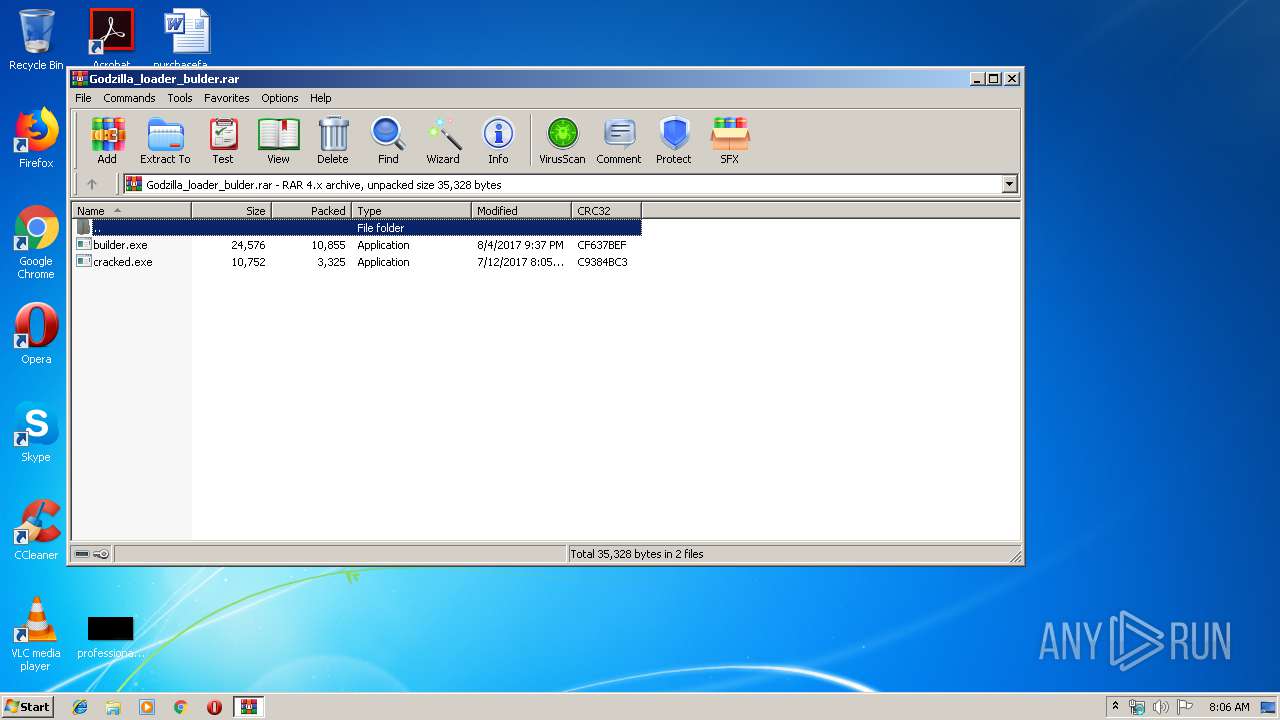
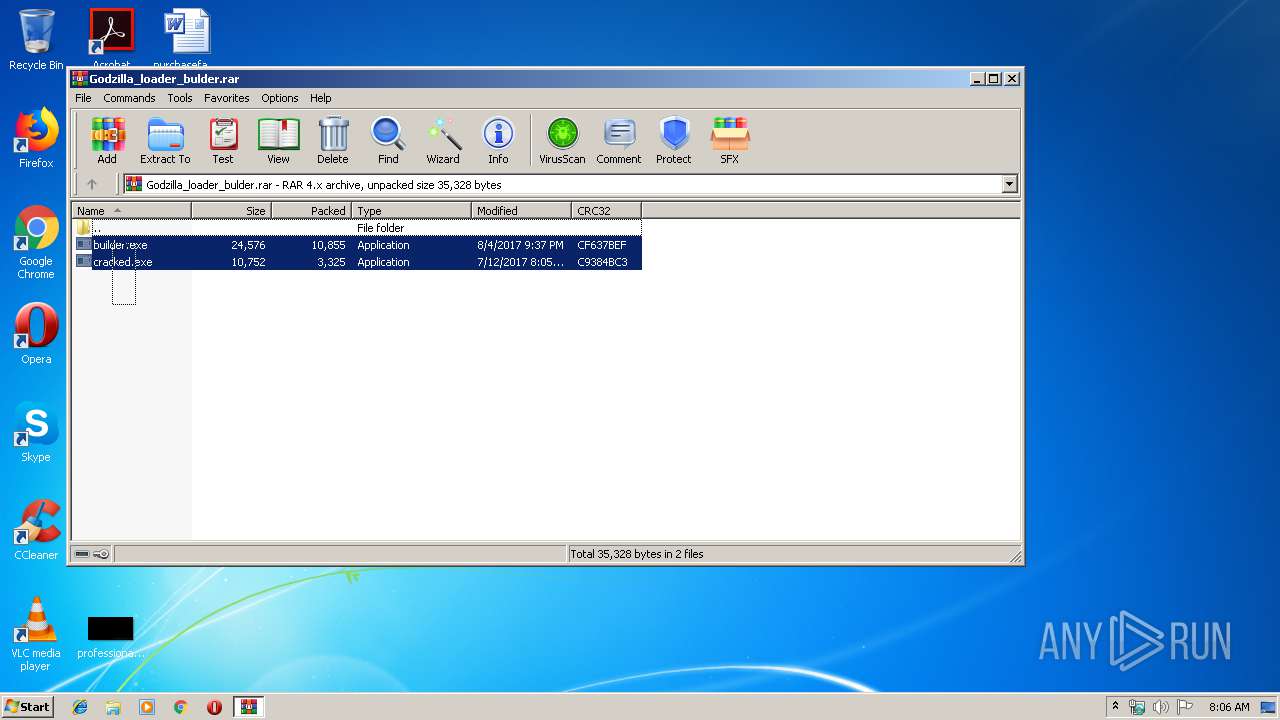
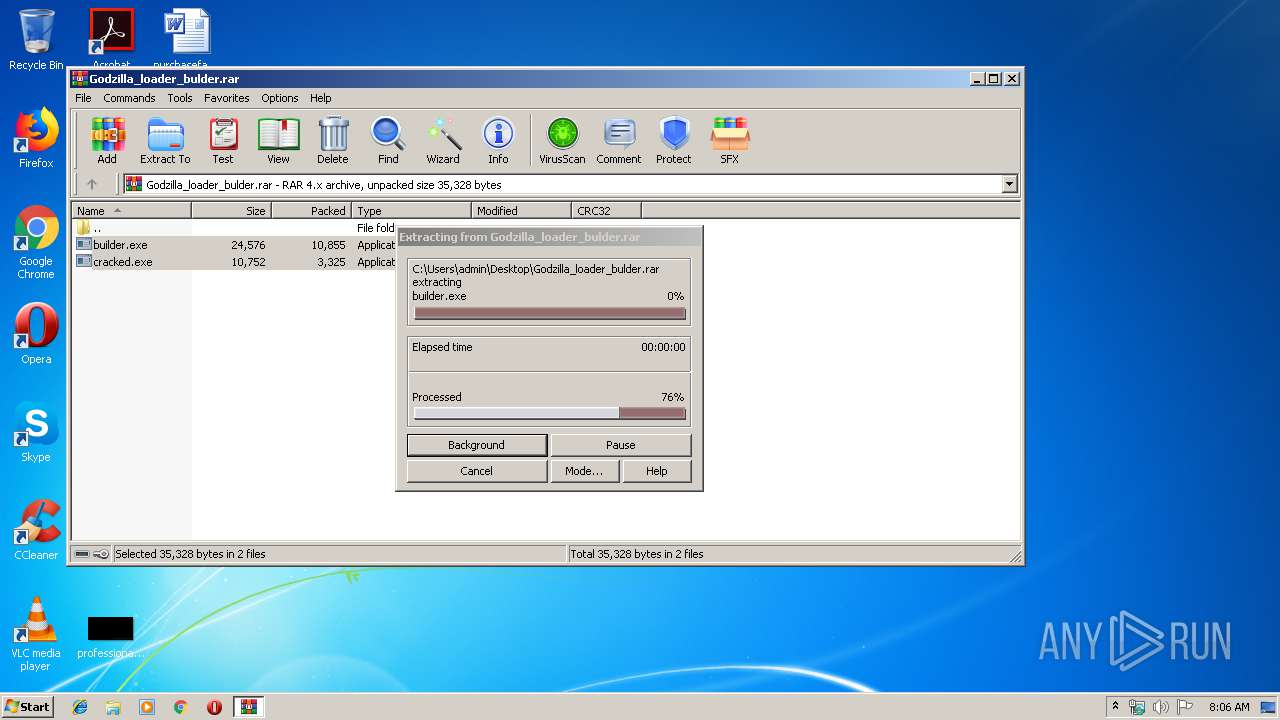
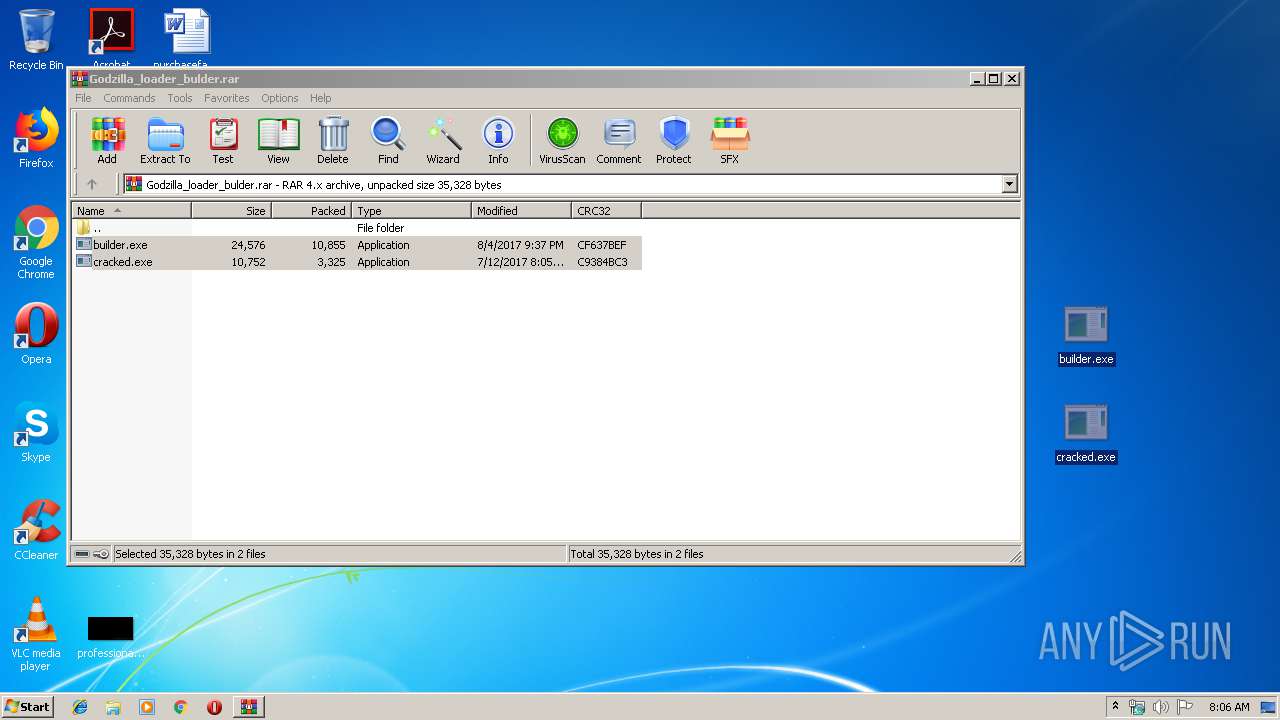
| File name: | Godzilla_loader_bulder.rar |
| Full analysis: | https://app.any.run/tasks/a6b2e75b-3b14-47f6-9291-ab618e15e1f8 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 08:06:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | CF9B8442C30BA42717224A8C0B040710 |
| SHA1: | 014618F7780AA06A4ADED1082CE4F739341CD2C0 |
| SHA256: | F9331B3B4C5F4FA95CCF776C575F674D08D982CA7C8335AB473FDA9EC1F9574F |
| SSDEEP: | 384:df4bDd6BK9g62lOUw+NXk8NFwd86fKDABnzcEGszhPByD:tCDdmKW6y7NVNud8SKMZzm6hPByD |
MALICIOUS
Application was dropped or rewritten from another process
- cracked.exe (PID: 3104)
- builder.exe (PID: 4044)
SUSPICIOUS
Reads internet explorer settings
- cracked.exe (PID: 3104)
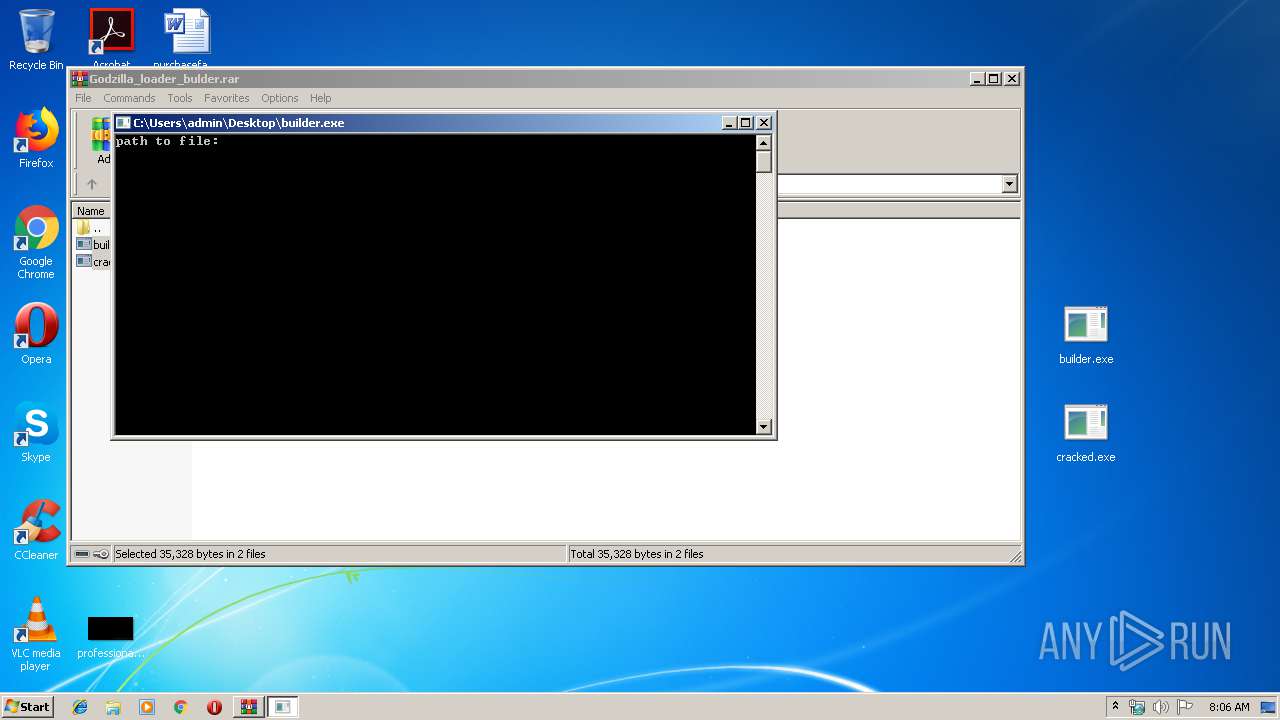
Starts CMD.EXE for commands execution
- cracked.exe (PID: 3104)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2924)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 10892 |
|---|---|
| UncompressedSize: | 24576 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:08:04 21:37:02 |
| PackingMethod: | Normal |
| ArchivedFileName: | builder.exe |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2924 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Godzilla_loader_bulder.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3104 | "C:\Users\admin\Desktop\cracked.exe" | C:\Users\admin\Desktop\cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
| 3520 | "C:\Windows\system32\cmd.exe" /c del C:\Users\admin\Desktop\cracked.exe >> NUL | C:\Windows\system32\cmd.exe | — | cracked.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4044 | "C:\Users\admin\Desktop\builder.exe" | C:\Users\admin\Desktop\builder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
435
Read events
409
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Godzilla_loader_bulder.rar | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2924) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3104) cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3104) cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
0
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\ErrorPageTemplate[1] | — | |
MD5:— | SHA256:— | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\errorPageStrings[1] | — | |
MD5:— | SHA256:— | |||
| 2924 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2924.10138\builder.exe | executable | |
MD5:— | SHA256:— | |||
| 2924 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2924.10138\cracked.exe | executable | |
MD5:— | SHA256:— | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\dnserrordiagoff_webOC[1] | html | |
MD5:— | SHA256:— | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\dnserrordiagoff_webOC[2] | html | |
MD5:— | SHA256:— | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\down[1] | image | |
MD5:555E83CE7F5D280D7454AF334571FB25 | SHA256:70F316A5492848BB8242D49539468830B353DDAA850964DB4E60A6D2D7DB4880 | |||
| 3104 | cracked.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3104 | cracked.exe | GET | — | 198.54.117.212:80 | http://www.lll14042016.xyz/gate.php?from=@ | US | — | — | malicious |
3104 | cracked.exe | GET | 302 | 192.64.119.78:80 | http://lll14042016.xyz/gate.php | US | html | 65 b | malicious |
3104 | cracked.exe | GET | 302 | 192.64.119.78:80 | http://lll14042016.xyz/gate.php | US | html | 65 b | malicious |
3104 | cracked.exe | GET | — | 198.54.117.212:80 | http://www.lll14042016.xyz/gate.php?from=@ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3104 | cracked.exe | 192.64.119.78:80 | lll14042016.xyz | Namecheap, Inc. | US | suspicious |
3104 | cracked.exe | 198.54.117.212:80 | www.lll14042016.xyz | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
shell.view |
| unknown |
lll14042016.xyz |
| malicious |
www.lll14042016.xyz |
| malicious |