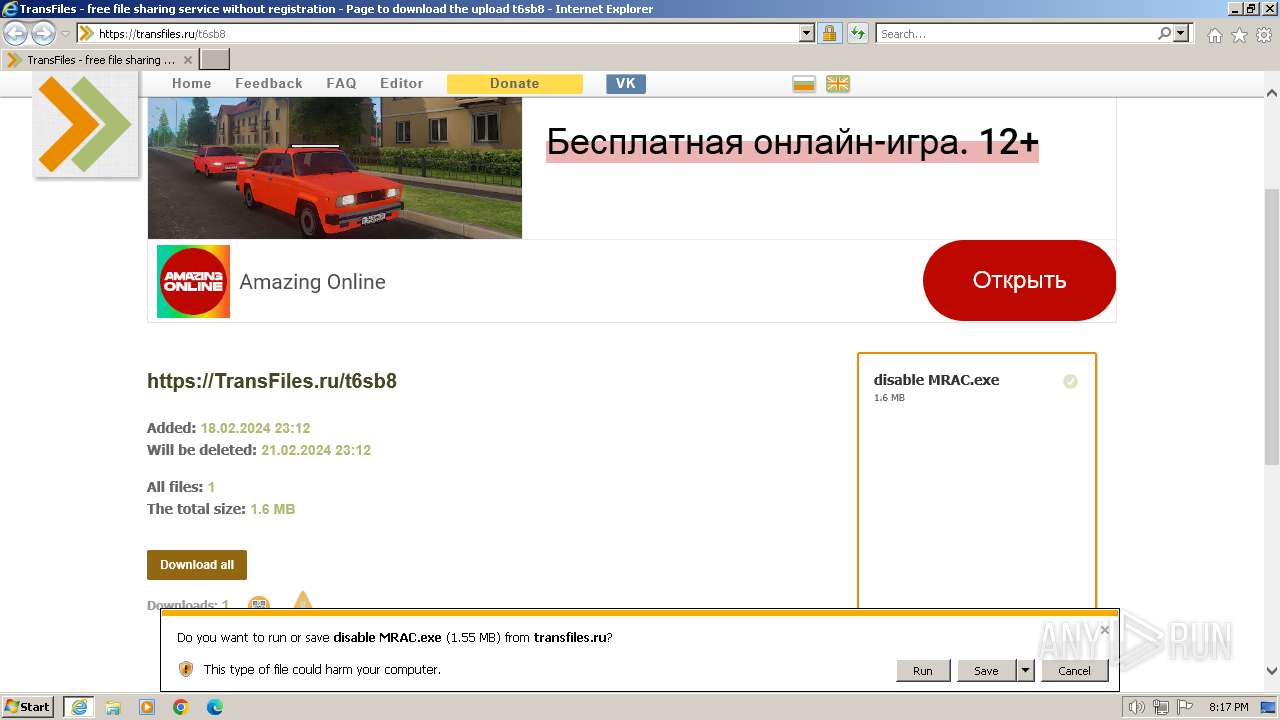
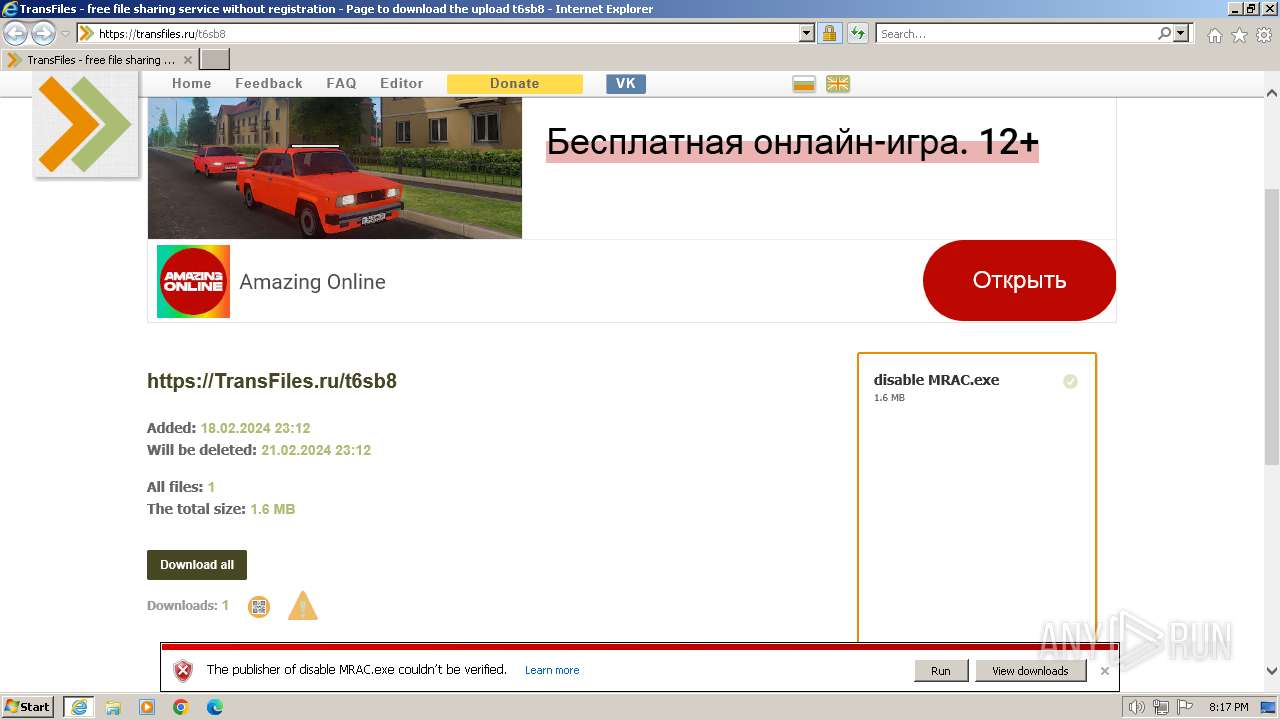
| URL: | https://transfiles.ru/t6sb8 |
| Full analysis: | https://app.any.run/tasks/5d239ef4-9bfc-425e-81aa-55fed5b85cd6 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 20:16:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4A39DCE7FB7741D7A81B7156FAEAEB44 |
| SHA1: | FDD50FBA1D3A80167E804E01F342C9E7FEAC0B40 |
| SHA256: | F9790FCCF10C113B9E3C09F0377D665D89792CA177B7166E991A57DFEA88DAF2 |
| SSDEEP: | 3:N8fiWD5Td:21 |
MALICIOUS
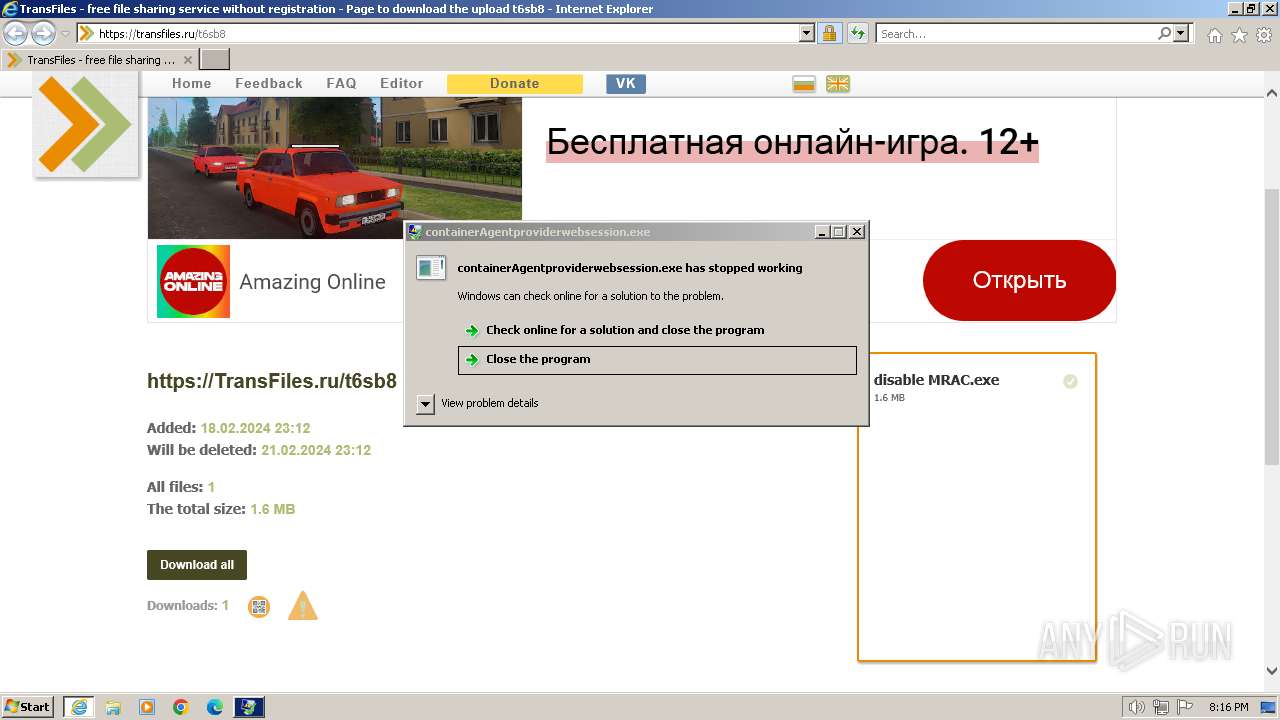
Drops the executable file immediately after the start
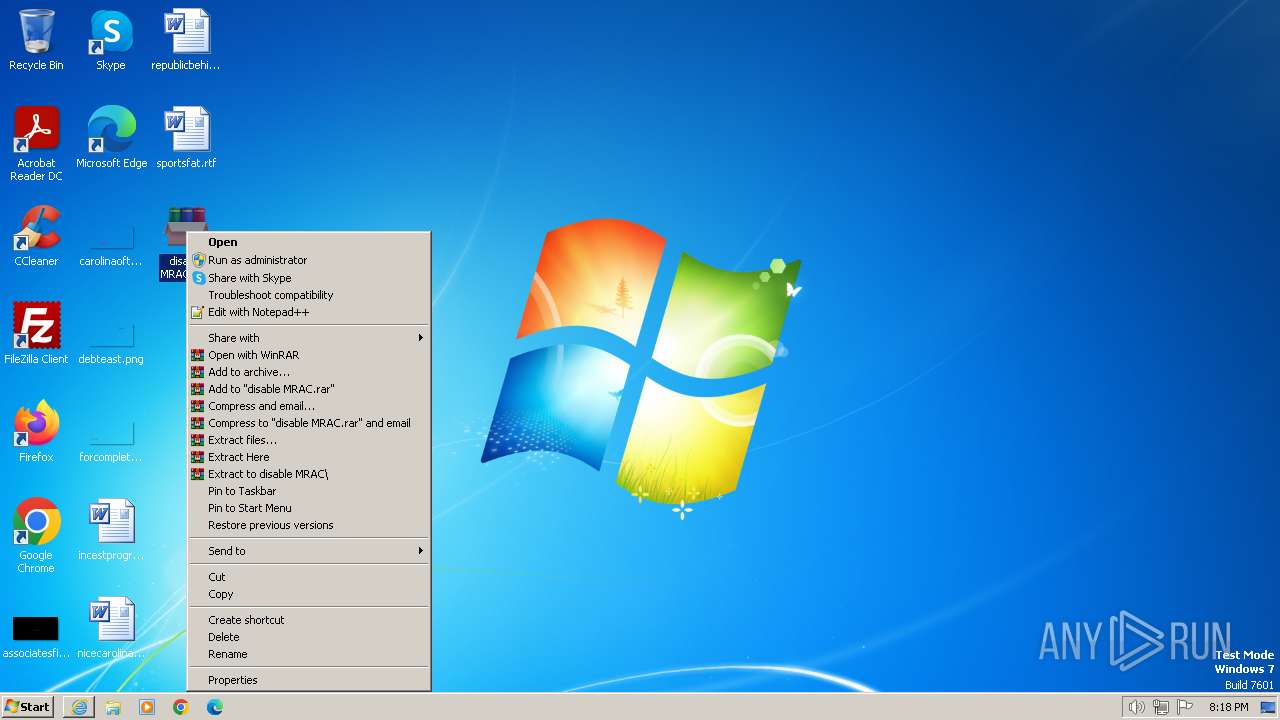
- disable MRAC.exe (PID: 2168)
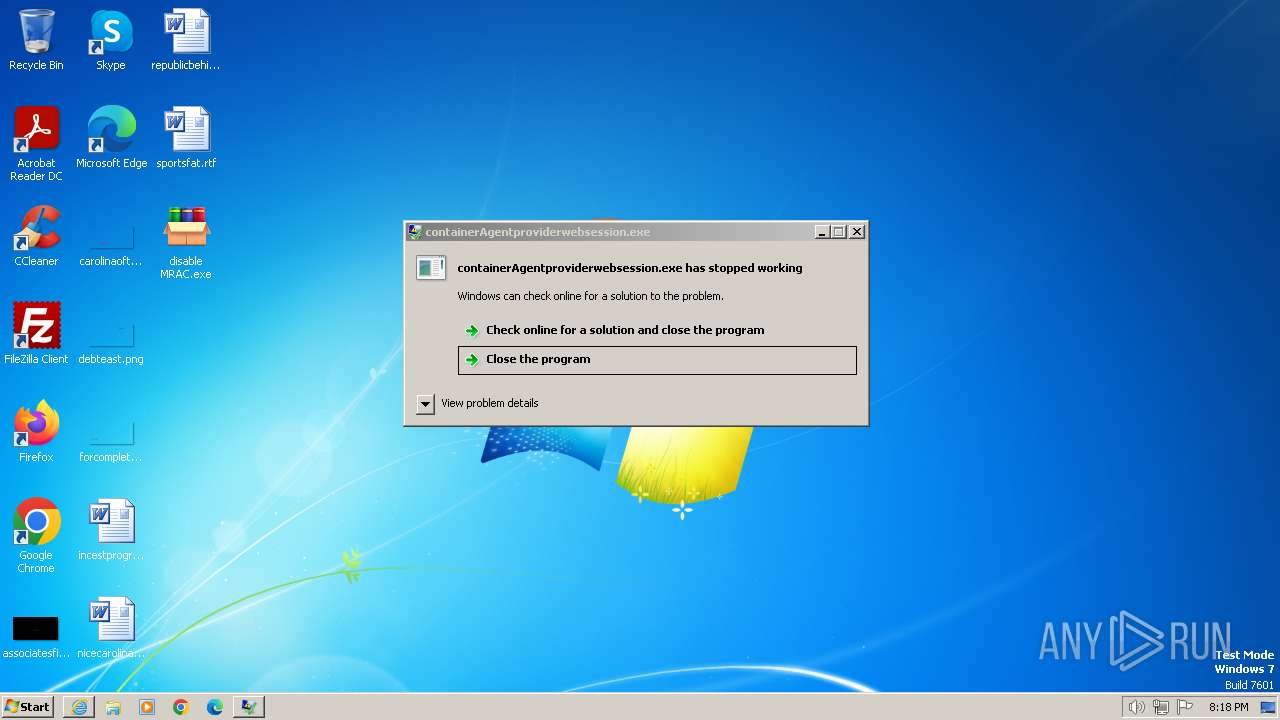
- containerAgentproviderwebsession.exe (PID: 1576)
- containerAgentproviderwebsession.exe (PID: 3252)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1888)
- wscript.exe (PID: 1636)
SUSPICIOUS
Executable content was dropped or overwritten
- disable MRAC.exe (PID: 2168)
- containerAgentproviderwebsession.exe (PID: 1576)
- containerAgentproviderwebsession.exe (PID: 3252)
Reads the Internet Settings
- disable MRAC.exe (PID: 2168)
- wscript.exe (PID: 1888)
- disable MRAC.exe (PID: 2560)
- wscript.exe (PID: 1636)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1888)
- wscript.exe (PID: 1636)
Reads security settings of Internet Explorer
- disable MRAC.exe (PID: 2168)
- disable MRAC.exe (PID: 2560)
Executing commands from a ".bat" file
- wscript.exe (PID: 1888)
- wscript.exe (PID: 1636)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1888)
- wscript.exe (PID: 1636)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3308)
- cmd.exe (PID: 2308)
INFO
Application launched itself
- iexplore.exe (PID: 2472)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3348)
- iexplore.exe (PID: 2472)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2472)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3348)
- iexplore.exe (PID: 2472)
The process uses the downloaded file
- iexplore.exe (PID: 2472)
Checks supported languages
- disable MRAC.exe (PID: 2168)
- containerAgentproviderwebsession.exe (PID: 1576)
- disable MRAC.exe (PID: 2560)
- containerAgentproviderwebsession.exe (PID: 3252)
Reads the computer name
- disable MRAC.exe (PID: 2168)
- containerAgentproviderwebsession.exe (PID: 1576)
- disable MRAC.exe (PID: 2560)
- containerAgentproviderwebsession.exe (PID: 3252)
Reads Environment values
- containerAgentproviderwebsession.exe (PID: 1576)
- containerAgentproviderwebsession.exe (PID: 3252)
Reads the machine GUID from the registry
- containerAgentproviderwebsession.exe (PID: 1576)
- containerAgentproviderwebsession.exe (PID: 3252)
Manual execution by a user
- disable MRAC.exe (PID: 2560)
Reads product name
- containerAgentproviderwebsession.exe (PID: 1576)
- containerAgentproviderwebsession.exe (PID: 3252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
60
Monitored processes
12
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | "C:\MsagentproviderHostdll/containerAgentproviderwebsession.exe" | C:\MsagentproviderHostdll\containerAgentproviderwebsession.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Version: 16.10.31418.88 Modules
| |||||||||||||||
| 1592 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1636 | "C:\Windows\System32\WScript.exe" "C:\MsagentproviderHostdll\DFRhGV72zcI4MoSMws3K.vbe" | C:\Windows\System32\wscript.exe | — | disable MRAC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1888 | "C:\Windows\System32\WScript.exe" "C:\MsagentproviderHostdll\DFRhGV72zcI4MoSMws3K.vbe" | C:\Windows\System32\wscript.exe | — | disable MRAC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\disable MRAC.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\disable MRAC.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2308 | C:\Windows\system32\cmd.exe /c ""C:\MsagentproviderHostdll\Ed5V8GaQIPZo2Xo1s8MXIpHI.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://transfiles.ru/t6sb8" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\Desktop\disable MRAC.exe" | C:\Users\admin\Desktop\disable MRAC.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 10 Modules
| |||||||||||||||
| 2564 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3252 | "C:\MsagentproviderHostdll/containerAgentproviderwebsession.exe" | C:\MsagentproviderHostdll\containerAgentproviderwebsession.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 16.10.31418.88 Modules
| |||||||||||||||
Total events
33 867
Read events
33 548
Write events
270
Delete events
49
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089319 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089319 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
9
Suspicious files
35
Text files
91
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\abuse[1].png | image | |
MD5:3B7F009B9E66DD02EEA2CCDB26402572 | SHA256:2B68B345C236CD622A7FF2B26F080D6CF820A8B684924533C28ED26DEF132E2C | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\functions[1].js | text | |
MD5:4D0B7732C95CC6AA9D5B63ED9FF3BDAD | SHA256:1BA0D75F0DE5B0569BF17B0D9FC0BA65F6859F6F775943E7894531E097CC0412 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\ru[1].png | image | |
MD5:01F78ADD7628815BAA0126489CA6BBB4 | SHA256:670BC999DF02739E39C67AB53DD9E9D4C7BE5049C14C29613FD96B2907A798A5 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery.bxslider.min[1].js | text | |
MD5:697D69A48E5356F7106E38C09F7F19E0 | SHA256:BB9E7DC822C6B7B95A6329932885C72FF2CAF74B243FC1C40ACA0E858123B83E | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\download[1].js | text | |
MD5:1019B453EBE2F71D8CE1B4CC4804EC55 | SHA256:9FC6A77284C6B5D46B25240FB3D5CB59533D64721129854B03E48A68BCE7DBAF | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:B92850AA4F601F1ED53E9C48FB73141A | SHA256:3EFF4406C697E63FFFDA3CE8FF4C06A064CC6CC7587DF3D7774A0C2BDEE283A1 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\en[1].png | image | |
MD5:06AA60774CECADD41E09151E2D006F16 | SHA256:9A87F8ADE1743DC729FD6066A644C763D997B3415CDD7D27D38B0BBB4DD4B172 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\btn_qrcode[1].png | image | |
MD5:8CD4697B378BDB77799A1D5DB2FE50C1 | SHA256:667D1872D646EFC435C01A6AF873B637545E011790236C6AEC3A0CEBD37B14FD | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery.bxslider[1].css | text | |
MD5:D6711DA316447431B655F1E80A001205 | SHA256:6300BA1C19B24D427FDEC05B16C8B7C85F21155097C82FFDCED06192A5F70D31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
69
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3348 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 200 | 195.138.255.19:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMYmg8JuP%2FAwSvawMgXBgq3sg%3D%3D | unknown | binary | 503 b | unknown |
3348 | iexplore.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3348 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3348 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3348 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBVwuMGYY9kfENL7iFzC1x0%3D | unknown | binary | 471 b | unknown |
3348 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCG5mYmc5exBwr3zurLpXnC | unknown | binary | 472 b | unknown |
3348 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHUeP1PjGFkz6V8I7O6tApc%3D | unknown | binary | 1.41 Kb | unknown |
2472 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3348 | iexplore.exe | 157.90.215.152:443 | transfiles.ru | Hetzner Online GmbH | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3348 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3348 | iexplore.exe | 72.246.169.163:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3348 | iexplore.exe | 195.138.255.19:80 | r3.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | unknown |
3348 | iexplore.exe | 172.217.18.98:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
3348 | iexplore.exe | 93.158.134.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
3348 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3348 | iexplore.exe | 142.250.185.174:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
transfiles.ru |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
pagead2.googlesyndication.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
mc.yandex.ru |
| whitelisted |
www.google-analytics.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |