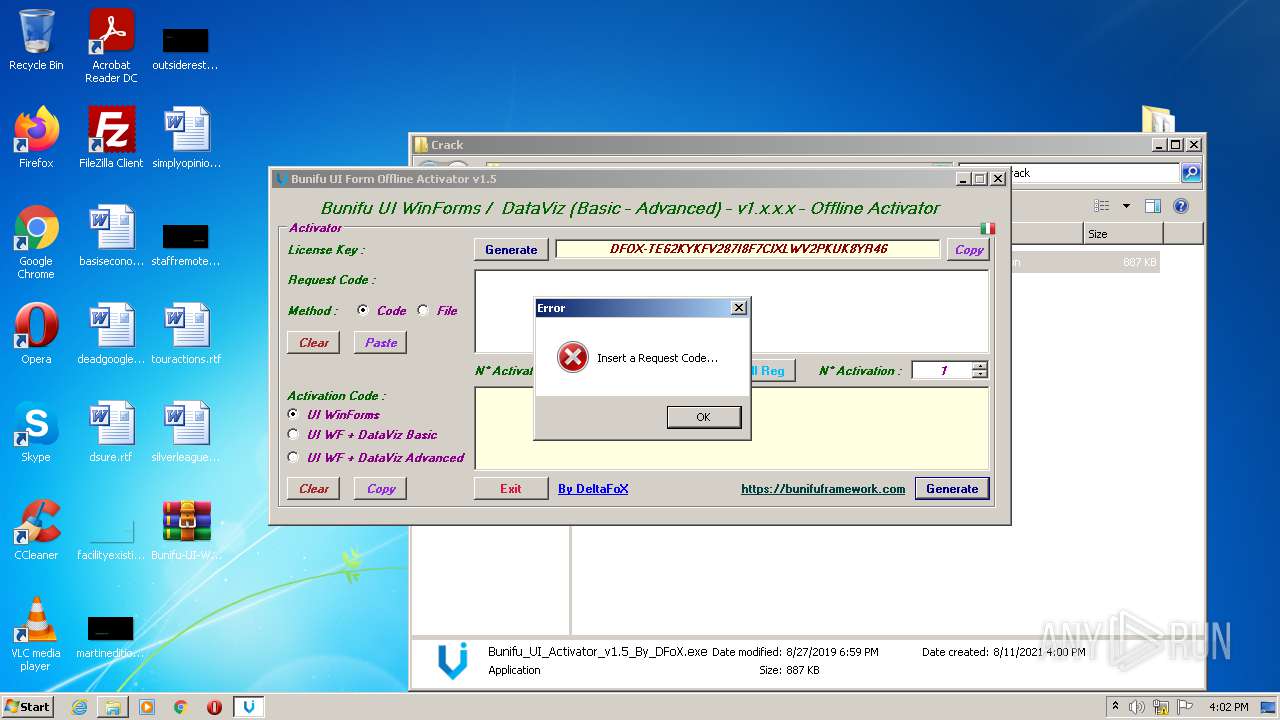
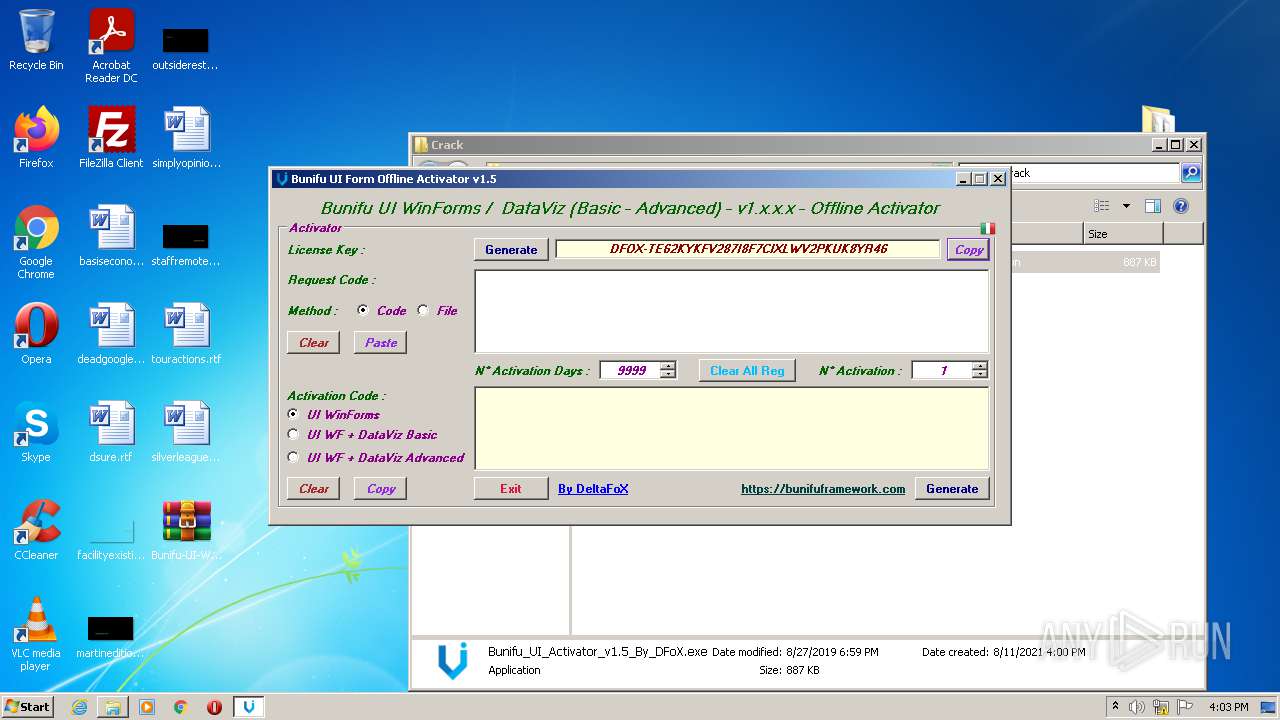
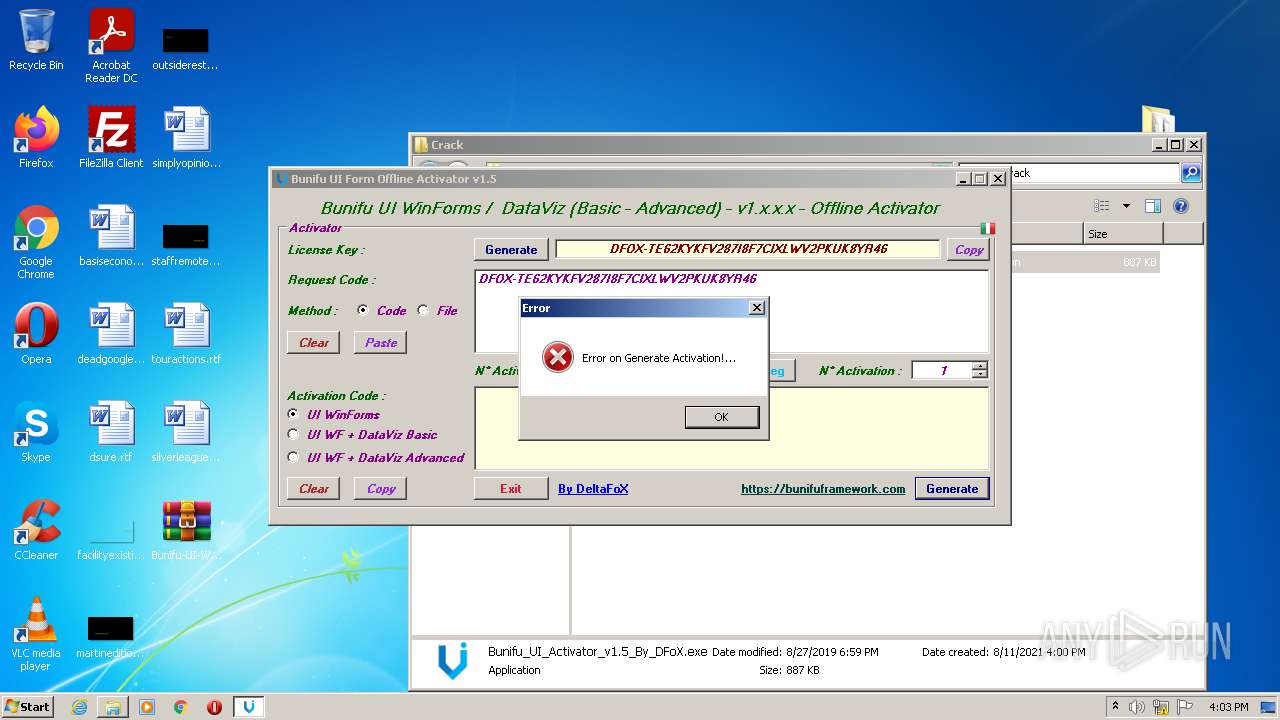
| File name: | Bunifu-UI-WinForms-1.11.5.1_ShareAppsCrack.com.rar |
| Full analysis: | https://app.any.run/tasks/b2d0b093-a465-4dfe-9ff0-f1a86496244b |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2021, 14:59:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, flags: EncryptedBlockHeader |
| MD5: | 4B19E971E1F5EAC6C0672462EF351D94 |
| SHA1: | 2A7EA8A84630362E69FB66BA9018F176DA24E318 |
| SHA256: | F9A6650DF2997FE50BC96E473BAD647976A7432027BB5FEE4509CE8CD6B093A2 |
| SSDEEP: | 98304:xUFhd11kltKhFB5PscYV0LkM+oe0sy10pUA/n:cd1mXKB2GVsy10pz |
MALICIOUS
Application was dropped or rewritten from another process
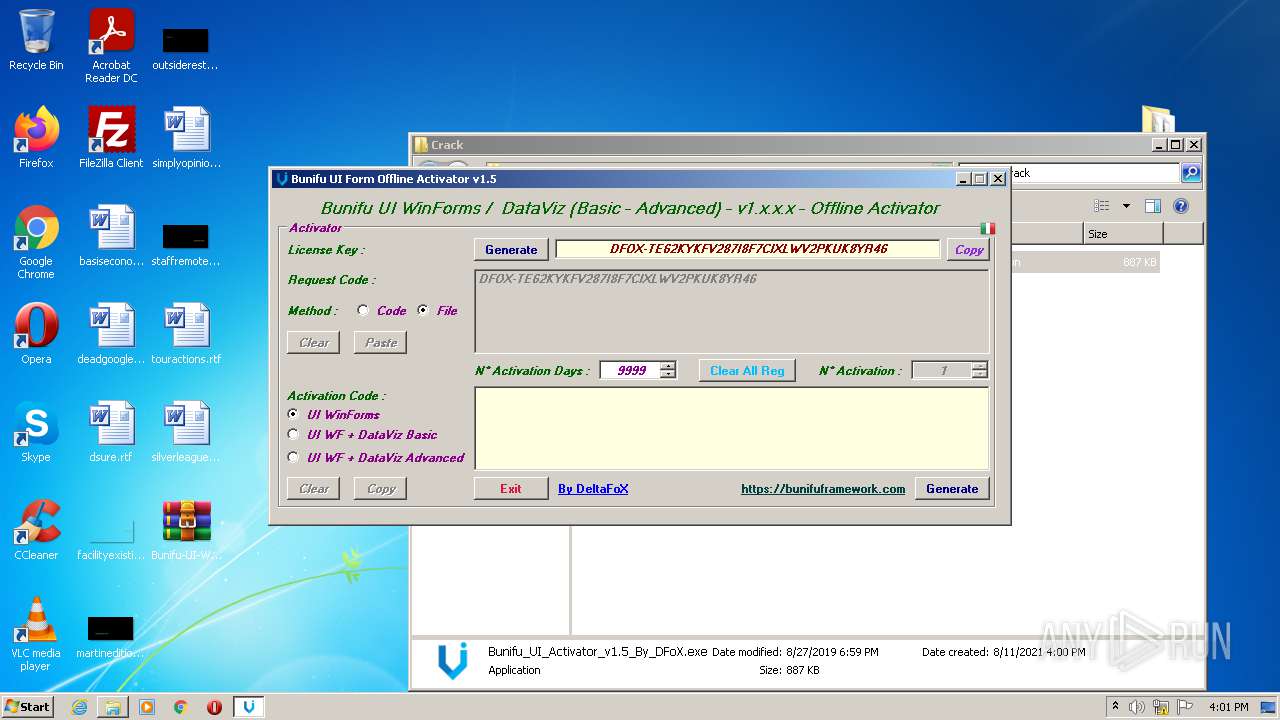
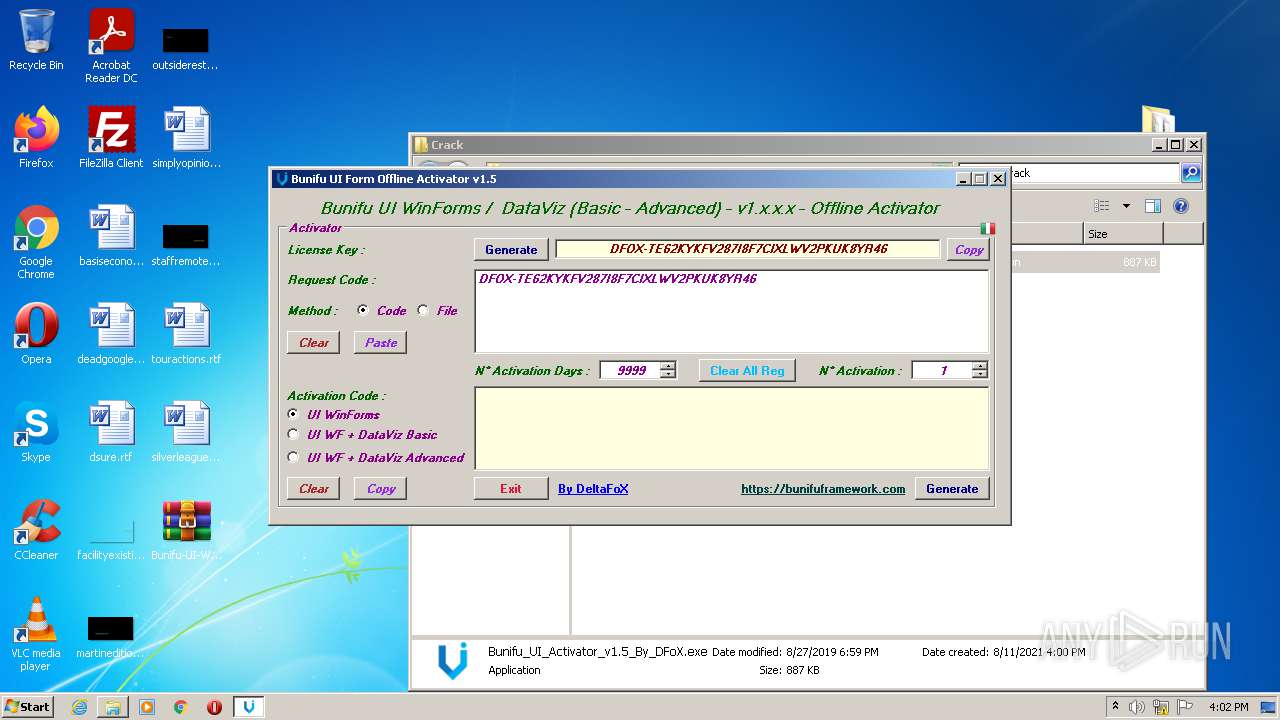
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1888)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2220)
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2220)
Checks supported languages
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
- WinRAR.exe (PID: 2220)
Starts Internet Explorer
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2220)
Reads internet explorer settings
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3568)
INFO
Manual execution by user
- Bunifu_UI_Activator_v1.5_By_DFoX.exe (PID: 3492)
Checks supported languages
- iexplore.exe (PID: 3704)
- iexplore.exe (PID: 3568)
Reads the computer name
- iexplore.exe (PID: 3704)
- iexplore.exe (PID: 3568)
Application launched itself
- iexplore.exe (PID: 3704)
Changes internet zones settings
- iexplore.exe (PID: 3704)
Checks Windows Trust Settings
- iexplore.exe (PID: 3568)
- iexplore.exe (PID: 3704)
Reads settings of System Certificates
- iexplore.exe (PID: 3568)
- iexplore.exe (PID: 3704)
Creates files in the user directory
- iexplore.exe (PID: 3568)
Reads the date of Windows installation
- iexplore.exe (PID: 3704)
Reads internet explorer settings
- iexplore.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
Total processes
40
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1888 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Bunifu-UI-WinForms-1.11.5.1_ShareAppsCrack.com.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3492 | "C:\Users\admin\Desktop\Bunifu UI WinForms 1.11.5.1\Crack\Bunifu_UI_Activator_v1.5_By_DFoX.exe" | C:\Users\admin\Desktop\Bunifu UI WinForms 1.11.5.1\Crack\Bunifu_UI_Activator_v1.5_By_DFoX.exe | — | Explorer.EXE | |||||||||||
User: admin Company: DeFconX Integrity Level: MEDIUM Description: Bunifu_UI_Activator_By_DFoX Exit code: 0 Version: 1.5.0.0 Modules
| |||||||||||||||
| 3568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3704 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3704 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.dfox.it/ | C:\Program Files\Internet Explorer\iexplore.exe | Bunifu_UI_Activator_v1.5_By_DFoX.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 470
Read events
17 354
Write events
115
Delete events
1
Modification events
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Bunifu-UI-WinForms-1.11.5.1_ShareAppsCrack.com.rar | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
26
Suspicious files
16
Text files
127
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuButton.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuCheckBox.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuColorTransition.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuDropdown.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuDataGridView.dll | executable | |
MD5:DD5DD7BF0F44E0E8B9E6437D91410352 | SHA256:D412950D8DA95F5A14217A1604B4CC04445084C5D4FC1239CA567F5782072B34 | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForm.BunifuShadowPanel.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuFormDock.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuDataGridView.xml | xml | |
MD5:— | SHA256:— | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuDropdown.dll | executable | |
MD5:51D4645646DA131CEFA7F368F53D72D9 | SHA256:E62A888775001AE85B5C0559CB4113E1069DD5B37CBDC6566A03B47E93A4B5FC | |||
| 2220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2220.16860\Bunifu UI WinForms 1.11.5.1\Bunifu.UI.WinForms.BunifuGauge.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
53
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECROUtlrVR%2BWCgAAAADyuvQ%3D | US | der | 471 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 23.55.163.57:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBtpDEx%2Fx4YJCgAAAADyw4g%3D | US | der | 471 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGq%2BdSta4rCACgAAAADyw3Q%3D | US | der | 471 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 104.117.200.9:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 205.185.216.10:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?04a706e2dc66ffd4 | US | compressed | 4.70 Kb | whitelisted |
3568 | iexplore.exe | GET | 200 | 205.185.216.10:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5323373561ba0018 | US | compressed | 4.70 Kb | whitelisted |
3568 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAFnXJaHpQX8CgAAAAD26ss%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3568 | iexplore.exe | 23.55.163.57:80 | crl.identrust.com | Akamai International B.V. | US | unknown |
3568 | iexplore.exe | 205.185.216.10:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3568 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3704 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3568 | iexplore.exe | 2.19.62.181:443 | z.moatads.com | Akamai International B.V. | — | whitelisted |
3704 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3568 | iexplore.exe | 142.250.181.238:443 | mt1.google.com | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 142.250.186.174:443 | mt2.google.com | Google Inc. | US | whitelisted |
3568 | iexplore.exe | 142.250.186.46:443 | mt.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dfox.it |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
dfox.it |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |